Botnet Design and Implementation Project
VerifiedAdded on 2019/09/16
|4
|999
|333
Project
AI Summary
This project requires students to design and implement a three-layered botnet capable of performing a Distributed Denial of Service (DDOS) attack. The project involves creating protocols for communication between controllers, handlers, and agents, using C and the Sockets API on a Linux environment. Students will develop software to add agents, interrogate handlers, validate agents, count agents, and initiate attacks. The project also includes analyzing network traffic and demonstrating the botnet's functionality on designated lab machines. The software must adhere to specific port numbers and command-line parameters, with a focus on using only the Sockets API and provided frameworks.

LEARNING OUTCOMES
This assignment is designed to link into the following Learning Outcomes of
the Module
Critically analyse a network stack at all OSI layers for security
vulnerabilities
Critically appraise network performance in light of current hacker
threats determining best practice for security.
Develop simple hacking tools that can either penetrate a network or
disable the function of a normal network.
Critically appraise the structure for Internet, Intranet and Extranet
systems.
This is achieved by developing several pieces of software, which will allow
you to gain an understanding of how services integrate over a network and
how protocols provide a communications infrastructure for Botnets.
TASKS
Design a set of protocols that will allow a set of machines to carry out a
DDOS (Distributed Denial Of Service) Attack.
Design and build a suite of software that utilise the protocols to carry
out a DDOS attack.
Analyse the resultant network traffic highlighting the Botnet structure
and the effects of the DDOS payload.
Demonstrate the suite of programs on a set of designated clients
against a designated target (Linux Lab Machines in Network Lab).
1
This assignment is designed to link into the following Learning Outcomes of
the Module
Critically analyse a network stack at all OSI layers for security
vulnerabilities
Critically appraise network performance in light of current hacker
threats determining best practice for security.
Develop simple hacking tools that can either penetrate a network or
disable the function of a normal network.
Critically appraise the structure for Internet, Intranet and Extranet
systems.
This is achieved by developing several pieces of software, which will allow
you to gain an understanding of how services integrate over a network and
how protocols provide a communications infrastructure for Botnets.
TASKS
Design a set of protocols that will allow a set of machines to carry out a
DDOS (Distributed Denial Of Service) Attack.
Design and build a suite of software that utilise the protocols to carry
out a DDOS attack.
Analyse the resultant network traffic highlighting the Botnet structure
and the effects of the DDOS payload.
Demonstrate the suite of programs on a set of designated clients
against a designated target (Linux Lab Machines in Network Lab).
1
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
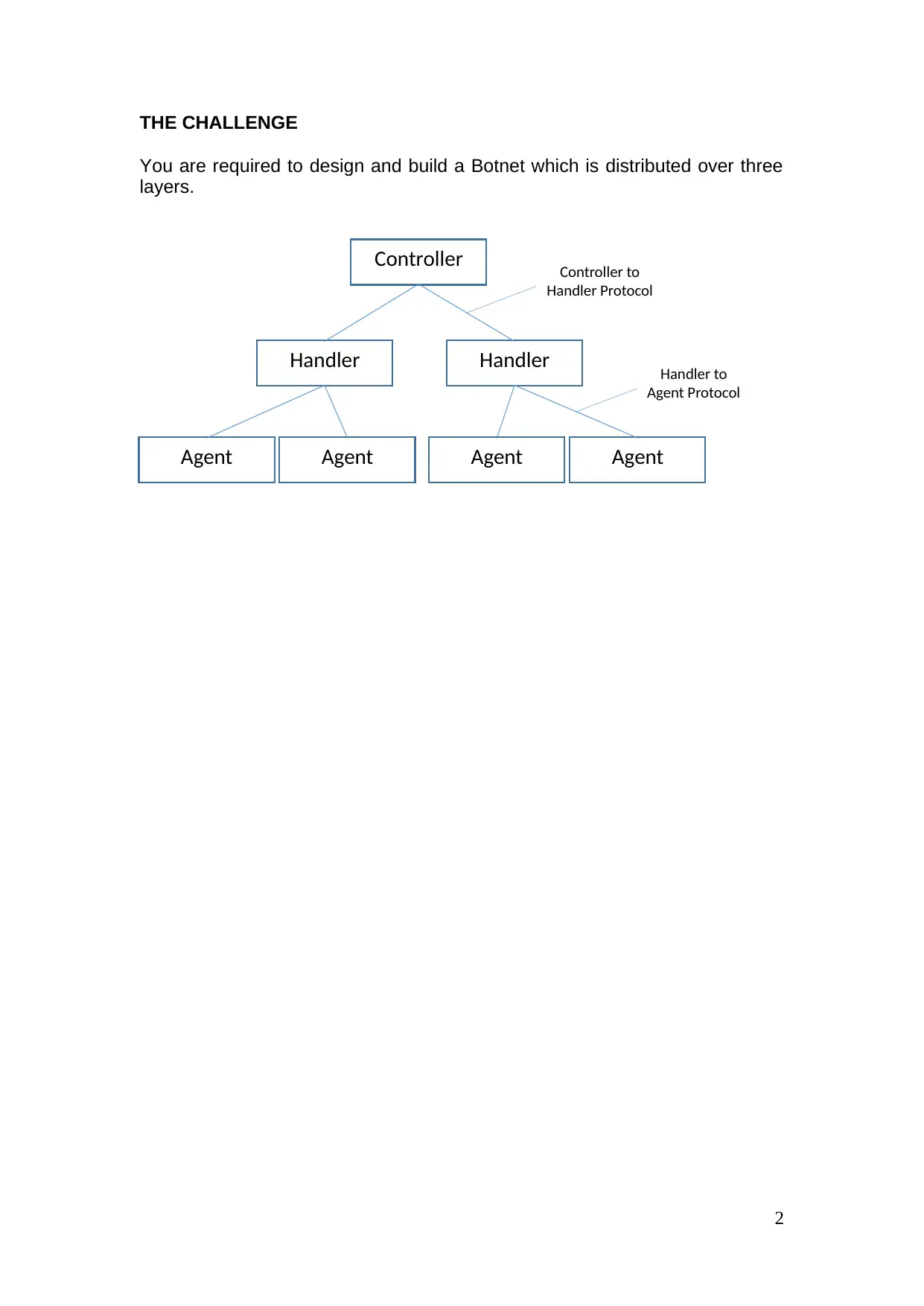
THE CHALLENGE
You are required to design and build a Botnet which is distributed over three
layers.
2
Controller
Handler Handler
Agent Agent Agent Agent
Controller to
Handler Protocol
Handler to
Agent Protocol
You are required to design and build a Botnet which is distributed over three
layers.
2
Controller
Handler Handler
Agent Agent Agent Agent
Controller to
Handler Protocol
Handler to
Agent Protocol

The protocols must use the following ports where possible.
Controller – Client (port 2112)
Handlers – (Client/Server) (port 1984/2112)
Agents - (Server) (port 1984)
If using multiple servers on the same machine the port numbers should be
used sequentially using the above port number as the starting port (this may
not be required!).
The software must run on an Ubuntu installation of Linux (as installed in
Networks Lab). You may use virtual machines rather than the bootable
images in the laboratory where necessary.
The application must be written in C using the Sockets API (Do not use any
libraries other than the Sockets libraries as covered in the lectures and
seminars in semester 1) it is permissible for you to use the provided Sockets
Client/Server Frameworks provided in semester 1, all coding other than the
framework must be your groups own work!
NOTE: All the controller programs should be written as utility programs
that accept command line parameters only; they/it must NOT act as an
interactive program. If an interactive program is submitted a mark of 0
(zero) will be applied to the whole assignment. The Handlers must act
as both a client and a server program and the Agents must all act as
server programs.
The application must function as follows:
Controller
This can be a set of programs
Mode of operation: Add Agent to Handler
Allow the IP address of a handler to be specified and the IP address of a
possible Agent so as to add the Agent to the Handlers list of possible
Agents. (The program should handle check the validated Handlers file)
The response to the user should be the version of the Handler and an
message to indicate is the Agent has been added to the Handlers file.
Mode of operation: Interrogate Handlers
Allow a filename to be specified that contains a list of possible handlers
and return a list (to the screen) of all the specified handlers indicating
which handlers are operational (include the version number) and those
that are not. The program must also create a validated Handler file which
contains viable Handlers in a format suitable for the attack mode (there
should be no Agent interaction!).
3
Controller – Client (port 2112)
Handlers – (Client/Server) (port 1984/2112)
Agents - (Server) (port 1984)
If using multiple servers on the same machine the port numbers should be
used sequentially using the above port number as the starting port (this may
not be required!).
The software must run on an Ubuntu installation of Linux (as installed in
Networks Lab). You may use virtual machines rather than the bootable
images in the laboratory where necessary.
The application must be written in C using the Sockets API (Do not use any
libraries other than the Sockets libraries as covered in the lectures and
seminars in semester 1) it is permissible for you to use the provided Sockets
Client/Server Frameworks provided in semester 1, all coding other than the
framework must be your groups own work!
NOTE: All the controller programs should be written as utility programs
that accept command line parameters only; they/it must NOT act as an
interactive program. If an interactive program is submitted a mark of 0
(zero) will be applied to the whole assignment. The Handlers must act
as both a client and a server program and the Agents must all act as
server programs.
The application must function as follows:
Controller
This can be a set of programs
Mode of operation: Add Agent to Handler
Allow the IP address of a handler to be specified and the IP address of a
possible Agent so as to add the Agent to the Handlers list of possible
Agents. (The program should handle check the validated Handlers file)
The response to the user should be the version of the Handler and an
message to indicate is the Agent has been added to the Handlers file.
Mode of operation: Interrogate Handlers
Allow a filename to be specified that contains a list of possible handlers
and return a list (to the screen) of all the specified handlers indicating
which handlers are operational (include the version number) and those
that are not. The program must also create a validated Handler file which
contains viable Handlers in a format suitable for the attack mode (there
should be no Agent interaction!).
3
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

Mode of operation: Validate Agents
Allow a filename to be specified that contains a list of validated Handlers
and return a list (to the screen) of all the specified Handlers and the
number of viable Agents each has (this operation should cause the
Handlers to update the viable Agents list).
Mode of operation: Count Agents
Allow a filename to be specified that contains a list of viable Handlers and
returns a count of the number of available Agents within the botnet. (This
should work in a similar way to the Validate Agents mode but return a
single value.
Mode of operation: Attack
Allow a filename to be specified that contains a list of viable Handlers
along with a target IP address and an option packet count for the number
of SYN packets to be sent to the target in total, if no packet count is
specified the Botnet should assume 100 packets in total for the entire
botnet. i.e. 100 packets over a 5 agent botnet would be 20 packets each.
Handler
This can be a set of programs
Mode of operation: Interrogate Handler
Upon receiving an interrogate request the Handler should respond with a
version number.
Mode of operation: Interrogate Agents
Access a filename containing a list of potential agents and create a list of
viable agents for an attack, this should then return the number of viable
agents to the controller.
Mode of operation: Attack
Using the file containing a list of viable Agents:
Upon receiving an attack request contact each agent to inform them of the
target and the number of packets they must broadcast.
Agent
This can be a set of programs
Mode of operation: Attack
Upon receiving an attack request the Agent must attack the target by
sending the appropriate number of SYN packets.
Mode of operation: Interrogate Agent
Upon receiving an interrogate request the Agent should respond with a
version number.
4
Allow a filename to be specified that contains a list of validated Handlers
and return a list (to the screen) of all the specified Handlers and the
number of viable Agents each has (this operation should cause the
Handlers to update the viable Agents list).
Mode of operation: Count Agents
Allow a filename to be specified that contains a list of viable Handlers and
returns a count of the number of available Agents within the botnet. (This
should work in a similar way to the Validate Agents mode but return a
single value.
Mode of operation: Attack
Allow a filename to be specified that contains a list of viable Handlers
along with a target IP address and an option packet count for the number
of SYN packets to be sent to the target in total, if no packet count is
specified the Botnet should assume 100 packets in total for the entire
botnet. i.e. 100 packets over a 5 agent botnet would be 20 packets each.
Handler
This can be a set of programs
Mode of operation: Interrogate Handler
Upon receiving an interrogate request the Handler should respond with a
version number.
Mode of operation: Interrogate Agents
Access a filename containing a list of potential agents and create a list of
viable agents for an attack, this should then return the number of viable
agents to the controller.
Mode of operation: Attack
Using the file containing a list of viable Agents:
Upon receiving an attack request contact each agent to inform them of the
target and the number of packets they must broadcast.
Agent
This can be a set of programs
Mode of operation: Attack
Upon receiving an attack request the Agent must attack the target by
sending the appropriate number of SYN packets.
Mode of operation: Interrogate Agent
Upon receiving an interrogate request the Agent should respond with a
version number.
4
1 out of 4
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.




