Lucent pharma - Assignment
Added on 2021-06-17
34 Pages4666 Words75 Views
Executive summaryLucent pharma is a pharmaceutical firm in Perth. The network topology used in currently inLucent pharma is analyzed and in the current network many vulnerabilities are present and inthat some used to reduces the effect of the pharmacy is identified and the details about thevulnerabilities are described. In the analysis of security devices best security devices is used toimprove the network security performance and security and the devices placed in the networklocation. Lucent pharma needs to be analyzed if there is any need and sub network purpose isadded. Firewall polices and the rules are created to implement the network and it consists offirewall by the network. IDS/IPS polices and rules for firewall and it is used for cyber security ofthe network and for the Lucent pharma network the additional security policies are added. Thedesign of the proposed secured network is designed for the pharmaceutical firm in MicrosoftVisio. Nmap tool is used for scanning purpose. Using Wire shark tool the traffics are recorded.Commands used for scanning the target server, IP address of the target server, port which usedfor the target server, web server are reported in the form of table. The filter used to extract andexclude the 'HTTP' traffic is analyzed. The major variations between the 'capture Filter' and a'Display Filter' is explained.

Table of ContentsExecutive summary...................................................................................................................................11. Introduction...........................................................................................................................................32. Background...........................................................................................................................................33. part-1: network design..........................................................................................................................44. Part 2: Hands on with Kali Linux and wire shark............................................................................145. Conclusion............................................................................................................................................31References............................................................................................................................................32

1. Introduction In regular day-to-day life, under unauthorized access, malfunctions are used to protectphysical and digital information has been taken several steps to protect the information. Networksecurity is one of the main securities for protecting much information. In country of Australia, alarge city is known as 'Perth’. In that city the Lucent pharma is presented which is a firm ofpharmacy. It has no strong security control, but it implements network topologies. In the Lucentpharma of current topology network, in which many problems has occurred. In the topologynetwork to raise the security and performance the sensible security devices are present withvulnerability low. By locating the network the security devices has placed. For improving thesecurity a software tool of 'Firewall' is used. It has contained codes and policies, which willcreate and implemented in networks by the administrator. There are two security devices ofnetwork and monitoring which is to increase the security level. The first one is IDS stands forIntrusion Detection System and the second one is IPS stands for Intrusion Prevention System.The software’s encloses the cyber-security. For protecting computers and networks leadingtechnologies of Cyber security is used. In the network of Lucent pharma, there are severalsecurity policies are present. Proposed Secure Network Design will be designed for thepharmaceutical firm. For scanning an Nmap tool is used for this network security. In thisnetwork to gather some information of data packets software used is Wire shark which is a Linuxdistribution. The IP address and ports of targets are the commands used for scanning. In thenetwork the complete incoming and outgoing are controlled using Filters by completemonitoring of data packets. Capture filter and Display filter are two types of Filters are used.These filters have some variations on their accessing. The network security and devices has beendiscussed above. 2. BackgroundThe present build network used in Lucent pharma planning will be done. There are manyaffects present in the network and main five faults that reduce the effect of pharmacy will beidentified. The knowledge for choosing the affects are clearly will be explained. By referringmany protect machine, good protect machine will be taken to increase the protect machine andperformance. The machine placed in the network location will be confidentially. Lucent pharma

network needs any partiality into group of platforms will plan and there is any need, sub-networkfor that purpose will be added. Firewall policies and rules will be created to executed in thenetwork consist of firewall by the administrator of network. IDS/IPS policies and rules also willbe generated and network administrator will execute the policies in network. The policies andrules for twice firewall and IDS/IPS will be covered the cyber-security of the network. ForLucent pharma network, ten additional security policies will be devised. The design for‘Proposed security network’ will be created for the pharmaceutical firm in Microsoft VisioNmap tool will be help for scanning purpose. Using wire shark tool the error will be recorded.Commands used scanning the target server. IP address of the target server, port which used forthe target server, web server will be reported in the form of table. The filter used to display andexclude the ‘HTTP’ traffic will be analyzed. The major difference between the ‘capture filter’and a ‘Display Filter’ will be explained.3. part-1: network design1. Analyze the current network topology implemented at ‘Lucent pharma’ and identify fivemajor vulnerabilities that exit in the network. You are also required to provide sound reasoning behind these identified vulnerabilitiesThe internet is used expose the intranet server. Because the attack is possible in many ways. The attack is created in no of choices.We need to protect the web servers in the environment. Intrusion prevention system is used to protect the web server.In this environment antivirus servers are not applicable. So using this operation we can easily protect the environment from virus out breakers. The business critical environment is protected by the user. The users have an ability to access the environment in unlimited times. By using this operation the security risks are easily handled and managedDirect internet access is possible in these users. Users are in direct internet connection, no restrictions are demanded. The whole environment is vulnerable by the above user.

In company network router is the most important resource. Router is act like an entry point in the company networkDifferent types of public facing servers are used. The public facing servers are used to perform DMZ zone.In the DMZ zone they have a DMZ IPS. The DMZ IPS are used to place the firewall in DMZ zone.

The DMZ zone is protected by the firewall. And also VON services are used to protect theDMZ zoneThe entire internal network from the external world is protected by the internal firewalls. So the internal firewalls are used to protect the internal networks.Public facing servers are access by the end users. And also send the external request through the switches.The wired switch is given by the wireless access point. The wireless access point is used to give more additional functionalities.In DMZ zone the proxy servers are applicable. All public facing servers are connected by the standard switch. Web servers, email server, application server, and database server are the types public facing server.The company has a site office. Another router is applicable in this site office.
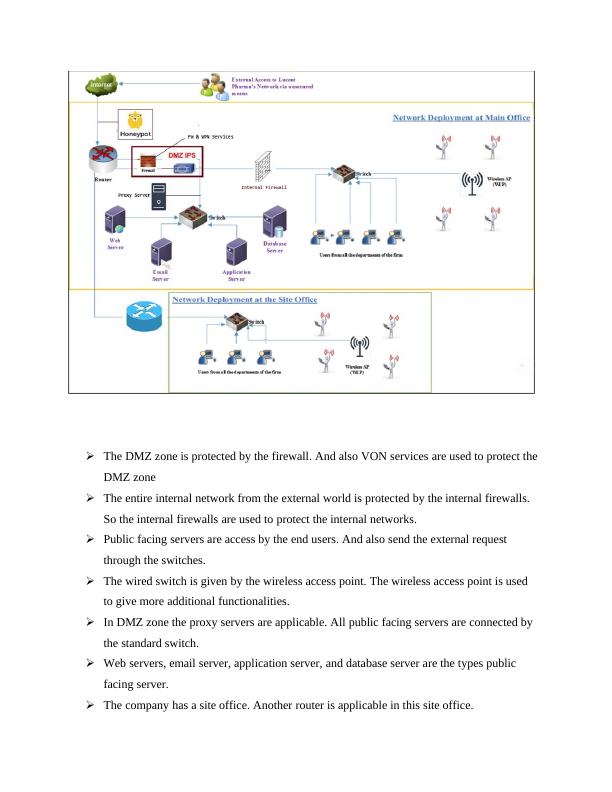
This router is connected by one standard switch and also a wireless access point.The internet is access by the entire user. This operation is done by this wire switch and wireless point.Below are the devices are added in the existing network to compliance the security Firewall The perimeter and internbelowet network is used to install the firewall. The perimeter is the firewall protection. The perimeter firewall protection is used to avoid the external attack in the environment. And also provide permission for access the mission critical application in DMZzone. If you want to access the internet, DMZ servers are used. Between the remote site and server environment the internal firewall is deployed. The remote sites are used to access the server in the DMZ zone. For this operation some specific services are used. These services protect the environment from the external and internal threads.IDS/IPSIDE/IPS devices are used to deploy in inline mode and also close perimeter environment. In perimeter IPS are used to get the resources between the perimeter firewall and the DMZ server. The traffic between the internet and DMZ environment is similar to the DMZ server traffic. We need to through IPS and first run the IPs scanning; the IPS scanning is fully against the threats. IPS functions are in belowAlerts are used to send the application for evaluation and mitigation The malicious code is detected by the traffic code. And also the IP will drop their packetIPS are used to block the traffic from source addressIf we want to reset the connection the IPS are used. And also is used to initiate the attacker.

RouterIn main office the additional routers are installed. These additional routers are used to connect the MPLS links. The main office server is reached by the remote site. MPLS router is used to find the solution.VPN Service: Services are mostly used in perimeter firewall.The VPN service is applicable in the perimeter firewall. The corporate user access the corporate network security done by the VPN service. The user system and corporate servers are encrypted by the VPN services. To identify the traffic content don’t use ISP. ISP is not applicable for traffic detection.Yes lucent pharma requires network segmentation. In lucent pharma environment multiple domains are used. Each and every domain is used to protect the resources. Below table represent the topology and network segmentation. Below are the topology and network segmentationNetwork SegmentationZone NameDescriptionApp ZoneApplication serverDP ZoneData Base serversWeb ZoneWeb serversExtranetEmail & Proxy serversIntranetRemote Offices

End of preview
Want to access all the pages? Upload your documents or become a member.
Related Documents
Desklib - Online Library for Study Material with Solved Assignments, Essays, Dissertationslg...
|20
|3651
|133
Network Security Fundamentals: Vulnerabilities, Security Devices, Policies and Morelg...
|19
|3735
|380
Assignment | Cyber Securitylg...
|23
|2174
|14
Analysis of Host Discovery Assignment 2022lg...
|22
|1377
|21
Network Security Fundamentals - Vulnerabilities, Devices, Segregation, Firewall Policies and Ruleslg...
|21
|4427
|443
Network Vulnerability And Cyber Securitylg...
|15
|1453
|15