Information Security Plan (ISP) for LearnIt University: Protecting Data and Enhancing Security Measures
VerifiedAdded on 2023/04/25
|8
|2384
|477
AI Summary
In this report we will discuss about Information security plan (ISP) and below are the summaries point:-
Information Security Plan (ISP) aims to protect data, resources, and assets from security attacks.
LearnIt University requires effective IT security measures to combat security threats.
ISP includes security models, access control, data integrity, network security, and compliance with standards.
Contribute Materials
Your contribution can guide someone’s learning journey. Share your
documents today.

qwertyuiopasdfghjklzxcvbn
mqwertyuiopasdfghjklzxcv
bnmqwertyuiopasdfghjklzx
cvbnmqwertyuiopasdfghjkl
zxcvbnmqwertyuiopasdfghj
klzxcvbnmqwertyuiopasdfg
hjklzxcvbnmqwertyuiopasd
fghjklzxcvbnmqwertyuiopa
sdfghjklzxcvbnmqwertyuio
pasdfghjklzxcvbnmqwertyu
iopasdfghjklzxcvbnmqwert
yuiopasdfghjklzxcvbnmqwe
rtyuiopasdfghjklzxcvbnmq
wertyuiopasdfghjklzxcvbn
mqwertyuiopasdfghjklzxcv
bnmqwertyuiopasdfghjklzx
cvbnmqwertyuiopasdfghjkl
zxcvbnmqwertyuiopasdfghj
LearnIt University
Information Security Plan (ISP)
3/12/2019
mqwertyuiopasdfghjklzxcv
bnmqwertyuiopasdfghjklzx
cvbnmqwertyuiopasdfghjkl
zxcvbnmqwertyuiopasdfghj
klzxcvbnmqwertyuiopasdfg
hjklzxcvbnmqwertyuiopasd
fghjklzxcvbnmqwertyuiopa
sdfghjklzxcvbnmqwertyuio
pasdfghjklzxcvbnmqwertyu
iopasdfghjklzxcvbnmqwert
yuiopasdfghjklzxcvbnmqwe
rtyuiopasdfghjklzxcvbnmq
wertyuiopasdfghjklzxcvbn
mqwertyuiopasdfghjklzxcv
bnmqwertyuiopasdfghjklzx
cvbnmqwertyuiopasdfghjkl
zxcvbnmqwertyuiopasdfghj
LearnIt University
Information Security Plan (ISP)
3/12/2019
Secure Best Marks with AI Grader
Need help grading? Try our AI Grader for instant feedback on your assignments.

Information Security Plan
Table of Contents
Executive Summary........................................................................................................................................................2
Security Model................................................................................................................................................................2
Access Control............................................................................................................................................................2
Data Integrity..............................................................................................................................................................3
Security Strategy and Policy...........................................................................................................................................3
Bring Your Own Devices (BYOD) Security...............................................................................................................3
Compliance and Standards..............................................................................................................................................4
Risk Analysis & Assessment...........................................................................................................................................4
Network Security............................................................................................................................................................5
Penetration Testing & Usable Security............................................................................................................................5
Digital Rights Protection.................................................................................................................................................6
Conclusion...................................................................................................................................................................... 6
References.......................................................................................................................................................................7
1
Table of Contents
Executive Summary........................................................................................................................................................2
Security Model................................................................................................................................................................2
Access Control............................................................................................................................................................2
Data Integrity..............................................................................................................................................................3
Security Strategy and Policy...........................................................................................................................................3
Bring Your Own Devices (BYOD) Security...............................................................................................................3
Compliance and Standards..............................................................................................................................................4
Risk Analysis & Assessment...........................................................................................................................................4
Network Security............................................................................................................................................................5
Penetration Testing & Usable Security............................................................................................................................5
Digital Rights Protection.................................................................................................................................................6
Conclusion...................................................................................................................................................................... 6
References.......................................................................................................................................................................7
1

Information Security Plan
Executive Summary
The purpose of an Information Security Plan (ISP) is to make sure that the information and data sets along
with the critical resources and assets are protected from the information security attacks. Also, the business
continuity, adequate risk management, business value, and return on investment are enhanced using the ISP.
LearnIt University is one such organization that is exposed to numerous security attacks. IT security in the
university can be achieved using the adequate mix of policies, controls, methodologies, and functions. It is
necessary that these controls are planned and reviewed correct to achieve the best results.
LearnIt University is an educational institution that was set up in 2001 and is currently composed of 3,000
students, 150 faculty staff members, and 100 administrative staff members. Information security is essential
for the university so that private student and employee details, course information, and administrative details
are not exposed to the third-parties.
Security Model
Control activities comprise of a wide range of policies, methodologies, techniques, and processes to make
sure that management responds correctly to reduce and treat the risks that are determined. These are
conducted for risk minimization. These activities are executed at all the University levels covering all of its
functions. A diverse range of tasks, such as authorizations, reconciliations, verifications, security of assets,
distribution of duties and review are included. There are different forms of controls that are designed, such
as internal controls, preventive controls, detective controls, and corrective controls (Kumar et al., 2018).
The risk assessment at the LearnIt University will recognize the internal and external risks that the university
is exposed to. These may include the unauthorized data access, data integrity issues, leakage of the data sets,
errors in the system, physical loss of data in the case of a natural disaster, data breaches, malware attacks,
and many more.
The resources that shall be responsible for risk assessment and security management shall include
Information Security Administrator (ISA), Chief Information Security Officer (CIO), Information Security
Manager (ISM), Information System Owners (ISOs), and the members of the board. CIO and the members
of the board shall make sure that the adherence and compliance towards the security policies are maintained
at all times (Palvia, 2011).
Access Control
The access control for the University will be applied for the systems, applications, data, and network. The
use of passwords, biometric-based authentication system, access control lists, and role-based access control
shall be done.
2
Executive Summary
The purpose of an Information Security Plan (ISP) is to make sure that the information and data sets along
with the critical resources and assets are protected from the information security attacks. Also, the business
continuity, adequate risk management, business value, and return on investment are enhanced using the ISP.
LearnIt University is one such organization that is exposed to numerous security attacks. IT security in the
university can be achieved using the adequate mix of policies, controls, methodologies, and functions. It is
necessary that these controls are planned and reviewed correct to achieve the best results.
LearnIt University is an educational institution that was set up in 2001 and is currently composed of 3,000
students, 150 faculty staff members, and 100 administrative staff members. Information security is essential
for the university so that private student and employee details, course information, and administrative details
are not exposed to the third-parties.
Security Model
Control activities comprise of a wide range of policies, methodologies, techniques, and processes to make
sure that management responds correctly to reduce and treat the risks that are determined. These are
conducted for risk minimization. These activities are executed at all the University levels covering all of its
functions. A diverse range of tasks, such as authorizations, reconciliations, verifications, security of assets,
distribution of duties and review are included. There are different forms of controls that are designed, such
as internal controls, preventive controls, detective controls, and corrective controls (Kumar et al., 2018).
The risk assessment at the LearnIt University will recognize the internal and external risks that the university
is exposed to. These may include the unauthorized data access, data integrity issues, leakage of the data sets,
errors in the system, physical loss of data in the case of a natural disaster, data breaches, malware attacks,
and many more.
The resources that shall be responsible for risk assessment and security management shall include
Information Security Administrator (ISA), Chief Information Security Officer (CIO), Information Security
Manager (ISM), Information System Owners (ISOs), and the members of the board. CIO and the members
of the board shall make sure that the adherence and compliance towards the security policies are maintained
at all times (Palvia, 2011).
Access Control
The access control for the University will be applied for the systems, applications, data, and network. The
use of passwords, biometric-based authentication system, access control lists, and role-based access control
shall be done.
2

Information Security Plan
The restriction on the permissions and grants will be done using identify control and controlled authorised
access to the users. There will also be frequent monitoring of the access control tools and techniques done so
that the updates may be carried out accordingly.
Data Integrity
The data will be cleansed periodically to avoid duplications and replications of the data sets. The data
released to the outside parties or transmitted over the network will be validated and verified. The use of
encryption will be done so that unauthorized modification of the data sets during transmission is avoided.
Operational security measures will be taken to ensure that the data is error free and is also reliable in nature.
Security Strategy and Policy
The following strategies and policies will be used to manage the information security and privacy.
Identity Management: The current employees shall be allocated with a unique identity validated
using biometric recognition and the access shall be discontinued as soon the employee leaves the
university.
Passwords: The passwords shall be set on all the internal systems, applications, and accounts. The
passwords shall meet the CISO complexity requirements.
Data Encryption and encrypted network transmission: The electronic data and information must be
encrypted using advanced encryption protocols. The same shall be followed for the data being
transmitted (Nie, Lu and Zhou, 2014).
Anti-malware and anti-denial tools: These security controls must be integrated with all the university
systems and applications.
System Hardening and Security Patches: The default credentials must be removed and the security
patches shall be released at regular intervals.
Encrypted Backups: The data sets shall be backed up in an encrypted form at regular intervals.
The physical security of the information and systems shall also be ensured. The critical paper-based files and
documents shall be kept in secure file cabinets. The access to the computer labs shall be made secure using
biometric-based authentication system.
Bring Your Own Devices (BYOD) Security
The employee devices under BYOD scheme shall be tagged using the university tags and security controls,
such as anti-malware and anti-denial tools shall be installed. The device owners must maintain the physical
security of the device to prevent the issues of device loss or theft (Tokuyoshi, 2013).
The passwords shall be applied on the device as well as all the applications installed in it.
3
The restriction on the permissions and grants will be done using identify control and controlled authorised
access to the users. There will also be frequent monitoring of the access control tools and techniques done so
that the updates may be carried out accordingly.
Data Integrity
The data will be cleansed periodically to avoid duplications and replications of the data sets. The data
released to the outside parties or transmitted over the network will be validated and verified. The use of
encryption will be done so that unauthorized modification of the data sets during transmission is avoided.
Operational security measures will be taken to ensure that the data is error free and is also reliable in nature.
Security Strategy and Policy
The following strategies and policies will be used to manage the information security and privacy.
Identity Management: The current employees shall be allocated with a unique identity validated
using biometric recognition and the access shall be discontinued as soon the employee leaves the
university.
Passwords: The passwords shall be set on all the internal systems, applications, and accounts. The
passwords shall meet the CISO complexity requirements.
Data Encryption and encrypted network transmission: The electronic data and information must be
encrypted using advanced encryption protocols. The same shall be followed for the data being
transmitted (Nie, Lu and Zhou, 2014).
Anti-malware and anti-denial tools: These security controls must be integrated with all the university
systems and applications.
System Hardening and Security Patches: The default credentials must be removed and the security
patches shall be released at regular intervals.
Encrypted Backups: The data sets shall be backed up in an encrypted form at regular intervals.
The physical security of the information and systems shall also be ensured. The critical paper-based files and
documents shall be kept in secure file cabinets. The access to the computer labs shall be made secure using
biometric-based authentication system.
Bring Your Own Devices (BYOD) Security
The employee devices under BYOD scheme shall be tagged using the university tags and security controls,
such as anti-malware and anti-denial tools shall be installed. The device owners must maintain the physical
security of the device to prevent the issues of device loss or theft (Tokuyoshi, 2013).
The passwords shall be applied on the device as well as all the applications installed in it.
3
Secure Best Marks with AI Grader
Need help grading? Try our AI Grader for instant feedback on your assignments.

Information Security Plan
Compliance and Standards
The adherence to the national standards must be ensured and complied with. The numerous standards under
National Standards and Guidelines will be applicable to the university.
NIST FIPS 199: It is a standard that categorizes the security of the federal information and systems.
NIST SP 800-53, Revision 4: The security controls for federal systems and organizations are
specified under this standard.
NIST Special Publication 800-60 Vol I Rev I: It must be used to map the information systems with
various security categories to apply the security controls accordingly (Nist, 2019).
NIST Special Publication 800-60 Vol I Rev II: It is an advanced version of the previous guide.
The Data Protection Act, 1998 and its policies must be complied with in order to protect and handle the
personal data of the entities associated with the university. The breaching of the act can lead to a fine of up
to £500,000 for the university. The member of the university purposely violating the act will also be
subjected to the disciplinary measures. There may also be certain legal obligations that may be applied.
Risk Analysis & Assessment
The risk assessment at the LearnIt University will recognize the internal and external risks that the university
is exposed to. These may include the unauthorized data access, data integrity issues, leakage of the data sets,
errors in the system, physical loss of data in the case of a natural disaster, data breaches, malware attacks,
and many more.
The process of risk analysis and assessment will include a total of five steps.
Risk Identification: The list of the risks that the university is exposed to will be prepared in this step.
The list will be based on the information collected from various university sources and external
information.
Risk Analysis: The analysis and assessment of the risks will be done to devise the probability and
consequence levels for every risk (Michael, 2012).
Risk Evaluation and Treatment: The risks will be classified in two categories as acceptable and non-
acceptable. The risks put in the latter category will be treated using the strategies as avoid, transfer,
mitigate, or share.
Risk Control: The ISAs, CIO, and ISMs will carry out risk monitoring and control processes by
reviewing and auditing the risk treatment strategies.
Risk Closure: The closure of the risk will be done once the treatment of the risk is complete.
4
Compliance and Standards
The adherence to the national standards must be ensured and complied with. The numerous standards under
National Standards and Guidelines will be applicable to the university.
NIST FIPS 199: It is a standard that categorizes the security of the federal information and systems.
NIST SP 800-53, Revision 4: The security controls for federal systems and organizations are
specified under this standard.
NIST Special Publication 800-60 Vol I Rev I: It must be used to map the information systems with
various security categories to apply the security controls accordingly (Nist, 2019).
NIST Special Publication 800-60 Vol I Rev II: It is an advanced version of the previous guide.
The Data Protection Act, 1998 and its policies must be complied with in order to protect and handle the
personal data of the entities associated with the university. The breaching of the act can lead to a fine of up
to £500,000 for the university. The member of the university purposely violating the act will also be
subjected to the disciplinary measures. There may also be certain legal obligations that may be applied.
Risk Analysis & Assessment
The risk assessment at the LearnIt University will recognize the internal and external risks that the university
is exposed to. These may include the unauthorized data access, data integrity issues, leakage of the data sets,
errors in the system, physical loss of data in the case of a natural disaster, data breaches, malware attacks,
and many more.
The process of risk analysis and assessment will include a total of five steps.
Risk Identification: The list of the risks that the university is exposed to will be prepared in this step.
The list will be based on the information collected from various university sources and external
information.
Risk Analysis: The analysis and assessment of the risks will be done to devise the probability and
consequence levels for every risk (Michael, 2012).
Risk Evaluation and Treatment: The risks will be classified in two categories as acceptable and non-
acceptable. The risks put in the latter category will be treated using the strategies as avoid, transfer,
mitigate, or share.
Risk Control: The ISAs, CIO, and ISMs will carry out risk monitoring and control processes by
reviewing and auditing the risk treatment strategies.
Risk Closure: The closure of the risk will be done once the treatment of the risk is complete.
4

Information Security Plan
Network Security
There will be a number of network security attacks that the university systems, networks, and data will be
exposed to. The following measures will be used for network security and control.
Any person entering the university campus will be allowed to make the entry only when the person is
found to be authorized.
User awareness will be provided so that the user mistakes and errors do not result in the compromise
of the security. The details on suspicious network links, choice of networks to connect to, etc. will be
explained.
The students, faculty members, and administrative staff members shall be held legally and
financially responsible if it is found that the unauthorized access is carried out by them.
In order to connect any of the servers to the university networks, there shall be a written permission
obtained from the IT division (Blandford, 2011).
The use of network security controls, such as network-based intrusion detection and prevention, anti-
denial tools, and firewalls shall be done.
Network scanners and monitoring tools shall be used to assess the network logs.
Penetration Testing & Usable Security
There shall be network discovery and vulnerability detection methods conducted on the university systems
and applications. Compliance testing and reporting shall be conducted on the services that are hosted by the
third-parties. Vulnerability assessment must be conducted on the systems before they are transitioned to the
production environment. There may be certain systems or servers that may be detected with an
unacceptable vulnerability level. These shall be subjected to penetration testing and deeper analysis.
The results that are obtained in the scans and detection methods shall be shared with the internal and
external stakeholders associated with the university (Antunes and Vieira, 2014).
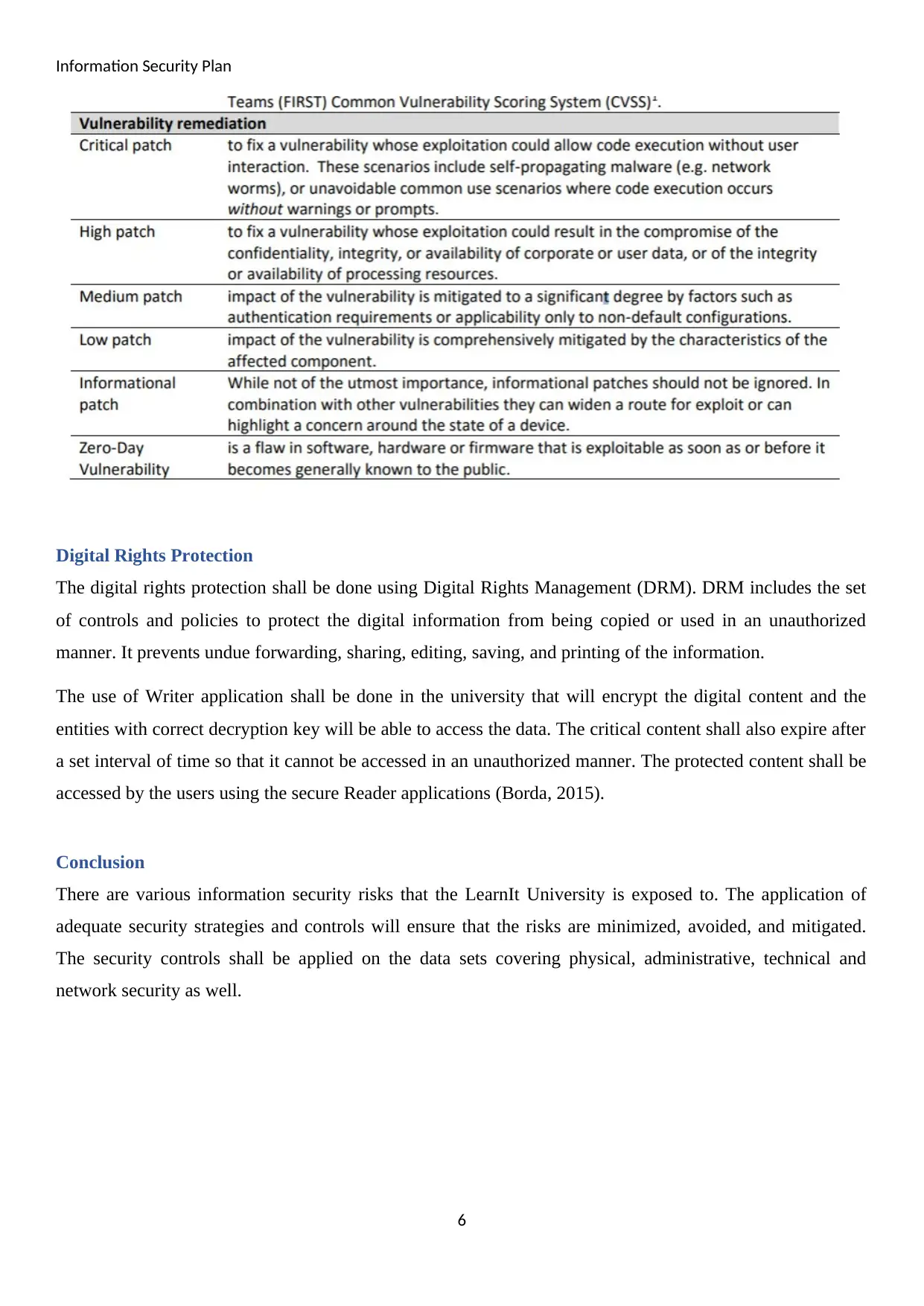
The use of security patches shall be done to fix the vulnerabilities that are detected. High patch shall be used
to treat the vulnerabilities that may result in the adverse implications on the information properties, such as
confidentiality, integrity, privacy, and availability. Medium patch shall be used to treat the vulnerabilities
associated with authentication and non-default configurations. Low patch shall be used to mitigate the
parameters associated with the components that are impacted. There may also be zero-day vulnerabilities
that may be present. These refer to the flaw in specific software, firmware, or hardware that can be exploited
as soon public release is made.
5
Network Security
There will be a number of network security attacks that the university systems, networks, and data will be
exposed to. The following measures will be used for network security and control.
Any person entering the university campus will be allowed to make the entry only when the person is
found to be authorized.
User awareness will be provided so that the user mistakes and errors do not result in the compromise
of the security. The details on suspicious network links, choice of networks to connect to, etc. will be
explained.
The students, faculty members, and administrative staff members shall be held legally and
financially responsible if it is found that the unauthorized access is carried out by them.
In order to connect any of the servers to the university networks, there shall be a written permission
obtained from the IT division (Blandford, 2011).
The use of network security controls, such as network-based intrusion detection and prevention, anti-
denial tools, and firewalls shall be done.
Network scanners and monitoring tools shall be used to assess the network logs.
Penetration Testing & Usable Security
There shall be network discovery and vulnerability detection methods conducted on the university systems
and applications. Compliance testing and reporting shall be conducted on the services that are hosted by the
third-parties. Vulnerability assessment must be conducted on the systems before they are transitioned to the
production environment. There may be certain systems or servers that may be detected with an
unacceptable vulnerability level. These shall be subjected to penetration testing and deeper analysis.
The results that are obtained in the scans and detection methods shall be shared with the internal and
external stakeholders associated with the university (Antunes and Vieira, 2014).
The use of security patches shall be done to fix the vulnerabilities that are detected. High patch shall be used
to treat the vulnerabilities that may result in the adverse implications on the information properties, such as
confidentiality, integrity, privacy, and availability. Medium patch shall be used to treat the vulnerabilities
associated with authentication and non-default configurations. Low patch shall be used to mitigate the
parameters associated with the components that are impacted. There may also be zero-day vulnerabilities
that may be present. These refer to the flaw in specific software, firmware, or hardware that can be exploited
as soon public release is made.
5
Information Security Plan
Digital Rights Protection
The digital rights protection shall be done using Digital Rights Management (DRM). DRM includes the set
of controls and policies to protect the digital information from being copied or used in an unauthorized
manner. It prevents undue forwarding, sharing, editing, saving, and printing of the information.
The use of Writer application shall be done in the university that will encrypt the digital content and the
entities with correct decryption key will be able to access the data. The critical content shall also expire after
a set interval of time so that it cannot be accessed in an unauthorized manner. The protected content shall be
accessed by the users using the secure Reader applications (Borda, 2015).
Conclusion
There are various information security risks that the LearnIt University is exposed to. The application of
adequate security strategies and controls will ensure that the risks are minimized, avoided, and mitigated.
The security controls shall be applied on the data sets covering physical, administrative, technical and
network security as well.
6
Digital Rights Protection
The digital rights protection shall be done using Digital Rights Management (DRM). DRM includes the set
of controls and policies to protect the digital information from being copied or used in an unauthorized
manner. It prevents undue forwarding, sharing, editing, saving, and printing of the information.
The use of Writer application shall be done in the university that will encrypt the digital content and the
entities with correct decryption key will be able to access the data. The critical content shall also expire after
a set interval of time so that it cannot be accessed in an unauthorized manner. The protected content shall be
accessed by the users using the secure Reader applications (Borda, 2015).
Conclusion
There are various information security risks that the LearnIt University is exposed to. The application of
adequate security strategies and controls will ensure that the risks are minimized, avoided, and mitigated.
The security controls shall be applied on the data sets covering physical, administrative, technical and
network security as well.
6
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

Information Security Plan
References
Antunes, N. and Vieira, M. (2014). Penetration Testing for Web Services. Computer, 47(2), pp.30-36.
Blandford, R. (2011). Information security in the cloud. Network Security, 2011(4), pp.15-17.
Borda, M. (2015). Digital Rights Protection - a Great Challenge of the New Millennium. TELSIKS 2005 -
2005 uth International Conference on Telecommunication in ModernSatellite, Cable and Broadcasting
Services.
Kumar, S., Kumar, M., Budhiraja, R., Das, M. and Singh, S. (2018). A cryptographic model for better
information security. Journal of Information Security and Applications, 43, pp.123-138.
Michael, K. (2012). Security Risk Management: Building an Information Security Risk Management
Program from the Ground Up. Computers & Security, 31(2), pp.249-250.
Nie, T., Lu, Z. and Zhou, L. (2014). Power evaluation methods for data encryption algorithms. IET
Software, 8(1), pp.12-18.
Nist (2019). Cybersecurity Framework. [online] NIST. Available at: https://www.nist.gov/cyberframework
[Accessed 12 Mar. 2019].
Palvia, P. (2011). Security Risk Management: Building and Information Security Risk. Journal of
Information Privacy and Security, 7(4), pp.72-73.
Tokuyoshi, B. (2013). The security implications of BYOD. Network Security, 2013(4), pp.12-13.
7
References
Antunes, N. and Vieira, M. (2014). Penetration Testing for Web Services. Computer, 47(2), pp.30-36.
Blandford, R. (2011). Information security in the cloud. Network Security, 2011(4), pp.15-17.
Borda, M. (2015). Digital Rights Protection - a Great Challenge of the New Millennium. TELSIKS 2005 -
2005 uth International Conference on Telecommunication in ModernSatellite, Cable and Broadcasting
Services.
Kumar, S., Kumar, M., Budhiraja, R., Das, M. and Singh, S. (2018). A cryptographic model for better
information security. Journal of Information Security and Applications, 43, pp.123-138.
Michael, K. (2012). Security Risk Management: Building an Information Security Risk Management
Program from the Ground Up. Computers & Security, 31(2), pp.249-250.
Nie, T., Lu, Z. and Zhou, L. (2014). Power evaluation methods for data encryption algorithms. IET
Software, 8(1), pp.12-18.
Nist (2019). Cybersecurity Framework. [online] NIST. Available at: https://www.nist.gov/cyberframework
[Accessed 12 Mar. 2019].
Palvia, P. (2011). Security Risk Management: Building and Information Security Risk. Journal of
Information Privacy and Security, 7(4), pp.72-73.
Tokuyoshi, B. (2013). The security implications of BYOD. Network Security, 2013(4), pp.12-13.
7
1 out of 8
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
© 2024 | Zucol Services PVT LTD | All rights reserved.





