Analysis of Lightweight Encryption Scheme for Fog-to-Things Communication
VerifiedAdded on 2023/05/29
|11
|10056
|476
AI Summary
This paper discusses the security challenges, threats, requirements, fog nodes based security architectures and the possible cryptographic solutions of fog-to-things communications. It proposes a novel encryption scheme for fog-to-things communication and analyzes security challenges in terms of cybersecurity principles. The distribution of fog nodes can solve the scalability of cloud by reducing central processing and communications.
Contribute Materials
Your contribution can guide someone’s learning journey. Share your
documents today.

SPECIAL SECTION ON REAL-TIME EDGE ANALYTICS FOR BIG DATA IN INTERNET OF TH
Received March 8, 2018, accepted March 24, 2018, date of publication April 6, 2018, date of current version June 5, 2018.
Digital Object Identifier 10.1109/ACCESS.2018.2822822
Analysis of Lightweight Encryption Scheme
for Fog-to-Things Communication
ABEBE ABESHU DIRO1, NAVEEN CHILAMKURTI 1, AND YUNYOUNG NAM 2
1Department of Computer Science and Information Technology, La Trobe University, Melbourne, VIC 3083, Australia
2Department of Computer Science and Engineering, Soonchunhyang University, Asan 31538, South Korea
Corresponding author: Yunyoung Nam (ynam@sch.ac.kr)
This work was supported in part by the Soonchunhyang University Research Fund and in part by the MSIP (Ministry of Science, ICT, and
Future Planning), South Korea, through the Information Technology Research Center Support Program Supervised by the Institute for
Information and Communications Technology Promotion under Grant IITP-2018-2014-1-00720.
ABSTRACT The growing concerns in cybersecurity is preventing unknowns which evolve from time to
time.Internetof Things (IoT) is one of the emerging fields thathave been applied for smartcities and
industries.The promises of IoTs could be confronted with the growth in the number and sophistication
of cyberattacks. The extension of digital world into physical environment adds new attack surfaces on the
existing security threats of traditional Internet. The major challenge brought about by physical connectivity
of IoTs is to implementdistributed security mechanisms for resource constrain of IoT devices.As an
emerging architecture supporting IoT applications, fog computing can be considered to solve the resource
and distribution issues in securing fog-to-things communication. Security functions and services, such as
cryptography, could be offloaded to fog nodes to reduce computational and storage burdens on IoT device
The distribution of fog nodes can also solve the scalability of cloud by reducing central processing and
communications. On the other hand, lightweight cryptographic functions, such as elliptic curve cryptograph
have been proved to be suitable for embedded systems. In this paper, we have analyzed security challenge
terms of cybersecurity principles and proposed a novel encryption scheme for fog-to-things communication
INDEX TERMS Cybersecurity, Internet of things, fog computing, elliptic curve cryptography, lightweight
cryptography.
I. INTRODUCTION
By the end ofthis decade,the exponentialgrowth in the
number of connected smartthings,known as IoTs,is esti-
mated to be about6 times the population ofthe world.
The adoption speed of these smartdevices is unprecedent-
edly aboutfive folds of the adoption history of electricity
and telephony altogether.The main contributing factor for
this increment in connectivity is the digitalization of home
devices (refrigerators,fans),smartcity applications (con-
nected cars, smart traffic lights, smart grids, smart water util-
ities) and operational technologies (factory machines) across
the globe.The trend has been ignited by the shiftfrom
IPv4 based Information technology (IT)to IPv6 oriented
operationaltechnology (OT).The invention of IPv6 is one
of the crucial enablers of the deployment of IoT as Ipv4 is
unable to meet the requirements of the massive connections of
IoT networks [1], [2].
The massive scale adoption ofIoTs, and the big data
generation in the vicinity trigger businesses and industries to
rethink the architecture of data processing, storage and com-
munications. The myriad of cloud computing applications in
business, industries, public services, etc. have been mag
icentover the lastdecades.Cloud computing has brought
essential breakthroughs of seamless IT outsourcing capa
with value-added services for customers. However, the c
rent explosion of edge computing paradigms has challen
the scalability and performance of centralized cloud for
applications [3]. Real-time applications such as smart ci
eHealth,intelligenttransportsystems,industries,etc.need
predictable and low latency,and distributed low bandwidth
communication from IoT end to data repositories,where
cloud computing cannot satisfy the requirements. To mi
these issues, distributed intelligence, known as fog com
ing (FC),that bridges cloud computing closer to the thing
has been introduced. Fig.1 shows typical fog architectur
the things-to-cloud continuum.
FC complements cloud computing as itforms a service
continuum between IoT and the cloud. Fog network mim
the cloud-to-things way of interaction at the edge netwo
It bridges the gap between the cloud and smart things, w
enables a service continuum. The gap is closed in the fo
enabling the distribution of computing and control, stora
26820
2169-3536 2018 IEEE. Translations and content mining are permitted for academic research only.
Personal use is also permitted, but republication/redistribution requires IEEE permission.
See http://www.ieee.org/publications_standards/publications/rights/index.html for more information.
VOLUME 6, 2018
Received March 8, 2018, accepted March 24, 2018, date of publication April 6, 2018, date of current version June 5, 2018.
Digital Object Identifier 10.1109/ACCESS.2018.2822822
Analysis of Lightweight Encryption Scheme
for Fog-to-Things Communication
ABEBE ABESHU DIRO1, NAVEEN CHILAMKURTI 1, AND YUNYOUNG NAM 2
1Department of Computer Science and Information Technology, La Trobe University, Melbourne, VIC 3083, Australia
2Department of Computer Science and Engineering, Soonchunhyang University, Asan 31538, South Korea
Corresponding author: Yunyoung Nam (ynam@sch.ac.kr)
This work was supported in part by the Soonchunhyang University Research Fund and in part by the MSIP (Ministry of Science, ICT, and
Future Planning), South Korea, through the Information Technology Research Center Support Program Supervised by the Institute for
Information and Communications Technology Promotion under Grant IITP-2018-2014-1-00720.
ABSTRACT The growing concerns in cybersecurity is preventing unknowns which evolve from time to
time.Internetof Things (IoT) is one of the emerging fields thathave been applied for smartcities and
industries.The promises of IoTs could be confronted with the growth in the number and sophistication
of cyberattacks. The extension of digital world into physical environment adds new attack surfaces on the
existing security threats of traditional Internet. The major challenge brought about by physical connectivity
of IoTs is to implementdistributed security mechanisms for resource constrain of IoT devices.As an
emerging architecture supporting IoT applications, fog computing can be considered to solve the resource
and distribution issues in securing fog-to-things communication. Security functions and services, such as
cryptography, could be offloaded to fog nodes to reduce computational and storage burdens on IoT device
The distribution of fog nodes can also solve the scalability of cloud by reducing central processing and
communications. On the other hand, lightweight cryptographic functions, such as elliptic curve cryptograph
have been proved to be suitable for embedded systems. In this paper, we have analyzed security challenge
terms of cybersecurity principles and proposed a novel encryption scheme for fog-to-things communication
INDEX TERMS Cybersecurity, Internet of things, fog computing, elliptic curve cryptography, lightweight
cryptography.
I. INTRODUCTION
By the end ofthis decade,the exponentialgrowth in the
number of connected smartthings,known as IoTs,is esti-
mated to be about6 times the population ofthe world.
The adoption speed of these smartdevices is unprecedent-
edly aboutfive folds of the adoption history of electricity
and telephony altogether.The main contributing factor for
this increment in connectivity is the digitalization of home
devices (refrigerators,fans),smartcity applications (con-
nected cars, smart traffic lights, smart grids, smart water util-
ities) and operational technologies (factory machines) across
the globe.The trend has been ignited by the shiftfrom
IPv4 based Information technology (IT)to IPv6 oriented
operationaltechnology (OT).The invention of IPv6 is one
of the crucial enablers of the deployment of IoT as Ipv4 is
unable to meet the requirements of the massive connections of
IoT networks [1], [2].
The massive scale adoption ofIoTs, and the big data
generation in the vicinity trigger businesses and industries to
rethink the architecture of data processing, storage and com-
munications. The myriad of cloud computing applications in
business, industries, public services, etc. have been mag
icentover the lastdecades.Cloud computing has brought
essential breakthroughs of seamless IT outsourcing capa
with value-added services for customers. However, the c
rent explosion of edge computing paradigms has challen
the scalability and performance of centralized cloud for
applications [3]. Real-time applications such as smart ci
eHealth,intelligenttransportsystems,industries,etc.need
predictable and low latency,and distributed low bandwidth
communication from IoT end to data repositories,where
cloud computing cannot satisfy the requirements. To mi
these issues, distributed intelligence, known as fog com
ing (FC),that bridges cloud computing closer to the thing
has been introduced. Fig.1 shows typical fog architectur
the things-to-cloud continuum.
FC complements cloud computing as itforms a service
continuum between IoT and the cloud. Fog network mim
the cloud-to-things way of interaction at the edge netwo
It bridges the gap between the cloud and smart things, w
enables a service continuum. The gap is closed in the fo
enabling the distribution of computing and control, stora
26820
2169-3536 2018 IEEE. Translations and content mining are permitted for academic research only.
Personal use is also permitted, but republication/redistribution requires IEEE permission.
See http://www.ieee.org/publications_standards/publications/rights/index.html for more information.
VOLUME 6, 2018
Secure Best Marks with AI Grader
Need help grading? Try our AI Grader for instant feedback on your assignments.

A. A. Diro et al.:Analysis of Lightweight Encryption Scheme for Fog-to-Things Communication
FIGURE 1.Basic Architecture of a fog network [8].
and networking functions closer to smart objects [4],[5] at
any location across the continuum.
II. SECURITY SCHEMES IN FOG-TO-THINGS
COMMUNICATION
The importance ofsecurity mechanismsfor unprotected
smartdevices is unquestionable.For instance,smartgrid
users need authentication and authorization mechanisms to
enable only subscribed users can access electric bills. Simi-
larly, in smart life, healthcare systems require only physicians
and nurses to notify about the status of patients as confiden-
tiality has ultimate importance.In both cases,unauthorized
adversaries should not eavesdrop on or access to the messages
sent by clients.
In this section, we discuss the security challenges, threats,
requirements, fog nodes based security architectures and the
possible cryptographic solutions of fog-to-things communi-
cations.
A. SECURITY CHALLENGES
The promises of FC could be challenged by the growth in the
number and sophistication of cyber-attacks in the communi-
cations of fog-to-things. The existing security threats of the
traditional Internet will continue to be the threats of fog-to-
things interactions. It is also evident that the extension of core
networks to the physical world brings more devices, interac-
tions,and protocols which can broaden attack surfaces and
born new cyber threats. The major challenge brought about
by physical connectivity is to implement distributed security
mechanisms for fog-to-things communication for resource
constrain of IoT devices [6]–[9]. It is bandwidth inefficient,
prone to high latency and suffer from scalability to offload
security functions ofmassively distributed IoT devices to
cloud while it is computationally prohibitive to deploy secu-
rity schemes on the devices. For instance, smart meter micro-
controller has no capability of performing traditional Internet
cryptographic operations, and the connection to cloud incurs
a significantbandwidth costand high latency for wireless
communication dominantIoT environment.The emerging
field of IoT needs a robust and lightweight security schemes.
In traditionalInternet,it is eitherthe device orthe cen-
tralized cloud that handles resource-intensive cybersecu
operations such as cryptographic encryption, access con
authentication, and authorization. These existing cybers
rity schemes for resource-rich infrastructure cannotprevail
for addressing IoT cybersecurity challenges. The distribu
and resource limitations of IoT devices in securing IoTs c
be tackled by offloading securing functions to the distrib
fog nodes [10]. Thus, fog nodes can be employed to offl
cryptographic computations as proxy nodes without rev
the data in communications.
B. SECURITY THREATS
The IoT/Fog computing ecosystem is partly confronted w
the same cybersecurity challenges as traditional IT ecos
tem.IoT devices add a completely differentdimension to
cybersecurity world because of their physical interaction
the Internet.This is a serious implication thatshows the
transformation of attack surfaces from digital world (dat
physical world (actuation), which can broaden the horizo
known threats to zero-day attacks of new devices, workfl
and protocols [11].The attack surface of fog-to-things can
further be expanded as closed operationalsystems such as
SCADA are moving to IP based open systems.
The majorattacksin fog-to-thingsare impersonation,
M-in-M, injection and DoS attacks [17]–[19]. Impersonat
attack is a form of attack pretending to have legitimate
tity using some other entity’s identity.In the fog-to-things
scenario,IoT devices could be eavesdropped or sniffed for
identity.As wireless communication is the common platfo
of communication in the ecosystem,it is one of the most
commonly observed attacks in the IoT use cases. This ki
of spoofing attack might target the identity-based authe
cation systems which use MAC and IP addresses.Man-in-
the-middle (MitM) attack is another type of impersonatio
attack in which the third node intercepts the communica
tions between two nodes to capture data or authenticat
credentials. For instance, a simple mobile node (e.g. car
Zeus) can act as a middleman to impersonate a sensor a
communicating fog node in the domain of Fog-to-things
work. In addition, a replay attack occurs when an advers
captures some parts of a communication between two n
and then retransmits the captured information, usually s
rity credentials,later to bypass authentication mechanisms
A rogue fog node could be installed as a replay or MitM
node in the Fog network eitherby the legitimate internal
entity or cyber attacker withoutexplicitauthorization.For
instance, a malicious rogue smart grid aggregator can ta
the data with smart meter creating wrong readings or it
modify IP addresses.Since itis stealthy to detect,a rogue
node can instantiate further attacks such as DoS,causing a
threat to data security and privacy [27], [28]. These indi
that strong identity management and mutual authentica
and encryption are the key elements for enhancing the
rity and privacy of IoT.
VOLUME 6, 2018 26821
FIGURE 1.Basic Architecture of a fog network [8].
and networking functions closer to smart objects [4],[5] at
any location across the continuum.
II. SECURITY SCHEMES IN FOG-TO-THINGS
COMMUNICATION
The importance ofsecurity mechanismsfor unprotected
smartdevices is unquestionable.For instance,smartgrid
users need authentication and authorization mechanisms to
enable only subscribed users can access electric bills. Simi-
larly, in smart life, healthcare systems require only physicians
and nurses to notify about the status of patients as confiden-
tiality has ultimate importance.In both cases,unauthorized
adversaries should not eavesdrop on or access to the messages
sent by clients.
In this section, we discuss the security challenges, threats,
requirements, fog nodes based security architectures and the
possible cryptographic solutions of fog-to-things communi-
cations.
A. SECURITY CHALLENGES
The promises of FC could be challenged by the growth in the
number and sophistication of cyber-attacks in the communi-
cations of fog-to-things. The existing security threats of the
traditional Internet will continue to be the threats of fog-to-
things interactions. It is also evident that the extension of core
networks to the physical world brings more devices, interac-
tions,and protocols which can broaden attack surfaces and
born new cyber threats. The major challenge brought about
by physical connectivity is to implement distributed security
mechanisms for fog-to-things communication for resource
constrain of IoT devices [6]–[9]. It is bandwidth inefficient,
prone to high latency and suffer from scalability to offload
security functions ofmassively distributed IoT devices to
cloud while it is computationally prohibitive to deploy secu-
rity schemes on the devices. For instance, smart meter micro-
controller has no capability of performing traditional Internet
cryptographic operations, and the connection to cloud incurs
a significantbandwidth costand high latency for wireless
communication dominantIoT environment.The emerging
field of IoT needs a robust and lightweight security schemes.
In traditionalInternet,it is eitherthe device orthe cen-
tralized cloud that handles resource-intensive cybersecu
operations such as cryptographic encryption, access con
authentication, and authorization. These existing cybers
rity schemes for resource-rich infrastructure cannotprevail
for addressing IoT cybersecurity challenges. The distribu
and resource limitations of IoT devices in securing IoTs c
be tackled by offloading securing functions to the distrib
fog nodes [10]. Thus, fog nodes can be employed to offl
cryptographic computations as proxy nodes without rev
the data in communications.
B. SECURITY THREATS
The IoT/Fog computing ecosystem is partly confronted w
the same cybersecurity challenges as traditional IT ecos
tem.IoT devices add a completely differentdimension to
cybersecurity world because of their physical interaction
the Internet.This is a serious implication thatshows the
transformation of attack surfaces from digital world (dat
physical world (actuation), which can broaden the horizo
known threats to zero-day attacks of new devices, workfl
and protocols [11].The attack surface of fog-to-things can
further be expanded as closed operationalsystems such as
SCADA are moving to IP based open systems.
The majorattacksin fog-to-thingsare impersonation,
M-in-M, injection and DoS attacks [17]–[19]. Impersonat
attack is a form of attack pretending to have legitimate
tity using some other entity’s identity.In the fog-to-things
scenario,IoT devices could be eavesdropped or sniffed for
identity.As wireless communication is the common platfo
of communication in the ecosystem,it is one of the most
commonly observed attacks in the IoT use cases. This ki
of spoofing attack might target the identity-based authe
cation systems which use MAC and IP addresses.Man-in-
the-middle (MitM) attack is another type of impersonatio
attack in which the third node intercepts the communica
tions between two nodes to capture data or authenticat
credentials. For instance, a simple mobile node (e.g. car
Zeus) can act as a middleman to impersonate a sensor a
communicating fog node in the domain of Fog-to-things
work. In addition, a replay attack occurs when an advers
captures some parts of a communication between two n
and then retransmits the captured information, usually s
rity credentials,later to bypass authentication mechanisms
A rogue fog node could be installed as a replay or MitM
node in the Fog network eitherby the legitimate internal
entity or cyber attacker withoutexplicitauthorization.For
instance, a malicious rogue smart grid aggregator can ta
the data with smart meter creating wrong readings or it
modify IP addresses.Since itis stealthy to detect,a rogue
node can instantiate further attacks such as DoS,causing a
threat to data security and privacy [27], [28]. These indi
that strong identity management and mutual authentica
and encryption are the key elements for enhancing the
rity and privacy of IoT.
VOLUME 6, 2018 26821
A. A. Diro et al.:Analysis of Lightweight Encryption Scheme for Fog-to-Things Communication
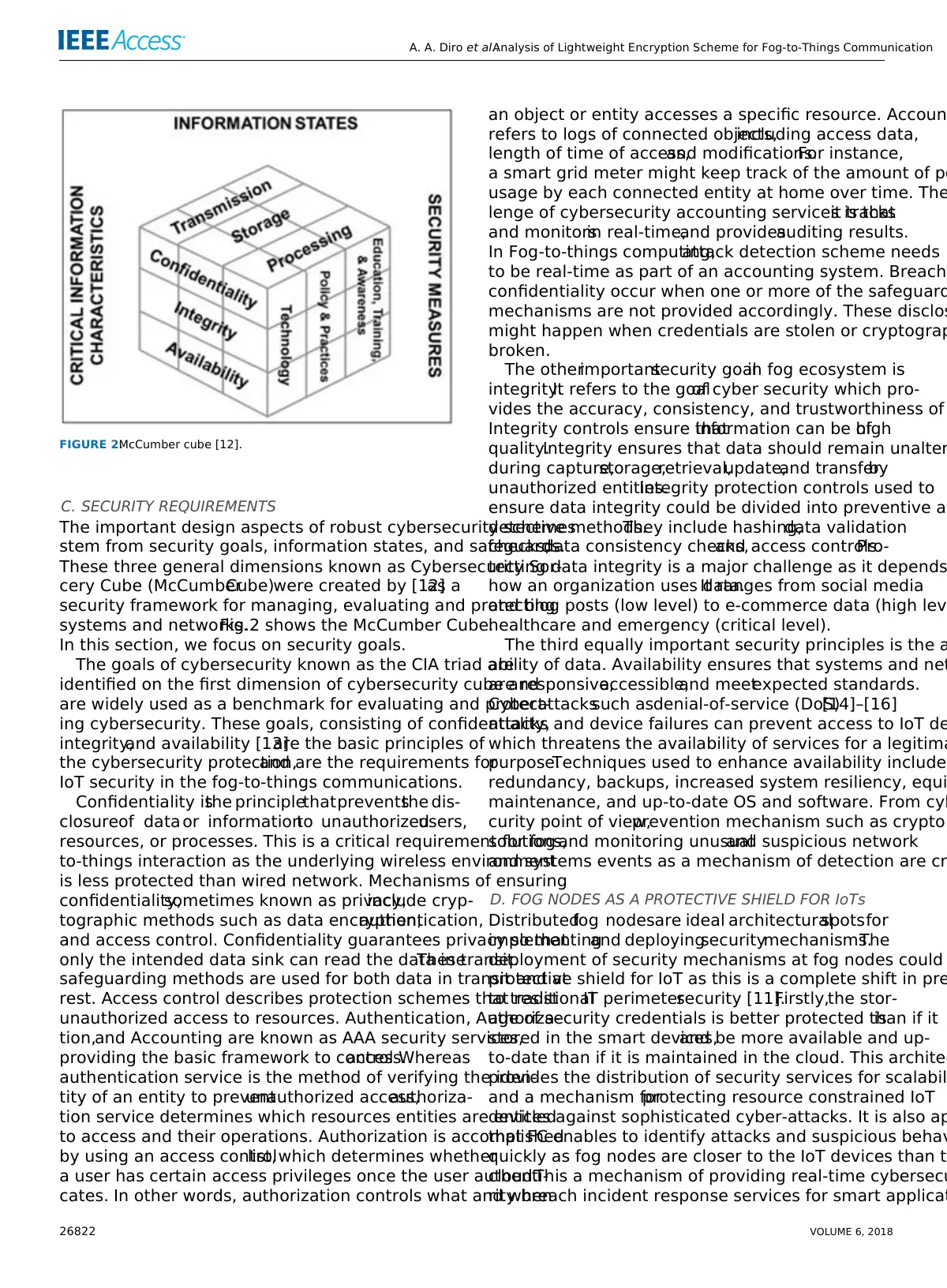
FIGURE 2.McCumber cube [12].
C. SECURITY REQUIREMENTS
The important design aspects of robust cybersecurity schemes
stem from security goals, information states, and safeguards.
These three general dimensions known as Cybersecurity Sor-
cery Cube (McCumberCube)were created by [12]as a
security framework for managing, evaluating and protecting
systems and networks.Fig.2 shows the McCumber Cube.
In this section, we focus on security goals.
The goals of cybersecurity known as the CIA triad are
identified on the first dimension of cybersecurity cube and
are widely used as a benchmark for evaluating and protect-
ing cybersecurity. These goals, consisting of confidentiality,
integrity,and availability [13]are the basic principles of
the cybersecurity protection,and are the requirements for
IoT security in the fog-to-things communications.
Confidentiality isthe principlethatpreventsthe dis-
closureof data or informationto unauthorizedusers,
resources, or processes. This is a critical requirement for fog-
to-things interaction as the underlying wireless environment
is less protected than wired network. Mechanisms of ensuring
confidentiality,sometimes known as privacy,include cryp-
tographic methods such as data encryption,authentication,
and access control. Confidentiality guarantees privacy so that
only the intended data sink can read the data in transit.These
safeguarding methods are used for both data in transit and at
rest. Access control describes protection schemes that resist
unauthorized access to resources. Authentication, Authoriza-
tion,and Accounting are known as AAA security services,
providing the basic framework to controlaccess.Whereas
authentication service is the method of verifying the iden-
tity of an entity to preventunauthorized access,authoriza-
tion service determines which resources entities are entitled
to access and their operations. Authorization is accomplished
by using an access controllist,which determines whether
a user has certain access privileges once the user authenti-
cates. In other words, authorization controls what and when
an object or entity accesses a specific resource. Accoun
refers to logs of connected objects,including access data,
length of time of access,and modifications.For instance,
a smart grid meter might keep track of the amount of po
usage by each connected entity at home over time. The
lenge of cybersecurity accounting services is thatit tracks
and monitorsin real-time,and providesauditing results.
In Fog-to-things computing,attack detection scheme needs
to be real-time as part of an accounting system. Breache
confidentiality occur when one or more of the safeguard
mechanisms are not provided accordingly. These disclos
might happen when credentials are stolen or cryptograp
broken.
The otherimportantsecurity goalin fog ecosystem is
integrity.It refers to the goalof cyber security which pro-
vides the accuracy, consistency, and trustworthiness of
Integrity controls ensure thatinformation can be ofhigh
quality.Integrity ensures that data should remain unalter
during capture,storage,retrieval,update,and transferby
unauthorized entities.Integrity protection controls used to
ensure data integrity could be divided into preventive an
detective methods.They include hashing,data validation
checks,data consistency checks,and access controls.Pro-
tecting data integrity is a major challenge as it depends
how an organization uses data.It ranges from social media
and blog posts (low level) to e-commerce data (high leve
healthcare and emergency (critical level).
The third equally important security principles is the a
ability of data. Availability ensures that systems and net
are responsive,accessible,and meetexpected standards.
Cyberattackssuch asdenial-of-service (DoS)[14]–[16]
attacks and device failures can prevent access to IoT de
which threatens the availability of services for a legitima
purpose.Techniques used to enhance availability include
redundancy, backups, increased system resiliency, equi
maintenance, and up-to-date OS and software. From cyb
curity point of view,prevention mechanism such as crypto
solutions,and monitoring unusualand suspicious network
and systems events as a mechanism of detection are cr
D. FOG NODES AS A PROTECTIVE SHIELD FOR IoTs
Distributedfog nodesare ideal architecturalspotsfor
implementingand deployingsecuritymechanisms.The
deployment of security mechanisms at fog nodes could
protective shield for IoT as this is a complete shift in pre
to traditionalIT perimetersecurity [11].Firstly,the stor-
age of security credentials is better protected than if itis
stored in the smart devices,and be more available and up-
to-date than if it is maintained in the cloud. This architec
provides the distribution of security services for scalabil
and a mechanism forprotecting resource constrained IoT
devices against sophisticated cyber-attacks. It is also ap
that FC enables to identify attacks and suspicious behav
quickly as fog nodes are closer to the IoT devices than th
cloud.This a mechanism of providing real-time cybersecu
rity breach incident response services for smart applicat
26822 VOLUME 6, 2018
FIGURE 2.McCumber cube [12].
C. SECURITY REQUIREMENTS
The important design aspects of robust cybersecurity schemes
stem from security goals, information states, and safeguards.
These three general dimensions known as Cybersecurity Sor-
cery Cube (McCumberCube)were created by [12]as a
security framework for managing, evaluating and protecting
systems and networks.Fig.2 shows the McCumber Cube.
In this section, we focus on security goals.
The goals of cybersecurity known as the CIA triad are
identified on the first dimension of cybersecurity cube and
are widely used as a benchmark for evaluating and protect-
ing cybersecurity. These goals, consisting of confidentiality,
integrity,and availability [13]are the basic principles of
the cybersecurity protection,and are the requirements for
IoT security in the fog-to-things communications.
Confidentiality isthe principlethatpreventsthe dis-
closureof data or informationto unauthorizedusers,
resources, or processes. This is a critical requirement for fog-
to-things interaction as the underlying wireless environment
is less protected than wired network. Mechanisms of ensuring
confidentiality,sometimes known as privacy,include cryp-
tographic methods such as data encryption,authentication,
and access control. Confidentiality guarantees privacy so that
only the intended data sink can read the data in transit.These
safeguarding methods are used for both data in transit and at
rest. Access control describes protection schemes that resist
unauthorized access to resources. Authentication, Authoriza-
tion,and Accounting are known as AAA security services,
providing the basic framework to controlaccess.Whereas
authentication service is the method of verifying the iden-
tity of an entity to preventunauthorized access,authoriza-
tion service determines which resources entities are entitled
to access and their operations. Authorization is accomplished
by using an access controllist,which determines whether
a user has certain access privileges once the user authenti-
cates. In other words, authorization controls what and when
an object or entity accesses a specific resource. Accoun
refers to logs of connected objects,including access data,
length of time of access,and modifications.For instance,
a smart grid meter might keep track of the amount of po
usage by each connected entity at home over time. The
lenge of cybersecurity accounting services is thatit tracks
and monitorsin real-time,and providesauditing results.
In Fog-to-things computing,attack detection scheme needs
to be real-time as part of an accounting system. Breache
confidentiality occur when one or more of the safeguard
mechanisms are not provided accordingly. These disclos
might happen when credentials are stolen or cryptograp
broken.
The otherimportantsecurity goalin fog ecosystem is
integrity.It refers to the goalof cyber security which pro-
vides the accuracy, consistency, and trustworthiness of
Integrity controls ensure thatinformation can be ofhigh
quality.Integrity ensures that data should remain unalter
during capture,storage,retrieval,update,and transferby
unauthorized entities.Integrity protection controls used to
ensure data integrity could be divided into preventive an
detective methods.They include hashing,data validation
checks,data consistency checks,and access controls.Pro-
tecting data integrity is a major challenge as it depends
how an organization uses data.It ranges from social media
and blog posts (low level) to e-commerce data (high leve
healthcare and emergency (critical level).
The third equally important security principles is the a
ability of data. Availability ensures that systems and net
are responsive,accessible,and meetexpected standards.
Cyberattackssuch asdenial-of-service (DoS)[14]–[16]
attacks and device failures can prevent access to IoT de
which threatens the availability of services for a legitima
purpose.Techniques used to enhance availability include
redundancy, backups, increased system resiliency, equi
maintenance, and up-to-date OS and software. From cyb
curity point of view,prevention mechanism such as crypto
solutions,and monitoring unusualand suspicious network
and systems events as a mechanism of detection are cr
D. FOG NODES AS A PROTECTIVE SHIELD FOR IoTs
Distributedfog nodesare ideal architecturalspotsfor
implementingand deployingsecuritymechanisms.The
deployment of security mechanisms at fog nodes could
protective shield for IoT as this is a complete shift in pre
to traditionalIT perimetersecurity [11].Firstly,the stor-
age of security credentials is better protected than if itis
stored in the smart devices,and be more available and up-
to-date than if it is maintained in the cloud. This architec
provides the distribution of security services for scalabil
and a mechanism forprotecting resource constrained IoT
devices against sophisticated cyber-attacks. It is also ap
that FC enables to identify attacks and suspicious behav
quickly as fog nodes are closer to the IoT devices than th
cloud.This a mechanism of providing real-time cybersecu
rity breach incident response services for smart applicat
26822 VOLUME 6, 2018

A. A. Diro et al.:Analysis of Lightweight Encryption Scheme for Fog-to-Things Communication
particularly for smart grids,critical industry functions,and
smartcities.Suppose thatcybersecurity system forsmart
grid and the connected car is provided by the cloud provider
and infected by malware which can completely block the
power generators in the grid or engines of the car.In both
cases, the complete shutdown of the systems is catastrophic
to delay.Furthermore,FC creates an environmentof col-
laborative attack fighting in which IoT devices share attack
signatures and experiences For instance, artificial intelligence
based lightweight intrusion detection can be implemented on
collaborative Fog nodes in collaboration to detect suspicious
traffic.Moreover,as data communications are confined to
distributed edge networks, FC design protects eavesdropping
easier than core networks such as the cloud. Thus, the deploy-
ment of security services and functions at fog nodes for IoT
applications is an ideal solution.
E. SECURITY MECHANISMS
Cryptographic solutions have been playing major roles in
secreting Internet. The most widely used functions of cryp-
tography are authentication and encryption. As it is connected
to Internet,Fog-to-things computing inherits threats from
traditional Internet.The environment is also prone to zero-
day attacks as a result of newly introduced flaws in emerging
protocols, workflows and devices. Thus, cybersecurity mech-
anisms such as authentication,encryption and access con-
trol [16] need to be implemented in fog-to-things computing
using cryptographic elements.
Mutual authentication has been a fundamental cybersecu-
rity mechanism in securing traditional networks against both
internal and external attacks. This control is even more impor-
tantin fog-to-things computing as trustis utmostneeded
in this ecosystem because of their large-scale communica-
tion.Reference [18]describes authentication as the core
layer of security framework in IoT/Fog computing in man-
aging strong identity,non-repudiation and building trustin
the ecosystem.By building trust,it is viable to combat
threats such as man-in-the-middle, impersonation, and replay
attacks,which are the mostthreatening attacks in IoT/fog
computing.Architecturalwise,authentication architectures
such as 802.1AR/ IEEE 802.1X could be extended for fog
systems. However, authentication itself cannot guarantee the
delivery of data withouteavesdropping or modification by
adversaries.
The transportation of data over an insecure channel such as
wireless should be guarded by encryption mechanisms. The
state of the art of encryption schemes is dependent on cryp-
tographic suites such as Advanced Encryption Suite (AES)
for confidential data transport,and Rivest-Shamir-Adleman
(RSA) for digital signatures. While the algorithms are robust
in fulfilling security requirements,they are notdirectly
suitable for resource-constrained IoT/Fog networks as they
require high resource usage.As resources are owned by
multi-parties and users, access control also plays a pivotal role
in the security of fog computing. Privacy has been always a
major concern of Internet, but more crucial for IoT because
FIGURE 3.Typical elliptic curves.
these devices hostapplications thattrace the location and
behaviors of individuals. The good scenarios of privacy i
are health care systems in which medicalequipmentare
tracked,and vitalpatientdata are monitored.In this case,
the identity of the device should be known without reve
the identity of the owner. As a combating mechanism, c
tographic elements still play the major role in cybersecu
of Internet and continues to be on the internet of things
well for their robustness. Because of resource limitations
IoT/Fog networks and evolving nature of cybersecurity, h
ever, the traditional cryptographic mechanisms such as
fail to support fog-to-things computing.Thus,investigating
lightweight cryptographic suites is of great importance.
III. ECC AS A LIGHTWEIGHT CRYPTOGRAPHIC SOLUTION
A. OVERVIEW
Proposed by Koblitz and Miller in the 1980s using group
points on an elliptic curve defined overa finite field in
discrete logarithmic cryptosystems,Elliptic curve cryptog-
raphy (ECC) is an algebraic method that uses the proper
of elliptic curves to produce cryptographic algorithms. T
curve is expressed overa non-singularcubic polynomial
equation with two unknowns over a field F in the form of
y2 = x3 + ax + b (mod F), where 4a3 + 27b2 (mod p) 6= 0.
Elliptic curves have the property thatif a straightline that
intersects the curve in two points is drawn, it will also in
sect the curve in a third point that is either on the curve
pointof infinity.The mirror of this third pointover x-axis
is the addition of the two points,which is crucialfor key
generation. The other important property of elliptic curv
that if you have a point P (x, y) then -P will be (x, −y), i.e
two vertical lines that never cross the curve at the third
(P − P = 0) or cross at infinity.In another word,they are
symmetric over the x-axis. It has also the domain D = (q
a,b, P, n),where q is a prime number,F is the field,a and
b are the curve coefficients, P is the base point and n is
order of P. Fig. 3 shows examples of elliptic curves.
The common way to performing multiplication of point
in elliptic curves is through point doubling (P + P = 2P).
In general, ECC point additions of P (x1, y1) and Q (x2, y
VOLUME 6, 2018 26823
particularly for smart grids,critical industry functions,and
smartcities.Suppose thatcybersecurity system forsmart
grid and the connected car is provided by the cloud provider
and infected by malware which can completely block the
power generators in the grid or engines of the car.In both
cases, the complete shutdown of the systems is catastrophic
to delay.Furthermore,FC creates an environmentof col-
laborative attack fighting in which IoT devices share attack
signatures and experiences For instance, artificial intelligence
based lightweight intrusion detection can be implemented on
collaborative Fog nodes in collaboration to detect suspicious
traffic.Moreover,as data communications are confined to
distributed edge networks, FC design protects eavesdropping
easier than core networks such as the cloud. Thus, the deploy-
ment of security services and functions at fog nodes for IoT
applications is an ideal solution.
E. SECURITY MECHANISMS
Cryptographic solutions have been playing major roles in
secreting Internet. The most widely used functions of cryp-
tography are authentication and encryption. As it is connected
to Internet,Fog-to-things computing inherits threats from
traditional Internet.The environment is also prone to zero-
day attacks as a result of newly introduced flaws in emerging
protocols, workflows and devices. Thus, cybersecurity mech-
anisms such as authentication,encryption and access con-
trol [16] need to be implemented in fog-to-things computing
using cryptographic elements.
Mutual authentication has been a fundamental cybersecu-
rity mechanism in securing traditional networks against both
internal and external attacks. This control is even more impor-
tantin fog-to-things computing as trustis utmostneeded
in this ecosystem because of their large-scale communica-
tion.Reference [18]describes authentication as the core
layer of security framework in IoT/Fog computing in man-
aging strong identity,non-repudiation and building trustin
the ecosystem.By building trust,it is viable to combat
threats such as man-in-the-middle, impersonation, and replay
attacks,which are the mostthreatening attacks in IoT/fog
computing.Architecturalwise,authentication architectures
such as 802.1AR/ IEEE 802.1X could be extended for fog
systems. However, authentication itself cannot guarantee the
delivery of data withouteavesdropping or modification by
adversaries.
The transportation of data over an insecure channel such as
wireless should be guarded by encryption mechanisms. The
state of the art of encryption schemes is dependent on cryp-
tographic suites such as Advanced Encryption Suite (AES)
for confidential data transport,and Rivest-Shamir-Adleman
(RSA) for digital signatures. While the algorithms are robust
in fulfilling security requirements,they are notdirectly
suitable for resource-constrained IoT/Fog networks as they
require high resource usage.As resources are owned by
multi-parties and users, access control also plays a pivotal role
in the security of fog computing. Privacy has been always a
major concern of Internet, but more crucial for IoT because
FIGURE 3.Typical elliptic curves.
these devices hostapplications thattrace the location and
behaviors of individuals. The good scenarios of privacy i
are health care systems in which medicalequipmentare
tracked,and vitalpatientdata are monitored.In this case,
the identity of the device should be known without reve
the identity of the owner. As a combating mechanism, c
tographic elements still play the major role in cybersecu
of Internet and continues to be on the internet of things
well for their robustness. Because of resource limitations
IoT/Fog networks and evolving nature of cybersecurity, h
ever, the traditional cryptographic mechanisms such as
fail to support fog-to-things computing.Thus,investigating
lightweight cryptographic suites is of great importance.
III. ECC AS A LIGHTWEIGHT CRYPTOGRAPHIC SOLUTION
A. OVERVIEW
Proposed by Koblitz and Miller in the 1980s using group
points on an elliptic curve defined overa finite field in
discrete logarithmic cryptosystems,Elliptic curve cryptog-
raphy (ECC) is an algebraic method that uses the proper
of elliptic curves to produce cryptographic algorithms. T
curve is expressed overa non-singularcubic polynomial
equation with two unknowns over a field F in the form of
y2 = x3 + ax + b (mod F), where 4a3 + 27b2 (mod p) 6= 0.
Elliptic curves have the property thatif a straightline that
intersects the curve in two points is drawn, it will also in
sect the curve in a third point that is either on the curve
pointof infinity.The mirror of this third pointover x-axis
is the addition of the two points,which is crucialfor key
generation. The other important property of elliptic curv
that if you have a point P (x, y) then -P will be (x, −y), i.e
two vertical lines that never cross the curve at the third
(P − P = 0) or cross at infinity.In another word,they are
symmetric over the x-axis. It has also the domain D = (q
a,b, P, n),where q is a prime number,F is the field,a and
b are the curve coefficients, P is the base point and n is
order of P. Fig. 3 shows examples of elliptic curves.
The common way to performing multiplication of point
in elliptic curves is through point doubling (P + P = 2P).
In general, ECC point additions of P (x1, y1) and Q (x2, y
VOLUME 6, 2018 26823
Secure Best Marks with AI Grader
Need help grading? Try our AI Grader for instant feedback on your assignments.
A. A. Diro et al.:Analysis of Lightweight Encryption Scheme for Fog-to-Things Communication
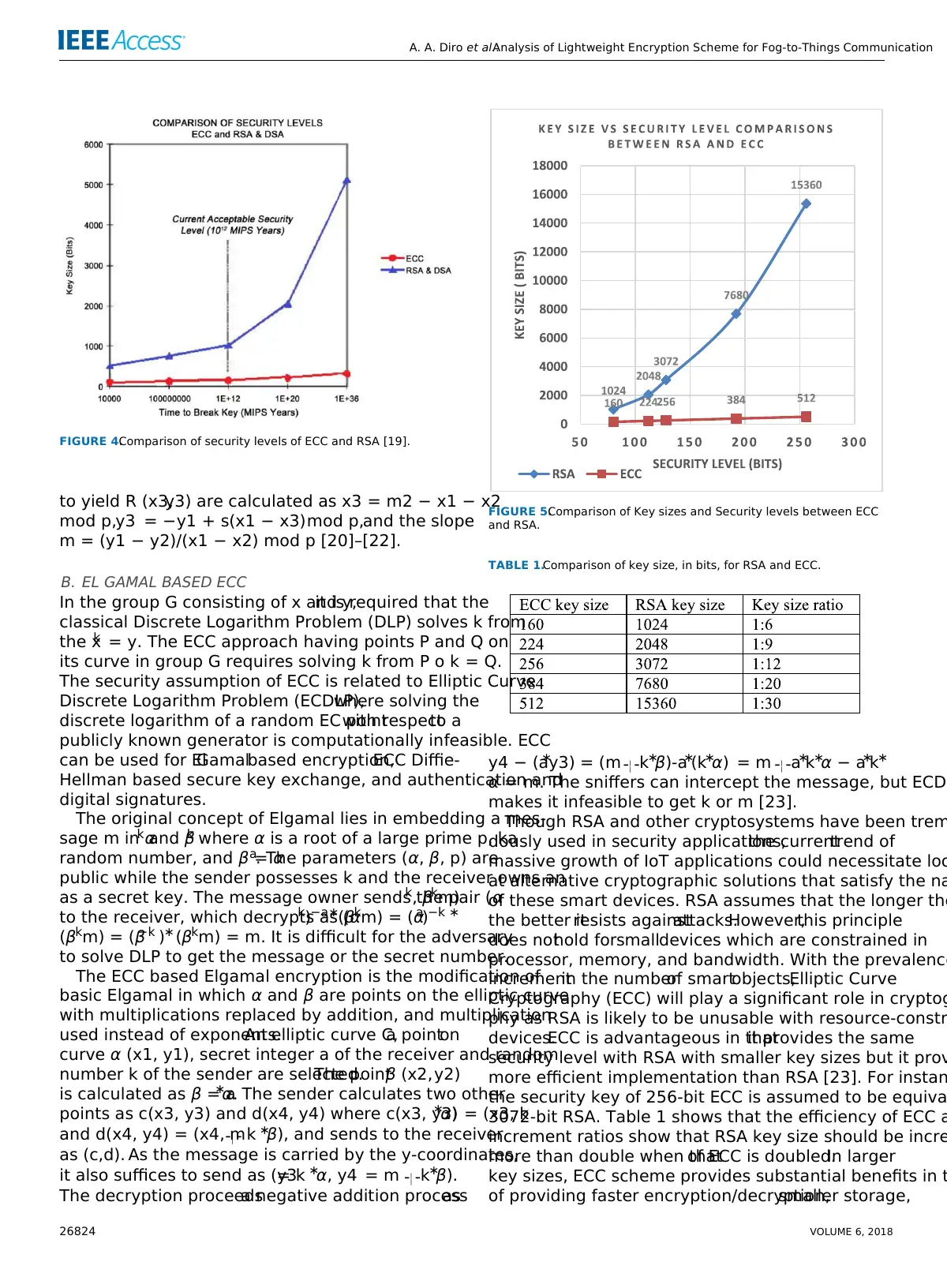
FIGURE 4.Comparison of security levels of ECC and RSA [19].
to yield R (x3,y3) are calculated as x3 = m2 − x1 − x2
mod p,y3 = −y1 + s(x1 − x3)mod p,and the slope
m = (y1 − y2)/(x1 − x2) mod p [20]–[22].
B. EL GAMAL BASED ECC
In the group G consisting of x and y,it is required that the
classical Discrete Logarithm Problem (DLP) solves k from
the xk = y. The ECC approach having points P and Q on
its curve in group G requires solving k from P o k = Q.
The security assumption of ECC is related to Elliptic Curve
Discrete Logarithm Problem (ECDLP),where solving the
discrete logarithm of a random EC pointwith respectto a
publicly known generator is computationally infeasible. ECC
can be used for ElGamalbased encryption,ECC Diffie-
Hellman based secure key exchange, and authentication and
digital signatures.
The original concept of Elgamal lies in embedding a mes-
sage m in αk and βk where α is a root of a large prime p, ka
random number, and β = αa. The parameters (α, β, p) are
public while the sender possesses k and the receiver owns an
as a secret key. The message owner sends the pair (αk, βkm)
to the receiver, which decrypts as (αk)−a∗(βkm) = (αa)−k ∗
(βkm) = (β−k )∗(βkm) = m. It is difficult for the adversary
to solve DLP to get the message or the secret number.
The ECC based Elgamal encryption is the modification of
basic Elgamal in which α and β are points on the elliptic curve
with multiplications replaced by addition, and multiplication
used instead of exponents.An elliptic curve C,a pointon
curve α (x1, y1), secret integer a of the receiver and random
number k of the sender are selected.The pointβ (x2,y2)
is calculated as β = a∗α. The sender calculates two other
points as c(x3, y3) and d(x4, y4) where c(x3, y3) = (x3, k∗α)
and d(x4, y4) = (x4, m|
- -| k ∗β), and sends to the receiver
as (c,d). As the message is carried by the y-coordinates,
it also suffices to send as (y3= k ∗α, y4 = m |
- -| k∗β).
The decryption proceedsa negative addition processas
FIGURE 5.Comparison of Key sizes and Security levels between ECC
and RSA.
TABLE 1.Comparison of key size, in bits, for RSA and ECC.
y4 − (a∗y3) = (m |
- -| k∗β)-a∗(k∗α) = m |
- -| a∗k∗α − a∗k∗
α = m. The sniffers can intercept the message, but ECDL
makes it infeasible to get k or m [23].
Though RSA and other cryptosystems have been trem
dously used in security applications,the currenttrend of
massive growth of IoT applications could necessitate loo
at alternative cryptographic solutions that satisfy the na
of these smart devices. RSA assumes that the longer the
the better itresists againstattacks.However,this principle
does nothold forsmalldevices which are constrained in
processor, memory, and bandwidth. With the prevalence
incrementin the numberof smartobjects,Elliptic Curve
Cryptography (ECC) will play a significant role in cryptog
phy as RSA is likely to be unusable with resource-constr
devices.ECC is advantageous in thatit provides the same
security level with RSA with smaller key sizes but it prov
more efficient implementation than RSA [23]. For instan
the security key of 256-bit ECC is assumed to be equiva
3072-bit RSA. Table 1 shows that the efficiency of ECC a
increment ratios show that RSA key size should be incre
more than double when thatof ECC is doubled.In larger
key sizes, ECC scheme provides substantial benefits in t
of providing faster encryption/decryption,smaller storage,
26824 VOLUME 6, 2018
FIGURE 4.Comparison of security levels of ECC and RSA [19].
to yield R (x3,y3) are calculated as x3 = m2 − x1 − x2
mod p,y3 = −y1 + s(x1 − x3)mod p,and the slope
m = (y1 − y2)/(x1 − x2) mod p [20]–[22].
B. EL GAMAL BASED ECC
In the group G consisting of x and y,it is required that the
classical Discrete Logarithm Problem (DLP) solves k from
the xk = y. The ECC approach having points P and Q on
its curve in group G requires solving k from P o k = Q.
The security assumption of ECC is related to Elliptic Curve
Discrete Logarithm Problem (ECDLP),where solving the
discrete logarithm of a random EC pointwith respectto a
publicly known generator is computationally infeasible. ECC
can be used for ElGamalbased encryption,ECC Diffie-
Hellman based secure key exchange, and authentication and
digital signatures.
The original concept of Elgamal lies in embedding a mes-
sage m in αk and βk where α is a root of a large prime p, ka
random number, and β = αa. The parameters (α, β, p) are
public while the sender possesses k and the receiver owns an
as a secret key. The message owner sends the pair (αk, βkm)
to the receiver, which decrypts as (αk)−a∗(βkm) = (αa)−k ∗
(βkm) = (β−k )∗(βkm) = m. It is difficult for the adversary
to solve DLP to get the message or the secret number.
The ECC based Elgamal encryption is the modification of
basic Elgamal in which α and β are points on the elliptic curve
with multiplications replaced by addition, and multiplication
used instead of exponents.An elliptic curve C,a pointon
curve α (x1, y1), secret integer a of the receiver and random
number k of the sender are selected.The pointβ (x2,y2)
is calculated as β = a∗α. The sender calculates two other
points as c(x3, y3) and d(x4, y4) where c(x3, y3) = (x3, k∗α)
and d(x4, y4) = (x4, m|
- -| k ∗β), and sends to the receiver
as (c,d). As the message is carried by the y-coordinates,
it also suffices to send as (y3= k ∗α, y4 = m |
- -| k∗β).
The decryption proceedsa negative addition processas
FIGURE 5.Comparison of Key sizes and Security levels between ECC
and RSA.
TABLE 1.Comparison of key size, in bits, for RSA and ECC.
y4 − (a∗y3) = (m |
- -| k∗β)-a∗(k∗α) = m |
- -| a∗k∗α − a∗k∗
α = m. The sniffers can intercept the message, but ECDL
makes it infeasible to get k or m [23].
Though RSA and other cryptosystems have been trem
dously used in security applications,the currenttrend of
massive growth of IoT applications could necessitate loo
at alternative cryptographic solutions that satisfy the na
of these smart devices. RSA assumes that the longer the
the better itresists againstattacks.However,this principle
does nothold forsmalldevices which are constrained in
processor, memory, and bandwidth. With the prevalence
incrementin the numberof smartobjects,Elliptic Curve
Cryptography (ECC) will play a significant role in cryptog
phy as RSA is likely to be unusable with resource-constr
devices.ECC is advantageous in thatit provides the same
security level with RSA with smaller key sizes but it prov
more efficient implementation than RSA [23]. For instan
the security key of 256-bit ECC is assumed to be equiva
3072-bit RSA. Table 1 shows that the efficiency of ECC a
increment ratios show that RSA key size should be incre
more than double when thatof ECC is doubled.In larger
key sizes, ECC scheme provides substantial benefits in t
of providing faster encryption/decryption,smaller storage,
26824 VOLUME 6, 2018

A. A. Diro et al.:Analysis of Lightweight Encryption Scheme for Fog-to-Things Communication
faster computations and fewer power utilization. Embedded
algorithms such as ECC can be adopted for cybersecurity
schemes of fog-to-things computing as it lightweight in stor-
age and computations.
C. ECC BASED PROXY RE-ENCRYPTION
The implementation of ECC reduces processing and stor-
age requirements of IoT as the key and encrypted message
sizes are much less than cryptographic suites such as RSA.
In addition to these novel features employed by ECC,it is
also possible to further enhance the processing and storage
efficiency of IoT devices by offloading functions of heavy
cryptographic elements to fog nodes in the vicinity.As fog
nodes act as proxy node between IoT and the cloud or another
IoT in fog computing,ECC based proxy re-encryption
technique[27], [30] could be adaptedfor resource-
constrained Fog-to-things communication using Fog node
as a broker.It is an encryption scheme by which a bro-
ker node such as Fog node is provided with intermediate
key rk1,2 thatenablesit to convertoriginalmessage m
encrypted with public key pk1 of a client into an encryption of
the same message m under a different public key pk2 without
revealing the message contents to the fog node and private
keys to either of the parties.Proxy re-encryption protocols
have some properties useful for IoTs, namely:
• Unidirectional: the re-encryption from A to B does not
necessarily imply the reverse.
• Proxy Transparency : the existence of proxy should be
hidden from clients
• Key optimal:the clientkeys should be keptconstant
regardless of communicating parties
• Collusion resistance: the proxy shouldn’t be colluded
with any of the clients to retrieve the message or keys of
another client
• Non-transitivity:if A delegates proxy to re-encrypt
for B, the proxy cannotdelegate another proxy to re-
encrypt for C.
Proxy re-encryption is a new encryption scheme devised for
security in a distributed environment such as smart applica-
tions supported by the Internet of things. The technique solves
the problem of key management and storage limitations of
resource-constrained ends such as IoT devices.Instead of
using El-Gamal based discrete logarithm problem,we used
El Gamal based ECC because of its efficiency in computa-
tions. ECC addition of points on an elliptic curve and multi-
plication of a point on an elliptic curve by an integer shares
equivalency to the modulus multiplication and exponentiation
in RSA, respectively.
IV. RELATED WORKS
The research on cybersecurity schemes of IoT/Fog computing
is in its infancy.Most of the research work on IoT/Fog
computing is focusing on architecturalissues and applica-
tion domains,while security schemes have been leftto be
patched in the years to come. In this section, we thoroughly
review and analyze literature and related works in cyber
rity schemes. We review proxy re-encryption related stu
for related applications as similar security schemes,to our
knowledge, don’t exist for fog-to-things applications.
The theoreticaland practical aspects of proxy
re-encryption have been explored in [24] for distributed
systems.The authors have shown the possibility of using
proxy nodes for encryption withoutdisclosing user’s data.
Yuriy et al. [25] have proposedIND-CPA-secure
unidirectionalProxy Re-Encryption(PRE) schemefor
publish-subscribe applications.The study has demonstrated
the efficiency ofproxy re-encryption forlimited resource
embedded systems such as IoT devices.The study in [26]
proposed the anonymouskey proxy re-encryption which
is CPA-secure using the assumption of Decisional Bilinea
Diffie Hellman (DBDH).However,the implementation of
the scheme is inefficient for resource limited devices. Id
based proxy re-encryption has been explored in [27] to
form plaintexts encrypted under one identity to another
work has demonstrated the possibility of adapting ident
based encryption to proxy re-encryption.Wang [30]pro-
posed id-based proxy re-encryption to protectkey leakage
from side-channel attacks using fog computing.They have
shown that the scheme could be implemented without u
PKI certificates. The article [31] summarizes the use of p
re-encryption for securely sharing data in fog environme
However,the paper lacks detailed experimental evaluatio
and results.
Our scheme differs from the above works in that we ha
applied ECC based proxy re-encryption scheme in distrib
fog-to-things environment.
V. THE PROPOSED CYBERSECURITY SYSTEM
Though layered cybersecurity mechanisms are required
secure fog-to-things computing, this research concentra
the encryption mechanism using proxy re-encryption sc
A. ALGORITHMS
Our scheme consists of 5 procedures: Key Generation, c
encryption procedure, Fog encryption procedure, Fog de
tion procedure and clientdecryption procedure.Since Fog
computing is distributed, one specific fog node can be c
as a trusted authority or coordinator for key and parame
generations. The key generation procedure (procedure 1
duces public curve parameters, public and secret keys o
coordinator fog node.The public elliptic curve parameters
PK are sent to the IoT nodes and other fog nodes. The tr
authority securely also sends kCi1 to the IoT device as a
private key and (Ci, kCi2) to the slave fog nodes, where Ci is
the identity ofclientIoT devices.In addition,the trusted
key authority has a responsibility of securely storing sec
key SK.
Clientencryption step shows the encryption ofa mes-
sage m by IoT end using its private key kIDi1 as shown in
procedure 2.The corresponding fog node re-encrypts the
client’sciphertextusing theportion ofthe key on the
VOLUME 6, 2018 26825
faster computations and fewer power utilization. Embedded
algorithms such as ECC can be adopted for cybersecurity
schemes of fog-to-things computing as it lightweight in stor-
age and computations.
C. ECC BASED PROXY RE-ENCRYPTION
The implementation of ECC reduces processing and stor-
age requirements of IoT as the key and encrypted message
sizes are much less than cryptographic suites such as RSA.
In addition to these novel features employed by ECC,it is
also possible to further enhance the processing and storage
efficiency of IoT devices by offloading functions of heavy
cryptographic elements to fog nodes in the vicinity.As fog
nodes act as proxy node between IoT and the cloud or another
IoT in fog computing,ECC based proxy re-encryption
technique[27], [30] could be adaptedfor resource-
constrained Fog-to-things communication using Fog node
as a broker.It is an encryption scheme by which a bro-
ker node such as Fog node is provided with intermediate
key rk1,2 thatenablesit to convertoriginalmessage m
encrypted with public key pk1 of a client into an encryption of
the same message m under a different public key pk2 without
revealing the message contents to the fog node and private
keys to either of the parties.Proxy re-encryption protocols
have some properties useful for IoTs, namely:
• Unidirectional: the re-encryption from A to B does not
necessarily imply the reverse.
• Proxy Transparency : the existence of proxy should be
hidden from clients
• Key optimal:the clientkeys should be keptconstant
regardless of communicating parties
• Collusion resistance: the proxy shouldn’t be colluded
with any of the clients to retrieve the message or keys of
another client
• Non-transitivity:if A delegates proxy to re-encrypt
for B, the proxy cannotdelegate another proxy to re-
encrypt for C.
Proxy re-encryption is a new encryption scheme devised for
security in a distributed environment such as smart applica-
tions supported by the Internet of things. The technique solves
the problem of key management and storage limitations of
resource-constrained ends such as IoT devices.Instead of
using El-Gamal based discrete logarithm problem,we used
El Gamal based ECC because of its efficiency in computa-
tions. ECC addition of points on an elliptic curve and multi-
plication of a point on an elliptic curve by an integer shares
equivalency to the modulus multiplication and exponentiation
in RSA, respectively.
IV. RELATED WORKS
The research on cybersecurity schemes of IoT/Fog computing
is in its infancy.Most of the research work on IoT/Fog
computing is focusing on architecturalissues and applica-
tion domains,while security schemes have been leftto be
patched in the years to come. In this section, we thoroughly
review and analyze literature and related works in cyber
rity schemes. We review proxy re-encryption related stu
for related applications as similar security schemes,to our
knowledge, don’t exist for fog-to-things applications.
The theoreticaland practical aspects of proxy
re-encryption have been explored in [24] for distributed
systems.The authors have shown the possibility of using
proxy nodes for encryption withoutdisclosing user’s data.
Yuriy et al. [25] have proposedIND-CPA-secure
unidirectionalProxy Re-Encryption(PRE) schemefor
publish-subscribe applications.The study has demonstrated
the efficiency ofproxy re-encryption forlimited resource
embedded systems such as IoT devices.The study in [26]
proposed the anonymouskey proxy re-encryption which
is CPA-secure using the assumption of Decisional Bilinea
Diffie Hellman (DBDH).However,the implementation of
the scheme is inefficient for resource limited devices. Id
based proxy re-encryption has been explored in [27] to
form plaintexts encrypted under one identity to another
work has demonstrated the possibility of adapting ident
based encryption to proxy re-encryption.Wang [30]pro-
posed id-based proxy re-encryption to protectkey leakage
from side-channel attacks using fog computing.They have
shown that the scheme could be implemented without u
PKI certificates. The article [31] summarizes the use of p
re-encryption for securely sharing data in fog environme
However,the paper lacks detailed experimental evaluatio
and results.
Our scheme differs from the above works in that we ha
applied ECC based proxy re-encryption scheme in distrib
fog-to-things environment.
V. THE PROPOSED CYBERSECURITY SYSTEM
Though layered cybersecurity mechanisms are required
secure fog-to-things computing, this research concentra
the encryption mechanism using proxy re-encryption sc
A. ALGORITHMS
Our scheme consists of 5 procedures: Key Generation, c
encryption procedure, Fog encryption procedure, Fog de
tion procedure and clientdecryption procedure.Since Fog
computing is distributed, one specific fog node can be c
as a trusted authority or coordinator for key and parame
generations. The key generation procedure (procedure 1
duces public curve parameters, public and secret keys o
coordinator fog node.The public elliptic curve parameters
PK are sent to the IoT nodes and other fog nodes. The tr
authority securely also sends kCi1 to the IoT device as a
private key and (Ci, kCi2) to the slave fog nodes, where Ci is
the identity ofclientIoT devices.In addition,the trusted
key authority has a responsibility of securely storing sec
key SK.
Clientencryption step shows the encryption ofa mes-
sage m by IoT end using its private key kIDi1 as shown in
procedure 2.The corresponding fog node re-encrypts the
client’sciphertextusing theportion ofthe key on the
VOLUME 6, 2018 26825

A. A. Diro et al.:Analysis of Lightweight Encryption Scheme for Fog-to-Things Communication
node kCi2 (procedure 3).Then,the fog node converts the
message encrypted by the client to intermediate (intermediate
decryption) form so thatthe cipher can be decrypted only
by clientCi as shown in procedure 4.Finally,clientCi
decrypts the message using its private key kCi1 as shown in
procedure 5.
Procedure 1 Key Generation
Input: security parameter 1n
Output: public elliptic curve parameters PK and a secret key
of master fog node SK.
1. Two prime numbers p and q are generated in such
a way that q = (p−1)/2 and |q| = n.
2. A base point P is generated such that cyclic group
G is the unique order q of subgroup of Z
∗
q
3. Choose k uniformly at random from Z
∗
q and com-
pute h = kP
4. Store public curve parameters PK = (G, P, q, h)
and SK = k
5. Choose a random kCi1 from Zp and compute
kCi2 = k⊕kCi1
6. return kCi1 and (Ci, kCi2)
Procedure 2 Client Encryption
Input: Message m, the public elliptic curve parameters PK,
and the client private key kCi1
Output: ciphertext using encryption EIDi(n)
1. Choose r randomly from Zq
2. ECi (m) ← (rP, m⊕rki1P)
3. return ECi (m)
Procedure 3 Fog Re-Encryption
Input: ciphertext ECi (m), the public elliptic curve parame-
ters PK, and the fog node key (Ci, kCi2) for user Ci
Output: The ciphertext E(m)
1. Compute (rP)kCi2⊕ (m⊕rkCi1P) =
rP(kCi1⊕kCi2)⊕m = rPk⊕m
2. E(m)=(rP, rPk⊕m)
3. return E(m)
B. SECURITY ANALYSIS
The fog nodes are assumed to be semi-trusted entities in the
process of re-encryption while the coordinator node or the
trusted authority is trusted in the system by all entities. The
communication between things and the fog nodes require
several security requirements such as correctness, confiden-
tiality and key scalability. The encrypted message sent from
one device to the other should be correctly decrypted.The
messages sent by each IoT device should not be disclosed to
the fog nodes and unintended IoT devices. The scheme should
also eliminate the need to share security keys by decoupling
Procedure 4 Fog Decryption
Input: Encrypted message E(m) = (rP, rkP⊕m) and the
key set (Ci, kCi2) corresponding to client Ci.
Output:The intermediate cipherdi(m) thatonly can be
decrypted by client Ci.
5. Compute (m⊕rkP)⊕ (rP)(kCj2) = rP(k⊕kCj2)
⊕m = rP kCj1⊕m
6. di(m)=(rP, rP kCj1⊕m)
7. return di(m)
Procedure 5 Client Decryption
Input:intermediate cipher from Fog node di(m) = (rP,rP
kCj1⊕m) and the client private key kCj1.
Output: message m
1. m = (rP kCj1⊕m) ⊕ (rP)(kCj1)
2. return m
the sender and the receiver since it is not scalable in ma
connected IoT environment. IoT devices lack the capabil
processing, storing, and communicating security keys w
other clients. In this study, we mainly focus on confident
requirement.
A cryptographic construction is correct if the decryptio
function always produces expected results with proper k
Our scheme has to deal with the correctness of encrypti
decryption. Assuming that ci←Re_Enc(. . . , Enc(m, . . .)) is
a ciphertext,∀m∈M,IDi, IDj ∈ {0, 1}
∗
, where kCi1, kCi2
are generated by initialization and key generation pro-
cedure,the following holds for correctnessof our
scheme:
• Decrypt(kCi1) = m
• Decrypt (kCj2, Re_Enc(kCi2)) = m
This indicates that our construction has security correctn
as it has been proved by implementation.
A system is said to be secure if the probability of brea
by adversaries is negligible. The adversary is assumed t
computationally bound random algorithm, and runs in p
abilistic polynomial time (PPT) to show that the probabil
of breach is negligible. A function f is said to be negligib
function if for each polynomial p() there K such that for a
integers k > K it holds that f (k)< 1
f (k ). The existence of
negligible function is required by a pseudorandom funct
whose output is indistinguishable from real random func
by the adversary.A function f :{0, 1}
∗
× {0, 1}
∗
→ {0, 1}
∗
is pseudorandom iffor all probabilistic polynomialtime
(PPT) adversaries A,there exists a negligible function neg
such thatP Afk(.) = 1 − P AF (.) = 1 < neg(n) where
k → {0, 1}n and F are chosen atuniform random from
their corresponding set. The proof lies on the assumptio
Diffie-Hellman (DH) algorithm is secure against adversar
the group G, and it is difficult for the adversary to obtain
group components such as kP. The DH algorithm with re
to group G of acyclic order q (|q| = k is secure against a
26826 VOLUME 6, 2018
node kCi2 (procedure 3).Then,the fog node converts the
message encrypted by the client to intermediate (intermediate
decryption) form so thatthe cipher can be decrypted only
by clientCi as shown in procedure 4.Finally,clientCi
decrypts the message using its private key kCi1 as shown in
procedure 5.
Procedure 1 Key Generation
Input: security parameter 1n
Output: public elliptic curve parameters PK and a secret key
of master fog node SK.
1. Two prime numbers p and q are generated in such
a way that q = (p−1)/2 and |q| = n.
2. A base point P is generated such that cyclic group
G is the unique order q of subgroup of Z
∗
q
3. Choose k uniformly at random from Z
∗
q and com-
pute h = kP
4. Store public curve parameters PK = (G, P, q, h)
and SK = k
5. Choose a random kCi1 from Zp and compute
kCi2 = k⊕kCi1
6. return kCi1 and (Ci, kCi2)
Procedure 2 Client Encryption
Input: Message m, the public elliptic curve parameters PK,
and the client private key kCi1
Output: ciphertext using encryption EIDi(n)
1. Choose r randomly from Zq
2. ECi (m) ← (rP, m⊕rki1P)
3. return ECi (m)
Procedure 3 Fog Re-Encryption
Input: ciphertext ECi (m), the public elliptic curve parame-
ters PK, and the fog node key (Ci, kCi2) for user Ci
Output: The ciphertext E(m)
1. Compute (rP)kCi2⊕ (m⊕rkCi1P) =
rP(kCi1⊕kCi2)⊕m = rPk⊕m
2. E(m)=(rP, rPk⊕m)
3. return E(m)
B. SECURITY ANALYSIS
The fog nodes are assumed to be semi-trusted entities in the
process of re-encryption while the coordinator node or the
trusted authority is trusted in the system by all entities. The
communication between things and the fog nodes require
several security requirements such as correctness, confiden-
tiality and key scalability. The encrypted message sent from
one device to the other should be correctly decrypted.The
messages sent by each IoT device should not be disclosed to
the fog nodes and unintended IoT devices. The scheme should
also eliminate the need to share security keys by decoupling
Procedure 4 Fog Decryption
Input: Encrypted message E(m) = (rP, rkP⊕m) and the
key set (Ci, kCi2) corresponding to client Ci.
Output:The intermediate cipherdi(m) thatonly can be
decrypted by client Ci.
5. Compute (m⊕rkP)⊕ (rP)(kCj2) = rP(k⊕kCj2)
⊕m = rP kCj1⊕m
6. di(m)=(rP, rP kCj1⊕m)
7. return di(m)
Procedure 5 Client Decryption
Input:intermediate cipher from Fog node di(m) = (rP,rP
kCj1⊕m) and the client private key kCj1.
Output: message m
1. m = (rP kCj1⊕m) ⊕ (rP)(kCj1)
2. return m
the sender and the receiver since it is not scalable in ma
connected IoT environment. IoT devices lack the capabil
processing, storing, and communicating security keys w
other clients. In this study, we mainly focus on confident
requirement.
A cryptographic construction is correct if the decryptio
function always produces expected results with proper k
Our scheme has to deal with the correctness of encrypti
decryption. Assuming that ci←Re_Enc(. . . , Enc(m, . . .)) is
a ciphertext,∀m∈M,IDi, IDj ∈ {0, 1}
∗
, where kCi1, kCi2
are generated by initialization and key generation pro-
cedure,the following holds for correctnessof our
scheme:
• Decrypt(kCi1) = m
• Decrypt (kCj2, Re_Enc(kCi2)) = m
This indicates that our construction has security correctn
as it has been proved by implementation.
A system is said to be secure if the probability of brea
by adversaries is negligible. The adversary is assumed t
computationally bound random algorithm, and runs in p
abilistic polynomial time (PPT) to show that the probabil
of breach is negligible. A function f is said to be negligib
function if for each polynomial p() there K such that for a
integers k > K it holds that f (k)< 1
f (k ). The existence of
negligible function is required by a pseudorandom funct
whose output is indistinguishable from real random func
by the adversary.A function f :{0, 1}
∗
× {0, 1}
∗
→ {0, 1}
∗
is pseudorandom iffor all probabilistic polynomialtime
(PPT) adversaries A,there exists a negligible function neg
such thatP Afk(.) = 1 − P AF (.) = 1 < neg(n) where
k → {0, 1}n and F are chosen atuniform random from
their corresponding set. The proof lies on the assumptio
Diffie-Hellman (DH) algorithm is secure against adversar
the group G, and it is difficult for the adversary to obtain
group components such as kP. The DH algorithm with re
to group G of acyclic order q (|q| = k is secure against a
26826 VOLUME 6, 2018
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
A. A. Diro et al.:Analysis of Lightweight Encryption Scheme for Fog-to-Things Communication
adversary A if there exists negligible function neg such that
|P [A(G, q, P, kP) = 1] − P[A(G, q, P, aP) = 1]| < neg(k)
for randomly chosen k, a ∈ Zq.
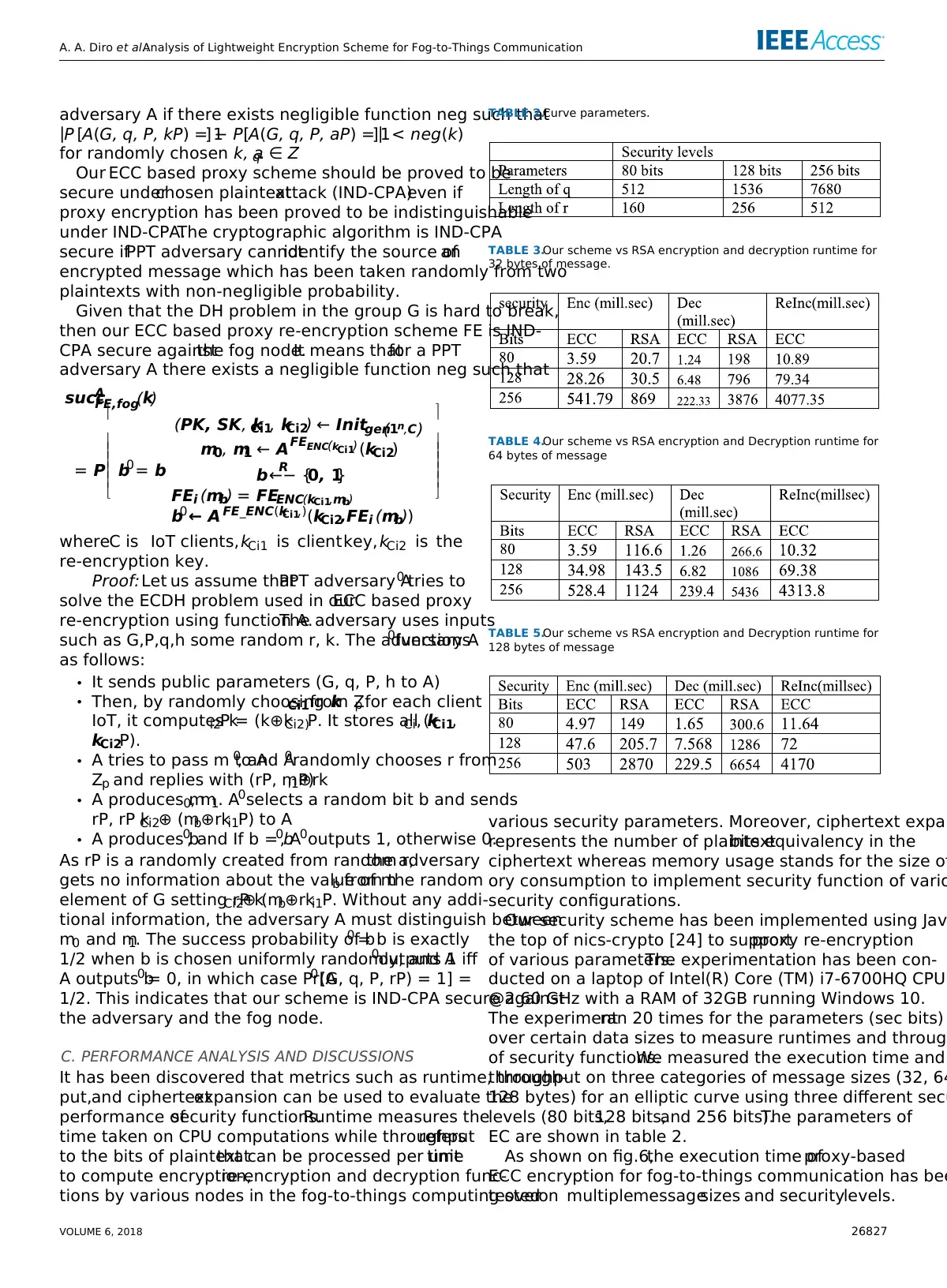
Our ECC based proxy scheme should be proved to be
secure underchosen plaintextattack (IND-CPA)even if
proxy encryption has been proved to be indistinguishable
under IND-CPA.The cryptographic algorithm is IND-CPA
secure ifPPT adversary cannotidentify the source ofan
encrypted message which has been taken randomly from two
plaintexts with non-negligible probability.
Given that the DH problem in the group G is hard to break,
then our ECC based proxy re-encryption scheme FE is IND-
CPA secure againstthe fog node.It means thatfor a PPT
adversary A there exists a negligible function neg such that
succA
FE,fog(k)
= P
b0= b
(PK, SK, kCi1, kCi2) ← Initgen(1n,C)
m0, m1 ← AFEENC(kCi1) (kCi2)
b R
←− {0, 1}
FEi (mb) = FEENC(kCi1,mb)
b0← A FE_ENC(kCi1,)(kCi2,FEi (mb))
whereC is IoT clients,kCi1 is clientkey, kCi2 is the
re-encryption key.
Proof:Let us assume thatPPT adversary A0 tries to
solve the ECDH problem used in ourECC based proxy
re-encryption using function A.The adversary uses inputs
such as G,P,q,h some random r, k. The adversary A0functions
as follows:
• It sends public parameters (G, q, P, h to A)
• Then, by randomly choosing kCi1from Zp for each client
IoT, it computes ki2P = (k⊕kCi2)P. It stores all (Ci, kCi1,
kCi2P).
• A tries to pass m to A0, and A0randomly chooses r from
Zp and replies with (rP, m⊕rki1P)
• A produces m0, m1. A0selects a random bit b and sends
rP, rP kCi2⊕ (mb⊕rki1P) to A
• A produces b0, and If b = b0, A0outputs 1, otherwise 0.
As rP is a randomly created from random r,the adversary
gets no information about the value of mb from the random
element of G setting rP kCi2⊕ (mb⊕rki1P. Without any addi-
tional information, the adversary A must distinguish between
m0 and m1. The success probability of b0 = b is exactly
1/2 when b is chosen uniformly randomly, and A0outputs 1 iff
A outputs b0 = 0, in which case Pr[A0(G, q, P, rP) = 1] =
1/2. This indicates that our scheme is IND-CPA secure against
the adversary and the fog node.
C. PERFORMANCE ANALYSIS AND DISCUSSIONS
It has been discovered that metrics such as runtime, through-
put,and ciphertextexpansion can be used to evaluate the
performance ofsecurity functions.Runtime measures the
time taken on CPU computations while throughputrefers
to the bits of plaintextthatcan be processed per unittime
to compute encryption,re-encryption and decryption func-
tions by various nodes in the fog-to-things computing over
TABLE 2.Curve parameters.
TABLE 3.Our scheme vs RSA encryption and decryption runtime for
32 bytes of message.
TABLE 4.Our scheme vs RSA encryption and Decryption runtime for
64 bytes of message
TABLE 5.Our scheme vs RSA encryption and Decryption runtime for
128 bytes of message
various security parameters. Moreover, ciphertext expan
represents the number of plaintextbits equivalency in the
ciphertext whereas memory usage stands for the size of
ory consumption to implement security function of vario
security configurations.
Our security scheme has been implemented using Jav
the top of nics-crypto [24] to supportproxy re-encryption
of various parameters.The experimentation has been con-
ducted on a laptop of Intel(R) Core (TM) i7-6700HQ CPU
@2.60 GHz with a RAM of 32GB running Windows 10.
The experimentran 20 times for the parameters (sec bits)
over certain data sizes to measure runtimes and through
of security functions.We measured the execution time and
throughput on three categories of message sizes (32, 64
128 bytes) for an elliptic curve using three different secu
levels (80 bits,128 bits,and 256 bits).The parameters of
EC are shown in table 2.
As shown on fig.6,the execution time ofproxy-based
ECC encryption for fog-to-things communication has bee
testedon multiplemessagesizes and securitylevels.
VOLUME 6, 2018 26827
adversary A if there exists negligible function neg such that
|P [A(G, q, P, kP) = 1] − P[A(G, q, P, aP) = 1]| < neg(k)
for randomly chosen k, a ∈ Zq.
Our ECC based proxy scheme should be proved to be
secure underchosen plaintextattack (IND-CPA)even if
proxy encryption has been proved to be indistinguishable
under IND-CPA.The cryptographic algorithm is IND-CPA
secure ifPPT adversary cannotidentify the source ofan
encrypted message which has been taken randomly from two
plaintexts with non-negligible probability.
Given that the DH problem in the group G is hard to break,
then our ECC based proxy re-encryption scheme FE is IND-
CPA secure againstthe fog node.It means thatfor a PPT
adversary A there exists a negligible function neg such that
succA
FE,fog(k)
= P
b0= b
(PK, SK, kCi1, kCi2) ← Initgen(1n,C)
m0, m1 ← AFEENC(kCi1) (kCi2)
b R
←− {0, 1}
FEi (mb) = FEENC(kCi1,mb)
b0← A FE_ENC(kCi1,)(kCi2,FEi (mb))
whereC is IoT clients,kCi1 is clientkey, kCi2 is the
re-encryption key.
Proof:Let us assume thatPPT adversary A0 tries to
solve the ECDH problem used in ourECC based proxy
re-encryption using function A.The adversary uses inputs
such as G,P,q,h some random r, k. The adversary A0functions
as follows:
• It sends public parameters (G, q, P, h to A)
• Then, by randomly choosing kCi1from Zp for each client
IoT, it computes ki2P = (k⊕kCi2)P. It stores all (Ci, kCi1,
kCi2P).
• A tries to pass m to A0, and A0randomly chooses r from
Zp and replies with (rP, m⊕rki1P)
• A produces m0, m1. A0selects a random bit b and sends
rP, rP kCi2⊕ (mb⊕rki1P) to A
• A produces b0, and If b = b0, A0outputs 1, otherwise 0.
As rP is a randomly created from random r,the adversary
gets no information about the value of mb from the random
element of G setting rP kCi2⊕ (mb⊕rki1P. Without any addi-
tional information, the adversary A must distinguish between
m0 and m1. The success probability of b0 = b is exactly
1/2 when b is chosen uniformly randomly, and A0outputs 1 iff
A outputs b0 = 0, in which case Pr[A0(G, q, P, rP) = 1] =
1/2. This indicates that our scheme is IND-CPA secure against
the adversary and the fog node.
C. PERFORMANCE ANALYSIS AND DISCUSSIONS
It has been discovered that metrics such as runtime, through-
put,and ciphertextexpansion can be used to evaluate the
performance ofsecurity functions.Runtime measures the
time taken on CPU computations while throughputrefers
to the bits of plaintextthatcan be processed per unittime
to compute encryption,re-encryption and decryption func-
tions by various nodes in the fog-to-things computing over
TABLE 2.Curve parameters.
TABLE 3.Our scheme vs RSA encryption and decryption runtime for
32 bytes of message.
TABLE 4.Our scheme vs RSA encryption and Decryption runtime for
64 bytes of message
TABLE 5.Our scheme vs RSA encryption and Decryption runtime for
128 bytes of message
various security parameters. Moreover, ciphertext expan
represents the number of plaintextbits equivalency in the
ciphertext whereas memory usage stands for the size of
ory consumption to implement security function of vario
security configurations.
Our security scheme has been implemented using Jav
the top of nics-crypto [24] to supportproxy re-encryption
of various parameters.The experimentation has been con-
ducted on a laptop of Intel(R) Core (TM) i7-6700HQ CPU
@2.60 GHz with a RAM of 32GB running Windows 10.
The experimentran 20 times for the parameters (sec bits)
over certain data sizes to measure runtimes and through
of security functions.We measured the execution time and
throughput on three categories of message sizes (32, 64
128 bytes) for an elliptic curve using three different secu
levels (80 bits,128 bits,and 256 bits).The parameters of
EC are shown in table 2.
As shown on fig.6,the execution time ofproxy-based
ECC encryption for fog-to-things communication has bee
testedon multiplemessagesizes and securitylevels.
VOLUME 6, 2018 26827
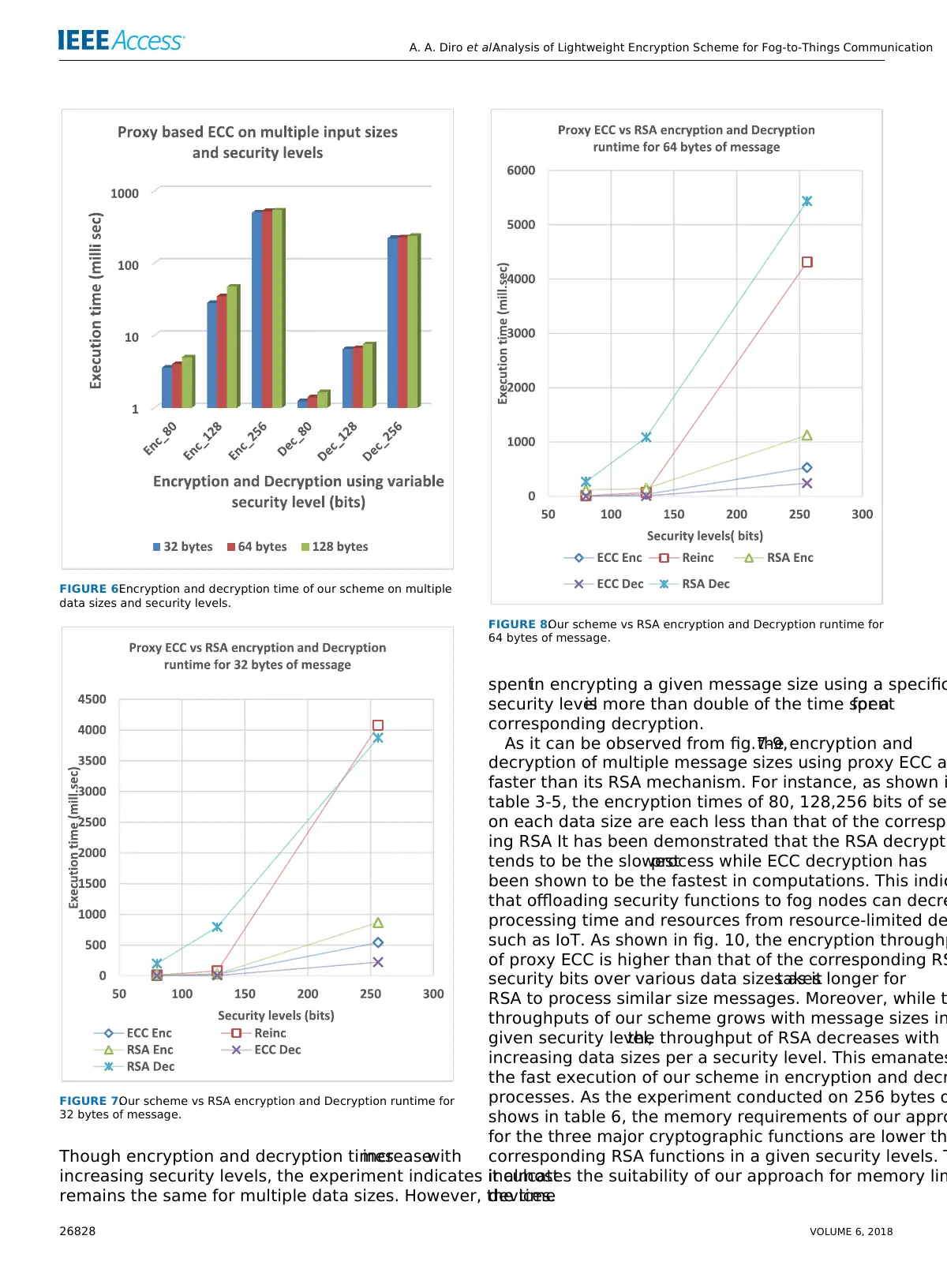
A. A. Diro et al.:Analysis of Lightweight Encryption Scheme for Fog-to-Things Communication
FIGURE 6.Encryption and decryption time of our scheme on multiple
data sizes and security levels.
FIGURE 7.Our scheme vs RSA encryption and Decryption runtime for
32 bytes of message.
Though encryption and decryption timesincreasewith
increasing security levels, the experiment indicates it almost
remains the same for multiple data sizes. However, the time
FIGURE 8.Our scheme vs RSA encryption and Decryption runtime for
64 bytes of message.
spentin encrypting a given message size using a specific
security levelis more than double of the time spentfor a
corresponding decryption.
As it can be observed from fig.7-9,the encryption and
decryption of multiple message sizes using proxy ECC a
faster than its RSA mechanism. For instance, as shown i
table 3-5, the encryption times of 80, 128,256 bits of sec
on each data size are each less than that of the correspo
ing RSA It has been demonstrated that the RSA decrypti
tends to be the slowestprocess while ECC decryption has
been shown to be the fastest in computations. This indic
that offloading security functions to fog nodes can decre
processing time and resources from resource-limited de
such as IoT. As shown in fig. 10, the encryption throughp
of proxy ECC is higher than that of the corresponding RS
security bits over various data sizes as ittakes longer for
RSA to process similar size messages. Moreover, while t
throughputs of our scheme grows with message sizes in
given security level,the throughput of RSA decreases with
increasing data sizes per a security level. This emanates
the fast execution of our scheme in encryption and decr
processes. As the experiment conducted on 256 bytes o
shows in table 6, the memory requirements of our appro
for the three major cryptographic functions are lower th
corresponding RSA functions in a given security levels. T
inculcates the suitability of our approach for memory lim
devices.
26828 VOLUME 6, 2018
FIGURE 6.Encryption and decryption time of our scheme on multiple
data sizes and security levels.
FIGURE 7.Our scheme vs RSA encryption and Decryption runtime for
32 bytes of message.
Though encryption and decryption timesincreasewith
increasing security levels, the experiment indicates it almost
remains the same for multiple data sizes. However, the time
FIGURE 8.Our scheme vs RSA encryption and Decryption runtime for
64 bytes of message.
spentin encrypting a given message size using a specific
security levelis more than double of the time spentfor a
corresponding decryption.
As it can be observed from fig.7-9,the encryption and
decryption of multiple message sizes using proxy ECC a
faster than its RSA mechanism. For instance, as shown i
table 3-5, the encryption times of 80, 128,256 bits of sec
on each data size are each less than that of the correspo
ing RSA It has been demonstrated that the RSA decrypti
tends to be the slowestprocess while ECC decryption has
been shown to be the fastest in computations. This indic
that offloading security functions to fog nodes can decre
processing time and resources from resource-limited de
such as IoT. As shown in fig. 10, the encryption throughp
of proxy ECC is higher than that of the corresponding RS
security bits over various data sizes as ittakes longer for
RSA to process similar size messages. Moreover, while t
throughputs of our scheme grows with message sizes in
given security level,the throughput of RSA decreases with
increasing data sizes per a security level. This emanates
the fast execution of our scheme in encryption and decr
processes. As the experiment conducted on 256 bytes o
shows in table 6, the memory requirements of our appro
for the three major cryptographic functions are lower th
corresponding RSA functions in a given security levels. T
inculcates the suitability of our approach for memory lim
devices.
26828 VOLUME 6, 2018
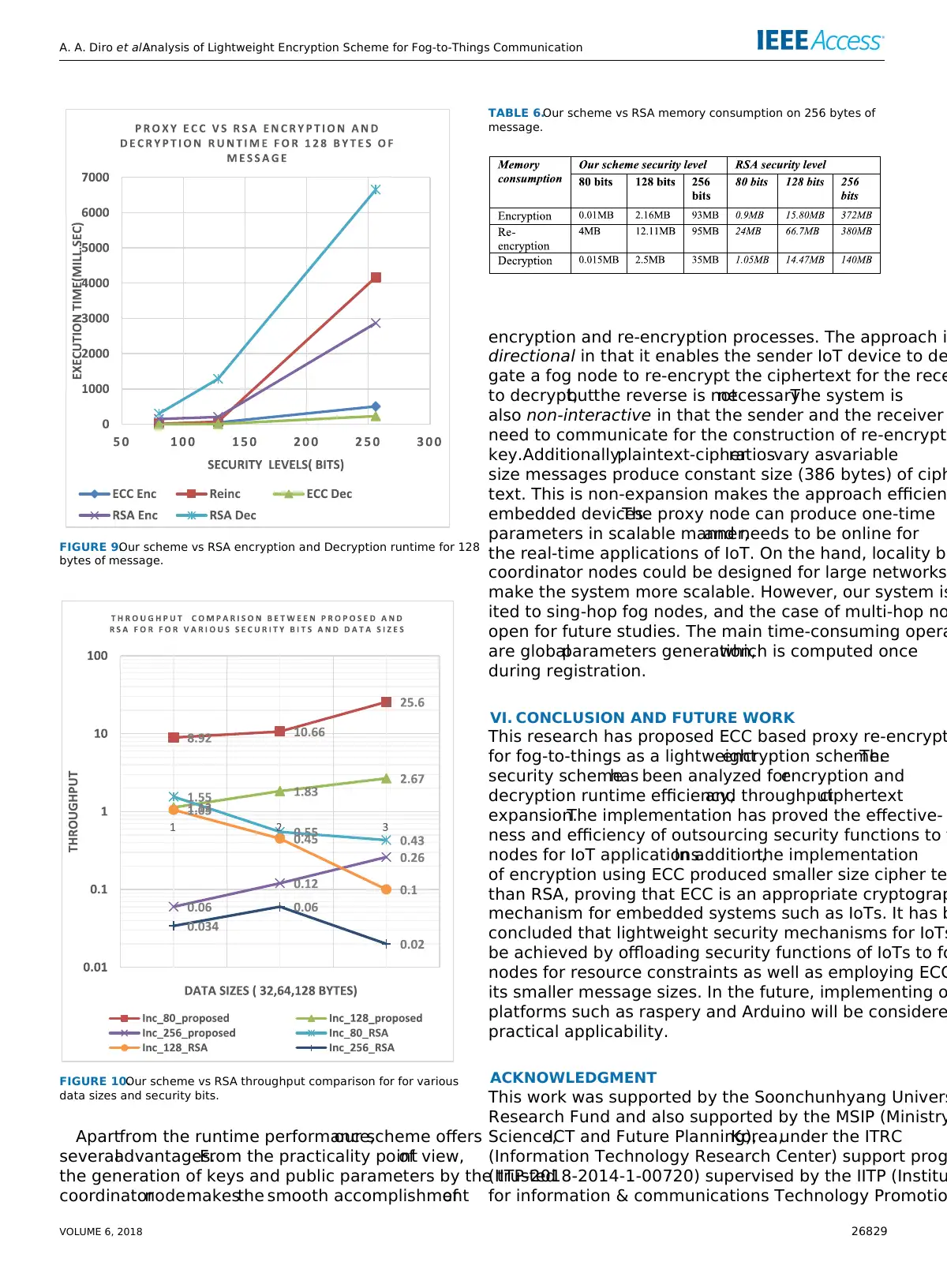
A. A. Diro et al.:Analysis of Lightweight Encryption Scheme for Fog-to-Things Communication
FIGURE 9.Our scheme vs RSA encryption and Decryption runtime for 128
bytes of message.
FIGURE 10.Our scheme vs RSA throughput comparison for for various
data sizes and security bits.
Apartfrom the runtime performance,our scheme offers
severaladvantages.From the practicality pointof view,
the generation of keys and public parameters by the trusted
coordinatornodemakesthe smooth accomplishmentof
TABLE 6.Our scheme vs RSA memory consumption on 256 bytes of
message.
encryption and re-encryption processes. The approach i
directional in that it enables the sender IoT device to de
gate a fog node to re-encrypt the ciphertext for the rece
to decrypt,butthe reverse is notnecessary.The system is
also non-interactive in that the sender and the receiver
need to communicate for the construction of re-encrypti
key.Additionally,plaintext-cipherratiosvary asvariable
size messages produce constant size (386 bytes) of ciph
text. This is non-expansion makes the approach efficien
embedded devices.The proxy node can produce one-time
parameters in scalable manner,and needs to be online for
the real-time applications of IoT. On the hand, locality ba
coordinator nodes could be designed for large networks
make the system more scalable. However, our system is
ited to sing-hop fog nodes, and the case of multi-hop no
open for future studies. The main time-consuming opera
are globalparameters generation,which is computed once
during registration.
VI. CONCLUSION AND FUTURE WORK
This research has proposed ECC based proxy re-encrypt
for fog-to-things as a lightweightencryption scheme.The
security schemehas been analyzed forencryption and
decryption runtime efficiency,and throughputciphertext
expansion.The implementation has proved the effective-
ness and efficiency of outsourcing security functions to f
nodes for IoT applications.In addition,the implementation
of encryption using ECC produced smaller size cipher te
than RSA, proving that ECC is an appropriate cryptograp
mechanism for embedded systems such as IoTs. It has b
concluded that lightweight security mechanisms for IoTs
be achieved by offloading security functions of IoTs to fo
nodes for resource constraints as well as employing ECC
its smaller message sizes. In the future, implementing o
platforms such as raspery and Arduino will be considere
practical applicability.
ACKNOWLEDGMENT
This work was supported by the Soonchunhyang Univers
Research Fund and also supported by the MSIP (Ministry
Science,ICT and Future Planning),Korea,under the ITRC
(Information Technology Research Center) support prog
(IITP-2018-2014-1-00720) supervised by the IITP (Institu
for information & communications Technology Promotio
VOLUME 6, 2018 26829
FIGURE 9.Our scheme vs RSA encryption and Decryption runtime for 128
bytes of message.
FIGURE 10.Our scheme vs RSA throughput comparison for for various
data sizes and security bits.
Apartfrom the runtime performance,our scheme offers
severaladvantages.From the practicality pointof view,
the generation of keys and public parameters by the trusted
coordinatornodemakesthe smooth accomplishmentof
TABLE 6.Our scheme vs RSA memory consumption on 256 bytes of
message.
encryption and re-encryption processes. The approach i
directional in that it enables the sender IoT device to de
gate a fog node to re-encrypt the ciphertext for the rece
to decrypt,butthe reverse is notnecessary.The system is
also non-interactive in that the sender and the receiver
need to communicate for the construction of re-encrypti
key.Additionally,plaintext-cipherratiosvary asvariable
size messages produce constant size (386 bytes) of ciph
text. This is non-expansion makes the approach efficien
embedded devices.The proxy node can produce one-time
parameters in scalable manner,and needs to be online for
the real-time applications of IoT. On the hand, locality ba
coordinator nodes could be designed for large networks
make the system more scalable. However, our system is
ited to sing-hop fog nodes, and the case of multi-hop no
open for future studies. The main time-consuming opera
are globalparameters generation,which is computed once
during registration.
VI. CONCLUSION AND FUTURE WORK
This research has proposed ECC based proxy re-encrypt
for fog-to-things as a lightweightencryption scheme.The
security schemehas been analyzed forencryption and
decryption runtime efficiency,and throughputciphertext
expansion.The implementation has proved the effective-
ness and efficiency of outsourcing security functions to f
nodes for IoT applications.In addition,the implementation
of encryption using ECC produced smaller size cipher te
than RSA, proving that ECC is an appropriate cryptograp
mechanism for embedded systems such as IoTs. It has b
concluded that lightweight security mechanisms for IoTs
be achieved by offloading security functions of IoTs to fo
nodes for resource constraints as well as employing ECC
its smaller message sizes. In the future, implementing o
platforms such as raspery and Arduino will be considere
practical applicability.
ACKNOWLEDGMENT
This work was supported by the Soonchunhyang Univers
Research Fund and also supported by the MSIP (Ministry
Science,ICT and Future Planning),Korea,under the ITRC
(Information Technology Research Center) support prog
(IITP-2018-2014-1-00720) supervised by the IITP (Institu
for information & communications Technology Promotio
VOLUME 6, 2018 26829
Secure Best Marks with AI Grader
Need help grading? Try our AI Grader for instant feedback on your assignments.

A. A. Diro et al.:Analysis of Lightweight Encryption Scheme for Fog-to-Things Communication
REFERENCES
[1] A. Diro, N. Chilamkurti,and N. Kumar,‘‘Lightweightcybersecurity
schemes using elliptic curve cryptography in publish-subscribe fog com-
puting,’’ Mobile Netw. Appl., vol. 22, no. 5, pp. 848–858, 2017.
[2] (2016). Securing the Internet of Things: A Proposed Framework. [Online].
Available: http://www.cisco.com/c/en/us/about/security-center/secure-iot-
proposed-framework.html
[3] A. A. Diro, N. Chilamkurti, and P. Veeraraghavan, ‘‘Elliptic curve based
cybersecurity schemes for publish-subscribe Internet of Things,’’ in Proc.
Int. Conf. Heterogeneous Netw. Quality, Rel., Secur. Robustness, Jul. 2016,
pp. 258–268.
[4] I. Stojmenovic,‘‘Fog computing:A cloud to the ground supportfor
smart things and machine-to-machine networks,’’ in Proc. IEEE Austral.
Telecommun. Netw. Appl. Conf. (ATNAC), Nov. 2014, pp. 117–122.
[5] A. A. Diro, H. T. Reda,and N.Chilamkurti,‘‘Differentialflow space
allocation scheme in SDN based fog computing for IoT applications,’’
J. AmbientIntell. HumanizedComput.,pp. 1–11, Jan. 2018,doi:
https://doi.org/10.1007/s12652-017-0677-z
[6] I. Stojmenovic and S. Wen, ‘‘The fog computing paradigm: Scenarios and
security issues,’’ in Proc.IEEE Federated Conf.Comput.Sci.Inf. Syst.,
Warsaw, Poland, Sep. 2014, pp. 1–8.
[7] M. Ibrahim,‘‘Octopus:An edge-fog mutualauthentication scheme,’’
J. Netw. Secur., vol. 18, no. 6, pp. 1089–1101, 2016.
[8] S. Yi, Z. Qin, and Q. Li, ‘‘Security and privacy issues of fog computing:
A survey,’’ in Proc.Int.Conf.Wireless Algorithms,Syst.Appl.(WASA),
2015, pp. 685–695.
[9] I. Yaqoob et al., ‘‘The rise of ransomware and emerging security challenges
and solutions in the Internet of Things,’’ Comput. Netw., vol. 129, no. 2,
pp. 444–458, Dec. 2017.
[10] A. Diro and N. Chilamkurti,‘‘Distributed attack detection scheme
using deep learning approach for Internetof Things,’’ Future Generat.
Comput.Syst.,vol. 282,pp. 761–768,May 2017.[Online].Available:
https://doi.org/10.1016/j.future.2017.08.043
[11] Top 5 WaysFog Computing Can Make IoT More Secure.Accessed:
Nov. 12, 2017.[Online].Available:https://www.openfogconsortium.
org/top-5-ways-fog-computing-can-make-iot-more-secure/
[12] J. McCumber,Assessingand ManagingSecurityRisk in IT Sys-
tems:A StructuredMethodology.1st ed. Boca Raton,FL, USA:
Auerbach Publications, Jun. 2004.
[13] W. Stallings and M.P. Tahiliani,Cryptography and Network Security:
Principles and Practice, vol. 6. London, U.K.: Pearson, 2014.
[14] Distributed Denialof Service Attacks—The InternetProtocolJournal.
Accessed:Nov. 14, 2016. [Online]. Available:http://www.cisco.
com/c/en/us/about/press/internet-protocol-journal/back-issues/table-
contents-30/dos-attacks.html
[15] C. Patrikakis, M. Masikos, and O. Zouraraki, ‘‘Distributed denial of service
attacks,’’ Internet Protocol J., vol. 7, no. 4, pp. 1–2, 2004.
[16] S. Yi, C. Li, and Q. Li, ‘‘A survey of fog computing:Concepts,
applicationsand issues,’’in Proc. WorkshopMobile Big Data
(Mobidata), New York, NY, USA, 2015, pp. 37–42. [Online]. Available:
http://dx.doi.org/10.1145/2757384.2757397
[17] C. Dsouza, G. J. Ahn, and M. Taguinod, ‘‘Policy-driven security manage-
ment for fog computing: Preliminary framework and a case study,’’ in Proc.
IEEE 15th Int.Conf.Inf. Reuse Integr.(IEEE IRI), Redwood City,CA,
USA, Aug. 2014, pp. 16–23, doi: 10.1109/IRI.2014.7051866.
[18] I. Stojmenovic, X. Huang, and H. Luan, ‘‘An overview of fog computing
and its security issues,’’ Concurrency Computat.Pract.Exper.,vol.28,
no. 10, pp. 2991–3005, 2016, doi: 10.1002/cpe.3485.
[19] R. Roman,J. Lopez,and M. Mambo,‘‘Mobile edge computing,fog:
A survey and analysis of security threats and challenges,’’ Future Generat.
Comput. Syst., vol. 78, no. 2, pp. 680–698, Nov. 2016, [Online]. Available:
http://dx.doi.org/10.1016/j.future.2016.11.009
[20] RSA vs ECC Comparisonfor EmbeddedSystems.Accessed:
Nov. 12, 2017. [Online].Available:http://www.atmel.com/Images/
Atmel-8951-CryptoAuth-RSA-ECC-Comparison-Embedded-Systems-
WhitePaper.pdf
[21] D. Hankerson,S. Vanstone,and A.J. Menezes,Guide to Elliptic Curve
Cryptography. New York, NY, USA: Springer-Verlag, 2004.
[22] S. Sandeep, ‘‘Elliptic curve cryptography for constrained devices,’’ Ph.D.
dissertation,Faculty Elect.Eng. Inf. Technol.,Ruhr-Univ.Bochum,
Bochum, Germany, 2006.
[23] ElgamalEncryptionUsing Elliptic Curve Cryptography.Accessed:
Nov. 11, 2017.[Online].Available:https://cse.unl.edu/~ssamal/crypto/
EEECC.pdf
[24] G. Ateniese, K. Fu, M. Green, and S. Hohenberger, ‘‘Improved proxy r
encryption schemes with applications to secure distributed storage,’’
Trans. Inf. Syst. Secur., vol. 9, no. 1, pp. 1–30, 2006.
[25] P. Yuriy, R. Kurt, S. Gyana, and V. Vinod, ‘‘Fast proxy re-encryption fo
publish/subscribe systems,’’ ACM Trans.Privacy Secur.,vol.20,no.4,
p. 14, 2017.
[26] G. Ateniese,K. Benson,and S.Hohenberger,‘‘Key-private proxy re-
encryption,’’ in Topics in Cryptology—CT-RSA (Lecture Notes in Com-
puter Science),vol.5473,M. Fischlin,Eds.Berlin,Germany: Springer,
Berlin, 2009.
[27] M. Green and G.Ateniese,‘‘Identity-based proxy re-encryption,’’in
Applied Cryptography and Network Security. Berlin, Germany: Spring
2007.
[28] Z. Ali, M. Imran,M. Alsulaiman,T. Zia, and M. Shoaib,‘‘A zero-
watermarking algorithm for privacy protection in a voice disorder det
system,’’ Future Gener. Comput. Syst., vol. 82, no. 5, pp. 290–303, 20
[29] I. Yaqoob et al.,‘‘Internet of Things architecture: Recent advances,tax-
onomy,requirements,and open challenges,’’IEEE Wireless Commun.,
vol. 24, no. 3, pp. 10–16, Jun. 2017.
[30] Z. Wang,‘‘Leakage resilientID-based proxy re-encryption scheme for
access control in fog computing,’’ Future Generat.Comput.Syst.,to be
published.
[31] Y.-J. Song and J.-M.Kim, ‘‘Secure data sharing based on proxy re-
encryption in fog computing environment,’’ in Proc.Asia–Pacific Appl.
Sci. Eng. Better Hum. Life, 2016, pp. 52–56.
[32] M. Sepehri,and A.Trombetta,‘‘Secure and efficientdata sharing with
atribute-based proxy re-encryption scheme,’’ in Proc. 12th Int. Conf.
ability, Rel. Secur., 2017, p. 63.
ABEBE ABESHU DIRO received the M.Sc.
degree in computerscience from Addis Ababa
University, Ethiopia, in 2010. He is currently pur-
suing the Ph.D.degree with the Departmentof
ComputerScience and Information Technology,
La Trobe University,Bundoora VIC,Australia.
From 2007 to 2013,he was the Director of ICT
Development with Wollega University,where he
is currently a Lecturer in computer science.His
research interests include software defined net-
working, Internet of Things, cybersecuirity, advanced networking, mac
learning, and big data.
NAVEEN CHILAMKURTI received thePh.D.
degreefrom La TrobeUniversity,Melbourne,
VIC, Australia.He is currently a Cybersecurity
Program Coordinatorwith the Departmentof
ComputerScience and Information Technology,
La Trobe University.His currentresearch areas
include intelligenttransportsystems,smartgrid
computing,vehicular communications,vehicular
cloud, cyber security,wireless multimedia,
wireless sensor networks, and mobile security.
YUNYOUNG NAM received the B.S., M.S., and
Ph.D. degrees in computer engineering from Ajou
University, South Korea, in 2001, 2003, and 2007,
respectively. From 2007 to 2010, he was a Senior
Researcherwith the Centerof Excellencein
Ubiquitous System. From 2010 to 2011, he was a
Research Professor with Ajou University. He also
spenttime as a Post-DoctoralResearcher atthe
Center of Excellence for Wireless and Information
Technology,Stony Brook University,NY, USA,
from 2009 to 2013.From 2013 to 2014,he was a Post-DoctoralFellow
with the Worcester Polytechnic Institute,Worcester,MA, USA. In 2017,
he was the Director of the ICT Convergence Rehabilitation Engineering
Research Center, Soonchunhyang University, where he is currently an
tant Professor with the Department of Computer Science and Engineer
His research interests include multimedia database, ubiquitous compu
image processing,pattern recognition,context-awareness,conflictresolu-
tion, wearable computing, intelligent video surveillance, cloud comput
biomedical signal processing, rehabilitation, and healthcare system.
26830 VOLUME 6, 2018
REFERENCES
[1] A. Diro, N. Chilamkurti,and N. Kumar,‘‘Lightweightcybersecurity
schemes using elliptic curve cryptography in publish-subscribe fog com-
puting,’’ Mobile Netw. Appl., vol. 22, no. 5, pp. 848–858, 2017.
[2] (2016). Securing the Internet of Things: A Proposed Framework. [Online].
Available: http://www.cisco.com/c/en/us/about/security-center/secure-iot-
proposed-framework.html
[3] A. A. Diro, N. Chilamkurti, and P. Veeraraghavan, ‘‘Elliptic curve based
cybersecurity schemes for publish-subscribe Internet of Things,’’ in Proc.
Int. Conf. Heterogeneous Netw. Quality, Rel., Secur. Robustness, Jul. 2016,
pp. 258–268.
[4] I. Stojmenovic,‘‘Fog computing:A cloud to the ground supportfor
smart things and machine-to-machine networks,’’ in Proc. IEEE Austral.
Telecommun. Netw. Appl. Conf. (ATNAC), Nov. 2014, pp. 117–122.
[5] A. A. Diro, H. T. Reda,and N.Chilamkurti,‘‘Differentialflow space
allocation scheme in SDN based fog computing for IoT applications,’’
J. AmbientIntell. HumanizedComput.,pp. 1–11, Jan. 2018,doi:
https://doi.org/10.1007/s12652-017-0677-z
[6] I. Stojmenovic and S. Wen, ‘‘The fog computing paradigm: Scenarios and
security issues,’’ in Proc.IEEE Federated Conf.Comput.Sci.Inf. Syst.,
Warsaw, Poland, Sep. 2014, pp. 1–8.
[7] M. Ibrahim,‘‘Octopus:An edge-fog mutualauthentication scheme,’’
J. Netw. Secur., vol. 18, no. 6, pp. 1089–1101, 2016.
[8] S. Yi, Z. Qin, and Q. Li, ‘‘Security and privacy issues of fog computing:
A survey,’’ in Proc.Int.Conf.Wireless Algorithms,Syst.Appl.(WASA),
2015, pp. 685–695.
[9] I. Yaqoob et al., ‘‘The rise of ransomware and emerging security challenges
and solutions in the Internet of Things,’’ Comput. Netw., vol. 129, no. 2,
pp. 444–458, Dec. 2017.
[10] A. Diro and N. Chilamkurti,‘‘Distributed attack detection scheme
using deep learning approach for Internetof Things,’’ Future Generat.
Comput.Syst.,vol. 282,pp. 761–768,May 2017.[Online].Available:
https://doi.org/10.1016/j.future.2017.08.043
[11] Top 5 WaysFog Computing Can Make IoT More Secure.Accessed:
Nov. 12, 2017.[Online].Available:https://www.openfogconsortium.
org/top-5-ways-fog-computing-can-make-iot-more-secure/
[12] J. McCumber,Assessingand ManagingSecurityRisk in IT Sys-
tems:A StructuredMethodology.1st ed. Boca Raton,FL, USA:
Auerbach Publications, Jun. 2004.
[13] W. Stallings and M.P. Tahiliani,Cryptography and Network Security:
Principles and Practice, vol. 6. London, U.K.: Pearson, 2014.
[14] Distributed Denialof Service Attacks—The InternetProtocolJournal.
Accessed:Nov. 14, 2016. [Online]. Available:http://www.cisco.
com/c/en/us/about/press/internet-protocol-journal/back-issues/table-
contents-30/dos-attacks.html
[15] C. Patrikakis, M. Masikos, and O. Zouraraki, ‘‘Distributed denial of service
attacks,’’ Internet Protocol J., vol. 7, no. 4, pp. 1–2, 2004.
[16] S. Yi, C. Li, and Q. Li, ‘‘A survey of fog computing:Concepts,
applicationsand issues,’’in Proc. WorkshopMobile Big Data
(Mobidata), New York, NY, USA, 2015, pp. 37–42. [Online]. Available:
http://dx.doi.org/10.1145/2757384.2757397
[17] C. Dsouza, G. J. Ahn, and M. Taguinod, ‘‘Policy-driven security manage-
ment for fog computing: Preliminary framework and a case study,’’ in Proc.
IEEE 15th Int.Conf.Inf. Reuse Integr.(IEEE IRI), Redwood City,CA,
USA, Aug. 2014, pp. 16–23, doi: 10.1109/IRI.2014.7051866.
[18] I. Stojmenovic, X. Huang, and H. Luan, ‘‘An overview of fog computing
and its security issues,’’ Concurrency Computat.Pract.Exper.,vol.28,
no. 10, pp. 2991–3005, 2016, doi: 10.1002/cpe.3485.
[19] R. Roman,J. Lopez,and M. Mambo,‘‘Mobile edge computing,fog:
A survey and analysis of security threats and challenges,’’ Future Generat.
Comput. Syst., vol. 78, no. 2, pp. 680–698, Nov. 2016, [Online]. Available:
http://dx.doi.org/10.1016/j.future.2016.11.009
[20] RSA vs ECC Comparisonfor EmbeddedSystems.Accessed:
Nov. 12, 2017. [Online].Available:http://www.atmel.com/Images/
Atmel-8951-CryptoAuth-RSA-ECC-Comparison-Embedded-Systems-
WhitePaper.pdf
[21] D. Hankerson,S. Vanstone,and A.J. Menezes,Guide to Elliptic Curve
Cryptography. New York, NY, USA: Springer-Verlag, 2004.
[22] S. Sandeep, ‘‘Elliptic curve cryptography for constrained devices,’’ Ph.D.
dissertation,Faculty Elect.Eng. Inf. Technol.,Ruhr-Univ.Bochum,
Bochum, Germany, 2006.
[23] ElgamalEncryptionUsing Elliptic Curve Cryptography.Accessed:
Nov. 11, 2017.[Online].Available:https://cse.unl.edu/~ssamal/crypto/
EEECC.pdf
[24] G. Ateniese, K. Fu, M. Green, and S. Hohenberger, ‘‘Improved proxy r
encryption schemes with applications to secure distributed storage,’’
Trans. Inf. Syst. Secur., vol. 9, no. 1, pp. 1–30, 2006.
[25] P. Yuriy, R. Kurt, S. Gyana, and V. Vinod, ‘‘Fast proxy re-encryption fo
publish/subscribe systems,’’ ACM Trans.Privacy Secur.,vol.20,no.4,
p. 14, 2017.
[26] G. Ateniese,K. Benson,and S.Hohenberger,‘‘Key-private proxy re-
encryption,’’ in Topics in Cryptology—CT-RSA (Lecture Notes in Com-
puter Science),vol.5473,M. Fischlin,Eds.Berlin,Germany: Springer,
Berlin, 2009.
[27] M. Green and G.Ateniese,‘‘Identity-based proxy re-encryption,’’in
Applied Cryptography and Network Security. Berlin, Germany: Spring
2007.
[28] Z. Ali, M. Imran,M. Alsulaiman,T. Zia, and M. Shoaib,‘‘A zero-
watermarking algorithm for privacy protection in a voice disorder det
system,’’ Future Gener. Comput. Syst., vol. 82, no. 5, pp. 290–303, 20
[29] I. Yaqoob et al.,‘‘Internet of Things architecture: Recent advances,tax-
onomy,requirements,and open challenges,’’IEEE Wireless Commun.,
vol. 24, no. 3, pp. 10–16, Jun. 2017.
[30] Z. Wang,‘‘Leakage resilientID-based proxy re-encryption scheme for
access control in fog computing,’’ Future Generat.Comput.Syst.,to be
published.
[31] Y.-J. Song and J.-M.Kim, ‘‘Secure data sharing based on proxy re-
encryption in fog computing environment,’’ in Proc.Asia–Pacific Appl.
Sci. Eng. Better Hum. Life, 2016, pp. 52–56.
[32] M. Sepehri,and A.Trombetta,‘‘Secure and efficientdata sharing with
atribute-based proxy re-encryption scheme,’’ in Proc. 12th Int. Conf.
ability, Rel. Secur., 2017, p. 63.
ABEBE ABESHU DIRO received the M.Sc.
degree in computerscience from Addis Ababa
University, Ethiopia, in 2010. He is currently pur-
suing the Ph.D.degree with the Departmentof
ComputerScience and Information Technology,
La Trobe University,Bundoora VIC,Australia.
From 2007 to 2013,he was the Director of ICT
Development with Wollega University,where he
is currently a Lecturer in computer science.His
research interests include software defined net-
working, Internet of Things, cybersecuirity, advanced networking, mac
learning, and big data.
NAVEEN CHILAMKURTI received thePh.D.
degreefrom La TrobeUniversity,Melbourne,
VIC, Australia.He is currently a Cybersecurity
Program Coordinatorwith the Departmentof
ComputerScience and Information Technology,
La Trobe University.His currentresearch areas
include intelligenttransportsystems,smartgrid
computing,vehicular communications,vehicular
cloud, cyber security,wireless multimedia,
wireless sensor networks, and mobile security.
YUNYOUNG NAM received the B.S., M.S., and
Ph.D. degrees in computer engineering from Ajou
University, South Korea, in 2001, 2003, and 2007,
respectively. From 2007 to 2010, he was a Senior
Researcherwith the Centerof Excellencein
Ubiquitous System. From 2010 to 2011, he was a
Research Professor with Ajou University. He also
spenttime as a Post-DoctoralResearcher atthe
Center of Excellence for Wireless and Information
Technology,Stony Brook University,NY, USA,
from 2009 to 2013.From 2013 to 2014,he was a Post-DoctoralFellow
with the Worcester Polytechnic Institute,Worcester,MA, USA. In 2017,
he was the Director of the ICT Convergence Rehabilitation Engineering
Research Center, Soonchunhyang University, where he is currently an
tant Professor with the Department of Computer Science and Engineer
His research interests include multimedia database, ubiquitous compu
image processing,pattern recognition,context-awareness,conflictresolu-
tion, wearable computing, intelligent video surveillance, cloud comput
biomedical signal processing, rehabilitation, and healthcare system.
26830 VOLUME 6, 2018
1 out of 11
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
© 2024 | Zucol Services PVT LTD | All rights reserved.




