Analysis of Lightweight Encryption Scheme for Fog-to-Things Communication
11 Pages10056 Words476 Views
Added on 2023-05-29
About This Document
This paper discusses the security challenges, threats, requirements, fog nodes based security architectures and the possible cryptographic solutions of fog-to-things communications. It proposes a novel encryption scheme for fog-to-things communication and analyzes security challenges in terms of cybersecurity principles. The distribution of fog nodes can solve the scalability of cloud by reducing central processing and communications.
Analysis of Lightweight Encryption Scheme for Fog-to-Things Communication
Added on 2023-05-29
ShareRelated Documents
SPECIAL SECTION ON REAL-TIME EDGE ANALYTICS FOR BIG DATA IN INTERNET OF THINGS
Received March 8, 2018, accepted March 24, 2018, date of publication April 6, 2018, date of current version June 5, 2018.
Digital Object Identifier 10.1109/ACCESS.2018.2822822
Analysis of Lightweight Encryption Scheme
for Fog-to-Things Communication
ABEBE ABESHU DIRO1, NAVEEN CHILAMKURTI 1, AND YUNYOUNG NAM 2
1Department of Computer Science and Information Technology, La Trobe University, Melbourne, VIC 3083, Australia
2Department of Computer Science and Engineering, Soonchunhyang University, Asan 31538, South Korea
Corresponding author: Yunyoung Nam (ynam@sch.ac.kr)
This work was supported in part by the Soonchunhyang University Research Fund and in part by the MSIP (Ministry of Science, ICT, and
Future Planning), South Korea, through the Information Technology Research Center Support Program Supervised by the Institute for
Information and Communications Technology Promotion under Grant IITP-2018-2014-1-00720.
ABSTRACT The growing concerns in cybersecurity is preventing unknowns which evolve from time to
time. Internet of Things (IoT) is one of the emerging fields that have been applied for smart cities and
industries. The promises of IoTs could be confronted with the growth in the number and sophistication
of cyberattacks. The extension of digital world into physical environment adds new attack surfaces on the
existing security threats of traditional Internet. The major challenge brought about by physical connectivity
of IoTs is to implement distributed security mechanisms for resource constrain of IoT devices. As an
emerging architecture supporting IoT applications, fog computing can be considered to solve the resource
and distribution issues in securing fog-to-things communication. Security functions and services, such as
cryptography, could be offloaded to fog nodes to reduce computational and storage burdens on IoT devices.
The distribution of fog nodes can also solve the scalability of cloud by reducing central processing and
communications. On the other hand, lightweight cryptographic functions, such as elliptic curve cryptography,
have been proved to be suitable for embedded systems. In this paper, we have analyzed security challenges in
terms of cybersecurity principles and proposed a novel encryption scheme for fog-to-things communication.
INDEX TERMS Cybersecurity, Internet of things, fog computing, elliptic curve cryptography, lightweight
cryptography.
I. INTRODUCTION
By the end of this decade, the exponential growth in the
number of connected smart things, known as IoTs, is esti-
mated to be about 6 times the population of the world.
The adoption speed of these smart devices is unprecedent-
edly about five folds of the adoption history of electricity
and telephony altogether. The main contributing factor for
this increment in connectivity is the digitalization of home
devices (refrigerators, fans), smart city applications (con-
nected cars, smart traffic lights, smart grids, smart water util-
ities) and operational technologies (factory machines) across
the globe. The trend has been ignited by the shift from
IPv4 based Information technology (IT) to IPv6 oriented
operational technology (OT). The invention of IPv6 is one
of the crucial enablers of the deployment of IoT as Ipv4 is
unable to meet the requirements of the massive connections of
IoT networks [1], [2].
The massive scale adoption of IoTs, and the big data
generation in the vicinity trigger businesses and industries to
rethink the architecture of data processing, storage and com-
munications. The myriad of cloud computing applications in
business, industries, public services, etc. have been magnif-
icent over the last decades. Cloud computing has brought
essential breakthroughs of seamless IT outsourcing capability
with value-added services for customers. However, the cur-
rent explosion of edge computing paradigms has challenged
the scalability and performance of centralized cloud for IoT
applications [3]. Real-time applications such as smart cities,
eHealth, intelligent transport systems, industries, etc. need
predictable and low latency, and distributed low bandwidth
communication from IoT end to data repositories, where
cloud computing cannot satisfy the requirements. To mitigate
these issues, distributed intelligence, known as fog comput-
ing (FC), that bridges cloud computing closer to the things
has been introduced. Fig.1 shows typical fog architecture in
the things-to-cloud continuum.
FC complements cloud computing as it forms a service
continuum between IoT and the cloud. Fog network mimics
the cloud-to-things way of interaction at the edge network.
It bridges the gap between the cloud and smart things, which
enables a service continuum. The gap is closed in the form of
enabling the distribution of computing and control, storage,
26820
2169-3536 2018 IEEE. Translations and content mining are permitted for academic research only.
Personal use is also permitted, but republication/redistribution requires IEEE permission.
See http://www.ieee.org/publications_standards/publications/rights/index.html for more information.
VOLUME 6, 2018
Received March 8, 2018, accepted March 24, 2018, date of publication April 6, 2018, date of current version June 5, 2018.
Digital Object Identifier 10.1109/ACCESS.2018.2822822
Analysis of Lightweight Encryption Scheme
for Fog-to-Things Communication
ABEBE ABESHU DIRO1, NAVEEN CHILAMKURTI 1, AND YUNYOUNG NAM 2
1Department of Computer Science and Information Technology, La Trobe University, Melbourne, VIC 3083, Australia
2Department of Computer Science and Engineering, Soonchunhyang University, Asan 31538, South Korea
Corresponding author: Yunyoung Nam (ynam@sch.ac.kr)
This work was supported in part by the Soonchunhyang University Research Fund and in part by the MSIP (Ministry of Science, ICT, and
Future Planning), South Korea, through the Information Technology Research Center Support Program Supervised by the Institute for
Information and Communications Technology Promotion under Grant IITP-2018-2014-1-00720.
ABSTRACT The growing concerns in cybersecurity is preventing unknowns which evolve from time to
time. Internet of Things (IoT) is one of the emerging fields that have been applied for smart cities and
industries. The promises of IoTs could be confronted with the growth in the number and sophistication
of cyberattacks. The extension of digital world into physical environment adds new attack surfaces on the
existing security threats of traditional Internet. The major challenge brought about by physical connectivity
of IoTs is to implement distributed security mechanisms for resource constrain of IoT devices. As an
emerging architecture supporting IoT applications, fog computing can be considered to solve the resource
and distribution issues in securing fog-to-things communication. Security functions and services, such as
cryptography, could be offloaded to fog nodes to reduce computational and storage burdens on IoT devices.
The distribution of fog nodes can also solve the scalability of cloud by reducing central processing and
communications. On the other hand, lightweight cryptographic functions, such as elliptic curve cryptography,
have been proved to be suitable for embedded systems. In this paper, we have analyzed security challenges in
terms of cybersecurity principles and proposed a novel encryption scheme for fog-to-things communication.
INDEX TERMS Cybersecurity, Internet of things, fog computing, elliptic curve cryptography, lightweight
cryptography.
I. INTRODUCTION
By the end of this decade, the exponential growth in the
number of connected smart things, known as IoTs, is esti-
mated to be about 6 times the population of the world.
The adoption speed of these smart devices is unprecedent-
edly about five folds of the adoption history of electricity
and telephony altogether. The main contributing factor for
this increment in connectivity is the digitalization of home
devices (refrigerators, fans), smart city applications (con-
nected cars, smart traffic lights, smart grids, smart water util-
ities) and operational technologies (factory machines) across
the globe. The trend has been ignited by the shift from
IPv4 based Information technology (IT) to IPv6 oriented
operational technology (OT). The invention of IPv6 is one
of the crucial enablers of the deployment of IoT as Ipv4 is
unable to meet the requirements of the massive connections of
IoT networks [1], [2].
The massive scale adoption of IoTs, and the big data
generation in the vicinity trigger businesses and industries to
rethink the architecture of data processing, storage and com-
munications. The myriad of cloud computing applications in
business, industries, public services, etc. have been magnif-
icent over the last decades. Cloud computing has brought
essential breakthroughs of seamless IT outsourcing capability
with value-added services for customers. However, the cur-
rent explosion of edge computing paradigms has challenged
the scalability and performance of centralized cloud for IoT
applications [3]. Real-time applications such as smart cities,
eHealth, intelligent transport systems, industries, etc. need
predictable and low latency, and distributed low bandwidth
communication from IoT end to data repositories, where
cloud computing cannot satisfy the requirements. To mitigate
these issues, distributed intelligence, known as fog comput-
ing (FC), that bridges cloud computing closer to the things
has been introduced. Fig.1 shows typical fog architecture in
the things-to-cloud continuum.
FC complements cloud computing as it forms a service
continuum between IoT and the cloud. Fog network mimics
the cloud-to-things way of interaction at the edge network.
It bridges the gap between the cloud and smart things, which
enables a service continuum. The gap is closed in the form of
enabling the distribution of computing and control, storage,
26820
2169-3536 2018 IEEE. Translations and content mining are permitted for academic research only.
Personal use is also permitted, but republication/redistribution requires IEEE permission.
See http://www.ieee.org/publications_standards/publications/rights/index.html for more information.
VOLUME 6, 2018

A. A. Diro et al.: Analysis of Lightweight Encryption Scheme for Fog-to-Things Communication
FIGURE 1. Basic Architecture of a fog network [8].
and networking functions closer to smart objects [4], [5] at
any location across the continuum.
II. SECURITY SCHEMES IN FOG-TO-THINGS
COMMUNICATION
The importance of security mechanisms for unprotected
smart devices is unquestionable. For instance, smart grid
users need authentication and authorization mechanisms to
enable only subscribed users can access electric bills. Simi-
larly, in smart life, healthcare systems require only physicians
and nurses to notify about the status of patients as confiden-
tiality has ultimate importance. In both cases, unauthorized
adversaries should not eavesdrop on or access to the messages
sent by clients.
In this section, we discuss the security challenges, threats,
requirements, fog nodes based security architectures and the
possible cryptographic solutions of fog-to-things communi-
cations.
A. SECURITY CHALLENGES
The promises of FC could be challenged by the growth in the
number and sophistication of cyber-attacks in the communi-
cations of fog-to-things. The existing security threats of the
traditional Internet will continue to be the threats of fog-to-
things interactions. It is also evident that the extension of core
networks to the physical world brings more devices, interac-
tions, and protocols which can broaden attack surfaces and
born new cyber threats. The major challenge brought about
by physical connectivity is to implement distributed security
mechanisms for fog-to-things communication for resource
constrain of IoT devices [6]–[9]. It is bandwidth inefficient,
prone to high latency and suffer from scalability to offload
security functions of massively distributed IoT devices to
cloud while it is computationally prohibitive to deploy secu-
rity schemes on the devices. For instance, smart meter micro-
controller has no capability of performing traditional Internet
cryptographic operations, and the connection to cloud incurs
a significant bandwidth cost and high latency for wireless
communication dominant IoT environment. The emerging
field of IoT needs a robust and lightweight security schemes.
In traditional Internet, it is either the device or the cen-
tralized cloud that handles resource-intensive cybersecurity
operations such as cryptographic encryption, access control,
authentication, and authorization. These existing cybersecu-
rity schemes for resource-rich infrastructure cannot prevail
for addressing IoT cybersecurity challenges. The distribution
and resource limitations of IoT devices in securing IoTs could
be tackled by offloading securing functions to the distributed
fog nodes [10]. Thus, fog nodes can be employed to offload
cryptographic computations as proxy nodes without revealing
the data in communications.
B. SECURITY THREATS
The IoT/Fog computing ecosystem is partly confronted with
the same cybersecurity challenges as traditional IT ecosys-
tem. IoT devices add a completely different dimension to
cybersecurity world because of their physical interaction with
the Internet. This is a serious implication that shows the
transformation of attack surfaces from digital world (data) to
physical world (actuation), which can broaden the horizon of
known threats to zero-day attacks of new devices, workflows,
and protocols [11]. The attack surface of fog-to-things can
further be expanded as closed operational systems such as
SCADA are moving to IP based open systems.
The major attacks in fog-to-things are impersonation,
M-in-M, injection and DoS attacks [17]–[19]. Impersonation
attack is a form of attack pretending to have legitimate iden-
tity using some other entity’s identity. In the fog-to-things
scenario, IoT devices could be eavesdropped or sniffed for
identity. As wireless communication is the common platform
of communication in the ecosystem, it is one of the most
commonly observed attacks in the IoT use cases. This kind
of spoofing attack might target the identity-based authenti-
cation systems which use MAC and IP addresses. Man-in-
the-middle (MitM) attack is another type of impersonation
attack in which the third node intercepts the communica-
tions between two nodes to capture data or authentication
credentials. For instance, a simple mobile node (e.g. carrying
Zeus) can act as a middleman to impersonate a sensor and its
communicating fog node in the domain of Fog-to-things net-
work. In addition, a replay attack occurs when an adversary
captures some parts of a communication between two nodes
and then retransmits the captured information, usually secu-
rity credentials, later to bypass authentication mechanisms.
A rogue fog node could be installed as a replay or MitM
node in the Fog network either by the legitimate internal
entity or cyber attacker without explicit authorization. For
instance, a malicious rogue smart grid aggregator can tamper
the data with smart meter creating wrong readings or it can
modify IP addresses. Since it is stealthy to detect, a rogue
node can instantiate further attacks such as DoS, causing a
threat to data security and privacy [27], [28]. These indicate
that strong identity management and mutual authentication,
and encryption are the key elements for enhancing the secu-
rity and privacy of IoT.
VOLUME 6, 2018 26821
FIGURE 1. Basic Architecture of a fog network [8].
and networking functions closer to smart objects [4], [5] at
any location across the continuum.
II. SECURITY SCHEMES IN FOG-TO-THINGS
COMMUNICATION
The importance of security mechanisms for unprotected
smart devices is unquestionable. For instance, smart grid
users need authentication and authorization mechanisms to
enable only subscribed users can access electric bills. Simi-
larly, in smart life, healthcare systems require only physicians
and nurses to notify about the status of patients as confiden-
tiality has ultimate importance. In both cases, unauthorized
adversaries should not eavesdrop on or access to the messages
sent by clients.
In this section, we discuss the security challenges, threats,
requirements, fog nodes based security architectures and the
possible cryptographic solutions of fog-to-things communi-
cations.
A. SECURITY CHALLENGES
The promises of FC could be challenged by the growth in the
number and sophistication of cyber-attacks in the communi-
cations of fog-to-things. The existing security threats of the
traditional Internet will continue to be the threats of fog-to-
things interactions. It is also evident that the extension of core
networks to the physical world brings more devices, interac-
tions, and protocols which can broaden attack surfaces and
born new cyber threats. The major challenge brought about
by physical connectivity is to implement distributed security
mechanisms for fog-to-things communication for resource
constrain of IoT devices [6]–[9]. It is bandwidth inefficient,
prone to high latency and suffer from scalability to offload
security functions of massively distributed IoT devices to
cloud while it is computationally prohibitive to deploy secu-
rity schemes on the devices. For instance, smart meter micro-
controller has no capability of performing traditional Internet
cryptographic operations, and the connection to cloud incurs
a significant bandwidth cost and high latency for wireless
communication dominant IoT environment. The emerging
field of IoT needs a robust and lightweight security schemes.
In traditional Internet, it is either the device or the cen-
tralized cloud that handles resource-intensive cybersecurity
operations such as cryptographic encryption, access control,
authentication, and authorization. These existing cybersecu-
rity schemes for resource-rich infrastructure cannot prevail
for addressing IoT cybersecurity challenges. The distribution
and resource limitations of IoT devices in securing IoTs could
be tackled by offloading securing functions to the distributed
fog nodes [10]. Thus, fog nodes can be employed to offload
cryptographic computations as proxy nodes without revealing
the data in communications.
B. SECURITY THREATS
The IoT/Fog computing ecosystem is partly confronted with
the same cybersecurity challenges as traditional IT ecosys-
tem. IoT devices add a completely different dimension to
cybersecurity world because of their physical interaction with
the Internet. This is a serious implication that shows the
transformation of attack surfaces from digital world (data) to
physical world (actuation), which can broaden the horizon of
known threats to zero-day attacks of new devices, workflows,
and protocols [11]. The attack surface of fog-to-things can
further be expanded as closed operational systems such as
SCADA are moving to IP based open systems.
The major attacks in fog-to-things are impersonation,
M-in-M, injection and DoS attacks [17]–[19]. Impersonation
attack is a form of attack pretending to have legitimate iden-
tity using some other entity’s identity. In the fog-to-things
scenario, IoT devices could be eavesdropped or sniffed for
identity. As wireless communication is the common platform
of communication in the ecosystem, it is one of the most
commonly observed attacks in the IoT use cases. This kind
of spoofing attack might target the identity-based authenti-
cation systems which use MAC and IP addresses. Man-in-
the-middle (MitM) attack is another type of impersonation
attack in which the third node intercepts the communica-
tions between two nodes to capture data or authentication
credentials. For instance, a simple mobile node (e.g. carrying
Zeus) can act as a middleman to impersonate a sensor and its
communicating fog node in the domain of Fog-to-things net-
work. In addition, a replay attack occurs when an adversary
captures some parts of a communication between two nodes
and then retransmits the captured information, usually secu-
rity credentials, later to bypass authentication mechanisms.
A rogue fog node could be installed as a replay or MitM
node in the Fog network either by the legitimate internal
entity or cyber attacker without explicit authorization. For
instance, a malicious rogue smart grid aggregator can tamper
the data with smart meter creating wrong readings or it can
modify IP addresses. Since it is stealthy to detect, a rogue
node can instantiate further attacks such as DoS, causing a
threat to data security and privacy [27], [28]. These indicate
that strong identity management and mutual authentication,
and encryption are the key elements for enhancing the secu-
rity and privacy of IoT.
VOLUME 6, 2018 26821

A. A. Diro et al.: Analysis of Lightweight Encryption Scheme for Fog-to-Things Communication
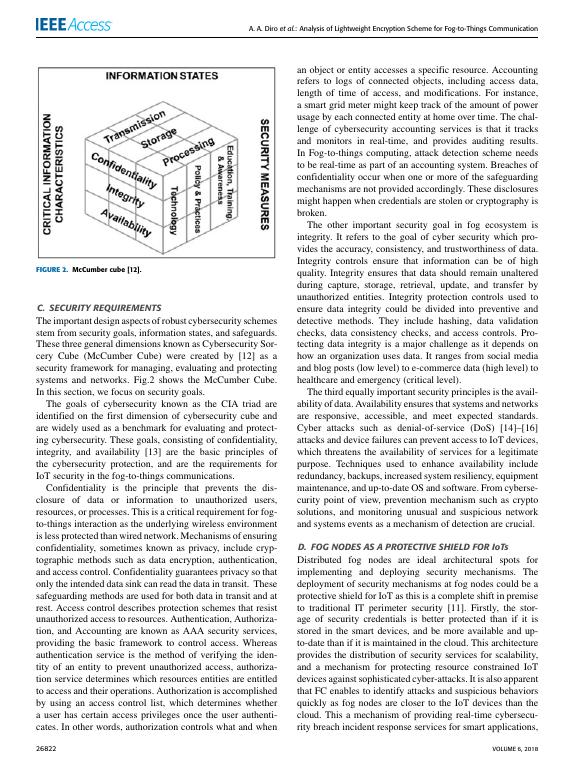
FIGURE 2. McCumber cube [12].
C. SECURITY REQUIREMENTS
The important design aspects of robust cybersecurity schemes
stem from security goals, information states, and safeguards.
These three general dimensions known as Cybersecurity Sor-
cery Cube (McCumber Cube) were created by [12] as a
security framework for managing, evaluating and protecting
systems and networks. Fig.2 shows the McCumber Cube.
In this section, we focus on security goals.
The goals of cybersecurity known as the CIA triad are
identified on the first dimension of cybersecurity cube and
are widely used as a benchmark for evaluating and protect-
ing cybersecurity. These goals, consisting of confidentiality,
integrity, and availability [13] are the basic principles of
the cybersecurity protection, and are the requirements for
IoT security in the fog-to-things communications.
Confidentiality is the principle that prevents the dis-
closure of data or information to unauthorized users,
resources, or processes. This is a critical requirement for fog-
to-things interaction as the underlying wireless environment
is less protected than wired network. Mechanisms of ensuring
confidentiality, sometimes known as privacy, include cryp-
tographic methods such as data encryption, authentication,
and access control. Confidentiality guarantees privacy so that
only the intended data sink can read the data in transit. These
safeguarding methods are used for both data in transit and at
rest. Access control describes protection schemes that resist
unauthorized access to resources. Authentication, Authoriza-
tion, and Accounting are known as AAA security services,
providing the basic framework to control access. Whereas
authentication service is the method of verifying the iden-
tity of an entity to prevent unauthorized access, authoriza-
tion service determines which resources entities are entitled
to access and their operations. Authorization is accomplished
by using an access control list, which determines whether
a user has certain access privileges once the user authenti-
cates. In other words, authorization controls what and when
an object or entity accesses a specific resource. Accounting
refers to logs of connected objects, including access data,
length of time of access, and modifications. For instance,
a smart grid meter might keep track of the amount of power
usage by each connected entity at home over time. The chal-
lenge of cybersecurity accounting services is that it tracks
and monitors in real-time, and provides auditing results.
In Fog-to-things computing, attack detection scheme needs
to be real-time as part of an accounting system. Breaches of
confidentiality occur when one or more of the safeguarding
mechanisms are not provided accordingly. These disclosures
might happen when credentials are stolen or cryptography is
broken.
The other important security goal in fog ecosystem is
integrity. It refers to the goal of cyber security which pro-
vides the accuracy, consistency, and trustworthiness of data.
Integrity controls ensure that information can be of high
quality. Integrity ensures that data should remain unaltered
during capture, storage, retrieval, update, and transfer by
unauthorized entities. Integrity protection controls used to
ensure data integrity could be divided into preventive and
detective methods. They include hashing, data validation
checks, data consistency checks, and access controls. Pro-
tecting data integrity is a major challenge as it depends on
how an organization uses data. It ranges from social media
and blog posts (low level) to e-commerce data (high level) to
healthcare and emergency (critical level).
The third equally important security principles is the avail-
ability of data. Availability ensures that systems and networks
are responsive, accessible, and meet expected standards.
Cyber attacks such as denial-of-service (DoS) [14]–[16]
attacks and device failures can prevent access to IoT devices,
which threatens the availability of services for a legitimate
purpose. Techniques used to enhance availability include
redundancy, backups, increased system resiliency, equipment
maintenance, and up-to-date OS and software. From cyberse-
curity point of view, prevention mechanism such as crypto
solutions, and monitoring unusual and suspicious network
and systems events as a mechanism of detection are crucial.
D. FOG NODES AS A PROTECTIVE SHIELD FOR IoTs
Distributed fog nodes are ideal architectural spots for
implementing and deploying security mechanisms. The
deployment of security mechanisms at fog nodes could be a
protective shield for IoT as this is a complete shift in premise
to traditional IT perimeter security [11]. Firstly, the stor-
age of security credentials is better protected than if it is
stored in the smart devices, and be more available and up-
to-date than if it is maintained in the cloud. This architecture
provides the distribution of security services for scalability,
and a mechanism for protecting resource constrained IoT
devices against sophisticated cyber-attacks. It is also apparent
that FC enables to identify attacks and suspicious behaviors
quickly as fog nodes are closer to the IoT devices than the
cloud. This a mechanism of providing real-time cybersecu-
rity breach incident response services for smart applications,
26822 VOLUME 6, 2018
FIGURE 2. McCumber cube [12].
C. SECURITY REQUIREMENTS
The important design aspects of robust cybersecurity schemes
stem from security goals, information states, and safeguards.
These three general dimensions known as Cybersecurity Sor-
cery Cube (McCumber Cube) were created by [12] as a
security framework for managing, evaluating and protecting
systems and networks. Fig.2 shows the McCumber Cube.
In this section, we focus on security goals.
The goals of cybersecurity known as the CIA triad are
identified on the first dimension of cybersecurity cube and
are widely used as a benchmark for evaluating and protect-
ing cybersecurity. These goals, consisting of confidentiality,
integrity, and availability [13] are the basic principles of
the cybersecurity protection, and are the requirements for
IoT security in the fog-to-things communications.
Confidentiality is the principle that prevents the dis-
closure of data or information to unauthorized users,
resources, or processes. This is a critical requirement for fog-
to-things interaction as the underlying wireless environment
is less protected than wired network. Mechanisms of ensuring
confidentiality, sometimes known as privacy, include cryp-
tographic methods such as data encryption, authentication,
and access control. Confidentiality guarantees privacy so that
only the intended data sink can read the data in transit. These
safeguarding methods are used for both data in transit and at
rest. Access control describes protection schemes that resist
unauthorized access to resources. Authentication, Authoriza-
tion, and Accounting are known as AAA security services,
providing the basic framework to control access. Whereas
authentication service is the method of verifying the iden-
tity of an entity to prevent unauthorized access, authoriza-
tion service determines which resources entities are entitled
to access and their operations. Authorization is accomplished
by using an access control list, which determines whether
a user has certain access privileges once the user authenti-
cates. In other words, authorization controls what and when
an object or entity accesses a specific resource. Accounting
refers to logs of connected objects, including access data,
length of time of access, and modifications. For instance,
a smart grid meter might keep track of the amount of power
usage by each connected entity at home over time. The chal-
lenge of cybersecurity accounting services is that it tracks
and monitors in real-time, and provides auditing results.
In Fog-to-things computing, attack detection scheme needs
to be real-time as part of an accounting system. Breaches of
confidentiality occur when one or more of the safeguarding
mechanisms are not provided accordingly. These disclosures
might happen when credentials are stolen or cryptography is
broken.
The other important security goal in fog ecosystem is
integrity. It refers to the goal of cyber security which pro-
vides the accuracy, consistency, and trustworthiness of data.
Integrity controls ensure that information can be of high
quality. Integrity ensures that data should remain unaltered
during capture, storage, retrieval, update, and transfer by
unauthorized entities. Integrity protection controls used to
ensure data integrity could be divided into preventive and
detective methods. They include hashing, data validation
checks, data consistency checks, and access controls. Pro-
tecting data integrity is a major challenge as it depends on
how an organization uses data. It ranges from social media
and blog posts (low level) to e-commerce data (high level) to
healthcare and emergency (critical level).
The third equally important security principles is the avail-
ability of data. Availability ensures that systems and networks
are responsive, accessible, and meet expected standards.
Cyber attacks such as denial-of-service (DoS) [14]–[16]
attacks and device failures can prevent access to IoT devices,
which threatens the availability of services for a legitimate
purpose. Techniques used to enhance availability include
redundancy, backups, increased system resiliency, equipment
maintenance, and up-to-date OS and software. From cyberse-
curity point of view, prevention mechanism such as crypto
solutions, and monitoring unusual and suspicious network
and systems events as a mechanism of detection are crucial.
D. FOG NODES AS A PROTECTIVE SHIELD FOR IoTs
Distributed fog nodes are ideal architectural spots for
implementing and deploying security mechanisms. The
deployment of security mechanisms at fog nodes could be a
protective shield for IoT as this is a complete shift in premise
to traditional IT perimeter security [11]. Firstly, the stor-
age of security credentials is better protected than if it is
stored in the smart devices, and be more available and up-
to-date than if it is maintained in the cloud. This architecture
provides the distribution of security services for scalability,
and a mechanism for protecting resource constrained IoT
devices against sophisticated cyber-attacks. It is also apparent
that FC enables to identify attacks and suspicious behaviors
quickly as fog nodes are closer to the IoT devices than the
cloud. This a mechanism of providing real-time cybersecu-
rity breach incident response services for smart applications,
26822 VOLUME 6, 2018
A. A. Diro et al.: Analysis of Lightweight Encryption Scheme for Fog-to-Things Communication
particularly for smart grids, critical industry functions, and
smart cities. Suppose that cybersecurity system for smart
grid and the connected car is provided by the cloud provider
and infected by malware which can completely block the
power generators in the grid or engines of the car. In both
cases, the complete shutdown of the systems is catastrophic
to delay. Furthermore, FC creates an environment of col-
laborative attack fighting in which IoT devices share attack
signatures and experiences For instance, artificial intelligence
based lightweight intrusion detection can be implemented on
collaborative Fog nodes in collaboration to detect suspicious
traffic. Moreover, as data communications are confined to
distributed edge networks, FC design protects eavesdropping
easier than core networks such as the cloud. Thus, the deploy-
ment of security services and functions at fog nodes for IoT
applications is an ideal solution.
E. SECURITY MECHANISMS
Cryptographic solutions have been playing major roles in
secreting Internet. The most widely used functions of cryp-
tography are authentication and encryption. As it is connected
to Internet, Fog-to-things computing inherits threats from
traditional Internet. The environment is also prone to zero-
day attacks as a result of newly introduced flaws in emerging
protocols, workflows and devices. Thus, cybersecurity mech-
anisms such as authentication, encryption and access con-
trol [16] need to be implemented in fog-to-things computing
using cryptographic elements.
Mutual authentication has been a fundamental cybersecu-
rity mechanism in securing traditional networks against both
internal and external attacks. This control is even more impor-
tant in fog-to-things computing as trust is utmost needed
in this ecosystem because of their large-scale communica-
tion. Reference [18] describes authentication as the core
layer of security framework in IoT/Fog computing in man-
aging strong identity, non-repudiation and building trust in
the ecosystem. By building trust, it is viable to combat
threats such as man-in-the-middle, impersonation, and replay
attacks, which are the most threatening attacks in IoT/fog
computing. Architectural wise, authentication architectures
such as 802.1AR/ IEEE 802.1X could be extended for fog
systems. However, authentication itself cannot guarantee the
delivery of data without eavesdropping or modification by
adversaries.
The transportation of data over an insecure channel such as
wireless should be guarded by encryption mechanisms. The
state of the art of encryption schemes is dependent on cryp-
tographic suites such as Advanced Encryption Suite (AES)
for confidential data transport, and Rivest-Shamir-Adleman
(RSA) for digital signatures. While the algorithms are robust
in fulfilling security requirements, they are not directly
suitable for resource-constrained IoT/Fog networks as they
require high resource usage. As resources are owned by
multi-parties and users, access control also plays a pivotal role
in the security of fog computing. Privacy has been always a
major concern of Internet, but more crucial for IoT because
FIGURE 3. Typical elliptic curves.
these devices host applications that trace the location and
behaviors of individuals. The good scenarios of privacy issues
are health care systems in which medical equipment are
tracked, and vital patient data are monitored. In this case,
the identity of the device should be known without revealing
the identity of the owner. As a combating mechanism, cryp-
tographic elements still play the major role in cybersecurity
of Internet and continues to be on the internet of things as
well for their robustness. Because of resource limitations of
IoT/Fog networks and evolving nature of cybersecurity, how-
ever, the traditional cryptographic mechanisms such as RSA
fail to support fog-to-things computing. Thus, investigating
lightweight cryptographic suites is of great importance.
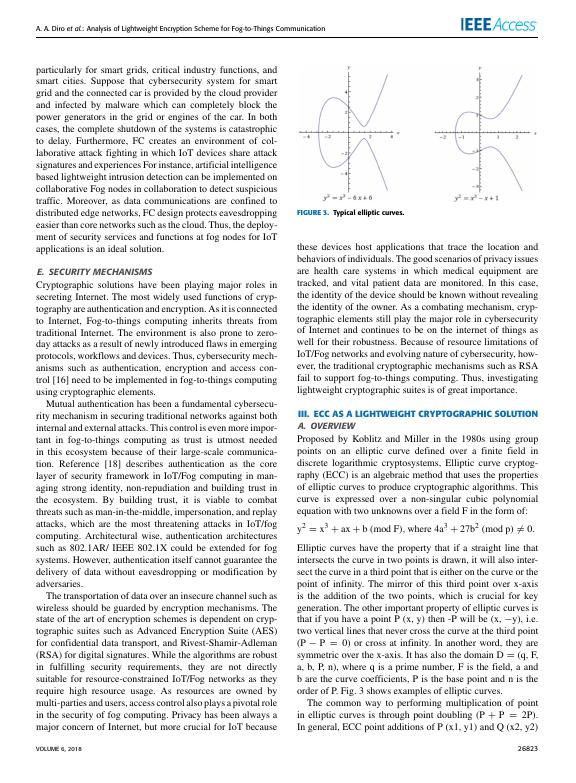
III. ECC AS A LIGHTWEIGHT CRYPTOGRAPHIC SOLUTION
A. OVERVIEW
Proposed by Koblitz and Miller in the 1980s using group
points on an elliptic curve defined over a finite field in
discrete logarithmic cryptosystems, Elliptic curve cryptog-
raphy (ECC) is an algebraic method that uses the properties
of elliptic curves to produce cryptographic algorithms. This
curve is expressed over a non-singular cubic polynomial
equation with two unknowns over a field F in the form of:
y2 = x3 + ax + b (mod F), where 4a3 + 27b2 (mod p) 6 = 0.
Elliptic curves have the property that if a straight line that
intersects the curve in two points is drawn, it will also inter-
sect the curve in a third point that is either on the curve or the
point of infinity. The mirror of this third point over x-axis
is the addition of the two points, which is crucial for key
generation. The other important property of elliptic curves is
that if you have a point P (x, y) then -P will be (x, −y), i.e.
two vertical lines that never cross the curve at the third point
(P − P = 0) or cross at infinity. In another word, they are
symmetric over the x-axis. It has also the domain D = (q, F,
a, b, P, n), where q is a prime number, F is the field, a and
b are the curve coefficients, P is the base point and n is the
order of P. Fig. 3 shows examples of elliptic curves.
The common way to performing multiplication of point
in elliptic curves is through point doubling (P + P = 2P).
In general, ECC point additions of P (x1, y1) and Q (x2, y2)
VOLUME 6, 2018 26823
particularly for smart grids, critical industry functions, and
smart cities. Suppose that cybersecurity system for smart
grid and the connected car is provided by the cloud provider
and infected by malware which can completely block the
power generators in the grid or engines of the car. In both
cases, the complete shutdown of the systems is catastrophic
to delay. Furthermore, FC creates an environment of col-
laborative attack fighting in which IoT devices share attack
signatures and experiences For instance, artificial intelligence
based lightweight intrusion detection can be implemented on
collaborative Fog nodes in collaboration to detect suspicious
traffic. Moreover, as data communications are confined to
distributed edge networks, FC design protects eavesdropping
easier than core networks such as the cloud. Thus, the deploy-
ment of security services and functions at fog nodes for IoT
applications is an ideal solution.
E. SECURITY MECHANISMS
Cryptographic solutions have been playing major roles in
secreting Internet. The most widely used functions of cryp-
tography are authentication and encryption. As it is connected
to Internet, Fog-to-things computing inherits threats from
traditional Internet. The environment is also prone to zero-
day attacks as a result of newly introduced flaws in emerging
protocols, workflows and devices. Thus, cybersecurity mech-
anisms such as authentication, encryption and access con-
trol [16] need to be implemented in fog-to-things computing
using cryptographic elements.
Mutual authentication has been a fundamental cybersecu-
rity mechanism in securing traditional networks against both
internal and external attacks. This control is even more impor-
tant in fog-to-things computing as trust is utmost needed
in this ecosystem because of their large-scale communica-
tion. Reference [18] describes authentication as the core
layer of security framework in IoT/Fog computing in man-
aging strong identity, non-repudiation and building trust in
the ecosystem. By building trust, it is viable to combat
threats such as man-in-the-middle, impersonation, and replay
attacks, which are the most threatening attacks in IoT/fog
computing. Architectural wise, authentication architectures
such as 802.1AR/ IEEE 802.1X could be extended for fog
systems. However, authentication itself cannot guarantee the
delivery of data without eavesdropping or modification by
adversaries.
The transportation of data over an insecure channel such as
wireless should be guarded by encryption mechanisms. The
state of the art of encryption schemes is dependent on cryp-
tographic suites such as Advanced Encryption Suite (AES)
for confidential data transport, and Rivest-Shamir-Adleman
(RSA) for digital signatures. While the algorithms are robust
in fulfilling security requirements, they are not directly
suitable for resource-constrained IoT/Fog networks as they
require high resource usage. As resources are owned by
multi-parties and users, access control also plays a pivotal role
in the security of fog computing. Privacy has been always a
major concern of Internet, but more crucial for IoT because
FIGURE 3. Typical elliptic curves.
these devices host applications that trace the location and
behaviors of individuals. The good scenarios of privacy issues
are health care systems in which medical equipment are
tracked, and vital patient data are monitored. In this case,
the identity of the device should be known without revealing
the identity of the owner. As a combating mechanism, cryp-
tographic elements still play the major role in cybersecurity
of Internet and continues to be on the internet of things as
well for their robustness. Because of resource limitations of
IoT/Fog networks and evolving nature of cybersecurity, how-
ever, the traditional cryptographic mechanisms such as RSA
fail to support fog-to-things computing. Thus, investigating
lightweight cryptographic suites is of great importance.
III. ECC AS A LIGHTWEIGHT CRYPTOGRAPHIC SOLUTION
A. OVERVIEW
Proposed by Koblitz and Miller in the 1980s using group
points on an elliptic curve defined over a finite field in
discrete logarithmic cryptosystems, Elliptic curve cryptog-
raphy (ECC) is an algebraic method that uses the properties
of elliptic curves to produce cryptographic algorithms. This
curve is expressed over a non-singular cubic polynomial
equation with two unknowns over a field F in the form of:
y2 = x3 + ax + b (mod F), where 4a3 + 27b2 (mod p) 6 = 0.
Elliptic curves have the property that if a straight line that
intersects the curve in two points is drawn, it will also inter-
sect the curve in a third point that is either on the curve or the
point of infinity. The mirror of this third point over x-axis
is the addition of the two points, which is crucial for key
generation. The other important property of elliptic curves is
that if you have a point P (x, y) then -P will be (x, −y), i.e.
two vertical lines that never cross the curve at the third point
(P − P = 0) or cross at infinity. In another word, they are
symmetric over the x-axis. It has also the domain D = (q, F,
a, b, P, n), where q is a prime number, F is the field, a and
b are the curve coefficients, P is the base point and n is the
order of P. Fig. 3 shows examples of elliptic curves.
The common way to performing multiplication of point
in elliptic curves is through point doubling (P + P = 2P).
In general, ECC point additions of P (x1, y1) and Q (x2, y2)
VOLUME 6, 2018 26823
End of preview
Want to access all the pages? Upload your documents or become a member.
Related Documents
Latest advances in encryption technologieslg...
|3
|568
|391
Analysis of Lightweight Encryption Scheme for Fog-to-Things Communication.lg...
|5
|1758
|429
Lightweight Encryption Algorithm for Secure IOTlg...
|53
|14901
|228
Securing MQTT Protocol for IoT Devices Research Paper 2022lg...
|3
|448
|1
Network and Securitylg...
|15
|3266
|22
Computer And Networks Security docx.lg...
|9
|1436
|26
