LAN Setup for People Software in Sydney
VerifiedAdded on 2023/04/26
|10
|1763
|233
AI Summary
This document provides an in-depth understanding of the network and network layout for People Software in Sydney. It includes the requirements, proposed servers and their services, and configurations for the LAN setup.
Contribute Materials
Your contribution can guide someone’s learning journey. Share your
documents today.

SCENARIO 1: Local Area Network (LAN) to support Windows Server and Client
Environment
People Software is a software development company requiring the setting up of a LAN for
their office located in Sydney. They have four departments: Developers, Marketing,
Operations, and Finance. All objects (e.g., users, computers, etc.) belonging to these
departments need to be created within their respective OU for their own department.
As a group, we choose to work for People Software as the team dealing with the network
implementation we plan to handle the following issues:
i) Analysing the requirements of the clients
ii) Identifying and proposing necessary severs and their services
iii) Providing the needed configurations for this scenario.
This task analyses various issues expected by clients such as how many personal computers
and what type of configurations are needed by a client, the number of servers with their
configurations required, analyse whether database will be required or not and if there is any
need for the web server to be hosted or not. All these will be dealt with in this first objective
according to a client’s desire.
The next part we will deal with the getting and proposing the best server configuration that
will be required at the end of the analysis. This will be done by configuring the proposed
server with an internet protocol since the specification given was that the following services
of the local area network are required by the People Software:
1) To centralise the authentication of the user
2) To print the server for its users
3) Ensure computers automatically obtain internet protocol’s address from the server
4) Use their own server to host their own website
5) Enable the company store their files separately on a different server such that only
appropriate users can access them. An assumption on the group to have an access to
the server will be clearly stated.
On the final part, we will give the required virtual configurations as per the specifications of
the company stated above and then later make a complete report with defined conclusions
which will be a summary of the whole report stating references as well.
Analysis of the Requirements:
This involves the requirements given by People Software specifying their expectations on
what services the local area network (LAN) should offer to the four departments. They
include;
1) To centralise the authentication of the user
2) To print the server for its users
3) Ensure computers automatically obtain internet protocol’s address from the server
4) Use their own server to host their own website
5) Enable the company store their files separately on a different server such that only
appropriate users can access them. An assumption on the group to have an access to
the server will be clearly stated.
Environment
People Software is a software development company requiring the setting up of a LAN for
their office located in Sydney. They have four departments: Developers, Marketing,
Operations, and Finance. All objects (e.g., users, computers, etc.) belonging to these
departments need to be created within their respective OU for their own department.
As a group, we choose to work for People Software as the team dealing with the network
implementation we plan to handle the following issues:
i) Analysing the requirements of the clients
ii) Identifying and proposing necessary severs and their services
iii) Providing the needed configurations for this scenario.
This task analyses various issues expected by clients such as how many personal computers
and what type of configurations are needed by a client, the number of servers with their
configurations required, analyse whether database will be required or not and if there is any
need for the web server to be hosted or not. All these will be dealt with in this first objective
according to a client’s desire.
The next part we will deal with the getting and proposing the best server configuration that
will be required at the end of the analysis. This will be done by configuring the proposed
server with an internet protocol since the specification given was that the following services
of the local area network are required by the People Software:
1) To centralise the authentication of the user
2) To print the server for its users
3) Ensure computers automatically obtain internet protocol’s address from the server
4) Use their own server to host their own website
5) Enable the company store their files separately on a different server such that only
appropriate users can access them. An assumption on the group to have an access to
the server will be clearly stated.
On the final part, we will give the required virtual configurations as per the specifications of
the company stated above and then later make a complete report with defined conclusions
which will be a summary of the whole report stating references as well.
Analysis of the Requirements:
This involves the requirements given by People Software specifying their expectations on
what services the local area network (LAN) should offer to the four departments. They
include;
1) To centralise the authentication of the user
2) To print the server for its users
3) Ensure computers automatically obtain internet protocol’s address from the server
4) Use their own server to host their own website
5) Enable the company store their files separately on a different server such that only
appropriate users can access them. An assumption on the group to have an access to
the server will be clearly stated.
Secure Best Marks with AI Grader
Need help grading? Try our AI Grader for instant feedback on your assignments.
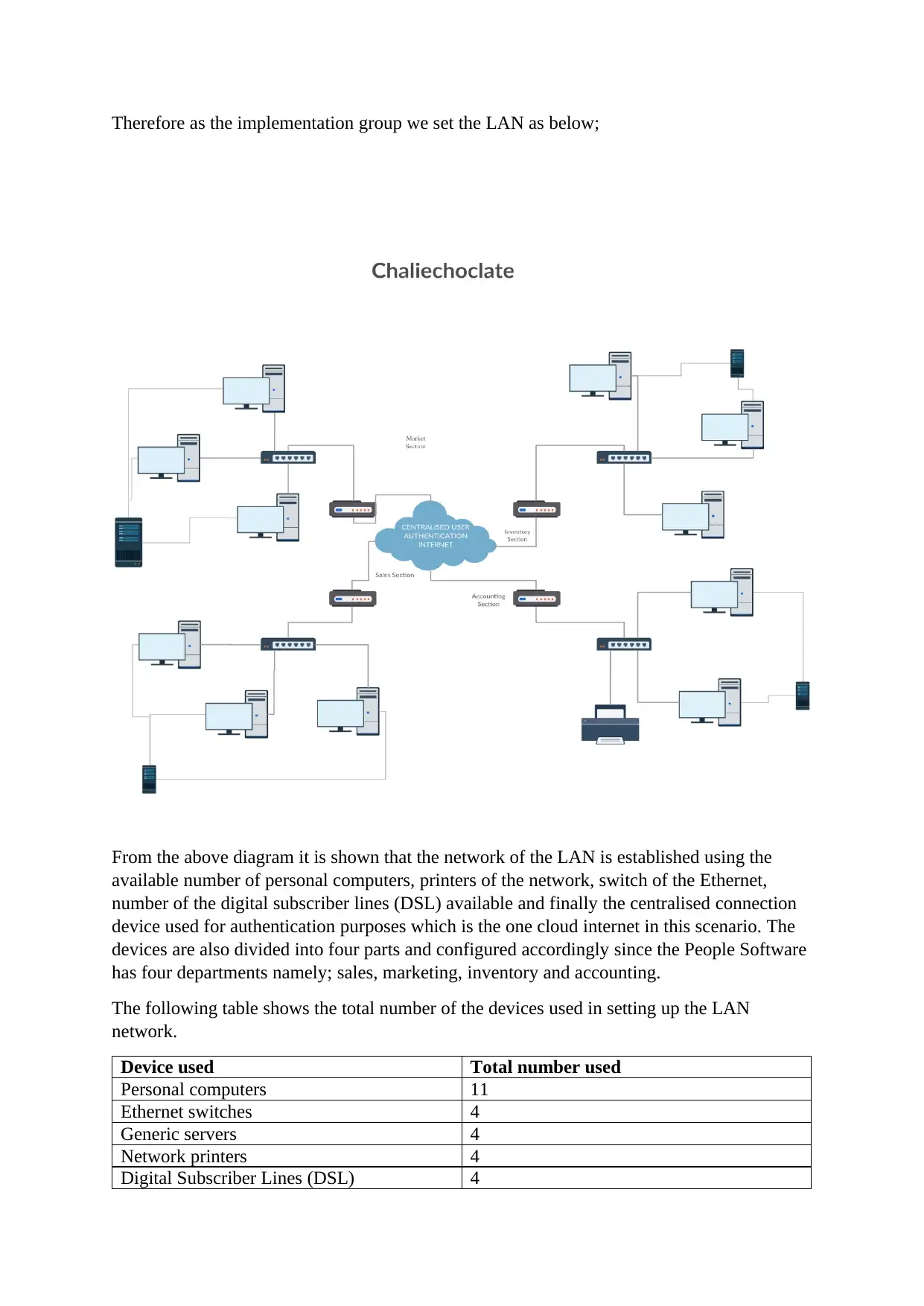
Therefore as the implementation group we set the LAN as below;
From the above diagram it is shown that the network of the LAN is established using the
available number of personal computers, printers of the network, switch of the Ethernet,
number of the digital subscriber lines (DSL) available and finally the centralised connection
device used for authentication purposes which is the one cloud internet in this scenario. The
devices are also divided into four parts and configured accordingly since the People Software
has four departments namely; sales, marketing, inventory and accounting.
The following table shows the total number of the devices used in setting up the LAN
network.
Device used Total number used
Personal computers 11
Ethernet switches 4
Generic servers 4
Network printers 4
Digital Subscriber Lines (DSL) 4
From the above diagram it is shown that the network of the LAN is established using the
available number of personal computers, printers of the network, switch of the Ethernet,
number of the digital subscriber lines (DSL) available and finally the centralised connection
device used for authentication purposes which is the one cloud internet in this scenario. The
devices are also divided into four parts and configured accordingly since the People Software
has four departments namely; sales, marketing, inventory and accounting.
The following table shows the total number of the devices used in setting up the LAN
network.
Device used Total number used
Personal computers 11
Ethernet switches 4
Generic servers 4
Network printers 4
Digital Subscriber Lines (DSL) 4
Cloud database 1
Centralised and authenticated server 1
The basic functions of these devices are as stated below;
Digital Subscriber Line (DSL) – this is used to define a series communications services with
high speed provided over (PSTN), that is Public Switched Telephone Network.
Wires – they are used to connect devices with each other and also available systems to the
personal computers.
Cloud database – used for storage of the majority data used in the personal computers. Just as
in this setup there is only one database for storing all the data of the network.
Personal computer – used for working on the network. It can be used for official or personal
works depending with the user.
Ethernet switch –from the physical concept, Ethernet originates from the word ether which is
defined as a channel where light waves travel through unrestricted universe. Hence its use is
to connect a computer or more to the internet through a wireless devices, internet router or
even an asymmetric digital subscriber line modem. In our network, when you connect a
single computer to the internet, you are not compelled to use earth net at all. It is derived
from the physical concept of the medium which was at some points support to pass the light
wave into a free space. There exist four Ethernet switches that help in the provision of
connection of various networks through the use of a single authentication server.
Configuration process
Centralised and authenticated server 1
The basic functions of these devices are as stated below;
Digital Subscriber Line (DSL) – this is used to define a series communications services with
high speed provided over (PSTN), that is Public Switched Telephone Network.
Wires – they are used to connect devices with each other and also available systems to the
personal computers.
Cloud database – used for storage of the majority data used in the personal computers. Just as
in this setup there is only one database for storing all the data of the network.
Personal computer – used for working on the network. It can be used for official or personal
works depending with the user.
Ethernet switch –from the physical concept, Ethernet originates from the word ether which is
defined as a channel where light waves travel through unrestricted universe. Hence its use is
to connect a computer or more to the internet through a wireless devices, internet router or
even an asymmetric digital subscriber line modem. In our network, when you connect a
single computer to the internet, you are not compelled to use earth net at all. It is derived
from the physical concept of the medium which was at some points support to pass the light
wave into a free space. There exist four Ethernet switches that help in the provision of
connection of various networks through the use of a single authentication server.
Configuration process
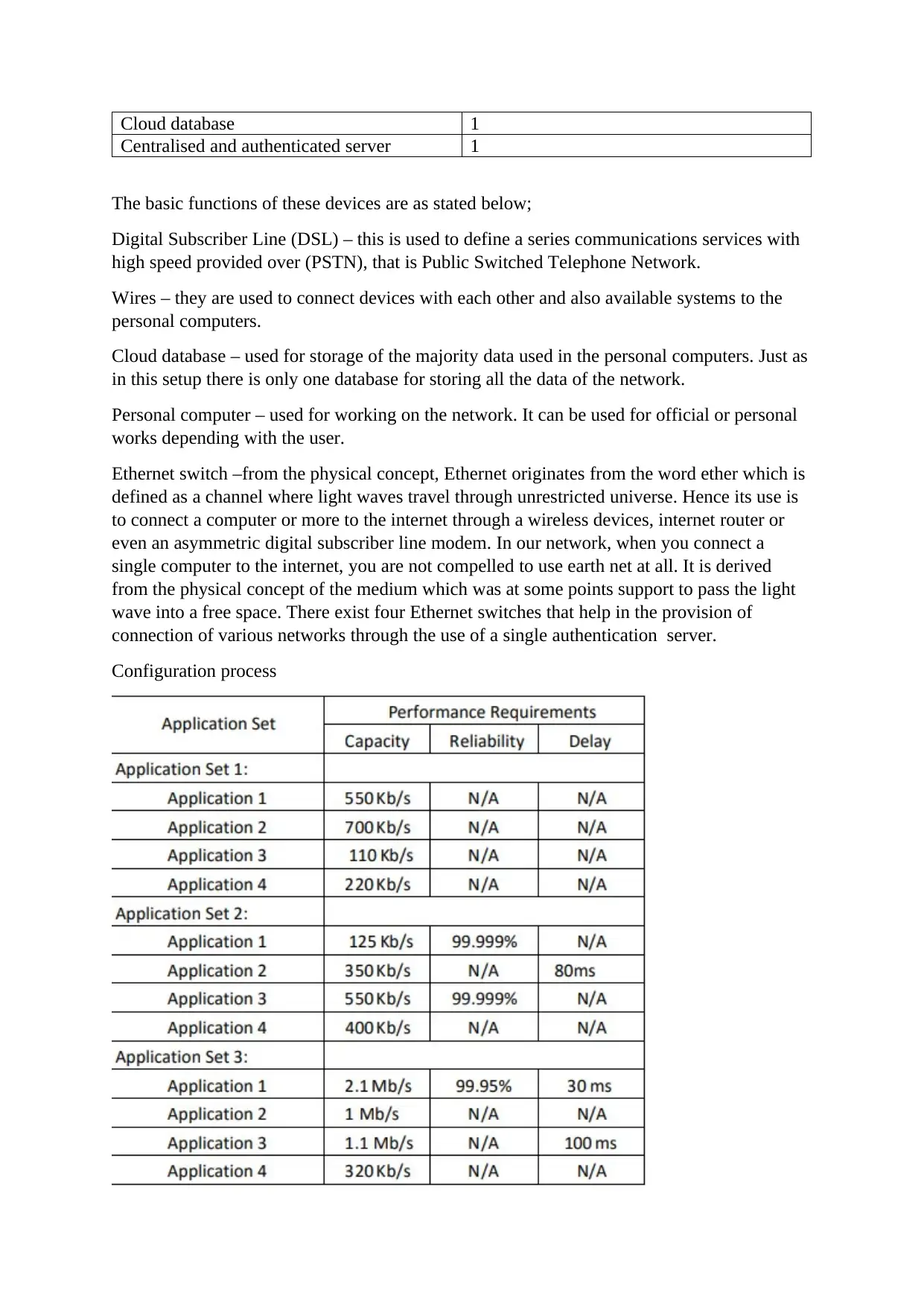
The configuration process is as shown below;
Router configuration- gives a specification of the best IP address together with the router
setting.
Host configuration- this is a combination of network connection in the computer the host uses
through logging into the default network setting like the IP addressing proxy name of the
network and the ID password which allows the network connection as well as
communication.
Software configuration- Any software that is dependent on the network like the intrusion
detection system (IDS) which gives the provision for the access and also provides appropriate
credential that helps in the monitor of network traffic.
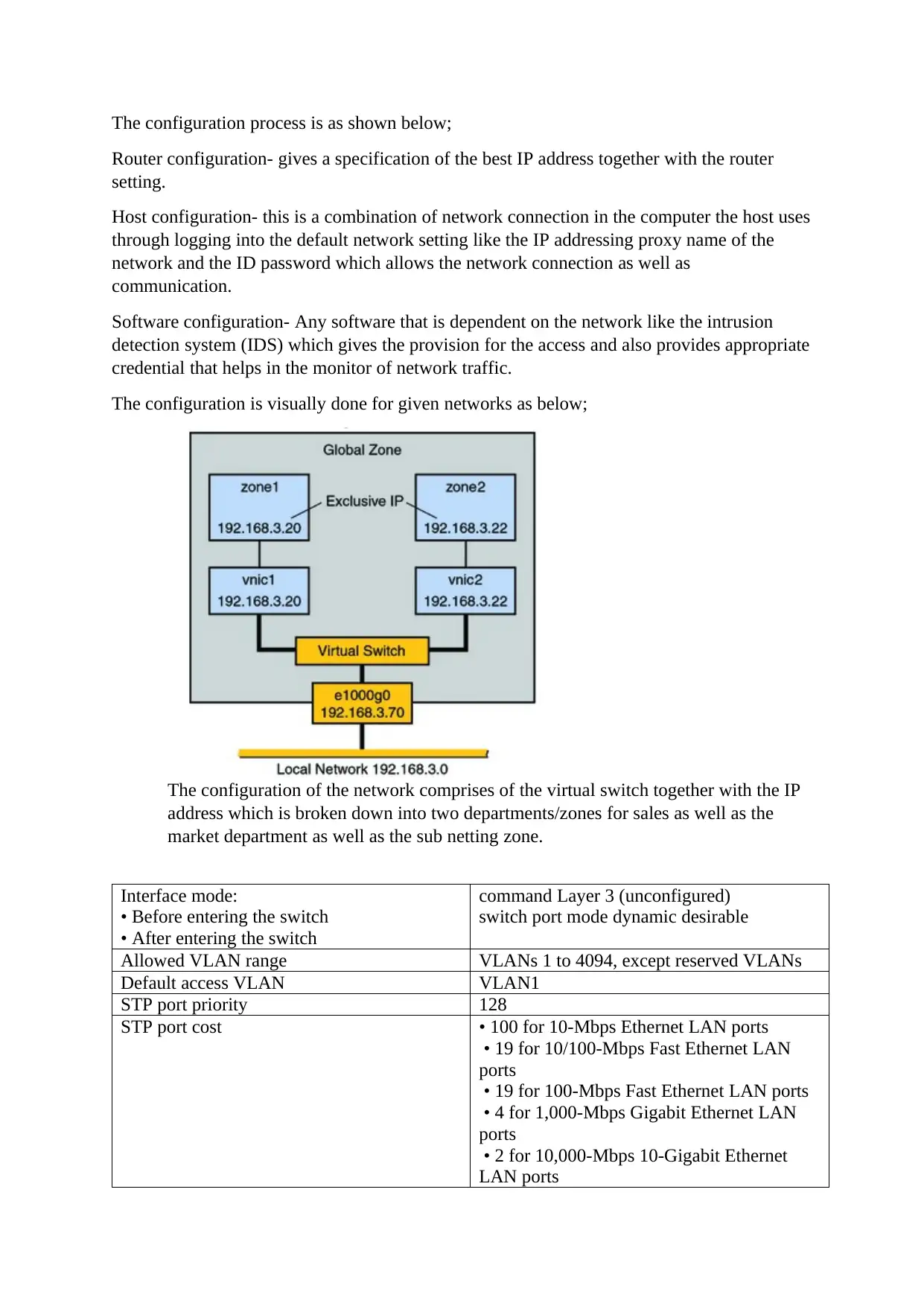
The configuration is visually done for given networks as below;
The configuration of the network comprises of the virtual switch together with the IP
address which is broken down into two departments/zones for sales as well as the
market department as well as the sub netting zone.
Interface mode:
• Before entering the switch
• After entering the switch
command Layer 3 (unconfigured)
switch port mode dynamic desirable
Allowed VLAN range VLANs 1 to 4094, except reserved VLANs
Default access VLAN VLAN1
STP port priority 128
STP port cost • 100 for 10-Mbps Ethernet LAN ports
• 19 for 10/100-Mbps Fast Ethernet LAN
ports
• 19 for 100-Mbps Fast Ethernet LAN ports
• 4 for 1,000-Mbps Gigabit Ethernet LAN
ports
• 2 for 10,000-Mbps 10-Gigabit Ethernet
LAN ports
Router configuration- gives a specification of the best IP address together with the router
setting.
Host configuration- this is a combination of network connection in the computer the host uses
through logging into the default network setting like the IP addressing proxy name of the
network and the ID password which allows the network connection as well as
communication.
Software configuration- Any software that is dependent on the network like the intrusion
detection system (IDS) which gives the provision for the access and also provides appropriate
credential that helps in the monitor of network traffic.
The configuration is visually done for given networks as below;
The configuration of the network comprises of the virtual switch together with the IP
address which is broken down into two departments/zones for sales as well as the
market department as well as the sub netting zone.
Interface mode:
• Before entering the switch
• After entering the switch
command Layer 3 (unconfigured)
switch port mode dynamic desirable
Allowed VLAN range VLANs 1 to 4094, except reserved VLANs
Default access VLAN VLAN1
STP port priority 128
STP port cost • 100 for 10-Mbps Ethernet LAN ports
• 19 for 10/100-Mbps Fast Ethernet LAN
ports
• 19 for 100-Mbps Fast Ethernet LAN ports
• 4 for 1,000-Mbps Gigabit Ethernet LAN
ports
• 2 for 10,000-Mbps 10-Gigabit Ethernet
LAN ports
Secure Best Marks with AI Grader
Need help grading? Try our AI Grader for instant feedback on your assignments.
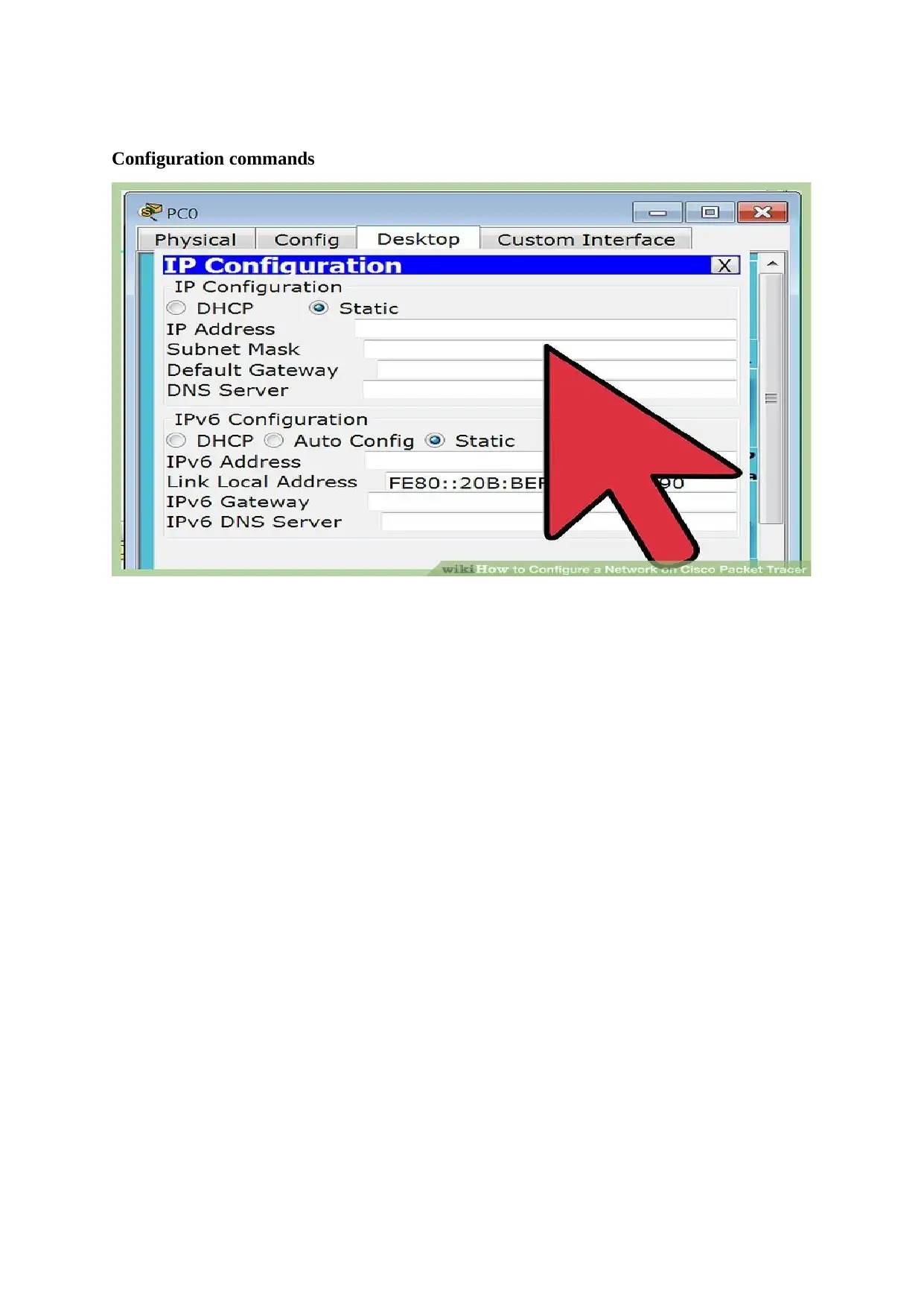
Configuration commands

The computer being connected will have the revision to determine the requite network
hardware. In case the connection is for less computers then only a single router will be
required or a single switch if internet is not required.
In case the number of computers being connected exceeds four them the then both the
router and a switch are required.
In a scenario where a permanent LAN solution is required then the length of the cable
must be kept in mind. CAT5 Ethernet cables should not be longer than 250 feet an if a
longer distance is to be covered, then there must be switches placed at regular intervals or
maybe the use of CAT6 may be required.
The Ethernet cable is a requirement for any computer that is to be connected to the LAN
and others to connect to the router to switch.
Creating LAN requires a router and network where the pieces of the hardware are the
‘hub’ or the LAN and must be connected to all the computers.
Switches resemble routers although they do not have an automatic capability to assign the
IP address. Ideally, switches automatically have the excess Ethernet ports compared to the
router.
hardware. In case the connection is for less computers then only a single router will be
required or a single switch if internet is not required.
In case the number of computers being connected exceeds four them the then both the
router and a switch are required.
In a scenario where a permanent LAN solution is required then the length of the cable
must be kept in mind. CAT5 Ethernet cables should not be longer than 250 feet an if a
longer distance is to be covered, then there must be switches placed at regular intervals or
maybe the use of CAT6 may be required.
The Ethernet cable is a requirement for any computer that is to be connected to the LAN
and others to connect to the router to switch.
Creating LAN requires a router and network where the pieces of the hardware are the
‘hub’ or the LAN and must be connected to all the computers.
Switches resemble routers although they do not have an automatic capability to assign the
IP address. Ideally, switches automatically have the excess Ethernet ports compared to the
router.
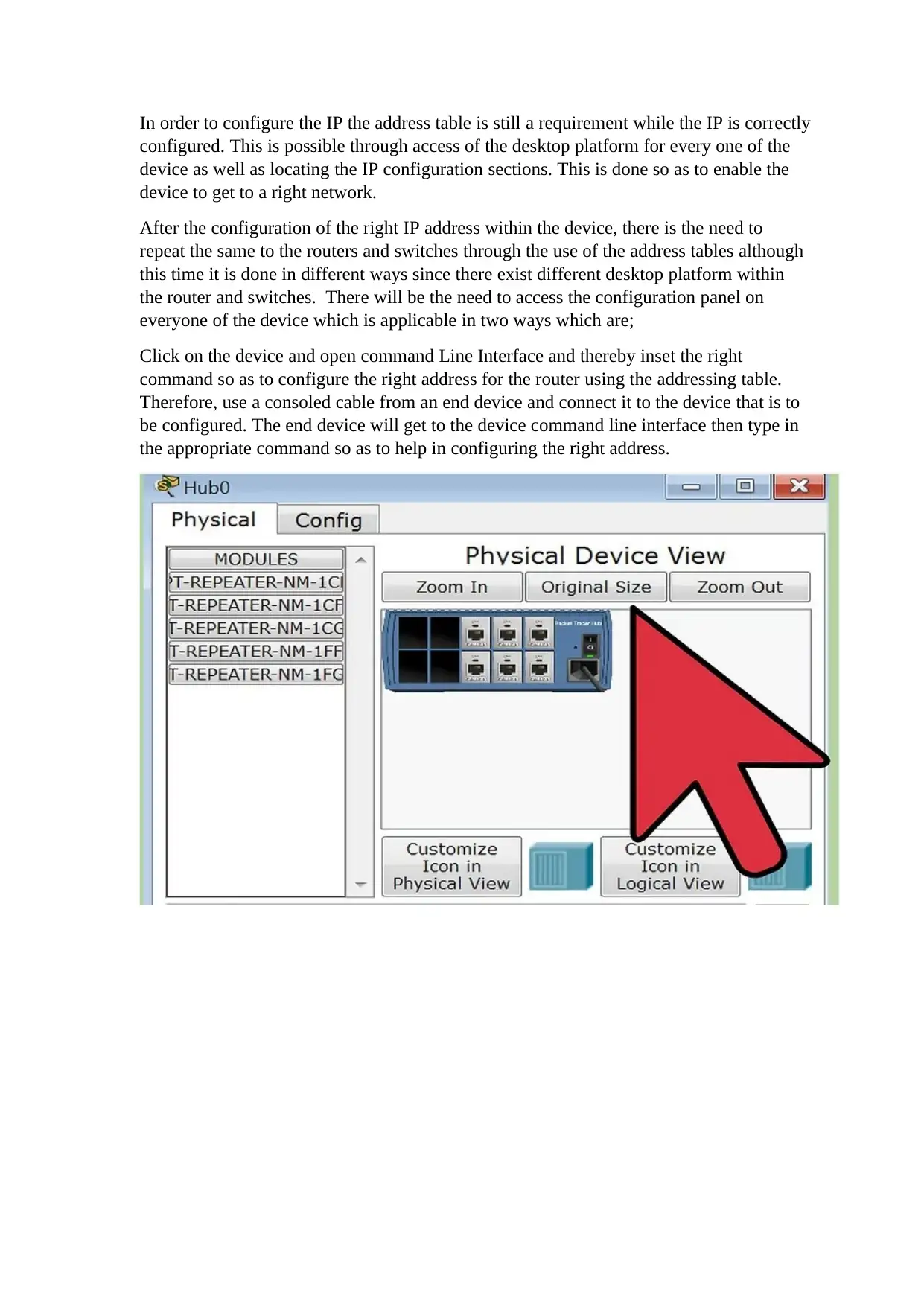
In order to configure the IP the address table is still a requirement while the IP is correctly
configured. This is possible through access of the desktop platform for every one of the
device as well as locating the IP configuration sections. This is done so as to enable the
device to get to a right network.
After the configuration of the right IP address within the device, there is the need to
repeat the same to the routers and switches through the use of the address tables although
this time it is done in different ways since there exist different desktop platform within
the router and switches. There will be the need to access the configuration panel on
everyone of the device which is applicable in two ways which are;
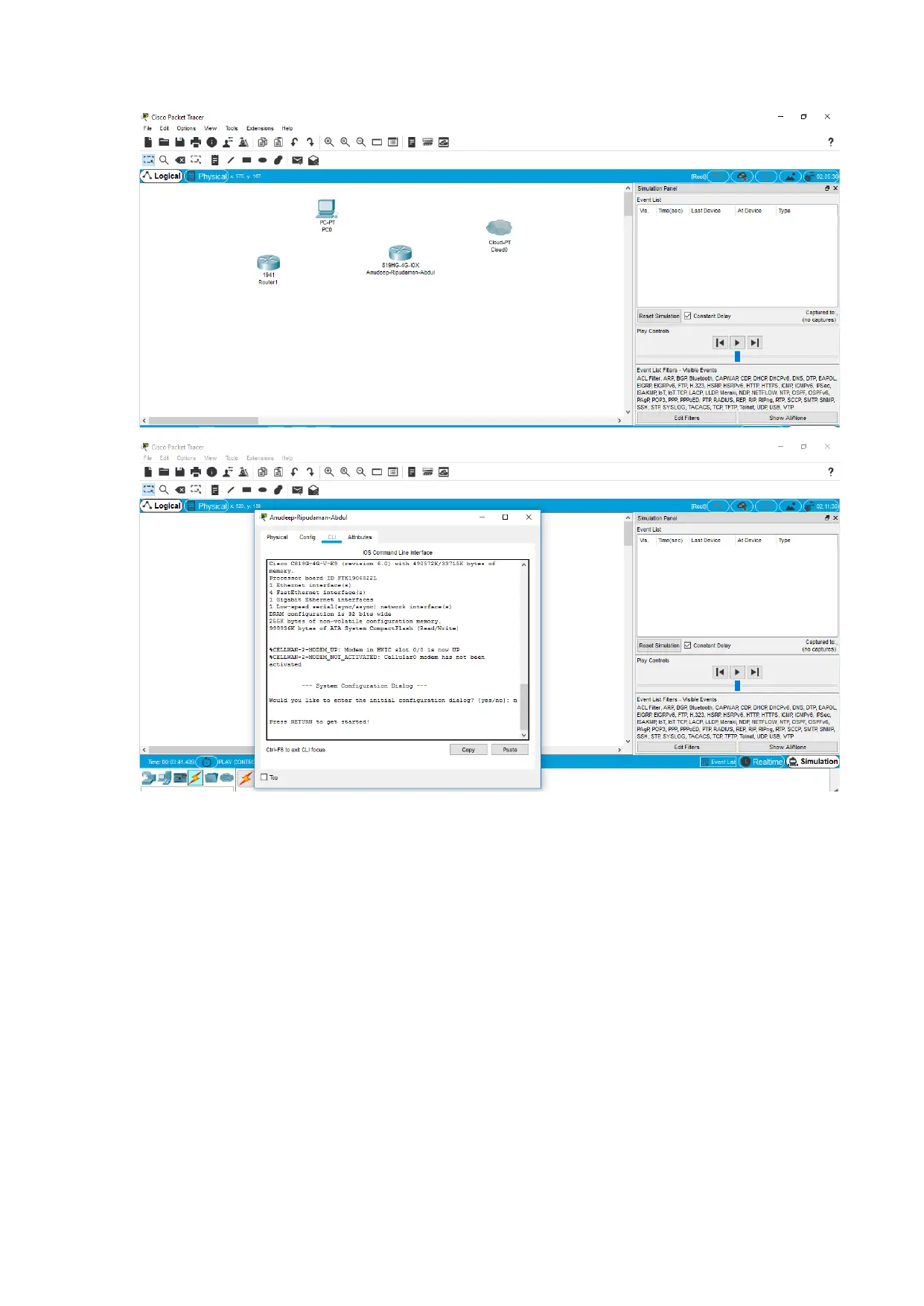
Click on the device and open command Line Interface and thereby inset the right
command so as to configure the right address for the router using the addressing table.
Therefore, use a consoled cable from an end device and connect it to the device that is to
be configured. The end device will get to the device command line interface then type in
the appropriate command so as to help in configuring the right address.
configured. This is possible through access of the desktop platform for every one of the
device as well as locating the IP configuration sections. This is done so as to enable the
device to get to a right network.
After the configuration of the right IP address within the device, there is the need to
repeat the same to the routers and switches through the use of the address tables although
this time it is done in different ways since there exist different desktop platform within
the router and switches. There will be the need to access the configuration panel on
everyone of the device which is applicable in two ways which are;
Click on the device and open command Line Interface and thereby inset the right
command so as to configure the right address for the router using the addressing table.
Therefore, use a consoled cable from an end device and connect it to the device that is to
be configured. The end device will get to the device command line interface then type in
the appropriate command so as to help in configuring the right address.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
Summary
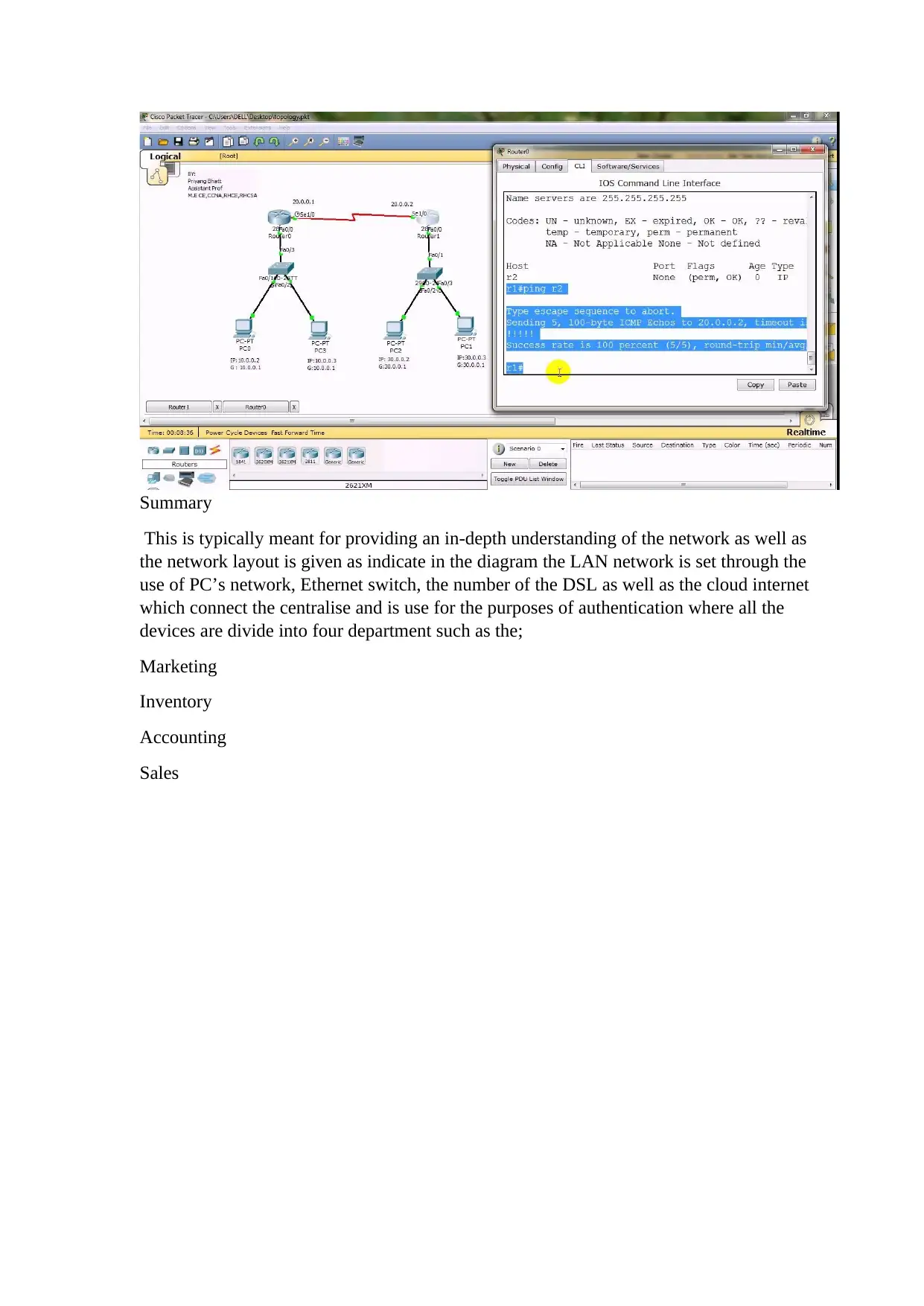
This is typically meant for providing an in-depth understanding of the network as well as
the network layout is given as indicate in the diagram the LAN network is set through the
use of PC’s network, Ethernet switch, the number of the DSL as well as the cloud internet
which connect the centralise and is use for the purposes of authentication where all the
devices are divide into four department such as the;
Marketing
Inventory
Accounting
Sales
This is typically meant for providing an in-depth understanding of the network as well as
the network layout is given as indicate in the diagram the LAN network is set through the
use of PC’s network, Ethernet switch, the number of the DSL as well as the cloud internet
which connect the centralise and is use for the purposes of authentication where all the
devices are divide into four department such as the;
Marketing
Inventory
Accounting
Sales

References
Cisco 7600 Series Router Software Configuration Guide, Cisco IOS Release 15S -
Configuring LAN Ports for Layer 2 Switching [Cisco IOS 15.0S]. (n.d.). Retrieved
from https://www.cisco.com/c/en/us/td/docs/routers/7600/ios/15S/configuration/
guide/7600_15_0s_book/layer2.html
Mazarick, M. E. (2016). U.S. Patent No. 9,282,055. Washington, DC: U.S. Patent and Trademark
Office.
Silberschatz, A., Gagne, G., & Galvin, P. B. (2018). Operating system concepts. Wiley.
Cisco 7600 Series Router Software Configuration Guide, Cisco IOS Release 15S -
Configuring LAN Ports for Layer 2 Switching [Cisco IOS 15.0S]. (n.d.). Retrieved
from https://www.cisco.com/c/en/us/td/docs/routers/7600/ios/15S/configuration/
guide/7600_15_0s_book/layer2.html
Mazarick, M. E. (2016). U.S. Patent No. 9,282,055. Washington, DC: U.S. Patent and Trademark
Office.
Silberschatz, A., Gagne, G., & Galvin, P. B. (2018). Operating system concepts. Wiley.
1 out of 10
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
© 2024 | Zucol Services PVT LTD | All rights reserved.





