LAN Network Design and Implementation for FootFall Marketing Field
VerifiedAdded on 2024/05/17
|47
|6713
|211
AI Summary
This report explores the design and implementation of a Local Area Network (LAN) for FootFall Marketing Field, a company with three offices on different floors. The report covers various aspects of LAN technology, including different types of LANs, VLANs, communication equipment, and interconnecting media. It also analyzes traffic-intensive services and their performance, discusses LAN concerns and recommendations for security, reliability, and performance, and provides a detailed design of the LAN infrastructure for FootFall Marketing Field. The report concludes with a critical evaluation of the performance of the implemented LAN network.
Contribute Materials
Your contribution can guide someone’s learning journey. Share your
documents today.

Local Area Network (LAN)
Secure Best Marks with AI Grader
Need help grading? Try our AI Grader for instant feedback on your assignments.

Table of Contents
Introduction.....................................................................................................................................4
LO1 Understand the impact of LAN technologies...........................................................................5
A.C 1.1 critically evaluate different LAN technologies................................................................5
A.C 1.2 Critically analyze traffic intensive services and their performance..............................15
A.C 1.3 Discuss LAN concerns and make recommendations to sustain network security,
reliability, and performance......................................................................................................18
LO2 - Be able to design LAN infrastructures..................................................................................20
A.C 2.1 Design a LAN infrastructure to meet a given requirement.....................................20
A.C 2.2 critically evaluate the suitability of LAN components...................................................23
LO3- Be able to implement LAN infrastructures...........................................................................24
A.C 3.1 Build and configure a LAN (including services) to meet a given requirement..............24
A.C 3.2 Implement network security on a LAN.........................................................................32
A.C 3.3 critically review and test a LAN.....................................................................................36
LO4- Be able to manage LAN infrastructures................................................................................39
AC 4.1 Monitor and troubleshoot a LAN................................................................................39
AC 4.2 Resolve LAN issues to improve security, reliability, and performance.......................40
AC 4.3 Critically evaluate the performance of a LAN.............................................................41
Conclusion:....................................................................................................................................42
References.....................................................................................................................................43
1
Introduction.....................................................................................................................................4
LO1 Understand the impact of LAN technologies...........................................................................5
A.C 1.1 critically evaluate different LAN technologies................................................................5
A.C 1.2 Critically analyze traffic intensive services and their performance..............................15
A.C 1.3 Discuss LAN concerns and make recommendations to sustain network security,
reliability, and performance......................................................................................................18
LO2 - Be able to design LAN infrastructures..................................................................................20
A.C 2.1 Design a LAN infrastructure to meet a given requirement.....................................20
A.C 2.2 critically evaluate the suitability of LAN components...................................................23
LO3- Be able to implement LAN infrastructures...........................................................................24
A.C 3.1 Build and configure a LAN (including services) to meet a given requirement..............24
A.C 3.2 Implement network security on a LAN.........................................................................32
A.C 3.3 critically review and test a LAN.....................................................................................36
LO4- Be able to manage LAN infrastructures................................................................................39
AC 4.1 Monitor and troubleshoot a LAN................................................................................39
AC 4.2 Resolve LAN issues to improve security, reliability, and performance.......................40
AC 4.3 Critically evaluate the performance of a LAN.............................................................41
Conclusion:....................................................................................................................................42
References.....................................................................................................................................43
1

List of Figures:
Figure 1 Wire LAN network.............................................................................................................6
Figure 2 Wireless LAN network.......................................................................................................6
Figure 3 Ethernet cable to connect the device................................................................................7
Figure 4 Token ring to connect the system.....................................................................................8
Figure 5 VLAN network....................................................................................................................9
Figure 6 Hub...................................................................................................................................10
Figure 7 Router..............................................................................................................................11
Figure 8 Switches...........................................................................................................................11
Figure 9 Repeaters.........................................................................................................................12
Figure 10 Bridges...........................................................................................................................12
Figure 11 UTP (unshielded twisted pair).......................................................................................13
Figure 12 Coaxial cable..................................................................................................................13
Figure 13 STP(shielded twisted pair).............................................................................................14
Figure 14 Optic fiber table.............................................................................................................14
Figure 15 Working of VoI...............................................................................................................15
Figure 16 Video-on-demand..........................................................................................................16
Figure 17 Video and audio streaming............................................................................................16
Figure 18 Network Design View of the Organization....................................................................20
Figure 19 Star topologies...............................................................................................................21
Figure 20Configuration..................................................................................................................25
Figure 21 Router configuration......................................................................................................27
Figure 22 Configuration of installed router...................................................................................29
Figure 23 HTTP and DNS service of the network...........................................................................30
Figure 24 DHCP Server...................................................................................................................30
Figure 25 Design view of Network of Cisco Packet Tracer............................................................31
Figure 26 Configuration.................................................................................................................34
Figure 27 Test Case 1.....................................................................................................................37
Figure 28 Test Case 2.....................................................................................................................37
2
Figure 1 Wire LAN network.............................................................................................................6
Figure 2 Wireless LAN network.......................................................................................................6
Figure 3 Ethernet cable to connect the device................................................................................7
Figure 4 Token ring to connect the system.....................................................................................8
Figure 5 VLAN network....................................................................................................................9
Figure 6 Hub...................................................................................................................................10
Figure 7 Router..............................................................................................................................11
Figure 8 Switches...........................................................................................................................11
Figure 9 Repeaters.........................................................................................................................12
Figure 10 Bridges...........................................................................................................................12
Figure 11 UTP (unshielded twisted pair).......................................................................................13
Figure 12 Coaxial cable..................................................................................................................13
Figure 13 STP(shielded twisted pair).............................................................................................14
Figure 14 Optic fiber table.............................................................................................................14
Figure 15 Working of VoI...............................................................................................................15
Figure 16 Video-on-demand..........................................................................................................16
Figure 17 Video and audio streaming............................................................................................16
Figure 18 Network Design View of the Organization....................................................................20
Figure 19 Star topologies...............................................................................................................21
Figure 20Configuration..................................................................................................................25
Figure 21 Router configuration......................................................................................................27
Figure 22 Configuration of installed router...................................................................................29
Figure 23 HTTP and DNS service of the network...........................................................................30
Figure 24 DHCP Server...................................................................................................................30
Figure 25 Design view of Network of Cisco Packet Tracer............................................................31
Figure 26 Configuration.................................................................................................................34
Figure 27 Test Case 1.....................................................................................................................37
Figure 28 Test Case 2.....................................................................................................................37
2

Figure 29: Test Scenario three.......................................................................................................38
List of Figures:
Table 1 Comparison between Wireless and Wired LAN..................................................................5
Table 2 Comparison of IEEE 802.11 and IEEE 802.3........................................................................8
Table 3 IP Precedence Table..........................................................................................................17
Table4 Test Case Table..................................................................................................................36
3
List of Figures:
Table 1 Comparison between Wireless and Wired LAN..................................................................5
Table 2 Comparison of IEEE 802.11 and IEEE 802.3........................................................................8
Table 3 IP Precedence Table..........................................................................................................17
Table4 Test Case Table..................................................................................................................36
3
Secure Best Marks with AI Grader
Need help grading? Try our AI Grader for instant feedback on your assignments.

Introduction
LAN (Local Area Network) is basically a limited area networking which connects the one or more
system for the purpose of sharing of important files and information. LAN services are used
mostly in every sector like college, small office, and schools. So, in this assignment report, there
are four sections in which the complete assignment is explained. In the very first section of this
assignment, I will be discussing the theoretical concept of LAN technology, its various types,
VLAN, types of VLAN, communication equipment for data in LAN, and interconnecting media.
Also, the discussion will be made on traffic services and to maintain the security and
performance. In the second section of this assignment, I will implement the LAN network for
the organization FootFall Marketing Field for their three-floor office department and by keeping
in mind their all requirements. Also, suitability of the components will be checked.
In the third section of this assignment, I will be discussing the infrastructure of the LAN network
of the organization, the design view, metadata, DNS server, and DHCP server. Also, I will make
the discussion on the security of the network of the organization and in addition to this various
test cases will also be discussed. In the last section of this assignment, I will make a discussion
on the managing the network through various tools and also, issues related to the LAN.
4
LAN (Local Area Network) is basically a limited area networking which connects the one or more
system for the purpose of sharing of important files and information. LAN services are used
mostly in every sector like college, small office, and schools. So, in this assignment report, there
are four sections in which the complete assignment is explained. In the very first section of this
assignment, I will be discussing the theoretical concept of LAN technology, its various types,
VLAN, types of VLAN, communication equipment for data in LAN, and interconnecting media.
Also, the discussion will be made on traffic services and to maintain the security and
performance. In the second section of this assignment, I will implement the LAN network for
the organization FootFall Marketing Field for their three-floor office department and by keeping
in mind their all requirements. Also, suitability of the components will be checked.
In the third section of this assignment, I will be discussing the infrastructure of the LAN network
of the organization, the design view, metadata, DNS server, and DHCP server. Also, I will make
the discussion on the security of the network of the organization and in addition to this various
test cases will also be discussed. In the last section of this assignment, I will make a discussion
on the managing the network through various tools and also, issues related to the LAN.
4
LO1 Understand the impact of LAN technologies
A.C 1.1 critically evaluate different LAN technologies
The LAN (Local Area Network) is a system network which is used and required for exchanging
information and resources over a local area. The resources like files, games, audio, applications,
printers, emails, media files, internet access and many more can be shared on two or more
system using LAN within the specific local area. The LAN services are mostly used in the sectors
of corporate building, offices, schools, colleges, and many more. A number of services of LAN
are provided in the modern network but earlier traditional network offers only the single
service (Mitchell, 2017).
LAN Network Types:
Table 1 Comparison between Wireless and Wired LAN
Wireless LAN Wired LAN
The use of low resources and power machines is
taken.
The use of high resources and power machines is
taken.
Proximity requirement is more in wireless LAN. Security requirement is more in wired LAN.
The problem of the hidden terminal is there. The wired network can be heard or listen.
It provides high variations in the bandwidth but
actually works in the low bandwidth.
It provides low variations in the bandwidth but
actually works in the high bandwidth.
High packet delay. Low packet delay.
5
A.C 1.1 critically evaluate different LAN technologies
The LAN (Local Area Network) is a system network which is used and required for exchanging
information and resources over a local area. The resources like files, games, audio, applications,
printers, emails, media files, internet access and many more can be shared on two or more
system using LAN within the specific local area. The LAN services are mostly used in the sectors
of corporate building, offices, schools, colleges, and many more. A number of services of LAN
are provided in the modern network but earlier traditional network offers only the single
service (Mitchell, 2017).
LAN Network Types:
Table 1 Comparison between Wireless and Wired LAN
Wireless LAN Wired LAN
The use of low resources and power machines is
taken.
The use of high resources and power machines is
taken.
Proximity requirement is more in wireless LAN. Security requirement is more in wired LAN.
The problem of the hidden terminal is there. The wired network can be heard or listen.
It provides high variations in the bandwidth but
actually works in the low bandwidth.
It provides low variations in the bandwidth but
actually works in the high bandwidth.
High packet delay. Low packet delay.
5
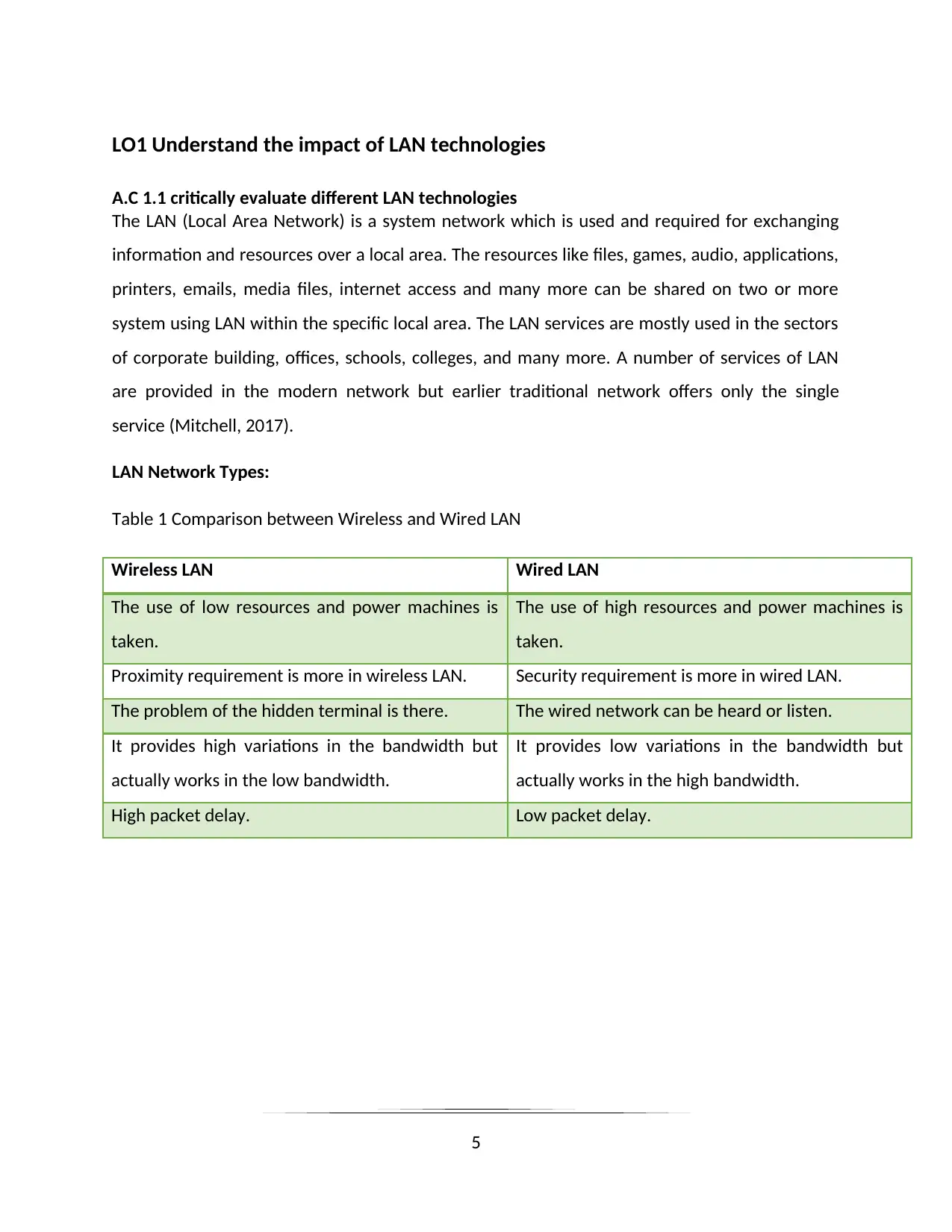
Figure 1 Wire LAN network
Source: (NEC-display,n.d.)
Figure 2 Wireless LAN network
Source: (NEC-display,n.d.)
6
Source: (NEC-display,n.d.)
Figure 2 Wireless LAN network
Source: (NEC-display,n.d.)
6
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

IEEE 802.11 Wi-Fi
This IEEE 802.11 is basically a standard for wireless networking system. It generally works on
the security of wireless networking, Access Control of Media, and QoS (Quality of Service)
(Hope, 2017).
IEEE 802.3 Ethernet
For a wired network, the Ethernet IEEE 802.3 standards are defined and are generally for MAC
layer and physical layers. The physical connection is established between the nodes of fiber and
copper wire. This network of LAN generally uses CD/CSMA method (Cozlink, 2016).
Figure 3 Ethernet cable to connect the device
Token Ring
Token Ring is also implemented in all of the organization systems in the network which are
interconnected to the selected topology (Star topology or hybrid topology). To pass the
message one host to other, it uses the logical token in the systems. By using the token ring the
colliding problem is resolved to form the network and data can be sent by implementing these
token rings.
7
This IEEE 802.11 is basically a standard for wireless networking system. It generally works on
the security of wireless networking, Access Control of Media, and QoS (Quality of Service)
(Hope, 2017).
IEEE 802.3 Ethernet
For a wired network, the Ethernet IEEE 802.3 standards are defined and are generally for MAC
layer and physical layers. The physical connection is established between the nodes of fiber and
copper wire. This network of LAN generally uses CD/CSMA method (Cozlink, 2016).
Figure 3 Ethernet cable to connect the device
Token Ring
Token Ring is also implemented in all of the organization systems in the network which are
interconnected to the selected topology (Star topology or hybrid topology). To pass the
message one host to other, it uses the logical token in the systems. By using the token ring the
colliding problem is resolved to form the network and data can be sent by implementing these
token rings.
7
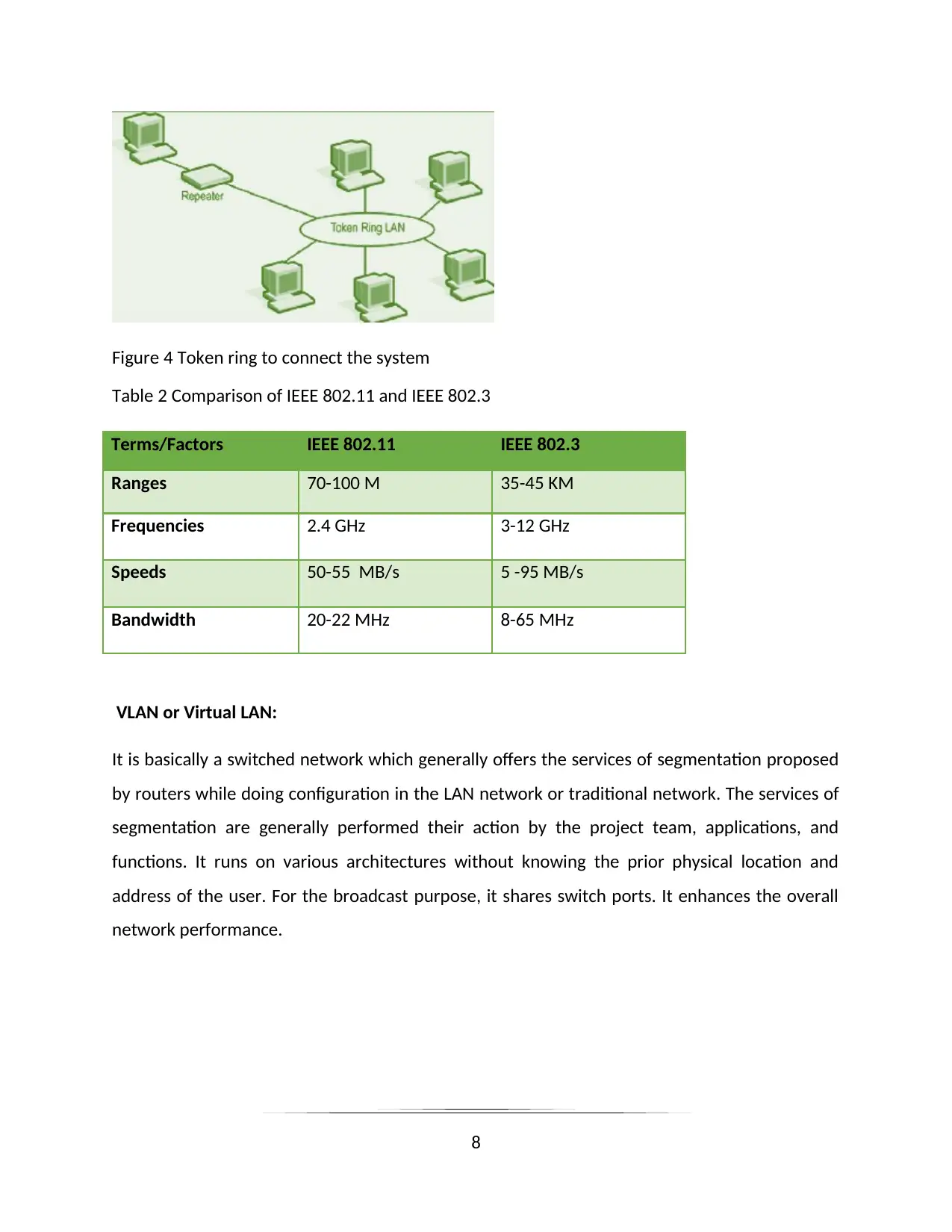
Figure 4 Token ring to connect the system
Table 2 Comparison of IEEE 802.11 and IEEE 802.3
Terms/Factors IEEE 802.11 IEEE 802.3
Ranges 70-100 M 35-45 KM
Frequencies 2.4 GHz 3-12 GHz
Speeds 50-55 MB/s 5 -95 MB/s
Bandwidth 20-22 MHz 8-65 MHz
VLAN or Virtual LAN:
It is basically a switched network which generally offers the services of segmentation proposed
by routers while doing configuration in the LAN network or traditional network. The services of
segmentation are generally performed their action by the project team, applications, and
functions. It runs on various architectures without knowing the prior physical location and
address of the user. For the broadcast purpose, it shares switch ports. It enhances the overall
network performance.
8
Table 2 Comparison of IEEE 802.11 and IEEE 802.3
Terms/Factors IEEE 802.11 IEEE 802.3
Ranges 70-100 M 35-45 KM
Frequencies 2.4 GHz 3-12 GHz
Speeds 50-55 MB/s 5 -95 MB/s
Bandwidth 20-22 MHz 8-65 MHz
VLAN or Virtual LAN:
It is basically a switched network which generally offers the services of segmentation proposed
by routers while doing configuration in the LAN network or traditional network. The services of
segmentation are generally performed their action by the project team, applications, and
functions. It runs on various architectures without knowing the prior physical location and
address of the user. For the broadcast purpose, it shares switch ports. It enhances the overall
network performance.
8
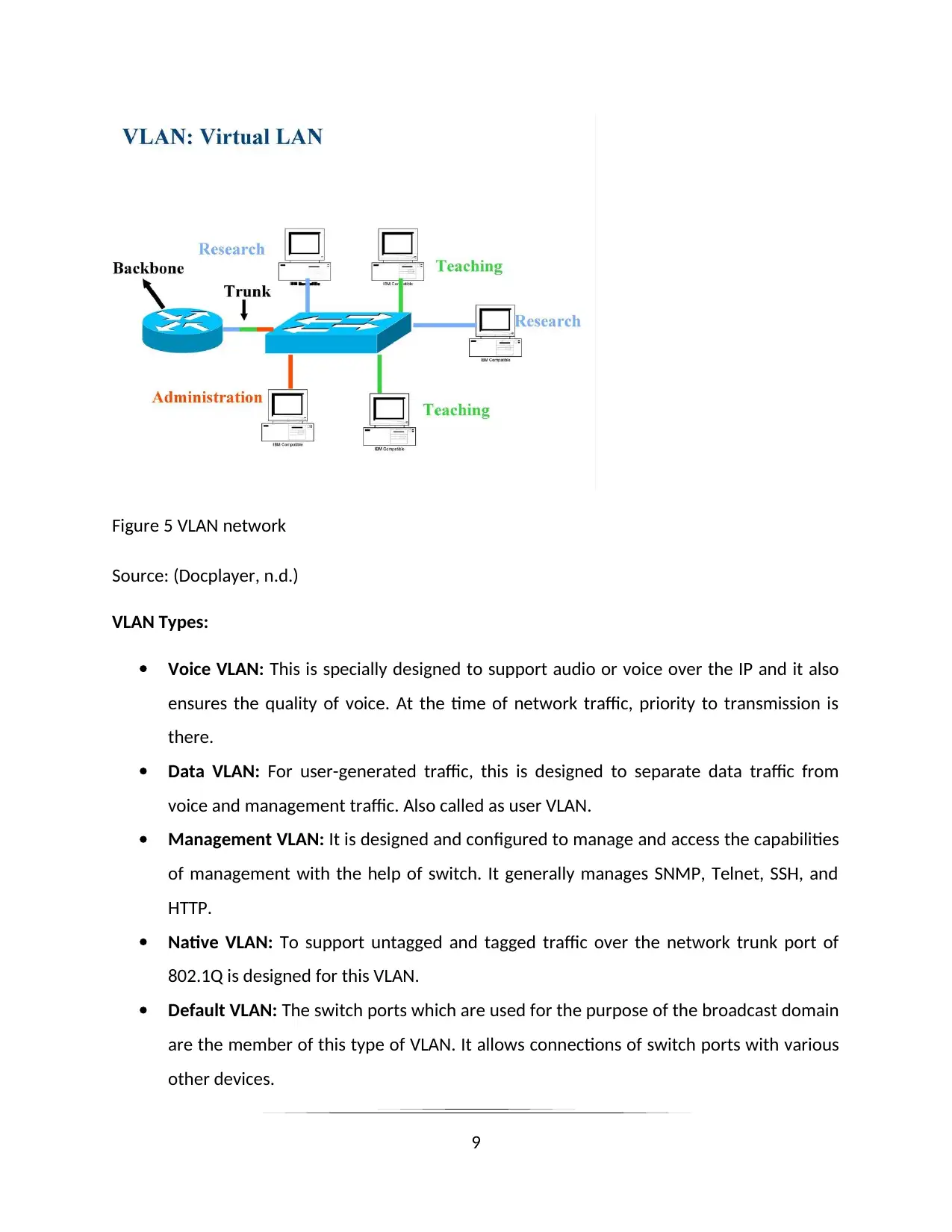
Figure 5 VLAN network
Source: (Docplayer, n.d.)
VLAN Types:
Voice VLAN: This is specially designed to support audio or voice over the IP and it also
ensures the quality of voice. At the time of network traffic, priority to transmission is
there.
Data VLAN: For user-generated traffic, this is designed to separate data traffic from
voice and management traffic. Also called as user VLAN.
Management VLAN: It is designed and configured to manage and access the capabilities
of management with the help of switch. It generally manages SNMP, Telnet, SSH, and
HTTP.
Native VLAN: To support untagged and tagged traffic over the network trunk port of
802.1Q is designed for this VLAN.
Default VLAN: The switch ports which are used for the purpose of the broadcast domain
are the member of this type of VLAN. It allows connections of switch ports with various
other devices.
9
Source: (Docplayer, n.d.)
VLAN Types:
Voice VLAN: This is specially designed to support audio or voice over the IP and it also
ensures the quality of voice. At the time of network traffic, priority to transmission is
there.
Data VLAN: For user-generated traffic, this is designed to separate data traffic from
voice and management traffic. Also called as user VLAN.
Management VLAN: It is designed and configured to manage and access the capabilities
of management with the help of switch. It generally manages SNMP, Telnet, SSH, and
HTTP.
Native VLAN: To support untagged and tagged traffic over the network trunk port of
802.1Q is designed for this VLAN.
Default VLAN: The switch ports which are used for the purpose of the broadcast domain
are the member of this type of VLAN. It allows connections of switch ports with various
other devices.
9
Secure Best Marks with AI Grader
Need help grading? Try our AI Grader for instant feedback on your assignments.

VLAN Benefits:
Higher Performance: It generally works in multiple workgroups with some logic which
helps in reducing the traffic flow and keeps the performance high.
Mitigation of Broadcast Storm: The network of VLAN generally reduces the devices into
the storm broadcast because the network is divided.
Security: The sensitive data is separated from the VLAN network but which results in the
increase of confidential of the information.
Cost Reduction: Due to efficient bandwidth, the network cost is reduced
(itknowledgeexchange, 2018).
Communication Equipment for LAN data:
Various LAN equipment is:
Hubs: The network device which is required for connecting various Ethernet devices. It
generally works as a segment of the single network. It works on the physical layer of the
OSI model. It has one port of input where signals are presented and the appearance of
output is in every part excluding the port of input.
Figure 6 Hub
Source: (Trendnet, n.d.)
10
Higher Performance: It generally works in multiple workgroups with some logic which
helps in reducing the traffic flow and keeps the performance high.
Mitigation of Broadcast Storm: The network of VLAN generally reduces the devices into
the storm broadcast because the network is divided.
Security: The sensitive data is separated from the VLAN network but which results in the
increase of confidential of the information.
Cost Reduction: Due to efficient bandwidth, the network cost is reduced
(itknowledgeexchange, 2018).
Communication Equipment for LAN data:
Various LAN equipment is:
Hubs: The network device which is required for connecting various Ethernet devices. It
generally works as a segment of the single network. It works on the physical layer of the
OSI model. It has one port of input where signals are presented and the appearance of
output is in every part excluding the port of input.
Figure 6 Hub
Source: (Trendnet, n.d.)
10

Routers: The role of routers is that it forwards packets of data between network and
internet. It also connects data lines to the various networks. The address of the packets
is read by the routers come through single data lines and the final destination is defined.
It has router tables which store information of the journey of the packets. The main role
is to control the traffic flow.
Figure 7 Router
Source: (Delaney, 2018)
Switches: It is required to connect LAN to the computer and is a hardware device. It is
similar to hubs but the work done by the switch is more effective and intelligent. Data
packets are received by switches and it determines the source and destination devices
and then transmitted it. Also, performance is enhanced due to optimization of the
bandwidth of the network.
Figure 8 Switches
11
internet. It also connects data lines to the various networks. The address of the packets
is read by the routers come through single data lines and the final destination is defined.
It has router tables which store information of the journey of the packets. The main role
is to control the traffic flow.
Figure 7 Router
Source: (Delaney, 2018)
Switches: It is required to connect LAN to the computer and is a hardware device. It is
similar to hubs but the work done by the switch is more effective and intelligent. Data
packets are received by switches and it determines the source and destination devices
and then transmitted it. Also, performance is enhanced due to optimization of the
bandwidth of the network.
Figure 8 Switches
11

Source: (Carter, 2012)
Repeaters: It generally connects two network segments which shrink the space for
transmission media. It forwards almost every frame lacking filtering amplifier and
capabilities.
Figure 9 Repeaters
Source: (Matrox, 2012)
Bridges: It is the double layer device which forms various LAN segments. Each segment
is having the distinct impact domain. It is used to control the traffic flow and keeping it
separate. Also, frame filtering in the LAN network (Cooper, n.d.).
Figure 10 Bridges
Source: (Simpson, 2015)
12
Repeaters: It generally connects two network segments which shrink the space for
transmission media. It forwards almost every frame lacking filtering amplifier and
capabilities.
Figure 9 Repeaters
Source: (Matrox, 2012)
Bridges: It is the double layer device which forms various LAN segments. Each segment
is having the distinct impact domain. It is used to control the traffic flow and keeping it
separate. Also, frame filtering in the LAN network (Cooper, n.d.).
Figure 10 Bridges
Source: (Simpson, 2015)
12
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
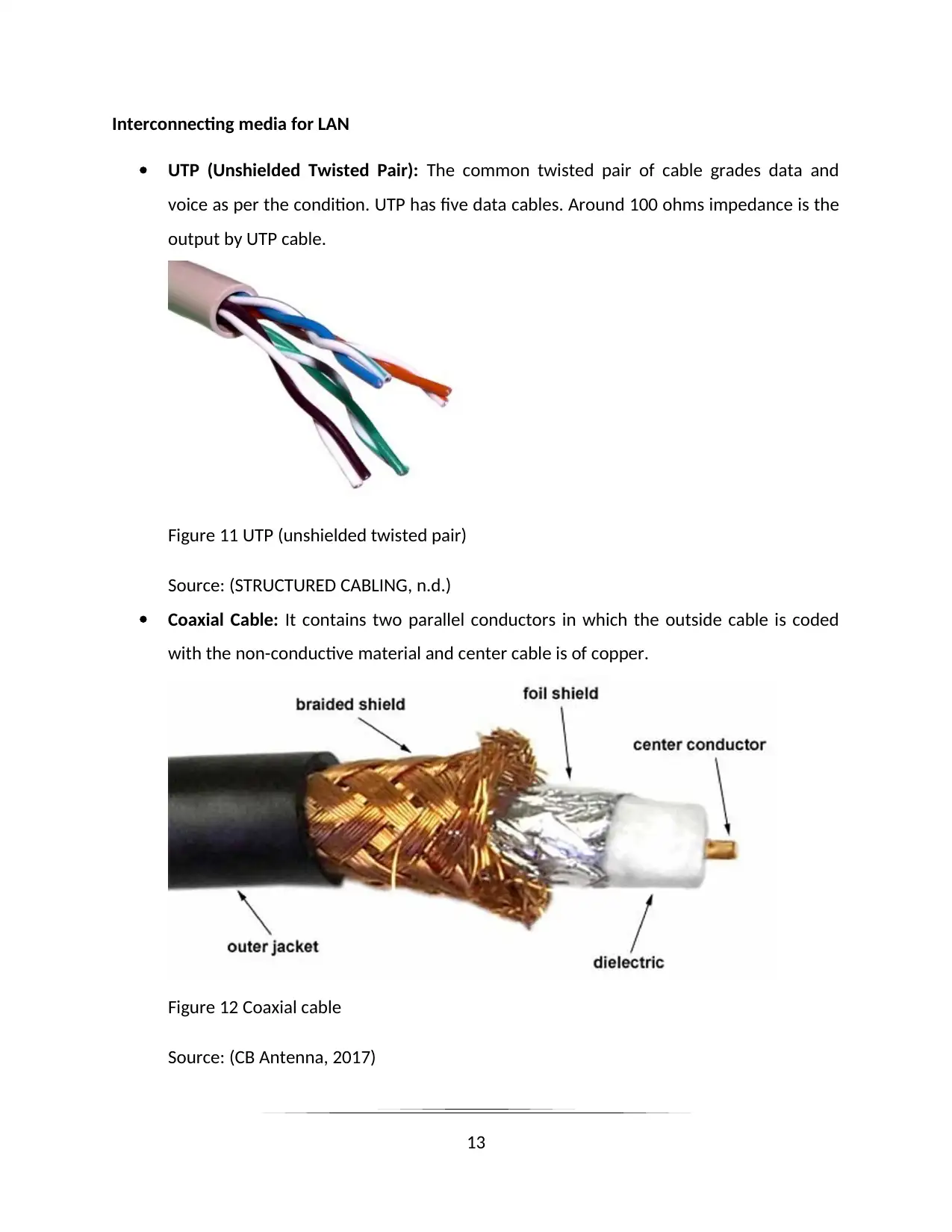
Interconnecting media for LAN
UTP (Unshielded Twisted Pair): The common twisted pair of cable grades data and
voice as per the condition. UTP has five data cables. Around 100 ohms impedance is the
output by UTP cable.
Figure 11 UTP (unshielded twisted pair)
Source: (STRUCTURED CABLING, n.d.)
Coaxial Cable: It contains two parallel conductors in which the outside cable is coded
with the non-conductive material and center cable is of copper.
Figure 12 Coaxial cable
Source: (CB Antenna, 2017)
13
UTP (Unshielded Twisted Pair): The common twisted pair of cable grades data and
voice as per the condition. UTP has five data cables. Around 100 ohms impedance is the
output by UTP cable.
Figure 11 UTP (unshielded twisted pair)
Source: (STRUCTURED CABLING, n.d.)
Coaxial Cable: It contains two parallel conductors in which the outside cable is coded
with the non-conductive material and center cable is of copper.
Figure 12 Coaxial cable
Source: (CB Antenna, 2017)
13
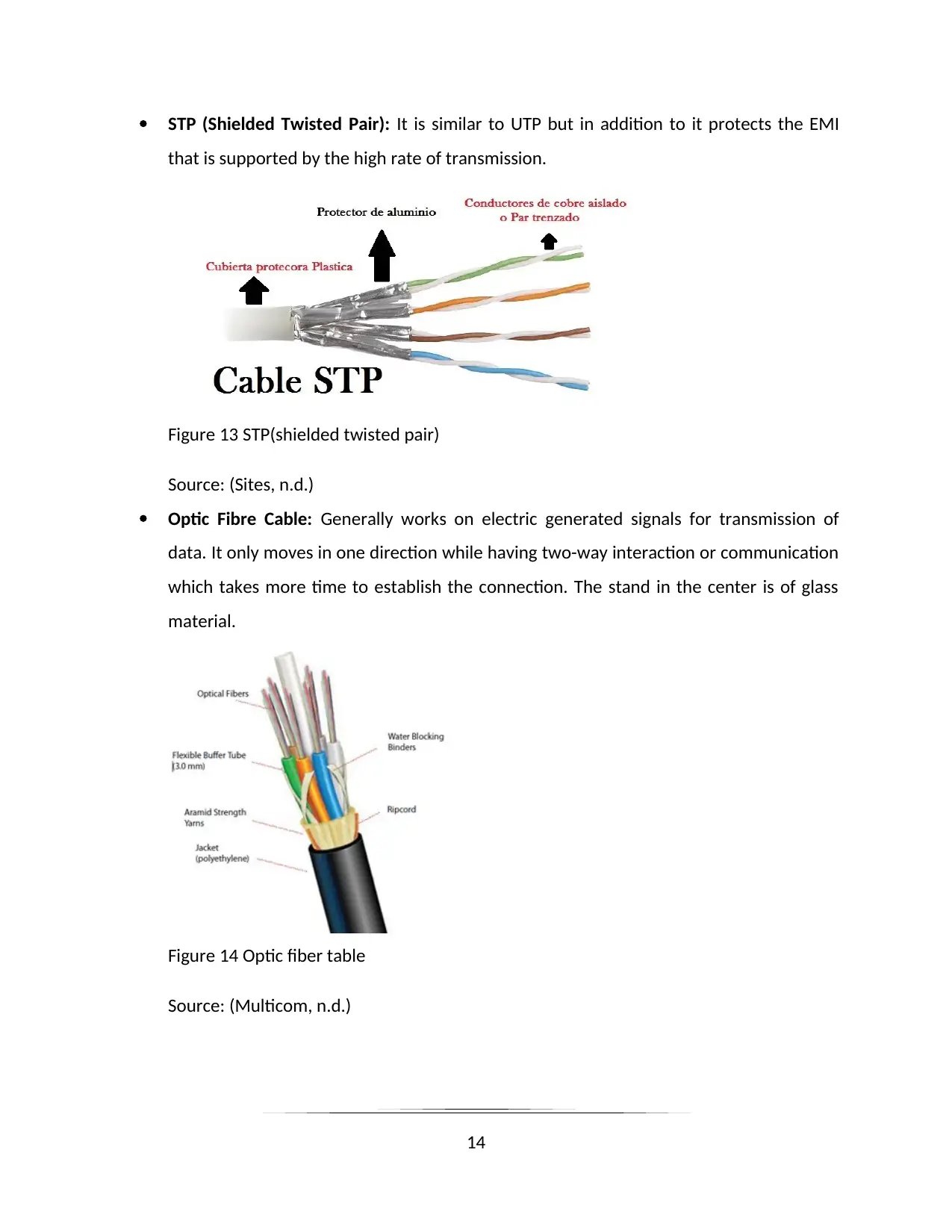
STP (Shielded Twisted Pair): It is similar to UTP but in addition to it protects the EMI
that is supported by the high rate of transmission.
Figure 13 STP(shielded twisted pair)
Source: (Sites, n.d.)
Optic Fibre Cable: Generally works on electric generated signals for transmission of
data. It only moves in one direction while having two-way interaction or communication
which takes more time to establish the connection. The stand in the center is of glass
material.
Figure 14 Optic fiber table
Source: (Multicom, n.d.)
14
that is supported by the high rate of transmission.
Figure 13 STP(shielded twisted pair)
Source: (Sites, n.d.)
Optic Fibre Cable: Generally works on electric generated signals for transmission of
data. It only moves in one direction while having two-way interaction or communication
which takes more time to establish the connection. The stand in the center is of glass
material.
Figure 14 Optic fiber table
Source: (Multicom, n.d.)
14

A.C 1.2 Critically analyze traffic intensive services and their performance
To analyze the traffic intensive services and their performance check the parity bit and data
transferring by detecting the error:
Parity Bit checker to analyze the traffic intensive services and their performance:
The parity checking is the procedure to ensure the data transmission accurately between the
installed nodes in the network during the data communication. The parity bit appends to the
real data bits for creating the odd and event bit number. When the data is transmitted it checks
the source and destination of data and also verifies the address.
The data transmission should be secure between the nodes of the FootFall Field Marketing Ltd
network. If the data is transmitted incorrectly then the parity bit values are become incorrect
by indicating the issues during the data transmission.
There are various intensive services related to traffic are (Mace, n.d.):
Video-over-IP: By the help of PSTN it receives the voice signal over the internet. It allows
communication in two ways on the broadcast network connection. It converts voice analog
signal to the digital signal and transmits it and vice-versa happens again. For the purpose of
voice transmission the routing, compression, and encapsulation.
Figure 15 Working of VoI
Source: (Yenra, 2004)
15
To analyze the traffic intensive services and their performance check the parity bit and data
transferring by detecting the error:
Parity Bit checker to analyze the traffic intensive services and their performance:
The parity checking is the procedure to ensure the data transmission accurately between the
installed nodes in the network during the data communication. The parity bit appends to the
real data bits for creating the odd and event bit number. When the data is transmitted it checks
the source and destination of data and also verifies the address.
The data transmission should be secure between the nodes of the FootFall Field Marketing Ltd
network. If the data is transmitted incorrectly then the parity bit values are become incorrect
by indicating the issues during the data transmission.
There are various intensive services related to traffic are (Mace, n.d.):
Video-over-IP: By the help of PSTN it receives the voice signal over the internet. It allows
communication in two ways on the broadcast network connection. It converts voice analog
signal to the digital signal and transmits it and vice-versa happens again. For the purpose of
voice transmission the routing, compression, and encapsulation.
Figure 15 Working of VoI
Source: (Yenra, 2004)
15
Secure Best Marks with AI Grader
Need help grading? Try our AI Grader for instant feedback on your assignments.
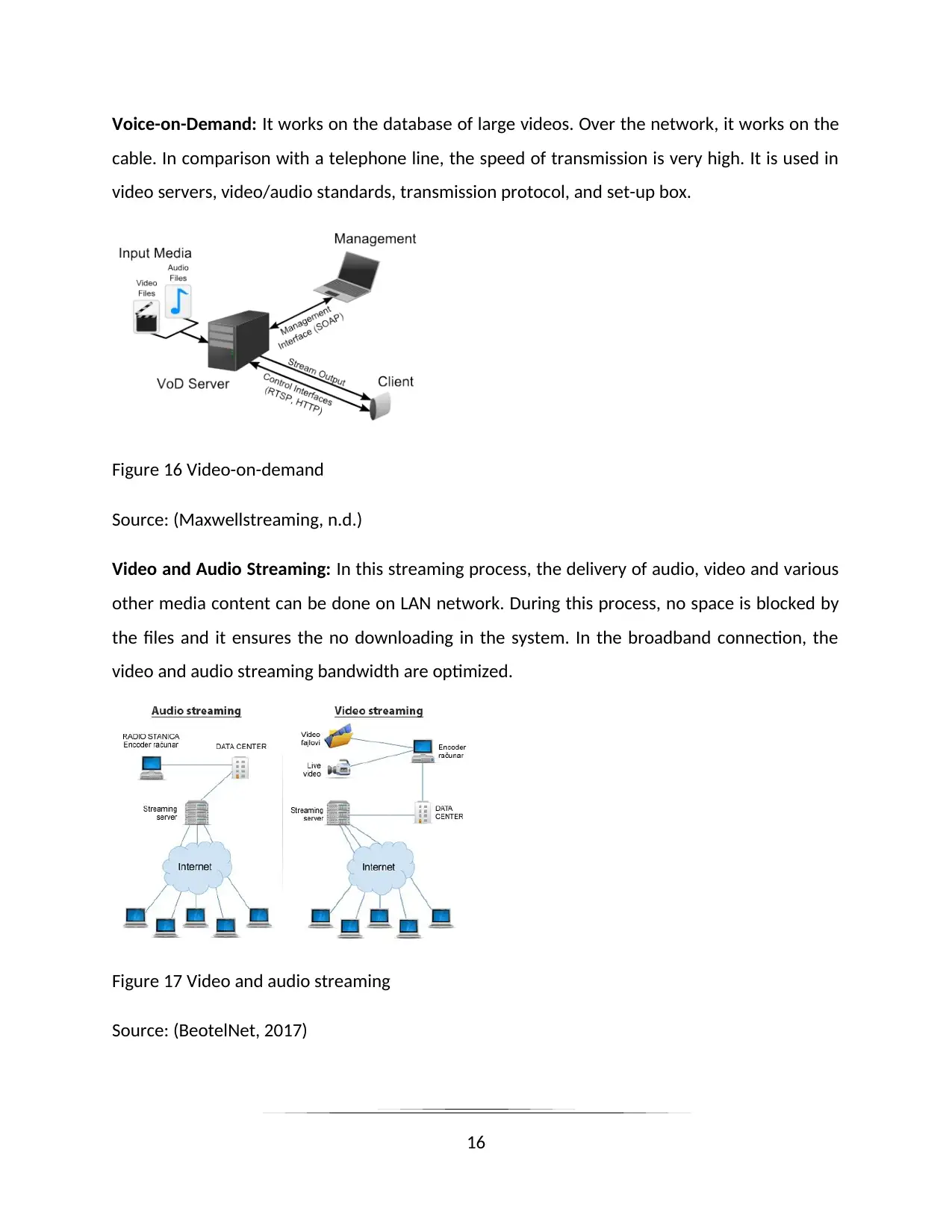
Voice-on-Demand: It works on the database of large videos. Over the network, it works on the
cable. In comparison with a telephone line, the speed of transmission is very high. It is used in
video servers, video/audio standards, transmission protocol, and set-up box.
Figure 16 Video-on-demand
Source: (Maxwellstreaming, n.d.)
Video and Audio Streaming: In this streaming process, the delivery of audio, video and various
other media content can be done on LAN network. During this process, no space is blocked by
the files and it ensures the no downloading in the system. In the broadband connection, the
video and audio streaming bandwidth are optimized.
Figure 17 Video and audio streaming
Source: (BeotelNet, 2017)
16
cable. In comparison with a telephone line, the speed of transmission is very high. It is used in
video servers, video/audio standards, transmission protocol, and set-up box.
Figure 16 Video-on-demand
Source: (Maxwellstreaming, n.d.)
Video and Audio Streaming: In this streaming process, the delivery of audio, video and various
other media content can be done on LAN network. During this process, no space is blocked by
the files and it ensures the no downloading in the system. In the broadband connection, the
video and audio streaming bandwidth are optimized.
Figure 17 Video and audio streaming
Source: (BeotelNet, 2017)
16

QOS: It is proposed on OSI model data-link layer. It manages traffic prioritization and bandwidth
which helps in reducing the delay in the network. Scheduling, service cost, policing, marking
and classification are managed by QoS for the delay in the network (ManageEngine, n.d.).
Quality-of-Service Implementation in LANS
802.1q frame tagging:
It is the standard of VLAN tagging which gives the protocol and interoperability. It is a working
of the inter_switch link that is encapsulated the FCS and mISL header.
DSCP (Differentiated Service Code Point):
The significant fields bit in DiffServ. It controls traffic management in QoS. The scalable and
simple mechanism is implemented which propose low-latency to the traffic web and network.
IP Precedence: It carries 8 bits in which first three value bits are for precedence. It carries a
higher value.
Table 3 IP Precedence Table
A.C 1.3 Discuss LAN concerns and make
recommendations to sustain network security, reliability, and performance
Performance of LAN can be measured using following factors:
17
Type of Service
000 Routine
001 Priority
010 Immediate
011 Flash
100 Flash Override
101 Critic/Critical
110 Internetwork Control
111 Network Control
which helps in reducing the delay in the network. Scheduling, service cost, policing, marking
and classification are managed by QoS for the delay in the network (ManageEngine, n.d.).
Quality-of-Service Implementation in LANS
802.1q frame tagging:
It is the standard of VLAN tagging which gives the protocol and interoperability. It is a working
of the inter_switch link that is encapsulated the FCS and mISL header.
DSCP (Differentiated Service Code Point):
The significant fields bit in DiffServ. It controls traffic management in QoS. The scalable and
simple mechanism is implemented which propose low-latency to the traffic web and network.
IP Precedence: It carries 8 bits in which first three value bits are for precedence. It carries a
higher value.
Table 3 IP Precedence Table
A.C 1.3 Discuss LAN concerns and make
recommendations to sustain network security, reliability, and performance
Performance of LAN can be measured using following factors:
17
Type of Service
000 Routine
001 Priority
010 Immediate
011 Flash
100 Flash Override
101 Critic/Critical
110 Internetwork Control
111 Network Control

Throughput:
The quantity of send and received packets are to measure by this. The throughput of LAN
network is impacted by TCP window congestion.
Latency:
Delay is measured in this case. For two-way communication, delay of round trips is used and
TCP/IP network is taken which sends the source of data and wait for the acknowledgment. It is
generally measured in mile sec (KeyCDN, 2016).
Packet Loss:
It means the packets did not reach the destination. Router Performance, hubs, switch, firewall
and link congestion and so many more are responsible for the loss of packets.
Bandwidth:
As LAN is usable in a limited area, it requires telecommunication line and high rates of data
transfer. Bandwidth makes the network smooth. For result for long-term, PRTG measurement is
used for bandwidth.
Jitter:
Measurement of the time difference is done by this in packet arrival time. It basically deals with
switched packet network in which the TCP/IP is responsible for the communication. Voice traffic
and VoIP are the type of jitters for load-balanced issued on the same track (Popeskic, n.d.).
Secure LAN Network:
Firewalls:
It works on the TCP/IP filter in between the LAN network and outside world. It configures with
some restrictions. Also known as security gates to manage sorts packets. It is integrated o the
hardware. It also provides system security.
VLAN:
18
The quantity of send and received packets are to measure by this. The throughput of LAN
network is impacted by TCP window congestion.
Latency:
Delay is measured in this case. For two-way communication, delay of round trips is used and
TCP/IP network is taken which sends the source of data and wait for the acknowledgment. It is
generally measured in mile sec (KeyCDN, 2016).
Packet Loss:
It means the packets did not reach the destination. Router Performance, hubs, switch, firewall
and link congestion and so many more are responsible for the loss of packets.
Bandwidth:
As LAN is usable in a limited area, it requires telecommunication line and high rates of data
transfer. Bandwidth makes the network smooth. For result for long-term, PRTG measurement is
used for bandwidth.
Jitter:
Measurement of the time difference is done by this in packet arrival time. It basically deals with
switched packet network in which the TCP/IP is responsible for the communication. Voice traffic
and VoIP are the type of jitters for load-balanced issued on the same track (Popeskic, n.d.).
Secure LAN Network:
Firewalls:
It works on the TCP/IP filter in between the LAN network and outside world. It configures with
some restrictions. Also known as security gates to manage sorts packets. It is integrated o the
hardware. It also provides system security.
VLAN:
18
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

It is basically a collection of a network of LAN that works on physical location and domain
broadcast which defined the network access restriction. The untagged traffic is sent and
received.
Access Control List:
It is the list used by switch or routers. The data flow is prohibited and allowed on the interface
of the network by this list. ACL is configured on interface network and then-then the data is
checked.
Encryption: It is the technology that is used to secure the data communication in the FootFall
Field Marketing Ltd network. To encrypt and decrypt the data, it uses the public and private
key. When an organization creates the data communication, the network applies the encryption
technology.
Wireless security: For providing the wireless security it uses the network security tool. Mainly it
is suing to protect the wireless security and also used to secure the wired equivalent privacy.
Switch Port control: This is the feature which is required to secure the network from the
attackers and threats. The switch port addresses the sending data traffic in the FootFall Field
Marketing Ltd network. The switch port helps the FootFall Field Marketing Ltd network to
provide the security by securing the systems of FootFall Field Marketing Ltd.
M1: I have successfully achieved merit point in task 1.1 and 1.2. I have explained briefly about
techniques used for LAN network technologies. I have also explained different traffic intensive
services and their performances.
LO2 - Be able to design LAN infrastructures
A.C 2.1 Design a LAN infrastructure to meet a given requirement
The LAN network is designed by me for the organization of FootFall Marketing Field in which
they required 3 offices and they are connected with each other. On the IP address of class C, the
required network protocol is used to manage the LAN infrastructure efficiently and reliably. On
the network of the organization, it manages the traffic and data flow.
19
broadcast which defined the network access restriction. The untagged traffic is sent and
received.
Access Control List:
It is the list used by switch or routers. The data flow is prohibited and allowed on the interface
of the network by this list. ACL is configured on interface network and then-then the data is
checked.
Encryption: It is the technology that is used to secure the data communication in the FootFall
Field Marketing Ltd network. To encrypt and decrypt the data, it uses the public and private
key. When an organization creates the data communication, the network applies the encryption
technology.
Wireless security: For providing the wireless security it uses the network security tool. Mainly it
is suing to protect the wireless security and also used to secure the wired equivalent privacy.
Switch Port control: This is the feature which is required to secure the network from the
attackers and threats. The switch port addresses the sending data traffic in the FootFall Field
Marketing Ltd network. The switch port helps the FootFall Field Marketing Ltd network to
provide the security by securing the systems of FootFall Field Marketing Ltd.
M1: I have successfully achieved merit point in task 1.1 and 1.2. I have explained briefly about
techniques used for LAN network technologies. I have also explained different traffic intensive
services and their performances.
LO2 - Be able to design LAN infrastructures
A.C 2.1 Design a LAN infrastructure to meet a given requirement
The LAN network is designed by me for the organization of FootFall Marketing Field in which
they required 3 offices and they are connected with each other. On the IP address of class C, the
required network protocol is used to manage the LAN infrastructure efficiently and reliably. On
the network of the organization, it manages the traffic and data flow.
19
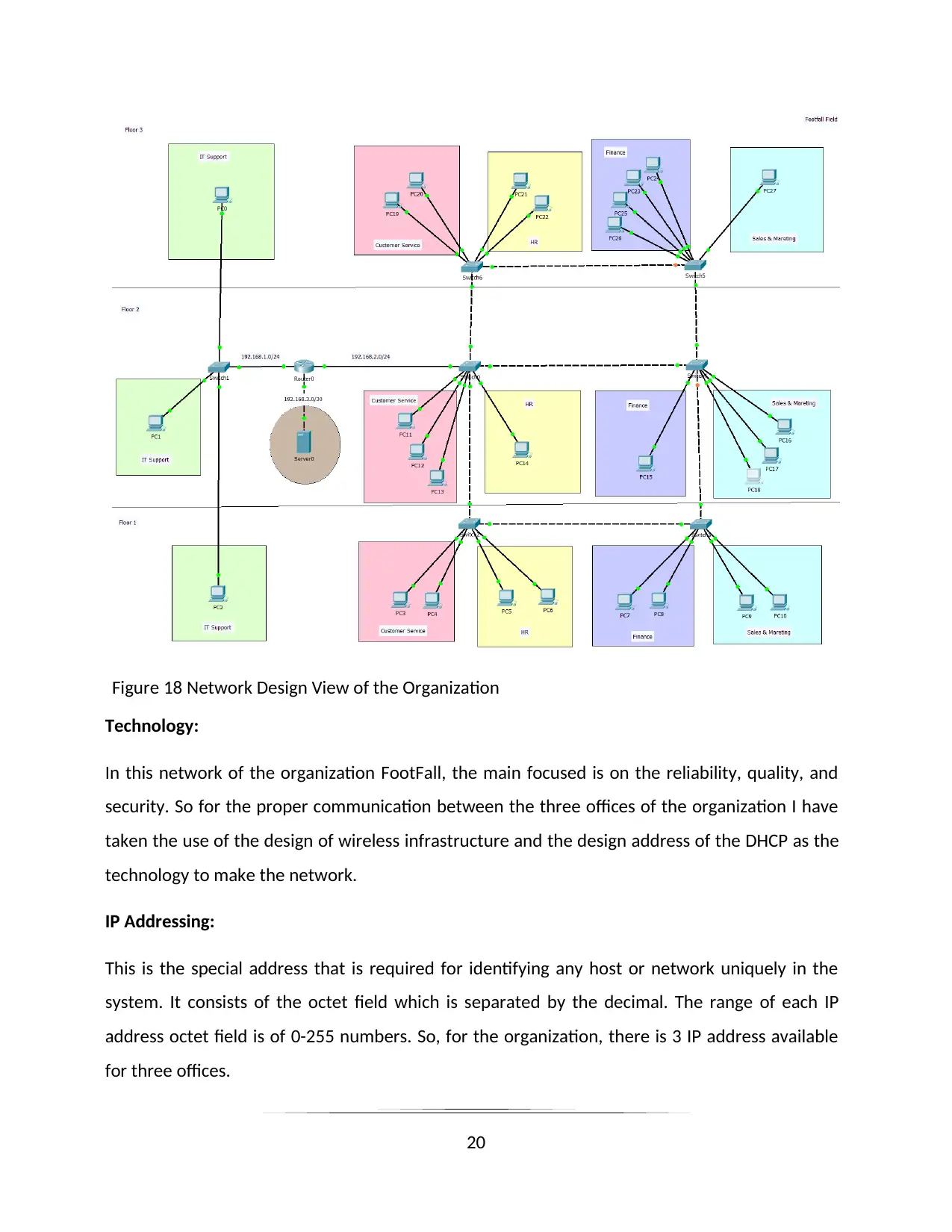
Figure 18 Network Design View of the Organization
Technology:
In this network of the organization FootFall, the main focused is on the reliability, quality, and
security. So for the proper communication between the three offices of the organization I have
taken the use of the design of wireless infrastructure and the design address of the DHCP as the
technology to make the network.
IP Addressing:
This is the special address that is required for identifying any host or network uniquely in the
system. It consists of the octet field which is separated by the decimal. The range of each IP
address octet field is of 0-255 numbers. So, for the organization, there is 3 IP address available
for three offices.
20
Technology:
In this network of the organization FootFall, the main focused is on the reliability, quality, and
security. So for the proper communication between the three offices of the organization I have
taken the use of the design of wireless infrastructure and the design address of the DHCP as the
technology to make the network.
IP Addressing:
This is the special address that is required for identifying any host or network uniquely in the
system. It consists of the octet field which is separated by the decimal. The range of each IP
address octet field is of 0-255 numbers. So, for the organization, there is 3 IP address available
for three offices.
20
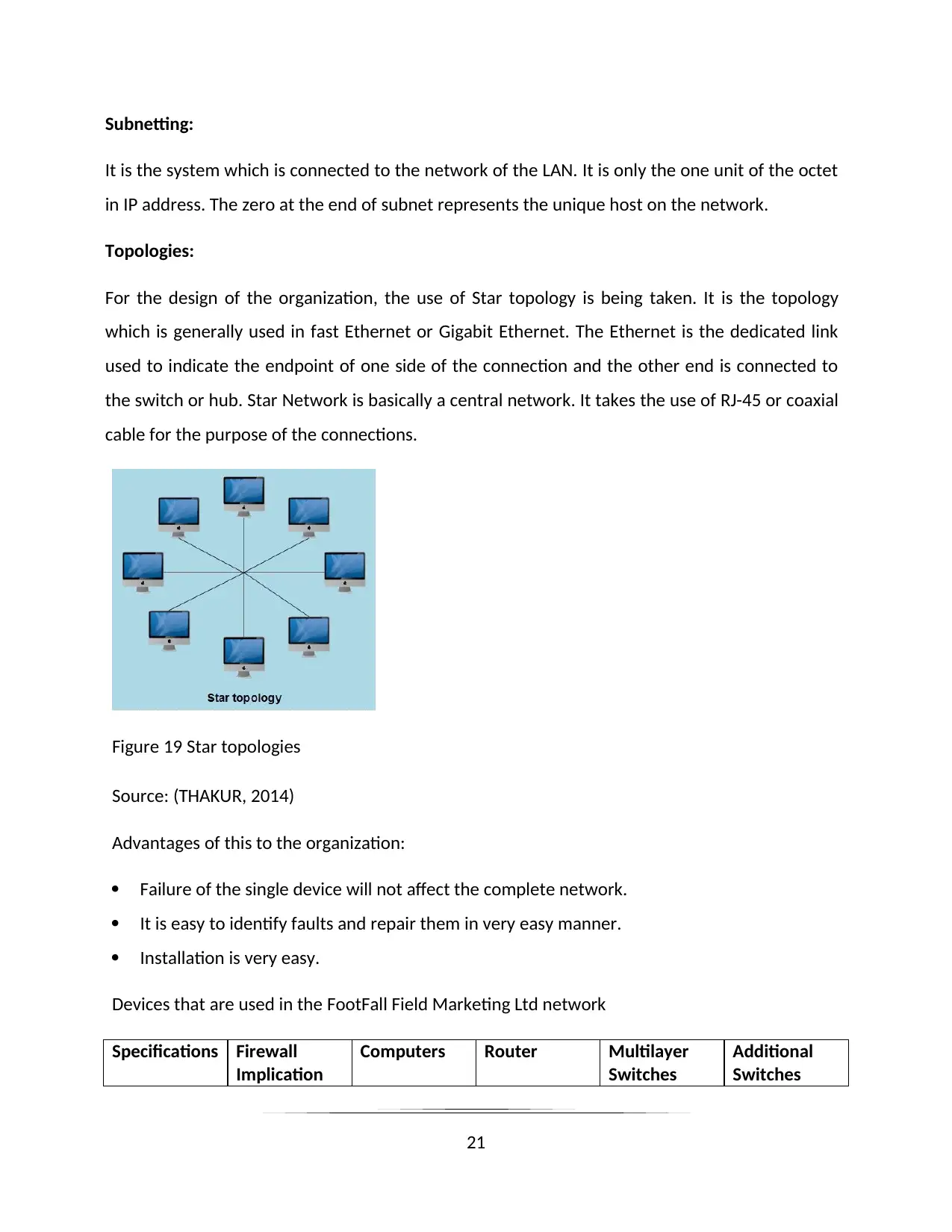
Subnetting:
It is the system which is connected to the network of the LAN. It is only the one unit of the octet
in IP address. The zero at the end of subnet represents the unique host on the network.
Topologies:
For the design of the organization, the use of Star topology is being taken. It is the topology
which is generally used in fast Ethernet or Gigabit Ethernet. The Ethernet is the dedicated link
used to indicate the endpoint of one side of the connection and the other end is connected to
the switch or hub. Star Network is basically a central network. It takes the use of RJ-45 or coaxial
cable for the purpose of the connections.
Figure 19 Star topologies
Source: (THAKUR, 2014)
Advantages of this to the organization:
Failure of the single device will not affect the complete network.
It is easy to identify faults and repair them in very easy manner.
Installation is very easy.
Devices that are used in the FootFall Field Marketing Ltd network
Specifications Firewall
Implication
Computers Router Multilayer
Switches
Additional
Switches
21
It is the system which is connected to the network of the LAN. It is only the one unit of the octet
in IP address. The zero at the end of subnet represents the unique host on the network.
Topologies:
For the design of the organization, the use of Star topology is being taken. It is the topology
which is generally used in fast Ethernet or Gigabit Ethernet. The Ethernet is the dedicated link
used to indicate the endpoint of one side of the connection and the other end is connected to
the switch or hub. Star Network is basically a central network. It takes the use of RJ-45 or coaxial
cable for the purpose of the connections.
Figure 19 Star topologies
Source: (THAKUR, 2014)
Advantages of this to the organization:
Failure of the single device will not affect the complete network.
It is easy to identify faults and repair them in very easy manner.
Installation is very easy.
Devices that are used in the FootFall Field Marketing Ltd network
Specifications Firewall
Implication
Computers Router Multilayer
Switches
Additional
Switches
21
Secure Best Marks with AI Grader
Need help grading? Try our AI Grader for instant feedback on your assignments.
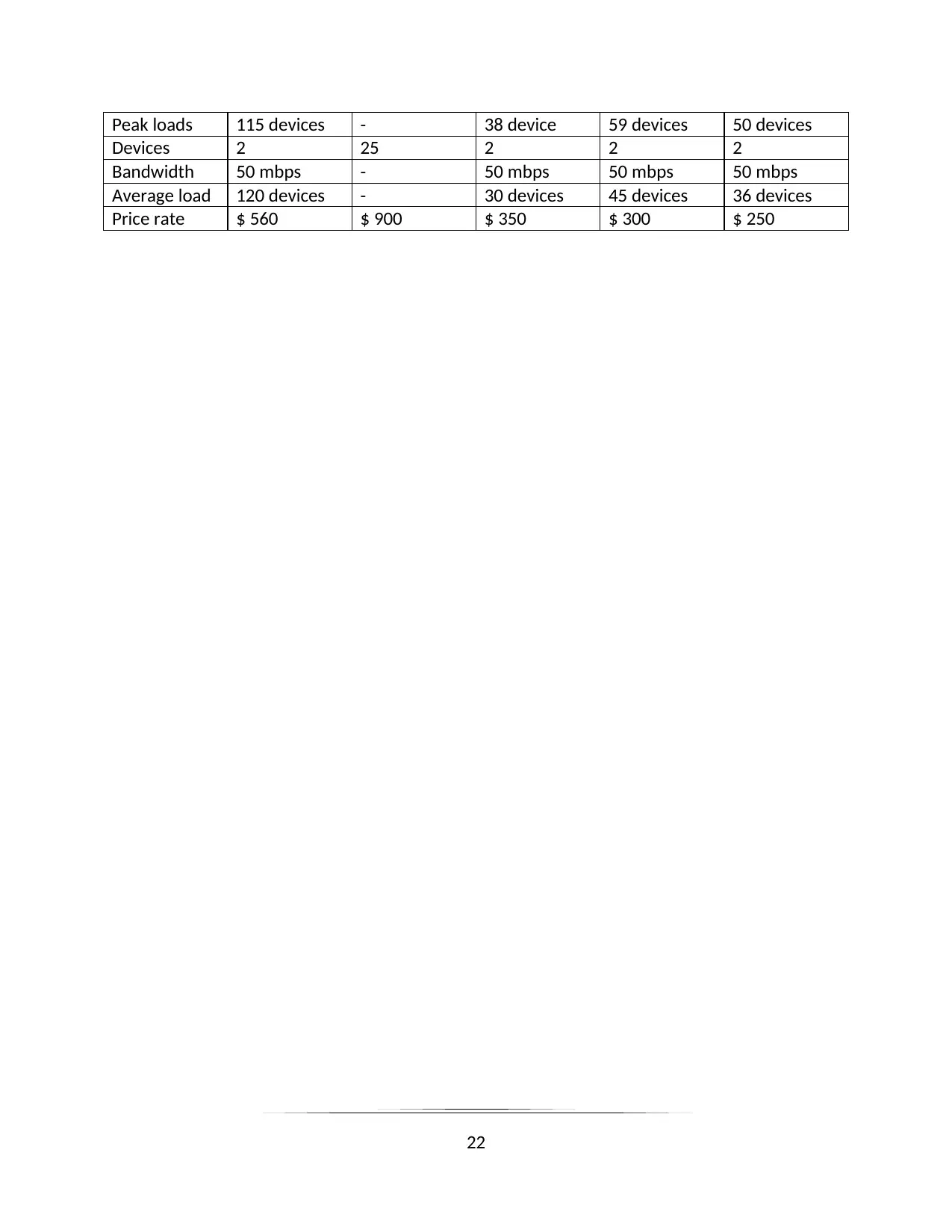
Peak loads 115 devices - 38 device 59 devices 50 devices
Devices 2 25 2 2 2
Bandwidth 50 mbps - 50 mbps 50 mbps 50 mbps
Average load 120 devices - 30 devices 45 devices 36 devices
Price rate $ 560 $ 900 $ 350 $ 300 $ 250
22
Devices 2 25 2 2 2
Bandwidth 50 mbps - 50 mbps 50 mbps 50 mbps
Average load 120 devices - 30 devices 45 devices 36 devices
Price rate $ 560 $ 900 $ 350 $ 300 $ 250
22

A.C 2.2 critically evaluate the suitability of LAN components
The implementation of the LAN network is being designed for the organization of FootFall
Marketing Field by taking the use of the DHCP servers; DNS switch servers, web servers, and
routers. The components of the LAN system are being evaluated on the following factors:
Scalability:
Horizontal: In the network of the LAN system, the parallel traffic, memory secession, state, and
the cache is being managed by the applications. The user information is being maintained by the
session that controls heavy loads to check the states of the server.
Vertical: The size of the RAM can be raised to balance the amount of load in the network of LAN
that is used to help the calls through the algorithm of routing. It depends on various servers.
Security:
The organization design is very much complex and needs to have the strong security on the
network or LAN to get out with the problems like a firewall issue or the communication issue. As
the firewalls are required to provide the high security to the network and act as a guard
between the receiver and sender. Also, it provides the service of packet filtering. Only the
authorized user can access the packets. For the purpose of the security, a network needs a
cryptography, routers, and modems.
Availability:
The network must be highly available for the system as the connection between all the office
requires all the times. The topography is also been checked for availability. The network must be
recoverable from the failure of components of the single unit. The factors of this are
temperature fluctuation, downtime and reboot time.
M2: I have successfully achieved merit point in task 2.1 and 2.2. I have used different techniques
to design the network infrastructure and also applied different theories to explain the suitability
of components of the LAN Network.
23
The implementation of the LAN network is being designed for the organization of FootFall
Marketing Field by taking the use of the DHCP servers; DNS switch servers, web servers, and
routers. The components of the LAN system are being evaluated on the following factors:
Scalability:
Horizontal: In the network of the LAN system, the parallel traffic, memory secession, state, and
the cache is being managed by the applications. The user information is being maintained by the
session that controls heavy loads to check the states of the server.
Vertical: The size of the RAM can be raised to balance the amount of load in the network of LAN
that is used to help the calls through the algorithm of routing. It depends on various servers.
Security:
The organization design is very much complex and needs to have the strong security on the
network or LAN to get out with the problems like a firewall issue or the communication issue. As
the firewalls are required to provide the high security to the network and act as a guard
between the receiver and sender. Also, it provides the service of packet filtering. Only the
authorized user can access the packets. For the purpose of the security, a network needs a
cryptography, routers, and modems.
Availability:
The network must be highly available for the system as the connection between all the office
requires all the times. The topography is also been checked for availability. The network must be
recoverable from the failure of components of the single unit. The factors of this are
temperature fluctuation, downtime and reboot time.
M2: I have successfully achieved merit point in task 2.1 and 2.2. I have used different techniques
to design the network infrastructure and also applied different theories to explain the suitability
of components of the LAN Network.
23

LO3- Be able to implement LAN infrastructures
A.C 3.1 Build and configure a LAN (including services) to meet a given requirement
The designing of this network of the FootFall Marketing Field company required VoIP, switches,
Router, and IP Routing for the purpose of implementation. It is implemented in the
environment of the Cisco Packet Tracer. The routers used in the design are of CISCO 2814 and
also series of the switch are catalyst 2890.
Communication device installations:
Routers, cabling, switch, a cable connector, access points, network software and the network
medium are used for the network of the organization.
The configuration of the Local Client:
The explanation of the configuration of local client is given here:
1. In the option of Networking, select LAN network and then select IPv4 LAN option in that.
2. Enter the name of the host in the field of hostname; it consists of hyphen, numbers, and
letters.
3. Now after doing this, apply changes by clicking save button.
24
A.C 3.1 Build and configure a LAN (including services) to meet a given requirement
The designing of this network of the FootFall Marketing Field company required VoIP, switches,
Router, and IP Routing for the purpose of implementation. It is implemented in the
environment of the Cisco Packet Tracer. The routers used in the design are of CISCO 2814 and
also series of the switch are catalyst 2890.
Communication device installations:
Routers, cabling, switch, a cable connector, access points, network software and the network
medium are used for the network of the organization.
The configuration of the Local Client:
The explanation of the configuration of local client is given here:
1. In the option of Networking, select LAN network and then select IPv4 LAN option in that.
2. Enter the name of the host in the field of hostname; it consists of hyphen, numbers, and
letters.
3. Now after doing this, apply changes by clicking save button.
24
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
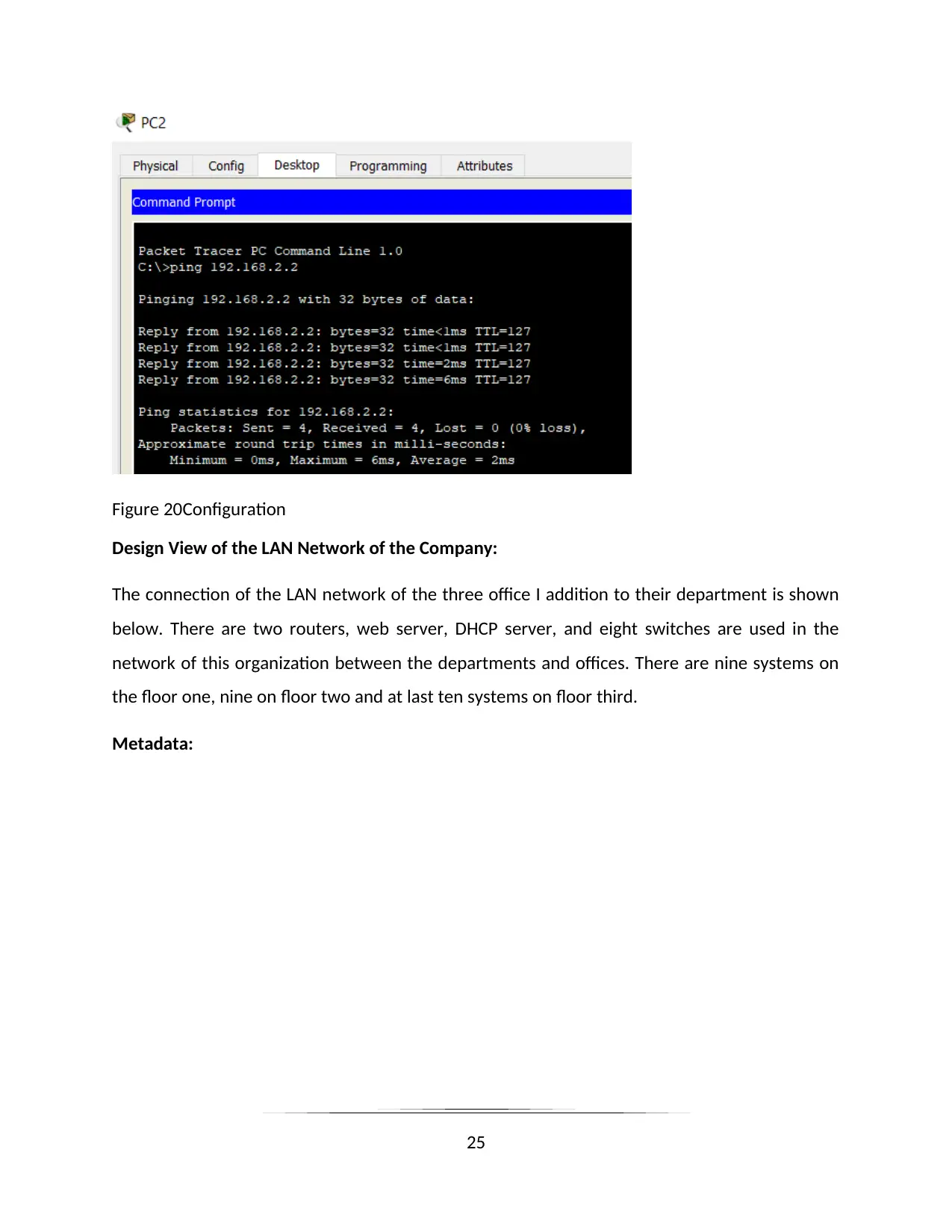
Figure 20Configuration
Design View of the LAN Network of the Company:
The connection of the LAN network of the three office I addition to their department is shown
below. There are two routers, web server, DHCP server, and eight switches are used in the
network of this organization between the departments and offices. There are nine systems on
the floor one, nine on floor two and at last ten systems on floor third.
Metadata:
25
Design View of the LAN Network of the Company:
The connection of the LAN network of the three office I addition to their department is shown
below. There are two routers, web server, DHCP server, and eight switches are used in the
network of this organization between the departments and offices. There are nine systems on
the floor one, nine on floor two and at last ten systems on floor third.
Metadata:
25

26

Figure 21 Router configuration
27
27
Secure Best Marks with AI Grader
Need help grading? Try our AI Grader for instant feedback on your assignments.
28
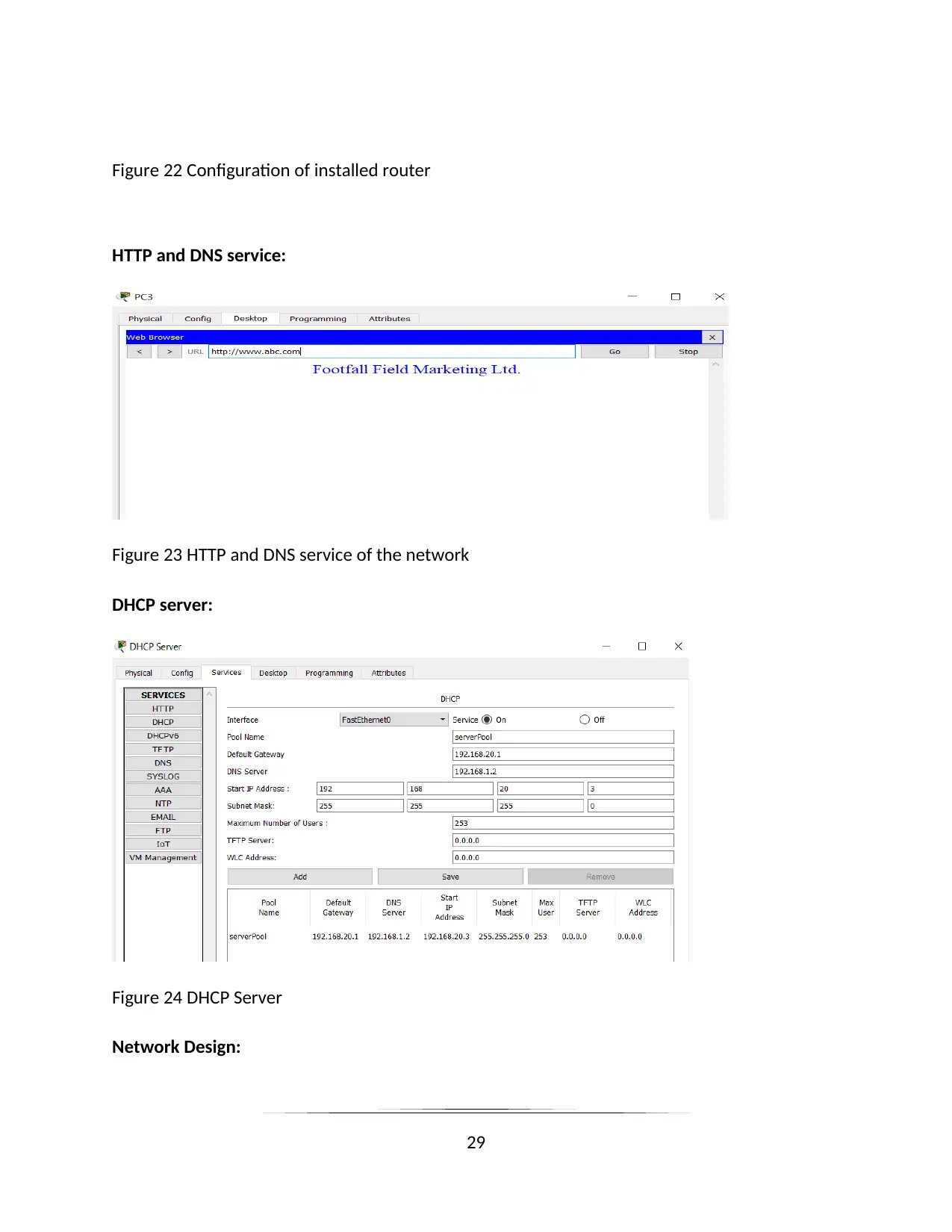
Figure 22 Configuration of installed router
HTTP and DNS service:
Figure 23 HTTP and DNS service of the network
DHCP server:
Figure 24 DHCP Server
Network Design:
29
HTTP and DNS service:
Figure 23 HTTP and DNS service of the network
DHCP server:
Figure 24 DHCP Server
Network Design:
29
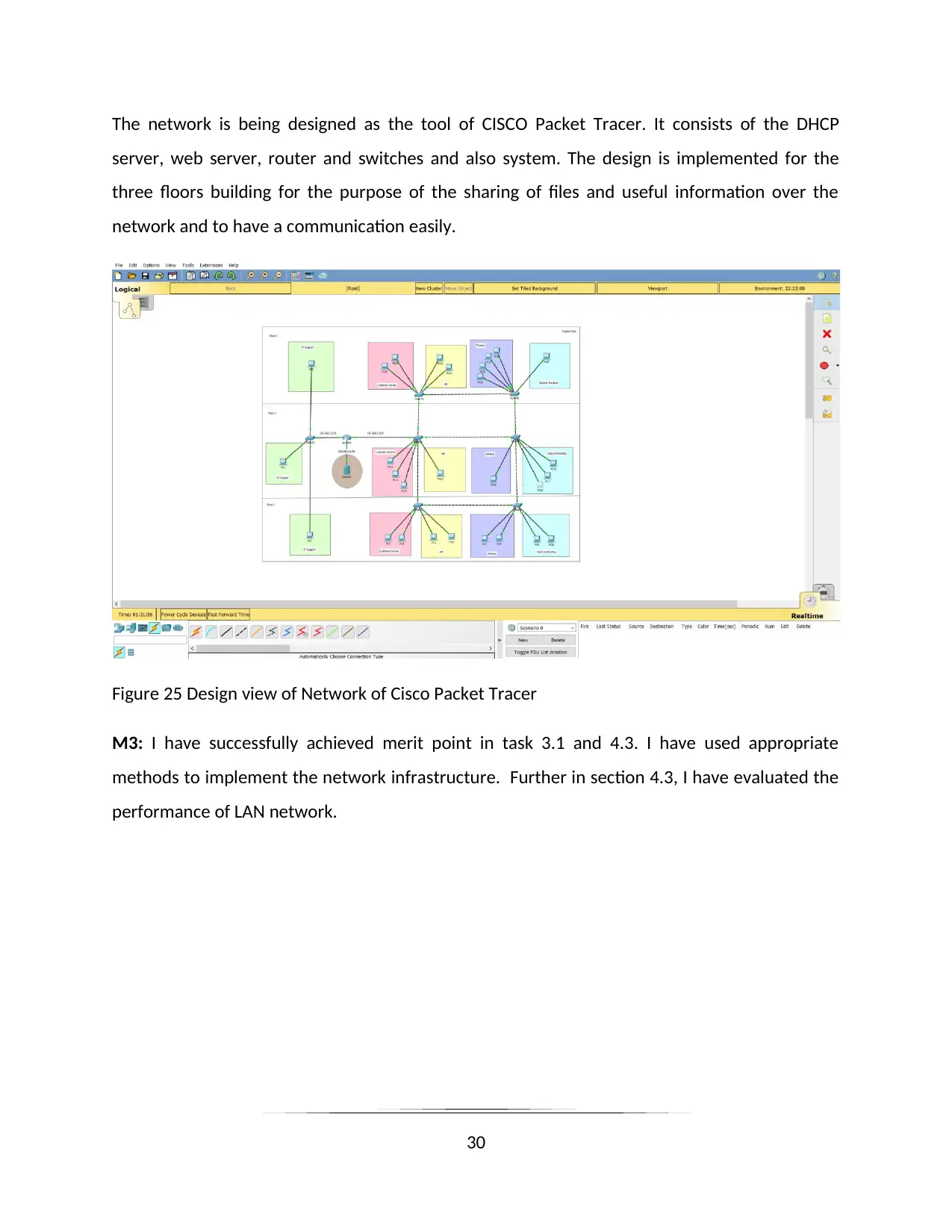
The network is being designed as the tool of CISCO Packet Tracer. It consists of the DHCP
server, web server, router and switches and also system. The design is implemented for the
three floors building for the purpose of the sharing of files and useful information over the
network and to have a communication easily.
Figure 25 Design view of Network of Cisco Packet Tracer
M3: I have successfully achieved merit point in task 3.1 and 4.3. I have used appropriate
methods to implement the network infrastructure. Further in section 4.3, I have evaluated the
performance of LAN network.
30
server, web server, router and switches and also system. The design is implemented for the
three floors building for the purpose of the sharing of files and useful information over the
network and to have a communication easily.
Figure 25 Design view of Network of Cisco Packet Tracer
M3: I have successfully achieved merit point in task 3.1 and 4.3. I have used appropriate
methods to implement the network infrastructure. Further in section 4.3, I have evaluated the
performance of LAN network.
30
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

A.C 3.2 Implement network security on a LAN
The security is the most common and useful feature when we talk about the LAN networking
because it carries and transfers the useful and sensitive data which can affect the goals of the
organization (Beal, n.d.). The security on this company LAN network is high. It is as follows:
Port Filter/Blocking:
The information is presented in the form of packets in the system of LAN network. Firewalls are
used as the safety guard from the unauthorized access of information from the intruder. The
internal security can be harmed by the connection of internet.
Authentication:
It is required to secure the process of authorization. It ensures the usability of the right user
into the network.
Encryption:
It is the most common method to provide security to the network. Also, it can be used for the
purpose of security. It does not allow the wrong or unauthorized user to have access to the
network. The cryptography is the technique which is mostly used for the process of encryption.
VLANs:
Sensitive information or data is being shared over the network in the system through the
process of the broadcast by the user. So for the system, we require having the network which is
highly secured and which do not allow any unauthorized user to access over the network
without getting the permission. The VLAN is required to control the broadcast domains,
intrusion information, and firewalls and restrict access.
Router configuration:
The use of two routers is taken to develop this network. The traffic and direction of the traffic
are being managed by these routers and the routers carry forward the packets over the
network.
31
The security is the most common and useful feature when we talk about the LAN networking
because it carries and transfers the useful and sensitive data which can affect the goals of the
organization (Beal, n.d.). The security on this company LAN network is high. It is as follows:
Port Filter/Blocking:
The information is presented in the form of packets in the system of LAN network. Firewalls are
used as the safety guard from the unauthorized access of information from the intruder. The
internal security can be harmed by the connection of internet.
Authentication:
It is required to secure the process of authorization. It ensures the usability of the right user
into the network.
Encryption:
It is the most common method to provide security to the network. Also, it can be used for the
purpose of security. It does not allow the wrong or unauthorized user to have access to the
network. The cryptography is the technique which is mostly used for the process of encryption.
VLANs:
Sensitive information or data is being shared over the network in the system through the
process of the broadcast by the user. So for the system, we require having the network which is
highly secured and which do not allow any unauthorized user to access over the network
without getting the permission. The VLAN is required to control the broadcast domains,
intrusion information, and firewalls and restrict access.
Router configuration:
The use of two routers is taken to develop this network. The traffic and direction of the traffic
are being managed by these routers and the routers carry forward the packets over the
network.
31

32

Figure 26 Configuration
33
33
Secure Best Marks with AI Grader
Need help grading? Try our AI Grader for instant feedback on your assignments.

DHCP configuration: It is the management of network protocol which is being used by the
servers of DHCP. The assignment of IP address and the parameters of configuration is given for
communication purpose.
34
servers of DHCP. The assignment of IP address and the parameters of configuration is given for
communication purpose.
34
A.C 3.3 critically review and test a LAN
I have performed some test case on the network of the organization of FootFall Marketing Field
to check its stability and correctness.
35
I have performed some test case on the network of the organization of FootFall Marketing Field
to check its stability and correctness.
35
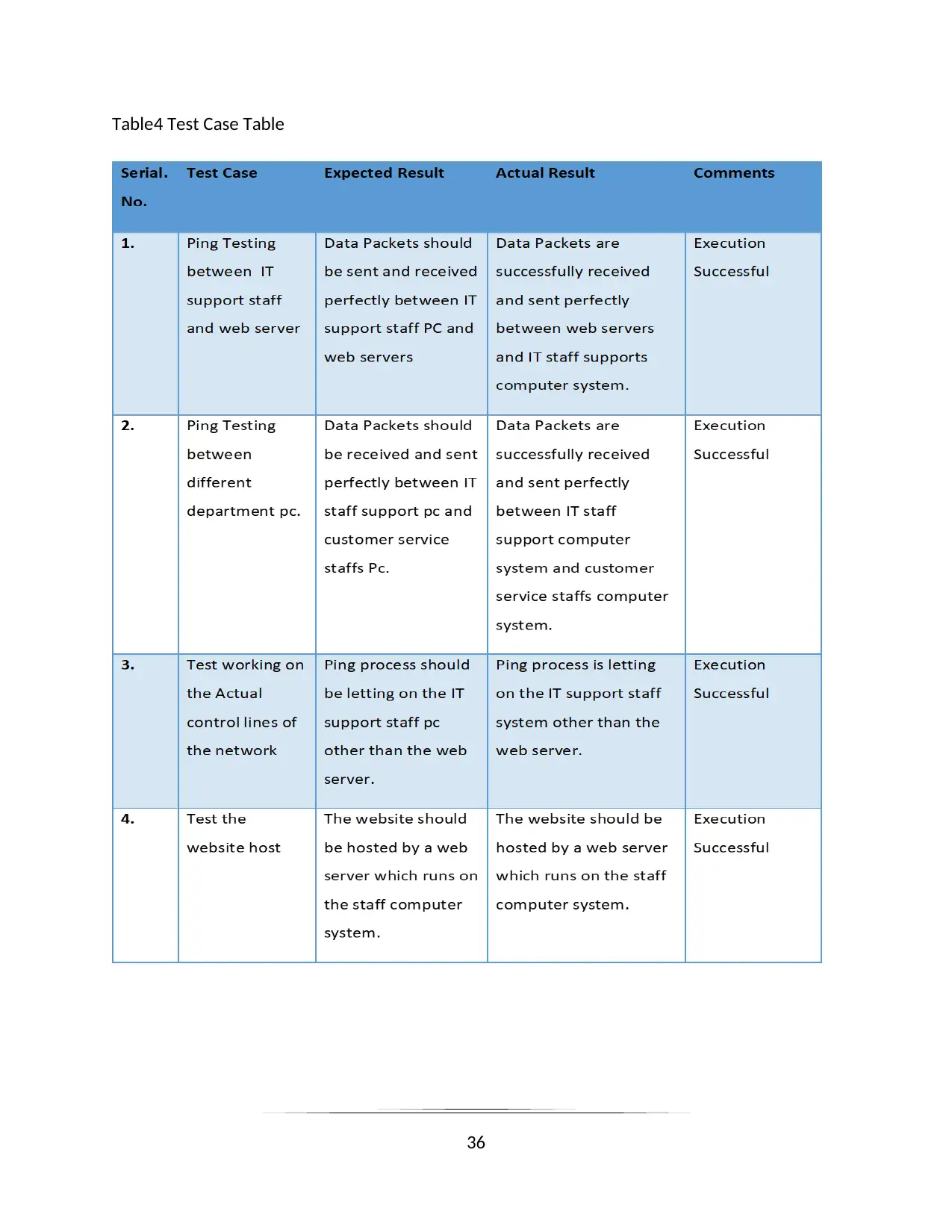
Table4 Test Case Table
36
36
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
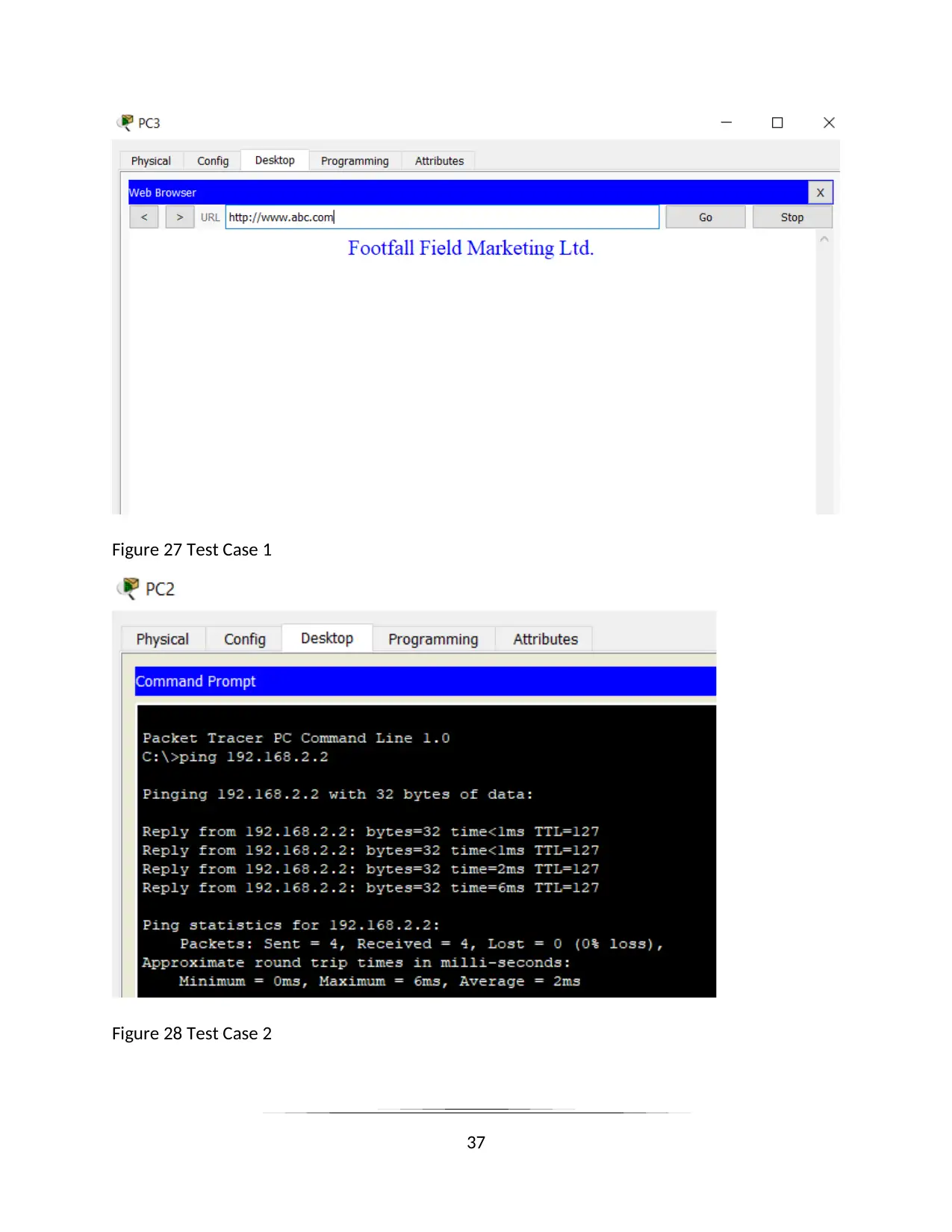
Figure 27 Test Case 1
Figure 28 Test Case 2
37
Figure 28 Test Case 2
37
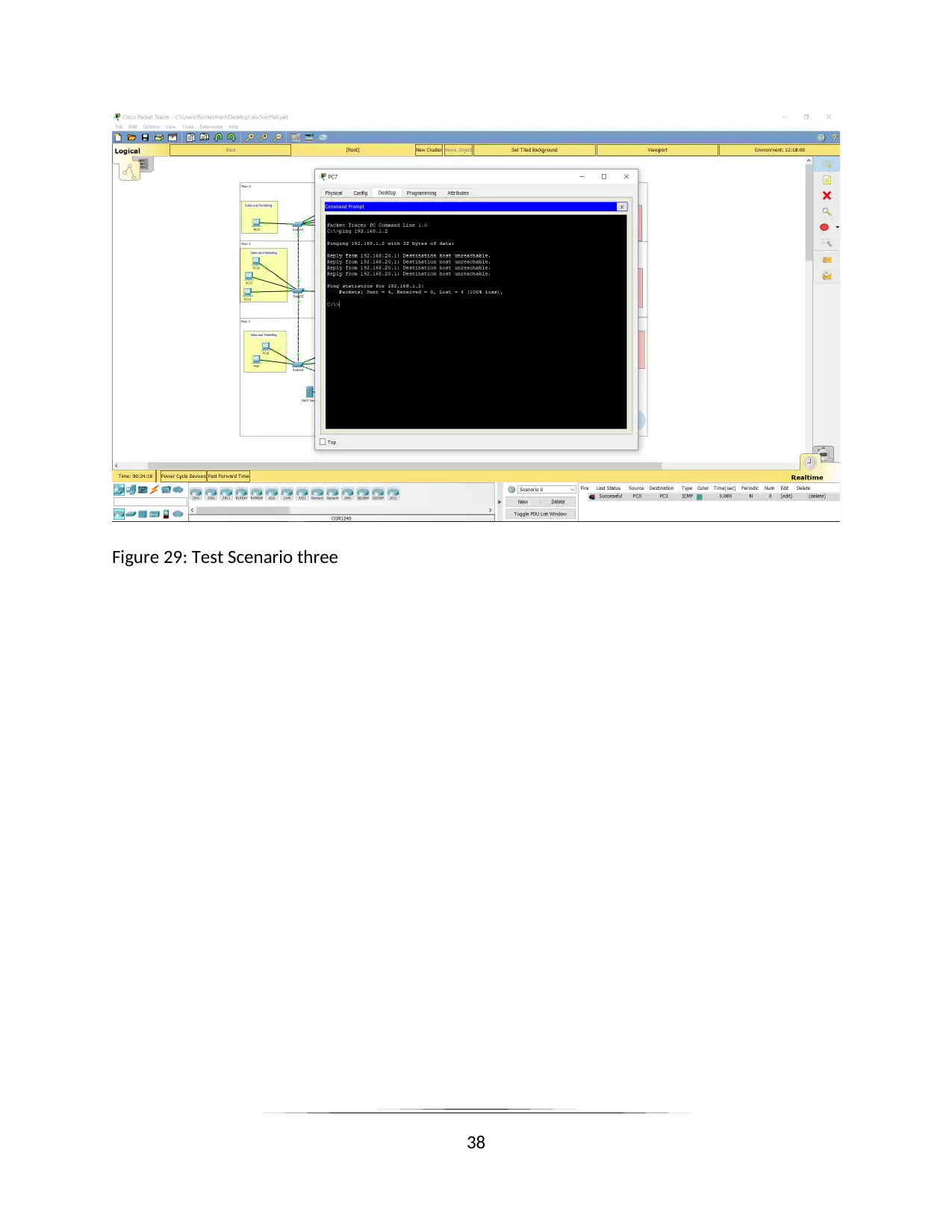
Figure 29: Test Scenario three
38
38

LO4- Be able to manage LAN infrastructures.
AC 4.1 Monitor and troubleshoot a LAN
The performance and reliability of the LAN System are improved by monitor process and
troubleshoot process. To monitor the system and to troubleshoot it there is various software
available.
Monitoring Tools:
The network of the LAN system proposed the topology services, MiniRMON tools, fault monitor
an event monitor which are monitored on the ports, links, events, and fault of the network. It
also performs the remote monitor functions (Smith, 2015).
Troubleshooting Tools:
A network of LAN proposed Netshow, workflow troubleshooting tool and VRF-lite which are
offered to troubleshoot the connectivity in the network, diagnose device problem,
authentication of the end-to-end connection and to identify the end issue of the devices which
are VRF configured.
Some software for the purpose of troubleshooting and monitor a network of LAN are:
PulseWay: This software monitor the network over anyplace and at any time. It provides
security to the software.
PRTG: It is the software which is used for the traffic monitoring and the components
scanning.
ManageEngine OpManager: It is used for the monitoring of emails, plugins, and emails.
It is comparatively expensive.
39
AC 4.1 Monitor and troubleshoot a LAN
The performance and reliability of the LAN System are improved by monitor process and
troubleshoot process. To monitor the system and to troubleshoot it there is various software
available.
Monitoring Tools:
The network of the LAN system proposed the topology services, MiniRMON tools, fault monitor
an event monitor which are monitored on the ports, links, events, and fault of the network. It
also performs the remote monitor functions (Smith, 2015).
Troubleshooting Tools:
A network of LAN proposed Netshow, workflow troubleshooting tool and VRF-lite which are
offered to troubleshoot the connectivity in the network, diagnose device problem,
authentication of the end-to-end connection and to identify the end issue of the devices which
are VRF configured.
Some software for the purpose of troubleshooting and monitor a network of LAN are:
PulseWay: This software monitor the network over anyplace and at any time. It provides
security to the software.
PRTG: It is the software which is used for the traffic monitoring and the components
scanning.
ManageEngine OpManager: It is used for the monitoring of emails, plugins, and emails.
It is comparatively expensive.
39
Secure Best Marks with AI Grader
Need help grading? Try our AI Grader for instant feedback on your assignments.

AC 4.2 Resolve LAN issues to improve security, reliability, and performance
There are some issues related to the LAN security, performance, and reliability.
Resolving Issues related to the Security:
The biggest challenge faced by any network is of security which can be resolved by various
techniques like authorization, authentication and also through anti-virus. A framework is set for
the LAN network.
The more use of authentication, encryption, and authorization is taken to make the
password more protected.
Firewall is being implemented on the network of the firewall.
Proxy Server is being monitored.
The latest antivirus is updated on every network system. The use of spyware and filters
were taken in frequent time.
The system is enhanced with the logging to make server machine more secure.
Resolving Issues related to the reliability and performance:
Also, we know that the major issues are of reliability and performance in the network. This can
be resolved using the LAN cards, Devices and subnets. Some process to take for enhancing the
performance and reliability.
RAM is being increased of the system.
Perform the division on the subnet network to balance the load.
To scan the rate of the system use of router has been taken.
Browser history is being deleted to resolve the performance and reliability.
LAN card has been installed to raise the speed to 100 Mbps.
Switch used is taken rather than a hub.
Separate gateways are formed and arranged to identify system uniquely.
The waste application is removed from the system (Withers, 2005).
40
There are some issues related to the LAN security, performance, and reliability.
Resolving Issues related to the Security:
The biggest challenge faced by any network is of security which can be resolved by various
techniques like authorization, authentication and also through anti-virus. A framework is set for
the LAN network.
The more use of authentication, encryption, and authorization is taken to make the
password more protected.
Firewall is being implemented on the network of the firewall.
Proxy Server is being monitored.
The latest antivirus is updated on every network system. The use of spyware and filters
were taken in frequent time.
The system is enhanced with the logging to make server machine more secure.
Resolving Issues related to the reliability and performance:
Also, we know that the major issues are of reliability and performance in the network. This can
be resolved using the LAN cards, Devices and subnets. Some process to take for enhancing the
performance and reliability.
RAM is being increased of the system.
Perform the division on the subnet network to balance the load.
To scan the rate of the system use of router has been taken.
Browser history is being deleted to resolve the performance and reliability.
LAN card has been installed to raise the speed to 100 Mbps.
Switch used is taken rather than a hub.
Separate gateways are formed and arranged to identify system uniquely.
The waste application is removed from the system (Withers, 2005).
40

AC 4.3 Critically evaluate the performance of a LAN
LAN can have various different problems related to the bandwidth, device, connection, and
speed. So here are some steps taken to enhance the network performance:
Router speed and switch port are checked to enhance the performance.
The single or common problems caused by the system network is being recognized
which always lack the performance and cause trouble and error.
The setting and configuration must be routinely checked to enhance the performance as
it can lead to time cause.
A number of application is being used on the network which needs to be analyzed and
judged. So the application must be free from any threat or error or cause to maintain
the performance of the system network.
Use of routing table must be taken in order to achieve the best routing path and to
upgrade the performance.
The use of backup system must be taken in order to achieve the smooth functioning of
the network. If it fails it can lead to data synchronization problem in the network.
SNMP stream is used by the network to rectify the problem of routers which can be the
long-term problem if not taken care properly and can lead to the downfall of the system
performance.
41
LAN can have various different problems related to the bandwidth, device, connection, and
speed. So here are some steps taken to enhance the network performance:
Router speed and switch port are checked to enhance the performance.
The single or common problems caused by the system network is being recognized
which always lack the performance and cause trouble and error.
The setting and configuration must be routinely checked to enhance the performance as
it can lead to time cause.
A number of application is being used on the network which needs to be analyzed and
judged. So the application must be free from any threat or error or cause to maintain
the performance of the system network.
Use of routing table must be taken in order to achieve the best routing path and to
upgrade the performance.
The use of backup system must be taken in order to achieve the smooth functioning of
the network. If it fails it can lead to data synchronization problem in the network.
SNMP stream is used by the network to rectify the problem of routers which can be the
long-term problem if not taken care properly and can lead to the downfall of the system
performance.
41

Conclusion:
In the complete assignment of LAN, I have discussed various points and implemented a LAN
network for the company FootFall Marketing Field. The implementation of the network is done
on the tool of Cisco Packet Tracer. This tool helps in adding and connecting various different
devices network. The organization network will resolve the performance, security and reliability
issue. Also, it will offer the connection of various department of the different floor of the same
building.
In the first section of this assignment, I have discussed all the theoretical concept of the
network of LAN, technology, types, and other features that can help the company to
understand the LAN network. In the second part, I have implemented the network for the
company. Further, in the third section, I have built the security standards and test the LAN
network for various test cases. In the last section, I have performed the action of
troubleshooting and monitor process and then recognized security, performance, and reliability
problem and after that resolved it on the network. Also, at last, I have discussed the
performance of LAN network.
42
In the complete assignment of LAN, I have discussed various points and implemented a LAN
network for the company FootFall Marketing Field. The implementation of the network is done
on the tool of Cisco Packet Tracer. This tool helps in adding and connecting various different
devices network. The organization network will resolve the performance, security and reliability
issue. Also, it will offer the connection of various department of the different floor of the same
building.
In the first section of this assignment, I have discussed all the theoretical concept of the
network of LAN, technology, types, and other features that can help the company to
understand the LAN network. In the second part, I have implemented the network for the
company. Further, in the third section, I have built the security standards and test the LAN
network for various test cases. In the last section, I have performed the action of
troubleshooting and monitor process and then recognized security, performance, and reliability
problem and after that resolved it on the network. Also, at last, I have discussed the
performance of LAN network.
42
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

References
Beal, V. n.d. What is Network Security? Webopedia Definition. [online] Webopedia.
Available at: https://www.webopedia.com/TERM/N/network_security.html [Accessed
27 Mar. 2018].
BeotelNet. 2017. Media streaming - audio and video. [online] Available at:
https://www.beotel.net/streaming [Accessed 23 Mar. 2018].
Carter, A. 2012. Different Types of Switches - Network Switches. [online] Eye web.
Available at: https://www.eeweb.com/profile/andrew-carter/articles/different-types-of-
switches-network-switches [Accessed 27 Mar. 2018].
CB Antenna. (2017). A Complete Guide to CB Coax Cable - Strykerradios. [online]
Available at: https://strykerradios.com/cb-coax-cable/ [Accessed 27 Mar. 2018].
Cooper, S. n.d. 6 Required Components of a LAN. [online] Smallbusiness.chron. Available
at: http://smallbusiness.chron.com/6-required-components-lan-26555.html [Accessed
27 Mar. 2018].
Cozlink 2016. What is IEEE 802.3? Cozlink. [online] Cozlink. Available at:
https://www.cozlink.com/modules-a272-275-276/article-69299.html [Accessed 27 Mar.
2018].
Delaney, J. 2018. The Best Wireless Routers of 2018. [online] PCMag UK. Available at:
http://uk.pcmag.com/wireless-networking-products/8151/guide/the-best-wireless-
routers-of-2018 [Accessed 27 Mar. 2018].
Hope, C. 2017. What is IEEE 802.11?. [online] Computerhope. Available at:
https://www.computerhope.com/jargon/num/80211.htm [Accessed 27 Mar. 2018].
Itknowledgeexchange 2018. Benefits of VLANs? - IT Answers. [online] IT Answers.
Available at: http://itknowledgeexchange.techtarget.com/itanswers/benefits-of-vlans/
[Accessed 27 Mar. 2018].
KeyCDN 2016. What is Latency - KeyCDN Support. [online] KeyCDN Support. Available at:
https://www.keycdn.com/support/what-is-latency/ [Accessed 27 Mar. 2018].
43
Beal, V. n.d. What is Network Security? Webopedia Definition. [online] Webopedia.
Available at: https://www.webopedia.com/TERM/N/network_security.html [Accessed
27 Mar. 2018].
BeotelNet. 2017. Media streaming - audio and video. [online] Available at:
https://www.beotel.net/streaming [Accessed 23 Mar. 2018].
Carter, A. 2012. Different Types of Switches - Network Switches. [online] Eye web.
Available at: https://www.eeweb.com/profile/andrew-carter/articles/different-types-of-
switches-network-switches [Accessed 27 Mar. 2018].
CB Antenna. (2017). A Complete Guide to CB Coax Cable - Strykerradios. [online]
Available at: https://strykerradios.com/cb-coax-cable/ [Accessed 27 Mar. 2018].
Cooper, S. n.d. 6 Required Components of a LAN. [online] Smallbusiness.chron. Available
at: http://smallbusiness.chron.com/6-required-components-lan-26555.html [Accessed
27 Mar. 2018].
Cozlink 2016. What is IEEE 802.3? Cozlink. [online] Cozlink. Available at:
https://www.cozlink.com/modules-a272-275-276/article-69299.html [Accessed 27 Mar.
2018].
Delaney, J. 2018. The Best Wireless Routers of 2018. [online] PCMag UK. Available at:
http://uk.pcmag.com/wireless-networking-products/8151/guide/the-best-wireless-
routers-of-2018 [Accessed 27 Mar. 2018].
Hope, C. 2017. What is IEEE 802.11?. [online] Computerhope. Available at:
https://www.computerhope.com/jargon/num/80211.htm [Accessed 27 Mar. 2018].
Itknowledgeexchange 2018. Benefits of VLANs? - IT Answers. [online] IT Answers.
Available at: http://itknowledgeexchange.techtarget.com/itanswers/benefits-of-vlans/
[Accessed 27 Mar. 2018].
KeyCDN 2016. What is Latency - KeyCDN Support. [online] KeyCDN Support. Available at:
https://www.keycdn.com/support/what-is-latency/ [Accessed 27 Mar. 2018].
43

Mace, T. n.d. Traffic Management for Optimizing Media-Intensive SoCs. [online] Design
And Reuse. Available at: https://www.design-reuse.com/articles/22738/traffic-
management-media-intensive-soc.html [Accessed 27 Mar. 2018].
ManageEngine n.d. Quality of Service QoS CBQoS reporting NetFlow Analyzer. [online]
ManageEngine. Available at:
https://www.manageengine.com/products/netflow/allaboutqos.html [Accessed 27 Mar.
2018].
Matrox. 2012. Matrox Graphics - Products - Legacy Products - Veos - Veos Repeater
Unit. [online] Available at:
http://www.matrox.com/graphics/en/products/legacy/veos/vsrptr0f/ [Accessed 27
Mar. 2018].
Maxwellstreaming. n.d. Video on Demand (VOD) Streaming Services London,
Manchester, Oxford, UK. [online] Available at:
http://www.maxwellstreaming.com/uk/video-on-demand-service-london-uk.php
[Accessed 23 Mar. 2018].
Mitchell, B. 2017. What's a LAN (Local Area Network)?. [online] Lifewire. Available at:
https://www.lifewire.com/local-area-network-816382 [Accessed 27 Mar. 2018].
Mitchell, B. 2018. What a VLAN Can Do for You and Your Business Computer Network.
[online] Lifewire. Available at: https://www.lifewire.com/virtual-local-area-network-
817357 [Accessed 27 Mar. 2018].
Multicom. n.d. Draka - ezSPAN - ADSS Long Span Fiber Optic Cable (2-288 Count).
[online] Available at: https://www.multicominc.com/product/draka-ezspan-adss-long-
span-fiber-optic-cable-2-288-count/ [Accessed 27 Mar. 2018].
Popeskic, V. n.d. What is Jitter in Networking?. [online] How Does Internet Work.
Available at: https://howdoesinternetwork.com/2013/jitter [Accessed 27 Mar. 2018].
Simpson, N. 2015. Network Components By Kagan Strayer. Network Components This
presentation will cover various network components and their functions. The
44
And Reuse. Available at: https://www.design-reuse.com/articles/22738/traffic-
management-media-intensive-soc.html [Accessed 27 Mar. 2018].
ManageEngine n.d. Quality of Service QoS CBQoS reporting NetFlow Analyzer. [online]
ManageEngine. Available at:
https://www.manageengine.com/products/netflow/allaboutqos.html [Accessed 27 Mar.
2018].
Matrox. 2012. Matrox Graphics - Products - Legacy Products - Veos - Veos Repeater
Unit. [online] Available at:
http://www.matrox.com/graphics/en/products/legacy/veos/vsrptr0f/ [Accessed 27
Mar. 2018].
Maxwellstreaming. n.d. Video on Demand (VOD) Streaming Services London,
Manchester, Oxford, UK. [online] Available at:
http://www.maxwellstreaming.com/uk/video-on-demand-service-london-uk.php
[Accessed 23 Mar. 2018].
Mitchell, B. 2017. What's a LAN (Local Area Network)?. [online] Lifewire. Available at:
https://www.lifewire.com/local-area-network-816382 [Accessed 27 Mar. 2018].
Mitchell, B. 2018. What a VLAN Can Do for You and Your Business Computer Network.
[online] Lifewire. Available at: https://www.lifewire.com/virtual-local-area-network-
817357 [Accessed 27 Mar. 2018].
Multicom. n.d. Draka - ezSPAN - ADSS Long Span Fiber Optic Cable (2-288 Count).
[online] Available at: https://www.multicominc.com/product/draka-ezspan-adss-long-
span-fiber-optic-cable-2-288-count/ [Accessed 27 Mar. 2018].
Popeskic, V. n.d. What is Jitter in Networking?. [online] How Does Internet Work.
Available at: https://howdoesinternetwork.com/2013/jitter [Accessed 27 Mar. 2018].
Simpson, N. 2015. Network Components By Kagan Strayer. Network Components This
presentation will cover various network components and their functions. The
44

components that. - ppt download. [online] Slide player. Available at:
http://slideplayer.com/slide/9079787/ [Accessed 27 Mar. 2018].
Sites. n.d. Tipo de Cable de Redes - Cableado de Redes. [online] Available at:
https://sites.google.com/site/inacapcableadoderedes/tipo-de-cable-de-redes [Accessed
23 Mar. 2018].
Smith, G. 2015. 10 of the best network and server monitoring tools. [online] Mashable.
Available at:
https://mashable.com/2015/11/17/network-server-tools/#i4wTQMzQmZqu [Accessed
27 Mar. 2018].
STRUCTURED CABLING. n.d. What is UTP Cable? [online] Available at:
http://structuredcabling.com/what-is-utp-cable/ [Accessed 23 Mar. 2018].
THAKUR, D. 2014. Star Topologies – What is Star Topologies?. [online] Ecomputernotes.
Available at: http://ecomputernotes.com/computernetworkingnotes/computer-
network/star-topologies [Accessed 23 Mar. 2018].
Trendnet. n.d. 4-Port Network USB Hub - TRENDnet TU2-NU4. [online] Available at:
http://www.trendnet.com/products/proddetail?prod=260_tu2-nu4 [Accessed 27 Mar.
2018].
Withers, S. 2005. 10 ways to improve network performance ZDNet. [online] ZDNet.
Available at: http://www.zdnet.com/article/10-ways-to-improve-network-performance/
[Accessed 27 Mar. 2018].
Yenra. (2004). Qwest VoIP. [online] Available at: https://yenra.com/how-voip-works/
[Accessed 23 Mar. 2018].
45
http://slideplayer.com/slide/9079787/ [Accessed 27 Mar. 2018].
Sites. n.d. Tipo de Cable de Redes - Cableado de Redes. [online] Available at:
https://sites.google.com/site/inacapcableadoderedes/tipo-de-cable-de-redes [Accessed
23 Mar. 2018].
Smith, G. 2015. 10 of the best network and server monitoring tools. [online] Mashable.
Available at:
https://mashable.com/2015/11/17/network-server-tools/#i4wTQMzQmZqu [Accessed
27 Mar. 2018].
STRUCTURED CABLING. n.d. What is UTP Cable? [online] Available at:
http://structuredcabling.com/what-is-utp-cable/ [Accessed 23 Mar. 2018].
THAKUR, D. 2014. Star Topologies – What is Star Topologies?. [online] Ecomputernotes.
Available at: http://ecomputernotes.com/computernetworkingnotes/computer-
network/star-topologies [Accessed 23 Mar. 2018].
Trendnet. n.d. 4-Port Network USB Hub - TRENDnet TU2-NU4. [online] Available at:
http://www.trendnet.com/products/proddetail?prod=260_tu2-nu4 [Accessed 27 Mar.
2018].
Withers, S. 2005. 10 ways to improve network performance ZDNet. [online] ZDNet.
Available at: http://www.zdnet.com/article/10-ways-to-improve-network-performance/
[Accessed 27 Mar. 2018].
Yenra. (2004). Qwest VoIP. [online] Available at: https://yenra.com/how-voip-works/
[Accessed 23 Mar. 2018].
45
Secure Best Marks with AI Grader
Need help grading? Try our AI Grader for instant feedback on your assignments.

1 out of 47
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
© 2024 | Zucol Services PVT LTD | All rights reserved.





