ITECH2300: Mobile Network & Wireless Communication Assignment 2022
VerifiedAdded on 2022/09/21
|15
|2980
|20
Assignment
AI Summary
Contribute Materials
Your contribution can guide someone’s learning journey. Share your
documents today.

Page 1 of 4
ITECH2300
Mobile Network & Wireless Communication Assignment 1 – Semester
2 2019
Submission Guidelines
Deadline: Sunday 1 September, 2019 (11:55pm midnight on Moodle)
Submission format: PDF only. You can use any freely available pdf converter to make pdf file
from editable one.
Submission platform: upload via Moodle
Files to submit:
You need to submit only one file: Assign1(student_id).pdf
Create a single file that contain answer to all questions
No late submissions unless SPECIAL CONSIDERAION IS PROCESSED
Plagiarism: It is an academic requirement that your submitted work be original. Zero marks will be
awarded for the whole submission if there is any evidence of copying, collaboration, pasting from
websites, or copying from textbooks. –Plagiarism policy applies to all assessments
Marks
This assignment is worth 15% of the total marks.
The assignment is marked out of 45 nominal marks.
For example, if you obtain 30 marks for this assignment, it will contribute
(30/45)*15=10 marks to you final grade.
ITECH2300
Mobile Network & Wireless Communication Assignment 1 – Semester
2 2019
Submission Guidelines
Deadline: Sunday 1 September, 2019 (11:55pm midnight on Moodle)
Submission format: PDF only. You can use any freely available pdf converter to make pdf file
from editable one.
Submission platform: upload via Moodle
Files to submit:
You need to submit only one file: Assign1(student_id).pdf
Create a single file that contain answer to all questions
No late submissions unless SPECIAL CONSIDERAION IS PROCESSED
Plagiarism: It is an academic requirement that your submitted work be original. Zero marks will be
awarded for the whole submission if there is any evidence of copying, collaboration, pasting from
websites, or copying from textbooks. –Plagiarism policy applies to all assessments
Marks
This assignment is worth 15% of the total marks.
The assignment is marked out of 45 nominal marks.
For example, if you obtain 30 marks for this assignment, it will contribute
(30/45)*15=10 marks to you final grade.
Secure Best Marks with AI Grader
Need help grading? Try our AI Grader for instant feedback on your assignments.

Page 2 of 4
Assignment Questions
Part –A
Q1. Given the bit pattern 11010011, encode this data using ASK, FSK and PSK (i.e., draw the
waveform that represents each ‘1’ or ‘0’ in a neat diagram). In the diagram, label the amplitude
values used in ASK, frequency values used in BFSK (binary FSK because there are only 0 and 1
in the data), as well as the phase values used in BPSK (binary PSK).
(Hint: see slides on ASK, FSK & PSK in Lecture 5).
Source code:
clc;
f=input ('enter frequency: ');
b= [ 1 1 0 1 0 0 1 1];
n= length(b);
t = 0 : 0.01 : n;
x =1 : 1 : (n+1)*100 ;
for i = 1 : n
for j= i : 0.01 : i+1
bw(x(i*100:(i+1)*100))= b(i);
end
end
pulse=bw(100:end);
carrier= sin(2 * pi* f* t);
modulated= pulse.* carrier;
subplot(3,1,1);
plot(t,pulse);
title 'digital pulse'
xlabel 'time-->', ylabel 'amplitude-->'
grid on; axis([0 n -2 +2])
subplot(3,1,3);
plot(t,modulated);
Assignment Questions
Part –A
Q1. Given the bit pattern 11010011, encode this data using ASK, FSK and PSK (i.e., draw the
waveform that represents each ‘1’ or ‘0’ in a neat diagram). In the diagram, label the amplitude
values used in ASK, frequency values used in BFSK (binary FSK because there are only 0 and 1
in the data), as well as the phase values used in BPSK (binary PSK).
(Hint: see slides on ASK, FSK & PSK in Lecture 5).
Source code:
clc;
f=input ('enter frequency: ');
b= [ 1 1 0 1 0 0 1 1];
n= length(b);
t = 0 : 0.01 : n;
x =1 : 1 : (n+1)*100 ;
for i = 1 : n
for j= i : 0.01 : i+1
bw(x(i*100:(i+1)*100))= b(i);
end
end
pulse=bw(100:end);
carrier= sin(2 * pi* f* t);
modulated= pulse.* carrier;
subplot(3,1,1);
plot(t,pulse);
title 'digital pulse'
xlabel 'time-->', ylabel 'amplitude-->'
grid on; axis([0 n -2 +2])
subplot(3,1,3);
plot(t,modulated);
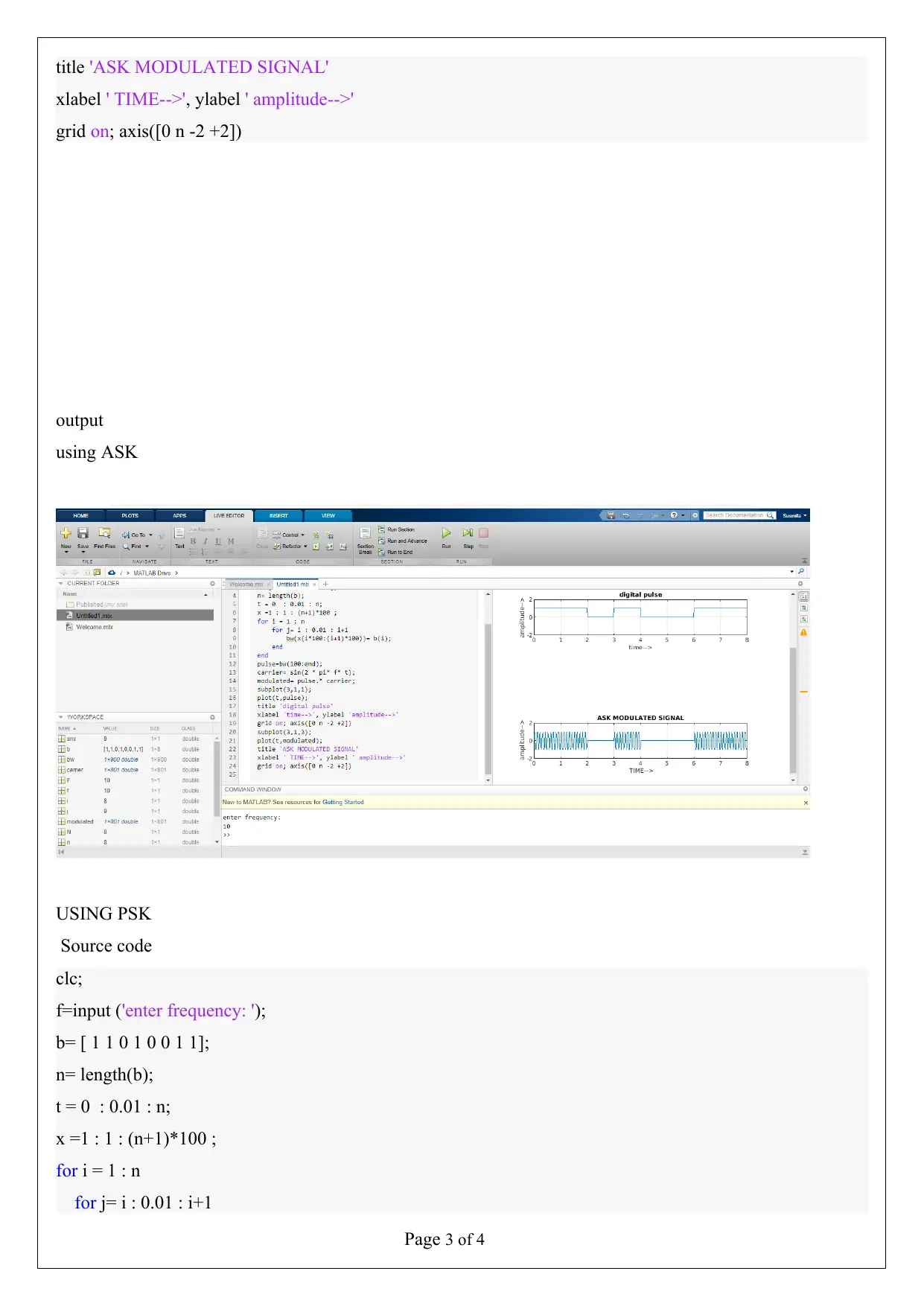
Page 3 of 4
title 'ASK MODULATED SIGNAL'
xlabel ' TIME-->', ylabel ' amplitude-->'
grid on; axis([0 n -2 +2])
output
using ASK
USING PSK
Source code
clc;
f=input ('enter frequency: ');
b= [ 1 1 0 1 0 0 1 1];
n= length(b);
t = 0 : 0.01 : n;
x =1 : 1 : (n+1)*100 ;
for i = 1 : n
for j= i : 0.01 : i+1
title 'ASK MODULATED SIGNAL'
xlabel ' TIME-->', ylabel ' amplitude-->'
grid on; axis([0 n -2 +2])
output
using ASK
USING PSK
Source code
clc;
f=input ('enter frequency: ');
b= [ 1 1 0 1 0 0 1 1];
n= length(b);
t = 0 : 0.01 : n;
x =1 : 1 : (n+1)*100 ;
for i = 1 : n
for j= i : 0.01 : i+1
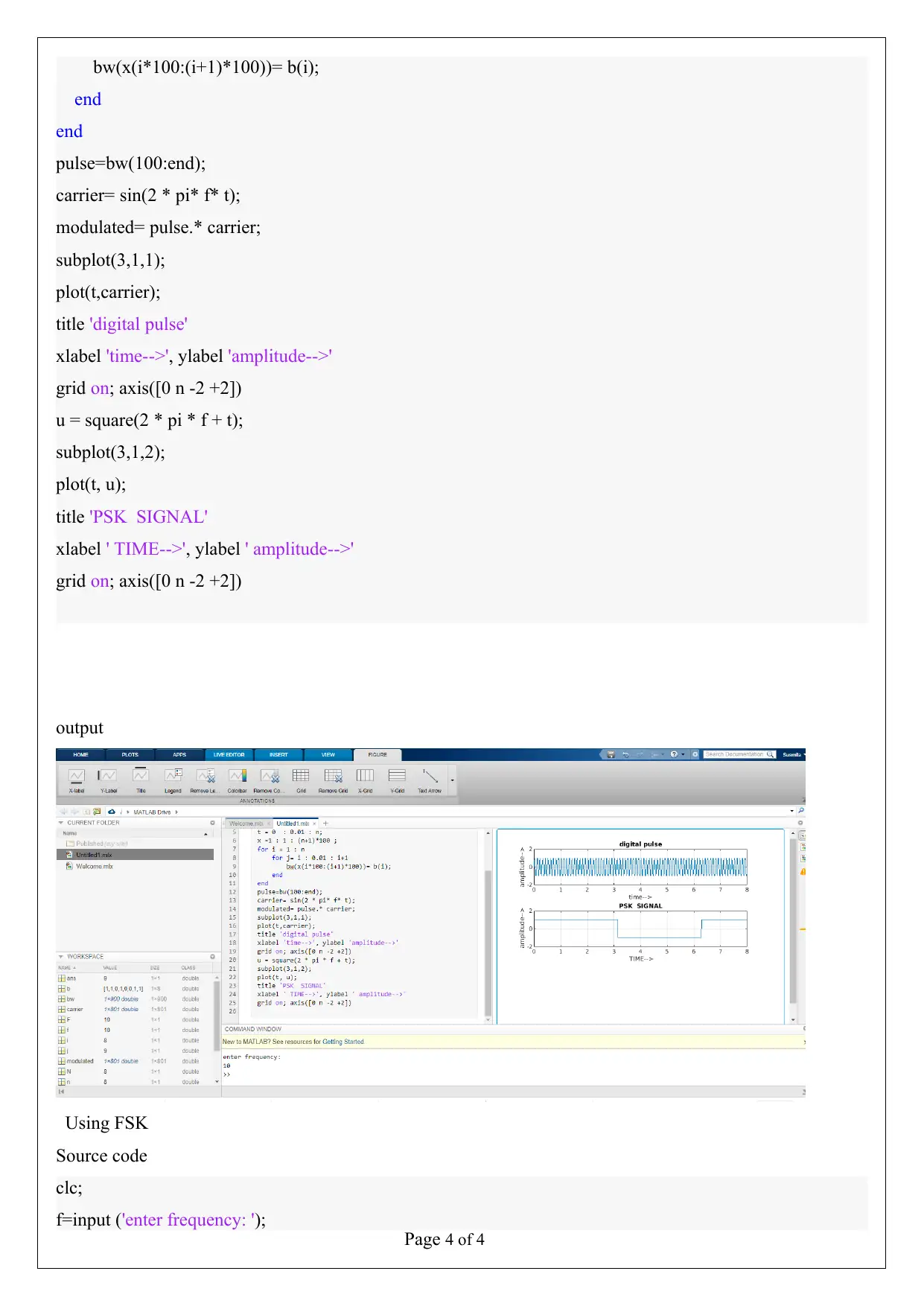
Page 4 of 4
bw(x(i*100:(i+1)*100))= b(i);
end
end
pulse=bw(100:end);
carrier= sin(2 * pi* f* t);
modulated= pulse.* carrier;
subplot(3,1,1);
plot(t,carrier);
title 'digital pulse'
xlabel 'time-->', ylabel 'amplitude-->'
grid on; axis([0 n -2 +2])
u = square(2 * pi * f + t);
subplot(3,1,2);
plot(t, u);
title 'PSK SIGNAL'
xlabel ' TIME-->', ylabel ' amplitude-->'
grid on; axis([0 n -2 +2])
output
Using FSK
Source code
clc;
f=input ('enter frequency: ');
bw(x(i*100:(i+1)*100))= b(i);
end
end
pulse=bw(100:end);
carrier= sin(2 * pi* f* t);
modulated= pulse.* carrier;
subplot(3,1,1);
plot(t,carrier);
title 'digital pulse'
xlabel 'time-->', ylabel 'amplitude-->'
grid on; axis([0 n -2 +2])
u = square(2 * pi * f + t);
subplot(3,1,2);
plot(t, u);
title 'PSK SIGNAL'
xlabel ' TIME-->', ylabel ' amplitude-->'
grid on; axis([0 n -2 +2])
output
Using FSK
Source code
clc;
f=input ('enter frequency: ');
Secure Best Marks with AI Grader
Need help grading? Try our AI Grader for instant feedback on your assignments.
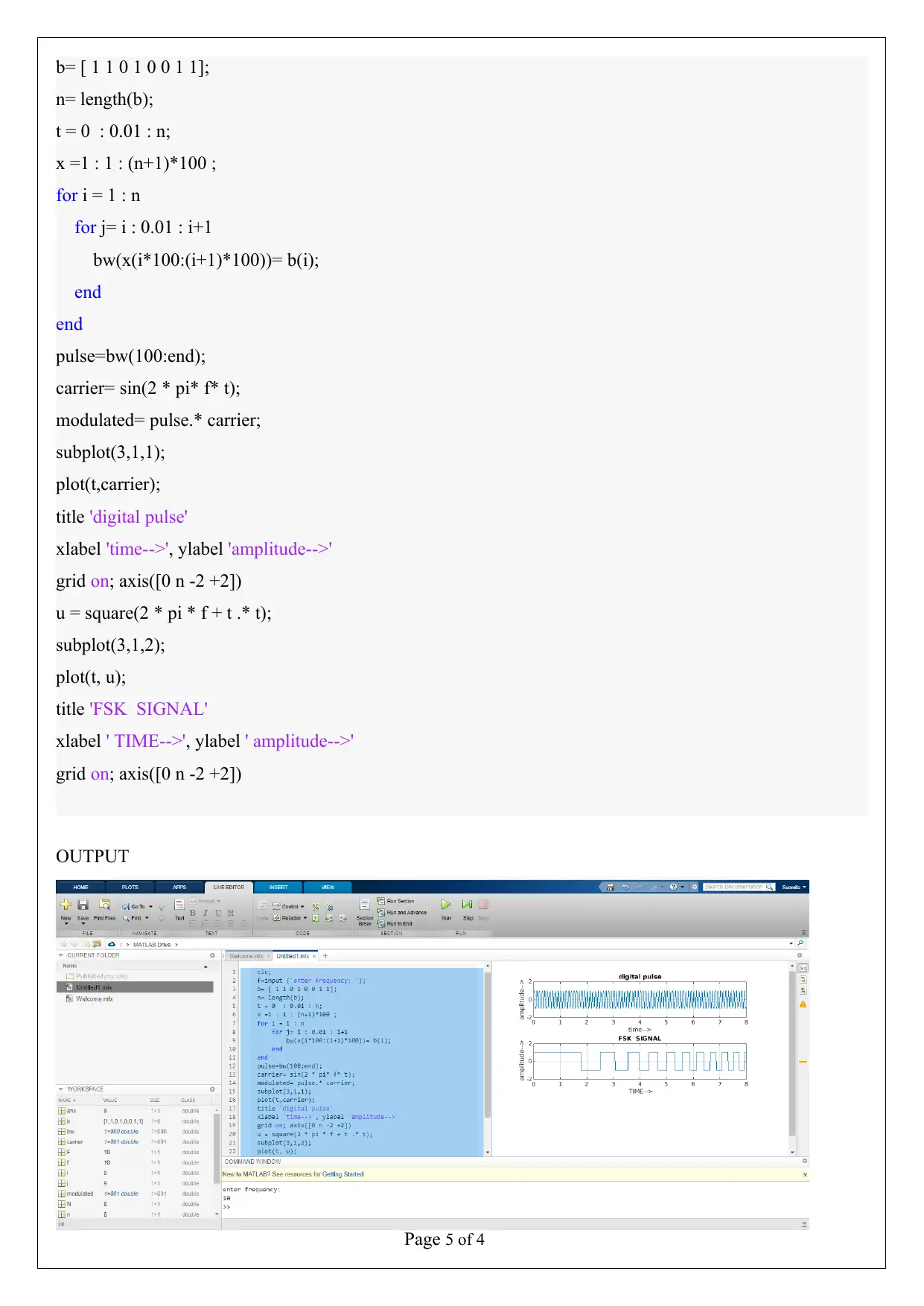
Page 5 of 4
b= [ 1 1 0 1 0 0 1 1];
n= length(b);
t = 0 : 0.01 : n;
x =1 : 1 : (n+1)*100 ;
for i = 1 : n
for j= i : 0.01 : i+1
bw(x(i*100:(i+1)*100))= b(i);
end
end
pulse=bw(100:end);
carrier= sin(2 * pi* f* t);
modulated= pulse.* carrier;
subplot(3,1,1);
plot(t,carrier);
title 'digital pulse'
xlabel 'time-->', ylabel 'amplitude-->'
grid on; axis([0 n -2 +2])
u = square(2 * pi * f + t .* t);
subplot(3,1,2);
plot(t, u);
title 'FSK SIGNAL'
xlabel ' TIME-->', ylabel ' amplitude-->'
grid on; axis([0 n -2 +2])
OUTPUT
b= [ 1 1 0 1 0 0 1 1];
n= length(b);
t = 0 : 0.01 : n;
x =1 : 1 : (n+1)*100 ;
for i = 1 : n
for j= i : 0.01 : i+1
bw(x(i*100:(i+1)*100))= b(i);
end
end
pulse=bw(100:end);
carrier= sin(2 * pi* f* t);
modulated= pulse.* carrier;
subplot(3,1,1);
plot(t,carrier);
title 'digital pulse'
xlabel 'time-->', ylabel 'amplitude-->'
grid on; axis([0 n -2 +2])
u = square(2 * pi * f + t .* t);
subplot(3,1,2);
plot(t, u);
title 'FSK SIGNAL'
xlabel ' TIME-->', ylabel ' amplitude-->'
grid on; axis([0 n -2 +2])
OUTPUT

Page 6 of 4
[3+3+3=9 marks]
[3+3+3=9 marks]
Page 7 of 4
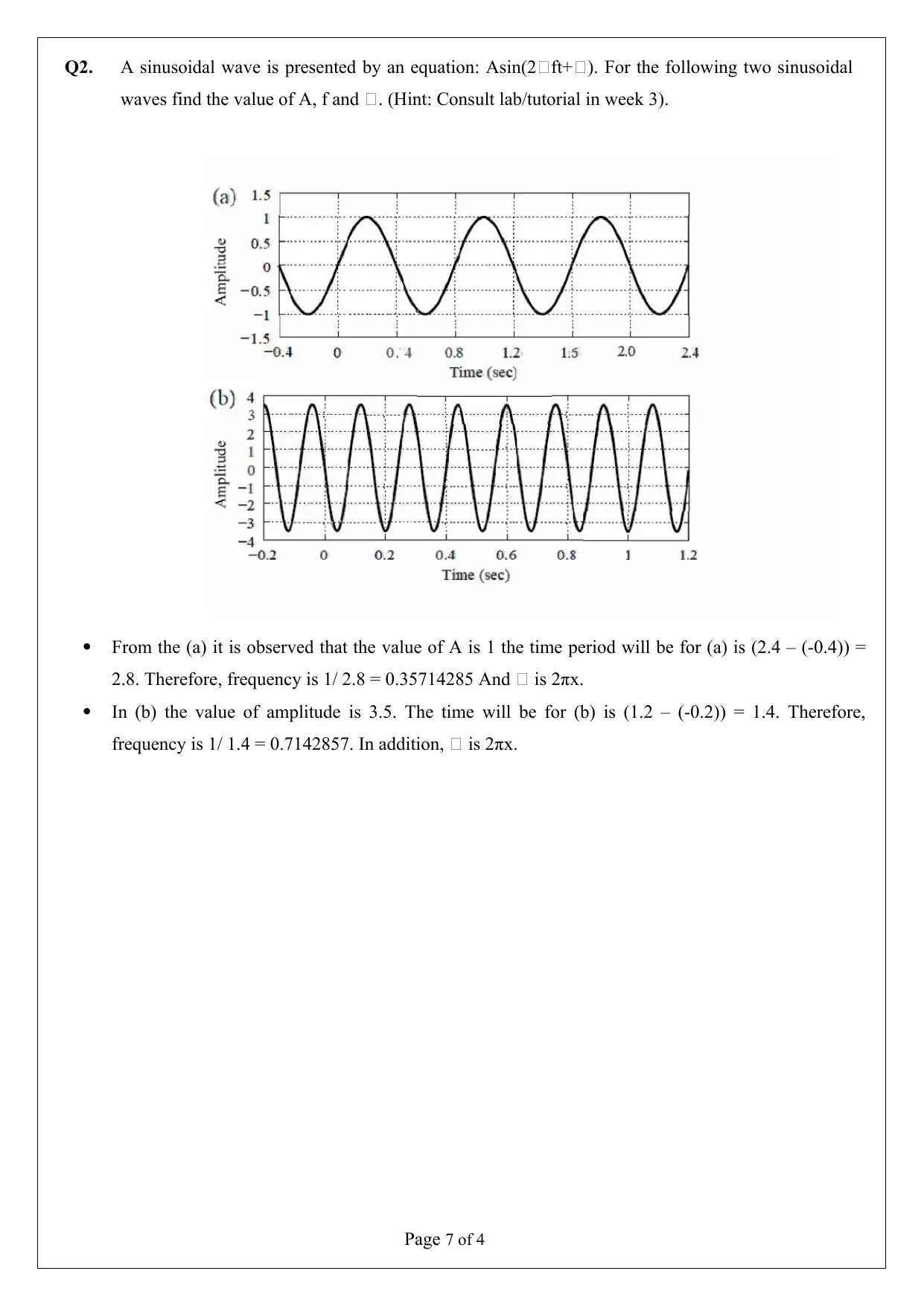
Q2. A sinusoidal wave is presented by an equation: Asin(2ft+). For the following two sinusoidal
waves find the value of A, f and . (Hint: Consult lab/tutorial in week 3).
From the (a) it is observed that the value of A is 1 the time period will be for (a) is (2.4 – (-0.4)) =
2.8. Therefore, frequency is 1/ 2.8 = 0.35714285 And is 2πx.
In (b) the value of amplitude is 3.5. The time will be for (b) is (1.2 – (-0.2)) = 1.4. Therefore,
frequency is 1/ 1.4 = 0.7142857. In addition, is 2πx.
Q2. A sinusoidal wave is presented by an equation: Asin(2ft+). For the following two sinusoidal
waves find the value of A, f and . (Hint: Consult lab/tutorial in week 3).
From the (a) it is observed that the value of A is 1 the time period will be for (a) is (2.4 – (-0.4)) =
2.8. Therefore, frequency is 1/ 2.8 = 0.35714285 And is 2πx.
In (b) the value of amplitude is 3.5. The time will be for (b) is (1.2 – (-0.2)) = 1.4. Therefore,
frequency is 1/ 1.4 = 0.7142857. In addition, is 2πx.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

Page 8 of 4
Q3. The Square Kilometre Array (SKA) is one of the biggest projects planned in Australia that has
international importance. Read articles on SKA and write a report of minimum 700 words. Your
report should include the wireless communication features of it, such a type, size and height of the
antennas, communication frequency bands, and any other technical specifications relevant to
wireless communication technology. You should may also include diagrams.
Introduction
The report will discuss the wireless communication features of the SKA including the size, height of
each antenna along with their band frequency and all other technical things that is related with the wireless
communication technology. The report will also discuss the overall wireless communication technology of
SKA music.
Discussion
The wireless communication technology is very popular alternative options for network. This system
cannot fully develop without including any wire but it connects various wireless devices that are used to
communicate with traditional network. The features of wireless communication technology are discussed in
the below section:
It has huge capacity including the load balancing: this is mainly used to coverage along with the Smartphone
such as tablets any laptops and all other devices. However, now a day, wireless network is planning for the
capacity. User can incorporate huge load on the wireless as well as wired network technology of SKA
(Holfeld et al., 2016). It indicates that when one part of network is hugely loaded then that parts shift user
from another part as per the capacity of the access point.
Scalability of wireless network: the wireless network technology can be increased rapidly as per the
requirement of user. Day by day, it continuously increased without having any overload (Mahmood
et al., 2015).
The management system of network: today, wireless communication technology is connected with
huge number of access point like thousand of access points and switch and firewalls are used to
manage all other components in the wireless networking technology. User has the ability to manage
the overall network from the central point of network.
The access control that is based on the role: it indicates when and from where the user can access the
overall wireless networking technology. After defining the role of the each user, the policies of
access control must be enforced.
Coverage of outdoor and indoor area coverage: the wireless network technology provides support in
both the case like indoor and outdoor. The user can access the wireless communication technology
from outdoor as well as indoor as per their needs.
The measurement of performance: due to large number of users, the wireless technology measures
the performance of the each end user and the overall performance of the network. It is mainly used to
Q3. The Square Kilometre Array (SKA) is one of the biggest projects planned in Australia that has
international importance. Read articles on SKA and write a report of minimum 700 words. Your
report should include the wireless communication features of it, such a type, size and height of the
antennas, communication frequency bands, and any other technical specifications relevant to
wireless communication technology. You should may also include diagrams.
Introduction
The report will discuss the wireless communication features of the SKA including the size, height of
each antenna along with their band frequency and all other technical things that is related with the wireless
communication technology. The report will also discuss the overall wireless communication technology of
SKA music.
Discussion
The wireless communication technology is very popular alternative options for network. This system
cannot fully develop without including any wire but it connects various wireless devices that are used to
communicate with traditional network. The features of wireless communication technology are discussed in
the below section:
It has huge capacity including the load balancing: this is mainly used to coverage along with the Smartphone
such as tablets any laptops and all other devices. However, now a day, wireless network is planning for the
capacity. User can incorporate huge load on the wireless as well as wired network technology of SKA
(Holfeld et al., 2016). It indicates that when one part of network is hugely loaded then that parts shift user
from another part as per the capacity of the access point.
Scalability of wireless network: the wireless network technology can be increased rapidly as per the
requirement of user. Day by day, it continuously increased without having any overload (Mahmood
et al., 2015).
The management system of network: today, wireless communication technology is connected with
huge number of access point like thousand of access points and switch and firewalls are used to
manage all other components in the wireless networking technology. User has the ability to manage
the overall network from the central point of network.
The access control that is based on the role: it indicates when and from where the user can access the
overall wireless networking technology. After defining the role of the each user, the policies of
access control must be enforced.
Coverage of outdoor and indoor area coverage: the wireless network technology provides support in
both the case like indoor and outdoor. The user can access the wireless communication technology
from outdoor as well as indoor as per their needs.
The measurement of performance: due to large number of users, the wireless technology measures
the performance of the each end user and the overall performance of the network. It is mainly used to

Page 9 of 4
see the real time user who used the wireless network and their devices by which they access the
wireless communication technology (Akyildiz et al., 2015). It also shows the impact on those
applications and each networking components.
Access control of network: the network access control or NAC provides the user to access the
network and the overall role is controlled by the NAC. It also allows user to make the registration on
the network for accessing the wireless communication technology (Mansour et al., 2017).
There are many others features of wireless technology that is observed in the SKA such as:
It has ability for communication different devices such as 2.4GHz and 5 GHz.
The content of web applications and filtering the applications to protect the user from their private
content.
It is also used to manage the mobile devices
It measures the performance of the application and based on this performance it prioritize the
application to the users.
It provides the facility of roaming that means any user from remote location can easily access the
wireless network technology.
There are many redundancies in the wifi system and for this reason user have to back up their data
for future use.
It is helpful to adapt the management of the radio.
It uses appropriate firewalls to maintain the security of the overall wireless communication network
technology.
With the help of wireless technology, the switching technology is provided. It helps to do the flow
more efficiently.
It used to mitigate the unnecessary traffic as well as unexpected traffic to improve the performance
of overall network.
By providing well-managed traffic, they can experience better feedback.
Conclusion
The report discussed the features of the wireless communication technology and its technical specification about the
articles of SKA. It also showed the bandwidth, size and other used devices in the SKA to improve its performance. By
using these advantages, SKA provides its performance as well as good services. It provides various types of music and
user can access music with the help of wireless technology from any location.
see the real time user who used the wireless network and their devices by which they access the
wireless communication technology (Akyildiz et al., 2015). It also shows the impact on those
applications and each networking components.
Access control of network: the network access control or NAC provides the user to access the
network and the overall role is controlled by the NAC. It also allows user to make the registration on
the network for accessing the wireless communication technology (Mansour et al., 2017).
There are many others features of wireless technology that is observed in the SKA such as:
It has ability for communication different devices such as 2.4GHz and 5 GHz.
The content of web applications and filtering the applications to protect the user from their private
content.
It is also used to manage the mobile devices
It measures the performance of the application and based on this performance it prioritize the
application to the users.
It provides the facility of roaming that means any user from remote location can easily access the
wireless network technology.
There are many redundancies in the wifi system and for this reason user have to back up their data
for future use.
It is helpful to adapt the management of the radio.
It uses appropriate firewalls to maintain the security of the overall wireless communication network
technology.
With the help of wireless technology, the switching technology is provided. It helps to do the flow
more efficiently.
It used to mitigate the unnecessary traffic as well as unexpected traffic to improve the performance
of overall network.
By providing well-managed traffic, they can experience better feedback.
Conclusion
The report discussed the features of the wireless communication technology and its technical specification about the
articles of SKA. It also showed the bandwidth, size and other used devices in the SKA to improve its performance. By
using these advantages, SKA provides its performance as well as good services. It provides various types of music and
user can access music with the help of wireless technology from any location.
Page 10 of
4
References
Akyildiz, I. F., Wang, P., & Lin, S. C. (2015). SoftAir: A software defined networking architecture for 5G wireless
systems. Computer Networks, 85, 1-18.
Holfeld, B., Wieruch, D., Wirth, T., Thiele, L., Ashraf, S. A., Huschke, J., ... & Ansari, J. (2016). Wireless
communication for factory automation: An opportunity for LTE and 5G systems. IEEE Communications
Magazine, 54(6), 36-43.
Mahmood, A., Javaid, N., & Razzaq, S. (2015). A review of wireless communications for smart grid. Renewable and
sustainable energy reviews, 41, 248-260.
Mansour, A., Mesleh, R., & Abaza, M. (2017). New challenges in wireless and free space optical
communications. Optics and lasers in engineering, 89, 95-108. [12 marks]
Part B – Studying home office wireless routers [Total 18 marks]
Q4. Some company staff members will require after hour access to the systems at the office, and to
the Internet for research projects. The intention is for the company to purchase broadband capability for
these staff members' home offices. Your task is to perform a comparative assessment of ADSL2+
equipment versus Cable modem equipment to determine which offers a better capability. The intention of
this exercise to understand the technical specification of two different types of router and know their
comparative advantages and limitations.
Select one ADSL2+ Modem-Router and one Cable Modem (Router) products in the market and
perform the following comparisons, in tabular form, item by item:
Topic ADSL2 + Modem-
Router
Cable modem
Modulation type Analog modulation Quadrature modulation
Modulation bit rates achievable 10 bits per symbols 56 thousand bits per second
Control
strategy
Premise control Implementation control
Is the modulation sensitive to
crosstalk?
Crosstalk Sensitive
What cable and connector types are
required for the line interface
Ethernet Coaxial cable
4
References
Akyildiz, I. F., Wang, P., & Lin, S. C. (2015). SoftAir: A software defined networking architecture for 5G wireless
systems. Computer Networks, 85, 1-18.
Holfeld, B., Wieruch, D., Wirth, T., Thiele, L., Ashraf, S. A., Huschke, J., ... & Ansari, J. (2016). Wireless
communication for factory automation: An opportunity for LTE and 5G systems. IEEE Communications
Magazine, 54(6), 36-43.
Mahmood, A., Javaid, N., & Razzaq, S. (2015). A review of wireless communications for smart grid. Renewable and
sustainable energy reviews, 41, 248-260.
Mansour, A., Mesleh, R., & Abaza, M. (2017). New challenges in wireless and free space optical
communications. Optics and lasers in engineering, 89, 95-108. [12 marks]
Part B – Studying home office wireless routers [Total 18 marks]
Q4. Some company staff members will require after hour access to the systems at the office, and to
the Internet for research projects. The intention is for the company to purchase broadband capability for
these staff members' home offices. Your task is to perform a comparative assessment of ADSL2+
equipment versus Cable modem equipment to determine which offers a better capability. The intention of
this exercise to understand the technical specification of two different types of router and know their
comparative advantages and limitations.
Select one ADSL2+ Modem-Router and one Cable Modem (Router) products in the market and
perform the following comparisons, in tabular form, item by item:
Topic ADSL2 + Modem-
Router
Cable modem
Modulation type Analog modulation Quadrature modulation
Modulation bit rates achievable 10 bits per symbols 56 thousand bits per second
Control
strategy
Premise control Implementation control
Is the modulation sensitive to
crosstalk?
Crosstalk Sensitive
What cable and connector types are
required for the line interface
Ethernet Coaxial cable
Secure Best Marks with AI Grader
Need help grading? Try our AI Grader for instant feedback on your assignments.

Page 11 of
4
Figure 1: ADSL2 + Modem-Router
(Source: created by author)
Figure 2: cable modem
(Source: created by author)
Host Interface [5 marks]:
What host side interfaces are provided? (Hint: Ethernet, Firewire, USB2)
The host side interfaces are provided such as Ethernet and fireware. In case of Ethernet, it is mainly used to
transfer the data as well as it is responsible to connect the various types of computers in the network and
help to transfer error free data across the network.
What bit rates do these support?
The bit rate of those support is 768 kbps
How many ports are provided?
256 ports are provided in this network.
Is an embedded switching capability provided? Is DHCP
provided?
Yes, DHCP is provided in this network.
Modulation Comparison and Recommendation [8=(5+3) marks]:
After you have completed, in tabular form, the comparison of basic parameters and specifications,
provide a comparison of at least 300 words between the modulation types used in these products,
4
Figure 1: ADSL2 + Modem-Router
(Source: created by author)
Figure 2: cable modem
(Source: created by author)
Host Interface [5 marks]:
What host side interfaces are provided? (Hint: Ethernet, Firewire, USB2)
The host side interfaces are provided such as Ethernet and fireware. In case of Ethernet, it is mainly used to
transfer the data as well as it is responsible to connect the various types of computers in the network and
help to transfer error free data across the network.
What bit rates do these support?
The bit rate of those support is 768 kbps
How many ports are provided?
256 ports are provided in this network.
Is an embedded switching capability provided? Is DHCP
provided?
Yes, DHCP is provided in this network.
Modulation Comparison and Recommendation [8=(5+3) marks]:
After you have completed, in tabular form, the comparison of basic parameters and specifications,
provide a comparison of at least 300 words between the modulation types used in these products,

Page 12 of
4
explaining their respective strengths and weaknesses for this application.
Modulation types Strength Weakness
Amplitude modulation It is very simple for
understanding as well
as implementing
It needs limited
bandwidth
It requires carriers
those are low
frequency
It takes very less cost
rather than frequency
modulation
techniques.
It is suitable for the
long distance
transmission.
It has very high speed
the carrier frequency
of the amplitude
modulation is less
than 10 percent
Based on the overall
amplitude.
It is not so efficient in
case of power
Its bandwidth is very
low
It is not suitable for
the large noise
because it is very
sensitive for the huge
amount of noise.
The reproduction is
not very high
faithfulness.
Frequency modulation It is used to improve
the signal by
removing the noise.
Neighboring station
can make interaction
very easily
It requires less power
It is used to define the
service area with
given power.
It is used for analog
and digital both
Fm requires very
wide and huge
channel for
communications
It is very complex in
structure when it
transmits and
receiving the signal.
4
explaining their respective strengths and weaknesses for this application.
Modulation types Strength Weakness
Amplitude modulation It is very simple for
understanding as well
as implementing
It needs limited
bandwidth
It requires carriers
those are low
frequency
It takes very less cost
rather than frequency
modulation
techniques.
It is suitable for the
long distance
transmission.
It has very high speed
the carrier frequency
of the amplitude
modulation is less
than 10 percent
Based on the overall
amplitude.
It is not so efficient in
case of power
Its bandwidth is very
low
It is not suitable for
the large noise
because it is very
sensitive for the huge
amount of noise.
The reproduction is
not very high
faithfulness.
Frequency modulation It is used to improve
the signal by
removing the noise.
Neighboring station
can make interaction
very easily
It requires less power
It is used to define the
service area with
given power.
It is used for analog
and digital both
Fm requires very
wide and huge
channel for
communications
It is very complex in
structure when it
transmits and
receiving the signal.

Page 13 of
4
The signal varies in
the continuous
manner.
Phase modulation It is very simple
It helps to identify the
velocity of the
targeted data.
It allows each
computer to use
telephone system for
communicating each
other.
It used to improve the
immunity towards
noise
The modulated carrier
signal is used to
follow the amplitude
of signal of the
transmitted message.
It requires huge
numbers of hardware
equipment that makes
the modulation
process very complex
Some ambiguity is
observed during the
transmission of the
signal when it
exceeds the pi radian.
With the help of
frequency multiplier,
the index of
modulation may be
improved.
4
The signal varies in
the continuous
manner.
Phase modulation It is very simple
It helps to identify the
velocity of the
targeted data.
It allows each
computer to use
telephone system for
communicating each
other.
It used to improve the
immunity towards
noise
The modulated carrier
signal is used to
follow the amplitude
of signal of the
transmitted message.
It requires huge
numbers of hardware
equipment that makes
the modulation
process very complex
Some ambiguity is
observed during the
transmission of the
signal when it
exceeds the pi radian.
With the help of
frequency multiplier,
the index of
modulation may be
improved.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
Page 14 of
4
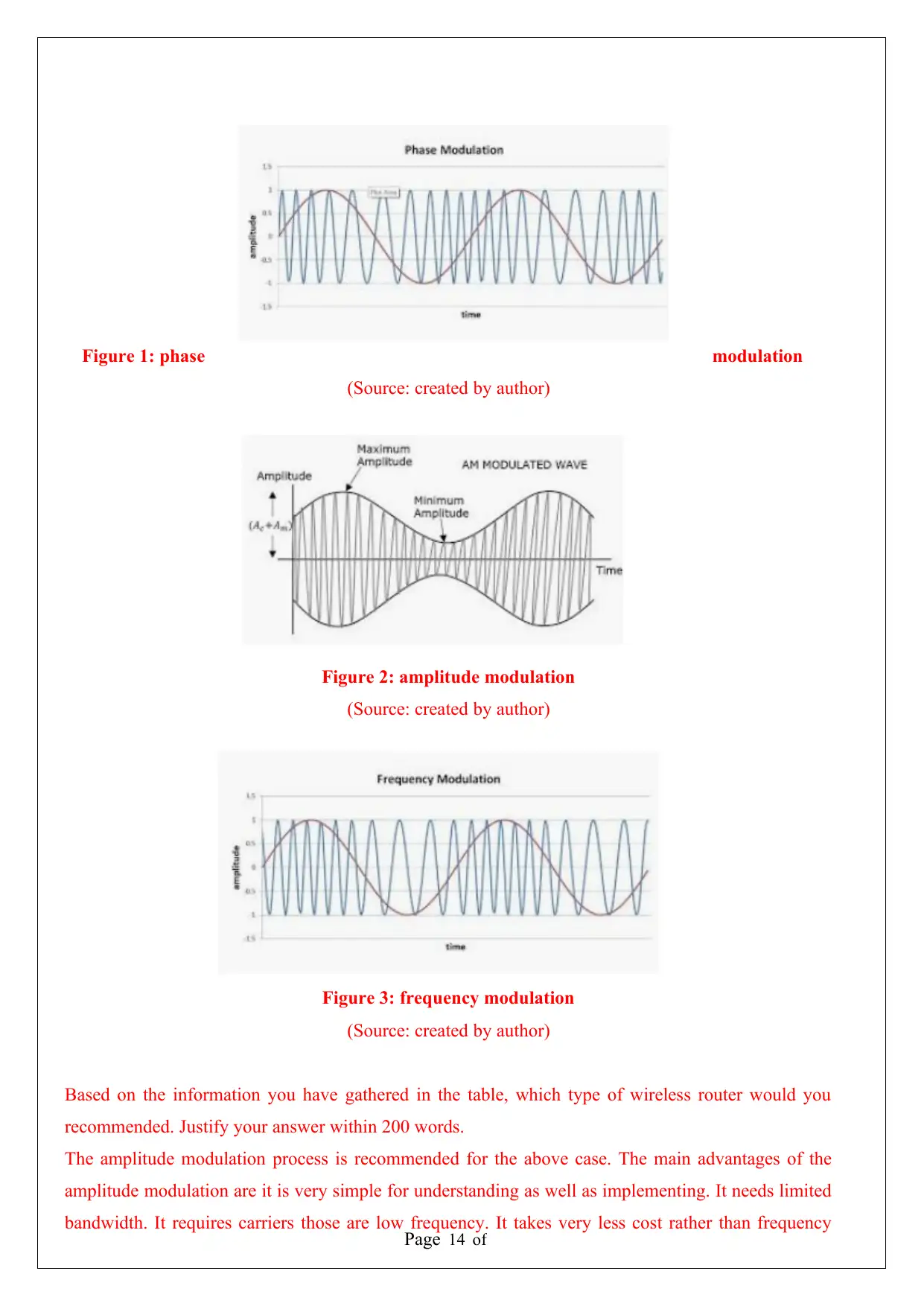
Figure 1: phase modulation
(Source: created by author)
Figure 2: amplitude modulation
(Source: created by author)
Figure 3: frequency modulation
(Source: created by author)
Based on the information you have gathered in the table, which type of wireless router would you
recommended. Justify your answer within 200 words.
The amplitude modulation process is recommended for the above case. The main advantages of the
amplitude modulation are it is very simple for understanding as well as implementing. It needs limited
bandwidth. It requires carriers those are low frequency. It takes very less cost rather than frequency
4
Figure 1: phase modulation
(Source: created by author)
Figure 2: amplitude modulation
(Source: created by author)
Figure 3: frequency modulation
(Source: created by author)
Based on the information you have gathered in the table, which type of wireless router would you
recommended. Justify your answer within 200 words.
The amplitude modulation process is recommended for the above case. The main advantages of the
amplitude modulation are it is very simple for understanding as well as implementing. It needs limited
bandwidth. It requires carriers those are low frequency. It takes very less cost rather than frequency

Page 15 of
4
modulation techniques. It is suitable for the long distance transmission. For this reason, it is suitable
for these product mentioned above. For this reason, it uses the amplitude modulation to get the better
performance very easily. It is better than frequency modulation as well as phase modulation. It is
suitable for very large area to transmit the signal and it allow user from the remote location. It has very
high speed and the carrier frequency of the amplitude modulation is less than 10 percent. It sometime
varies based on the overall amplitude.
4
modulation techniques. It is suitable for the long distance transmission. For this reason, it is suitable
for these product mentioned above. For this reason, it uses the amplitude modulation to get the better
performance very easily. It is better than frequency modulation as well as phase modulation. It is
suitable for very large area to transmit the signal and it allow user from the remote location. It has very
high speed and the carrier frequency of the amplitude modulation is less than 10 percent. It sometime
varies based on the overall amplitude.
1 out of 15
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
© 2024 | Zucol Services PVT LTD | All rights reserved.





