LAN to Support Windows Server and Client
VerifiedAdded on 2023/03/21
|32
|3011
|99
AI Summary
This report provides a detailed implementation guide for setting up a network for the client side as well as supporting Windows server. It includes requirement analysis, configuring process description, IP addressing plan, configuration screenshots or commands, centralised user authentication, print server configuration, DHCP server configuration, IIS configuration for hosting own website, file server configuration, and active directory domain structure diagram.
Contribute Materials
Your contribution can guide someone’s learning journey. Share your
documents today.

Local Area Network (LAN) to support Windows Server and Client
Environment
Name of the Student
Name of the University
Author’s Note
Environment
Name of the Student
Name of the University
Author’s Note
Secure Best Marks with AI Grader
Need help grading? Try our AI Grader for instant feedback on your assignments.

Table of Contents
Introduction...........................................................................................................................................2
Requirement analysis............................................................................................................................2
Configuring process description............................................................................................................3
IP Addressing Plan.............................................................................................................................3
Configuration Screenshots or commands..............................................................................................5
Centralised user authentication........................................................................................................5
Print server configuration..................................................................................................................5
DHCP server configuration...............................................................................................................10
IIS configuration for hosting own website.......................................................................................19
File server configuration..................................................................................................................21
Active Directory Domain Structure Diagram....................................................................................27
Summary.............................................................................................................................................28
Conclusions..........................................................................................................................................29
Bibliography.........................................................................................................................................30
Introduction...........................................................................................................................................2
Requirement analysis............................................................................................................................2
Configuring process description............................................................................................................3
IP Addressing Plan.............................................................................................................................3
Configuration Screenshots or commands..............................................................................................5
Centralised user authentication........................................................................................................5
Print server configuration..................................................................................................................5
DHCP server configuration...............................................................................................................10
IIS configuration for hosting own website.......................................................................................19
File server configuration..................................................................................................................21
Active Directory Domain Structure Diagram....................................................................................27
Summary.............................................................................................................................................28
Conclusions..........................................................................................................................................29
Bibliography.........................................................................................................................................30

Introduction
The report, which is prepared for thinktank, is aimed at providing a detailed implementation guide
for setting up a network for the client side as well as supporting Windows server. This network is
designed on local area network Technology. According to the requirement of the organization, this
Network Support present needs of the organizations while allocating various users. Not only that this
network should be scalable enough so that it provides support to future users whenever there is a
need to allocate more users than the organization presently needs to manage. Analysis has been
made for the existing organizational network to identify the infrastructure so that the network is
designed in an appropriate way while providing the benefits of the network according to the
organizational requirements. All configuration that will be considered for this network has been
discussed in details in this report. Along with those relevant commands that will be considered for
design, the network has also been included in the report and this has been followed by proper
screenshots so that it is easier to review the network configuration as well as the proposed design in
this context.
Requirement analysis
In order to identify the requirements in an appropriate way and define those requirements for the
network design, it is important to involve serious users at a different level based on their roles and
interest in this project. This analysis for the network requirements is essential to identify various
errors that might be associated with the network design. If these errors are not identified during the
planning of the network design it will be difficult to modify the issues during the design
implementation of the network. Requirement gathering and analysis has been done with proper
detailing of various errors that might be relevant in this network design. All the important
stakeholders of this project might be involved in this process so that it is easier to identify sensitive
information what level of protection this information should have and how the organization is
thinking to define access to that information. This information is very essential in designing the
network because this network should support client service, therefore, it is extremely important to
protect the information from illegal access. In this context, separate subnets will be considered for
the network design, as it will help to deny any request to access sensitive data if the user is not
authenticated and does not have the required permission for accessing the data. The IP address that
will be assigned to various clients will be integrated into similar Local area network or LAN.
The report, which is prepared for thinktank, is aimed at providing a detailed implementation guide
for setting up a network for the client side as well as supporting Windows server. This network is
designed on local area network Technology. According to the requirement of the organization, this
Network Support present needs of the organizations while allocating various users. Not only that this
network should be scalable enough so that it provides support to future users whenever there is a
need to allocate more users than the organization presently needs to manage. Analysis has been
made for the existing organizational network to identify the infrastructure so that the network is
designed in an appropriate way while providing the benefits of the network according to the
organizational requirements. All configuration that will be considered for this network has been
discussed in details in this report. Along with those relevant commands that will be considered for
design, the network has also been included in the report and this has been followed by proper
screenshots so that it is easier to review the network configuration as well as the proposed design in
this context.
Requirement analysis
In order to identify the requirements in an appropriate way and define those requirements for the
network design, it is important to involve serious users at a different level based on their roles and
interest in this project. This analysis for the network requirements is essential to identify various
errors that might be associated with the network design. If these errors are not identified during the
planning of the network design it will be difficult to modify the issues during the design
implementation of the network. Requirement gathering and analysis has been done with proper
detailing of various errors that might be relevant in this network design. All the important
stakeholders of this project might be involved in this process so that it is easier to identify sensitive
information what level of protection this information should have and how the organization is
thinking to define access to that information. This information is very essential in designing the
network because this network should support client service, therefore, it is extremely important to
protect the information from illegal access. In this context, separate subnets will be considered for
the network design, as it will help to deny any request to access sensitive data if the user is not
authenticated and does not have the required permission for accessing the data. The IP address that
will be assigned to various clients will be integrated into similar Local area network or LAN.
Configuring process description
For designing the network LAN technology has been considered and this has provided the
framework for designing the overall network. This network architecture will be deployed to manage
the overall service network that is connected with the server of the client. This LAN also provides
interface that connects various hosts of various router and this provides connection between various
network hosts. Interface provided by the LAN architecture also connects file servers that is
associated with various routers which is having various interfaces. Another important aspect of the
network design is to provide secure access to the data servers and data storage as it has various
important data including organizational and consumer data. Hence, adequate importance has been
provided for securing the network infrastructure. In order to provide an effective and secured design
for this network, the IP subnet scheme defined for five subnets has been considered.
IP Addressing Plan
Subnet
Name
Neede
d Size
Allocate
d Size
Address Mas
k
Dec Mask Assignable
Range
Broadcast
Finance 5 6 192.168.1.
32
/29 255.255.255.2
48
192.168.1.
33 -
192.168.1.
38
192.168.1.
39
Sales 20 30 192.168.1.
0
/27 255.255.255.2
24
192.168.1.
1 -
192.168.1.
30
192.168.1.
31
Managers 3 6 192.168.1.
40
/29 255.255.255.2
48
192.168.1.
41 -
192.168.1.
46
192.168.1.
47
Workgrou
p
Computer
s
2 2 192.168.1.
48
/30 255.255.255.2
52
192.168.1.
49 -
192.168.1.
50
192.168.1.
51
For designing the network LAN technology has been considered and this has provided the
framework for designing the overall network. This network architecture will be deployed to manage
the overall service network that is connected with the server of the client. This LAN also provides
interface that connects various hosts of various router and this provides connection between various
network hosts. Interface provided by the LAN architecture also connects file servers that is
associated with various routers which is having various interfaces. Another important aspect of the
network design is to provide secure access to the data servers and data storage as it has various
important data including organizational and consumer data. Hence, adequate importance has been
provided for securing the network infrastructure. In order to provide an effective and secured design
for this network, the IP subnet scheme defined for five subnets has been considered.
IP Addressing Plan
Subnet
Name
Neede
d Size
Allocate
d Size
Address Mas
k
Dec Mask Assignable
Range
Broadcast
Finance 5 6 192.168.1.
32
/29 255.255.255.2
48
192.168.1.
33 -
192.168.1.
38
192.168.1.
39
Sales 20 30 192.168.1.
0
/27 255.255.255.2
24
192.168.1.
1 -
192.168.1.
30
192.168.1.
31
Managers 3 6 192.168.1.
40
/29 255.255.255.2
48
192.168.1.
41 -
192.168.1.
46
192.168.1.
47
Workgrou
p
Computer
s
2 2 192.168.1.
48
/30 255.255.255.2
52
192.168.1.
49 -
192.168.1.
50
192.168.1.
51
Secure Best Marks with AI Grader
Need help grading? Try our AI Grader for instant feedback on your assignments.

Centralised User Authentication – To ensue authentication for the network and define it for all the
central users of the network, windows server need to be configured with active directory. Domain
service needs to be integrated with other network services. Domain should be properly configured
and proper password should be assigned for every domain name so that it is easier for ensuring
security of various network resources.
Print servers for users – all of the features related to the printing are managed by the network
servers which provides print service. This service is provided by the network manager.
DHCP Configuration – Proper configuration design that is an important requirement for the
Windows Server is done with DHCP service Security group. This security group has been created for
DHCP server and it provides authorization. This is an important requirement for increasing network
security.
Hosting Own Website – Window server provides easy access to host the internal website. Services
like FTP services, WWW could also be implemented as well that is required for the internal website.
Description of OUs, Groups, Users and Access Levels - In order to ensure centralized access control
with accuracy, it is required to install RADIUS. Along with that, certificate of various software needs
to be encrypted with public key encryption technique and this will ensure security of the network.
Here in this context, DHCP service also plays an important role and this needs to be considered as
well. In order to configure various network servers through DHCP service, it is required to design
separate VLAN for all of the departments of the organization and integrate with DHCP service for
enhancing network security through effective control over the network.
File Server configuration –In order to allow various users to send and receive files, it is required to
configure the file servers of the network properly. Sever manager needs to configure file server with
the network and also provide access to network storage so that it is easier to store and receive files
over the network.
central users of the network, windows server need to be configured with active directory. Domain
service needs to be integrated with other network services. Domain should be properly configured
and proper password should be assigned for every domain name so that it is easier for ensuring
security of various network resources.
Print servers for users – all of the features related to the printing are managed by the network
servers which provides print service. This service is provided by the network manager.
DHCP Configuration – Proper configuration design that is an important requirement for the
Windows Server is done with DHCP service Security group. This security group has been created for
DHCP server and it provides authorization. This is an important requirement for increasing network
security.
Hosting Own Website – Window server provides easy access to host the internal website. Services
like FTP services, WWW could also be implemented as well that is required for the internal website.
Description of OUs, Groups, Users and Access Levels - In order to ensure centralized access control
with accuracy, it is required to install RADIUS. Along with that, certificate of various software needs
to be encrypted with public key encryption technique and this will ensure security of the network.
Here in this context, DHCP service also plays an important role and this needs to be considered as
well. In order to configure various network servers through DHCP service, it is required to design
separate VLAN for all of the departments of the organization and integrate with DHCP service for
enhancing network security through effective control over the network.
File Server configuration –In order to allow various users to send and receive files, it is required to
configure the file servers of the network properly. Sever manager needs to configure file server with
the network and also provide access to network storage so that it is easier to store and receive files
over the network.
Configuration Screenshots or commands
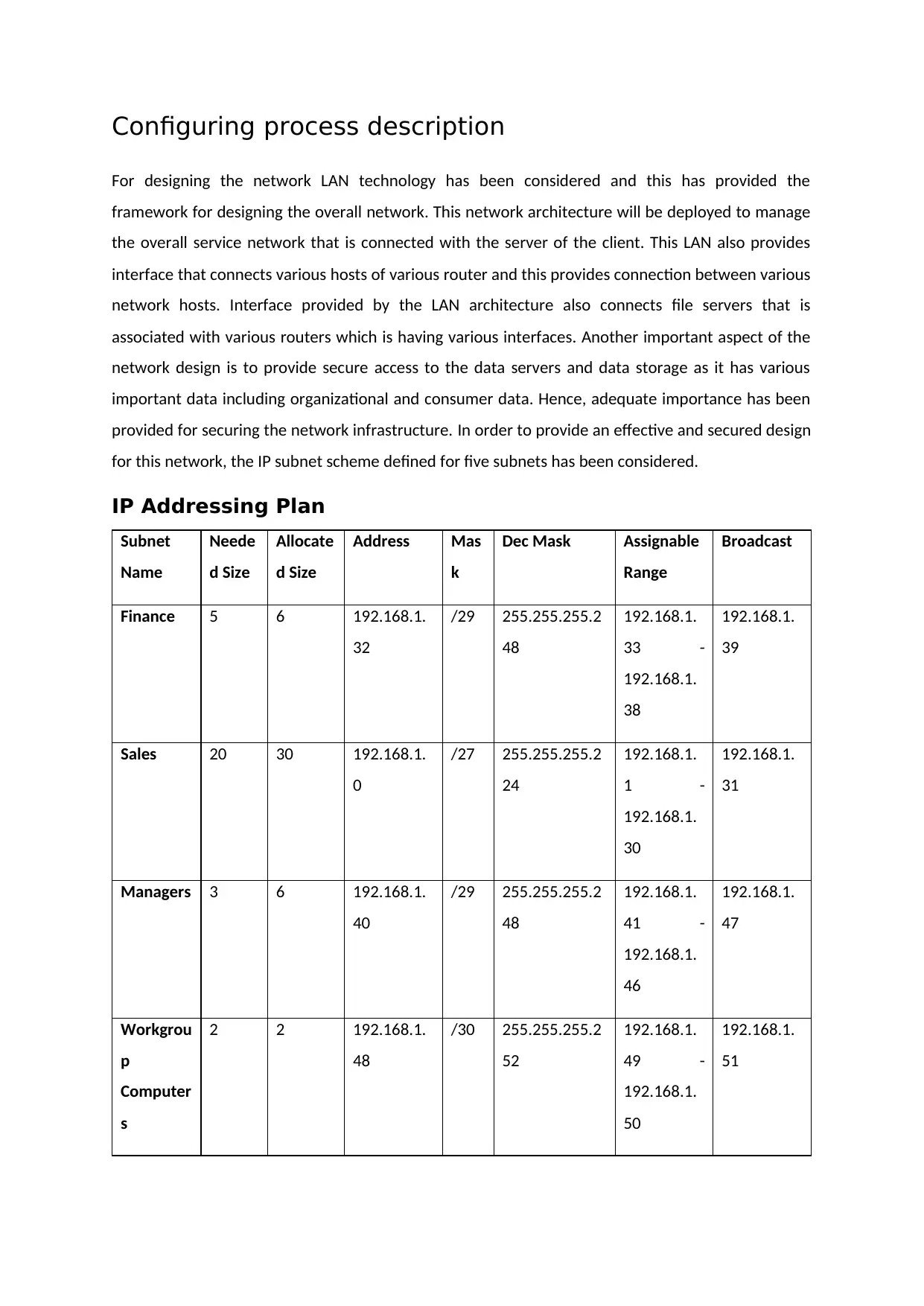
Centralised user authentication
For configuration of centralized user authentication, RADIUS server installed and active directory
also configured. New group created, users have been added for user management.
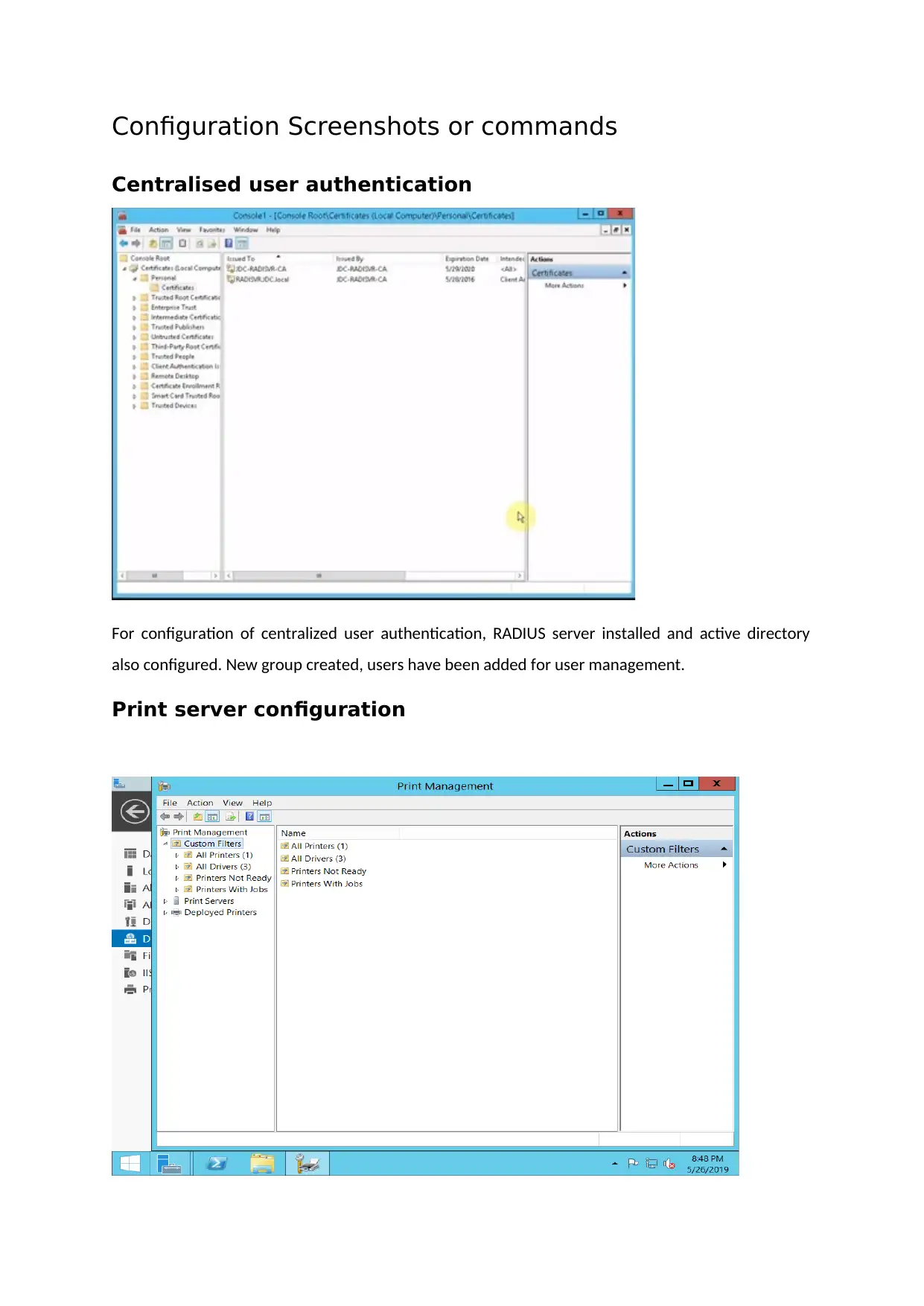
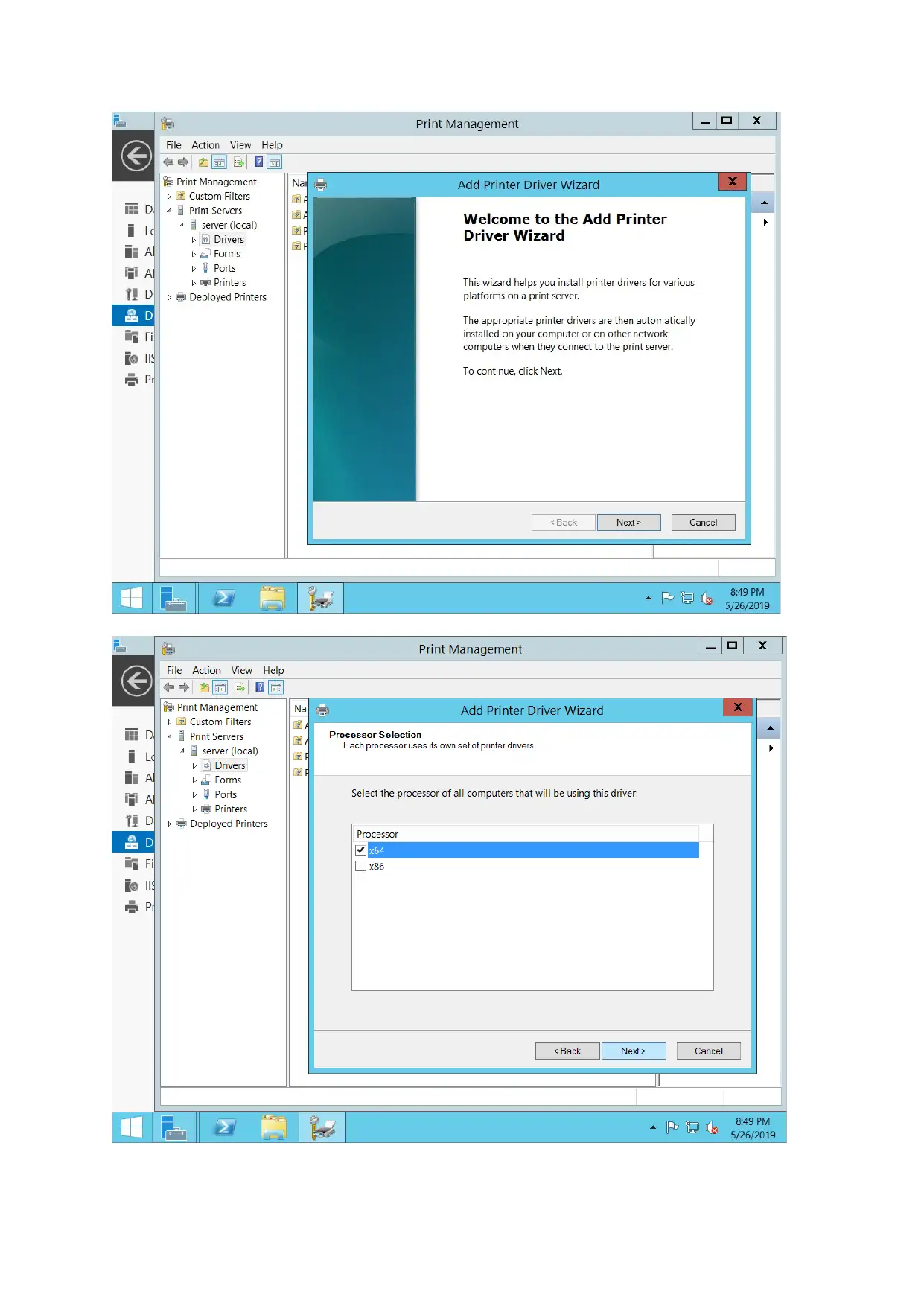
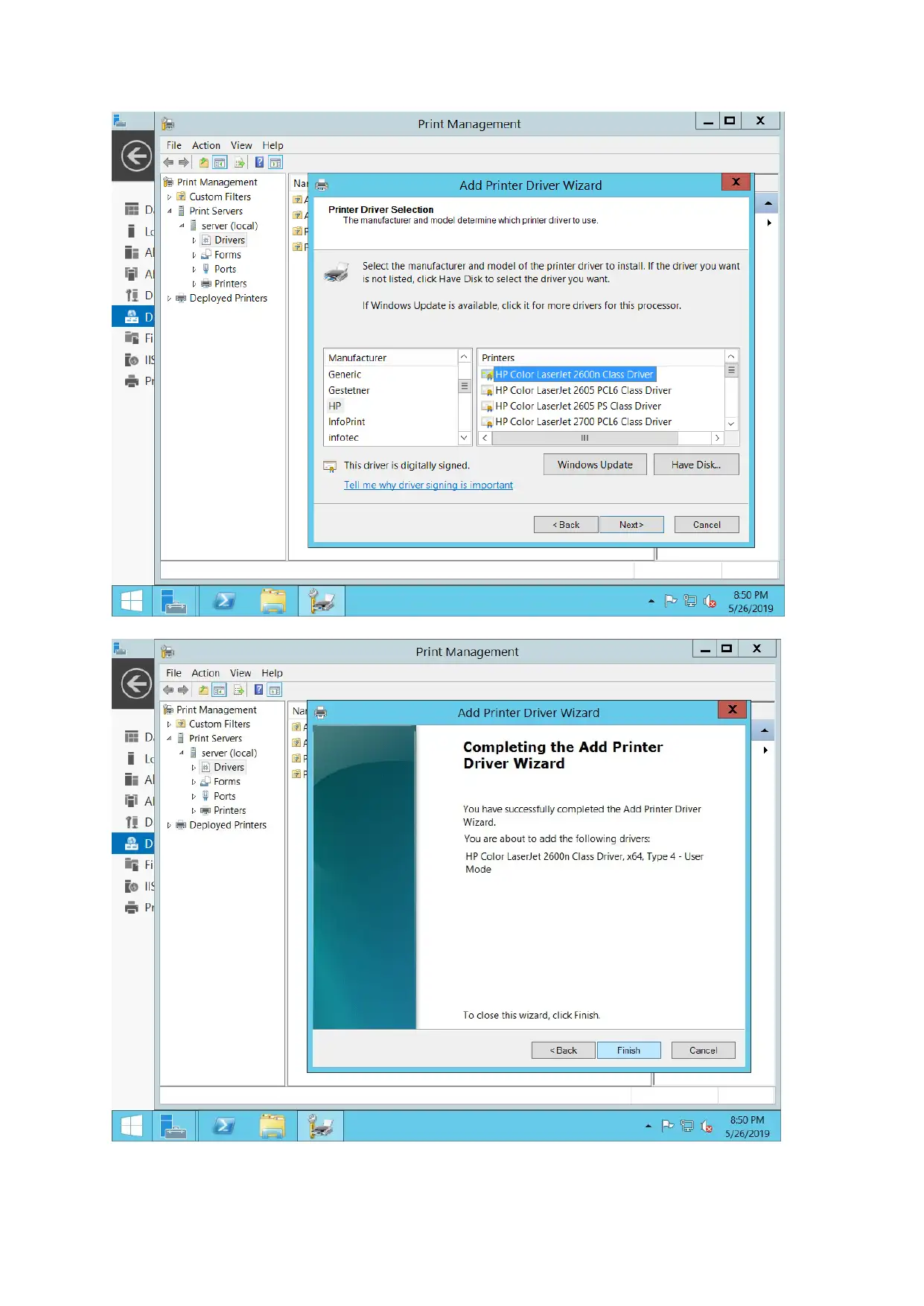
Print server configuration
Centralised user authentication
For configuration of centralized user authentication, RADIUS server installed and active directory
also configured. New group created, users have been added for user management.
Print server configuration
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
Secure Best Marks with AI Grader
Need help grading? Try our AI Grader for instant feedback on your assignments.
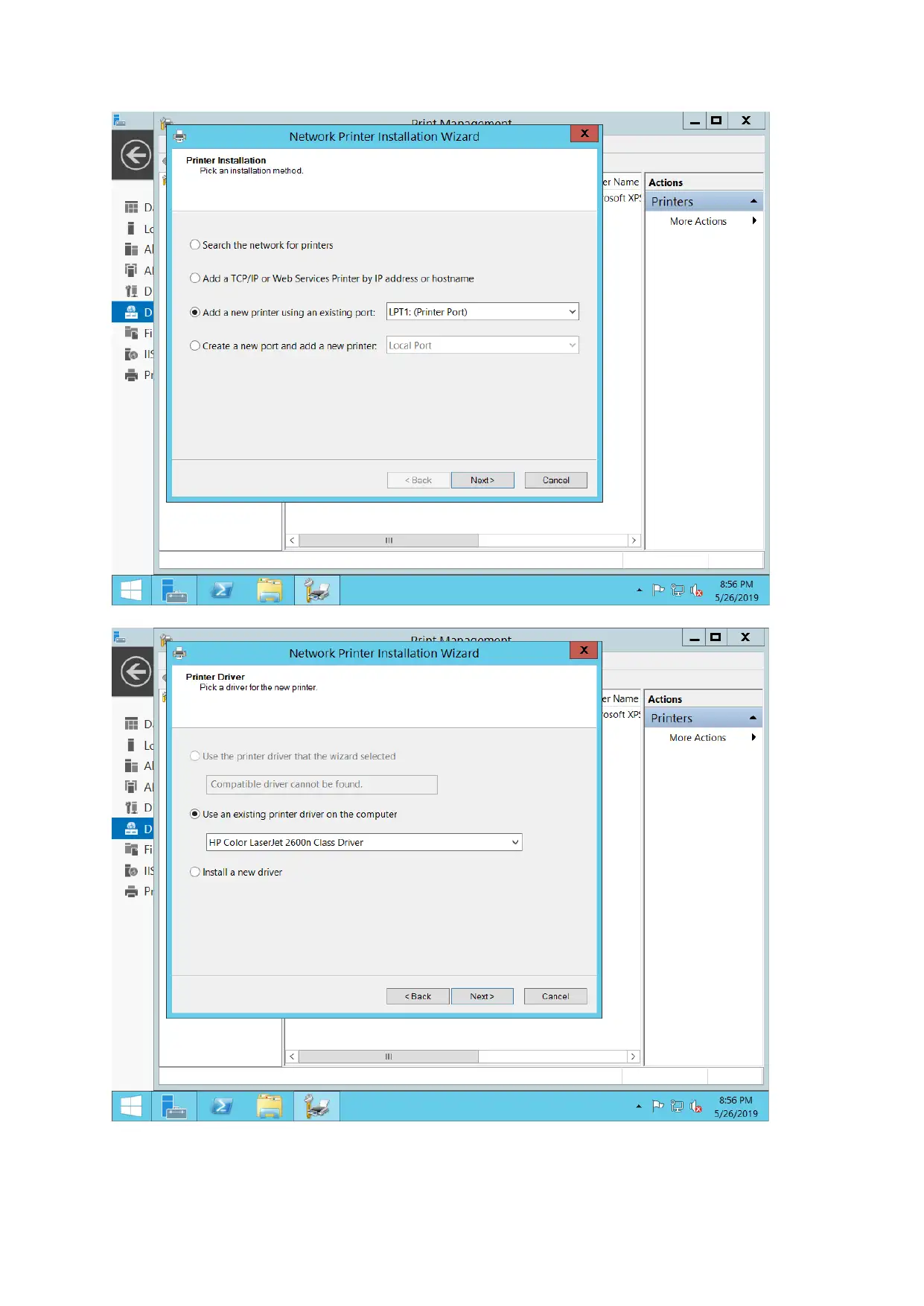
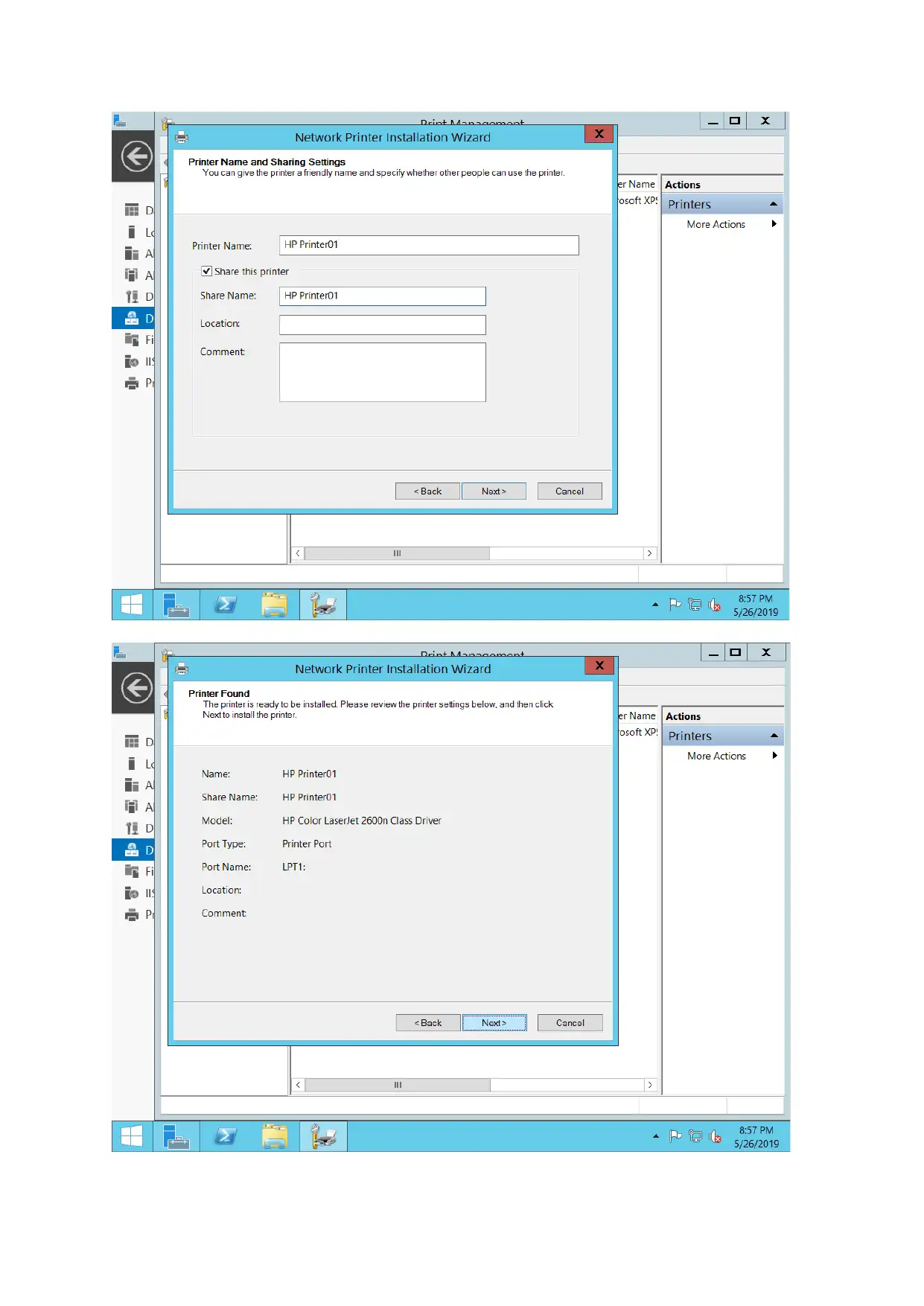
For configuring print server, document service along with print services is added and printer is
connected as well. New port added through printer management options.
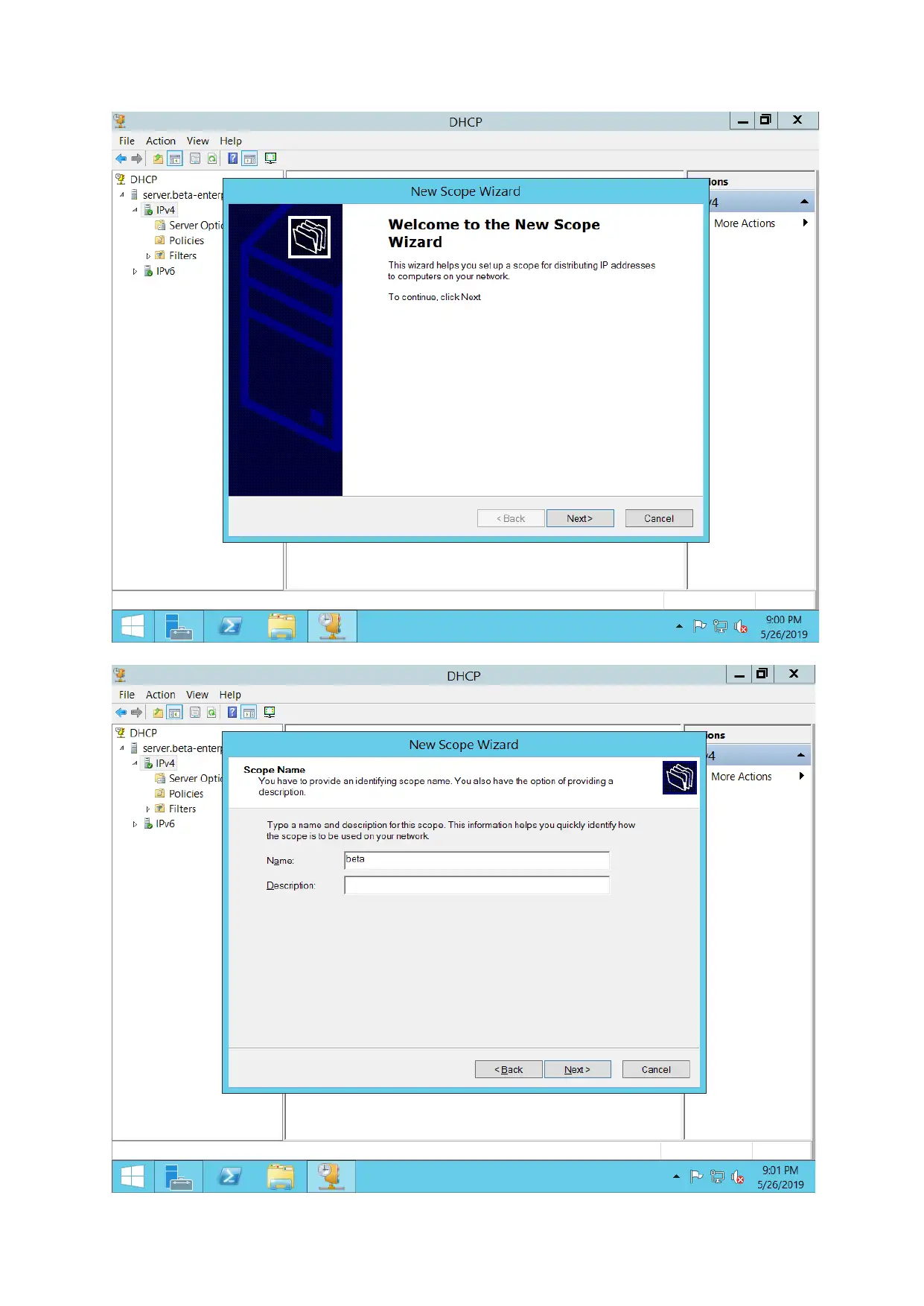
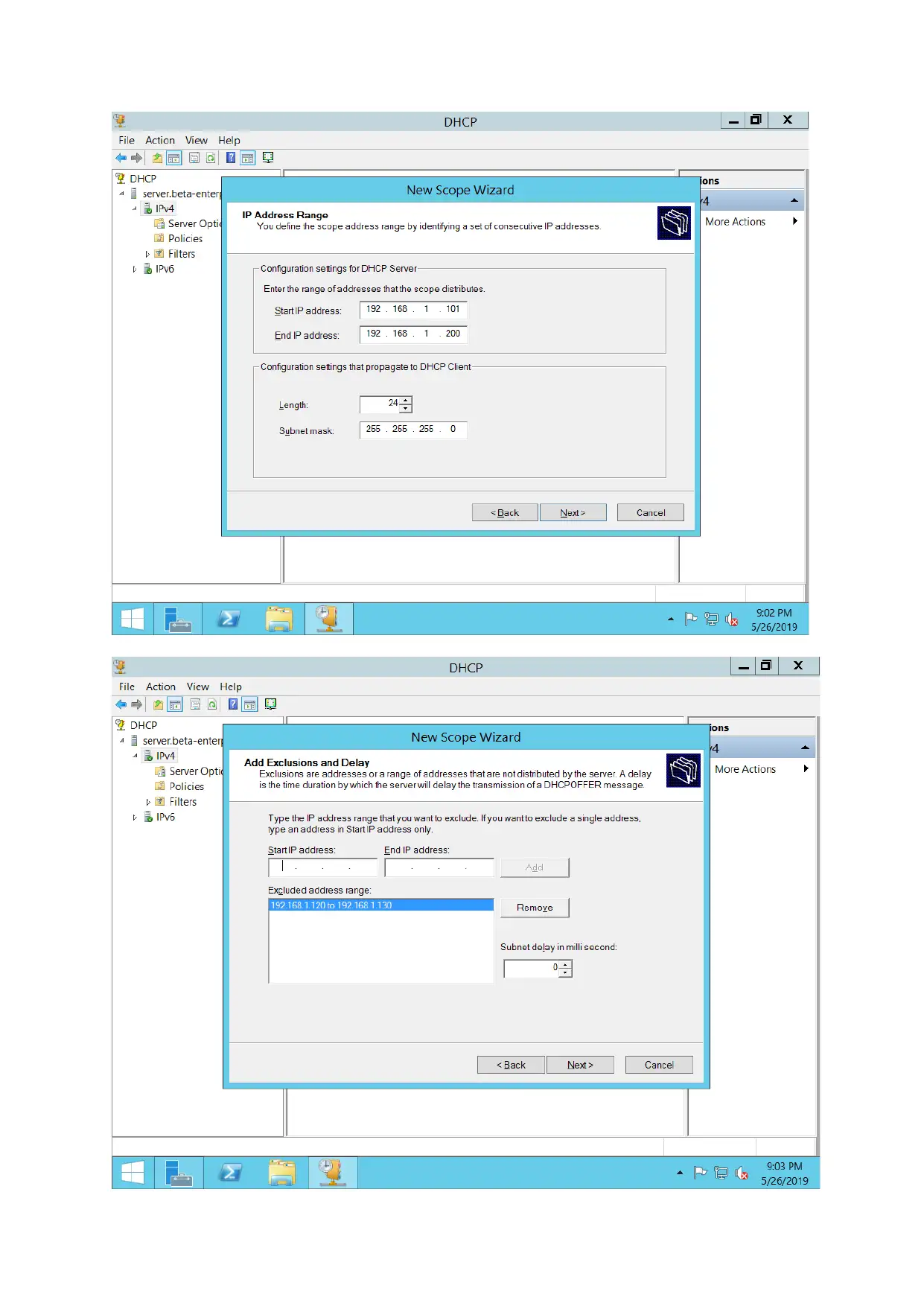
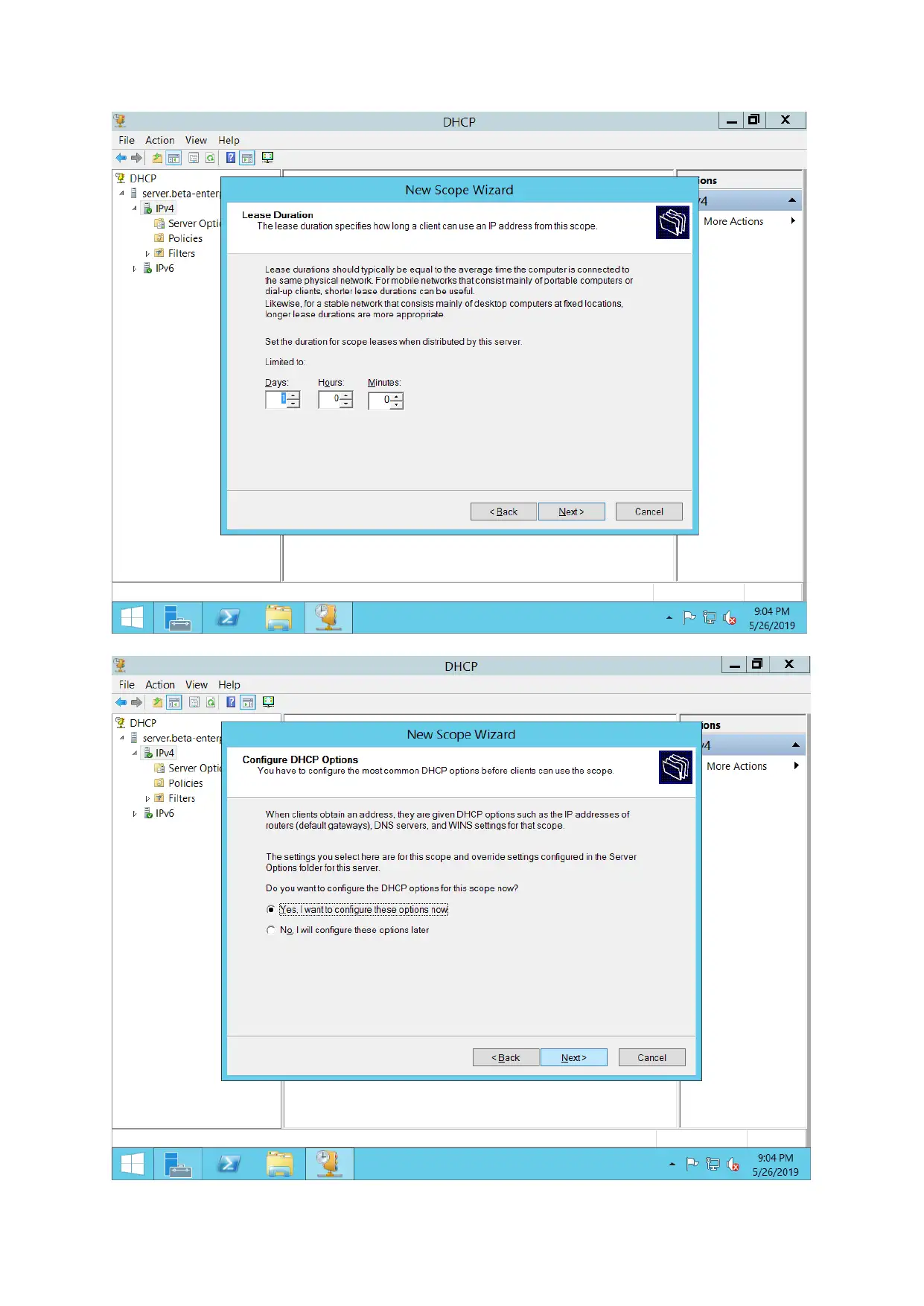
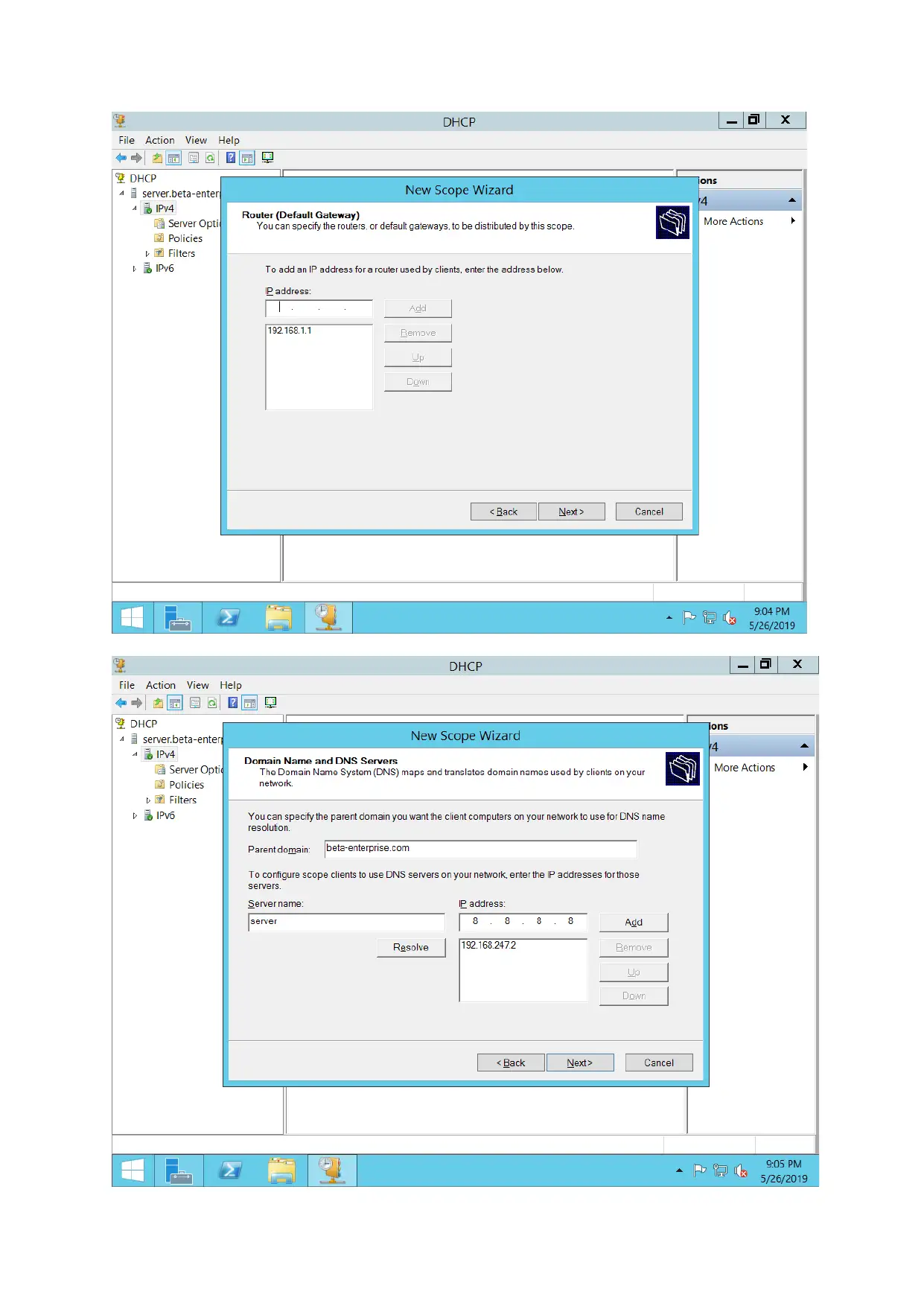
DHCP server configuration
connected as well. New port added through printer management options.
DHCP server configuration
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
Secure Best Marks with AI Grader
Need help grading? Try our AI Grader for instant feedback on your assignments.
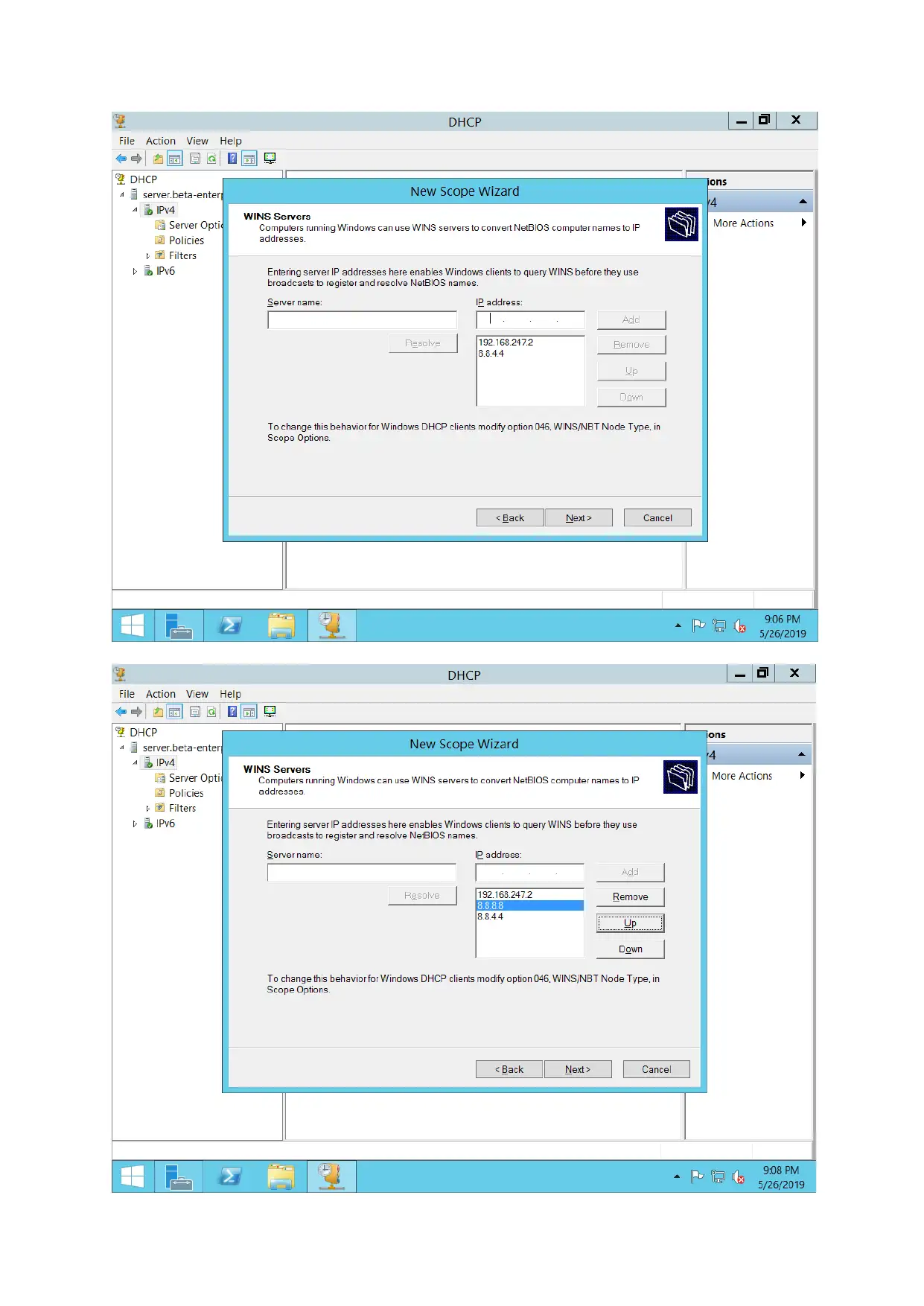
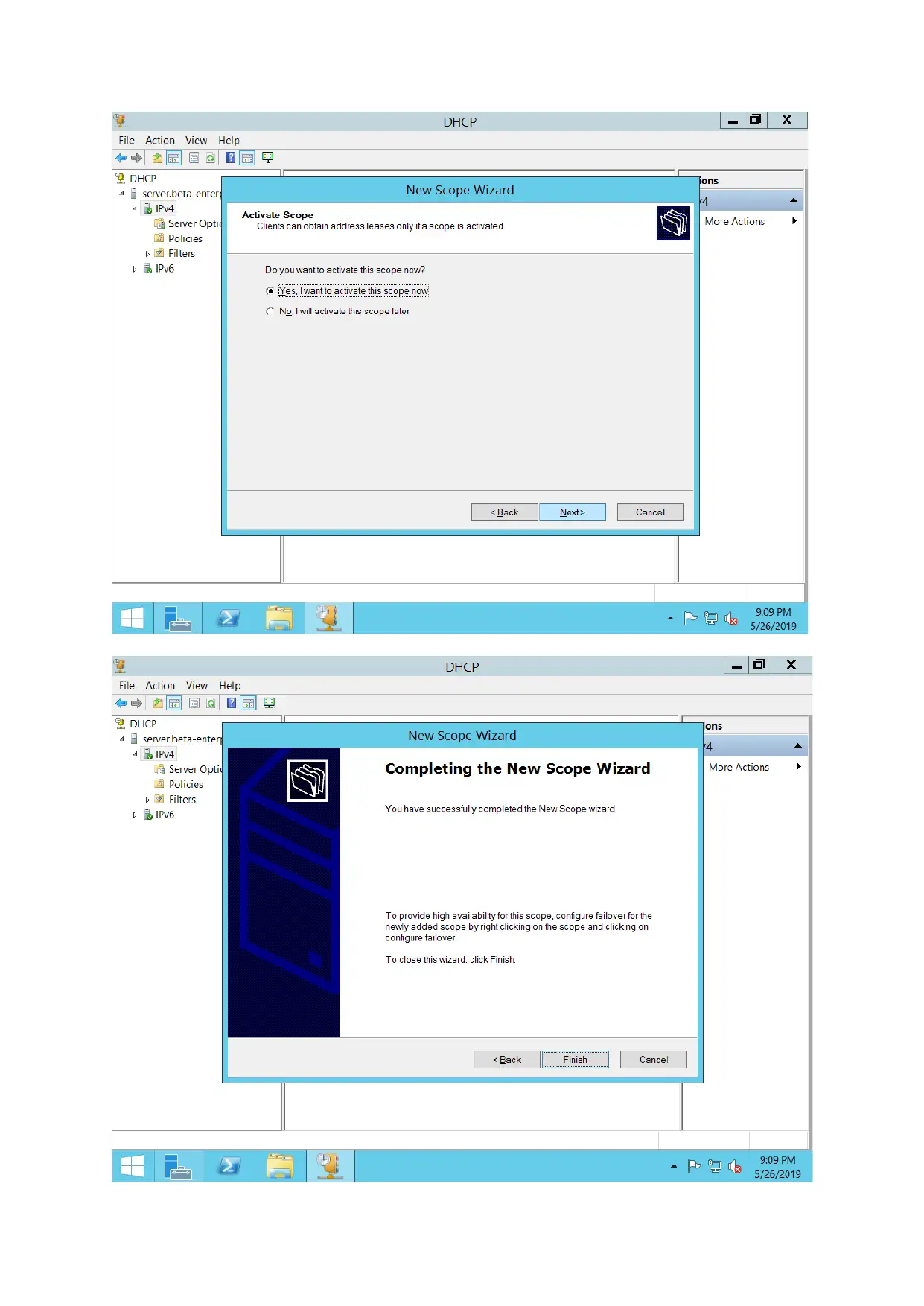
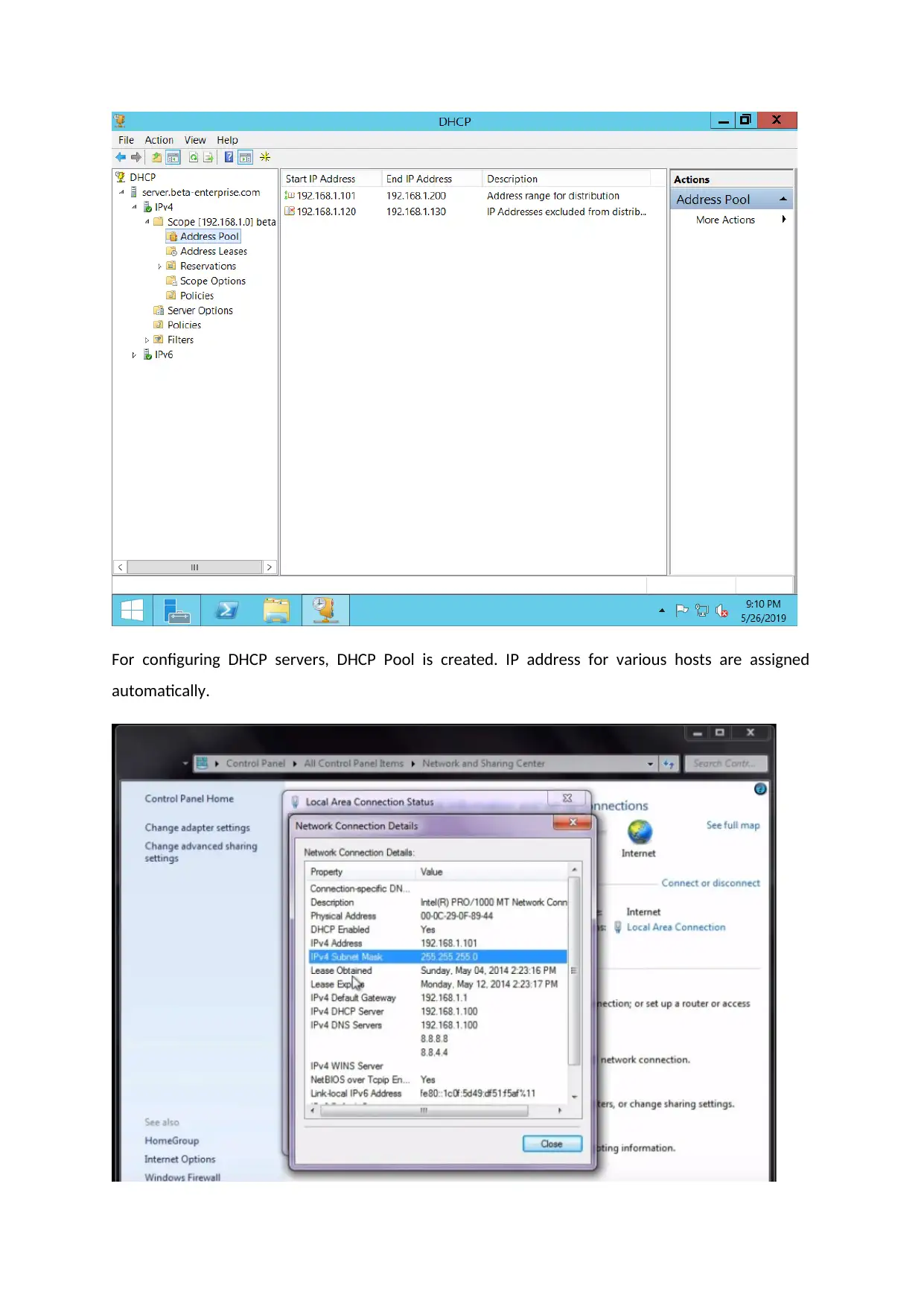
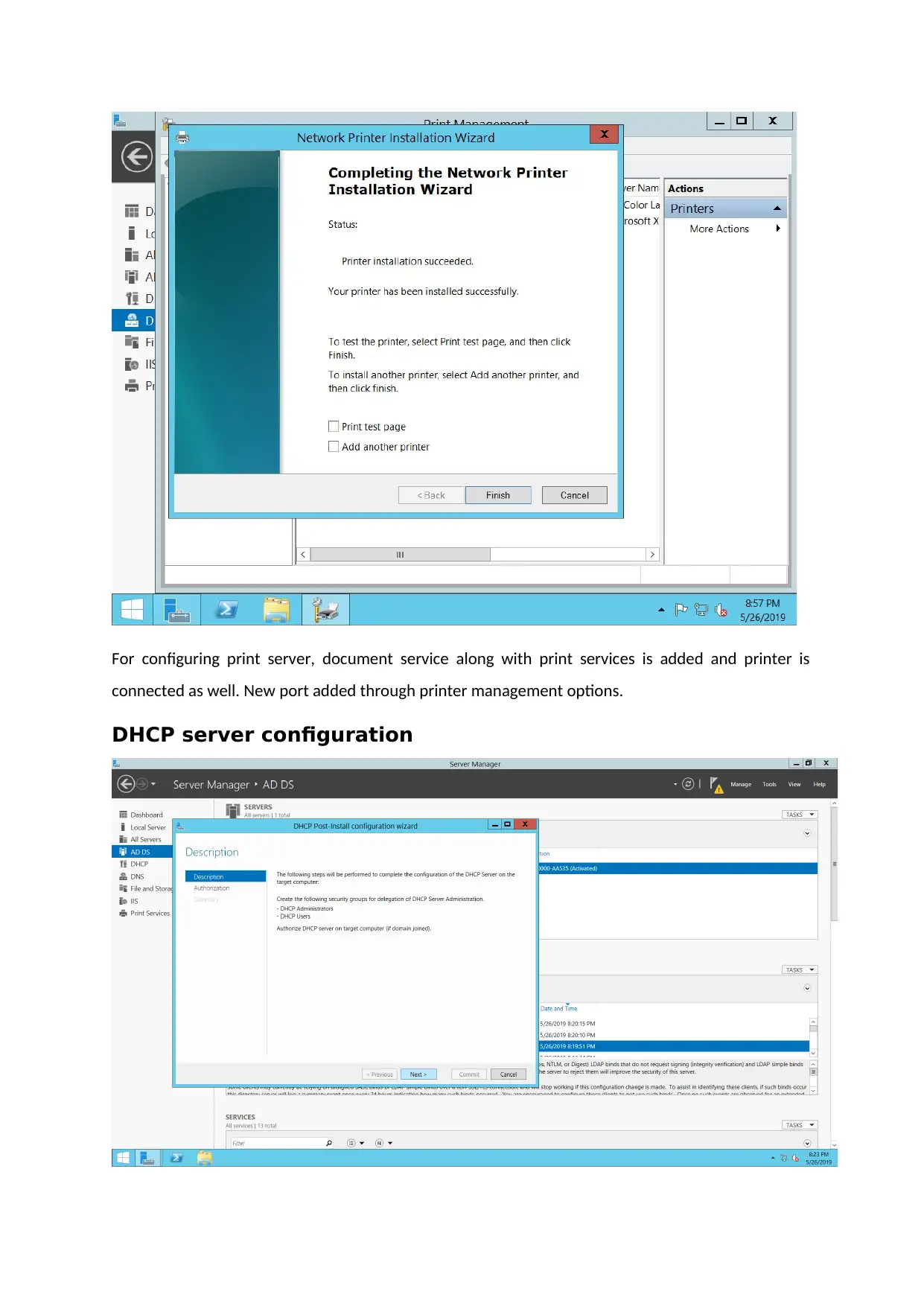
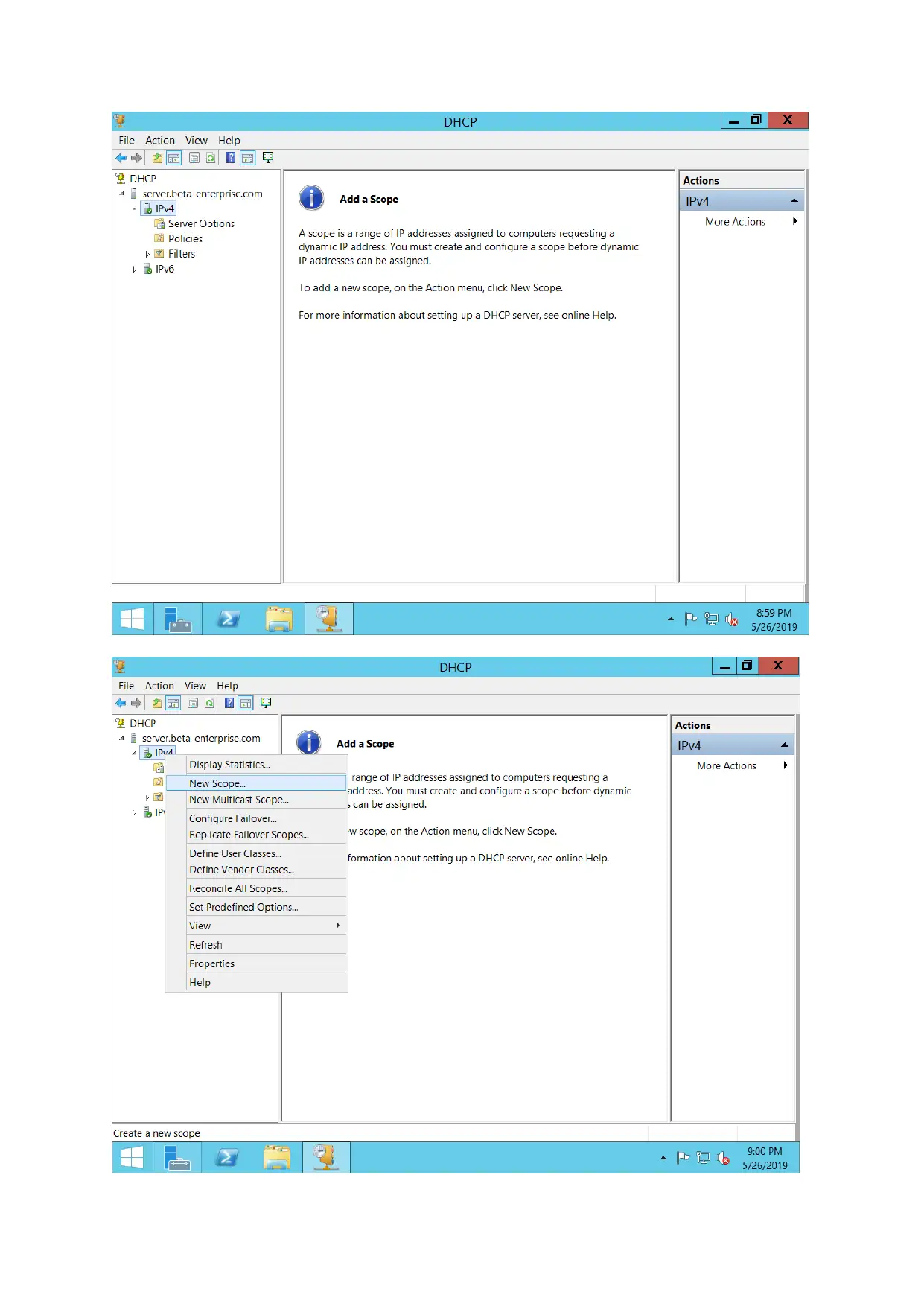
For configuring DHCP servers, DHCP Pool is created. IP address for various hosts are assigned
automatically.
automatically.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
The working of a DHCP server have been demonstrated in above screenshot.
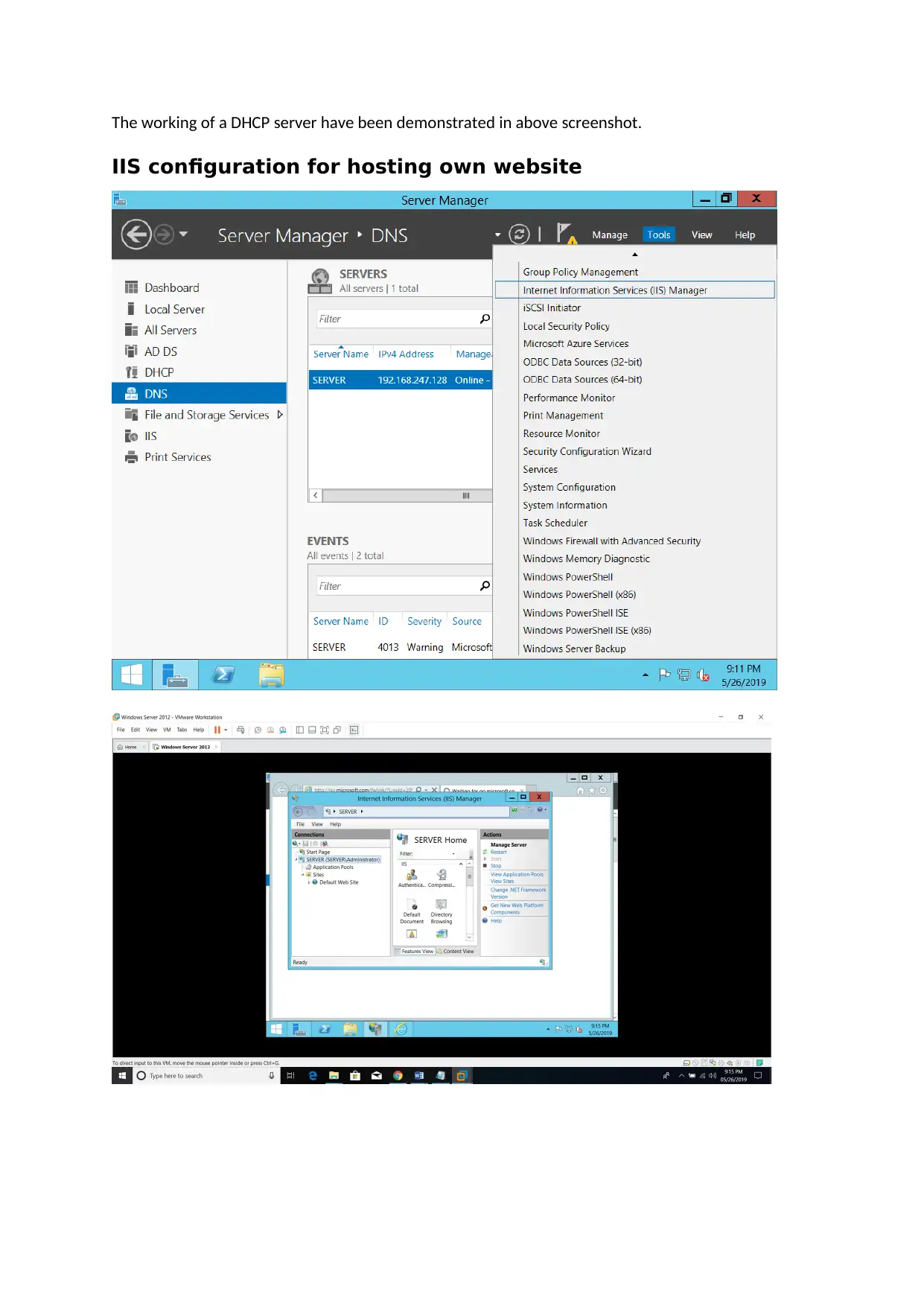
IIS configuration for hosting own website
IIS configuration for hosting own website
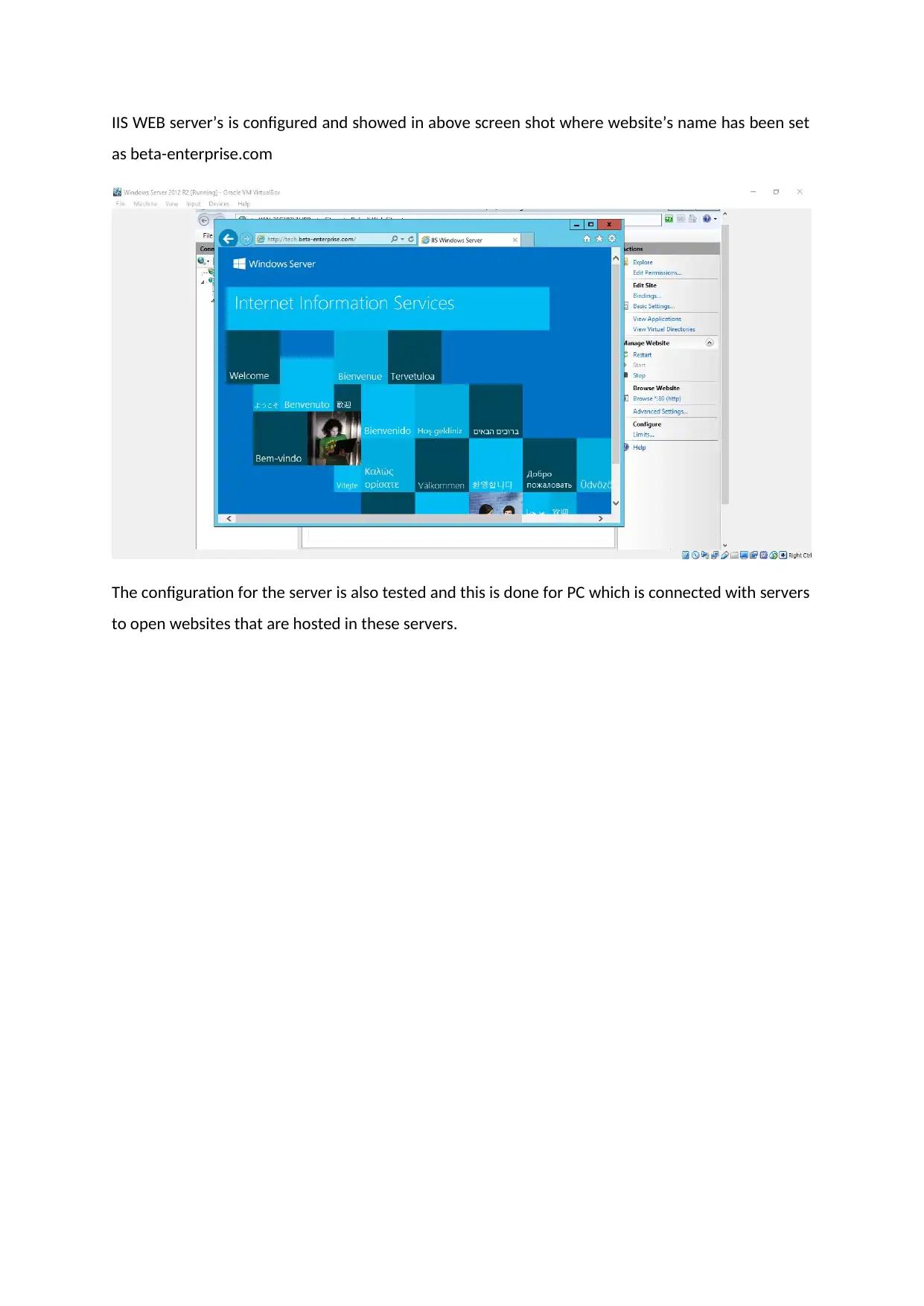
IIS WEB server’s is configured and showed in above screen shot where website’s name has been set
as beta-enterprise.com
The configuration for the server is also tested and this is done for PC which is connected with servers
to open websites that are hosted in these servers.
as beta-enterprise.com
The configuration for the server is also tested and this is done for PC which is connected with servers
to open websites that are hosted in these servers.
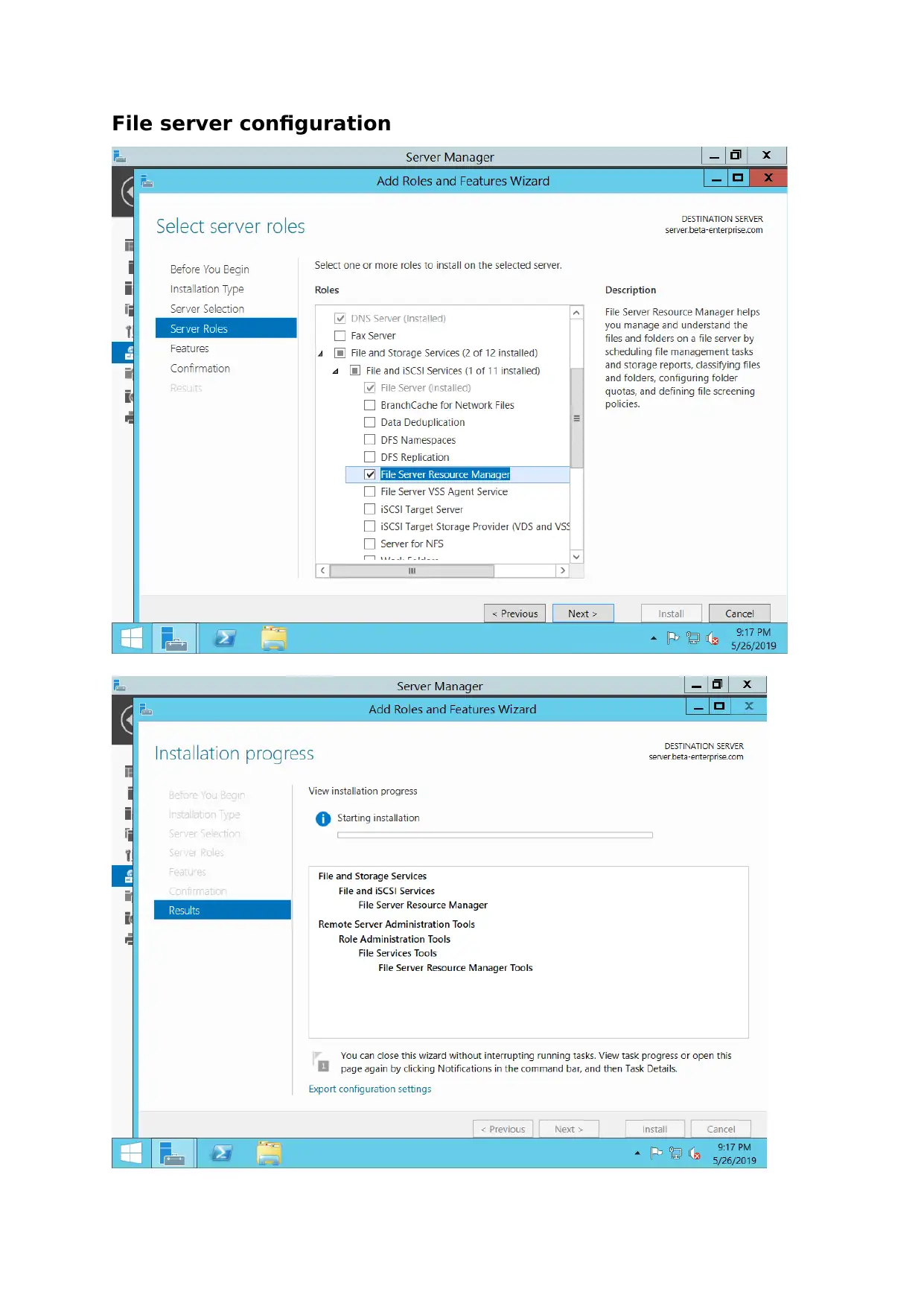
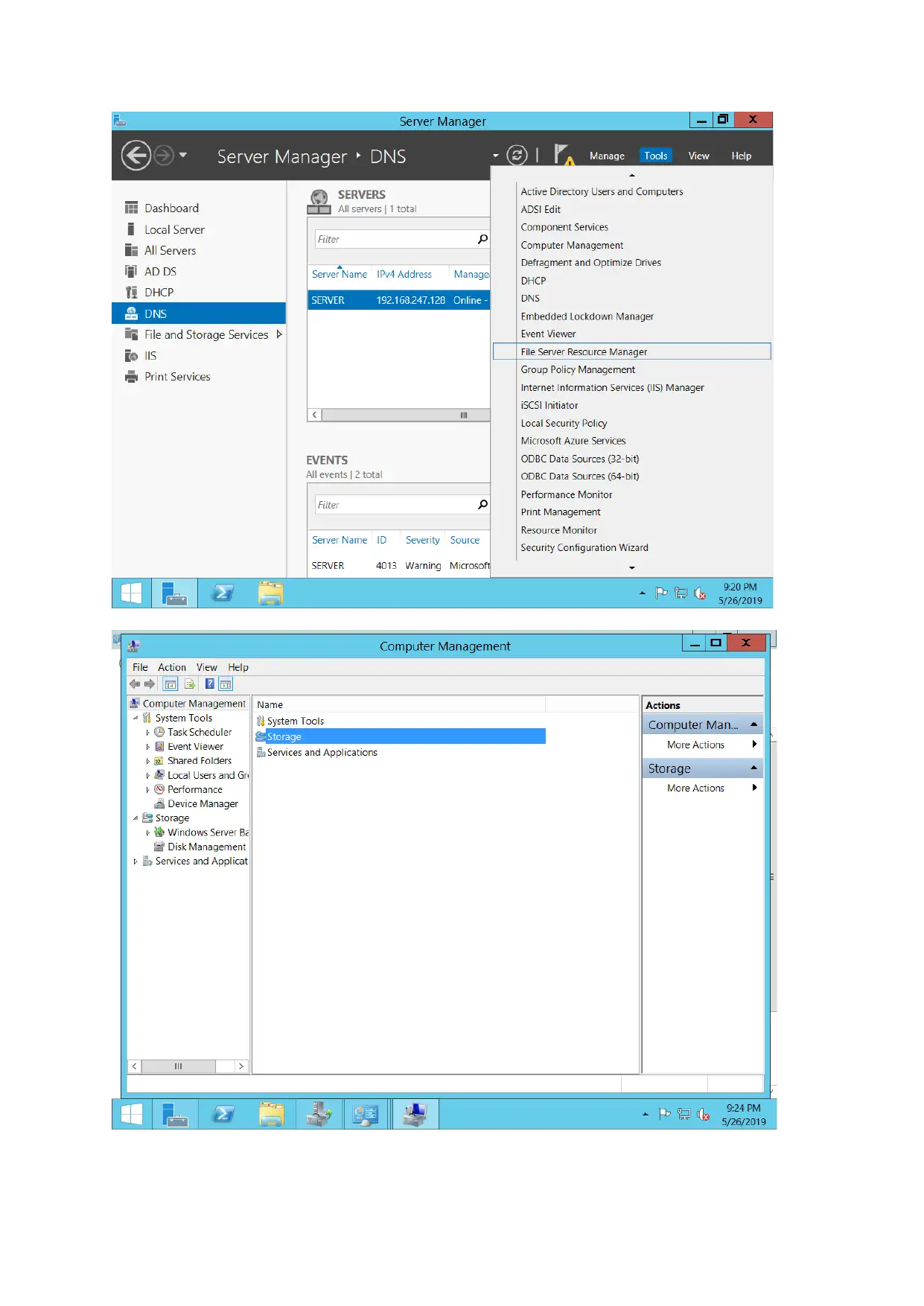
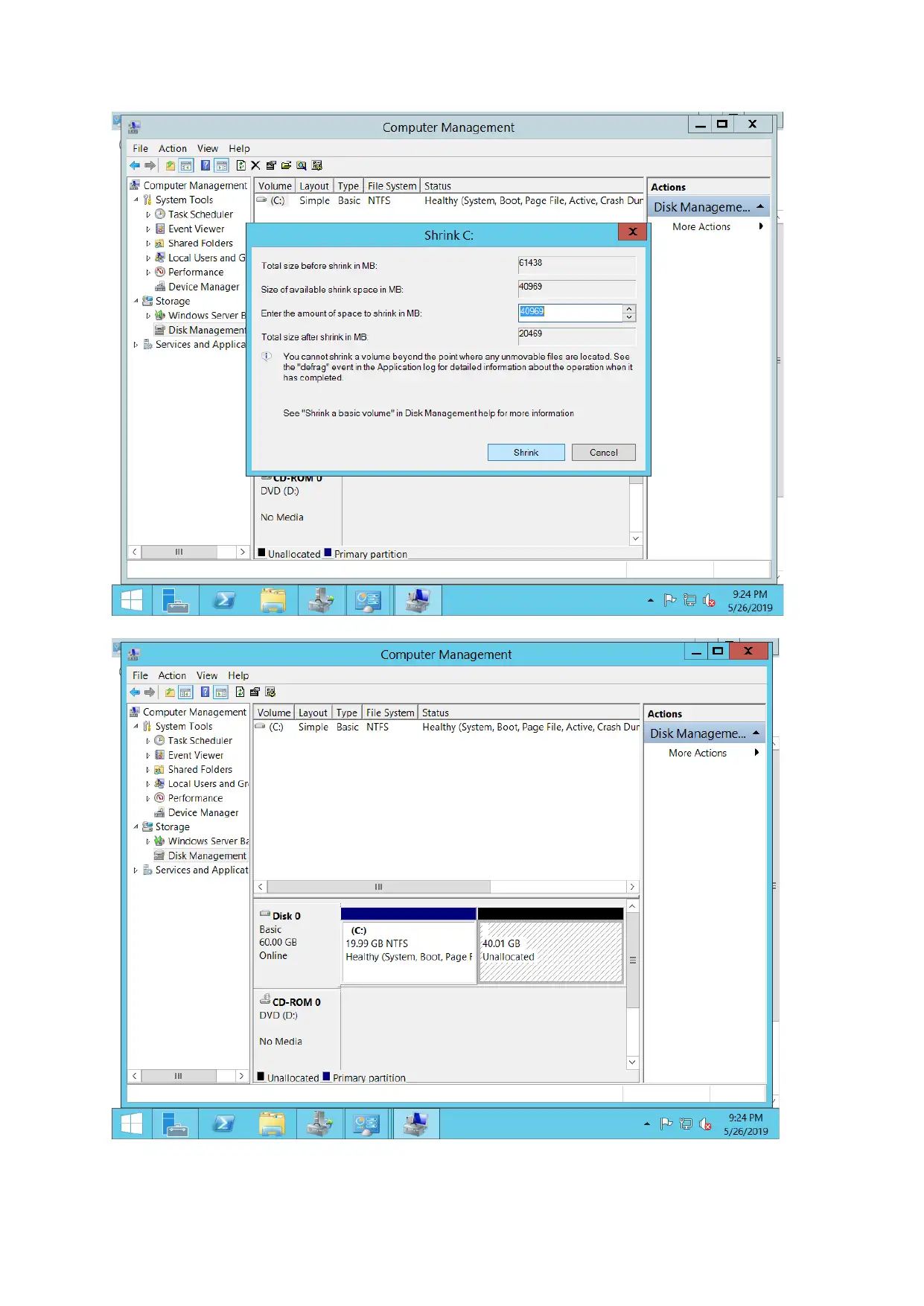
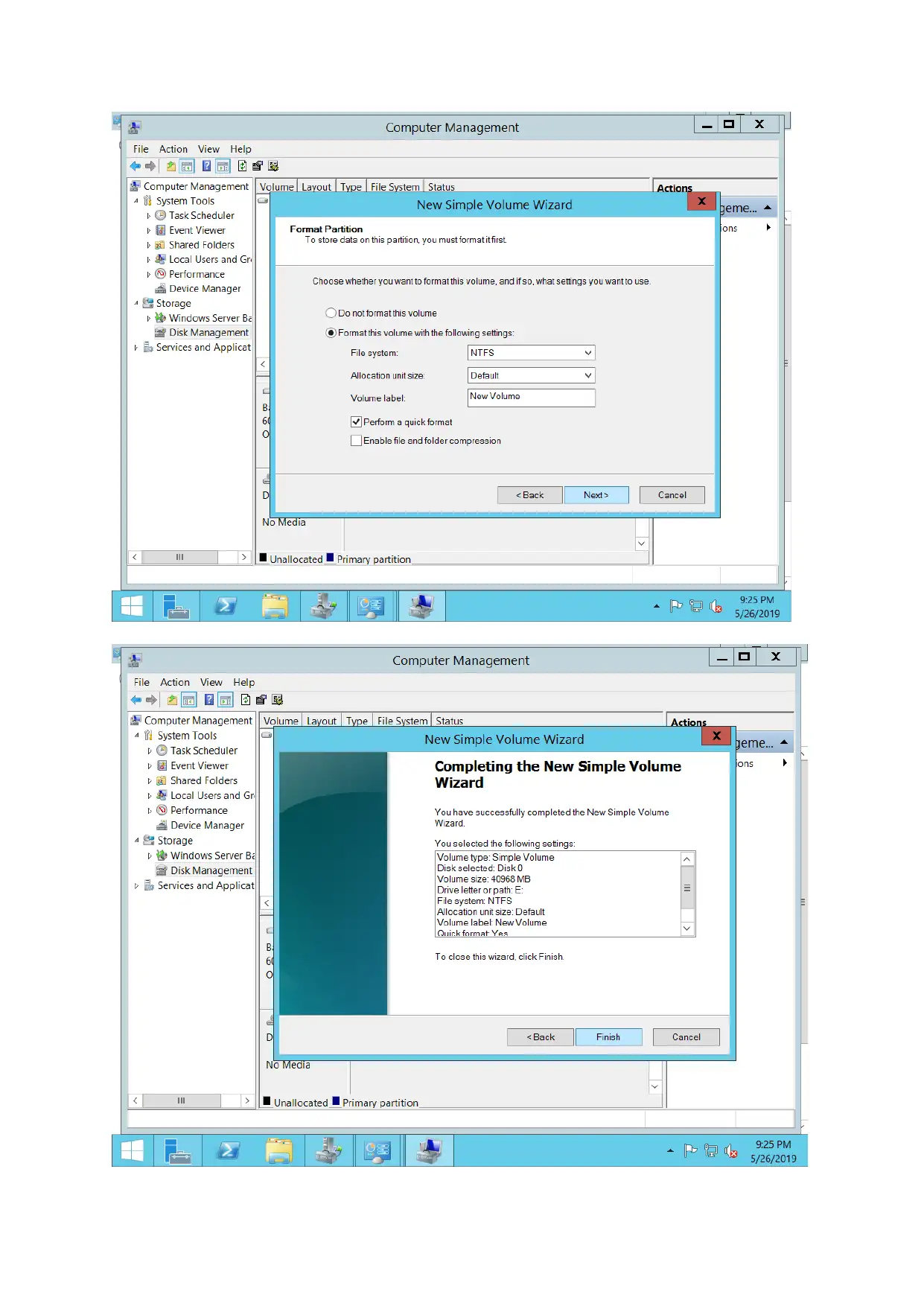
File server configuration
Secure Best Marks with AI Grader
Need help grading? Try our AI Grader for instant feedback on your assignments.
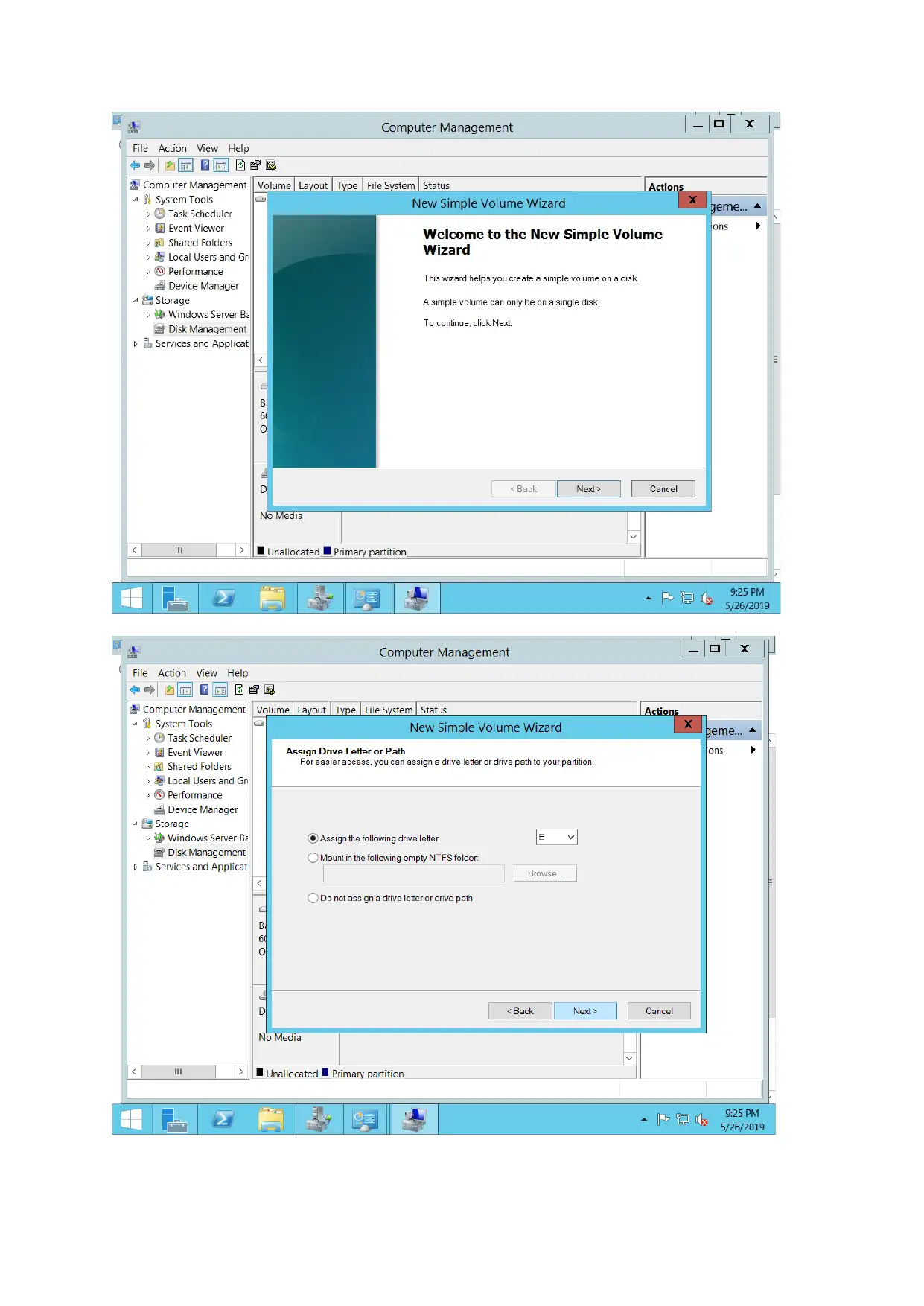
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
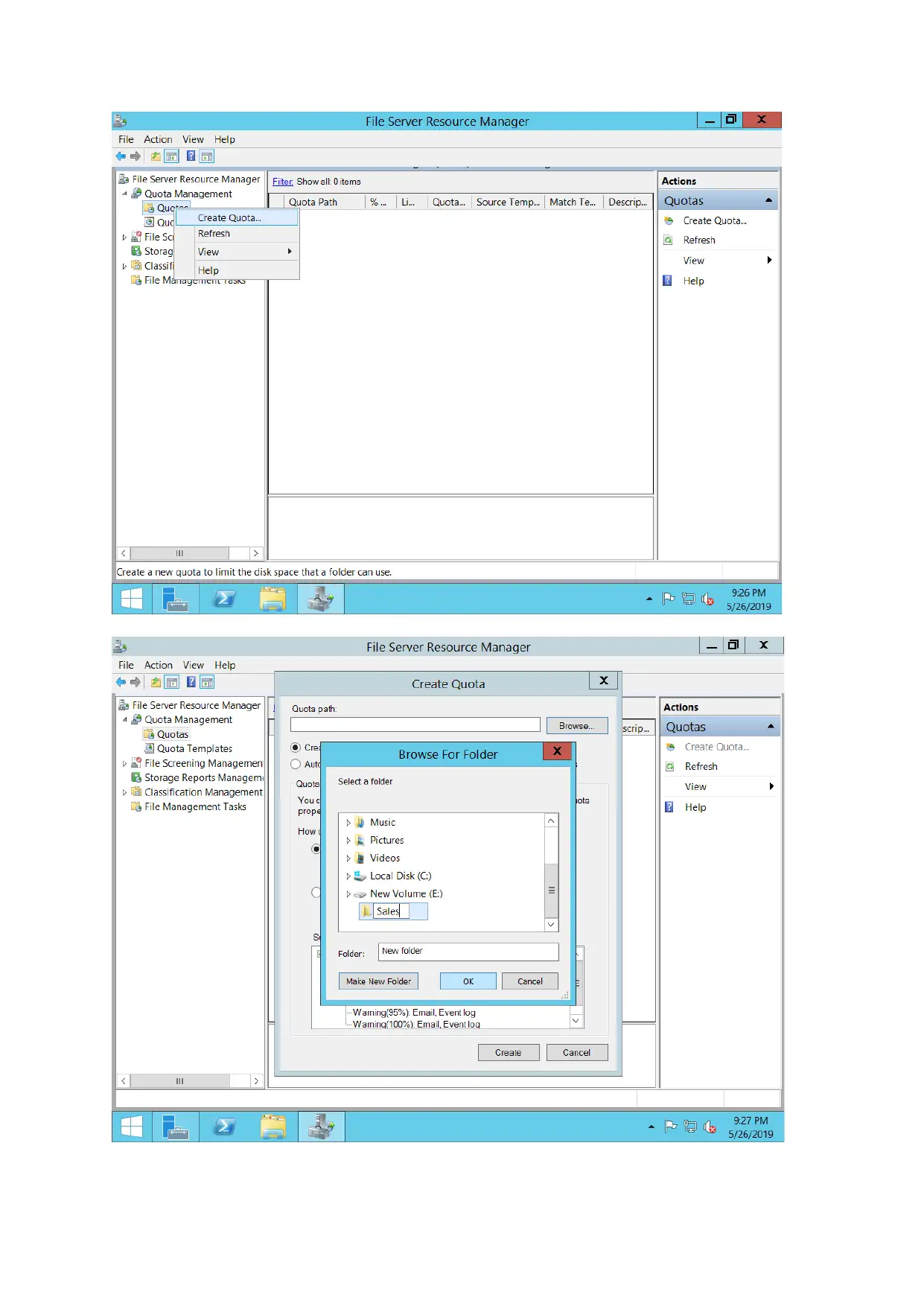
Quota management is considered to configure file server to share files between various
departments. The space is allocated during sharing of information through the network.
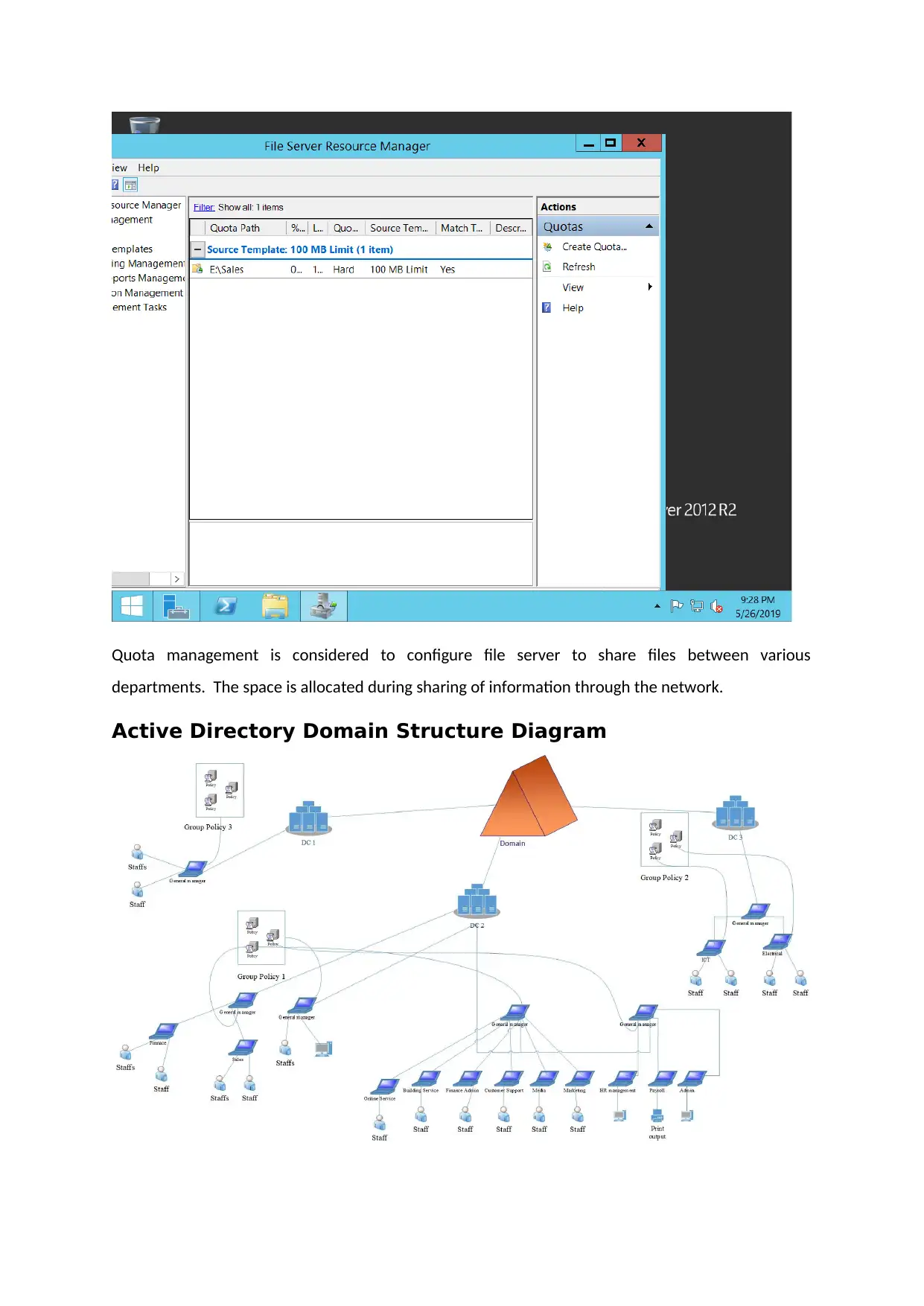
Active Directory Domain Structure Diagram
departments. The space is allocated during sharing of information through the network.
Active Directory Domain Structure Diagram
Secure Best Marks with AI Grader
Need help grading? Try our AI Grader for instant feedback on your assignments.

Summary
In order to design the solution for this network, the IP subnet scheme for five subnets has been
considered. Proper analysis of a number of users has been done accordingly for estimating growth in
the number of users associated with various department for the organization. An important
requirement for this network design is to calculate the range of IP address that is associated with the
VLAN. In order to perform this calculation various department such as marketing sales management
and accounting has been considered. A separate VLAN has been considered for this network design
and this has been done for minimizing traffic condition of the network. Along with that smaller
subnet has been deployed in this design for reducing Broadcast message. It not only improves the
traffic of the network but also increase the network efficiency. In order to make proper configuration
for the Windows Server with DHCP service Security group has been created and this security group is
an important requirement for DHCP server as it provides authorization, which is required for
increasing network security. A client to access DHCP server need to authorize first. For deploying
network service properly DHCP server should be restarted. For configuring DHCP proper plan is
required which in this context is an IP address plan. Range of IP address need to be associated with
each VLAN that is part of the network. However, among valid IP address range, IP address that is
permitted by the network should be considered as the default gateway for VLAN.
This default gateway is an important part of the network as it allows different departments to
communicate with each other through this network. The local area network that is designed for the
organization should provide support for executing various services that organization includes in the
business process and this requirement should be done with perfection as this has a significant
impact on the overall business process of the organization hence efficiency in this context is
required. While providing services through this network it is important to identify that this process is
not effective if the security aspect is not properly assessed and if it is not integrated with the
network solution. Hence enhancing the security of this network is an essential requirement in this
project. If security is not insured it will provide easy access to important data. It is essential for
Organizational process to secure business data, consumer data and important information about the
organization success strategy, market ideas for product development and other important
information that have a significant impact on the competitive advantage of the organization in the
market. Hence, it is important to secure the server, database and other network storage that is
associated with this network infrastructure. In order to enhance efficiency in the organizational
process, this network also provides remote access to the network. However, it is required to restrict
access to the employees of the organization only and any other third party and hackers should not
In order to design the solution for this network, the IP subnet scheme for five subnets has been
considered. Proper analysis of a number of users has been done accordingly for estimating growth in
the number of users associated with various department for the organization. An important
requirement for this network design is to calculate the range of IP address that is associated with the
VLAN. In order to perform this calculation various department such as marketing sales management
and accounting has been considered. A separate VLAN has been considered for this network design
and this has been done for minimizing traffic condition of the network. Along with that smaller
subnet has been deployed in this design for reducing Broadcast message. It not only improves the
traffic of the network but also increase the network efficiency. In order to make proper configuration
for the Windows Server with DHCP service Security group has been created and this security group is
an important requirement for DHCP server as it provides authorization, which is required for
increasing network security. A client to access DHCP server need to authorize first. For deploying
network service properly DHCP server should be restarted. For configuring DHCP proper plan is
required which in this context is an IP address plan. Range of IP address need to be associated with
each VLAN that is part of the network. However, among valid IP address range, IP address that is
permitted by the network should be considered as the default gateway for VLAN.
This default gateway is an important part of the network as it allows different departments to
communicate with each other through this network. The local area network that is designed for the
organization should provide support for executing various services that organization includes in the
business process and this requirement should be done with perfection as this has a significant
impact on the overall business process of the organization hence efficiency in this context is
required. While providing services through this network it is important to identify that this process is
not effective if the security aspect is not properly assessed and if it is not integrated with the
network solution. Hence enhancing the security of this network is an essential requirement in this
project. If security is not insured it will provide easy access to important data. It is essential for
Organizational process to secure business data, consumer data and important information about the
organization success strategy, market ideas for product development and other important
information that have a significant impact on the competitive advantage of the organization in the
market. Hence, it is important to secure the server, database and other network storage that is
associated with this network infrastructure. In order to enhance efficiency in the organizational
process, this network also provides remote access to the network. However, it is required to restrict
access to the employees of the organization only and any other third party and hackers should not

be able to access the network. Hence, file servers of the network have been secured with Central
user authentication services. Another important aspect of network security is to filter network traffic
based on its characteristics. In order to do that Firewall has been integrated with a network, which
will help to identify if the traffic has any security issues, and based on the assessment it will provide
security measures, which will ensure that the network is secured and is not affected by traffic that
might be harmful to the network. It has been recommended that this firewall service should be
consistent with the organizational security policy so that security associated with file server as well
as other network devices are properly insured and maintained for safe and secure access to the
network so that it enhances the organizational process.
Conclusions
This report has analysed various requirements for designing of the network. In-depth analysis of the
requirements has helped in designing the network that is consistent with the business requirements
of the organization. As the network needs to be scalable for supporting growth of users, an detailed
assessment has been done on number of users that needs to be included in the network initially and
in accordance with that network capacity is designed so that it is easier to extend the capacity of the
network for allocating users with the network when required. In order to ensure accuracy in
calculating capacity of the network a range of IP address is calculated that needs to be assigned to
the VLAN. In order to execute this calculation various department such as marketing sales
management and accounting has been considered. A distinct VLAN has been selected for this
network design which is done for decreasing traffic overflow in the network. In this network design,
smaller subnet has been deployed as it reduces Broadcast message. It improves the traffic of the
network and at the same time it also provides context to improve the network efficiency. A client for
accessing DHCP server first need to ensure proper authorization for accessing the server and the
storage of the network. To implement network service properly DHCP server require to restart this
service. To configure an IP address plan is designed in this context. Range of IP address is assigned
with each VLAN which is associated with the network. However, among various IP address range
that is available, IP address that the network support, is considered and this provides the default
gateway for the VLAN.
user authentication services. Another important aspect of network security is to filter network traffic
based on its characteristics. In order to do that Firewall has been integrated with a network, which
will help to identify if the traffic has any security issues, and based on the assessment it will provide
security measures, which will ensure that the network is secured and is not affected by traffic that
might be harmful to the network. It has been recommended that this firewall service should be
consistent with the organizational security policy so that security associated with file server as well
as other network devices are properly insured and maintained for safe and secure access to the
network so that it enhances the organizational process.
Conclusions
This report has analysed various requirements for designing of the network. In-depth analysis of the
requirements has helped in designing the network that is consistent with the business requirements
of the organization. As the network needs to be scalable for supporting growth of users, an detailed
assessment has been done on number of users that needs to be included in the network initially and
in accordance with that network capacity is designed so that it is easier to extend the capacity of the
network for allocating users with the network when required. In order to ensure accuracy in
calculating capacity of the network a range of IP address is calculated that needs to be assigned to
the VLAN. In order to execute this calculation various department such as marketing sales
management and accounting has been considered. A distinct VLAN has been selected for this
network design which is done for decreasing traffic overflow in the network. In this network design,
smaller subnet has been deployed as it reduces Broadcast message. It improves the traffic of the
network and at the same time it also provides context to improve the network efficiency. A client for
accessing DHCP server first need to ensure proper authorization for accessing the server and the
storage of the network. To implement network service properly DHCP server require to restart this
service. To configure an IP address plan is designed in this context. Range of IP address is assigned
with each VLAN which is associated with the network. However, among various IP address range
that is available, IP address that the network support, is considered and this provides the default
gateway for the VLAN.

Bibliography
[1]. Christopher, G.E. and Jack, I.E.K.E. A model of local area network based application for Inter-
office communication. In Proceedings of the World Congress on Engineering and Computer
Science (Vol. 1, pp. 19-21). , 2016.
[2]. Kolahi, S.S. and Almatrook, A.A. Impact of Security on Bandwidth and Latency in IEEE 802.11 ac
Client-to-Server WLAN. In 2017 Ninth International Conference on Ubiquitous and Future
Networks (ICUFN) (pp. 893-897). IEEE. , 2017, July.
[3]. Rajgopal, R. Handbook of Heterogeneous Networking. Auerbach Publications. , 2018.
[4]. Pinnaka, V.V., King, S.A. and Katangur, A.A. SLIP: A Cost-Effective Infrastructure for a Smart
Environment. In 2017 IEEE International Symposium on Parallel and Distributed Processing with
Applications and 2017 IEEE International Conference on Ubiquitous Computing and
Communications (ISPA/IUCC) (pp. 1439-1443). IEEE. , 2017, December.
[5]. Odagiri, K., Shimizu, S., Ishii, N. and Takizawa, M. Establishment of Virtual Policy Based Network
Management Scheme by Load Experimets in Virtual Environment. In 2015 IEEE 29th
International Conference on Advanced Information Networking and Applications (pp. 769-776).
IEEE. , 2015, March.
[6]. Burke, C. Implementation and Evaluation of Virtual Network Functions Performance in the Home
Environment. , 2015.
[7]. Tate, J., Beck, P., Ibarra, H.H., Kumaravel, S. and Miklas, L. Introduction to storage area networks.
IBM Redbooks. , 2018.
[8]. Antony, J., Mathuria, D.S., Datta, T.S. and Maity, T. Development of intelligent instruments with
embedded HTTP servers for control and data acquisition in a cryogenic setup—The hardware,
firmware, and software implementation. Review of Scientific Instruments, 86(12), p.125003. ,
2015.
[9]. Liu, G. and Xu, J. A Metadata Redundancy Approach for File Systems over Lossy Packet-based
Network. Procedia computer science, 131, pp.1196-1201. , 2018.
[10]. Velde, G.V.D. and Gont, F. DHCPv6-Shield: Protecting against Rogue DHCPv6 Servers. , 2015.
[11]. Shete, A., Lahade, A., Patil, T. and Pawar, R. DHCP Protocol Using OTP Based Two-Factor
Authentication. In 2018 2nd International Conference on Trends in Electronics and Informatics
(ICOEI) (pp. 136-141). IEEE. , 2018, May.
[12]. Lawas, J.B.R., Vivero, A.C. and Sharma, A. Network performance evaluation of VPN protocols
(SSTP and IKEv2). In 2016 Thirteenth International Conference on Wireless and Optical
Communications Networks (WOCN) (pp. 1-5). IEEE. , 2016, July.
[1]. Christopher, G.E. and Jack, I.E.K.E. A model of local area network based application for Inter-
office communication. In Proceedings of the World Congress on Engineering and Computer
Science (Vol. 1, pp. 19-21). , 2016.
[2]. Kolahi, S.S. and Almatrook, A.A. Impact of Security on Bandwidth and Latency in IEEE 802.11 ac
Client-to-Server WLAN. In 2017 Ninth International Conference on Ubiquitous and Future
Networks (ICUFN) (pp. 893-897). IEEE. , 2017, July.
[3]. Rajgopal, R. Handbook of Heterogeneous Networking. Auerbach Publications. , 2018.
[4]. Pinnaka, V.V., King, S.A. and Katangur, A.A. SLIP: A Cost-Effective Infrastructure for a Smart
Environment. In 2017 IEEE International Symposium on Parallel and Distributed Processing with
Applications and 2017 IEEE International Conference on Ubiquitous Computing and
Communications (ISPA/IUCC) (pp. 1439-1443). IEEE. , 2017, December.
[5]. Odagiri, K., Shimizu, S., Ishii, N. and Takizawa, M. Establishment of Virtual Policy Based Network
Management Scheme by Load Experimets in Virtual Environment. In 2015 IEEE 29th
International Conference on Advanced Information Networking and Applications (pp. 769-776).
IEEE. , 2015, March.
[6]. Burke, C. Implementation and Evaluation of Virtual Network Functions Performance in the Home
Environment. , 2015.
[7]. Tate, J., Beck, P., Ibarra, H.H., Kumaravel, S. and Miklas, L. Introduction to storage area networks.
IBM Redbooks. , 2018.
[8]. Antony, J., Mathuria, D.S., Datta, T.S. and Maity, T. Development of intelligent instruments with
embedded HTTP servers for control and data acquisition in a cryogenic setup—The hardware,
firmware, and software implementation. Review of Scientific Instruments, 86(12), p.125003. ,
2015.
[9]. Liu, G. and Xu, J. A Metadata Redundancy Approach for File Systems over Lossy Packet-based
Network. Procedia computer science, 131, pp.1196-1201. , 2018.
[10]. Velde, G.V.D. and Gont, F. DHCPv6-Shield: Protecting against Rogue DHCPv6 Servers. , 2015.
[11]. Shete, A., Lahade, A., Patil, T. and Pawar, R. DHCP Protocol Using OTP Based Two-Factor
Authentication. In 2018 2nd International Conference on Trends in Electronics and Informatics
(ICOEI) (pp. 136-141). IEEE. , 2018, May.
[12]. Lawas, J.B.R., Vivero, A.C. and Sharma, A. Network performance evaluation of VPN protocols
(SSTP and IKEv2). In 2016 Thirteenth International Conference on Wireless and Optical
Communications Networks (WOCN) (pp. 1-5). IEEE. , 2016, July.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

[13]. Harborth, D., Herrmann, D., Köpsell, S., Pape, S., Roth, C., Federrath, H., Kesdogan, D. and
Rannenberg, K. Integrating Privacy-Enhancing Technologies into the Internet
Infrastructure. arXiv preprint arXiv:1711.07220. , 2017.
[14]. Lacković, D. and Tomić, M. Performance analysis of virtualized VPN endpoints. In 2017 40th
International Convention on Information and Communication Technology, Electronics and
Microelectronics (MIPRO) (pp. 466-471). IEEE. , 2017, May.
[15]. Jyothi, K.K. and Reddy, B.I. Study on Virtual Private Network (VPN), VPN’s Protocols And
Security. , 2018.
[16]. Pudelko, M. and Gallenmüller, S. Performance Analysis of VPN Gateways
Performanceanalyse von VPN Gateways. , 2018.
Rannenberg, K. Integrating Privacy-Enhancing Technologies into the Internet
Infrastructure. arXiv preprint arXiv:1711.07220. , 2017.
[14]. Lacković, D. and Tomić, M. Performance analysis of virtualized VPN endpoints. In 2017 40th
International Convention on Information and Communication Technology, Electronics and
Microelectronics (MIPRO) (pp. 466-471). IEEE. , 2017, May.
[15]. Jyothi, K.K. and Reddy, B.I. Study on Virtual Private Network (VPN), VPN’s Protocols And
Security. , 2018.
[16]. Pudelko, M. and Gallenmüller, S. Performance Analysis of VPN Gateways
Performanceanalyse von VPN Gateways. , 2018.
1 out of 32
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
© 2024 | Zucol Services PVT LTD | All rights reserved.





