SEC 410: IT Security Report: Designing Security for E-commerce
VerifiedAdded on 2020/04/07
|20
|4157
|31
Report
AI Summary
This IT security report, focusing on the protection of e-commerce websites, delves into critical aspects of network and data security. The report begins with an executive summary, outlining the challenges faced by e-commerce businesses, including database abuses and various types of attacks. It provides a comprehensive literature review, examining the integration of corporate environments, intrusion detection systems (IDS), web vulnerability scanners (WVS), and network firewalls. The report explores the functions of IDS, including network-based and host-based systems, and analyzes the significance of WVS, such as SQL injection and cross-site scripting (XSS) vulnerabilities. Furthermore, it offers a comparison between IDS, WFS, and firewalls, concluding with recommendations for effective security implementations. The report emphasizes the importance of designing security policies, auditing networks, and selecting appropriate IDS to safeguard web information and protect e-commerce businesses from threats. The report also focuses on the merging of two organizations and its impact on IT security.

Running Header: IT Security 1
SEC 410 Web & Data Security Paper
Submitted By
Course
Professor
Date
SEC 410 Web & Data Security Paper
Submitted By
Course
Professor
Date
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

IT Security 2
Table of Contents
1. Executive Summary.............................................................................................................................2
2. Introduction........................................................................................................................................3
2.1 Problem Statement...........................................................................................................................4
2.2 Purpose.............................................................................................................................................4
3. Literature Review....................................................................................................................................4
3.1 Integrating Both Corporate Environments.......................................................................................4
3.2 Intrusion Detection System (IDS)......................................................................................................6
3.2.1 Network based IDS -..................................................................................................................7
3.2.2 Host Based IDS...........................................................................................................................7
3.3 Web Vulnerability Scanners..............................................................................................................8
3.3.1 SQL Injection -............................................................................................................................8
32.3.2 Cross-site Scripting (XSS):........................................................................................................9
WAVS by HTTP Method....................................................................................................................10
JAVA Tool -........................................................................................................................................11
3.3 Network Firewall Devices...............................................................................................................11
3.3.1 Application Level Firewalls -....................................................................................................12
3.3.2 Multilayer Firewalls -...............................................................................................................13
4. Comparison between IDS, WFS and Firewall...................................................................................14
5. Conclusion.........................................................................................................................................14
6. References.........................................................................................................................................15
2. Budget...............................................................................................................................................19
Table of Contents
1. Executive Summary.............................................................................................................................2
2. Introduction........................................................................................................................................3
2.1 Problem Statement...........................................................................................................................4
2.2 Purpose.............................................................................................................................................4
3. Literature Review....................................................................................................................................4
3.1 Integrating Both Corporate Environments.......................................................................................4
3.2 Intrusion Detection System (IDS)......................................................................................................6
3.2.1 Network based IDS -..................................................................................................................7
3.2.2 Host Based IDS...........................................................................................................................7
3.3 Web Vulnerability Scanners..............................................................................................................8
3.3.1 SQL Injection -............................................................................................................................8
32.3.2 Cross-site Scripting (XSS):........................................................................................................9
WAVS by HTTP Method....................................................................................................................10
JAVA Tool -........................................................................................................................................11
3.3 Network Firewall Devices...............................................................................................................11
3.3.1 Application Level Firewalls -....................................................................................................12
3.3.2 Multilayer Firewalls -...............................................................................................................13
4. Comparison between IDS, WFS and Firewall...................................................................................14
5. Conclusion.........................................................................................................................................14
6. References.........................................................................................................................................15
2. Budget...............................................................................................................................................19

IT Security 3
1.Executive Summary
The network security in an organization is the main line of protection to achieve data affirmation.
The system network is at risk without a very much composed and perfect actualized network
security strategy. The principle issue is that system managers are not ready to check the system
security arrangement. In spite of the fact that additionally examine has been done, it principally
concerns some general issue. The network administration of security, operations as well as
services in large scale endeavor systems is getting to be more troublesome because of complex
security arrangements of the merged associations and furthermore because of dynamic changes
in network topologies.
In e-commerce business effectiveness matters for the network application. The transaction of
data in e-business finds some challenges like database abuses, log information mining and
sniffing assaults which can be settled by utilizing distinctive safety effort. Subsequently security
is vital in online business application. The research in this report mainly focused on identifying
vulnerabilities, which comes about because of unreliable data flow in web applications like
cross-site scripting and SQL infusion have additionally expanded. Infusion Attacks misuse
vulnerabilities of sites by embedding’s and executing malignant code like data query, JavaScript
capacities in susceptible clients, processing environment or on a web server. In this report, Web
Vulnerability Scanner (WVS) policy which questions the vulnerable segment of applications and
then distinguished and analyzed it offline. Also, firewalls and IDS systems are analyzed for its
successful implementation in the merged IT environments.
1.Executive Summary
The network security in an organization is the main line of protection to achieve data affirmation.
The system network is at risk without a very much composed and perfect actualized network
security strategy. The principle issue is that system managers are not ready to check the system
security arrangement. In spite of the fact that additionally examine has been done, it principally
concerns some general issue. The network administration of security, operations as well as
services in large scale endeavor systems is getting to be more troublesome because of complex
security arrangements of the merged associations and furthermore because of dynamic changes
in network topologies.
In e-commerce business effectiveness matters for the network application. The transaction of
data in e-business finds some challenges like database abuses, log information mining and
sniffing assaults which can be settled by utilizing distinctive safety effort. Subsequently security
is vital in online business application. The research in this report mainly focused on identifying
vulnerabilities, which comes about because of unreliable data flow in web applications like
cross-site scripting and SQL infusion have additionally expanded. Infusion Attacks misuse
vulnerabilities of sites by embedding’s and executing malignant code like data query, JavaScript
capacities in susceptible clients, processing environment or on a web server. In this report, Web
Vulnerability Scanner (WVS) policy which questions the vulnerable segment of applications and
then distinguished and analyzed it offline. Also, firewalls and IDS systems are analyzed for its
successful implementation in the merged IT environments.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

IT Security 4
2.Introduction
The process of security management is important in order to refine the existing arrangement and
also to develop new strategies as the risk as well as processing services. The process of
developing IT security process provides the knowledge of existing threats. There is dependably
a requirement to keep up the trust of customers for an effective figuring service. The compelling
security arrangement development process is the assessment of threats. (Anand, V. & Saniie, J.,
2012). The various security efforts in global e commerce business have different techniques and
systems for various purposes. Distinctive techniques are appropriate for particular circumstances.
We characterize the probability of a misrepresentation as a threat.
Various areas in e-commerce business like networking, storing data, various scanning
methodology and to investigate various threats. The current policies are unable to fulfill all the
requirements of users. Implementing security policy is considered as a challenge as well as the
primary issue for web based business. Network security can be considered as the various steps
that are taken for preventing any type of data loss. Securing the whole networking system
requires the coordination of a wide assortment of safety efforts from making user records to hire
better representatives and to keep the server secured in a room. As I am appointed as the
consultant for designing network and IT security for enhancing global site. My responsibility is
to design security document for e-commerce website as well as the merged organization by
considering all facts and figures. (Kaur, K. & Dr. Pathak, A., 2015).
2.1 Problem Statement
As we know that network e-commerce website are more intense to any type of threat or risk, as
all the customer information like their personal information, their banking information etc are
saved online. The main targets of hackers are these online sites through which they can hack all
the important and confidential information of clients.
2.Introduction
The process of security management is important in order to refine the existing arrangement and
also to develop new strategies as the risk as well as processing services. The process of
developing IT security process provides the knowledge of existing threats. There is dependably
a requirement to keep up the trust of customers for an effective figuring service. The compelling
security arrangement development process is the assessment of threats. (Anand, V. & Saniie, J.,
2012). The various security efforts in global e commerce business have different techniques and
systems for various purposes. Distinctive techniques are appropriate for particular circumstances.
We characterize the probability of a misrepresentation as a threat.
Various areas in e-commerce business like networking, storing data, various scanning
methodology and to investigate various threats. The current policies are unable to fulfill all the
requirements of users. Implementing security policy is considered as a challenge as well as the
primary issue for web based business. Network security can be considered as the various steps
that are taken for preventing any type of data loss. Securing the whole networking system
requires the coordination of a wide assortment of safety efforts from making user records to hire
better representatives and to keep the server secured in a room. As I am appointed as the
consultant for designing network and IT security for enhancing global site. My responsibility is
to design security document for e-commerce website as well as the merged organization by
considering all facts and figures. (Kaur, K. & Dr. Pathak, A., 2015).
2.1 Problem Statement
As we know that network e-commerce website are more intense to any type of threat or risk, as
all the customer information like their personal information, their banking information etc are
saved online. The main targets of hackers are these online sites through which they can hack all
the important and confidential information of clients.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

IT Security 5
2.2 Purpose
The main purpose of this IT security report is to design a security policy for the e-commerce
website, to determine network auditing process and to determine which IDS (Intrusion Detection
System) will be better for e-commerce website. This report will upgrade the opportunity to
secure the web information. The main purpose behind this report is to make e-commerce
business secure from the hackers, SQL injection or any type of vulnerability.
3. Literature Review
3.1 Integrating Both Corporate Environments
Merging of two organizations is meant to merge the two different cultures through a
corresponding impact. The integration will require the selection by the undertaking of the other
organization's culture. The detachment requires the protection of the culture of the second
organization. The ingestion incorporation between these two organizations will be prescribed
when administration and the organization methods for the merged organization are not planned
to be kept. This policy of merging of organizations is intended to revamp the assets of the
acquirer and of the obtained endeavor inside another entire for the acquisition of scale as well as
economies, on the administrative practices and the reinforcing the competitive environment. This
merging strategy is acknowledged from method of rationale identified with its activities or their
complementarity that propose to acknowledge cooperative energies. In this way, the presence of
methodological associations, supported with the absence of specificity, prompts to the
integration of associations which go through a retention incorporation process. (Vancea, M.,
2011).
2.2 Purpose
The main purpose of this IT security report is to design a security policy for the e-commerce
website, to determine network auditing process and to determine which IDS (Intrusion Detection
System) will be better for e-commerce website. This report will upgrade the opportunity to
secure the web information. The main purpose behind this report is to make e-commerce
business secure from the hackers, SQL injection or any type of vulnerability.
3. Literature Review
3.1 Integrating Both Corporate Environments
Merging of two organizations is meant to merge the two different cultures through a
corresponding impact. The integration will require the selection by the undertaking of the other
organization's culture. The detachment requires the protection of the culture of the second
organization. The ingestion incorporation between these two organizations will be prescribed
when administration and the organization methods for the merged organization are not planned
to be kept. This policy of merging of organizations is intended to revamp the assets of the
acquirer and of the obtained endeavor inside another entire for the acquisition of scale as well as
economies, on the administrative practices and the reinforcing the competitive environment. This
merging strategy is acknowledged from method of rationale identified with its activities or their
complementarity that propose to acknowledge cooperative energies. In this way, the presence of
methodological associations, supported with the absence of specificity, prompts to the
integration of associations which go through a retention incorporation process. (Vancea, M.,
2011).

IT Security 6
Taken from (Gringolts, V., 2015).
Absence of synchronization in IT framework in both organizations can have challenges with
regular business processes like hiring staff, sales, customer records etc. This challenges will be a
reason to slow all the daily processes. If both organization's IT processes will not integrate,
various errors or network threat can be possible. It will diverts both organizations from
concentrating on their center business capabilities. As both the procured and the obtaining
organization come in with independent financial frameworks, providers, accomplices, it is
crucial to guarantee a standard is set up. (MulSoft Inc., 2017).
Integrating IT departments from both organizations will require that innovation pioneers adjust
their assets in three main priorities - Firstly, IT divisions are entrusted with "keeping the lights
on," or guaranteeing the same operations during its incorporation procedure. Secondly, they
should consolidate the IT branches for merging the organizations, with the point of diminishing
expenses or to perceive other collaborations. Finally, they should give IT support for
incorporating all departments while building up the IT infrastructure for the long term business
goals of the organization in its new emphasis. (Dawson, D. & Waller, S., 2010).
From a specialized security angle there is an extensive variety of issues that needs to be secured.
Various access controls needs to be comprehend; the kind of information communications that
are actualized; regardless of whether external elements are associated to the organization
Taken from (Gringolts, V., 2015).
Absence of synchronization in IT framework in both organizations can have challenges with
regular business processes like hiring staff, sales, customer records etc. This challenges will be a
reason to slow all the daily processes. If both organization's IT processes will not integrate,
various errors or network threat can be possible. It will diverts both organizations from
concentrating on their center business capabilities. As both the procured and the obtaining
organization come in with independent financial frameworks, providers, accomplices, it is
crucial to guarantee a standard is set up. (MulSoft Inc., 2017).
Integrating IT departments from both organizations will require that innovation pioneers adjust
their assets in three main priorities - Firstly, IT divisions are entrusted with "keeping the lights
on," or guaranteeing the same operations during its incorporation procedure. Secondly, they
should consolidate the IT branches for merging the organizations, with the point of diminishing
expenses or to perceive other collaborations. Finally, they should give IT support for
incorporating all departments while building up the IT infrastructure for the long term business
goals of the organization in its new emphasis. (Dawson, D. & Waller, S., 2010).
From a specialized security angle there is an extensive variety of issues that needs to be secured.
Various access controls needs to be comprehend; the kind of information communications that
are actualized; regardless of whether external elements are associated to the organization
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

IT Security 7
frameworks and provided; any remote access and its management. Also implementation of
various hardware resources like firewall, encryption, and installation of anti-virus must be
understand by network manager. If two organizations have worked on all requirements, their set
up and the norms for utilizing them, the simpler it will be to see where there are gaps that should
be tended to as these organizations combine. (Hartman, A., 2002).
3.2 Intrusion Detection System (IDS)
The objective of interruption detection system (IDS) is to screen network resources to identify
any type of abnormal behavior and abuse in the entire network. The IDS mainly screens network
traffic for action that falls inside the restricted action in the system. The main function of IDS is
to make the alert action for network administrator for enable them to make restorative move, to
block the unauthorized access for vulnerable ports, to deny the access to particular IP address or
to close down administrations used for the attack purpose. (Ashoor, A., S. & Prof. Gore, S.,
2011).
As we know that, the network architecture of e-commerce business is constantly prone to be
assaulted particularly when managing a network in which data flows on regular basis and
showing vulnerabilities that permit an assailant to enter and authorize illegal activities that
produce abnormalities in the system, subsequently to actualize for investigating network to
detect the interruption. It can also detect any malicious activity in network traffic from Internet.
It can likewise be used to recognize any defect that endeavor to assault PCs in a LAN. The IDS
framework investigates the substance as well as data from the header of the IP and then
distinguish this data and marks of known assaults. If the details are as per the attack, IDS gives
some warning for planning action accordingly. (Ourida, 2012).
frameworks and provided; any remote access and its management. Also implementation of
various hardware resources like firewall, encryption, and installation of anti-virus must be
understand by network manager. If two organizations have worked on all requirements, their set
up and the norms for utilizing them, the simpler it will be to see where there are gaps that should
be tended to as these organizations combine. (Hartman, A., 2002).
3.2 Intrusion Detection System (IDS)
The objective of interruption detection system (IDS) is to screen network resources to identify
any type of abnormal behavior and abuse in the entire network. The IDS mainly screens network
traffic for action that falls inside the restricted action in the system. The main function of IDS is
to make the alert action for network administrator for enable them to make restorative move, to
block the unauthorized access for vulnerable ports, to deny the access to particular IP address or
to close down administrations used for the attack purpose. (Ashoor, A., S. & Prof. Gore, S.,
2011).
As we know that, the network architecture of e-commerce business is constantly prone to be
assaulted particularly when managing a network in which data flows on regular basis and
showing vulnerabilities that permit an assailant to enter and authorize illegal activities that
produce abnormalities in the system, subsequently to actualize for investigating network to
detect the interruption. It can also detect any malicious activity in network traffic from Internet.
It can likewise be used to recognize any defect that endeavor to assault PCs in a LAN. The IDS
framework investigates the substance as well as data from the header of the IP and then
distinguish this data and marks of known assaults. If the details are as per the attack, IDS gives
some warning for planning action accordingly. (Ourida, 2012).
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

IT Security 8
Interruption prevention system (IPS) can be defined as the process though which any type of
intrusion or network risk are detected and in turn overseeing responsive activities on those
distinguished interruptions as well as risks all through the system. The main function of IPS is to
monitor network traffic with any type of malicious activity and which coordinate particular
profiles and will trigger the age of alarms and it can drop, obstruct that movement continuously
go through in the network. (Chakraborty, N., 2013).
3.2.1 Network based IDS - The main function of NIDS (Network based IDS) is to
monitor for a specific system and examines the system as well as application protocol to
distinguish any type of suspicious action. This IDS is deployed at a limit between systems like in
switches, firewalls, virtual private systems and so on. But it is less commonly used as failure
occurs at single point. Also, it is unable to detect any type of DoS attack. It screens the entire
system and deliver it at the limit of the system. However, it isn't appropriate for securing every
hosts inside the system.
3.2.2 Host Based IDS - In Host-based IDS (HIDS) innovation, software is introduced on
each of the system hosts of networking framework in order to monitor any malicious activity in
the networking. Its main function is to to monitor network traffic and any other activity like
security policy, log audit etc. Log analysis, analyzing policy, checking integrity etc are also
performed by HIDS. These IDS are also used to deploy critical hosts like any accessible server,
or any confidential information. So it will be better to implement host based IDS that will
monitor the integration of both cooperate network. (Chakraborty, N., 2013).
Interruption prevention system (IPS) can be defined as the process though which any type of
intrusion or network risk are detected and in turn overseeing responsive activities on those
distinguished interruptions as well as risks all through the system. The main function of IPS is to
monitor network traffic with any type of malicious activity and which coordinate particular
profiles and will trigger the age of alarms and it can drop, obstruct that movement continuously
go through in the network. (Chakraborty, N., 2013).
3.2.1 Network based IDS - The main function of NIDS (Network based IDS) is to
monitor for a specific system and examines the system as well as application protocol to
distinguish any type of suspicious action. This IDS is deployed at a limit between systems like in
switches, firewalls, virtual private systems and so on. But it is less commonly used as failure
occurs at single point. Also, it is unable to detect any type of DoS attack. It screens the entire
system and deliver it at the limit of the system. However, it isn't appropriate for securing every
hosts inside the system.
3.2.2 Host Based IDS - In Host-based IDS (HIDS) innovation, software is introduced on
each of the system hosts of networking framework in order to monitor any malicious activity in
the networking. Its main function is to to monitor network traffic and any other activity like
security policy, log audit etc. Log analysis, analyzing policy, checking integrity etc are also
performed by HIDS. These IDS are also used to deploy critical hosts like any accessible server,
or any confidential information. So it will be better to implement host based IDS that will
monitor the integration of both cooperate network. (Chakraborty, N., 2013).
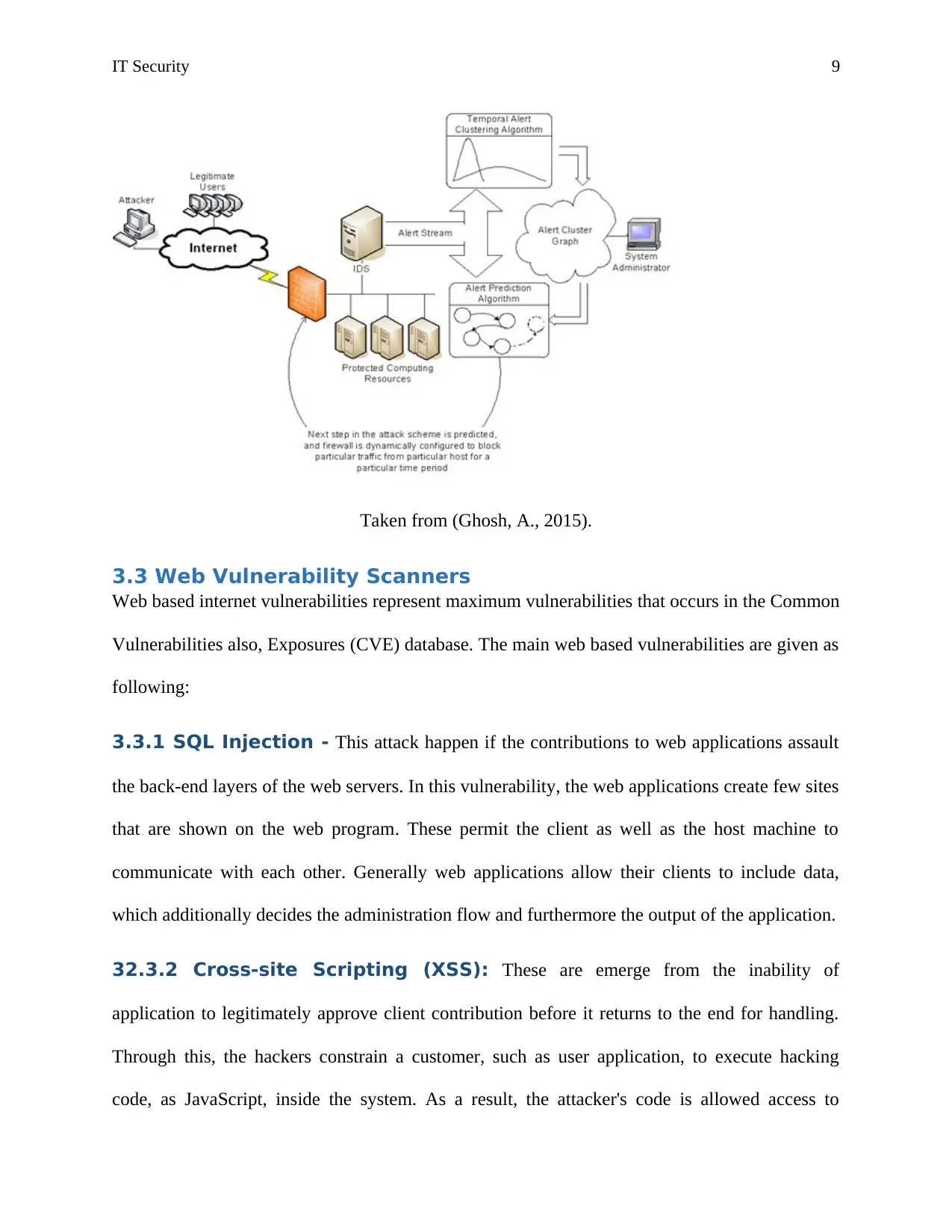
IT Security 9
Taken from (Ghosh, A., 2015).
3.3 Web Vulnerability Scanners
Web based internet vulnerabilities represent maximum vulnerabilities that occurs in the Common
Vulnerabilities also, Exposures (CVE) database. The main web based vulnerabilities are given as
following:
3.3.1 SQL Injection - This attack happen if the contributions to web applications assault
the back-end layers of the web servers. In this vulnerability, the web applications create few sites
that are shown on the web program. These permit the client as well as the host machine to
communicate with each other. Generally web applications allow their clients to include data,
which additionally decides the administration flow and furthermore the output of the application.
32.3.2 Cross-site Scripting (XSS): These are emerge from the inability of
application to legitimately approve client contribution before it returns to the end for handling.
Through this, the hackers constrain a customer, such as user application, to execute hacking
code, as JavaScript, inside the system. As a result, the attacker's code is allowed access to
Taken from (Ghosh, A., 2015).
3.3 Web Vulnerability Scanners
Web based internet vulnerabilities represent maximum vulnerabilities that occurs in the Common
Vulnerabilities also, Exposures (CVE) database. The main web based vulnerabilities are given as
following:
3.3.1 SQL Injection - This attack happen if the contributions to web applications assault
the back-end layers of the web servers. In this vulnerability, the web applications create few sites
that are shown on the web program. These permit the client as well as the host machine to
communicate with each other. Generally web applications allow their clients to include data,
which additionally decides the administration flow and furthermore the output of the application.
32.3.2 Cross-site Scripting (XSS): These are emerge from the inability of
application to legitimately approve client contribution before it returns to the end for handling.
Through this, the hackers constrain a customer, such as user application, to execute hacking
code, as JavaScript, inside the system. As a result, the attacker's code is allowed access to
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
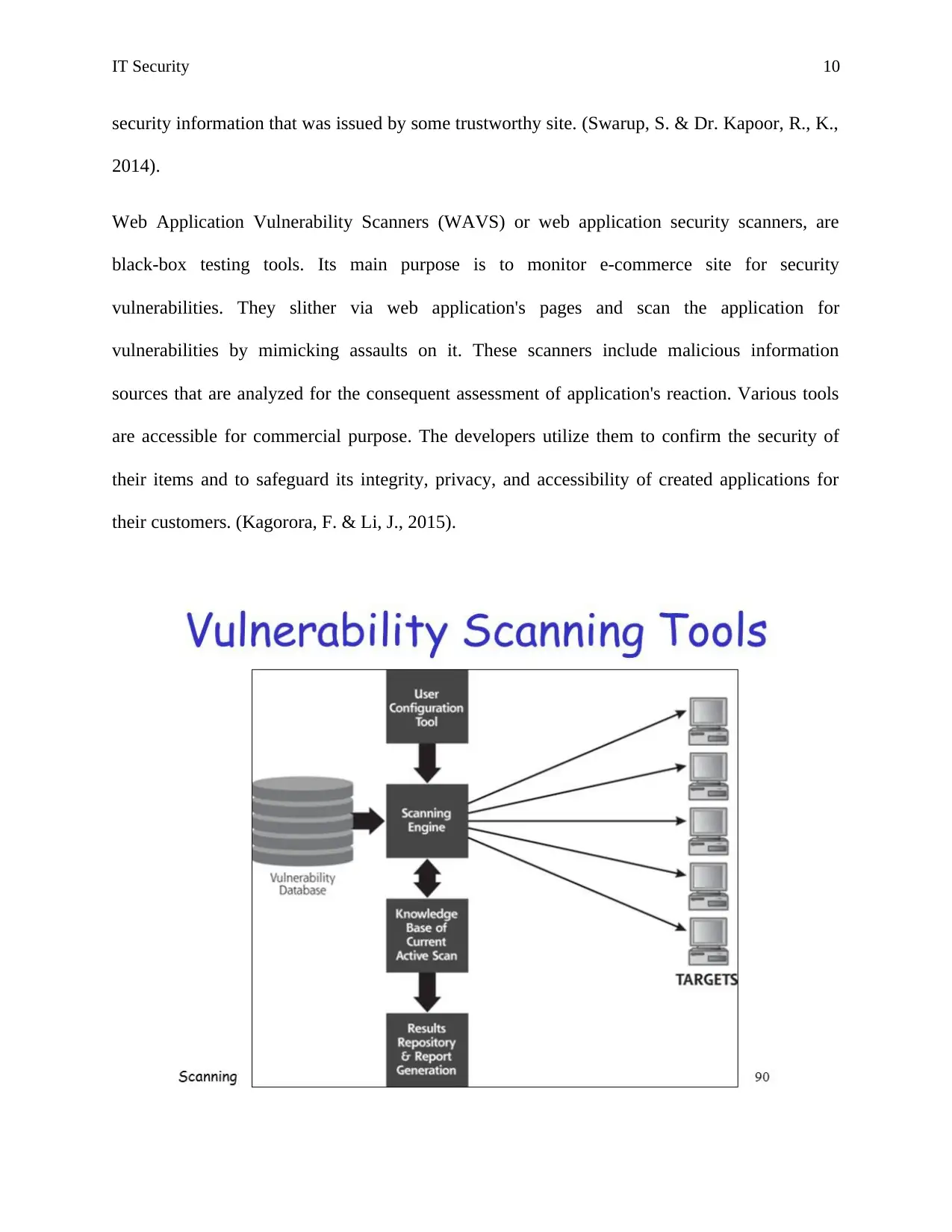
IT Security 10
security information that was issued by some trustworthy site. (Swarup, S. & Dr. Kapoor, R., K.,
2014).
Web Application Vulnerability Scanners (WAVS) or web application security scanners, are
black-box testing tools. Its main purpose is to monitor e-commerce site for security
vulnerabilities. They slither via web application's pages and scan the application for
vulnerabilities by mimicking assaults on it. These scanners include malicious information
sources that are analyzed for the consequent assessment of application's reaction. Various tools
are accessible for commercial purpose. The developers utilize them to confirm the security of
their items and to safeguard its integrity, privacy, and accessibility of created applications for
their customers. (Kagorora, F. & Li, J., 2015).
security information that was issued by some trustworthy site. (Swarup, S. & Dr. Kapoor, R., K.,
2014).
Web Application Vulnerability Scanners (WAVS) or web application security scanners, are
black-box testing tools. Its main purpose is to monitor e-commerce site for security
vulnerabilities. They slither via web application's pages and scan the application for
vulnerabilities by mimicking assaults on it. These scanners include malicious information
sources that are analyzed for the consequent assessment of application's reaction. Various tools
are accessible for commercial purpose. The developers utilize them to confirm the security of
their items and to safeguard its integrity, privacy, and accessibility of created applications for
their customers. (Kagorora, F. & Li, J., 2015).
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

IT Security 11
WAVS by HTTP Method - HTTP web application scanner can check e-commerce site, to
check that each file is accessible from the web and reenact programmer movement so as to
distinguish vulnerable segments. These vulnerability scanner can be utilized to evaluate the code
which makes up a web application, enabling it to recognize potential vulnerabilities which won't
be clear from the web, but rather still exist in the web application, and can still be abused. This
process scan the application for shells from client system for any infused areas and with their
standard names. It is the remarkable component of the framework which will be at customer
machine. It is mainly found in Web applications. XSS empowers assailants to infuse customer
side content into Web pages viewed by different clients. This is the best method for detection of
any vulnerability in the network. (Patil & Prof. Gosavi, 2015).
JAVA Tool - The tool is produced in JAVA and can be possible for any environment. The
central function of the tool is:
It checks each access one-by-one to inspect for any powerless SQL vulnerability. It shows all
such SQL proclamations (dangers) in client well-disposed interface with the file name, and with
the purpose behind vulnerability.
It furthermore exhorts the users that concern what to attempt and improve the situation for each
risk. This tool looks through each file to gather all the factors and keep in an ArrayList (say
varList). The variable method is predicated on normal articulation composed on a design record.
(Swarup, S. & Dr. Kapoor, R., K., 2014).
3.3 Network Firewall Devices
A firewall can be defined as hardware or software system that are planned to allow or deny the
transmission of network traffic in light of set of security tenets as well as directions to authorize
control in between two systems to secure internal or external network system. The main function
WAVS by HTTP Method - HTTP web application scanner can check e-commerce site, to
check that each file is accessible from the web and reenact programmer movement so as to
distinguish vulnerable segments. These vulnerability scanner can be utilized to evaluate the code
which makes up a web application, enabling it to recognize potential vulnerabilities which won't
be clear from the web, but rather still exist in the web application, and can still be abused. This
process scan the application for shells from client system for any infused areas and with their
standard names. It is the remarkable component of the framework which will be at customer
machine. It is mainly found in Web applications. XSS empowers assailants to infuse customer
side content into Web pages viewed by different clients. This is the best method for detection of
any vulnerability in the network. (Patil & Prof. Gosavi, 2015).
JAVA Tool - The tool is produced in JAVA and can be possible for any environment. The
central function of the tool is:
It checks each access one-by-one to inspect for any powerless SQL vulnerability. It shows all
such SQL proclamations (dangers) in client well-disposed interface with the file name, and with
the purpose behind vulnerability.
It furthermore exhorts the users that concern what to attempt and improve the situation for each
risk. This tool looks through each file to gather all the factors and keep in an ArrayList (say
varList). The variable method is predicated on normal articulation composed on a design record.
(Swarup, S. & Dr. Kapoor, R., K., 2014).
3.3 Network Firewall Devices
A firewall can be defined as hardware or software system that are planned to allow or deny the
transmission of network traffic in light of set of security tenets as well as directions to authorize
control in between two systems to secure internal or external network system. The main function
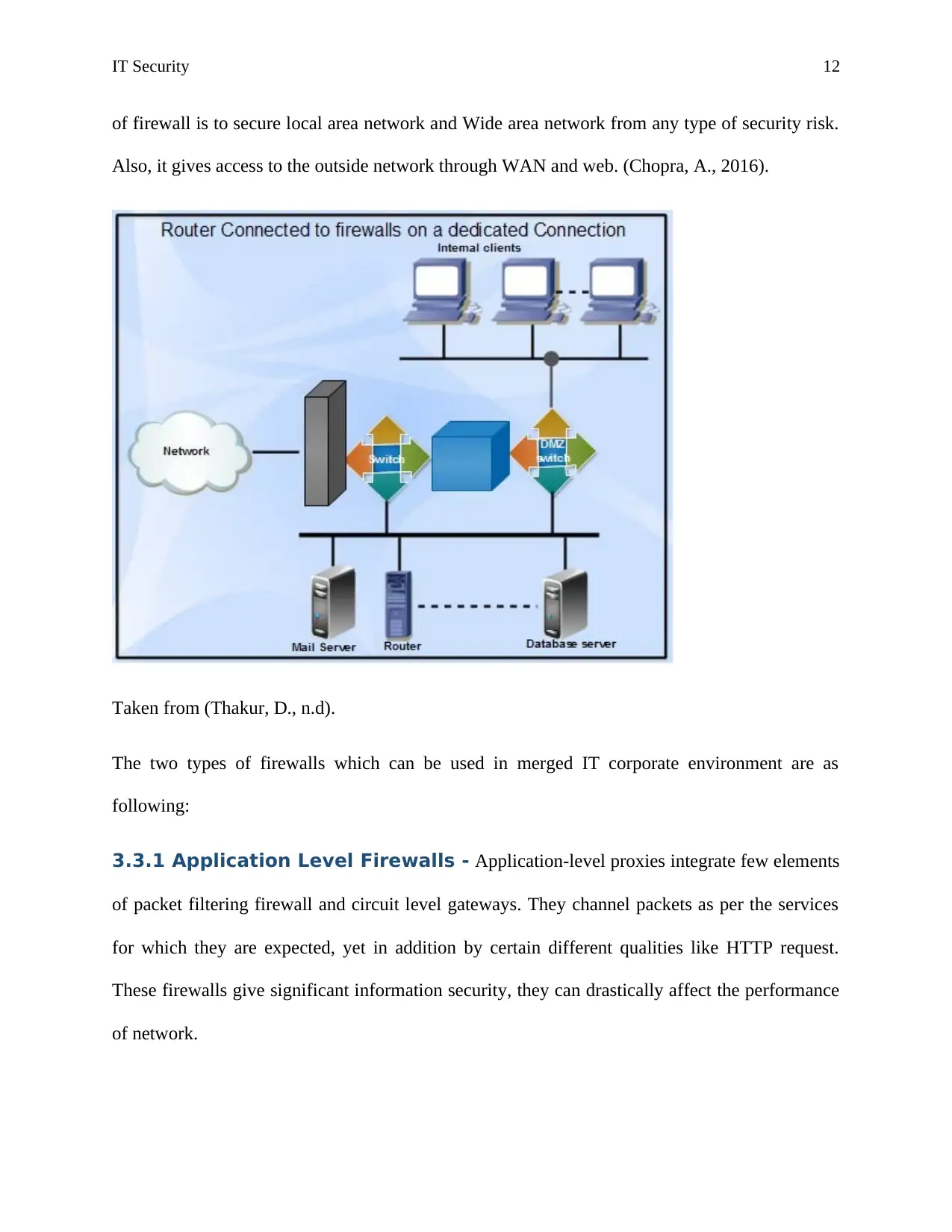
IT Security 12
of firewall is to secure local area network and Wide area network from any type of security risk.
Also, it gives access to the outside network through WAN and web. (Chopra, A., 2016).
Taken from (Thakur, D., n.d).
The two types of firewalls which can be used in merged IT corporate environment are as
following:
3.3.1 Application Level Firewalls - Application-level proxies integrate few elements
of packet filtering firewall and circuit level gateways. They channel packets as per the services
for which they are expected, yet in addition by certain different qualities like HTTP request.
These firewalls give significant information security, they can drastically affect the performance
of network.
of firewall is to secure local area network and Wide area network from any type of security risk.
Also, it gives access to the outside network through WAN and web. (Chopra, A., 2016).
Taken from (Thakur, D., n.d).
The two types of firewalls which can be used in merged IT corporate environment are as
following:
3.3.1 Application Level Firewalls - Application-level proxies integrate few elements
of packet filtering firewall and circuit level gateways. They channel packets as per the services
for which they are expected, yet in addition by certain different qualities like HTTP request.
These firewalls give significant information security, they can drastically affect the performance
of network.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
1 out of 20
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.





