Digital Forensics Assessment 2: ITC597 - Hashing, Case, Research
VerifiedAdded on 2023/03/17
|17
|1491
|95
Report
AI Summary
This report presents a comprehensive analysis of digital forensics, addressing hashing algorithms, a case project, and a research project. The report begins with an exploration of hashing algorithms, specifically focusing on SHA3, and compares it with SHA1 and SHA2, detailing their characteristics and requirements. The second part of the report involves a hands-on case project utilizing OSForensic software to analyze a disk image, extracting and managing digital evidence. Finally, the report concludes with a research project emphasizing the importance of fraud investigation in enhancing organizational performance, highlighting the role of hashing functions in verifying data integrity during digital forensic investigations. The report provides detailed insights into the application of forensic techniques and the importance of data security in digital environments.

Running head: ITC597 - DIGITAL FORENSICS
Assessment 2 - Tasks and Research Project
ITC597 - Digital Forensics
Name of the Student
Name of the University
Author’s Note
Assessment 2 - Tasks and Research Project
ITC597 - Digital Forensics
Name of the Student
Name of the University
Author’s Note
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

1
ITC597 - DIGITAL FORENSICS
Task 1: Hashing Algorithm investigation
1.1 Illustration about Hashing Algorithm
The hashing algorithm operations is considered as one of the procedure of data
security that assists in offering security to the different types of data as well as information
with the help of appropriate technique of encryption. The major important procedure that is
utilized in order to provide proper security to the various targeted information generally helps
in generating a proper algorithm for a specific size of data and this type of algorithm is
mainly known as the hash algorithm (Jin et al., 2014). The term “hashing” generally assists in
converting a large information size into small code of encryption that helps in enhancing the
transaction process of information with very much high security. This is further considered as
one of the important aspect of algorithm when the entire information is properly encoded
with the help of proper hash function that can be accessed or can be modified.
The procedure of encryption is generally started by developing a key point index that
will be required during the time of decoding when the information and data will be decrypted.
It is found that along with that, all the information generally has own keys of decryption and
therefore any random key can be helpful in decrypting any type of random information as
well as data.
1.2 Requirement and characteristics of SHA3 algorithm
Characteristics
SHA3 generally stands for Secure Hash Algorithm within the field of hashing
Algorithm as well as Hash functions. It is found that SHA3 are quite significant in context to
Hashing algorithm so that the information security can be successfully published with the
help of the NIST (Dilli & Reddy, 2016). With the help of proper comparison with the
algorithm, it is analysed that there are a number of similarity between SHA-3 and SHA0-2 in
ITC597 - DIGITAL FORENSICS
Task 1: Hashing Algorithm investigation
1.1 Illustration about Hashing Algorithm
The hashing algorithm operations is considered as one of the procedure of data
security that assists in offering security to the different types of data as well as information
with the help of appropriate technique of encryption. The major important procedure that is
utilized in order to provide proper security to the various targeted information generally helps
in generating a proper algorithm for a specific size of data and this type of algorithm is
mainly known as the hash algorithm (Jin et al., 2014). The term “hashing” generally assists in
converting a large information size into small code of encryption that helps in enhancing the
transaction process of information with very much high security. This is further considered as
one of the important aspect of algorithm when the entire information is properly encoded
with the help of proper hash function that can be accessed or can be modified.
The procedure of encryption is generally started by developing a key point index that
will be required during the time of decoding when the information and data will be decrypted.
It is found that along with that, all the information generally has own keys of decryption and
therefore any random key can be helpful in decrypting any type of random information as
well as data.
1.2 Requirement and characteristics of SHA3 algorithm
Characteristics
SHA3 generally stands for Secure Hash Algorithm within the field of hashing
Algorithm as well as Hash functions. It is found that SHA3 are quite significant in context to
Hashing algorithm so that the information security can be successfully published with the
help of the NIST (Dilli & Reddy, 2016). With the help of proper comparison with the
algorithm, it is analysed that there are a number of similarity between SHA-3 and SHA0-2 in

2
ITC597 - DIGITAL FORENSICS
context to the has security key length. But there are number of challenges or limitation that
are mainly seen within the code structure as there are some limitations that generally exists
between the encrypted structure. The characteristics of the aspects that are generally reflected
above are illustrated below:
It is identified that unidirectional function is one of the important characteristics SHA-
3 algorithm
It is found that the algorithm is helpful in generating encoded algorithm of fixed
length as it only supports 512 bits, 256 bits, 224 bits and 384 bits (Zhu, Zhu & Wang,
2018).
It generally comprises of a number of effective efficiency of the hardware
The efficiency of the software is not appropriate that is mainly utilized
SHA-3 generally needs much more effective technology of data compressing along
with all the expected that are illustrated above.
Requirement
By considering various characteristics as well as features of the hash function it is
found that there are a number of requirements that are generally needed. The requirements
mainly include the addition of both software as well as hardware that further includes various
types of features in order to select proper hardware as well as software. With the custom code
development, it is very much important to properly use the algorithm of hash. In addition to
this, it is found that it generally needs proper structure of the firmware for effectively
executing the algorithm of hash.
1.4 SHA3 comparison with SHA1 and SHA2
No. Secure Hashing Algorithm-1 Secure Hashing
Algorithm-2
Secure Hashing
Algorithm-3
ITC597 - DIGITAL FORENSICS
context to the has security key length. But there are number of challenges or limitation that
are mainly seen within the code structure as there are some limitations that generally exists
between the encrypted structure. The characteristics of the aspects that are generally reflected
above are illustrated below:
It is identified that unidirectional function is one of the important characteristics SHA-
3 algorithm
It is found that the algorithm is helpful in generating encoded algorithm of fixed
length as it only supports 512 bits, 256 bits, 224 bits and 384 bits (Zhu, Zhu & Wang,
2018).
It generally comprises of a number of effective efficiency of the hardware
The efficiency of the software is not appropriate that is mainly utilized
SHA-3 generally needs much more effective technology of data compressing along
with all the expected that are illustrated above.
Requirement
By considering various characteristics as well as features of the hash function it is
found that there are a number of requirements that are generally needed. The requirements
mainly include the addition of both software as well as hardware that further includes various
types of features in order to select proper hardware as well as software. With the custom code
development, it is very much important to properly use the algorithm of hash. In addition to
this, it is found that it generally needs proper structure of the firmware for effectively
executing the algorithm of hash.
1.4 SHA3 comparison with SHA1 and SHA2
No. Secure Hashing Algorithm-1 Secure Hashing
Algorithm-2
Secure Hashing
Algorithm-3
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
3
ITC597 - DIGITAL FORENSICS
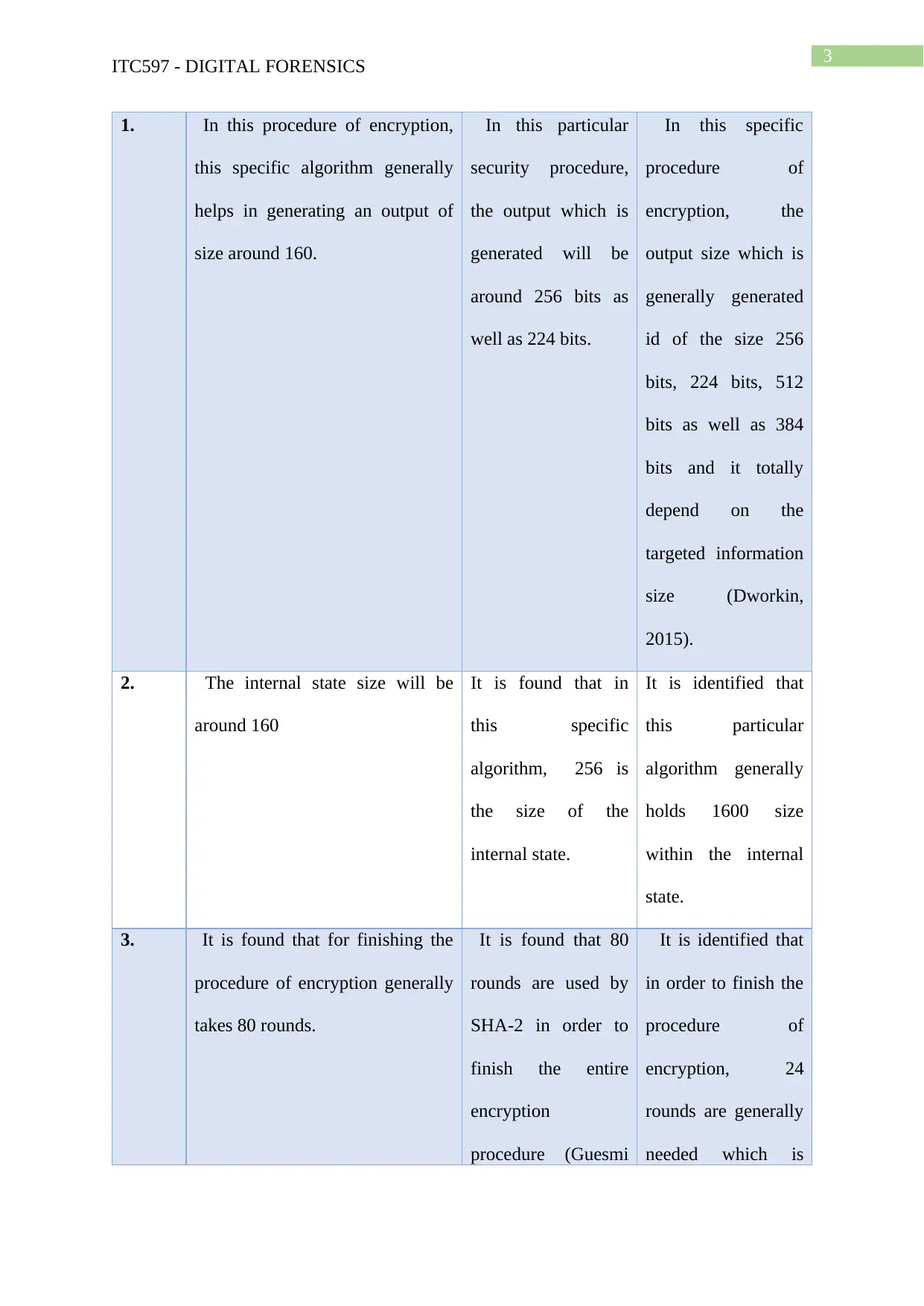
1. In this procedure of encryption,
this specific algorithm generally
helps in generating an output of
size around 160.
In this particular
security procedure,
the output which is
generated will be
around 256 bits as
well as 224 bits.
In this specific
procedure of
encryption, the
output size which is
generally generated
id of the size 256
bits, 224 bits, 512
bits as well as 384
bits and it totally
depend on the
targeted information
size (Dworkin,
2015).
2. The internal state size will be
around 160
It is found that in
this specific
algorithm, 256 is
the size of the
internal state.
It is identified that
this particular
algorithm generally
holds 1600 size
within the internal
state.
3. It is found that for finishing the
procedure of encryption generally
takes 80 rounds.
It is found that 80
rounds are used by
SHA-2 in order to
finish the entire
encryption
procedure (Guesmi
It is identified that
in order to finish the
procedure of
encryption, 24
rounds are generally
needed which is
ITC597 - DIGITAL FORENSICS
1. In this procedure of encryption,
this specific algorithm generally
helps in generating an output of
size around 160.
In this particular
security procedure,
the output which is
generated will be
around 256 bits as
well as 224 bits.
In this specific
procedure of
encryption, the
output size which is
generally generated
id of the size 256
bits, 224 bits, 512
bits as well as 384
bits and it totally
depend on the
targeted information
size (Dworkin,
2015).
2. The internal state size will be
around 160
It is found that in
this specific
algorithm, 256 is
the size of the
internal state.
It is identified that
this particular
algorithm generally
holds 1600 size
within the internal
state.
3. It is found that for finishing the
procedure of encryption generally
takes 80 rounds.
It is found that 80
rounds are used by
SHA-2 in order to
finish the entire
encryption
procedure (Guesmi
It is identified that
in order to finish the
procedure of
encryption, 24
rounds are generally
needed which is
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

4
ITC597 - DIGITAL FORENSICS
et al., 2016). quite high as
compared to other
algorithm and this it
is considered to be
time consuming
(Laxmi &
Chilambuchelvan,
2017).
ITC597 - DIGITAL FORENSICS
et al., 2016). quite high as
compared to other
algorithm and this it
is considered to be
time consuming
(Laxmi &
Chilambuchelvan,
2017).

5
ITC597 - DIGITAL FORENSICS
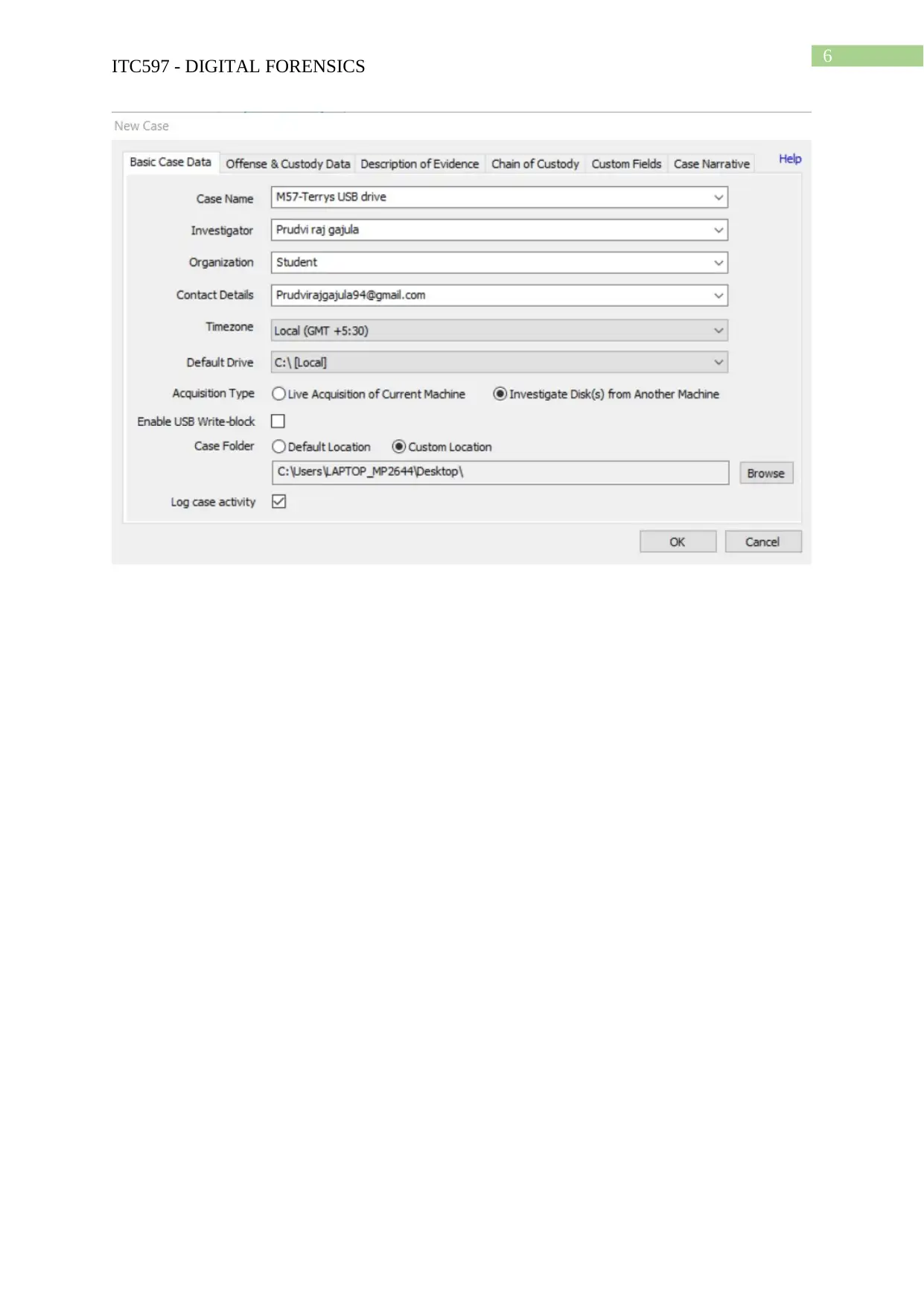
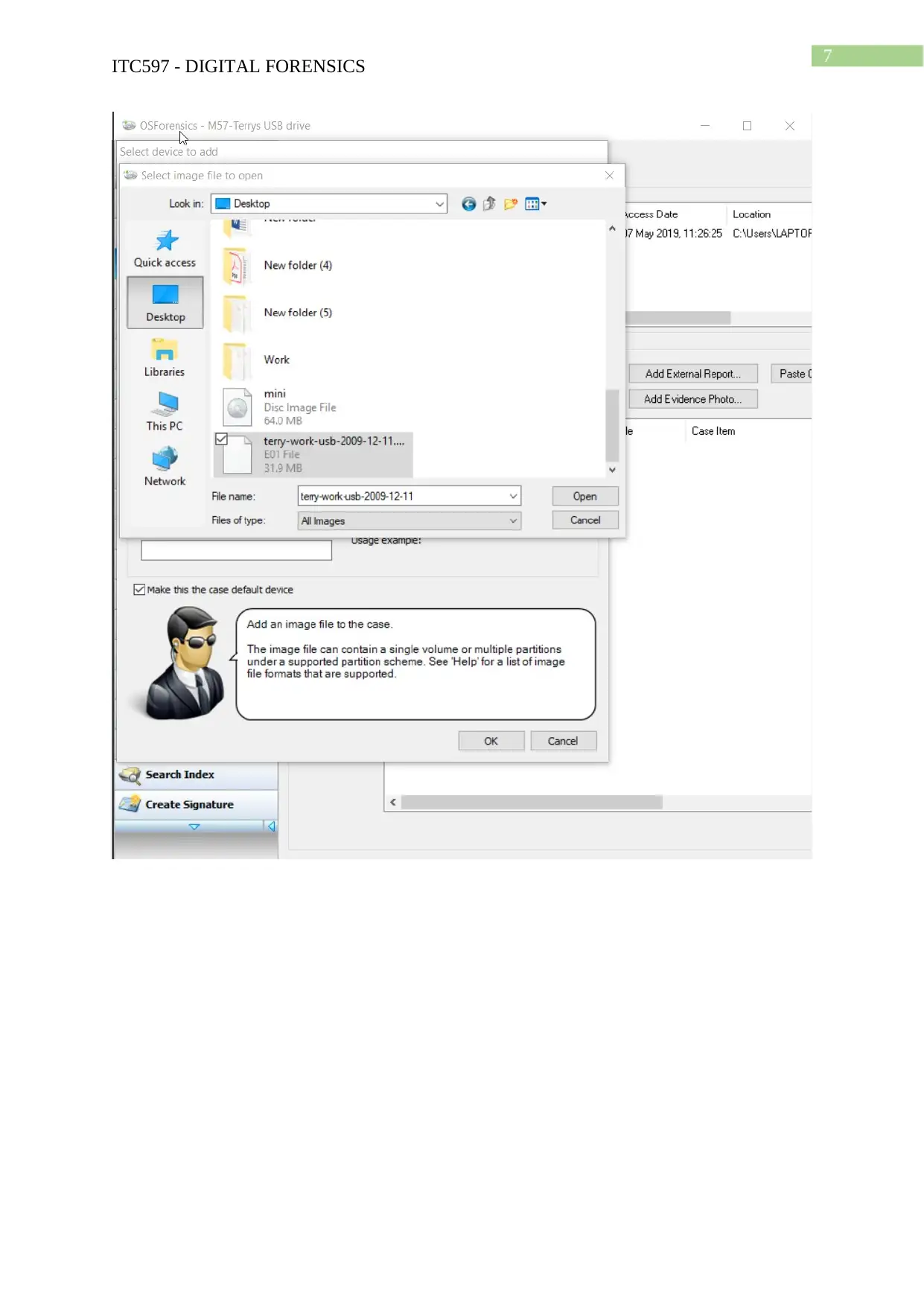
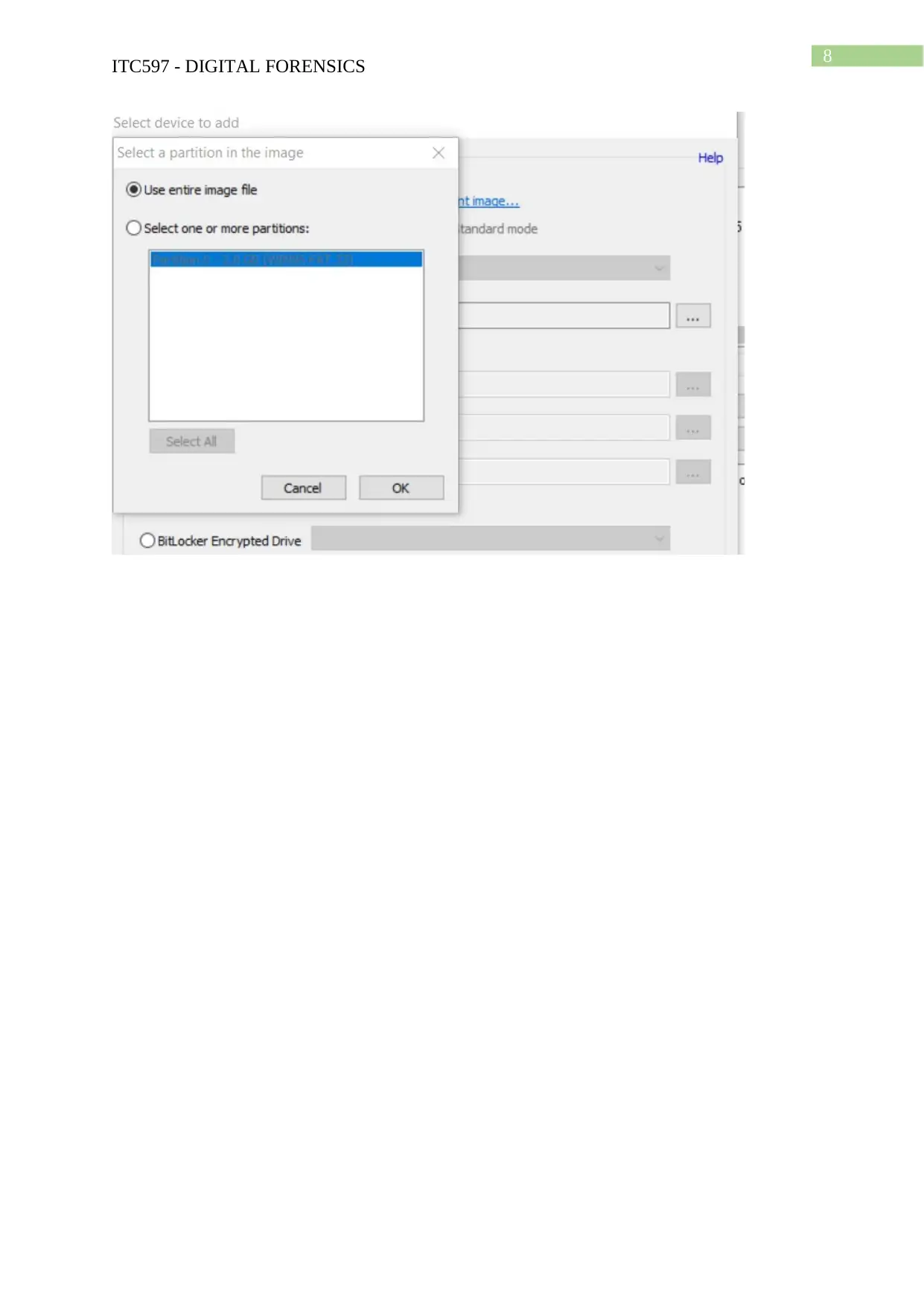
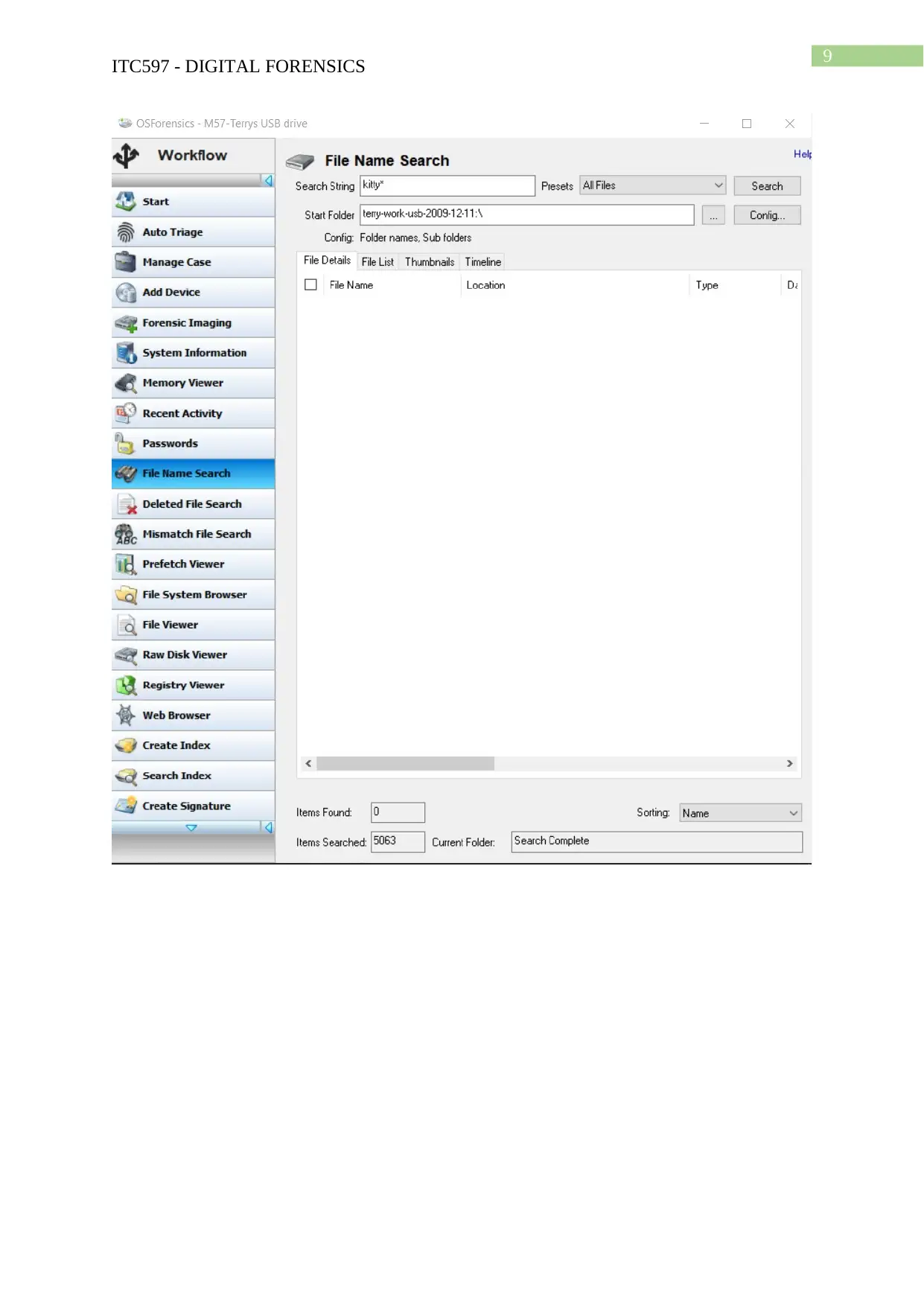
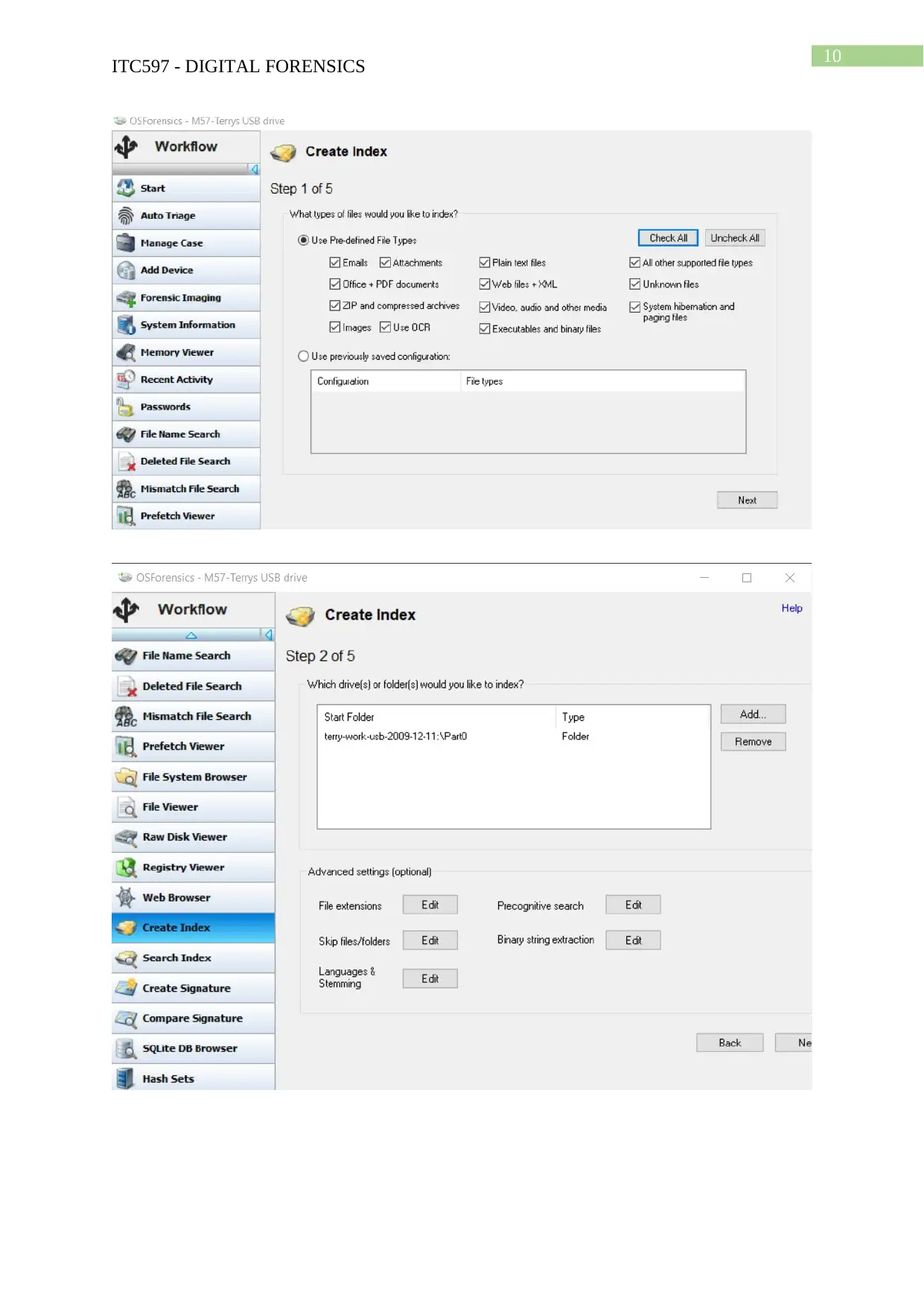
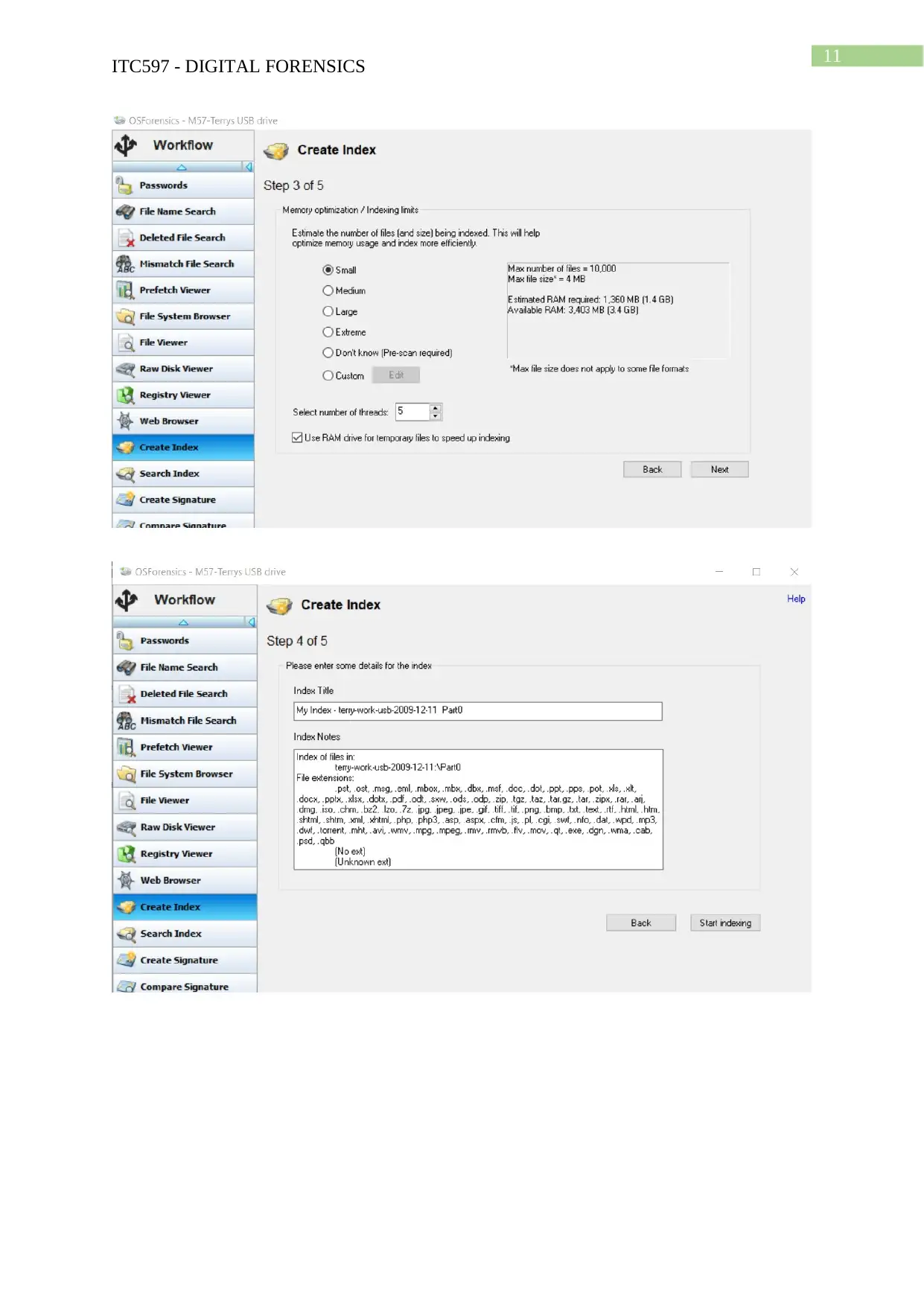
Task 2: Case Project
Hands-on Project 4-3
ITC597 - DIGITAL FORENSICS
Task 2: Case Project
Hands-on Project 4-3
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
6
ITC597 - DIGITAL FORENSICS
ITC597 - DIGITAL FORENSICS
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
7
ITC597 - DIGITAL FORENSICS
ITC597 - DIGITAL FORENSICS
8
ITC597 - DIGITAL FORENSICS
ITC597 - DIGITAL FORENSICS
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
9
ITC597 - DIGITAL FORENSICS
ITC597 - DIGITAL FORENSICS
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
10
ITC597 - DIGITAL FORENSICS
ITC597 - DIGITAL FORENSICS
11
ITC597 - DIGITAL FORENSICS
ITC597 - DIGITAL FORENSICS
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
1 out of 17
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2025 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.





