MITS5004 IT Security: Literature Review of Social Engineering
VerifiedAdded on 2022/10/04
|8
|2099
|52
Literature Review
AI Summary
This document presents a literature review focused on social engineering attacks, with a particular emphasis on phishing. It introduces the concept of social engineering as a manipulation tactic targeting individuals with limited security knowledge, highlighting its significant impact on information security. The review identifies various types of phishing attacks, including spoofed emails, fake social network accounts, hacking attempts, and Trojan horse deployments, detailing how each method compromises user data and system integrity. Furthermore, it explores prevention and detection techniques, such as spoofed email detection using spam filters and DMARC, fake account detection through user awareness and cautious sharing, hacking detection via password management and updated antivirus software, and Trojan horse detection by careful file handling. The review also summarizes various detection techniques like SURF, SEAD, Anti Phishing tool, authentication, link guard algorithm and the ontological model. The paper concludes by emphasizing the ongoing challenge of detecting sophisticated phishing attempts and suggests the future implementation of advanced algorithms for enhanced security.

Running head: IT SECURITY
IT SECURITY
Name of the Student
Name of the Organization
Author Note
IT SECURITY
Name of the Student
Name of the Organization
Author Note
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

1IT SECURITY
A Literature Survey on Social Engineering Attacks: Phishing Attack
Introduction
The actual aim of the security of information is mainly to protect the information
which is greatly sensitive from that of all the various attacks of social engineering like the
attack of phishing and laundering of money. The attack of social engineering is basically a
kind of art where people gets manipulated who possess very much less knowledge regarding
all the various kinds of attack. It has been well noticed that each and every organization
possess a number of various issues related to security which brings in a number of various
concerns to all the users, developers of site and several specialists for the purpose of
defending the data which is greatly confidential from certain kinds of attacks of social
engineering. Phishing has been observed to be a hugely serious problem in the unlimited
internet service. There are a number of various ways of tricking various people for the
purpose of disclosing information from that of the user by utilising attacks of social
engineering. This attack of phishing is considered to be one of the most popular among all of
them. Here in this case, all the attackers highly bait various users by sending a number of
mails like winning prizes, sending messages from certain kinds of accounts which are entirely
fake on the sites of social networking and password hacking. Attackers even asks for the
account numbers as well as the numbers of credit cards for capturing various details. It
utilised various techniques of social engineering with several tricks that have been greatly
arranged for baiting users. This article has its main aim towards describing various kinds of
phishing attacks and properly explaining broadly regarding the prevention from various kinds
of attacks of social engineering. The paper will also be comprising of the proper analysis on
the techniques of the detection of social engineering attacks.
Phishing attacks
This particular attack is basically a cybercrime where the attacker will be
manipulating various people for eliciting all the data which are greatly personal. It has been
considered to be a huge issue related to security within the society. There are various
numbers as well as techniques of different kinds of solutions which have been present in the
current days for preventing such kinds of attacks [1]. However, it has also been observed that
various users are offering a lot of various personal information upon the webpage of phishing
which makes it really very much difficult for all the programmers. It has really become very
A Literature Survey on Social Engineering Attacks: Phishing Attack
Introduction
The actual aim of the security of information is mainly to protect the information
which is greatly sensitive from that of all the various attacks of social engineering like the
attack of phishing and laundering of money. The attack of social engineering is basically a
kind of art where people gets manipulated who possess very much less knowledge regarding
all the various kinds of attack. It has been well noticed that each and every organization
possess a number of various issues related to security which brings in a number of various
concerns to all the users, developers of site and several specialists for the purpose of
defending the data which is greatly confidential from certain kinds of attacks of social
engineering. Phishing has been observed to be a hugely serious problem in the unlimited
internet service. There are a number of various ways of tricking various people for the
purpose of disclosing information from that of the user by utilising attacks of social
engineering. This attack of phishing is considered to be one of the most popular among all of
them. Here in this case, all the attackers highly bait various users by sending a number of
mails like winning prizes, sending messages from certain kinds of accounts which are entirely
fake on the sites of social networking and password hacking. Attackers even asks for the
account numbers as well as the numbers of credit cards for capturing various details. It
utilised various techniques of social engineering with several tricks that have been greatly
arranged for baiting users. This article has its main aim towards describing various kinds of
phishing attacks and properly explaining broadly regarding the prevention from various kinds
of attacks of social engineering. The paper will also be comprising of the proper analysis on
the techniques of the detection of social engineering attacks.
Phishing attacks
This particular attack is basically a cybercrime where the attacker will be
manipulating various people for eliciting all the data which are greatly personal. It has been
considered to be a huge issue related to security within the society. There are various
numbers as well as techniques of different kinds of solutions which have been present in the
current days for preventing such kinds of attacks [1]. However, it has also been observed that
various users are offering a lot of various personal information upon the webpage of phishing
which makes it really very much difficult for all the programmers. It has really become very

2IT SECURITY
much difficult to properly distinguish between the email which is a legitimate one and the
one which is spoofed [2]. The email which is spoofed is known to be causing a huge harm to
the authentication of various users.
Types of Phishing Attacks
Spoofing email: This is basically a kind of attack of phishing and this spoofing is whenever
any spammer will be sending an email by utilising some other address of email. It will
actually seem as if the message is only for them and this will be tricking various people into
directly opening it.
Fake accounts of social networks: It has been noticed that all the various users of social
media sites like Facebook, LinkedIn as well as Twitter are totally unconscious regarding all
of their accounts. Any kind of fake account is easily created on the sites of social networking
by any kind of attacker [3]. Utilising such kinds of fake accounts, attackers often obtains the
access of all the secret data which any user provides whenever the account is created.
Hacking: Hacking is basically a kind of effort which is technical for manipulating the
system’s access or rather resources. A hacker is basically a kind of person who is capable of
engaging within that procedure [4]. Hackers mostly utilises any kind of scanner of
vulnerability or rather scanner of port for checking various computers upon the network for
all kinds of weaknesses which are totally known. Within this, social engineering has been
observed to be very much efficient as the users have been observed to be the part which is
mostly vulnerable of any organization [5].
Trojan horse: The attacks of Trojan horse is considered to be the threat which is mostly
deliberate to that of the security of the system [6]. It is basically a program which is
executable. It is a kind of code which has been specially designed for obtaining control over
the entire system.
Prevention of Phishing Social Engineering Attack
Detection of spoofed email: However there are no such way of stopping the spoofing of
email, there is only one possible trick of setting filtering of span for identifying all the emails
which will be spoofed. Actually the best way of stopping phishing is the direct blocking of
various emails which are malicious before they will be reaching the customer with the
DMARC by any organization [7]. It can be recommended that no one must be trusting upon
the name written on the display as various attackers utilise the names of brands. Any attacker
much difficult to properly distinguish between the email which is a legitimate one and the
one which is spoofed [2]. The email which is spoofed is known to be causing a huge harm to
the authentication of various users.
Types of Phishing Attacks
Spoofing email: This is basically a kind of attack of phishing and this spoofing is whenever
any spammer will be sending an email by utilising some other address of email. It will
actually seem as if the message is only for them and this will be tricking various people into
directly opening it.
Fake accounts of social networks: It has been noticed that all the various users of social
media sites like Facebook, LinkedIn as well as Twitter are totally unconscious regarding all
of their accounts. Any kind of fake account is easily created on the sites of social networking
by any kind of attacker [3]. Utilising such kinds of fake accounts, attackers often obtains the
access of all the secret data which any user provides whenever the account is created.
Hacking: Hacking is basically a kind of effort which is technical for manipulating the
system’s access or rather resources. A hacker is basically a kind of person who is capable of
engaging within that procedure [4]. Hackers mostly utilises any kind of scanner of
vulnerability or rather scanner of port for checking various computers upon the network for
all kinds of weaknesses which are totally known. Within this, social engineering has been
observed to be very much efficient as the users have been observed to be the part which is
mostly vulnerable of any organization [5].
Trojan horse: The attacks of Trojan horse is considered to be the threat which is mostly
deliberate to that of the security of the system [6]. It is basically a program which is
executable. It is a kind of code which has been specially designed for obtaining control over
the entire system.
Prevention of Phishing Social Engineering Attack
Detection of spoofed email: However there are no such way of stopping the spoofing of
email, there is only one possible trick of setting filtering of span for identifying all the emails
which will be spoofed. Actually the best way of stopping phishing is the direct blocking of
various emails which are malicious before they will be reaching the customer with the
DMARC by any organization [7]. It can be recommended that no one must be trusting upon
the name written on the display as various attackers utilise the names of brands. Any attacker
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

3IT SECURITY
may also be utilising the method of spelling mistake for making an email which will be
totally fake. In certain kinds of emails there is only the utilization of anchor test which is
observed in the browser of web but not in the URL.
Detection of fake accounts: Various sites of social networking possess a number of various
rules against the creation of accounts which will be fake but there is a huge lack of the
appropriate conformity towards the identification of the particular user. There is high chance
of manipulating someone by all the attackers which are making fake accounts in the social
networking sites [8]. It has been observed that various users shares a lot of information which
are greatly personal in their respective status or profile and this is where they offers the
hackers with the chance of assembling a lot of information regarding them for performing
spear phishing. For preventing certain kinds of attacks, the user must be maintaining a fixed
awareness of whatever they are sharing as well as posting and they must also be hugely aware
of the media which they will be actually sharing with some others utilising various links.
Detection of hacking: Detection of attacks of hacking is not at all a very simple task mainly
for all the users who do not possess any kind of information regarding the security of
accounts and attacks of internet. The very first thing which is to be done is that the password
must be kept secret and anytime any users provides the password to someone else, he/she
must be altering the password after they have completed the purpose of access [9]. Systems
must not be possessing any kind of virus and for this one must be downloading all the
programs and anti-virus that must be updated.
Detection of Trojan horse: One must be very much careful whenever any file will be
downloaded online and it is mostly just a specific matter of time before any one becomes the
victim of the Trojan horse [10]. If any file will be coming from any friend of office then one
must be confident enough regarding what the file is about before opening it as various
Trojans will be greatly trying to easily spread up themselves in the list of friend by utilising
any address book of email. One must also be taking care of all kinds of extensions of file that
will be entirely hidden as windows has been observed to be hiding the last file’s extension by
default.
Detection techniques of social engineering attacks
Some technique of detection will be involving SURF, SEAD, Anti Phishing tool,
authentication, link guard algorithm and the ontological model [11]. These are all the various
kinds of techniques of prevention from attacks of phishing and all of these techniques will be
may also be utilising the method of spelling mistake for making an email which will be
totally fake. In certain kinds of emails there is only the utilization of anchor test which is
observed in the browser of web but not in the URL.
Detection of fake accounts: Various sites of social networking possess a number of various
rules against the creation of accounts which will be fake but there is a huge lack of the
appropriate conformity towards the identification of the particular user. There is high chance
of manipulating someone by all the attackers which are making fake accounts in the social
networking sites [8]. It has been observed that various users shares a lot of information which
are greatly personal in their respective status or profile and this is where they offers the
hackers with the chance of assembling a lot of information regarding them for performing
spear phishing. For preventing certain kinds of attacks, the user must be maintaining a fixed
awareness of whatever they are sharing as well as posting and they must also be hugely aware
of the media which they will be actually sharing with some others utilising various links.
Detection of hacking: Detection of attacks of hacking is not at all a very simple task mainly
for all the users who do not possess any kind of information regarding the security of
accounts and attacks of internet. The very first thing which is to be done is that the password
must be kept secret and anytime any users provides the password to someone else, he/she
must be altering the password after they have completed the purpose of access [9]. Systems
must not be possessing any kind of virus and for this one must be downloading all the
programs and anti-virus that must be updated.
Detection of Trojan horse: One must be very much careful whenever any file will be
downloaded online and it is mostly just a specific matter of time before any one becomes the
victim of the Trojan horse [10]. If any file will be coming from any friend of office then one
must be confident enough regarding what the file is about before opening it as various
Trojans will be greatly trying to easily spread up themselves in the list of friend by utilising
any address book of email. One must also be taking care of all kinds of extensions of file that
will be entirely hidden as windows has been observed to be hiding the last file’s extension by
default.
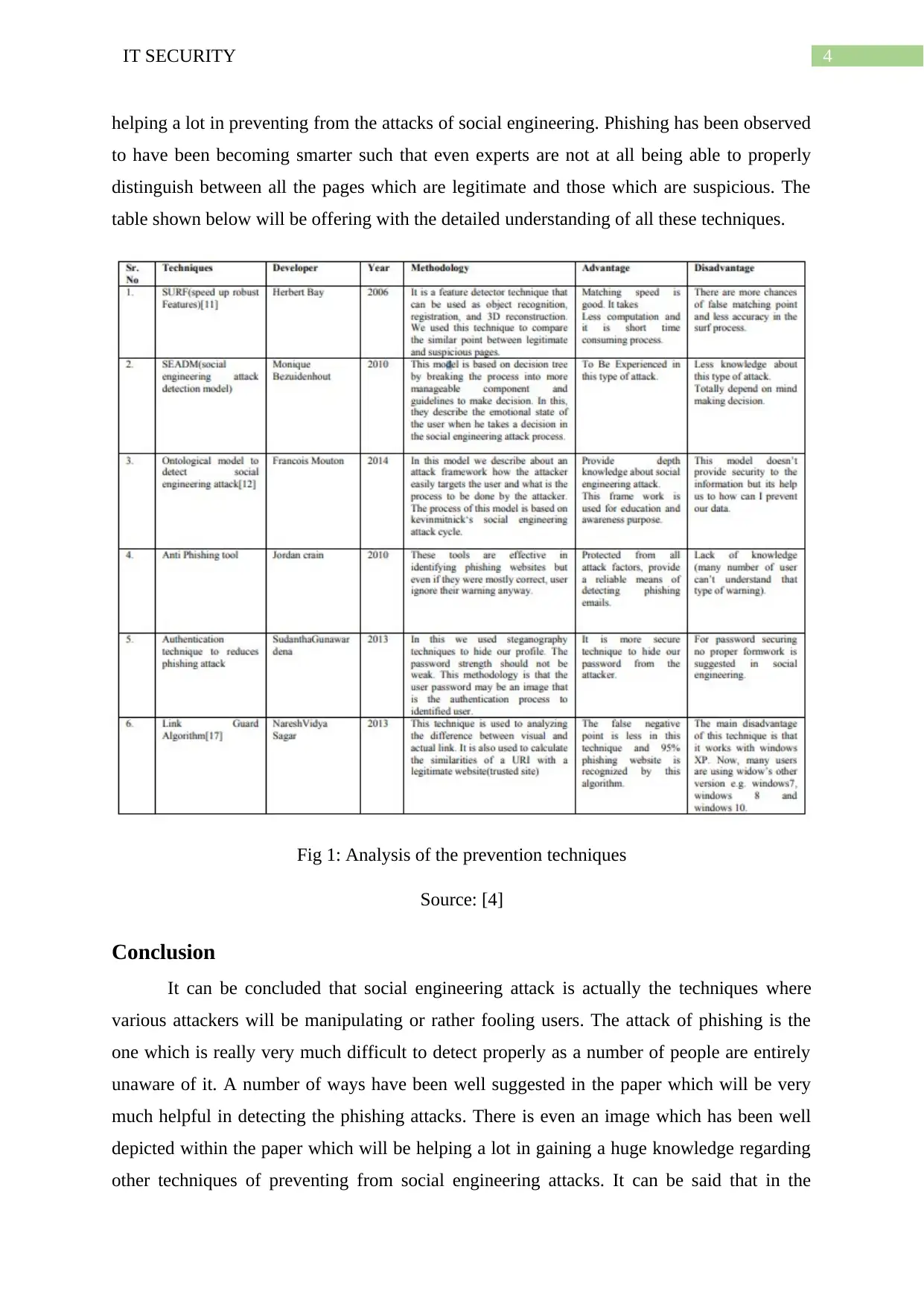
Detection techniques of social engineering attacks
Some technique of detection will be involving SURF, SEAD, Anti Phishing tool,
authentication, link guard algorithm and the ontological model [11]. These are all the various
kinds of techniques of prevention from attacks of phishing and all of these techniques will be
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
4IT SECURITY
helping a lot in preventing from the attacks of social engineering. Phishing has been observed
to have been becoming smarter such that even experts are not at all being able to properly
distinguish between all the pages which are legitimate and those which are suspicious. The
table shown below will be offering with the detailed understanding of all these techniques.
Fig 1: Analysis of the prevention techniques
Source: [4]
Conclusion
It can be concluded that social engineering attack is actually the techniques where
various attackers will be manipulating or rather fooling users. The attack of phishing is the
one which is really very much difficult to detect properly as a number of people are entirely
unaware of it. A number of ways have been well suggested in the paper which will be very
much helpful in detecting the phishing attacks. There is even an image which has been well
depicted within the paper which will be helping a lot in gaining a huge knowledge regarding
other techniques of preventing from social engineering attacks. It can be said that in the
helping a lot in preventing from the attacks of social engineering. Phishing has been observed
to have been becoming smarter such that even experts are not at all being able to properly
distinguish between all the pages which are legitimate and those which are suspicious. The
table shown below will be offering with the detailed understanding of all these techniques.
Fig 1: Analysis of the prevention techniques
Source: [4]
Conclusion
It can be concluded that social engineering attack is actually the techniques where
various attackers will be manipulating or rather fooling users. The attack of phishing is the
one which is really very much difficult to detect properly as a number of people are entirely
unaware of it. A number of ways have been well suggested in the paper which will be very
much helpful in detecting the phishing attacks. There is even an image which has been well
depicted within the paper which will be helping a lot in gaining a huge knowledge regarding
other techniques of preventing from social engineering attacks. It can be said that in the

5IT SECURITY
nearer future, there may be the implementation of various algorithms like detector of surf and
the algorithm of link guard for the versions of windows involving 7, 8, 9 and the other ones
as a number of users are already utilising such versions.
nearer future, there may be the implementation of various algorithms like detector of surf and
the algorithm of link guard for the versions of windows involving 7, 8, 9 and the other ones
as a number of users are already utilising such versions.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

6IT SECURITY
References
[1] J., Chhikara, R., Dahiya, N., Garg & M., Rani, Phishing & anti-phishing techniques: Case
study, International journal of advanced research in computer science and software
engineering, 3(5), 2013.
[2]J.A., Chaudhry, S.A., Chaudhry & R.G. Rittenhouse, Phishing attacks and
defenses. International Journal of Security and Its Applications, 10(1), 247-256,
2016.
[3]N.Y., Conteh & P.J. Schmick, Cybersecurity: risks, vulnerabilities and countermeasures to
prevent social engineering attacks. International Journal of Advanced Computer
Research, 6(23), 31, 2016.
[4]S., Gupta, A., Singhal & A. Kapoor, A literature survey on social engineering attacks:
Phishing attack. In 2016 international conference on computing, communication and
automation (ICCCA) (pp. 537-540). IEEE, 2016.
[5]W. Fan, L., Kevin & R. Rong, Social engineering: Ie based model of human weakness for
attack and defense investigations. IJ Computer Network and Information
Security, 9(1), 1-11, 2017.
[6]K. Jansson & R. von Solms, Phishing for phishing awareness, Behaviour & information
technology, 32(6), 584-593, 2013.
[7]M., Junger, L., Montoya & F.J. Overink, Priming and warnings are not effective to prevent
social engineering attacks, Computers in human behavior, 66, 75-87, 2017.
[8]K., Krombholz, H., Hobel, M., Huber & E. Weippl, Social engineering attacks on the
knowledge worker, In Proceedings of the 6th International Conference on Security of
Information and Networks (pp. 28-35). ACM, 2013.
[9]K., Krombholz, H., Hobel, M., Huber & E. Weippl, Advanced social engineering attacks,
Journal of Information Security and applications, 22, 113-122, 2015.
[10]I. Mann, Hacking the human: social engineering techniques and security
countermeasures. Routledge, 2017.
[11]F., Mouton, M.M., Malan, L., Leenen & H.S. Venter, Social engineering attack
framework. In 2014 Information Security for South Africa (pp. 1-9). IEEE, 2014.
References
[1] J., Chhikara, R., Dahiya, N., Garg & M., Rani, Phishing & anti-phishing techniques: Case
study, International journal of advanced research in computer science and software
engineering, 3(5), 2013.
[2]J.A., Chaudhry, S.A., Chaudhry & R.G. Rittenhouse, Phishing attacks and
defenses. International Journal of Security and Its Applications, 10(1), 247-256,
2016.
[3]N.Y., Conteh & P.J. Schmick, Cybersecurity: risks, vulnerabilities and countermeasures to
prevent social engineering attacks. International Journal of Advanced Computer
Research, 6(23), 31, 2016.
[4]S., Gupta, A., Singhal & A. Kapoor, A literature survey on social engineering attacks:
Phishing attack. In 2016 international conference on computing, communication and
automation (ICCCA) (pp. 537-540). IEEE, 2016.
[5]W. Fan, L., Kevin & R. Rong, Social engineering: Ie based model of human weakness for
attack and defense investigations. IJ Computer Network and Information
Security, 9(1), 1-11, 2017.
[6]K. Jansson & R. von Solms, Phishing for phishing awareness, Behaviour & information
technology, 32(6), 584-593, 2013.
[7]M., Junger, L., Montoya & F.J. Overink, Priming and warnings are not effective to prevent
social engineering attacks, Computers in human behavior, 66, 75-87, 2017.
[8]K., Krombholz, H., Hobel, M., Huber & E. Weippl, Social engineering attacks on the
knowledge worker, In Proceedings of the 6th International Conference on Security of
Information and Networks (pp. 28-35). ACM, 2013.
[9]K., Krombholz, H., Hobel, M., Huber & E. Weippl, Advanced social engineering attacks,
Journal of Information Security and applications, 22, 113-122, 2015.
[10]I. Mann, Hacking the human: social engineering techniques and security
countermeasures. Routledge, 2017.
[11]F., Mouton, M.M., Malan, L., Leenen & H.S. Venter, Social engineering attack
framework. In 2014 Information Security for South Africa (pp. 1-9). IEEE, 2014.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

7IT SECURITY
1 out of 8
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.





