IT Risk Management Report: Aztec Organization Cloud Adoption and Risks
VerifiedAdded on 2020/03/28
|20
|4952
|94
Report
AI Summary
This report provides a comprehensive analysis of IT risk management for the Aztec organization, focusing on the transition to cloud computing. It examines the current financial services review, security posture, and potential threats and vulnerabilities associated with cloud adoption. The report highlights the importance of ethical conduct and relevant legislation in financial services, including the Consumer and Competition Act 2010 and the Corporations Act 2001. It assesses risks through a matrix and emphasizes the need for a robust data security strategy. The report recommends a security framework encompassing client accumulation, secure portals, single-level security, and trust management. It also discusses the benefits of cloud computing, such as improved network management and resource scheduling, while addressing the inherent risks, including API insecurity, malicious attacks, and data leakage. The report concludes with recommendations to mitigate these risks and ensure a successful cloud transformation for the Aztec organization. It emphasizes the importance of adapting to changing digital technologies and managing operational policies effectively to reduce costs and enhance the company's turnover.

[IT Risks Management]
2017
2017
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

Executive summary:
The Aztec organization wants to transform their working tactics with new and advanced
features which helps in enhancing their turnover of the company. We as a project consultant
recommended the Aztec organization to change their business functionality with the
migration of business operation to the external cloud hosting solution. It has been seen that
the ethical code of conduct should be deprived in the curriculum of the Aztec organization to
improve the financial services by managing good and clear relationship with the banking
sector. The legislations which are used for providing financial insurance services to the Aztec
organization are categorised as consumer and competition act 2010, law implied for
Australian consumers, act passed for corporation 2001, amendment act 2012 for corporations,
financial act 2006 passed for counter terrorism and anti-money laundering schemes, and
protection act 2010 passed for national consumer. The operational policies of the Aztec
organization should focuses on deploying insurance service architecture. The budget of the
enterprise can be reduced by managing resources availability according to the demand of the
user. The InfoSec security model is used for securing the traditional processes and application
of the Aztec organization. Now it is recommended that with the changing digital technology,
the company has to transform their working to the cloud environment. The adoption of cloud
computing environment helps in dealing with network management, deployment of the
operating system and the databases, inclusion of resource scheduling plan, management of
the transactional processing, management of the concurrency control, and planning of
memory management. The management of risks is the basic criteria for managing the cloud
computing activities. The analysis of the security should be done with the help of qualitative
and quantitative research methodology. The migration towards the adoption of cloud is
equipped with some major threats which are classified as insecurity associated with the
application programming interfaces, inclusion of malicious and virus attacks, vulnerabilities
associated with the shared technologies, data leakages, hijacking of user account, and
inclusion of risk profile. The Aztec organization is recommended to consider some of the
major potential risks which are assimilated with the inclusion of cloud architecture in the
working curriculum of the enterprise.
1
The Aztec organization wants to transform their working tactics with new and advanced
features which helps in enhancing their turnover of the company. We as a project consultant
recommended the Aztec organization to change their business functionality with the
migration of business operation to the external cloud hosting solution. It has been seen that
the ethical code of conduct should be deprived in the curriculum of the Aztec organization to
improve the financial services by managing good and clear relationship with the banking
sector. The legislations which are used for providing financial insurance services to the Aztec
organization are categorised as consumer and competition act 2010, law implied for
Australian consumers, act passed for corporation 2001, amendment act 2012 for corporations,
financial act 2006 passed for counter terrorism and anti-money laundering schemes, and
protection act 2010 passed for national consumer. The operational policies of the Aztec
organization should focuses on deploying insurance service architecture. The budget of the
enterprise can be reduced by managing resources availability according to the demand of the
user. The InfoSec security model is used for securing the traditional processes and application
of the Aztec organization. Now it is recommended that with the changing digital technology,
the company has to transform their working to the cloud environment. The adoption of cloud
computing environment helps in dealing with network management, deployment of the
operating system and the databases, inclusion of resource scheduling plan, management of
the transactional processing, management of the concurrency control, and planning of
memory management. The management of risks is the basic criteria for managing the cloud
computing activities. The analysis of the security should be done with the help of qualitative
and quantitative research methodology. The migration towards the adoption of cloud is
equipped with some major threats which are classified as insecurity associated with the
application programming interfaces, inclusion of malicious and virus attacks, vulnerabilities
associated with the shared technologies, data leakages, hijacking of user account, and
inclusion of risk profile. The Aztec organization is recommended to consider some of the
major potential risks which are assimilated with the inclusion of cloud architecture in the
working curriculum of the enterprise.
1

Contents
Executive summary:..............................................................................................................................1
Introduction:..........................................................................................................................................3
Financial Services Review:....................................................................................................................3
Security posture Review:.......................................................................................................................5
Threats vulnerabilities and consequences assessment:..........................................................................9
Risks identification and assessment matrix:....................................................................................10
Data security:.......................................................................................................................................15
Recommendation:................................................................................................................................17
Conclusion:..........................................................................................................................................19
References:..........................................................................................................................................19
2
Executive summary:..............................................................................................................................1
Introduction:..........................................................................................................................................3
Financial Services Review:....................................................................................................................3
Security posture Review:.......................................................................................................................5
Threats vulnerabilities and consequences assessment:..........................................................................9
Risks identification and assessment matrix:....................................................................................10
Data security:.......................................................................................................................................15
Recommendation:................................................................................................................................17
Conclusion:..........................................................................................................................................19
References:..........................................................................................................................................19
2
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

Introduction:
The Aztec organization wants to transform their working tactics with new and advanced
features which helps in enhancing their turnover of the company. The senior executives of the
enterprise has decided to transform their working curriculum with the deployment of any one
of the recent technology into their enterprise such s bring your own device, migration to
cloud computing, changing techniques with IPv6, and other. We as a project consultant
recommended the Aztec organization to change their business functionality with the
migration of business operation to the external cloud hosting solution.
The changing of the traditional working style with the new innovative concepts is complied
with many risks and challenges. The adoption of cloud computing platform increases the
risks associated with the traditional physical infrastructure (Hogmen, 2012). The renovation
of the existing devices can be easily done with the inclusion of cloud environment with
minimum cost.
Financial Services Review:
The follow up of the standard are used for data security to manage the financial security
procedures. The analysis of the financial data is measured in terms of government norms. It
has been seen that the ethical code of conduct should be deprived in the curriculum of the
Aztec organization to improve the financial services by managing good and clear relationship
with the banking sector. The customers are provided with the unique banking codes for
carrying out effective transaction. The planning of the financial services helps in developing
cost effective plan (Chauhan, 2014). The operational policies of the Aztec organization
should focuses on deploying insurance service architecture. The budget of the enterprise can
be reduced by managing resources availability according to the demand of the user. The
capability of the financial sector can be improved with the deployment of cloud software as a
service model for effectively managing functions with suppliers, dealers, and customers, and
etc. (Dhammeratchi, 2012). The electronic trading services are used for managing the
financial services of the Aztec enterprise. The legislation plays an important role in
captivating insurance services provided to the financial department with regard to safety,
security, integrity, and reliability of the financial processes. It is significantly important for
managing rules and regulations associated with the implication of financial market. The
legislations which are used for providing financial insurance services to the Aztec
3
The Aztec organization wants to transform their working tactics with new and advanced
features which helps in enhancing their turnover of the company. The senior executives of the
enterprise has decided to transform their working curriculum with the deployment of any one
of the recent technology into their enterprise such s bring your own device, migration to
cloud computing, changing techniques with IPv6, and other. We as a project consultant
recommended the Aztec organization to change their business functionality with the
migration of business operation to the external cloud hosting solution.
The changing of the traditional working style with the new innovative concepts is complied
with many risks and challenges. The adoption of cloud computing platform increases the
risks associated with the traditional physical infrastructure (Hogmen, 2012). The renovation
of the existing devices can be easily done with the inclusion of cloud environment with
minimum cost.
Financial Services Review:
The follow up of the standard are used for data security to manage the financial security
procedures. The analysis of the financial data is measured in terms of government norms. It
has been seen that the ethical code of conduct should be deprived in the curriculum of the
Aztec organization to improve the financial services by managing good and clear relationship
with the banking sector. The customers are provided with the unique banking codes for
carrying out effective transaction. The planning of the financial services helps in developing
cost effective plan (Chauhan, 2014). The operational policies of the Aztec organization
should focuses on deploying insurance service architecture. The budget of the enterprise can
be reduced by managing resources availability according to the demand of the user. The
capability of the financial sector can be improved with the deployment of cloud software as a
service model for effectively managing functions with suppliers, dealers, and customers, and
etc. (Dhammeratchi, 2012). The electronic trading services are used for managing the
financial services of the Aztec enterprise. The legislation plays an important role in
captivating insurance services provided to the financial department with regard to safety,
security, integrity, and reliability of the financial processes. It is significantly important for
managing rules and regulations associated with the implication of financial market. The
legislations which are used for providing financial insurance services to the Aztec
3
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

organization are categorised as consumer and competition act 2010, law implied for
Australian consumers, act passed for corporation 2001, amendment act 2012 for corporations,
financial act 2006 passed for counter terrorism and anti-money laundering schemes, and
protection act 2010 passed for national consumer. The key legislation which are used for
providing efficient financial services for taking authorised decision for business activity, for
providing general legislation, legislation used for superannuation policies and standards, and
society life insurance. The licence and permits are used for providing insurance to the
financial services in the discipline of general ledger, provision developed for providing credit
schemes, services related with deposits and custody, and products affiliated to the financial
sector of the Aztec organization. The enterprise is moving towards the new and advanced
technology for enhancing the advice related to the financial productivity. The financial
products can be efficiently taken under consideration with the implication of legislation law
in using cloud environment. The market policies of the underlying product changed with the
cloud technology for increasing the market ability of the enterprise. It helps in remaining
ahead of the competitors in the financial sector by reducing the cost incurred on the resources
and other operational functions. The skills of the working employees can be enhanced with
the effective management of training and development program for fulfilling the requirement
of global demand due to the changing trends of new technology. The owner of the company
is working on reducing financial risks associated with the deployment of cloud environment
in the traditional working of the company. The financial risks can be reduced by the
following procedures:
Implication of Goods and service tax: The good and service tax associated with the
productivity should be taken under consideration for achieving the accuracy in the
optimization of the product. The GST credits can be claimed by the Aztec
organization in the later cases.
Policies related with reinsurance pool corporation: These policies help in
administrating and monitoring of the cyber-terrorism activities which focuses on
providing facilities to the primary insurers for resolving the issues related with the
insurance policies implied on commercial properties harmed by the cyber-terrorism.
The insurance packages used for providing supports to the practitioners of medical
market for achieving sustainability of the enterprise. The policies should be developed
for financial claims because the decision making capability of the owner can be
enhanced by focusing on the potential losses associated with failure of the business
4
Australian consumers, act passed for corporation 2001, amendment act 2012 for corporations,
financial act 2006 passed for counter terrorism and anti-money laundering schemes, and
protection act 2010 passed for national consumer. The key legislation which are used for
providing efficient financial services for taking authorised decision for business activity, for
providing general legislation, legislation used for superannuation policies and standards, and
society life insurance. The licence and permits are used for providing insurance to the
financial services in the discipline of general ledger, provision developed for providing credit
schemes, services related with deposits and custody, and products affiliated to the financial
sector of the Aztec organization. The enterprise is moving towards the new and advanced
technology for enhancing the advice related to the financial productivity. The financial
products can be efficiently taken under consideration with the implication of legislation law
in using cloud environment. The market policies of the underlying product changed with the
cloud technology for increasing the market ability of the enterprise. It helps in remaining
ahead of the competitors in the financial sector by reducing the cost incurred on the resources
and other operational functions. The skills of the working employees can be enhanced with
the effective management of training and development program for fulfilling the requirement
of global demand due to the changing trends of new technology. The owner of the company
is working on reducing financial risks associated with the deployment of cloud environment
in the traditional working of the company. The financial risks can be reduced by the
following procedures:
Implication of Goods and service tax: The good and service tax associated with the
productivity should be taken under consideration for achieving the accuracy in the
optimization of the product. The GST credits can be claimed by the Aztec
organization in the later cases.
Policies related with reinsurance pool corporation: These policies help in
administrating and monitoring of the cyber-terrorism activities which focuses on
providing facilities to the primary insurers for resolving the issues related with the
insurance policies implied on commercial properties harmed by the cyber-terrorism.
The insurance packages used for providing supports to the practitioners of medical
market for achieving sustainability of the enterprise. The policies should be developed
for financial claims because the decision making capability of the owner can be
enhanced by focusing on the potential losses associated with failure of the business
4

operations. The funding activities associated with enterprise helps in levying the
charges associated with financial activities.
The capability of the financial services helps in improving the productivity of the
organization which creates the environment of innovation by providing open platform for
exchanging of vision, thoughts, and business advice. The skills and knowledge of the
employees should be improved according to the requirement of management policies for
cloud environment. The business strategies should be focused on the health and safety
requirement for improving the working standards of the employees. The transformation of
traditional working structure with the cloud computing infrastructure can affect the legal
compliance with government policies. The working employees should be provided with the
standard equipment. The insurance is required for providing general liability to provide
financial services to the employees at the time of personal injuries. The superannuation
liability helps in developing laws for overcoming the breaches. The financial insurance
policies are used for providing financial covers for theft, resource utilization, and others. The
operational policies of the Aztec organization should focuses on deploying insurance service
architecture. The budget of the enterprise can be reduced by managing resources availability
according to the demand of the user.
Security posture Review:
It has been seen that the traditional working of the enterprise have older version devices
which are placed with the help of wires and cables. USB and CD drives are used for storing
the data of the organization. The IT department is working on legacy system with the
incorporation of adequate security policies. The InfoSec security model is used for securing
the traditional processes and application of the Aztec organization. Now it is recommended
that with the changing digital technology, the company has to transform their working to the
cloud environment. The cloud environment is capable of resolving all the issues of the
company which exist with the continuation of the business application. The renovation of the
existing devices can be easily done with the inclusion of cloud environment with minimum
cost. The data storage capability of the organization can be improved with the management of
data on the cloud using Hadoop file system. The Hadoop file system can efficiently maintains
the big data of the enterprise for easy retrieval of information. The most important step is to
develop a security architecture for the Aztec organization to overcome the problem of risks
and challenges. The services provided to the end user can be made secure by organizing a
5
charges associated with financial activities.
The capability of the financial services helps in improving the productivity of the
organization which creates the environment of innovation by providing open platform for
exchanging of vision, thoughts, and business advice. The skills and knowledge of the
employees should be improved according to the requirement of management policies for
cloud environment. The business strategies should be focused on the health and safety
requirement for improving the working standards of the employees. The transformation of
traditional working structure with the cloud computing infrastructure can affect the legal
compliance with government policies. The working employees should be provided with the
standard equipment. The insurance is required for providing general liability to provide
financial services to the employees at the time of personal injuries. The superannuation
liability helps in developing laws for overcoming the breaches. The financial insurance
policies are used for providing financial covers for theft, resource utilization, and others. The
operational policies of the Aztec organization should focuses on deploying insurance service
architecture. The budget of the enterprise can be reduced by managing resources availability
according to the demand of the user.
Security posture Review:
It has been seen that the traditional working of the enterprise have older version devices
which are placed with the help of wires and cables. USB and CD drives are used for storing
the data of the organization. The IT department is working on legacy system with the
incorporation of adequate security policies. The InfoSec security model is used for securing
the traditional processes and application of the Aztec organization. Now it is recommended
that with the changing digital technology, the company has to transform their working to the
cloud environment. The cloud environment is capable of resolving all the issues of the
company which exist with the continuation of the business application. The renovation of the
existing devices can be easily done with the inclusion of cloud environment with minimum
cost. The data storage capability of the organization can be improved with the management of
data on the cloud using Hadoop file system. The Hadoop file system can efficiently maintains
the big data of the enterprise for easy retrieval of information. The most important step is to
develop a security architecture for the Aztec organization to overcome the problem of risks
and challenges. The services provided to the end user can be made secure by organizing a
5
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
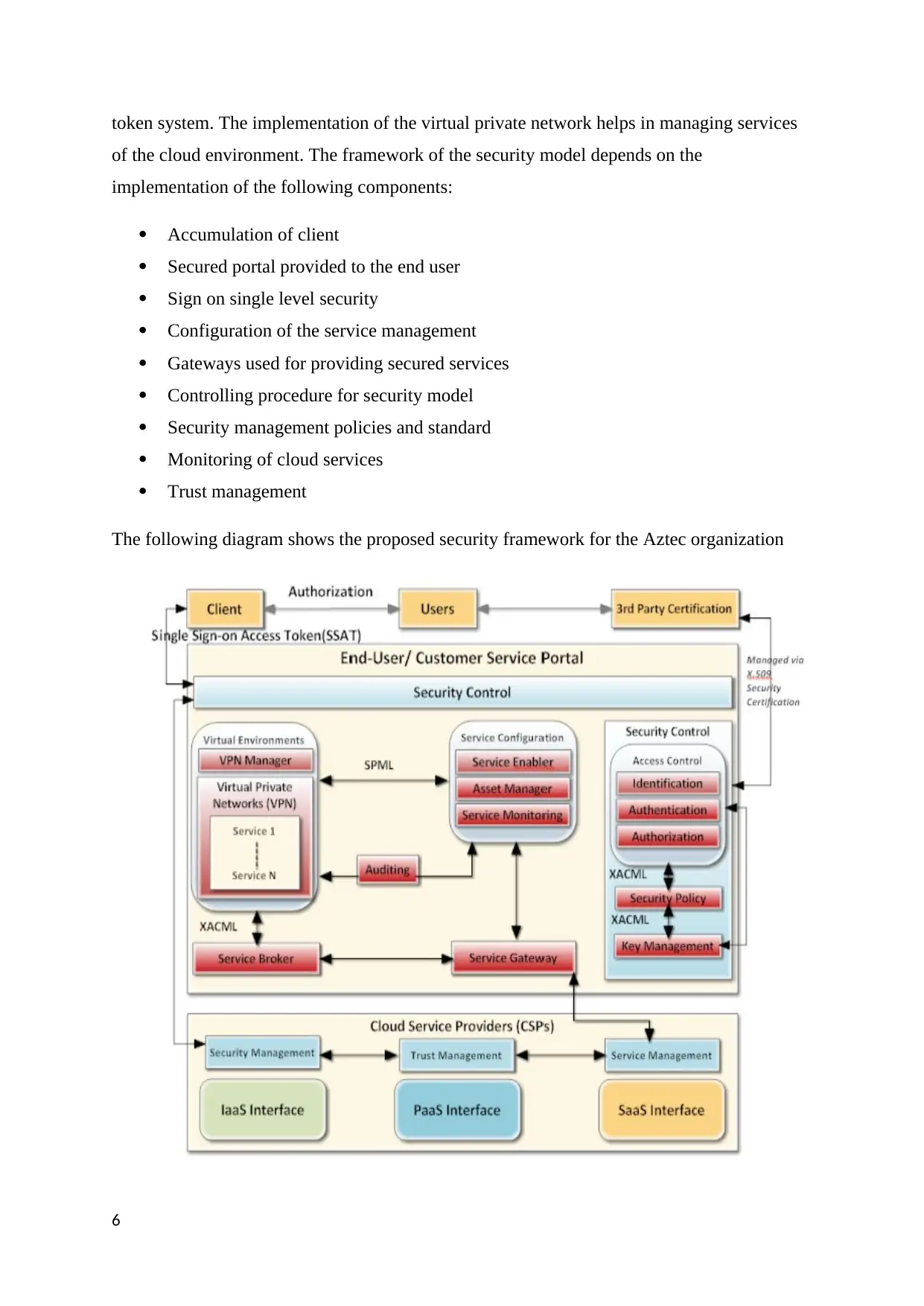
token system. The implementation of the virtual private network helps in managing services
of the cloud environment. The framework of the security model depends on the
implementation of the following components:
Accumulation of client
Secured portal provided to the end user
Sign on single level security
Configuration of the service management
Gateways used for providing secured services
Controlling procedure for security model
Security management policies and standard
Monitoring of cloud services
Trust management
The following diagram shows the proposed security framework for the Aztec organization
6
of the cloud environment. The framework of the security model depends on the
implementation of the following components:
Accumulation of client
Secured portal provided to the end user
Sign on single level security
Configuration of the service management
Gateways used for providing secured services
Controlling procedure for security model
Security management policies and standard
Monitoring of cloud services
Trust management
The following diagram shows the proposed security framework for the Aztec organization
6
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
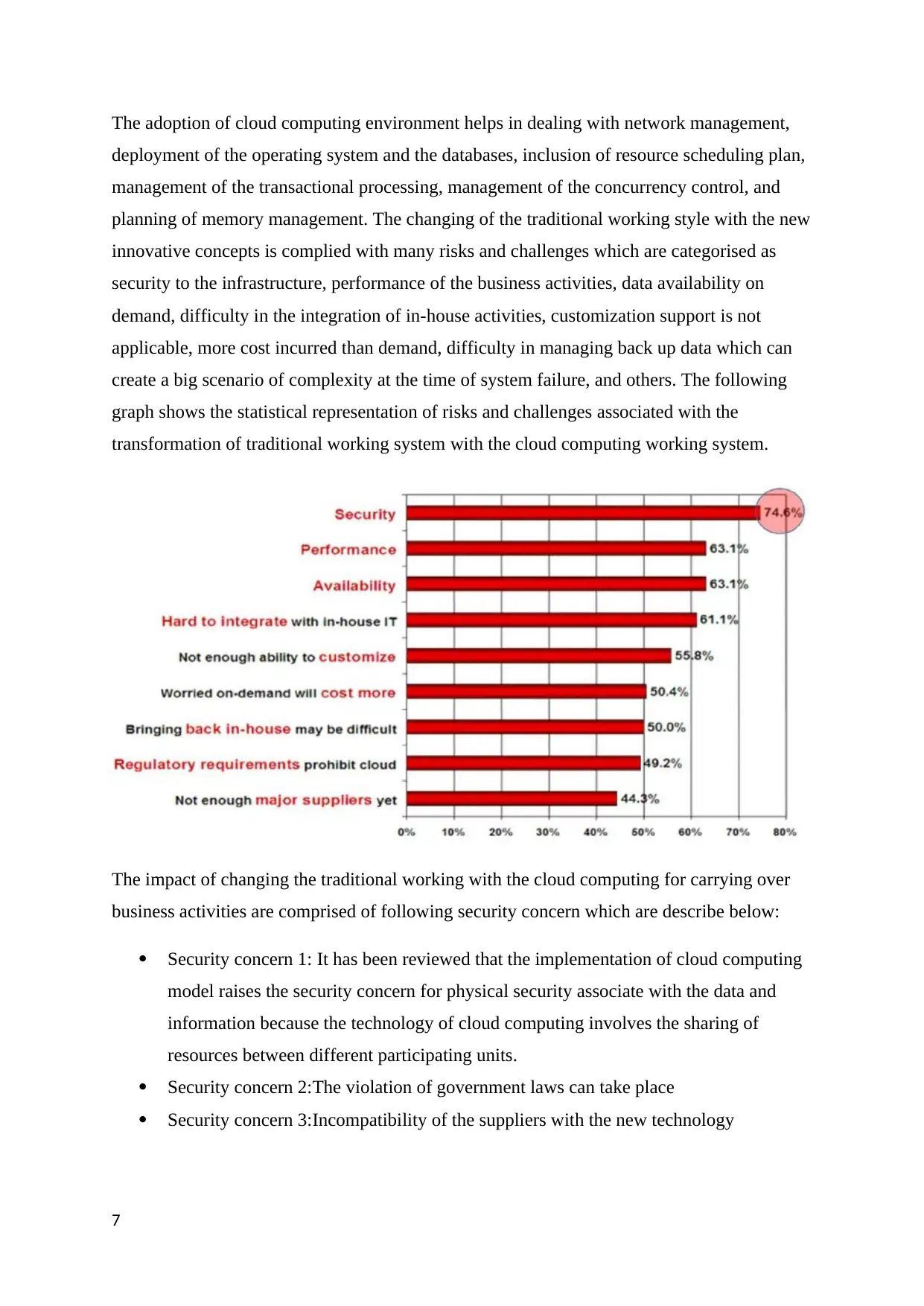
The adoption of cloud computing environment helps in dealing with network management,
deployment of the operating system and the databases, inclusion of resource scheduling plan,
management of the transactional processing, management of the concurrency control, and
planning of memory management. The changing of the traditional working style with the new
innovative concepts is complied with many risks and challenges which are categorised as
security to the infrastructure, performance of the business activities, data availability on
demand, difficulty in the integration of in-house activities, customization support is not
applicable, more cost incurred than demand, difficulty in managing back up data which can
create a big scenario of complexity at the time of system failure, and others. The following
graph shows the statistical representation of risks and challenges associated with the
transformation of traditional working system with the cloud computing working system.
The impact of changing the traditional working with the cloud computing for carrying over
business activities are comprised of following security concern which are describe below:
Security concern 1: It has been reviewed that the implementation of cloud computing
model raises the security concern for physical security associate with the data and
information because the technology of cloud computing involves the sharing of
resources between different participating units.
Security concern 2:The violation of government laws can take place
Security concern 3:Incompatibility of the suppliers with the new technology
7
deployment of the operating system and the databases, inclusion of resource scheduling plan,
management of the transactional processing, management of the concurrency control, and
planning of memory management. The changing of the traditional working style with the new
innovative concepts is complied with many risks and challenges which are categorised as
security to the infrastructure, performance of the business activities, data availability on
demand, difficulty in the integration of in-house activities, customization support is not
applicable, more cost incurred than demand, difficulty in managing back up data which can
create a big scenario of complexity at the time of system failure, and others. The following
graph shows the statistical representation of risks and challenges associated with the
transformation of traditional working system with the cloud computing working system.
The impact of changing the traditional working with the cloud computing for carrying over
business activities are comprised of following security concern which are describe below:
Security concern 1: It has been reviewed that the implementation of cloud computing
model raises the security concern for physical security associate with the data and
information because the technology of cloud computing involves the sharing of
resources between different participating units.
Security concern 2:The violation of government laws can take place
Security concern 3:Incompatibility of the suppliers with the new technology
7

Security concern 4: Focus should be given on the authorised person who is
responsible for performing the action of encryption and decryption associated with the
working capabilities of the organization (Zhao, 2015).
Security concern 5: The methodology responsible for performing actions related with
data integrity, data transfer, data retrieval, and data storage. The authorised
transaction should be ensured for managing the integrity of the data.
Security concern 6: The follow up of the standard used for data security to manage the
financial security procedures (Greenwood, 2014).
Security concern 7: The updated information should be provided for upgrading the
traditional applications according requirement of cloud computing environment.
Security concern 8: The analysis of the financial data to be measured in terms of
government norms.
Security concern 9: The fluidity of the virtual machine should be taken into
consideration for maintaining the security consistency (Garg, 2013).
Security concern 10: The violation of the private rights should be taken under
consideration for managing the services provided by the cloud.
The management of risks is the basic criteria for managing the cloud computing activities.
The analysis of the security should be done with the help of qualitative and quantitative
research methodology. The research methodology was designed to analyse the risks
associated with the migration to cloud computing environment.
Questionnaire: The arrangement of questionnaire with the top executives of the
enterprise helps in generating ideas, opinions, thoughts, and vision in adopting new
technology for increasing the efficiency of the business operation. We analysed that
the top executives are satisfied with the services provided by the cloud computing
environment than the traditional way of working. The questions are organized to
analyse the benefits of cloud computing environment and the security concern
associated with the migration of traditional platform.
Data collection techniques: The data are collected from different sources to evaluate
the measurement of strategic decision to transform their working tactics. It has been
analysed that the cloud computing environment play a vital role in overcoming the
flaws of the traditional system.
8
responsible for performing the action of encryption and decryption associated with the
working capabilities of the organization (Zhao, 2015).
Security concern 5: The methodology responsible for performing actions related with
data integrity, data transfer, data retrieval, and data storage. The authorised
transaction should be ensured for managing the integrity of the data.
Security concern 6: The follow up of the standard used for data security to manage the
financial security procedures (Greenwood, 2014).
Security concern 7: The updated information should be provided for upgrading the
traditional applications according requirement of cloud computing environment.
Security concern 8: The analysis of the financial data to be measured in terms of
government norms.
Security concern 9: The fluidity of the virtual machine should be taken into
consideration for maintaining the security consistency (Garg, 2013).
Security concern 10: The violation of the private rights should be taken under
consideration for managing the services provided by the cloud.
The management of risks is the basic criteria for managing the cloud computing activities.
The analysis of the security should be done with the help of qualitative and quantitative
research methodology. The research methodology was designed to analyse the risks
associated with the migration to cloud computing environment.
Questionnaire: The arrangement of questionnaire with the top executives of the
enterprise helps in generating ideas, opinions, thoughts, and vision in adopting new
technology for increasing the efficiency of the business operation. We analysed that
the top executives are satisfied with the services provided by the cloud computing
environment than the traditional way of working. The questions are organized to
analyse the benefits of cloud computing environment and the security concern
associated with the migration of traditional platform.
Data collection techniques: The data are collected from different sources to evaluate
the measurement of strategic decision to transform their working tactics. It has been
analysed that the cloud computing environment play a vital role in overcoming the
flaws of the traditional system.
8
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

Literature review: The documentation of the organization which are enrolling on the
principles of cloud computing should be reviewed to analyse the actual situation and
benefits and risks associated with this working platform.
Threats vulnerabilities and consequences assessment:
The migration process is equipped with threats and vulnerabilities because the
implementation of the new architecture involves the change management program of the
traditional working architecture (Samad, 2014). The migration towards the adoption of cloud
is equipped with some major threats which are classified as insecurity associated with the
application programming interfaces, inclusion of malicious and virus attacks, vulnerabilities
associated with the shared technologies, data leakages, hijacking of user account, and
inclusion of risk profile. The Aztec organization is recommended to consider some of the
major potential risks which are assimilated with the inclusion of cloud architecture in the
working curriculum of the enterprise.
The implementation of the interoperable operation issues related with the deployment
of the communication network between participating units. The compatibility of
managing the cloud devices is the major concern area in the deployment of cloud
architecture.
It is difficult to port all the application on the cloud environment. The portability of
the application should be taken into consideration (Bhopale, 2013).
Migration to the cloud environment involves changes in the new environment
required the setting of goal, funding sources, required skilled staff, and others.
The financial management of required resources involves the estimation of cost
required to purchase resources. The failure of estimation can affect the budget of the
organization.
Organization of service level agreement involves clear specification of goals, mission,
and services provided by the cloud providers. It helps in specifying the distribution of
roles and responsibilities between the customers and stakeholders. It is difficult to
prepare the metric for the deliverables of the project in the initial phases of the
migration of activities to the cloud environment. The failure of service level
agreement can affect the working operation of the enterprise.
9
principles of cloud computing should be reviewed to analyse the actual situation and
benefits and risks associated with this working platform.
Threats vulnerabilities and consequences assessment:
The migration process is equipped with threats and vulnerabilities because the
implementation of the new architecture involves the change management program of the
traditional working architecture (Samad, 2014). The migration towards the adoption of cloud
is equipped with some major threats which are classified as insecurity associated with the
application programming interfaces, inclusion of malicious and virus attacks, vulnerabilities
associated with the shared technologies, data leakages, hijacking of user account, and
inclusion of risk profile. The Aztec organization is recommended to consider some of the
major potential risks which are assimilated with the inclusion of cloud architecture in the
working curriculum of the enterprise.
The implementation of the interoperable operation issues related with the deployment
of the communication network between participating units. The compatibility of
managing the cloud devices is the major concern area in the deployment of cloud
architecture.
It is difficult to port all the application on the cloud environment. The portability of
the application should be taken into consideration (Bhopale, 2013).
Migration to the cloud environment involves changes in the new environment
required the setting of goal, funding sources, required skilled staff, and others.
The financial management of required resources involves the estimation of cost
required to purchase resources. The failure of estimation can affect the budget of the
organization.
Organization of service level agreement involves clear specification of goals, mission,
and services provided by the cloud providers. It helps in specifying the distribution of
roles and responsibilities between the customers and stakeholders. It is difficult to
prepare the metric for the deliverables of the project in the initial phases of the
migration of activities to the cloud environment. The failure of service level
agreement can affect the working operation of the enterprise.
9
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

The encryption and decryption of files can affect the confidentiality of the information
stored on the third party cloud environment.
Failure of managing backups can result into the development of big complex scenario
at the time of network failure.
The expectation of high skilled employees can be failure in determining right person
for the right job. It leads to inefficiency in the completion of business activities.
It is difficult in tracking of the potential risks associated with the projects because the
migration to the cloud environment changes the risks associated with the project.
Threats associated with the migration of business activities to the platform of cloud
computing architecture
It is difficult to estimate the cost associated with the flow of data transfer.
It is not guaranteed that the services level agreement determinants will be completely
fulfilled or not (Kushwah, 2013).
Risks identification and assessment matrix:
Identification of risks Categorise of attack Explanation Consequences
Theft of data
associated with cloud
services
The unauthenticated
person can access the
data from the internet
Physical security of
the cloud
infrastructure get
affected
Inclusion of DOS
attack
Distributed The supply and
demand of the
resources is not met
Adverse impact on
cloud network
Hypertext Scheduling the
history of resources
used
XML XML signatures are
used getting
unauthorised
accessing of data
from the cloud
etwork
Attack of viruses and
malware
Leaking of
confidential
The infrastructure of
the cloud is get
10
stored on the third party cloud environment.
Failure of managing backups can result into the development of big complex scenario
at the time of network failure.
The expectation of high skilled employees can be failure in determining right person
for the right job. It leads to inefficiency in the completion of business activities.
It is difficult in tracking of the potential risks associated with the projects because the
migration to the cloud environment changes the risks associated with the project.
Threats associated with the migration of business activities to the platform of cloud
computing architecture
It is difficult to estimate the cost associated with the flow of data transfer.
It is not guaranteed that the services level agreement determinants will be completely
fulfilled or not (Kushwah, 2013).
Risks identification and assessment matrix:
Identification of risks Categorise of attack Explanation Consequences
Theft of data
associated with cloud
services
The unauthenticated
person can access the
data from the internet
Physical security of
the cloud
infrastructure get
affected
Inclusion of DOS
attack
Distributed The supply and
demand of the
resources is not met
Adverse impact on
cloud network
Hypertext Scheduling the
history of resources
used
XML XML signatures are
used getting
unauthorised
accessing of data
from the cloud
etwork
Attack of viruses and
malware
Leaking of
confidential
The infrastructure of
the cloud is get
10

information of the
user login
Data leakages
The change in
behaviour of the
cloud services
affected
The implementation
of the virtual system
Time Data loss Cloud physical
infrastructureEnergy consumption Resources used
Process of memory
sharing
Resources are leaked
on the external
environment
Cloud physical
infrastructure
User credentials are
leaked
Direct attack of
malware and viruses
Adverse effect of
phishing process
Accessing of user
credentials
Cloud network and
cloud physical
infrastructureInstallation of the
malicious codes and
viruses
Change in the
behaviour of cloud
services
Unavailability of the
information to the
requested client
Installation of the
botnets
Unauthorised
accessing of the
cloud resource from
the external parties
Cloud network and
cloud physical
infrastructure
11
user login
Data leakages
The change in
behaviour of the
cloud services
affected
The implementation
of the virtual system
Time Data loss Cloud physical
infrastructureEnergy consumption Resources used
Process of memory
sharing
Resources are leaked
on the external
environment
Cloud physical
infrastructure
User credentials are
leaked
Direct attack of
malware and viruses
Adverse effect of
phishing process
Accessing of user
credentials
Cloud network and
cloud physical
infrastructureInstallation of the
malicious codes and
viruses
Change in the
behaviour of cloud
services
Unavailability of the
information to the
requested client
Installation of the
botnets
Unauthorised
accessing of the
cloud resource from
the external parties
Cloud network and
cloud physical
infrastructure
11
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
1 out of 20
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.





