IT Security: A Comprehensive Guide to Protecting Your Organization
VerifiedAdded on 2024/05/31
|31
|8229
|330
AI Summary
This comprehensive report delves into the critical aspects of IT security, exploring various security risks, evaluating organizational security procedures, and analyzing physical security issues. It examines data protection processes and regulations, including the Data Protection Act 1998 and the Computer Misuse Act 1990, and discusses the importance of ISO 31000 standards. The report also designs and implements a security policy for an organization, evaluates the suitability of tools used in organizational policy, and discusses human resource issues to be considered when carrying out security audits. This report provides valuable insights and practical recommendations for organizations seeking to enhance their IT security posture.
Contribute Materials
Your contribution can guide someone’s learning journey. Share your
documents today.

IT SECURITY
Secure Best Marks with AI Grader
Need help grading? Try our AI Grader for instant feedback on your assignments.

TABLE OF CONTENTS
Introduction..................................................................................................................................................1
Task 1...........................................................................................................................................................2
P1.1 Identify and evaluate types of security risks to organisations.........................................................2
P1.2 Evaluate organisational security procedures...................................................................................4
Task 2...........................................................................................................................................................7
P 2.1 Discuss risk assessment procedure.................................................................................................7
P 2.2 Evaluate data protection processes and regulations as applicable to an organisation..................10
P 2.3 Analyse physical security issues for an organisation...................................................................13
Task 3.........................................................................................................................................................17
P3.1 Design and implement a security policy for an organisation........................................................17
P3.2 Evaluate the suitability of the tools used in an organisational policy............................................20
P 3.3 Discuss the human resource issues that have to be considered when carrying out security audits
...............................................................................................................................................................23
Conclusion.................................................................................................................................................24
References..................................................................................................................................................25
Introduction..................................................................................................................................................1
Task 1...........................................................................................................................................................2
P1.1 Identify and evaluate types of security risks to organisations.........................................................2
P1.2 Evaluate organisational security procedures...................................................................................4
Task 2...........................................................................................................................................................7
P 2.1 Discuss risk assessment procedure.................................................................................................7
P 2.2 Evaluate data protection processes and regulations as applicable to an organisation..................10
P 2.3 Analyse physical security issues for an organisation...................................................................13
Task 3.........................................................................................................................................................17
P3.1 Design and implement a security policy for an organisation........................................................17
P3.2 Evaluate the suitability of the tools used in an organisational policy............................................20
P 3.3 Discuss the human resource issues that have to be considered when carrying out security audits
...............................................................................................................................................................23
Conclusion.................................................................................................................................................24
References..................................................................................................................................................25

LIST OF FIGURES
Figure 1: Risk assessment procedure...........................................................................................................9
Figure 2: ISO 31000 standard....................................................................................................................12
Figure 3: Physical security.........................................................................................................................13
Figure 4: Physical security on the doors....................................................................................................16
Figure 5: IT system monitoring tool by solarwinds...................................................................................20
Figure 6: PRTG network monitoring tool..................................................................................................21
Figure 7: NetFort tool................................................................................................................................22
Figure 1: Risk assessment procedure...........................................................................................................9
Figure 2: ISO 31000 standard....................................................................................................................12
Figure 3: Physical security.........................................................................................................................13
Figure 4: Physical security on the doors....................................................................................................16
Figure 5: IT system monitoring tool by solarwinds...................................................................................20
Figure 6: PRTG network monitoring tool..................................................................................................21
Figure 7: NetFort tool................................................................................................................................22

Introduction
Information technology enables the organization to process the data in faster and reliable manner but it
also has threats from the environment which can influence the data security and asset functioning.
Today, information systems are the most critical and expensive sources for the organization those work
as backbone for many business operations. The report will discuss different types of the security risks
and security procedure of the organization to manage the risks. Hilton Hotel, a leading hotel chain is
considered as the case study for the report so that appropriate risk assessment procedure and data
protection process and regulations can be discussed. The report will focus on the physical security issues
of the IT systems in the organization and recommend the practices to resolve the issues. Later, report
will design and implement security policy, evaluate the suitability of the tool to monitor the user
activities and network. Also human issues to be considered during security audit will be discussed for
the organization.
1
Information technology enables the organization to process the data in faster and reliable manner but it
also has threats from the environment which can influence the data security and asset functioning.
Today, information systems are the most critical and expensive sources for the organization those work
as backbone for many business operations. The report will discuss different types of the security risks
and security procedure of the organization to manage the risks. Hilton Hotel, a leading hotel chain is
considered as the case study for the report so that appropriate risk assessment procedure and data
protection process and regulations can be discussed. The report will focus on the physical security issues
of the IT systems in the organization and recommend the practices to resolve the issues. Later, report
will design and implement security policy, evaluate the suitability of the tool to monitor the user
activities and network. Also human issues to be considered during security audit will be discussed for
the organization.
1
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

Task 1
P1.1 Identify and evaluate types of security risks to organisations
Increasing use of the information technology in the business has provided the strength to manage the
data more effectively but also opened the door of insecurity with poor implementation and configuration
of the systems. At present, security risks to the organizations are impacting the business to achieve the
reliability, data confidentiality and performance along with security. The organization is facing security
risks on the loss of access to the devices, poor configuration leading unauthorized access and
modification to the system or data sources, theft of the information and damage to the assets for
continuance of operations. The organization can face the following types of the security risks:
Intellectual property theft and business espionage
Attackers are establishing root in the organizational network or information systems to monitor the
network and fetch the data to gain business espionage. For example, patents, confidential data, financial
records, ideas for new products and strategic growth, business plans or military secrets can be theft from
the organization. Access or theft of such confidential details of the organization can deliver the
profitability to the attacker. In competitive environment, attackers trying to steal the information for the
longer time till they are identified and continue to monitor the business for profitable intellectual
property (Roger, 2017).
Malware mercenaries
It is the program intentionally created to damage the computing resources or impact the user activities
on the system. However, the traditional system to create and impact the single user has been changed in
the multi user environment where malware is injected on the customer or clients computers as an
innocent program. It follows the mother-ship where all the malware programs are connected to a single
server and wait for the instructions to initialize the damage or malfunctioning (Michael, 2010). The
organizations infected with the malware program have low performance, low security on the
confidential data and reduced control on the functions within the network or system. The goal of the
malware mercenaries is the exploit the multiple computers through a single server at a time for the
particular goal or objectives.
2
P1.1 Identify and evaluate types of security risks to organisations
Increasing use of the information technology in the business has provided the strength to manage the
data more effectively but also opened the door of insecurity with poor implementation and configuration
of the systems. At present, security risks to the organizations are impacting the business to achieve the
reliability, data confidentiality and performance along with security. The organization is facing security
risks on the loss of access to the devices, poor configuration leading unauthorized access and
modification to the system or data sources, theft of the information and damage to the assets for
continuance of operations. The organization can face the following types of the security risks:
Intellectual property theft and business espionage
Attackers are establishing root in the organizational network or information systems to monitor the
network and fetch the data to gain business espionage. For example, patents, confidential data, financial
records, ideas for new products and strategic growth, business plans or military secrets can be theft from
the organization. Access or theft of such confidential details of the organization can deliver the
profitability to the attacker. In competitive environment, attackers trying to steal the information for the
longer time till they are identified and continue to monitor the business for profitable intellectual
property (Roger, 2017).
Malware mercenaries
It is the program intentionally created to damage the computing resources or impact the user activities
on the system. However, the traditional system to create and impact the single user has been changed in
the multi user environment where malware is injected on the customer or clients computers as an
innocent program. It follows the mother-ship where all the malware programs are connected to a single
server and wait for the instructions to initialize the damage or malfunctioning (Michael, 2010). The
organizations infected with the malware program have low performance, low security on the
confidential data and reduced control on the functions within the network or system. The goal of the
malware mercenaries is the exploit the multiple computers through a single server at a time for the
particular goal or objectives.
2

The increasingly compromised web
The poor configuration of the web server can impact the business for the security risks. Attackers are
targeting web servers to exploit the risks to the connected client computers. Normally, attackers in the
network system use the vulnerabilities, weaknesses and poor configuration on the server to bypass the
security mechanism which helped them to control the web server. With bypass they can change the
authentication details or code the malicious scripts for the clients. Poor password, SQL injections,
vulnerable software, cross-site scripting vulnerabilities and insecure permissions are the some of the
vulnerabilities on web server (Rapid7.com, 2018). Such attacks can impact the organization for the poor
connectivity, performance and reduced security to the users whereas confidentiality and privacy of the
user data over the website might be compromised.
Hacking activities
IT systems have high threat of the activities from the user or attacker to become administrator for
complete control. Hacking activities can impact the system for the user management, file permissions,
access to the resources and services for the operations. In a network system, the organization might loss
the access to the resources providing easy communication and security in the network. Also, hacking
has main goal to influence the users, generate the profitability through device access, data security or
demand of the capital for access and to impact the reputation of the organization (Conklin et al, 2015).
Infrastructure
The organizational infrastructure might become the prompter for the security risks as the poor
classification of the computing devices can allow them to access regardless of their role and
responsibilities in the organization. Also poor infrastructure can motivate the main-in-middle attacks
through the direct connections to the computing devices. Infrastructure for the wireless connectivity and
open access to the network components can reduce the security on the data and assets. It can generate
the loss of financial and physical assets on the organization.
All-in-one malware
The code designed to infect the computing devices in the network is called malware. However, a
malware can take the form of virus, Trojan horse, worms and malware. Virus can infect the system code
3
The poor configuration of the web server can impact the business for the security risks. Attackers are
targeting web servers to exploit the risks to the connected client computers. Normally, attackers in the
network system use the vulnerabilities, weaknesses and poor configuration on the server to bypass the
security mechanism which helped them to control the web server. With bypass they can change the
authentication details or code the malicious scripts for the clients. Poor password, SQL injections,
vulnerable software, cross-site scripting vulnerabilities and insecure permissions are the some of the
vulnerabilities on web server (Rapid7.com, 2018). Such attacks can impact the organization for the poor
connectivity, performance and reduced security to the users whereas confidentiality and privacy of the
user data over the website might be compromised.
Hacking activities
IT systems have high threat of the activities from the user or attacker to become administrator for
complete control. Hacking activities can impact the system for the user management, file permissions,
access to the resources and services for the operations. In a network system, the organization might loss
the access to the resources providing easy communication and security in the network. Also, hacking
has main goal to influence the users, generate the profitability through device access, data security or
demand of the capital for access and to impact the reputation of the organization (Conklin et al, 2015).
Infrastructure
The organizational infrastructure might become the prompter for the security risks as the poor
classification of the computing devices can allow them to access regardless of their role and
responsibilities in the organization. Also poor infrastructure can motivate the main-in-middle attacks
through the direct connections to the computing devices. Infrastructure for the wireless connectivity and
open access to the network components can reduce the security on the data and assets. It can generate
the loss of financial and physical assets on the organization.
All-in-one malware
The code designed to infect the computing devices in the network is called malware. However, a
malware can take the form of virus, Trojan horse, worms and malware. Virus can infect the system code
3

for the malfunctioning and damage the data for the usability (Carroll, 2014). Also, Trojan horse is a
program which is embedded into the legitimate program code so that it installs automatically and
performs background operations to impact the computer security. Worms are also programs like virus
but they consume storage space and perform background operations to breach the security. Worms
never affect tor damage the assets in the system.
P1.2 Evaluate organisational security procedures
The organizational security procedure can be defined as the way to control the security among the users,
systems and network technologies so that business operation continuance can be assured. The
organization normally follows the four major stages during the establishment of the security procedures:
focus on the business continuance, back up and restoration of data, audits on security and testing
procedures after implementation. However the organizational security procedures can be evaluated in
following sections:
Administrative procedures
This section has focus on the security of the systems through the administrative operations. It constrains
the users for the use and ownership of the system and data. The administrative procedure of the
organization is effective to manage the user access to the network resources and utilization of the
services for the business. The organization also has focused on the security and proprietary information
being collected and processed in the administrative operations of the organization. It controls
unacceptable use of the systems (Information security procedures, 2018). Therefore, it works as
guideline for the users to make use of the resources and information for the business purpose only.
However, it has enforced the monitoring practices and resulting outcomes if procedure is not followed
by the users.
Technical procedures
The security procedure for the technical set up and configuration has involvement of the procedures for
the password management and rules, anti-virus process, server security process, security on router and
wireless connections, remote access, encryption, web access and database storing confidential
information. The technical procedure has focus on the security of the data and assets through the
technical set up of the communication mechanism, network resources and user configuration along with
4
program which is embedded into the legitimate program code so that it installs automatically and
performs background operations to impact the computer security. Worms are also programs like virus
but they consume storage space and perform background operations to breach the security. Worms
never affect tor damage the assets in the system.
P1.2 Evaluate organisational security procedures
The organizational security procedure can be defined as the way to control the security among the users,
systems and network technologies so that business operation continuance can be assured. The
organization normally follows the four major stages during the establishment of the security procedures:
focus on the business continuance, back up and restoration of data, audits on security and testing
procedures after implementation. However the organizational security procedures can be evaluated in
following sections:
Administrative procedures
This section has focus on the security of the systems through the administrative operations. It constrains
the users for the use and ownership of the system and data. The administrative procedure of the
organization is effective to manage the user access to the network resources and utilization of the
services for the business. The organization also has focused on the security and proprietary information
being collected and processed in the administrative operations of the organization. It controls
unacceptable use of the systems (Information security procedures, 2018). Therefore, it works as
guideline for the users to make use of the resources and information for the business purpose only.
However, it has enforced the monitoring practices and resulting outcomes if procedure is not followed
by the users.
Technical procedures
The security procedure for the technical set up and configuration has involvement of the procedures for
the password management and rules, anti-virus process, server security process, security on router and
wireless connections, remote access, encryption, web access and database storing confidential
information. The technical procedure has focus on the security of the data and assets through the
technical set up of the communication mechanism, network resources and user configuration along with
4
Secure Best Marks with AI Grader
Need help grading? Try our AI Grader for instant feedback on your assignments.

management of the information sensitivity for sharing and processing (Ray, 2018). However, it provides
strong guidelines for the password and user detail management in database systems, ownership and
responsibility of the server security, authentication and encryption during the communication and access
to the website with high security risks.
Physical security procedure
This procedure has focus on the security of the system and network assets. It has focus on the security of
the server machines, client computing devices including computers, printers and fax machines, storage
devices and network components like switches, router and firewall. The physical security procedure of
the organization has used to limit the user access to the assets to prevent the unwanted use of the system.
It provides server room security through the guidance and recommendations. It ensures the data storage
with high security and prevents the destruction of the storage of the sensitive information. It also
enforces the legal compliance of the regulations for the data protection.
Impact of security breach to an organization
The security procedure needs to be executed effectively in the organization to prevent the unauthorized
access or data theft. Security breaches in the organization can impact the organization for the poor
availability of the data so that users cannot get the required information on time or unable to the fetch
the data from the server. Operational activities cannot get the data for the business continuance and in
this manner; the organization has poor performance and productivity. Security breaches also can theft
the data from the system so that authenticated users cannot avail the data. Loss of such confidential
information on business plan or product ideas can impact the business for financial loss or high risks on
the sustainability (Zafar et al, 2012). The attacker also breaches into the security to monitor the data
over a long time with the help of the organization resources. Such activities can transmit the business
data to the remote location and the organizational efforts for the ideas or concept through data can be
used by attacker to make profitability.
Security breaches in the competitive environment also has goal to prevent the organization to achieve
the specific benefits. For example, competitor in market can promote the attacker to damage the
resources in the network of the other organization so that that organization has reduced performance,
5
strong guidelines for the password and user detail management in database systems, ownership and
responsibility of the server security, authentication and encryption during the communication and access
to the website with high security risks.
Physical security procedure
This procedure has focus on the security of the system and network assets. It has focus on the security of
the server machines, client computing devices including computers, printers and fax machines, storage
devices and network components like switches, router and firewall. The physical security procedure of
the organization has used to limit the user access to the assets to prevent the unwanted use of the system.
It provides server room security through the guidance and recommendations. It ensures the data storage
with high security and prevents the destruction of the storage of the sensitive information. It also
enforces the legal compliance of the regulations for the data protection.
Impact of security breach to an organization
The security procedure needs to be executed effectively in the organization to prevent the unauthorized
access or data theft. Security breaches in the organization can impact the organization for the poor
availability of the data so that users cannot get the required information on time or unable to the fetch
the data from the server. Operational activities cannot get the data for the business continuance and in
this manner; the organization has poor performance and productivity. Security breaches also can theft
the data from the system so that authenticated users cannot avail the data. Loss of such confidential
information on business plan or product ideas can impact the business for financial loss or high risks on
the sustainability (Zafar et al, 2012). The attacker also breaches into the security to monitor the data
over a long time with the help of the organization resources. Such activities can transmit the business
data to the remote location and the organizational efforts for the ideas or concept through data can be
used by attacker to make profitability.
Security breaches in the competitive environment also has goal to prevent the organization to achieve
the specific benefits. For example, competitor in market can promote the attacker to damage the
resources in the network of the other organization so that that organization has reduced performance,
5

poor access to the machines or damage of the assets for financial loss. In this manner, the organization
might not be able to access the specific competitive advantages.
6
might not be able to access the specific competitive advantages.
6

Task 2
P 2.1 Discuss risk assessment procedure
Risk assessment is the way to determine the qualitative and quantitative estimated risk which is
related to the situations and threat recognition. Every project has some type of risk which is
required to be assessed and identified by the organization and their team so that they can
overcome and reduce the chances of risk in the project. Risk assessment procedure is the
procedure that can be used by the organizations to assess their associated risk in the project and
the steps or stages to overcome or control the risk. Risk assessment procedure covers some of the
stages which is implemented to identify the associated risk in the project. The stages of risk
assessment procedure help the organization to avoid the risk which may be related to the health
and safety of the employee who are working in the project (Dottori et al, 2015).
Stages which are covered in the risk assessment procedure are- risk identification under that
organization need to identify the system which is responsible for the risk happening or the
system which generate the main risk. With the help of the risk identification it becomes easy for
the organization to identify the primary source of the generated risk in the project or under any
activity. On the other side, harms and hazards risk are also identified with the help of the well
structured risk assessment plan. All the stages and steps involved under this procedure is the
main and key part of the risk analysis. Under the risk evaluation procedure, organizations
required to make the list of all the risk but in a systematic way because this will help the
organization to identify its impact, solutions and primary source (Li, 2014). With this they can
determine the level of the associated risk.
Following are some of the stages which are related to the risk assessment procedure which is
required to be followed and considered by the organization:
Step 1: Identify the harm and hazards risk
It is the responsibility of the employer to assess the risk which is related to the health and safety
of the workers who are working in that environment. Employer need to check the possible
mental, physical, biological and chemical harms or hazards. This type of identification will help
P 2.1 Discuss risk assessment procedure
Risk assessment is the way to determine the qualitative and quantitative estimated risk which is
related to the situations and threat recognition. Every project has some type of risk which is
required to be assessed and identified by the organization and their team so that they can
overcome and reduce the chances of risk in the project. Risk assessment procedure is the
procedure that can be used by the organizations to assess their associated risk in the project and
the steps or stages to overcome or control the risk. Risk assessment procedure covers some of the
stages which is implemented to identify the associated risk in the project. The stages of risk
assessment procedure help the organization to avoid the risk which may be related to the health
and safety of the employee who are working in the project (Dottori et al, 2015).
Stages which are covered in the risk assessment procedure are- risk identification under that
organization need to identify the system which is responsible for the risk happening or the
system which generate the main risk. With the help of the risk identification it becomes easy for
the organization to identify the primary source of the generated risk in the project or under any
activity. On the other side, harms and hazards risk are also identified with the help of the well
structured risk assessment plan. All the stages and steps involved under this procedure is the
main and key part of the risk analysis. Under the risk evaluation procedure, organizations
required to make the list of all the risk but in a systematic way because this will help the
organization to identify its impact, solutions and primary source (Li, 2014). With this they can
determine the level of the associated risk.
Following are some of the stages which are related to the risk assessment procedure which is
required to be followed and considered by the organization:
Step 1: Identify the harm and hazards risk
It is the responsibility of the employer to assess the risk which is related to the health and safety
of the workers who are working in that environment. Employer need to check the possible
mental, physical, biological and chemical harms or hazards. This type of identification will help
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

the employer to safeguard their workers from the harmful activities. The hazards risks are mainly
classified under following terms:
Chemical risk: cleaning fluids, asbestos or aerosols
Physical risk: slips and trip, awkward postures, dust, lifting, machinery or computer
equipment (William et al, 2016).
Biological risk: hepatitis, infectious diseases, tuberculosis etc faced by the healthcare
employees, healthcare professionals and other staff members.
Mental risk: long hours, bullying, excess workload or working with the high
expectations of the customers. These types of risk are also termed as the psychosocial'
hazards.
Step 2: Identify the effecting person and how
After identifying the hazards and harm risk, it is essential to analyze the person who may be
harmed and in which manner. It is responsibility of the employer to assess the risk which is faced
by the staffs, visitors, agency, members or clients of the organization within their workplace.
This will include the regular review of the situations of the business operations and locations of
the workplace (Knechel and Salterio, 2016). For example: In the organizations, who are dealing
in the supermarket, identify the hazards activities that are related to the lifting loads or trips and
slips from obstacles and spillages in the storerooms.
Step 3: Identified risk must be assess and them take actions
After identifying all type of risk and nature of the risk, it is essential for the organization and
employer to assess the risk and then take an appropriate action plan to reduce or overcome that
risk in the organization. With the help of this step, the employer can easily identify the level of
the risk and the way to reduce that risk for their employee benefits. Action plan for assessment of
the risk is related to the high, medium and low.
Step 4: Make the findings records
The findings regarding the risk must need to be maintained and recorded by the employer or any
other authorized person (Suter II, 2016). The findings of the risk assessment must be record and
maintained in the written so that in future it be considered by the employer or organization. This
classified under following terms:
Chemical risk: cleaning fluids, asbestos or aerosols
Physical risk: slips and trip, awkward postures, dust, lifting, machinery or computer
equipment (William et al, 2016).
Biological risk: hepatitis, infectious diseases, tuberculosis etc faced by the healthcare
employees, healthcare professionals and other staff members.
Mental risk: long hours, bullying, excess workload or working with the high
expectations of the customers. These types of risk are also termed as the psychosocial'
hazards.
Step 2: Identify the effecting person and how
After identifying the hazards and harm risk, it is essential to analyze the person who may be
harmed and in which manner. It is responsibility of the employer to assess the risk which is faced
by the staffs, visitors, agency, members or clients of the organization within their workplace.
This will include the regular review of the situations of the business operations and locations of
the workplace (Knechel and Salterio, 2016). For example: In the organizations, who are dealing
in the supermarket, identify the hazards activities that are related to the lifting loads or trips and
slips from obstacles and spillages in the storerooms.
Step 3: Identified risk must be assess and them take actions
After identifying all type of risk and nature of the risk, it is essential for the organization and
employer to assess the risk and then take an appropriate action plan to reduce or overcome that
risk in the organization. With the help of this step, the employer can easily identify the level of
the risk and the way to reduce that risk for their employee benefits. Action plan for assessment of
the risk is related to the high, medium and low.
Step 4: Make the findings records
The findings regarding the risk must need to be maintained and recorded by the employer or any
other authorized person (Suter II, 2016). The findings of the risk assessment must be record and
maintained in the written so that in future it be considered by the employer or organization. This

type of record of the findings must include the details of the hazards and harm risk which is
identified in the risk assessment, planned actions and eliminated risk.
Step 5: At last review the risk assessment
After completing all the above mentioned steps, the last step is about review of the assessed risk
by the employer or organization (Cherdantseva et al, 2016). The review of the risk assessment
includes the some of the important points. It is essential to ensure about the working practices
and its implementation.
Figure 1: Risk assessment procedure
(Source: Integrated annual report, 2012)
identified in the risk assessment, planned actions and eliminated risk.
Step 5: At last review the risk assessment
After completing all the above mentioned steps, the last step is about review of the assessed risk
by the employer or organization (Cherdantseva et al, 2016). The review of the risk assessment
includes the some of the important points. It is essential to ensure about the working practices
and its implementation.
Figure 1: Risk assessment procedure
(Source: Integrated annual report, 2012)

P 2.2 Evaluate data protection processes and regulations as applicable to an organisation
Data protection Act 1998
Data protection Act 1998 is the UK Act of the Parliament which is mainly designed to protect
the confidential and personal data or information which are stored in the computer systems or
within the organized. This data protection Act 1998 follows the EU (European Union) Data
Protection Directive 1995 protection, movement and processing of data. Every individual have
the legal rights for controlling the information about their own. Most of the Acts are not applied
for the domestic use such as- keeping the personal address book (Gan et al, 2018).
Holding of the personal data for any purpose is legally applied and obliged for complying with
the Data Protect Act. Within the data protection act there are mainly eight principles are
mentioned which are related to ensuring the information which is processed lawfully. With the
help of the Data Protection Act, it becomes easy for the organization to communicate the
importance and circumstances of the Act violation so that every worker should follow this Act
and keeps the confidentiality maintained (Tan, 2017). In the current time, protection of the
stakeholders data becoming the major and one of the important responsibility of the organization
for which they applied this Data Protection Act within their workplace.
The Computer Misuse Act 1990
The computer misuse Act 1990 is also one of the important Acts in the UK of the Parliament
which is introduced partly towards the response for taking the decision in the R v Gold &
Schifreen 1998. This bill is critics by many people and complained that this was introduced
hastily and also poorly. In the starting time the intention behind this Act is difficult to prove.
After some time, the bill is supported by the government and came in the force from 1990.
Under this Act, the unauthorized user if access any computers and its confidential information
then the person is punished by 12 months of imprisonment. With the help of this Act it becomes
easy for the organizations to eliminate the unwanted access of the information which are stored
in the computer system (Wall, 2015). This Act also reduces the cybercrimes in which include the
computers and network that protects the cyber crime and the data theft.
Data protection Act 1998
Data protection Act 1998 is the UK Act of the Parliament which is mainly designed to protect
the confidential and personal data or information which are stored in the computer systems or
within the organized. This data protection Act 1998 follows the EU (European Union) Data
Protection Directive 1995 protection, movement and processing of data. Every individual have
the legal rights for controlling the information about their own. Most of the Acts are not applied
for the domestic use such as- keeping the personal address book (Gan et al, 2018).
Holding of the personal data for any purpose is legally applied and obliged for complying with
the Data Protect Act. Within the data protection act there are mainly eight principles are
mentioned which are related to ensuring the information which is processed lawfully. With the
help of the Data Protection Act, it becomes easy for the organization to communicate the
importance and circumstances of the Act violation so that every worker should follow this Act
and keeps the confidentiality maintained (Tan, 2017). In the current time, protection of the
stakeholders data becoming the major and one of the important responsibility of the organization
for which they applied this Data Protection Act within their workplace.
The Computer Misuse Act 1990
The computer misuse Act 1990 is also one of the important Acts in the UK of the Parliament
which is introduced partly towards the response for taking the decision in the R v Gold &
Schifreen 1998. This bill is critics by many people and complained that this was introduced
hastily and also poorly. In the starting time the intention behind this Act is difficult to prove.
After some time, the bill is supported by the government and came in the force from 1990.
Under this Act, the unauthorized user if access any computers and its confidential information
then the person is punished by 12 months of imprisonment. With the help of this Act it becomes
easy for the organizations to eliminate the unwanted access of the information which are stored
in the computer system (Wall, 2015). This Act also reduces the cybercrimes in which include the
computers and network that protects the cyber crime and the data theft.
Secure Best Marks with AI Grader
Need help grading? Try our AI Grader for instant feedback on your assignments.

Cybercrimes are defined as the offences which are committed by the individuals or any
individual groups as they are having motive to do crime and also have the criminal personality.
This criminal intention of the person can harm the reputation and goodwill of the victim and this
will also cause the mental and physical harm to the person. The motive behind this type of crime
done by the individual is to harm the confidentiality of any person and to harm the reputation of
the person. Computer misuse Act enforces all the stakeholders of the organization for using the
systems just to define the purpose (El Asam and Samara, 2016). As per the Act, the employees
of the organization cannot use the systems, operations and services to carry the personal
objectives. This misuse of the data storage and resources which can be prevented processes and
policies in that user action and their decisions can be monitored with the utilization of the
resources.
ISO 31000 standard
ISO 31000 Standard will be provided as the important guidelines so that all the process for
managing the associated risk. The organizations will implement all the standards as the activities
framework which can manage the project or operations risk for the employees. This type of
standards also protects the activities set for controlling the risk and also to reduce the risk
impacts. This standard provides the principles for handling the risk which are related to the
sector information technology (Ibáñez et al, 2016). ISO 31000 standards mainly focus on the
implementation of the security system with the help of the business risk management.
This standard has the scope for all the organizations to the design, implementation and
maintenance of the risk with the capability, process and functions for achieving the strategic
stability and security. This standard also involves the stakeholders of the business for supporting
the organizational operations in effective manner (de Oliveira et al, 2017). The main objective of
this standard is to formulate the risk and then improve its security with the help of the
sustainable practices.
individual groups as they are having motive to do crime and also have the criminal personality.
This criminal intention of the person can harm the reputation and goodwill of the victim and this
will also cause the mental and physical harm to the person. The motive behind this type of crime
done by the individual is to harm the confidentiality of any person and to harm the reputation of
the person. Computer misuse Act enforces all the stakeholders of the organization for using the
systems just to define the purpose (El Asam and Samara, 2016). As per the Act, the employees
of the organization cannot use the systems, operations and services to carry the personal
objectives. This misuse of the data storage and resources which can be prevented processes and
policies in that user action and their decisions can be monitored with the utilization of the
resources.
ISO 31000 standard
ISO 31000 Standard will be provided as the important guidelines so that all the process for
managing the associated risk. The organizations will implement all the standards as the activities
framework which can manage the project or operations risk for the employees. This type of
standards also protects the activities set for controlling the risk and also to reduce the risk
impacts. This standard provides the principles for handling the risk which are related to the
sector information technology (Ibáñez et al, 2016). ISO 31000 standards mainly focus on the
implementation of the security system with the help of the business risk management.
This standard has the scope for all the organizations to the design, implementation and
maintenance of the risk with the capability, process and functions for achieving the strategic
stability and security. This standard also involves the stakeholders of the business for supporting
the organizational operations in effective manner (de Oliveira et al, 2017). The main objective of
this standard is to formulate the risk and then improve its security with the help of the
sustainable practices.
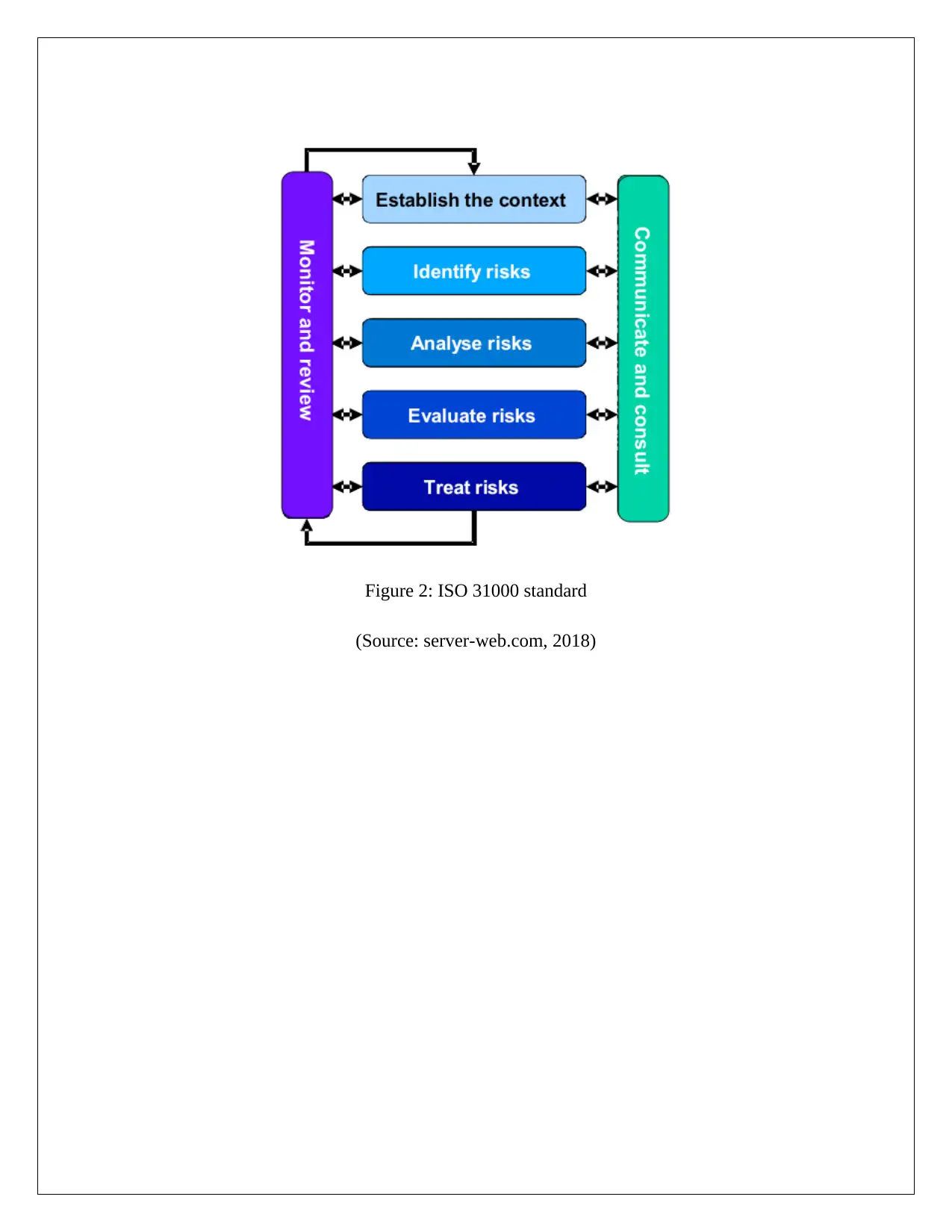
Figure 2: ISO 31000 standard
(Source: server-web.com, 2018)
(Source: server-web.com, 2018)
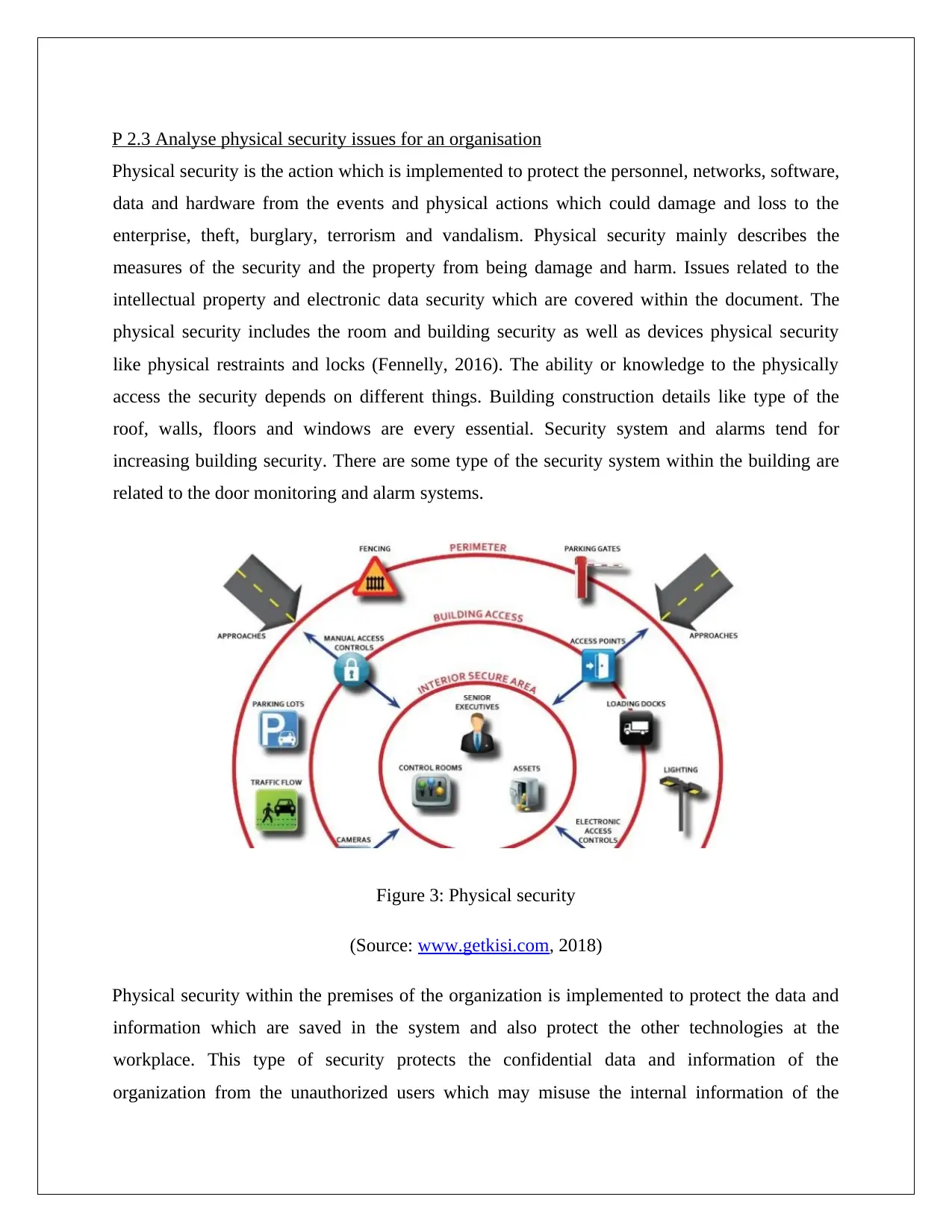
P 2.3 Analyse physical security issues for an organisation
Physical security is the action which is implemented to protect the personnel, networks, software,
data and hardware from the events and physical actions which could damage and loss to the
enterprise, theft, burglary, terrorism and vandalism. Physical security mainly describes the
measures of the security and the property from being damage and harm. Issues related to the
intellectual property and electronic data security which are covered within the document. The
physical security includes the room and building security as well as devices physical security
like physical restraints and locks (Fennelly, 2016). The ability or knowledge to the physically
access the security depends on different things. Building construction details like type of the
roof, walls, floors and windows are every essential. Security system and alarms tend for
increasing building security. There are some type of the security system within the building are
related to the door monitoring and alarm systems.
Figure 3: Physical security
(Source: www.getkisi.com, 2018)
Physical security within the premises of the organization is implemented to protect the data and
information which are saved in the system and also protect the other technologies at the
workplace. This type of security protects the confidential data and information of the
organization from the unauthorized users which may misuse the internal information of the
Physical security is the action which is implemented to protect the personnel, networks, software,
data and hardware from the events and physical actions which could damage and loss to the
enterprise, theft, burglary, terrorism and vandalism. Physical security mainly describes the
measures of the security and the property from being damage and harm. Issues related to the
intellectual property and electronic data security which are covered within the document. The
physical security includes the room and building security as well as devices physical security
like physical restraints and locks (Fennelly, 2016). The ability or knowledge to the physically
access the security depends on different things. Building construction details like type of the
roof, walls, floors and windows are every essential. Security system and alarms tend for
increasing building security. There are some type of the security system within the building are
related to the door monitoring and alarm systems.
Figure 3: Physical security
(Source: www.getkisi.com, 2018)
Physical security within the premises of the organization is implemented to protect the data and
information which are saved in the system and also protect the other technologies at the
workplace. This type of security protects the confidential data and information of the
organization from the unauthorized users which may misuse the internal information of the
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

organization (Rumelili, 2015). Following are the physical security procedure which can be used
and implemented by all the organizations to protect their computer systems and its information
from the unauthorized users:
The buildings and exterior doors of the premises are required to be kept locked all the
times except the specific purpose or procedure which has been established to leave that
door open. The doors only left open when the person is allowed to use the place and
under the monitoring assessment.
The individual workstations are required to be located in the single office or in the large
office with the various or multiple workstations. The users most control the physical
access to the business computers and office also (Hong et al, 2015). The rooms of the
workplace should be kept locked unless the members left it open for any official and
valid reason.
The rooms of the workplace contain the allocated systems, related equipment and
productive services which are kept to be locked with the access limitation to the
authorized employees.
The windows within the premises are also required to be kept locked unless the
employees within the rooms or in that position to access and monitor the things in the
rooms (Almorsy et al, 2016). This is essential and important for the organization to close
and lock all the rooms and windows on all the floors.
Buildings and offices keys are distributed to only those employees who are authorized
which are based on the individual employee actual needs to access the specific areas and
information of the organization.
The equipment which is assigned to the employee is under their responsibility to access
and protect from the unauthorized users also. If any provided equipment can break,
replaced or moved then the staff of information technology is the only team who is
responsible as they are assigned to use and protect the equipments (Granjal et al, 2015).
All the essential machines which are swapped among the individual or individual groups
that are contained all the sensitive information or data must require to have the hard drive
of the information before being utilized by any new member or users.
The organizations of every sector must be traced with the help of the inventory control
and the process of auditing once in a year (Ortmeier, 2017). This type of procedure or
and implemented by all the organizations to protect their computer systems and its information
from the unauthorized users:
The buildings and exterior doors of the premises are required to be kept locked all the
times except the specific purpose or procedure which has been established to leave that
door open. The doors only left open when the person is allowed to use the place and
under the monitoring assessment.
The individual workstations are required to be located in the single office or in the large
office with the various or multiple workstations. The users most control the physical
access to the business computers and office also (Hong et al, 2015). The rooms of the
workplace should be kept locked unless the members left it open for any official and
valid reason.
The rooms of the workplace contain the allocated systems, related equipment and
productive services which are kept to be locked with the access limitation to the
authorized employees.
The windows within the premises are also required to be kept locked unless the
employees within the rooms or in that position to access and monitor the things in the
rooms (Almorsy et al, 2016). This is essential and important for the organization to close
and lock all the rooms and windows on all the floors.
Buildings and offices keys are distributed to only those employees who are authorized
which are based on the individual employee actual needs to access the specific areas and
information of the organization.
The equipment which is assigned to the employee is under their responsibility to access
and protect from the unauthorized users also. If any provided equipment can break,
replaced or moved then the staff of information technology is the only team who is
responsible as they are assigned to use and protect the equipments (Granjal et al, 2015).
All the essential machines which are swapped among the individual or individual groups
that are contained all the sensitive information or data must require to have the hard drive
of the information before being utilized by any new member or users.
The organizations of every sector must be traced with the help of the inventory control
and the process of auditing once in a year (Ortmeier, 2017). This type of procedure or

process will help the organization to identify their security issues and other related
problems.
Physical security issues
With the help of the above discussion it will become clear that physical security of the premises
is equally important as the logical security is. It is analyzed that, with the physical security
implementation they can avoid the chances of the data theft, access of data by unauthorized users
of any machinery or equipment (Trappe, 2015). Still there are some physical security issues that
are faced by the organization and their information technology team regarding the data and
system security. There are some of the guidelines which are related to the physical security
which can be used to implement the security but issues occurred when these guidelines are not
followed by the organization and its team and that issues are discussed below:
Physical security issues faced by the organization when arouse of the internet in the
secured areas done unnecessary. When the use of the locations signs are increased then
the issues in the physical security increased.
When the external access is also increased or enhanced by the user then the issues are
faced by the organization and their team. Security of the rooms is also not up to the mark
as they do not have any solid locking system at the doors (Yan et al, 2015).
The opened doors or windows are not under the supervision of any authorized person or
observation then the misuse of the system and its data can be occurred which cause the
issues in the physical security.
When organization do not maintain the secured systems for any combination or keys
them the physical security issues are faced by the organization within their premises. It is
important to secure the doors with any locking or combination pattern to protect the
particular area.
Issues related to the physical security occurred when the non-essential things or materials
which could jeopardize the secured rooms is happened (Almorsy et al, 2016). This will
causes the actual issues for the organization when the loss to implement the up to date
physical security system.
problems.
Physical security issues
With the help of the above discussion it will become clear that physical security of the premises
is equally important as the logical security is. It is analyzed that, with the physical security
implementation they can avoid the chances of the data theft, access of data by unauthorized users
of any machinery or equipment (Trappe, 2015). Still there are some physical security issues that
are faced by the organization and their information technology team regarding the data and
system security. There are some of the guidelines which are related to the physical security
which can be used to implement the security but issues occurred when these guidelines are not
followed by the organization and its team and that issues are discussed below:
Physical security issues faced by the organization when arouse of the internet in the
secured areas done unnecessary. When the use of the locations signs are increased then
the issues in the physical security increased.
When the external access is also increased or enhanced by the user then the issues are
faced by the organization and their team. Security of the rooms is also not up to the mark
as they do not have any solid locking system at the doors (Yan et al, 2015).
The opened doors or windows are not under the supervision of any authorized person or
observation then the misuse of the system and its data can be occurred which cause the
issues in the physical security.
When organization do not maintain the secured systems for any combination or keys
them the physical security issues are faced by the organization within their premises. It is
important to secure the doors with any locking or combination pattern to protect the
particular area.
Issues related to the physical security occurred when the non-essential things or materials
which could jeopardize the secured rooms is happened (Almorsy et al, 2016). This will
causes the actual issues for the organization when the loss to implement the up to date
physical security system.
Figure 4: Physical security on the doors
(Source: trueies.com, 2018)
(Source: trueies.com, 2018)
Secure Best Marks with AI Grader
Need help grading? Try our AI Grader for instant feedback on your assignments.

Task 3
P3.1 Design and implement a security policy for an organisation
Security policy can be defined as the framework of the data and asset management so that security can
be achieved. It guides the organization and users for the security process. The organization can use the
following processes to design the security policy:
Identify sensitive information and critical systems
The organization has to identify the systems those are vulnerable for the risks and contain the sensitive
information. The organization has to identify the information and systems those must be taken on the
priorities to meet the security goals. For example, accounting and management computers contain the
confidential information required for the organizational growth whereas the organizational server
contains the private information of the users including their financial records and bank details.
Incorporate laws
The organization has to incorporate with the ethical standards and local and federal laws those can be
used to protect the security. The design process has to consider the integration of the laws and standards
in the practices so that internal and external conflicts for the data management and communication can
be prevented (Nces.ed.gov, 2018).
Defines security goals
Design of the security policies has focus on the organizational goals and objectives for the security as it
helps to understand the requirements and constraints for the desired outcomes. It is also useful to
understand the required process for the security policy.
Set a course for policy
Once the organization goals and objectives are clearly identified then the organization can define the set
of actions those can accomplished the goals in to the desired security. The organization can standardize
the process and actions in the business according to the goals so that security on the user management,
data access and device utilization can be enforced. It simply means to document the practices, guidelines
P3.1 Design and implement a security policy for an organisation
Security policy can be defined as the framework of the data and asset management so that security can
be achieved. It guides the organization and users for the security process. The organization can use the
following processes to design the security policy:
Identify sensitive information and critical systems
The organization has to identify the systems those are vulnerable for the risks and contain the sensitive
information. The organization has to identify the information and systems those must be taken on the
priorities to meet the security goals. For example, accounting and management computers contain the
confidential information required for the organizational growth whereas the organizational server
contains the private information of the users including their financial records and bank details.
Incorporate laws
The organization has to incorporate with the ethical standards and local and federal laws those can be
used to protect the security. The design process has to consider the integration of the laws and standards
in the practices so that internal and external conflicts for the data management and communication can
be prevented (Nces.ed.gov, 2018).
Defines security goals
Design of the security policies has focus on the organizational goals and objectives for the security as it
helps to understand the requirements and constraints for the desired outcomes. It is also useful to
understand the required process for the security policy.
Set a course for policy
Once the organization goals and objectives are clearly identified then the organization can define the set
of actions those can accomplished the goals in to the desired security. The organization can standardize
the process and actions in the business according to the goals so that security on the user management,
data access and device utilization can be enforced. It simply means to document the practices, guidelines

and principles those can be used to boost the security. For example, the organization has define the
process for the physical security of the servers and systems, user access management and their roles to
the resource utilization and management, access control on the website and security during the data
transmission over the internet connections (Nsit.ac.in, 2018). Each area is required to be bounded with
desired actions to meet the security goals.
Review the policy to ensure security
Then the design process for the security policy has to focus on the review so that missing actions can be
considered to ensure proper security. The organization can review the policy for the security standards
and laws along with the organizational goals and objectives.
Security policy
Purpose: Security policy has goal to standardize the process to make use of the services for the
profitability and operations of the organization. It has objectives to empower the operations with
limitation of the security threats on the system.
Computing devices
Any damage or destruction to the computing devices allocated to the users at workplace should
be handled and beard at user side if it is generated from the user unawareness or improper use of
systems.
User has to take the role and responsibilities to protect the devices physically or logically
accessible for others to ensure assets as well as data security.
Improper use or misuse of the systems should be reported to the management to avoid the loss to
the business.
It is not ethical to access the others system or try to breach them for personal objectives.
Web access
The users are recommended to use the following guidelines when they prefer to access the web services
over the wireless or unsecure connection:
process for the physical security of the servers and systems, user access management and their roles to
the resource utilization and management, access control on the website and security during the data
transmission over the internet connections (Nsit.ac.in, 2018). Each area is required to be bounded with
desired actions to meet the security goals.
Review the policy to ensure security
Then the design process for the security policy has to focus on the review so that missing actions can be
considered to ensure proper security. The organization can review the policy for the security standards
and laws along with the organizational goals and objectives.
Security policy
Purpose: Security policy has goal to standardize the process to make use of the services for the
profitability and operations of the organization. It has objectives to empower the operations with
limitation of the security threats on the system.
Computing devices
Any damage or destruction to the computing devices allocated to the users at workplace should
be handled and beard at user side if it is generated from the user unawareness or improper use of
systems.
User has to take the role and responsibilities to protect the devices physically or logically
accessible for others to ensure assets as well as data security.
Improper use or misuse of the systems should be reported to the management to avoid the loss to
the business.
It is not ethical to access the others system or try to breach them for personal objectives.
Web access
The users are recommended to use the following guidelines when they prefer to access the web services
over the wireless or unsecure connection:

Do not share the financial, confidential or private information on the mail or websites. It might
become the issue on security.
Ensure that there is no unwanted traffic on the web server due to uncontrolled requests from the
unauthorized users. It can bottleneck the server performance.
Do not share or access the prohibited content on the website (Nces.ed.gov, 2018).
Make sure that the content or media shared on the websites are free from the ethical issues and
do not promote the internal conflicts among users.
Mail services
Do not share authentication details with others as they can access mail account, fetch
information, make miscommunication with others and delete the account. Do not store the authentication details on the web browsers or client mail applications. Ensure to use two-step authentication method for high security. Do not use abusing language with others on mail during the communication. It can lead the
internal issues for the services. Encrypt the data and validate the receivers address for further authentication on communication.
become the issue on security.
Ensure that there is no unwanted traffic on the web server due to uncontrolled requests from the
unauthorized users. It can bottleneck the server performance.
Do not share or access the prohibited content on the website (Nces.ed.gov, 2018).
Make sure that the content or media shared on the websites are free from the ethical issues and
do not promote the internal conflicts among users.
Mail services
Do not share authentication details with others as they can access mail account, fetch
information, make miscommunication with others and delete the account. Do not store the authentication details on the web browsers or client mail applications. Ensure to use two-step authentication method for high security. Do not use abusing language with others on mail during the communication. It can lead the
internal issues for the services. Encrypt the data and validate the receivers address for further authentication on communication.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
P3.2 Evaluate the suitability of the tools used in an organisational policy
The organization can use various tools to monitor the user access in the system and ensure that the
access to the external network components is safe and secure. The organization has to consider the
features and functions of the monitoring software to meet the security policy related demands.
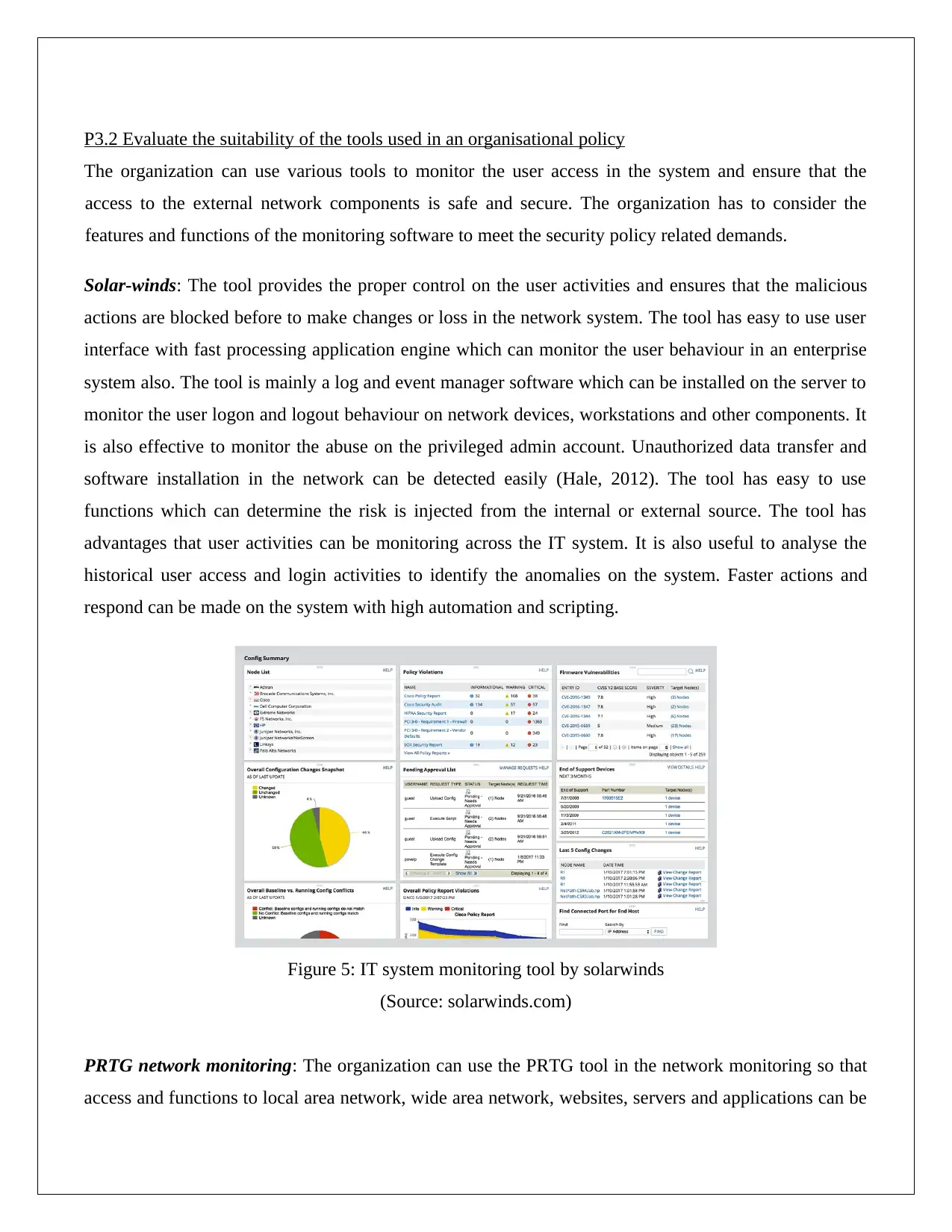
Solar-winds: The tool provides the proper control on the user activities and ensures that the malicious
actions are blocked before to make changes or loss in the network system. The tool has easy to use user
interface with fast processing application engine which can monitor the user behaviour in an enterprise
system also. The tool is mainly a log and event manager software which can be installed on the server to
monitor the user logon and logout behaviour on network devices, workstations and other components. It
is also effective to monitor the abuse on the privileged admin account. Unauthorized data transfer and
software installation in the network can be detected easily (Hale, 2012). The tool has easy to use
functions which can determine the risk is injected from the internal or external source. The tool has
advantages that user activities can be monitoring across the IT system. It is also useful to analyse the
historical user access and login activities to identify the anomalies on the system. Faster actions and
respond can be made on the system with high automation and scripting.
Figure 5: IT system monitoring tool by solarwinds
(Source: solarwinds.com)
PRTG network monitoring: The organization can use the PRTG tool in the network monitoring so that
access and functions to local area network, wide area network, websites, servers and applications can be
The organization can use various tools to monitor the user access in the system and ensure that the
access to the external network components is safe and secure. The organization has to consider the
features and functions of the monitoring software to meet the security policy related demands.
Solar-winds: The tool provides the proper control on the user activities and ensures that the malicious
actions are blocked before to make changes or loss in the network system. The tool has easy to use user
interface with fast processing application engine which can monitor the user behaviour in an enterprise
system also. The tool is mainly a log and event manager software which can be installed on the server to
monitor the user logon and logout behaviour on network devices, workstations and other components. It
is also effective to monitor the abuse on the privileged admin account. Unauthorized data transfer and
software installation in the network can be detected easily (Hale, 2012). The tool has easy to use
functions which can determine the risk is injected from the internal or external source. The tool has
advantages that user activities can be monitoring across the IT system. It is also useful to analyse the
historical user access and login activities to identify the anomalies on the system. Faster actions and
respond can be made on the system with high automation and scripting.
Figure 5: IT system monitoring tool by solarwinds
(Source: solarwinds.com)
PRTG network monitoring: The organization can use the PRTG tool in the network monitoring so that
access and functions to local area network, wide area network, websites, servers and applications can be

managed. With the network auto-discovery feature in the tool, the organization can save a lot of time on
the network configuration as it can use auto ping command to ensure the secure connectivity to the end
devices (Solomon et al, 2016). It provides robust security in the design and implementation of the web
pages so that the organization can focus on the monitoring rather than the mapping of the pages to each
other to create the shared environment for IT systems. The tool has flexible alert system so that
administrator in the network can control the user access to the external website or manage the risks on
the data storage. Multiuser interface also enables the organization to work from the different computers
and scale the services to the large number of the users. Distributed monitoring and in-depth reporting of
network has helped to understand the network health for the security, user access and remote access. It
has helped to understand the potential weaker or insecure areas.
Figure 6: PRTG network monitoring tool
(Source: paessler.com)
NetFort LanGuardian: The tool is also a powerful tool designed to monitor the user activities and
network performance. The tool can accomplish the in-depth analysis of the network data packets so that
ransomware, network attacks and file compromising actions can be identified. It is effective to analyse
the data packets (Netfort.com, 2018). However, the organization has lack of automation and scripting on
the user and network management. The tool has only support for the manual operations and decision
making.
the network configuration as it can use auto ping command to ensure the secure connectivity to the end
devices (Solomon et al, 2016). It provides robust security in the design and implementation of the web
pages so that the organization can focus on the monitoring rather than the mapping of the pages to each
other to create the shared environment for IT systems. The tool has flexible alert system so that
administrator in the network can control the user access to the external website or manage the risks on
the data storage. Multiuser interface also enables the organization to work from the different computers
and scale the services to the large number of the users. Distributed monitoring and in-depth reporting of
network has helped to understand the network health for the security, user access and remote access. It
has helped to understand the potential weaker or insecure areas.
Figure 6: PRTG network monitoring tool
(Source: paessler.com)
NetFort LanGuardian: The tool is also a powerful tool designed to monitor the user activities and
network performance. The tool can accomplish the in-depth analysis of the network data packets so that
ransomware, network attacks and file compromising actions can be identified. It is effective to analyse
the data packets (Netfort.com, 2018). However, the organization has lack of automation and scripting on
the user and network management. The tool has only support for the manual operations and decision
making.
Figure 7: NetFort tool
(Source: Netfort.com)
From the above three major network monitoring and user activity monitoring software, the organization
is recommended to use the PRTG tool because of the faster and reliable user interface with high support
to decision making process. The tool is also scalable and flexible to work in the increasing number of
the IT systems. It is recommended to use PRTG tool because of the functions and features for device
mapping, faster issue resolving and alert system. However, the tool has high cost on the installation and
maintenance.
(Source: Netfort.com)
From the above three major network monitoring and user activity monitoring software, the organization
is recommended to use the PRTG tool because of the faster and reliable user interface with high support
to decision making process. The tool is also scalable and flexible to work in the increasing number of
the IT systems. It is recommended to use PRTG tool because of the functions and features for device
mapping, faster issue resolving and alert system. However, the tool has high cost on the installation and
maintenance.
Secure Best Marks with AI Grader
Need help grading? Try our AI Grader for instant feedback on your assignments.

P 3.3 Discuss the human resource issues that have to be considered when carrying out security audits
The organization has stakeholders that are basically defines as the depositors that conduct the activities
and efforts for determining the organizational output. The role of the organizational stakeholders is
related to the security within the organizational premises. The employees of the organizations are
treated as the internal stakeholders and play major role to protect the security at their workplace. Their
goal is related to the security audit which is essentially recommended for meeting the security and other
demands that come from the actual and authorized users. Technical team of the organization also play
major role for ensuring about the security audit that is undergoing with the desired operations for
determining the security which can fulfil all the requirements of the business (Rozanski and Woods,
2012).
The investors within the organization role vital role to protect the security at their workplace as they
identify the requirement of the security audit and compare that result with the current market trends for
achieving the surveillance and profitability in the stable condition. To interfaced the user, the process of
transmission of the information and data which are based on the suggestions or recommendations which
are provided by the users. All essential type of things can be performed to support the security system of
the organization which is required by the organization and that include the potential resources, time, cost
and knowledge. The directors of the firm have the special power which is related to the counsel the
organizational strengths and structural outcomes so that they can accomplish the performance in
effective manner to achieve the objective of the organization with the huge profit margin through the
implementation of security audit (Ernawati and Nugroho, 2012).
The management team within the organization play the central role by providing the official and
important guidelines to all the employees so that they can understand the importance of the security. On
the other side, the other stakeholders play the vital role which is related to the installation panel and
network designer. The main role of these is to simplify the changes in the future and also update the
document preparation in the network. To rectify the future problems and their solutions the IT systems
are used in the organization which enhance the role of the team (Trappe, 2015). Leaders of the
organization are also having the essential role which is related to the determination of the opportunities
and scope of the organization.
The organization has stakeholders that are basically defines as the depositors that conduct the activities
and efforts for determining the organizational output. The role of the organizational stakeholders is
related to the security within the organizational premises. The employees of the organizations are
treated as the internal stakeholders and play major role to protect the security at their workplace. Their
goal is related to the security audit which is essentially recommended for meeting the security and other
demands that come from the actual and authorized users. Technical team of the organization also play
major role for ensuring about the security audit that is undergoing with the desired operations for
determining the security which can fulfil all the requirements of the business (Rozanski and Woods,
2012).
The investors within the organization role vital role to protect the security at their workplace as they
identify the requirement of the security audit and compare that result with the current market trends for
achieving the surveillance and profitability in the stable condition. To interfaced the user, the process of
transmission of the information and data which are based on the suggestions or recommendations which
are provided by the users. All essential type of things can be performed to support the security system of
the organization which is required by the organization and that include the potential resources, time, cost
and knowledge. The directors of the firm have the special power which is related to the counsel the
organizational strengths and structural outcomes so that they can accomplish the performance in
effective manner to achieve the objective of the organization with the huge profit margin through the
implementation of security audit (Ernawati and Nugroho, 2012).
The management team within the organization play the central role by providing the official and
important guidelines to all the employees so that they can understand the importance of the security. On
the other side, the other stakeholders play the vital role which is related to the installation panel and
network designer. The main role of these is to simplify the changes in the future and also update the
document preparation in the network. To rectify the future problems and their solutions the IT systems
are used in the organization which enhance the role of the team (Trappe, 2015). Leaders of the
organization are also having the essential role which is related to the determination of the opportunities
and scope of the organization.

Conclusion
The above report is all about the IT (Information technology) security importance in the organization.
The report has concluded the facts which are responsible for the security issues which are faced by the
organization and their team members. The vulnerable threats and issues of security related which are
related to the use of the internet are also concluded from the above report. This report has concluded that
to secure the IT systems against the security risk then the organization should implement the methods
and procedures which are related to the security. This report has also highlight the prospective impacts
because of the wrong configuration of the IT systems. It has also revealed that with the help of the
implementation of the regulations and security policies to protect the data is essential for the
organization. The report has concluded that proper and effective integration of the risk management
process within the business will reduce the risk and its impact.
The above report is all about the IT (Information technology) security importance in the organization.
The report has concluded the facts which are responsible for the security issues which are faced by the
organization and their team members. The vulnerable threats and issues of security related which are
related to the use of the internet are also concluded from the above report. This report has concluded that
to secure the IT systems against the security risk then the organization should implement the methods
and procedures which are related to the security. This report has also highlight the prospective impacts
because of the wrong configuration of the IT systems. It has also revealed that with the help of the
implementation of the regulations and security policies to protect the data is essential for the
organization. The report has concluded that proper and effective integration of the risk management
process within the business will reduce the risk and its impact.

References
Books and Journals
Hale, B., 2012. Network Management–Back to the Basics. Solarwinds Whitepaper, 16.
Zafar, H., Ko, M. and Osei-Bryson, K.M., 2012. Financial impact of information security
breaches on breached firms and their non-breached competitors. Information Resources
Management Journal (IRMJ), 25(1), pp.21-37.
Conklin, W.A., White, G., Cothren, C., Davis, R. and Williams, D., 2015. Principles of computer
security. McGraw-Hill Education Group.
Carroll, J.M., 2014. Computer security. Butterworth-Heinemann.
Dottori, F.R.A.N.C.E.S.C.O., Salamon, P.E.T.E.R., Kalas, M.I.L.A.N., Bianchi,
A.L.E.S.S.A.N.D.R.A., Thielen, J.U.T.T.A. and Feyen, L., 2015, June. A near real-time
procedure for flood hazard mapping and risk assessment in Europe. In 36th IAHR World
Congress (Vol. 28).
Li, W., 2014. Risk assessment of power systems: models, methods, and applications. John Wiley
& Sons.
William Jr, M., Glover, S. and Prawitt, D., 2016. Auditing and assurance services: A systematic
approach. McGraw-Hill Education.
Knechel, W.R. and Salterio, S.E., 2016. Auditing: Assurance and risk. Taylor & Francis.
Cherdantseva, Y., Burnap, P., Blyth, A., Eden, P., Jones, K., Soulsby, H. and Stoddart, K., 2016.
A review of cyber security risk assessment methods for SCADA systems. Computers &
security, 56, pp.1-27.
Suter II, G.W., 2016. Ecological risk assessment. CRC press.
Gan, M.F., Chua, H.N. and Wong, S.F., 2018. Personal Data Protection Act Enforcement with
PETs Adoption: An Exploratory Study on Employees’ Working Process Change. In IT
Convergence and Security 2017 (pp. 193-202). Springer, Singapore.
Tan, D., 2017. Image Rights and Data Protection.
Wall, D.S., 2015. The Internet as a conduit for criminal activity.
El Asam, A. and Samara, M., 2016. Cyberbullying and the law: A review of psychological and
legal challenges. Computers in Human Behavior, 65, pp.127-141.
Books and Journals
Hale, B., 2012. Network Management–Back to the Basics. Solarwinds Whitepaper, 16.
Zafar, H., Ko, M. and Osei-Bryson, K.M., 2012. Financial impact of information security
breaches on breached firms and their non-breached competitors. Information Resources
Management Journal (IRMJ), 25(1), pp.21-37.
Conklin, W.A., White, G., Cothren, C., Davis, R. and Williams, D., 2015. Principles of computer
security. McGraw-Hill Education Group.
Carroll, J.M., 2014. Computer security. Butterworth-Heinemann.
Dottori, F.R.A.N.C.E.S.C.O., Salamon, P.E.T.E.R., Kalas, M.I.L.A.N., Bianchi,
A.L.E.S.S.A.N.D.R.A., Thielen, J.U.T.T.A. and Feyen, L., 2015, June. A near real-time
procedure for flood hazard mapping and risk assessment in Europe. In 36th IAHR World
Congress (Vol. 28).
Li, W., 2014. Risk assessment of power systems: models, methods, and applications. John Wiley
& Sons.
William Jr, M., Glover, S. and Prawitt, D., 2016. Auditing and assurance services: A systematic
approach. McGraw-Hill Education.
Knechel, W.R. and Salterio, S.E., 2016. Auditing: Assurance and risk. Taylor & Francis.
Cherdantseva, Y., Burnap, P., Blyth, A., Eden, P., Jones, K., Soulsby, H. and Stoddart, K., 2016.
A review of cyber security risk assessment methods for SCADA systems. Computers &
security, 56, pp.1-27.
Suter II, G.W., 2016. Ecological risk assessment. CRC press.
Gan, M.F., Chua, H.N. and Wong, S.F., 2018. Personal Data Protection Act Enforcement with
PETs Adoption: An Exploratory Study on Employees’ Working Process Change. In IT
Convergence and Security 2017 (pp. 193-202). Springer, Singapore.
Tan, D., 2017. Image Rights and Data Protection.
Wall, D.S., 2015. The Internet as a conduit for criminal activity.
El Asam, A. and Samara, M., 2016. Cyberbullying and the law: A review of psychological and
legal challenges. Computers in Human Behavior, 65, pp.127-141.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

Ibáñez, A.J.P., Bernal, J.M.M., de Diego, M.J.C. and Sánchez, F.J.A., 2016. Expert system for
predicting buildings service life under ISO 31000 standard. Application in architectural
heritage. Journal of Cultural Heritage, 18, pp.209-218.
de Oliveira, U.R., Marins, F.A.S., Rocha, H.M. and Salomon, V.A.P., 2017. The ISO 31000
standard in supply chain risk management. Journal of Cleaner Production, 151, pp.616-633.
Fennelly, L., 2016. Effective physical security. Butterworth-Heinemann.
Rumelili, B., 2015. Identity and desecuritisation: the pitfalls of conflating ontological and
physical security. Journal of International Relations and Development, 18(1), pp.52-74.
Ortmeier, P.J., 2017. Introduction to security. Pearson.
Granjal, J., Monteiro, E. and Silva, J.S., 2015. Security for the internet of things: a survey of
existing protocols and open research issues. IEEE Communications Surveys & Tutorials, 17(3),
pp.1294-1312.
Almorsy, M., Grundy, J. and Müller, I., 2016. An analysis of the cloud computing security
problem. arXiv preprint arXiv:1609.01107.
Hong, J., Nuqui, R., Ishchenko, D., Wang, Z., Cui, T., Kondabathini, A., Coats, D. and
Kunsman, S.A., 2015. Cyber-physical security test bed: A platform for enabling collaborative
cyber defense methods. In PACWorld Americas Conference.
Trappe, W., 2015. The challenges facing physical layer security. IEEE communications
magazine, 53(6), pp.16-20.
Yang, N., Wang, L., Geraci, G., Elkashlan, M., Yuan, J. and Di Renzo, M., 2015. Safeguarding
5G wireless communication networks using physical layer security. IEEE Communications
Magazine, 53(4), pp.20-27.
Rozanski, N. and Woods, E., 2012. Software systems architecture: working with stakeholders
using viewpoints and perspectives. Addison-Wesley.
Ernawati, T. and Nugroho, D.R., 2012, September. IT risk management framework based on ISO
31000: 2009. In System Engineering and Technology (ICSET), 2012 International Conference
on (pp. 1-8). IEEE.
Solomon, T., Zungeru, A.M. and Selvaraj, R., 2016, April. Network traffic monitoring in an
industrial environment. In Electrical, Electronics, Computer Engineering and their Applications
(EECEA), 2016 Third International Conference on(pp. 133-139). IEEE.
Online references
predicting buildings service life under ISO 31000 standard. Application in architectural
heritage. Journal of Cultural Heritage, 18, pp.209-218.
de Oliveira, U.R., Marins, F.A.S., Rocha, H.M. and Salomon, V.A.P., 2017. The ISO 31000
standard in supply chain risk management. Journal of Cleaner Production, 151, pp.616-633.
Fennelly, L., 2016. Effective physical security. Butterworth-Heinemann.
Rumelili, B., 2015. Identity and desecuritisation: the pitfalls of conflating ontological and
physical security. Journal of International Relations and Development, 18(1), pp.52-74.
Ortmeier, P.J., 2017. Introduction to security. Pearson.
Granjal, J., Monteiro, E. and Silva, J.S., 2015. Security for the internet of things: a survey of
existing protocols and open research issues. IEEE Communications Surveys & Tutorials, 17(3),
pp.1294-1312.
Almorsy, M., Grundy, J. and Müller, I., 2016. An analysis of the cloud computing security
problem. arXiv preprint arXiv:1609.01107.
Hong, J., Nuqui, R., Ishchenko, D., Wang, Z., Cui, T., Kondabathini, A., Coats, D. and
Kunsman, S.A., 2015. Cyber-physical security test bed: A platform for enabling collaborative
cyber defense methods. In PACWorld Americas Conference.
Trappe, W., 2015. The challenges facing physical layer security. IEEE communications
magazine, 53(6), pp.16-20.
Yang, N., Wang, L., Geraci, G., Elkashlan, M., Yuan, J. and Di Renzo, M., 2015. Safeguarding
5G wireless communication networks using physical layer security. IEEE Communications
Magazine, 53(4), pp.20-27.
Rozanski, N. and Woods, E., 2012. Software systems architecture: working with stakeholders
using viewpoints and perspectives. Addison-Wesley.
Ernawati, T. and Nugroho, D.R., 2012, September. IT risk management framework based on ISO
31000: 2009. In System Engineering and Technology (ICSET), 2012 International Conference
on (pp. 1-8). IEEE.
Solomon, T., Zungeru, A.M. and Selvaraj, R., 2016, April. Network traffic monitoring in an
industrial environment. In Electrical, Electronics, Computer Engineering and their Applications
(EECEA), 2016 Third International Conference on(pp. 133-139). IEEE.
Online references

Information security procedures, 2018. Data privacy and security [Online] [Accessed Through]
<http://www.naic.org/documents/committees_e_ritf_receivership_data_privacy_and_security.pd
f> [Accessed On: 28th May, 2018]
ISO 31000 standard, 2018 [Online] [Assessed through] <http://esvc001356.wic015u.server-
web.com/iso31000/index.html>, [Assessed on 28th May, 2018]
Michael Sanchez, 2010. The 10 most common security threats explained [Online] [Accessed
Through] <https://blogs.cisco.com/smallbusiness/the-10-most-common-security-threats-
explained> [Accessed On: 28th May, 2018]
Nces.ed.gov, 2018. Security Policy: Development and Implementation [Online] [Accessed
Through] <https://nces.ed.gov/pubs98/safetech/chapter3.asp> [Accessed On: 28th May, 2018]
Netfort.com, 2018. About Netfort LanGuardian [Online] [Accessed Through]
<https://www.netfort.com/languardian/> [Accessed On: 28th May, 2018]
Nsit.ac.in, 2018. IT security and audit policy [Online] [Accessed Through]
<http://www.nsit.ac.in/static/documents/notices/itsa_policy.pdf> [Accessed On: 28th May, 2018]
Paessler.com, 2018. About PRTG tool [Online] [Accessed Through]
<https://blog.paessler.com/a-year-in-reviews https://blog.paessler.com/a-year-in-reviews>
[Accessed On: 28th May, 2018]
Physical security on the doors, 2018 [Online] [Assessed through]
<http://www.trueies.com/service/physical-security/>, [Assessed on 28th May, 2018]
Physical security, 2018 [Online] [Assessed through] <https://www.getkisi.com/blog/physical-
security-assessment-problems-it-can-uncover>, [Assessed on 28th May, 2018]
Rapid7.com, 2018. Common Types of Cybesecurity Attacks [Online] [Accessed Through]
<https://www.rapid7.com/fundamentals/types-of-attacks/> [Accessed On: 28th May, 2018]
Ray Dunham, 2018. Security Procedures – How Do They Fit Into My Overall Security
Documentation Library? [Online] [Accessed Through] <https://linfordco.com/blog/security-
procedures/> [Accessed On: 28th May, 2018]
Risk assessment procedure, 2018 [Online] [Assessed through]
<https://www.idc.co.za/IR2012/governance-enterprise-risk-management.php>, [Assessed on 28th
May, 2018]
<http://www.naic.org/documents/committees_e_ritf_receivership_data_privacy_and_security.pd
f> [Accessed On: 28th May, 2018]
ISO 31000 standard, 2018 [Online] [Assessed through] <http://esvc001356.wic015u.server-
web.com/iso31000/index.html>, [Assessed on 28th May, 2018]
Michael Sanchez, 2010. The 10 most common security threats explained [Online] [Accessed
Through] <https://blogs.cisco.com/smallbusiness/the-10-most-common-security-threats-
explained> [Accessed On: 28th May, 2018]
Nces.ed.gov, 2018. Security Policy: Development and Implementation [Online] [Accessed
Through] <https://nces.ed.gov/pubs98/safetech/chapter3.asp> [Accessed On: 28th May, 2018]
Netfort.com, 2018. About Netfort LanGuardian [Online] [Accessed Through]
<https://www.netfort.com/languardian/> [Accessed On: 28th May, 2018]
Nsit.ac.in, 2018. IT security and audit policy [Online] [Accessed Through]
<http://www.nsit.ac.in/static/documents/notices/itsa_policy.pdf> [Accessed On: 28th May, 2018]
Paessler.com, 2018. About PRTG tool [Online] [Accessed Through]
<https://blog.paessler.com/a-year-in-reviews https://blog.paessler.com/a-year-in-reviews>
[Accessed On: 28th May, 2018]
Physical security on the doors, 2018 [Online] [Assessed through]
<http://www.trueies.com/service/physical-security/>, [Assessed on 28th May, 2018]
Physical security, 2018 [Online] [Assessed through] <https://www.getkisi.com/blog/physical-
security-assessment-problems-it-can-uncover>, [Assessed on 28th May, 2018]
Rapid7.com, 2018. Common Types of Cybesecurity Attacks [Online] [Accessed Through]
<https://www.rapid7.com/fundamentals/types-of-attacks/> [Accessed On: 28th May, 2018]
Ray Dunham, 2018. Security Procedures – How Do They Fit Into My Overall Security
Documentation Library? [Online] [Accessed Through] <https://linfordco.com/blog/security-
procedures/> [Accessed On: 28th May, 2018]
Risk assessment procedure, 2018 [Online] [Assessed through]
<https://www.idc.co.za/IR2012/governance-enterprise-risk-management.php>, [Assessed on 28th
May, 2018]

Roger A. Grimes, 2017. IT's 9 biggest security threats [Online] [Accessed Through]
<https://www.csoonline.com/article/3215111/security/security-it-s-9-biggest-security-
threats.html> [Accessed On: 28th May, 2018]
Solarwinds.com, 2018. About solarwind monitoring tool [Online] [Accessed Through]
<https://www.solarwinds.com/orion> [Accessed On: 28th May, 2018]
<https://www.csoonline.com/article/3215111/security/security-it-s-9-biggest-security-
threats.html> [Accessed On: 28th May, 2018]
Solarwinds.com, 2018. About solarwind monitoring tool [Online] [Accessed Through]
<https://www.solarwinds.com/orion> [Accessed On: 28th May, 2018]
1 out of 31
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)





