Understanding Handover in Cellular Networks During Call Continuation
VerifiedAdded on 2020/04/29
|9
|3382
|79
AI Summary
In mobile telecommunications, maintaining an uninterrupted call as a user moves from one geographical area to another is crucial. This process, known as 'handover' or 'handoff', involves transferring the call from one cell's base station (or tower) to another without any noticeable interruption in service. When you're on a call and start moving, your mobile device continuously scans for signals from nearby towers to determine which has the strongest signal at any given moment. As you approach the edge of a cell where the current base station's signal weakens, and that of an adjacent cell strengthens, the network initiates a handover procedure.
This seamless transition requires several steps. First, both the old and new cells must be ready to handle the call simultaneously for a short period. The network then communicates with your mobile device to confirm the availability of resources on the new base station. Next, it performs synchronization processes ensuring that all necessary parameters such as frequency bands, modulation schemes, and encryption keys are aligned between your device and the new tower. Finally, when everything is verified, the call switches to the new cell's network. This complex coordination is managed by sophisticated algorithms within the mobile network infrastructure, ensuring efficient use of resources while maintaining quality communication service for users on the move.

MOBILE DATA NETWORK
Q.1: The following packets are transmitted in a SCTP session. The marked packet is lost. What are
the complete contents of the packet including the SACK chunk from Node 2?
Ans. The data over the network is transmitted in the form of packets. The data is bind and provided
over the network to be transmitted at another end. The packets move accordingly to the specified IP
address. If any packet gets lost, it is due to the transmission error or various other factors i.e.
network congestion, due to packet loss the reliability of network decreased as well as latency and
throughput get affected (Xinogalos, Psannis, and Sifaleras, 2012). It also affects the quality of service.
Here the data is communicated between node 1 and node 2 and thus packets are transmitted over
the network medium. The various packets transmitted from node 1 are:- TSN 105, TSN 106, TSN 107,
TSN 108, TSN 109, TSN 110 out of which acknowledgement is received only for 106 i.e. ACK 106 and
thus it indicates that TSN 106 is received to the node 2. The packet TSN 107 gets lost in the
transmission medium and thus cannot be reached to node 2, the transmission medium might be
filled with various packets or the network traffic might be more while transmitting the TSN 107.
Similarly other packets are transmitted and thus another acknowledgement for the packets is
received and that should be for the last send packet so the sender is aware about whether the data
is reached to the respective authority.
SCTP provides a secure, reliable and message-oriented transmission of data like TCP and UDP. It also
provides congestion control mechanism. It sends message in the form of chunks and thus provides a
sequence number to the streams of data so that the receiver can know the actual sequence of data
transmitted to provide easy implementation and processing of data and provide desired results
(Khan, Othman, and Khan, 2013). The data transmission with the help of SCTP is shown in the figure
below, various request are being made for the transmission of data. Chunks are the additional data
storage information that moves with SCTP protocol to provide the reliability of data.
The data is transmitted from SCTP A to SCTP Z and thus sender sends the actual amount of data that
other party wants and thus starts the communication. The SACK value is transmitted along with the
Q.1: The following packets are transmitted in a SCTP session. The marked packet is lost. What are
the complete contents of the packet including the SACK chunk from Node 2?
Ans. The data over the network is transmitted in the form of packets. The data is bind and provided
over the network to be transmitted at another end. The packets move accordingly to the specified IP
address. If any packet gets lost, it is due to the transmission error or various other factors i.e.
network congestion, due to packet loss the reliability of network decreased as well as latency and
throughput get affected (Xinogalos, Psannis, and Sifaleras, 2012). It also affects the quality of service.
Here the data is communicated between node 1 and node 2 and thus packets are transmitted over
the network medium. The various packets transmitted from node 1 are:- TSN 105, TSN 106, TSN 107,
TSN 108, TSN 109, TSN 110 out of which acknowledgement is received only for 106 i.e. ACK 106 and
thus it indicates that TSN 106 is received to the node 2. The packet TSN 107 gets lost in the
transmission medium and thus cannot be reached to node 2, the transmission medium might be
filled with various packets or the network traffic might be more while transmitting the TSN 107.
Similarly other packets are transmitted and thus another acknowledgement for the packets is
received and that should be for the last send packet so the sender is aware about whether the data
is reached to the respective authority.
SCTP provides a secure, reliable and message-oriented transmission of data like TCP and UDP. It also
provides congestion control mechanism. It sends message in the form of chunks and thus provides a
sequence number to the streams of data so that the receiver can know the actual sequence of data
transmitted to provide easy implementation and processing of data and provide desired results
(Khan, Othman, and Khan, 2013). The data transmission with the help of SCTP is shown in the figure
below, various request are being made for the transmission of data. Chunks are the additional data
storage information that moves with SCTP protocol to provide the reliability of data.
The data is transmitted from SCTP A to SCTP Z and thus sender sends the actual amount of data that
other party wants and thus starts the communication. The SACK value is transmitted along with the
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

actual data and by checking the available resources that are with the SACK at SCTP A the further
SACK and DATA is transmitted that makes data executable. The SACK value can further be taken as
the acknowledgement of the available data files and resources.
Q.2: Consider the topology shown below. Simulate the DSR protocol to establish a path from node
1 to node 10. Find the paths found and the ratio of the number of Route Request packets sent out
in the network.
Ans. Table driven in routing helps to maintain consistent information regarding all the paths that are
available and maintained to reach to a destination. The path is provided from each node to every
other node in the network. The Ad-hoc network is analysed and established with the help of table
driven routing. Whenever a network topology changes the update message is propagated to
maintain simultaneous flow of data at different nodes. Each node maintains multiple routing tables
so that the information is reliable and consistent throughout the network (Khan, Kiah, Khan and
Madani, 2013).
DSDV (Destination Sequenced Distance Vector) is usually suitable for small networks. The criteria
depend on time complexity. The two basic disadvantages with this are that they have respective
amount of data to be operated and they have slow reaction to every failures. Routing protocols are
there to show the available route with low weights to make data packets move efficiently.
Q.3: The Ad Hoc network shown below (including node Q) is currently operating. The network is
running the AODV routing protocol. Show the steps required to route a packet from node N to
node I. In particular, what state is maintained at each node in the network? What changes occur to
the route, and how are these determined if node Q drops out of the network?
Ans. Ad-hoc on demand distance vector routing protocol is basically developed for wireless mobile
data communications. It is free to be operated on mobile Ad-hoc network. The AODV routing
protocol does not affect the global nodes, the local network affects only the local nodes that are to
be available within the area interface. They also make use of sequence number to indicate which
route to be followed. Further, it helps for uncast and multicast communications (Palmer, 2008). The
AODV protocol has expiry date for particular route which expires if that route is not used. All the
routes are maintained but the one that used on regular basis are maintained periodically but the
route that are not in use they get expired and thus are not maintained for operation as they get
destroyed. The unused route is also called as STALE. The route table gives the entry of all the
available routes and thus specifies the lifetime for which particular route is valid (Lorenzo,
Constantinides, Geurts & Gómez, 2007).
SACK and DATA is transmitted that makes data executable. The SACK value can further be taken as
the acknowledgement of the available data files and resources.
Q.2: Consider the topology shown below. Simulate the DSR protocol to establish a path from node
1 to node 10. Find the paths found and the ratio of the number of Route Request packets sent out
in the network.
Ans. Table driven in routing helps to maintain consistent information regarding all the paths that are
available and maintained to reach to a destination. The path is provided from each node to every
other node in the network. The Ad-hoc network is analysed and established with the help of table
driven routing. Whenever a network topology changes the update message is propagated to
maintain simultaneous flow of data at different nodes. Each node maintains multiple routing tables
so that the information is reliable and consistent throughout the network (Khan, Kiah, Khan and
Madani, 2013).
DSDV (Destination Sequenced Distance Vector) is usually suitable for small networks. The criteria
depend on time complexity. The two basic disadvantages with this are that they have respective
amount of data to be operated and they have slow reaction to every failures. Routing protocols are
there to show the available route with low weights to make data packets move efficiently.
Q.3: The Ad Hoc network shown below (including node Q) is currently operating. The network is
running the AODV routing protocol. Show the steps required to route a packet from node N to
node I. In particular, what state is maintained at each node in the network? What changes occur to
the route, and how are these determined if node Q drops out of the network?
Ans. Ad-hoc on demand distance vector routing protocol is basically developed for wireless mobile
data communications. It is free to be operated on mobile Ad-hoc network. The AODV routing
protocol does not affect the global nodes, the local network affects only the local nodes that are to
be available within the area interface. They also make use of sequence number to indicate which
route to be followed. Further, it helps for uncast and multicast communications (Palmer, 2008). The
AODV protocol has expiry date for particular route which expires if that route is not used. All the
routes are maintained but the one that used on regular basis are maintained periodically but the
route that are not in use they get expired and thus are not maintained for operation as they get
destroyed. The unused route is also called as STALE. The route table gives the entry of all the
available routes and thus specifies the lifetime for which particular route is valid (Lorenzo,
Constantinides, Geurts & Gómez, 2007).
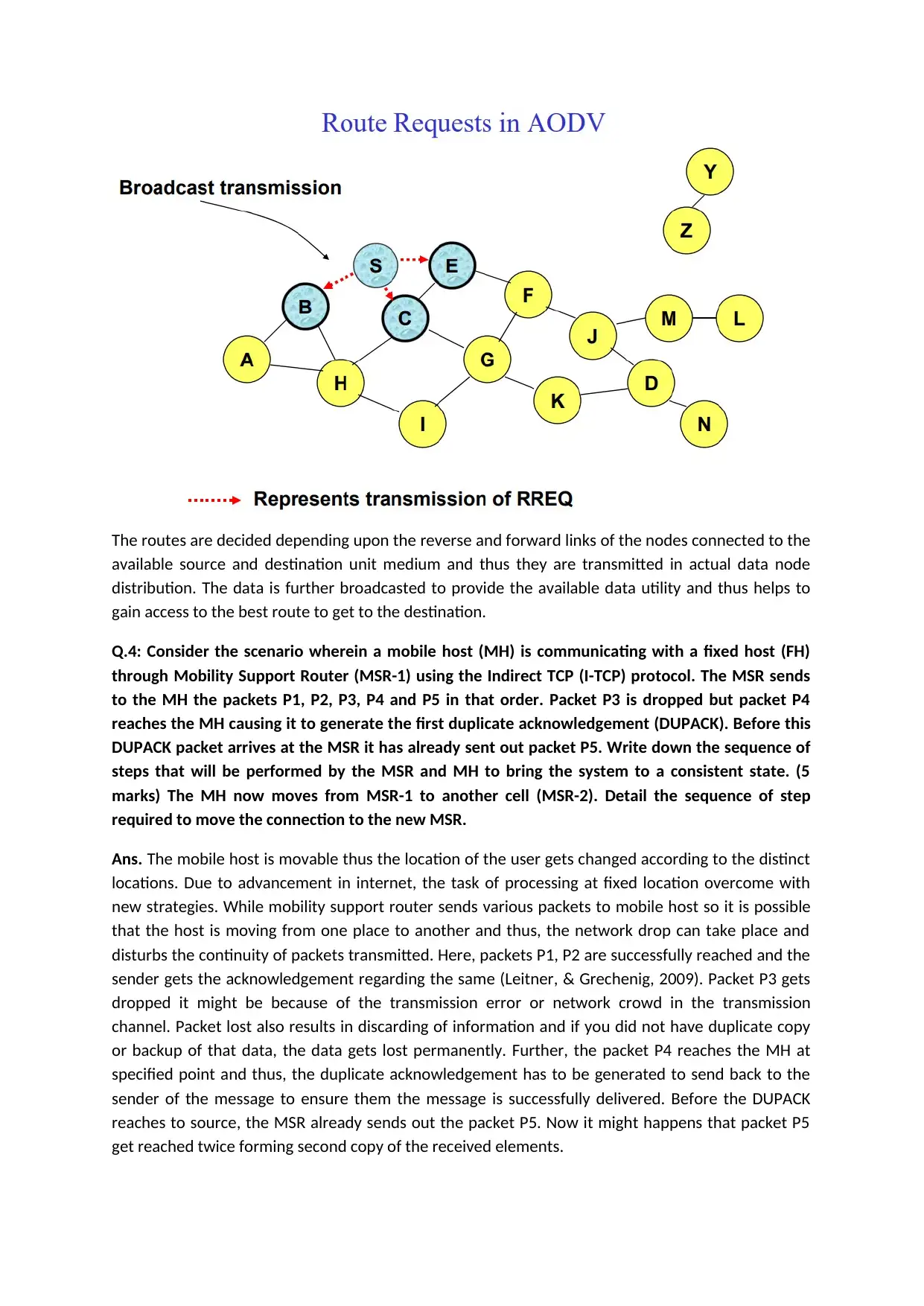
The routes are decided depending upon the reverse and forward links of the nodes connected to the
available source and destination unit medium and thus they are transmitted in actual data node
distribution. The data is further broadcasted to provide the available data utility and thus helps to
gain access to the best route to get to the destination.
Q.4: Consider the scenario wherein a mobile host (MH) is communicating with a fixed host (FH)
through Mobility Support Router (MSR-1) using the Indirect TCP (I-TCP) protocol. The MSR sends
to the MH the packets P1, P2, P3, P4 and P5 in that order. Packet P3 is dropped but packet P4
reaches the MH causing it to generate the first duplicate acknowledgement (DUPACK). Before this
DUPACK packet arrives at the MSR it has already sent out packet P5. Write down the sequence of
steps that will be performed by the MSR and MH to bring the system to a consistent state. (5
marks) The MH now moves from MSR-1 to another cell (MSR-2). Detail the sequence of step
required to move the connection to the new MSR.
Ans. The mobile host is movable thus the location of the user gets changed according to the distinct
locations. Due to advancement in internet, the task of processing at fixed location overcome with
new strategies. While mobility support router sends various packets to mobile host so it is possible
that the host is moving from one place to another and thus, the network drop can take place and
disturbs the continuity of packets transmitted. Here, packets P1, P2 are successfully reached and the
sender gets the acknowledgement regarding the same (Leitner, & Grechenig, 2009). Packet P3 gets
dropped it might be because of the transmission error or network crowd in the transmission
channel. Packet lost also results in discarding of information and if you did not have duplicate copy
or backup of that data, the data gets lost permanently. Further, the packet P4 reaches the MH at
specified point and thus, the duplicate acknowledgement has to be generated to send back to the
sender of the message to ensure them the message is successfully delivered. Before the DUPACK
reaches to source, the MSR already sends out the packet P5. Now it might happens that packet P5
get reached twice forming second copy of the received elements.
available source and destination unit medium and thus they are transmitted in actual data node
distribution. The data is further broadcasted to provide the available data utility and thus helps to
gain access to the best route to get to the destination.
Q.4: Consider the scenario wherein a mobile host (MH) is communicating with a fixed host (FH)
through Mobility Support Router (MSR-1) using the Indirect TCP (I-TCP) protocol. The MSR sends
to the MH the packets P1, P2, P3, P4 and P5 in that order. Packet P3 is dropped but packet P4
reaches the MH causing it to generate the first duplicate acknowledgement (DUPACK). Before this
DUPACK packet arrives at the MSR it has already sent out packet P5. Write down the sequence of
steps that will be performed by the MSR and MH to bring the system to a consistent state. (5
marks) The MH now moves from MSR-1 to another cell (MSR-2). Detail the sequence of step
required to move the connection to the new MSR.
Ans. The mobile host is movable thus the location of the user gets changed according to the distinct
locations. Due to advancement in internet, the task of processing at fixed location overcome with
new strategies. While mobility support router sends various packets to mobile host so it is possible
that the host is moving from one place to another and thus, the network drop can take place and
disturbs the continuity of packets transmitted. Here, packets P1, P2 are successfully reached and the
sender gets the acknowledgement regarding the same (Leitner, & Grechenig, 2009). Packet P3 gets
dropped it might be because of the transmission error or network crowd in the transmission
channel. Packet lost also results in discarding of information and if you did not have duplicate copy
or backup of that data, the data gets lost permanently. Further, the packet P4 reaches the MH at
specified point and thus, the duplicate acknowledgement has to be generated to send back to the
sender of the message to ensure them the message is successfully delivered. Before the DUPACK
reaches to source, the MSR already sends out the packet P5. Now it might happens that packet P5
get reached twice forming second copy of the received elements.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
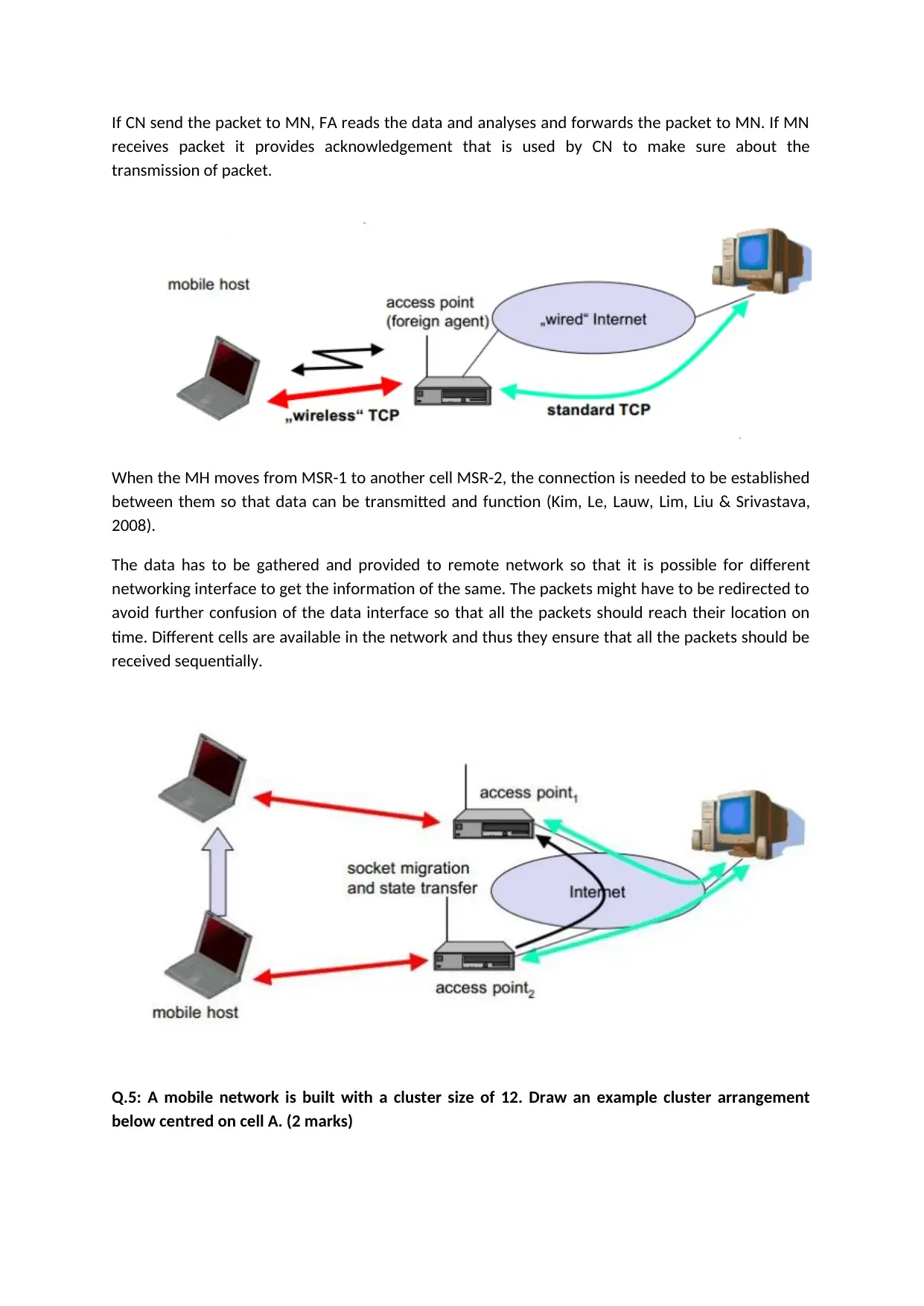
If CN send the packet to MN, FA reads the data and analyses and forwards the packet to MN. If MN
receives packet it provides acknowledgement that is used by CN to make sure about the
transmission of packet.
When the MH moves from MSR-1 to another cell MSR-2, the connection is needed to be established
between them so that data can be transmitted and function (Kim, Le, Lauw, Lim, Liu & Srivastava,
2008).
The data has to be gathered and provided to remote network so that it is possible for different
networking interface to get the information of the same. The packets might have to be redirected to
avoid further confusion of the data interface so that all the packets should reach their location on
time. Different cells are available in the network and thus they ensure that all the packets should be
received sequentially.
Q.5: A mobile network is built with a cluster size of 12. Draw an example cluster arrangement
below centred on cell A. (2 marks)
receives packet it provides acknowledgement that is used by CN to make sure about the
transmission of packet.
When the MH moves from MSR-1 to another cell MSR-2, the connection is needed to be established
between them so that data can be transmitted and function (Kim, Le, Lauw, Lim, Liu & Srivastava,
2008).
The data has to be gathered and provided to remote network so that it is possible for different
networking interface to get the information of the same. The packets might have to be redirected to
avoid further confusion of the data interface so that all the packets should reach their location on
time. Different cells are available in the network and thus they ensure that all the packets should be
received sequentially.
Q.5: A mobile network is built with a cluster size of 12. Draw an example cluster arrangement
below centred on cell A. (2 marks)
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
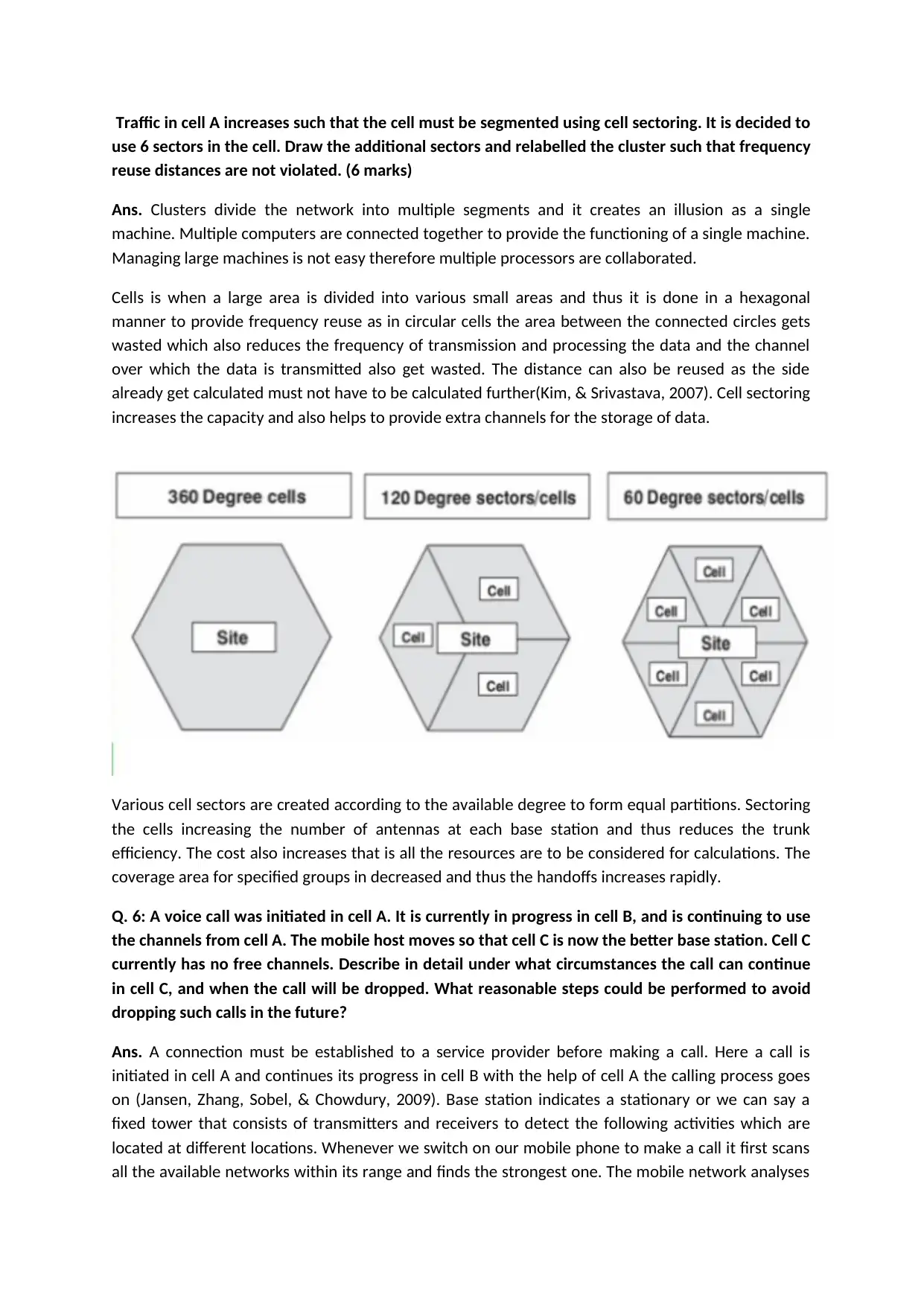
Traffic in cell A increases such that the cell must be segmented using cell sectoring. It is decided to
use 6 sectors in the cell. Draw the additional sectors and relabelled the cluster such that frequency
reuse distances are not violated. (6 marks)
Ans. Clusters divide the network into multiple segments and it creates an illusion as a single
machine. Multiple computers are connected together to provide the functioning of a single machine.
Managing large machines is not easy therefore multiple processors are collaborated.
Cells is when a large area is divided into various small areas and thus it is done in a hexagonal
manner to provide frequency reuse as in circular cells the area between the connected circles gets
wasted which also reduces the frequency of transmission and processing the data and the channel
over which the data is transmitted also get wasted. The distance can also be reused as the side
already get calculated must not have to be calculated further(Kim, & Srivastava, 2007). Cell sectoring
increases the capacity and also helps to provide extra channels for the storage of data.
Various cell sectors are created according to the available degree to form equal partitions. Sectoring
the cells increasing the number of antennas at each base station and thus reduces the trunk
efficiency. The cost also increases that is all the resources are to be considered for calculations. The
coverage area for specified groups in decreased and thus the handoffs increases rapidly.
Q. 6: A voice call was initiated in cell A. It is currently in progress in cell B, and is continuing to use
the channels from cell A. The mobile host moves so that cell C is now the better base station. Cell C
currently has no free channels. Describe in detail under what circumstances the call can continue
in cell C, and when the call will be dropped. What reasonable steps could be performed to avoid
dropping such calls in the future?
Ans. A connection must be established to a service provider before making a call. Here a call is
initiated in cell A and continues its progress in cell B with the help of cell A the calling process goes
on (Jansen, Zhang, Sobel, & Chowdury, 2009). Base station indicates a stationary or we can say a
fixed tower that consists of transmitters and receivers to detect the following activities which are
located at different locations. Whenever we switch on our mobile phone to make a call it first scans
all the available networks within its range and finds the strongest one. The mobile network analyses
use 6 sectors in the cell. Draw the additional sectors and relabelled the cluster such that frequency
reuse distances are not violated. (6 marks)
Ans. Clusters divide the network into multiple segments and it creates an illusion as a single
machine. Multiple computers are connected together to provide the functioning of a single machine.
Managing large machines is not easy therefore multiple processors are collaborated.
Cells is when a large area is divided into various small areas and thus it is done in a hexagonal
manner to provide frequency reuse as in circular cells the area between the connected circles gets
wasted which also reduces the frequency of transmission and processing the data and the channel
over which the data is transmitted also get wasted. The distance can also be reused as the side
already get calculated must not have to be calculated further(Kim, & Srivastava, 2007). Cell sectoring
increases the capacity and also helps to provide extra channels for the storage of data.
Various cell sectors are created according to the available degree to form equal partitions. Sectoring
the cells increasing the number of antennas at each base station and thus reduces the trunk
efficiency. The cost also increases that is all the resources are to be considered for calculations. The
coverage area for specified groups in decreased and thus the handoffs increases rapidly.
Q. 6: A voice call was initiated in cell A. It is currently in progress in cell B, and is continuing to use
the channels from cell A. The mobile host moves so that cell C is now the better base station. Cell C
currently has no free channels. Describe in detail under what circumstances the call can continue
in cell C, and when the call will be dropped. What reasonable steps could be performed to avoid
dropping such calls in the future?
Ans. A connection must be established to a service provider before making a call. Here a call is
initiated in cell A and continues its progress in cell B with the help of cell A the calling process goes
on (Jansen, Zhang, Sobel, & Chowdury, 2009). Base station indicates a stationary or we can say a
fixed tower that consists of transmitters and receivers to detect the following activities which are
located at different locations. Whenever we switch on our mobile phone to make a call it first scans
all the available networks within its range and finds the strongest one. The mobile network analyses

the same strong channel and it keeps on monitoring until the network gets dropped to its minimum
level before the network actually starts to reboot (Fisher, 2010). Every mobile network do this
process to get the knowledge of all available strong networks and it is efficient to use the one that
maintains its characteristics for a long duration of time. We can also analyse the signal level as it is
displayed on our phone screen and thus get to know which network is better to use.
The phone call we make is converted into electrical signals, which is further transmitted in the form
of radio waves and before reaching the receiver end it is again converted into your sound to reach
your friend. For example: the experiment of making phone call with the help of tin cans and string,
we can say like a guy C holding that and let us consider that he is the cell tower. When A makes a call
to B, the cell tower C analyses and connects both according to the requirements specified(Duan, Gu,
& Whinston, 2008).
Following process takes place when a call is made: At first, a call initiation request along with Mobile
Identification Number (MIN), Electronic Serial Number (ESN) and the dialled telephone number is
sent on the reverse control channel. All this data is received by the base station and further it is sent
to the Mobile Switching Control (MSC). The MSC helps to check the validity of the request by
checking the MIN with the stored data in the database. If it matched, the connection is established
by a third party with the help of Public Switched Telephone Network (PSTN). The MSC plays an
important part to manage the communication, as it helps to maintain the power transmitted by the
mobile when it moves in and out of the network area. The MSC also makes request to base station
to transfer the mobile phone to the unused channel so that the communication can be started
without the call drop. All the requests are made to the base station so that the transmitter and
receiver are aware of what data is actually operating over the connected stations. If a mobile phone
that contains a call moves from one base station to another base station that process is called as
handoff. Further, if a call is made and the executable voice channel is not free then we get the
message like network busy and this takes place when large number of calls are made within the
coverage area of single base station. It is obvious that if single base station is used for operating of
multiple call requests then call dropping will take place more frequently and thus there results no
reliability and accuracy of call made (Berger, & Heath, 2007).
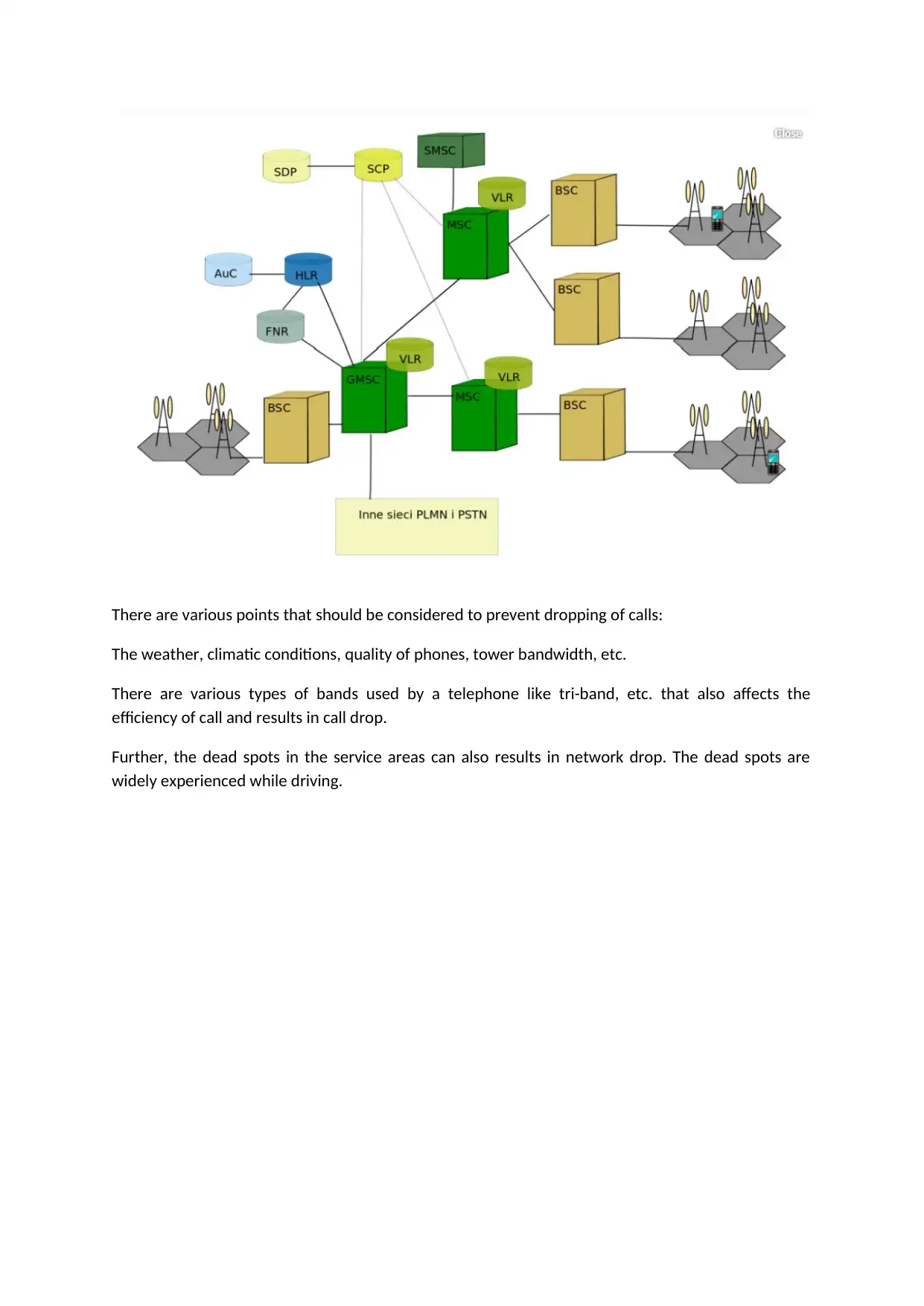
In figure it is represented that all the mobile devices are connected to BTS (Antenna). BTS is
connected to a switching system called BSC. BSC is connected to main switching system called MSC.
MSC has its own VLR (Visitor Location Register) whenever we move from one place to another VLR
keeps the track of all the places we visit and thus it is a temporary storage for the network
information. There is also a main database that is called as HLR (Home Location Register) where all
the information and documents are stored that we provide before we buy a SIM card. Thus, VLR
takes all the data from HLR whenever we roam from one state to another or anywhere in the
network area.
level before the network actually starts to reboot (Fisher, 2010). Every mobile network do this
process to get the knowledge of all available strong networks and it is efficient to use the one that
maintains its characteristics for a long duration of time. We can also analyse the signal level as it is
displayed on our phone screen and thus get to know which network is better to use.
The phone call we make is converted into electrical signals, which is further transmitted in the form
of radio waves and before reaching the receiver end it is again converted into your sound to reach
your friend. For example: the experiment of making phone call with the help of tin cans and string,
we can say like a guy C holding that and let us consider that he is the cell tower. When A makes a call
to B, the cell tower C analyses and connects both according to the requirements specified(Duan, Gu,
& Whinston, 2008).
Following process takes place when a call is made: At first, a call initiation request along with Mobile
Identification Number (MIN), Electronic Serial Number (ESN) and the dialled telephone number is
sent on the reverse control channel. All this data is received by the base station and further it is sent
to the Mobile Switching Control (MSC). The MSC helps to check the validity of the request by
checking the MIN with the stored data in the database. If it matched, the connection is established
by a third party with the help of Public Switched Telephone Network (PSTN). The MSC plays an
important part to manage the communication, as it helps to maintain the power transmitted by the
mobile when it moves in and out of the network area. The MSC also makes request to base station
to transfer the mobile phone to the unused channel so that the communication can be started
without the call drop. All the requests are made to the base station so that the transmitter and
receiver are aware of what data is actually operating over the connected stations. If a mobile phone
that contains a call moves from one base station to another base station that process is called as
handoff. Further, if a call is made and the executable voice channel is not free then we get the
message like network busy and this takes place when large number of calls are made within the
coverage area of single base station. It is obvious that if single base station is used for operating of
multiple call requests then call dropping will take place more frequently and thus there results no
reliability and accuracy of call made (Berger, & Heath, 2007).
In figure it is represented that all the mobile devices are connected to BTS (Antenna). BTS is
connected to a switching system called BSC. BSC is connected to main switching system called MSC.
MSC has its own VLR (Visitor Location Register) whenever we move from one place to another VLR
keeps the track of all the places we visit and thus it is a temporary storage for the network
information. There is also a main database that is called as HLR (Home Location Register) where all
the information and documents are stored that we provide before we buy a SIM card. Thus, VLR
takes all the data from HLR whenever we roam from one state to another or anywhere in the
network area.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
There are various points that should be considered to prevent dropping of calls:
The weather, climatic conditions, quality of phones, tower bandwidth, etc.
There are various types of bands used by a telephone like tri-band, etc. that also affects the
efficiency of call and results in call drop.
Further, the dead spots in the service areas can also results in network drop. The dead spots are
widely experienced while driving.
The weather, climatic conditions, quality of phones, tower bandwidth, etc.
There are various types of bands used by a telephone like tri-band, etc. that also affects the
efficiency of call and results in call drop.
Further, the dead spots in the service areas can also results in network drop. The dead spots are
widely experienced while driving.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

Reference
Berger, J. & Heath C., 2007. Where Consumers Diverge from Others: Identity Signalling and Product
Domains. Journal of Consumer Research: An Interdisciplinary Quarterly, 34(2), 121-134.
Duan, W., Gu, B., & Whinston, A. B., 2008. Do online reviews matter? - An empirical investigation of
panel data. Decis. Support Syst., 45(4), 1007-1016.
Fisher, S., 2010. Social Commerce Camp - Killer Social Commerce Experience. Retrieved from
http://www.slideshare.net/stevenfisher/soc ial-commerce-camp-killer-socialcommerce-
experience
Jansen, B. J., Zhang, M., Sobel, K., & Chowdury, A., 2009. Micro-blogging as online word of mouth
branding. In Proceedings of the 27th international conference extended abstracts on Human
factors in computing systems (pp. 3859- 3864). Boston, MA, USA: ACM.
doi:10.1145/1520340.1520584
Khan, A.N., Kiah, M. M., Khan, S. U. and Madani, S. A., 2013, "Towards secure mobile cloud
computing: A survey," Future Generation Computer Systems, vol. 29, issue 5, pp. 1278–
1299.
Khan, M. Othman, S. M., and Khan, S., 2013, "A survey of mobile cloud computing application
models," IEEE Communications Surveys & Tutorials, issue 99.
Kim, Y. A., & Srivastava, J., 2007. Impact of social influence in e-commerce decision making. In
Proceedings of the ninth international conference on Electronic commerce (pp. 293-302).
Minneapolis, MN, USA: ACM. doi:10.1145/1282100.1282157
Kim, Y. A., Le, M., Lauw, H. W., Lim, E., Liu, H., & Srivastava, J., 2008. Building a web of trust without
explicit trust ratings. In ICDE 2008. Presented at the Workshop on Data Engineering for
Blogs, Social Medial and Web 2.0, Mexico.
Leitner, P., & Grechenig, T., 2008. Collaborative Shopping Networks: Sharing the Wisdom of Crowds
in E-Commerce Environments. In BLED 2008 (Vol. 21, p. 321).
Leitner, P., & Grechenig, T., 2009. Smart shopping spaces: connecting merchants and consumers by
innovative online marketplaces. Presented at the IADIS International Conference e-
Commerce.
Berger, J. & Heath C., 2007. Where Consumers Diverge from Others: Identity Signalling and Product
Domains. Journal of Consumer Research: An Interdisciplinary Quarterly, 34(2), 121-134.
Duan, W., Gu, B., & Whinston, A. B., 2008. Do online reviews matter? - An empirical investigation of
panel data. Decis. Support Syst., 45(4), 1007-1016.
Fisher, S., 2010. Social Commerce Camp - Killer Social Commerce Experience. Retrieved from
http://www.slideshare.net/stevenfisher/soc ial-commerce-camp-killer-socialcommerce-
experience
Jansen, B. J., Zhang, M., Sobel, K., & Chowdury, A., 2009. Micro-blogging as online word of mouth
branding. In Proceedings of the 27th international conference extended abstracts on Human
factors in computing systems (pp. 3859- 3864). Boston, MA, USA: ACM.
doi:10.1145/1520340.1520584
Khan, A.N., Kiah, M. M., Khan, S. U. and Madani, S. A., 2013, "Towards secure mobile cloud
computing: A survey," Future Generation Computer Systems, vol. 29, issue 5, pp. 1278–
1299.
Khan, M. Othman, S. M., and Khan, S., 2013, "A survey of mobile cloud computing application
models," IEEE Communications Surveys & Tutorials, issue 99.
Kim, Y. A., & Srivastava, J., 2007. Impact of social influence in e-commerce decision making. In
Proceedings of the ninth international conference on Electronic commerce (pp. 293-302).
Minneapolis, MN, USA: ACM. doi:10.1145/1282100.1282157
Kim, Y. A., Le, M., Lauw, H. W., Lim, E., Liu, H., & Srivastava, J., 2008. Building a web of trust without
explicit trust ratings. In ICDE 2008. Presented at the Workshop on Data Engineering for
Blogs, Social Medial and Web 2.0, Mexico.
Leitner, P., & Grechenig, T., 2008. Collaborative Shopping Networks: Sharing the Wisdom of Crowds
in E-Commerce Environments. In BLED 2008 (Vol. 21, p. 321).
Leitner, P., & Grechenig, T., 2009. Smart shopping spaces: connecting merchants and consumers by
innovative online marketplaces. Presented at the IADIS International Conference e-
Commerce.

Lorenzo, C., Constantinides, E., Geurts, P., & Gómez, M., 2007. Impact of Web Experience on e-
Consumer Responses. In E-Commerce and Web Technologies (pp. 191-200). Retrieved from
http://dx.doi.org/10.1007/978-3-540- 74563-1_19
Palmer, M., 2008. Social shoppers find goods well recommended. Financial Times. Retrieved March
5, 2010, from http://www.ft.com/cms/s/0/349ca1bac7c3-11dc-a0b4- 0000779fd2ac.html?
nclick_check=1
Stephen, A. T., & Toubia, O., 2009. Deriving Value from Social Commerce Networks. SSRN eLibrary.
Retrieved from http://papers.ssrn.com/sol3/papers.cfm?a bstract_id=1150995
Xinogalos, S., Psannis, K.E and Sifaleras, A., 2012, "Recent advances delivered by HTML 5 in mobile
cloud computing applications: a survey," in Proc. the Fifth Balkan Conference in Informatics,
pp. 199-204
Consumer Responses. In E-Commerce and Web Technologies (pp. 191-200). Retrieved from
http://dx.doi.org/10.1007/978-3-540- 74563-1_19
Palmer, M., 2008. Social shoppers find goods well recommended. Financial Times. Retrieved March
5, 2010, from http://www.ft.com/cms/s/0/349ca1bac7c3-11dc-a0b4- 0000779fd2ac.html?
nclick_check=1
Stephen, A. T., & Toubia, O., 2009. Deriving Value from Social Commerce Networks. SSRN eLibrary.
Retrieved from http://papers.ssrn.com/sol3/papers.cfm?a bstract_id=1150995
Xinogalos, S., Psannis, K.E and Sifaleras, A., 2012, "Recent advances delivered by HTML 5 in mobile
cloud computing applications: a survey," in Proc. the Fifth Balkan Conference in Informatics,
pp. 199-204
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
1 out of 9
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.





