LINUX File System
VerifiedAdded on 2023/03/21
|23
|1749
|97
AI Summary
This document provides a step-by-step guide on configuring virtual machines, DNS & SSH server, web and database servers, remote file access, and simple web services in LINUX. It includes instructions for installing and configuring various components such as bind, Apache server, MySQL, PHP, and FTP. The document also provides references for further information.
Contribute Materials
Your contribution can guide someone’s learning journey. Share your
documents today.

Running head: LINUX File System
LINUX File System
Name of the Student:
Name of the University:
Author Note:
LINUX File System
Name of the Student:
Name of the University:
Author Note:
Secure Best Marks with AI Grader
Need help grading? Try our AI Grader for instant feedback on your assignments.

1LINUX File System
Table of Contents
Part 1: Virtual Machine One (Ubuntu) – DNS & SSH Server...................................................2
Part 2: Virtual Machine Two (Fedora) - Web and Database servers........................................5
Part 3: : Remote File Access......................................................................................................6
Part 4: Simple Web Services......................................................................................................8
References................................................................................................................................12
Table of Contents
Part 1: Virtual Machine One (Ubuntu) – DNS & SSH Server...................................................2
Part 2: Virtual Machine Two (Fedora) - Web and Database servers........................................5
Part 3: : Remote File Access......................................................................................................6
Part 4: Simple Web Services......................................................................................................8
References................................................................................................................................12

2LINUX File System
Part 1: Virtual Machine One (Ubuntu) – DNS & SSH Server
In this part, the first virtual machine is configured to use bind to configure it as a private DNS
virtual server. Here, first the Ubuntu server 18.04 is installed in the VMware virtual machine.
The ip address of the server is chosen by modifying the existing ip address of the VM by
seeing it via ifconfig command. The following steps are performed:
1. Bind is installed via: sudo apt-get install bind9 bind9utils bind9-doc
2. The next step is to configure the bind to set it in ipv4 mode by this command:
sudo nano /etc/default/bind9
And then add "-4" to the end of the OPTIONS parameter. The result is as follows:
OPTIONS="-u bind -4"
3. The next step is to restart bind to implement changes via
sudo systemctl restart bind9
Part 1: Virtual Machine One (Ubuntu) – DNS & SSH Server
In this part, the first virtual machine is configured to use bind to configure it as a private DNS
virtual server. Here, first the Ubuntu server 18.04 is installed in the VMware virtual machine.
The ip address of the server is chosen by modifying the existing ip address of the VM by
seeing it via ifconfig command. The following steps are performed:
1. Bind is installed via: sudo apt-get install bind9 bind9utils bind9-doc
2. The next step is to configure the bind to set it in ipv4 mode by this command:
sudo nano /etc/default/bind9
And then add "-4" to the end of the OPTIONS parameter. The result is as follows:
OPTIONS="-u bind -4"
3. The next step is to restart bind to implement changes via
sudo systemctl restart bind9

3LINUX File System
4. Now it’s time to configure the main DNS server that is VM1. Open the
named.conf.options file using: sudo nano /etc/bind/named.conf.options
5. Create a new ACL block and add the details about the primary IP address and the host
IP address.
6. After creating the ACL block, edit the options block below and add:
options {
directory "/var/cache/bind";
recursion yes; # enables resursive queries
allow-recursion { trusted; }; # allows recursive queries from "trusted"
clients
listen-on { ip address; }; # ns1 private IP address - listen on private
network only
allow-transfer { none; }; # disable zone transfers by default
forwarders {
8.8.8.8;
8.8.4.4;
};
Save the file and exit using CTRL + O and CTRL + X.
4. Now it’s time to configure the main DNS server that is VM1. Open the
named.conf.options file using: sudo nano /etc/bind/named.conf.options
5. Create a new ACL block and add the details about the primary IP address and the host
IP address.
6. After creating the ACL block, edit the options block below and add:
options {
directory "/var/cache/bind";
recursion yes; # enables resursive queries
allow-recursion { trusted; }; # allows recursive queries from "trusted"
clients
listen-on { ip address; }; # ns1 private IP address - listen on private
network only
allow-transfer { none; }; # disable zone transfers by default
forwarders {
8.8.8.8;
8.8.4.4;
};
Save the file and exit using CTRL + O and CTRL + X.
Secure Best Marks with AI Grader
Need help grading? Try our AI Grader for instant feedback on your assignments.

4LINUX File System
7. Next its time to configure the local file. Open named.conf.local file for edit using:
sudo nano /etc/bind/named.conf.local
Add the following lines in the file:
zone "shekhda.net.au" {
type master;
file "/etc/bind/zones/db.nyc3.example.com"; # zone file path
allow-transfer { ip address; }; # ns2 private IP address - secondary
};
Add these lines too:
zone "128.10.in-addr.arpa" {
type master;
file "/etc/bind/zones/db.10.128"; # 10.128.0.0/16 subnet //assumed
allow-transfer { ip address; }; # ns2 private IP address - secondary
};
7. Next its time to configure the local file. Open named.conf.local file for edit using:
sudo nano /etc/bind/named.conf.local
Add the following lines in the file:
zone "shekhda.net.au" {
type master;
file "/etc/bind/zones/db.nyc3.example.com"; # zone file path
allow-transfer { ip address; }; # ns2 private IP address - secondary
};
Add these lines too:
zone "128.10.in-addr.arpa" {
type master;
file "/etc/bind/zones/db.10.128"; # 10.128.0.0/16 subnet //assumed
allow-transfer { ip address; }; # ns2 private IP address - secondary
};

5LINUX File System
Save the file and exit.
8. Create the forward zone as shown below:
Create this directory by: sudo mkdir /etc/bind/zones
Copy the db file using this command:
sudo cp /etc/bind/db.local /etc/bind/zones/db. shekhda.net.au
Edit the file by opening it via:
sudo nano /etc/bind/zones/ db. shekhda.net.au
Make the necessary changes so that it looks like this:
$TTL 604800
@ IN SOA ns1. shekhda.net.au. admin. shekhda.net.au. (
3 ; Serial
604800 ; Refresh
86400 ; Retry
2419200 ; Expire
604800 ) ; Negative Cache TTL
;
; name servers - NS records
IN NS ns1.nyc3.example.com.
Save the file and exit.
8. Create the forward zone as shown below:
Create this directory by: sudo mkdir /etc/bind/zones
Copy the db file using this command:
sudo cp /etc/bind/db.local /etc/bind/zones/db. shekhda.net.au
Edit the file by opening it via:
sudo nano /etc/bind/zones/ db. shekhda.net.au
Make the necessary changes so that it looks like this:
$TTL 604800
@ IN SOA ns1. shekhda.net.au. admin. shekhda.net.au. (
3 ; Serial
604800 ; Refresh
86400 ; Retry
2419200 ; Expire
604800 ) ; Negative Cache TTL
;
; name servers - NS records
IN NS ns1.nyc3.example.com.

6LINUX File System
IN NS ns2.nyc3.example.com.
; name servers - A records
ns1. shekhda.net.au. IN A server ip address
; 10.128.0.0/16 - A records
host1. shekhda.net.au. IN A host ip address
9. Create the reverse zone file in the following way:
sudo cp /etc/bind/db.127 /etc/bind/zones/db.10.128
sudo nano /etc/bind/zones/db.10.128
Make the necessary changes until it looks like this:
$TTL 604800
@ IN SOA shekhda.net.au. admin. shekhda.net.au. (
3 ; Serial
604800 ; Refresh
86400 ; Retry
2419200 ; Expire
604800 ) ; Negative Cache TTL
; name servers
IN NS ns2.nyc3.example.com.
; name servers - A records
ns1. shekhda.net.au. IN A server ip address
; 10.128.0.0/16 - A records
host1. shekhda.net.au. IN A host ip address
9. Create the reverse zone file in the following way:
sudo cp /etc/bind/db.127 /etc/bind/zones/db.10.128
sudo nano /etc/bind/zones/db.10.128
Make the necessary changes until it looks like this:
$TTL 604800
@ IN SOA shekhda.net.au. admin. shekhda.net.au. (
3 ; Serial
604800 ; Refresh
86400 ; Retry
2419200 ; Expire
604800 ) ; Negative Cache TTL
; name servers
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

7LINUX File System
IN NS ns1. shekhda.net.au.
; PTR Records
11.10 IN PTR ns1. shekhda.net.au. ; server ip
101.100 IN PTR host1. shekhda.net.au. ; host ip
10. After saving and exiting all the files check for bind errors using:
sudo named-checkconf
Correct all the errors reported and run the command again.
Restart the bind server:
sudo systemctl restart bind9
Allow firewall access to bind DNS server using ufw:
sudo ufw allow Bind9
IN NS ns1. shekhda.net.au.
; PTR Records
11.10 IN PTR ns1. shekhda.net.au. ; server ip
101.100 IN PTR host1. shekhda.net.au. ; host ip
10. After saving and exiting all the files check for bind errors using:
sudo named-checkconf
Correct all the errors reported and run the command again.
Restart the bind server:
sudo systemctl restart bind9
Allow firewall access to bind DNS server using ufw:
sudo ufw allow Bind9

8LINUX File System
The DNS server has successfully been configured. Install ssh if it is not preinstalled.
Part 2: Virtual Machine Two (Fedora) - Web and Database servers
1. Install the Apache server, My SQL and PHP(preinstalled) using the following
commands:
For apache server:
sudo apt-get install apache2
The DNS server has successfully been configured. Install ssh if it is not preinstalled.
Part 2: Virtual Machine Two (Fedora) - Web and Database servers
1. Install the Apache server, My SQL and PHP(preinstalled) using the following
commands:
For apache server:
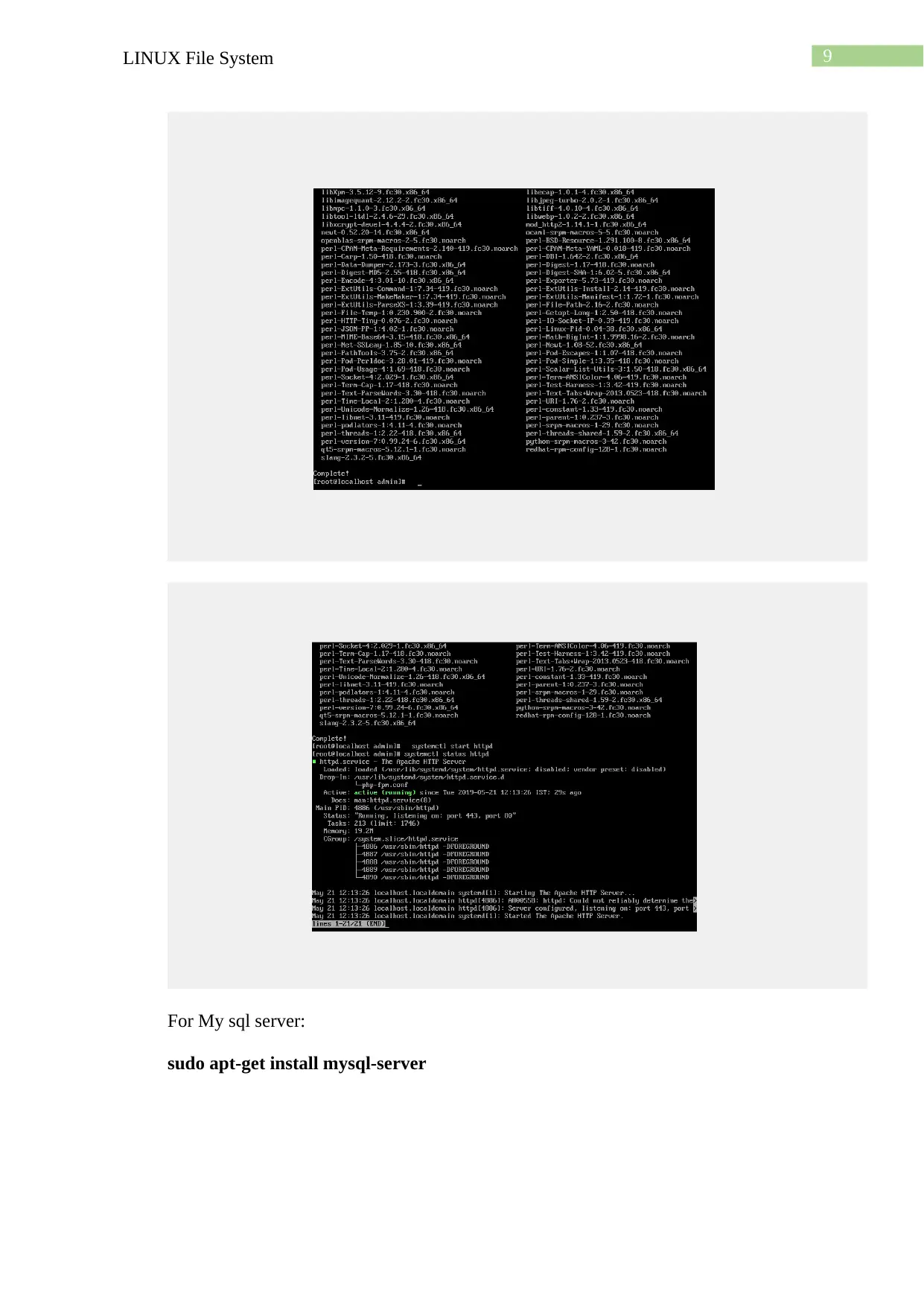
sudo apt-get install apache2
9LINUX File System
For My sql server:
sudo apt-get install mysql-server
For My sql server:
sudo apt-get install mysql-server
Secure Best Marks with AI Grader
Need help grading? Try our AI Grader for instant feedback on your assignments.

10LINUX File System
Start mysql server:
Start mysql server:

11LINUX File System
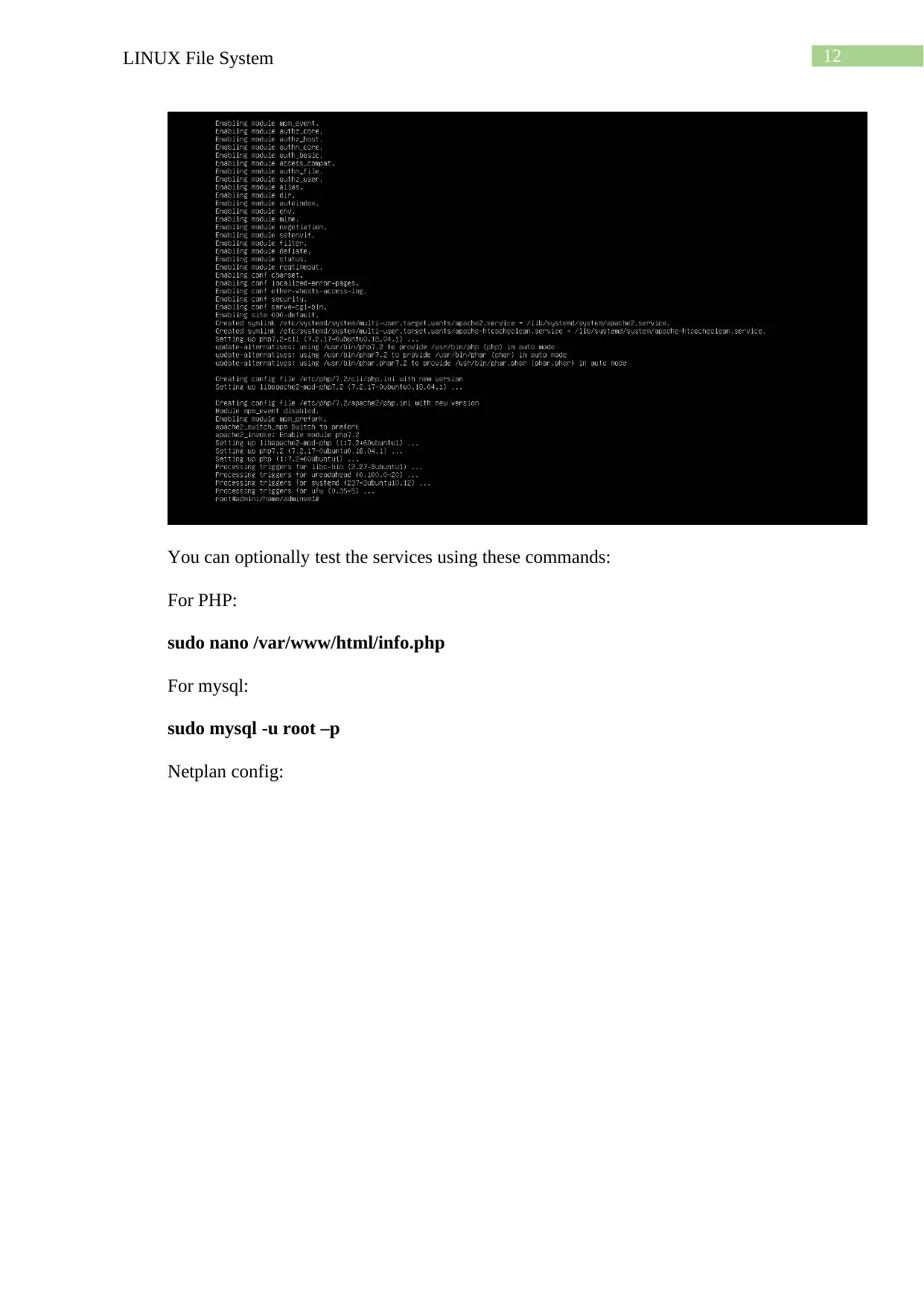
For php:
sudo apt-get install php libapache2-mod-php
For php:
sudo apt-get install php libapache2-mod-php
12LINUX File System
You can optionally test the services using these commands:
For PHP:
sudo nano /var/www/html/info.php
For mysql:
sudo mysql -u root –p
Netplan config:
You can optionally test the services using these commands:
For PHP:
sudo nano /var/www/html/info.php
For mysql:
sudo mysql -u root –p
Netplan config:
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

13LINUX File System
Reverse lookup host:
Reverse lookup host:

14LINUX File System
Check whether both the both the mysql and ssh are working for VM1 when connected
using the VM2 using the DNS created earlier.
Part 3: : Remote File Access
There are two ways to send files from one virtual machine to another. The first way is
the secure way and the second the unsecure.
The secure way is called sftp or secured file transfer protocol and the unsecure way is
ftp or normal file transfer protocol. The installation of ftp is compulsory for using
both the services.
The secure sftp way:
1. Install ssh first by:
sudo apt install ssh
Edit ssh config file:
sudo nano /etc/ssh/sshd_config
Add these to the end:
Match group sftp
Check whether both the both the mysql and ssh are working for VM1 when connected
using the VM2 using the DNS created earlier.
Part 3: : Remote File Access
There are two ways to send files from one virtual machine to another. The first way is
the secure way and the second the unsecure.
The secure way is called sftp or secured file transfer protocol and the unsecure way is
ftp or normal file transfer protocol. The installation of ftp is compulsory for using
both the services.
The secure sftp way:
1. Install ssh first by:
sudo apt install ssh
Edit ssh config file:
sudo nano /etc/ssh/sshd_config
Add these to the end:
Match group sftp

15LINUX File System
ChrootDirectory /home
X11Forwarding no
AllowTcpForwarding no
ForceCommand internal-sftp
Restart ssh server:
sudo service ssh restart
Now create sftp user account by:
sudo addgroup sftp
create new user:
udo useradd -m sftpuser -g sftp
set new password:
sudo passwd sftpuser
Enter new UNIX password:
Retype new UNIX password:
passwd: password updated successfully
change permissions for others:
sudo chmod 700 /home/sftpuser/
Now use this sftp like normal ftp should transfer files securely.
ChrootDirectory /home
X11Forwarding no
AllowTcpForwarding no
ForceCommand internal-sftp
Restart ssh server:
sudo service ssh restart
Now create sftp user account by:
sudo addgroup sftp
create new user:
udo useradd -m sftpuser -g sftp
set new password:
sudo passwd sftpuser
Enter new UNIX password:
Retype new UNIX password:
passwd: password updated successfully
change permissions for others:
sudo chmod 700 /home/sftpuser/
Now use this sftp like normal ftp should transfer files securely.
Secure Best Marks with AI Grader
Need help grading? Try our AI Grader for instant feedback on your assignments.

16LINUX File System
2. The unsecure way using pure ftp by:
Install ftp by:
sudo apt-get install vim
Second is to just install the plain ftp and start it:
sudo apt-get install pure-ftpd
2. The unsecure way using pure ftp by:
Install ftp by:
sudo apt-get install vim
Second is to just install the plain ftp and start it:
sudo apt-get install pure-ftpd

17LINUX File System
Run it as daemon:
echo "yes" > /etc/pure-ftpd/conf/Daemonize
Prohibit anonymous users:
echo "yes" > /etc/pure-ftpd/conf/NoAnonymous
Enable chroot:
echo "yes" > /etc/pure-ftpd/conf/ChrootEveryone
Configure it for only IPv4 system file transfers:
echo "yes" > /etc/pure-ftpd/conf/IPV4Only
Restart the server:
/etc/init.d/pure-ftpd restart
Now the user can send or receive files using this service with the normal syntax.
Part 4: Simple Web Services
This process is similar as part 1 and requires bind to be installed on the fedora VM.
The following command is used:
Run it as daemon:
echo "yes" > /etc/pure-ftpd/conf/Daemonize
Prohibit anonymous users:
echo "yes" > /etc/pure-ftpd/conf/NoAnonymous
Enable chroot:
echo "yes" > /etc/pure-ftpd/conf/ChrootEveryone
Configure it for only IPv4 system file transfers:
echo "yes" > /etc/pure-ftpd/conf/IPV4Only
Restart the server:
/etc/init.d/pure-ftpd restart
Now the user can send or receive files using this service with the normal syntax.
Part 4: Simple Web Services
This process is similar as part 1 and requires bind to be installed on the fedora VM.
The following command is used:

18LINUX File System
dnf -y install bind bind-utils
The next step is to config the bind server as per your IP address and already created
DNS. In this example replace the DNS with “shekdha.net.au” and server IP
127.0.116.80 and Host IP 127.0.115.151. Change the port to 8888. The following
commands are used:
vi /etc/named.conf
Change the file as follows:
options {
# change ( listen all )
listen-on port 8888 { any; };
# change( if not use IPv6 )
listen-on-v6 { none; };
directory "/var/named";
dump-file "/var/named/data/cache_dump.db";
statistics-file "/var/named/data/named_stats.txt";
memstatistics-file "/var/named/data/named_mem_stats.txt";
# query range ( set internal server and so on )
allow-query { localhost; 127.0.0.0/24; };
# transfer range ( set it if you have secondary DNS )
allow-transfer { localhost; 127.0.0.0/24; };
recursion yes;
dnssec-enable yes;
dnf -y install bind bind-utils
The next step is to config the bind server as per your IP address and already created
DNS. In this example replace the DNS with “shekdha.net.au” and server IP
127.0.116.80 and Host IP 127.0.115.151. Change the port to 8888. The following
commands are used:
vi /etc/named.conf
Change the file as follows:
options {
# change ( listen all )
listen-on port 8888 { any; };
# change( if not use IPv6 )
listen-on-v6 { none; };
directory "/var/named";
dump-file "/var/named/data/cache_dump.db";
statistics-file "/var/named/data/named_stats.txt";
memstatistics-file "/var/named/data/named_mem_stats.txt";
# query range ( set internal server and so on )
allow-query { localhost; 127.0.0.0/24; };
# transfer range ( set it if you have secondary DNS )
allow-transfer { localhost; 127.0.0.0/24; };
recursion yes;
dnssec-enable yes;
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

19LINUX File System
dnssec-validation yes;
bindkeys-file "/etc/named.iscdlv.key";
managed-keys-directory "/var/named/dynamic";
pid-file "/run/named/named.pid";
session-keyfile "/run/named/session.key";
/* https://fedoraproject.org/wiki/Changes/CryptoPolicy */
include "/etc/crypto-policies/back-ends/bind.config";
};
logging {
channel default_debug {
file "data/named.run";
severity dynamic;
};
};
# change all from here
view "internal" {
match-clients {
localhost;
127.0.0.0/24;
dnssec-validation yes;
bindkeys-file "/etc/named.iscdlv.key";
managed-keys-directory "/var/named/dynamic";
pid-file "/run/named/named.pid";
session-keyfile "/run/named/session.key";
/* https://fedoraproject.org/wiki/Changes/CryptoPolicy */
include "/etc/crypto-policies/back-ends/bind.config";
};
logging {
channel default_debug {
file "data/named.run";
severity dynamic;
};
};
# change all from here
view "internal" {
match-clients {
localhost;
127.0.0.0/24;

20LINUX File System
};
zone "." IN {
type hint;
file "named.ca";
};
zone " shekdha.net" IN {
type master;
file " shekdha.net.au ";
allow-update { none; };
};
zone "0.0.127.in-addr.arpa" IN {
type master;
file "0.0.127.db";
allow-update { none; };
};
include "/etc/named.rfc1912.zones";
include "/etc/named.root.key";
};
view "external" {
match-clients { any; };
allow-query { any; };
recursion no;
zone " shekdha.net" IN {
type master;
file " shekdha.net.au ";
};
zone "." IN {
type hint;
file "named.ca";
};
zone " shekdha.net" IN {
type master;
file " shekdha.net.au ";
allow-update { none; };
};
zone "0.0.127.in-addr.arpa" IN {
type master;
file "0.0.127.db";
allow-update { none; };
};
include "/etc/named.rfc1912.zones";
include "/etc/named.root.key";
};
view "external" {
match-clients { any; };
allow-query { any; };
recursion no;
zone " shekdha.net" IN {
type master;
file " shekdha.net.au ";

21LINUX File System
allow-update { none; };
};
zone "80.116.0.127.in-addr.arpa" IN {
type master;
file "80.116.0.127.db";
allow-update { none; };
};
};
Now the fedora sever is configured and you can access the website www.shekhda.net.au.
Thank you. The necessary firewall permission can be given using iptables for fedora.
allow-update { none; };
};
zone "80.116.0.127.in-addr.arpa" IN {
type master;
file "80.116.0.127.db";
allow-update { none; };
};
};
Now the fedora sever is configured and you can access the website www.shekhda.net.au.
Thank you. The necessary firewall permission can be given using iptables for fedora.
Secure Best Marks with AI Grader
Need help grading? Try our AI Grader for instant feedback on your assignments.

22LINUX File System
References
Fedora 27 : DNS Server : Install BIND : Server World. (2019). Retrieved from
https://www.server-world.info/en/note?os=Fedora_27&p=dns&f=1
How To Configure BIND as a Private Network DNS Server on Ubuntu 18.04 | DigitalOcean.
(2019). Retrieved from https://www.digitalocean.com/community/tutorials/how-to-
configure-bind-as-a-private-network-dns-server-on-ubuntu-18-04
References
Fedora 27 : DNS Server : Install BIND : Server World. (2019). Retrieved from
https://www.server-world.info/en/note?os=Fedora_27&p=dns&f=1
How To Configure BIND as a Private Network DNS Server on Ubuntu 18.04 | DigitalOcean.
(2019). Retrieved from https://www.digitalocean.com/community/tutorials/how-to-
configure-bind-as-a-private-network-dns-server-on-ubuntu-18-04
1 out of 23
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
© 2024 | Zucol Services PVT LTD | All rights reserved.





