Analysis of Linux OS Security: Architecture, Attributes, and Steps
VerifiedAdded on 2023/01/17
|27
|1747
|30
Report
AI Summary
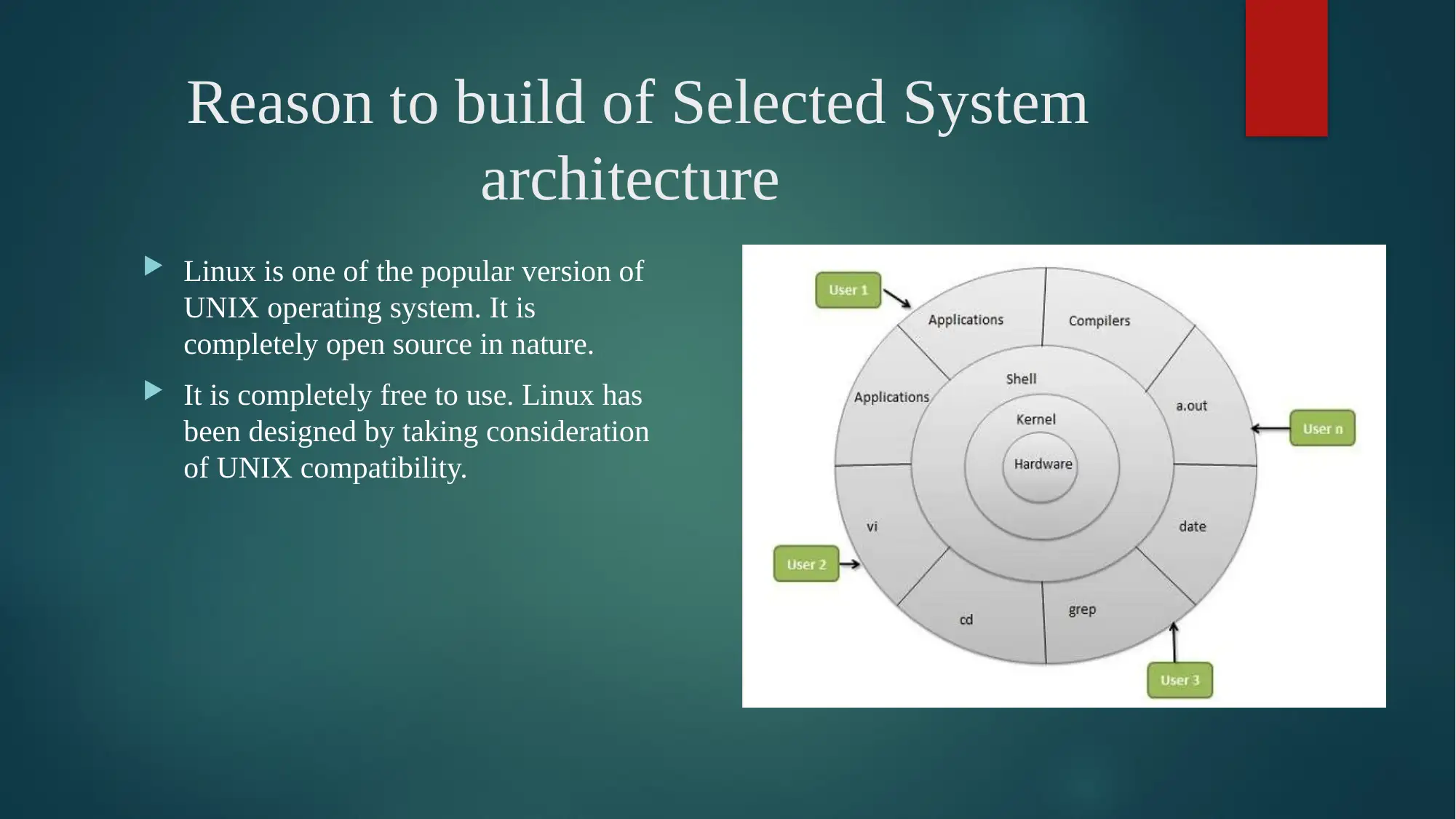
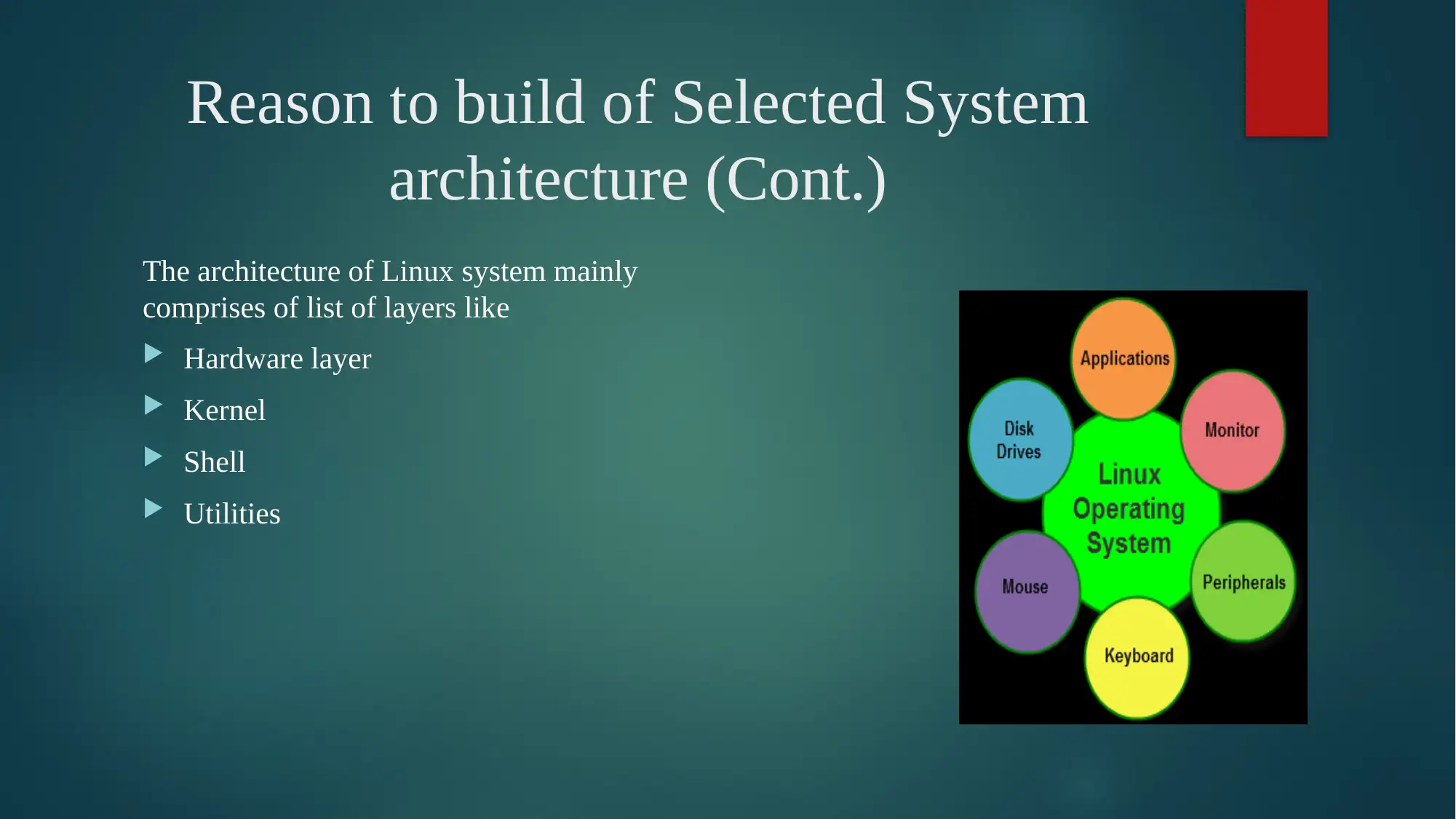
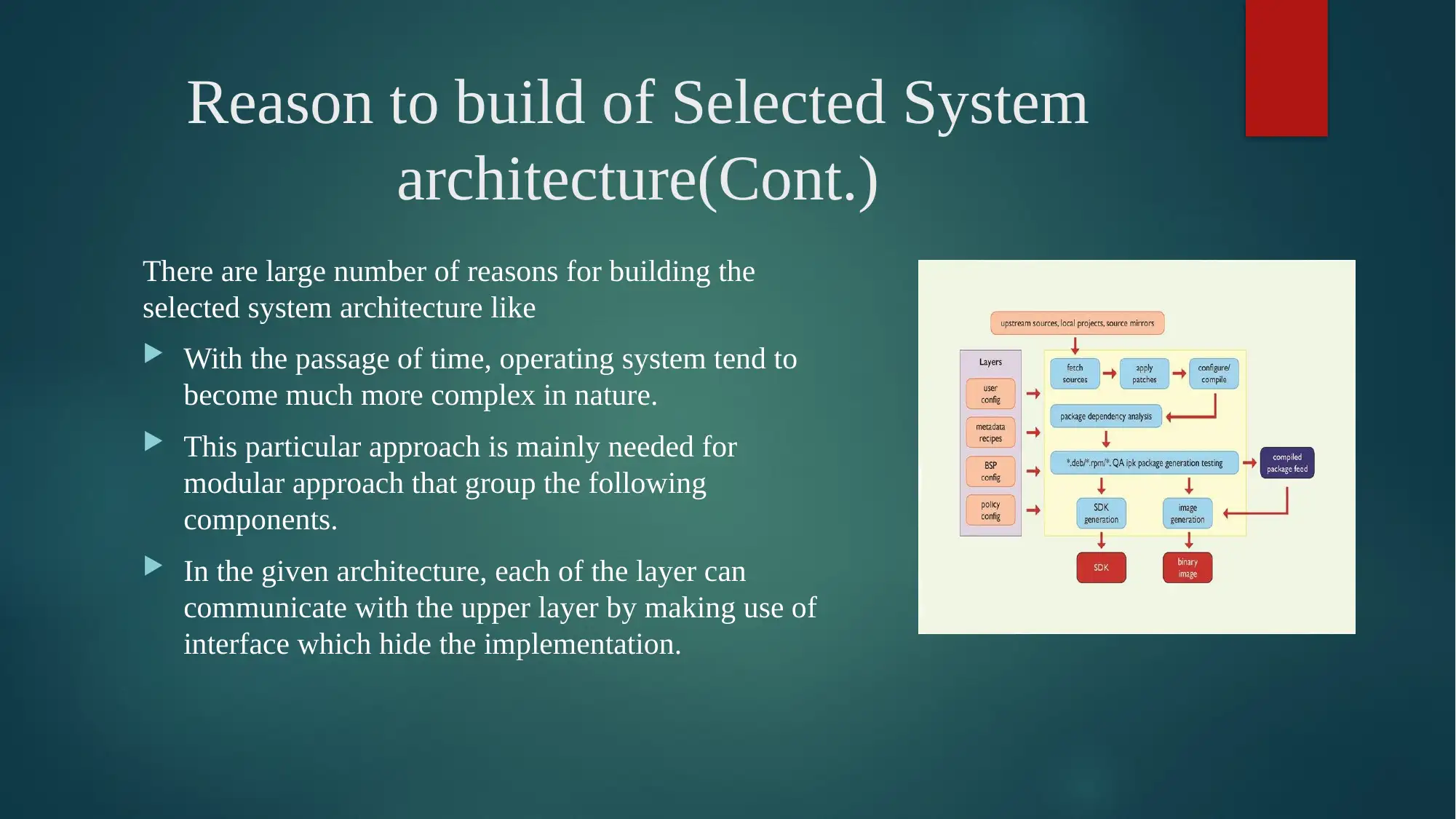
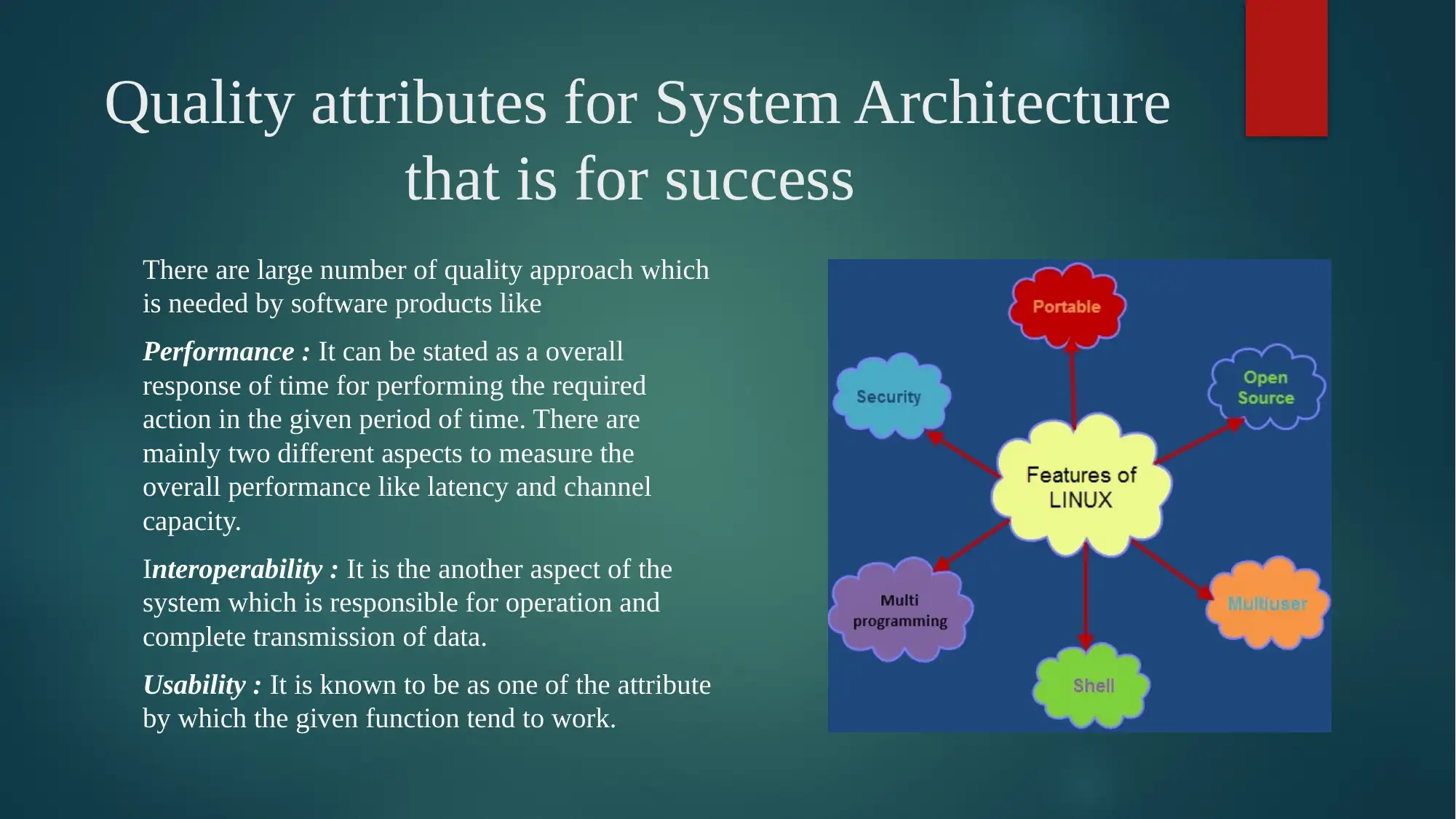
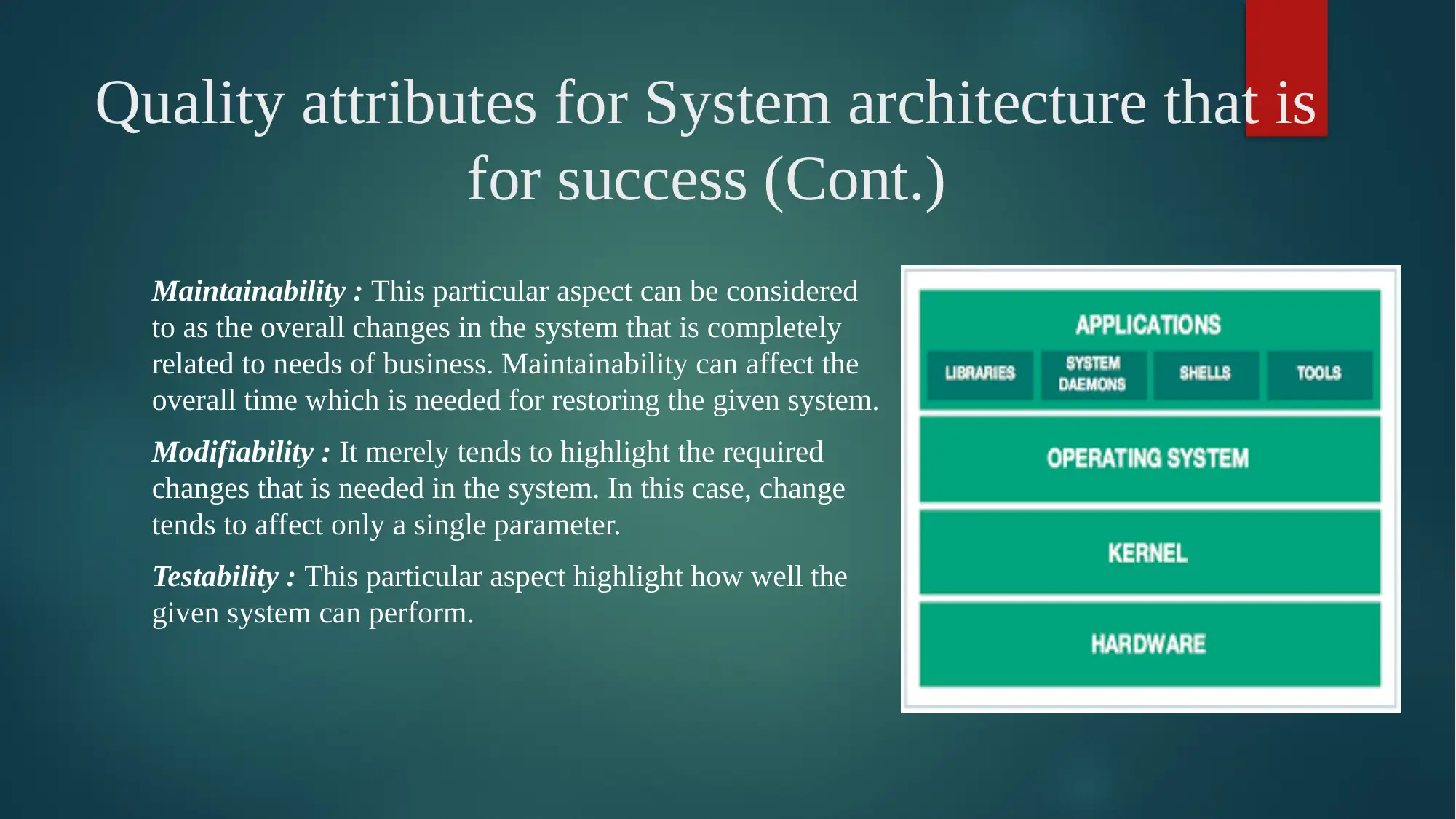
This report provides a detailed analysis of Linux OS security, starting with an introduction to the operating system and its core components. It delves into the analysis of Linux-based OS security, discussing the kernel, user manners, types of processes, device drivers, memory management, and networking. The report explores the reasons behind building the selected system architecture, emphasizing the modular approach and the layers involved, including hardware, kernel, shell, and utilities. It then identifies and discusses the quality attributes crucial for system success, such as performance, interoperability, usability, reliability, availability, security, maintainability, modifiability, and testability. The report further examines the effect of architecture and quality on the overall success of the system, explaining how architectural decisions impact the quality and performance of the Linux OS. It outlines steps taken to improve quality attributes, including design, run-time, and system qualities, along with design plans. The report also considers the quality attributes that are affected, trade-offs made, and implications of the Linux OS, along with a comparison with other systems like Windows. The conclusion summarizes the key aspects of Linux OS security and highlights the references used.
1 out of 27









![[object Object]](/_next/static/media/star-bottom.7253800d.svg)