Network Management: Importance, Protocols, and Standards
VerifiedAdded on 2021/07/28

Working with an outdated network can have disastrous results on productivity. How can we
make sure that our network is ahead of the curve rather than falling behind? Regular network
maintenance is the simplest way to comprehensively check our network’s capabilities.
Consistent, thorough network maintenance and management administered by support specialists
give our team the opportunity to stay ahead of potential roadblocks and avoid issues that might
hamper productivity and increase downtime. Here are some reasons why network management
and maintenance services are crucial to your IT environment:
Threat Detection: Whether we bought our hardware one week or one year ago, there’s a
chance that our network may be susceptible to threats from harmful external agents.
Sophisticated phishing scams and other outside threats can have disastrous results on
your network—staying ahead of any given issue is crucial for maintaining a secure, fully-
functioning network. Don’t let a preventable issue take down your entire network!
Virus and Malware Prevention: If your network management system isn’t alerting you
to oncoming threats, then it’s not doing its job. Your network security should actively
work to not only repel threats but lessen your chances of future attacks. A trained
professional network management consultant can help you identify threats like phishing,
viruses, and malware to keep everything running smoothly.
Maximum Efficiency: No matter how recently you’ve implemented a new network
operating system, before long it will become sluggish relative to newer, more modern
iterations. Consistent network maintenance gives you the satisfaction of knowing that
your IT environment is running as well as it possibly can due to frequent check-ups and
updates. If your network isn’t adjusting to accommodate your needs for data storage,
speed, and accessibility, then it’s time to reevaluate and have a professional come in and
take a look.
System Updates: From antivirus software to remote accessibility, updating your network
for optimal performance is crucial for sustained success and avoiding costly repairs.
Frequent network maintenance and management is the easiest way to put your network in
the best position for repelling threats and increasing productivity. You wouldn’t drive a
car that’s not fit for the road; don’t operate a computer that’s not optimized for modern
usage.
Page | 1
Paraphrase This Document

Preventing network outages before they happen: A network outage is one of the worst
nightmares of any network administrator. Network monitoring solutions can help
companies prevent an outage before it happens. A monitoring tool will sweep your
network for any suspicious performance behavior that indicates an outage is about to
happen. If a device or portion of your network is lagging in performance, your
monitoring solution will detect the problem and alert you to it.
Reducing performance failure time: Your company will most likely discover a major
network performance issue on its own eventually, but it could take a long time to fix the
issue after it’s discovered. A monitoring solution will inform your team of issues as they
happen, drastically reducing the time it takes for your enterprise to discover problems.
Your company can also reduce the mean time to repair (MTTR) of network performance
issues; many monitoring solutions will apply diagnostics to issues it discovers so
employees will understand the issue before investigating it themselves.
Generating network performance reports: Monitoring solutions deliver visualizations
on key performance metrics. Any decent monitoring tool will automatically generate
performance reports for your company to review. These reports should include both
recent and historical data so your company can analyze your network performance over
time. In addition, some monitoring solutions allow you to customize reports to focus on
metrics that matter to your enterprise.
Discovering security threats on your network: A monitoring tool isn’t just useful for
tracking the performance of your systems; they also help your enterprise to deal with
security threats that invade your network. With a monitoring tool, your company will be
alerted to events that indicate malware is present on your system (abnormal data
transfers, failing systems, etc.). Some vendors will also include network detection and
response (NDR) capabilities, which search for harmful actors on a network and take steps
to eliminate them.
Maintaining full network visibility: In order to truly understand your network
performance, your enterprise needs to be able to observe every area of your network. A
Page | 2

issues that might affect your entire system. Monitoring solutions automatically detect
devices that connect to a network, drawing and updating visual maps that display insights
into the performance of your network nodes.
https://solutionsreview.com/network-monitoring/why-is-network-monitoring-important-for-
enterprises/
Business Leads: Managing a network is an excellent approach to acquire new business
leads. Using the contacts, you can get in touch with your clients to open doors for new
business opportunities. Connect professionally when you follow up on leads, as SMBs
and enterprises level businesses always look for outsourcing companies to manage their
network. Always be on time and use common courtesy while following up with your
contacts.
Identify Best Practices: Network monitoring is the best way to determine the best
practices or industry benchmark for business. Learning from what others do is a
significant strategy for your company. Network management services ensure that your IT
infrastructure management tools and devices work smoothly. Monitoring helps you to
recognize the existence and changes within your organization’s IT. It also assists you to
define the importance of latest technologies for your business.
New Business Trends: Networking can help you stay ahead in this competitive era of
advancing technology and new business trends in your industry. These relationships and
“inside” information can add advantage to your business over your competitors by
applying new and fresh methods of doing things. It also allows businesses to generate
new leads, whether it is a new partner for future project or a new customer.
Save Money: A professional network team can save you lots of money with their
expertise, knowledge and resourceful network management skills. They keep themselves
up-to-date with the latest technological trends of network industry that can create
opportunities for you. By being proactively associated with your IT infrastructure, you
can be sure that you will encounter less downtime and achieve enhanced productivity.
Accelerated Growth: Services provided by a network solution provider can help your
business become poised for an increased growth. With a tailored, scalable, and reliable
network services in place, your organization will be able to acknowledge possibilities for
Page | 3
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

help transition larger scale operations for your organization.
Proactively Managed Network: Rather than answering reactively, your network
management services will work proactively. The network service provider will determine
the weakness of your IT infrastructure and handle those problems appropriately before
they expand to a crisis point. To manage the network dynamically, network solution
providers consider real-time and historical reporting of your network’s usage and its
statistics.
A precisely set up network helps is raising your business through technology performance,
diminishes overall cost and empowers focus on internal IT resources, so that you can pay heed to
business growth initiatives instead of building and managing network infrastructure.
https://www.algolitsolutions.com/blog/importance-of-network-management/
Page | 4
Paraphrase This Document

TCP/IP, HTTP, DNS, DHCP, SSL, IPSec, IEEE, ITU, ISO, OSI including IANA and
ICANN.
A network protocol is an established set of rules that determine how data is transmitted between
different devices in the same network. Essentially, it allows connected devices to communicate
with each other, regardless of any differences in their internal processes, structure or design.
Network protocols are the reason you can easily communicate with people all over the world,
and thus play a critical role in modern digital communications.
Similar to the way that speaking the same language simplifies communication between two
people, network protocols make it possible for devices to interact with each other because of
predetermined rules built into devices’ software and hardware. Neither local area networks
(LAN) nor wide area networks (WAN) could function the way they do today without the use of
network protocols.
Network protocols are typically created according to industry standard by various networking or
information technology organizations.
Network management protocols define and describe the various procedures needed to effectively
operate a computer network. These protocols affect various devices on a single network —
including computers, routers and servers — to ensure each one, and the network as a whole,
perform optimally.
The functions of network management protocols include the following:
Connection: These protocols establish and maintain stable connections between different
devices on the same network.
Link aggregation: Link aggregation protocols allow you to combine multiple network
connections into one link between two devices. This works to increase the strength of the
connection and helps sustain the connection should one of the links fail.
Troubleshooting: Troubleshooting protocols allow network administrators to identify
errors affecting the network, evaluate the quality of the network connection, and
determine how administrators can fix any issues.
Page | 5

Network protocols aren’t only relevant to certified network specialists or IT professionals.
Billions of people use network protocols daily, whether they know it or not. Every time you use
the internet, you leverage network protocols. Though you may not know how network protocols
work or how frequently you encounter them, they are necessary for using the internet or digital
communications in any capacity. https://www.comptia.org/content/guides/what-is-a-network-
protocol
Network Protocols:
SNMP: SNMP (Simple Network Management Protocol) is an application layer protocol used
to manage nodes, like servers, workstations, routers, switches, etc., on an IP network. SNMP
enables network admins to monitor network performance, identify network glitches, and
troubleshoot them. SNMP protocol is comprised of three components: a managed device, an
SNMP agent, and an SNMP manager. Currently, there are three versions of SNMP: SNMP
v1, SNMP v2, and SNMP v3. Both versions 1 and 2 have many features in common, but
SNMP v2 offers enhancements such as additional protocol operations. SNMP version 3
(SNMP v3) adds security and remote configuration capabilities to the previous versions.
NETCONF: Network Configuration Protocol (NETCONF) is a standard transport protocol
that communicates with network devices. NETCONF provides mechanisms to edit
configuration data and retrieve operational data from network devices. The configuration
data represents the way interfaces, routing protocols and other network features are
provisioned. The operational data represents the interface statistics, memory utilization,
errors, and so on. NETCONF uses an Extensible Markup Language (XML)-based data
encoding for the configuration data, as well as protocol messages. It uses a simple RPC-
based (Remote Procedure Call) mechanism to facilitate communication between a client and
a server. The client can be a script or application that runs as part of a network manager. The
server is a network device such as a router. NETCONF defines how to communicate with the
devices, but does not handle what data is exchanged between the client and the server.
Page | 6
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

configuration/guide/b-programmability-cg-ncs6000-71x/b-programmability-cg-ncs6000-
71x_chapter_010.pdf
RMON: Remote Monitoring (RMON) is a standard specification that facilitates the
monitoring of network operational activities through the use of remote devices known as
monitors or probes. RMON assists network administrators (NA) with efficient network
infrastructure control and management.
TCP/IP: TCP (Transmission Control Protocol/Internet Protocol) is a transport layer protocol
that provides a reliable stream delivery and virtual connection service to applications through
the use of sequenced acknowledgement. TCP is a connection-oriented protocol, as it requires
a connection to be established between applications before data transfer. Through flow
control and acknowledgement of data, TCP provides extensive error checking. TCP ensures
sequencing of data, meaning the data packets arrive in order at the receiving end.
Retransmission of lost data packets is also feasible with TCP.
UDP: UDP (User Datagram Protocol) is a connection-less transport layer protocol that
provides a simple but unreliable message service. Unlike TCP, UDP adds no reliability, flow
control, or error recovery functions. UDP is useful in situations where the reliability
mechanisms of TCP are not necessary. Retransmission of lost data packets isn't possible with
UDP.
IP: IPv4 i.e., Internet Protocol (IPv4) is a network layer protocol that contains addressing
and control information, which helps packets be routed in a network. IP works in tandem
with TCP to deliver data packets across the network. Under IP, each host is assigned a 32-bit
address comprised of two major parts: the network number and host number. The network
number identifies a network and is assigned by the internet, while the host number identifies
a host on the network and is assigned by a network admin. The IP is only responsible for
delivering the packets, and TCP helps puts them back in the right order.
Page | 7
Paraphrase This Document

network layer protocol that possesses addressing and control information for enabling
packets to be routed in the network. IPv6 was created to deal with IPv4 exhaustion. It
increases the IP address size from 32 bits to 128 bits to support more levels of addressing.
HTTP: HTTP (Hyper Text Transfer Protocol) is an application layer protocol used for
distributed, collaborative, and hypermedia information systems. It works on a client-server
model, where the web browser acts as the client. Data such as text, images, and other
multimedia files are shared over the World Wide Web using HTTP. As a request and
response type protocol, the client sends a request to the server, which is then processed by the
server before sending a response back to the client. HTTP is a stateless protocol, meaning the
client and server are only aware of each other while the connection between them is intact.
After that, both the client and server forget about each other's existence. Due to this
phenomenon, the client and server can't both retain information between requests.
DNS: Domain Name System protocol, The DNS protocol helps in translating or mapping
host names to IP addresses. DNS works on a client-server model, and uses a distributed
database over a hierarchy of name servers. Hosts are identified based on their IP addresses,
but memorizing an IP address is difficult due to its complexity. IPs are also dynamic, making
it all the more necessary to map domain names to IP addresses. DNS helps resolve this issue
by converting the domain names of websites into numerical IP addresses.
DHCP: DHCP (Dynamic Host Configuration Protocol) is a communication protocol that
enables network administrators to automate the assignment of IP addresses in a network. In
an IP network, every device connecting to the internet requires a unique IP. DHCP lets
network admins distribute IP addresses from a central point and automatically send a new IP
address when a device is plugged in from a different place in the network. DHCP works on a
client-server model.
SSL: SSL, or Secure Sockets Layer, is an encryption-based Internet security protocol. It was
first developed by Netscape in 1995 for the purpose of ensuring privacy, authentication, and
Page | 8

modern TLS encryption used today. A website that implements SSL/TLS has "HTTPS" in its
URL instead of "HTTP." https://www.cloudflare.com/learning/ssl/what-is-ssl/
IPsec: Internet Protocol Security (IPsec) sets up encrypted, authenticated IP connections over
a virtual private network (VPN). Technically IPsec is not a protocol, but rather a collection of
protocols that includes the Encapsulating Security Protocol (ESP), Authentication Header
(AH), and Security Associations (SA).
https://www.manageengine.com/network-monitoring/network-protocols.html
Network Standards:
Networking standards define the rules for data communications that are needed for
interoperability of networking technologies and processes. Standards help in creating and
maintaining open markets and allow different vendors to compete on the basis of the quality of
their products while being compatible with existing market products.
Types of Standards
De facto − These are the standards that are followed without any formal plan or approval
by any organization. They have come into existence due to traditions or facts. For
example, the HTTP had started as a de facto standard.
De jure − These standards are the ones which have been adopted through legislation by
any officially recognized standards organization. Most of the communication standards
that are used today are de jure standards. https://www.tutorialspoint.com/Network-
Standardization
Standards Organizations:
International Telecommunication Union (ITU)
The International Telecommunication Union (ITU) is made up of telecommunication policy
makers and regulators, network operators, equipment manufacturers, hardware and software
developers, regional standards-making organizations, and financing institutions. The activities,
policies, and strategic direction of the ITU are determined and shaped by the industry it serves.
Page | 9
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

Standardization (ITU-T), and Telecommunication Development (ITU-D).
ITU-R draws up the technical characteristics of terrestrial and space-based wireless
services and systems, and develops operational procedures. It also undertakes the
important technical studies, which serve as a basis for the regulatory decisions made at
radio communication conferences.
ITU-T experts prepare the technical specifications for telecommunication systems,
networks, and services, including their operation, performance, and maintenance. Their
work also covers the tariff principles and accounting methods used to provide
international service.
ITU-D experts focus their work on the preparation and development of recommendations,
opinions, guidelines, handbooks, manuals and reports. These documents provide decision
makers with "best business practices" relating to a host of issues ranging from
development strategies and policies to network management.
Each of the three ITU sectors works through conferences and meetings at which members
negotiate the agreements that serve as the basis for the operation of global telecommunication
services. The activities of the ITU cover all aspects of telecommunication: setting standards that
facilitate seamless interworking of equipment and systems on a global basis; adopting
operational procedures for the vast and growing array of wireless services; and designing
programs to improve telecommunication infrastructure in the developing world.
http://etutorials.org/Networking/Lan+switching+first-step/
Chapter+2.+Network+Models+and+Standards/Network+Standards/
ISO:
ISO stands for International Organization for Standardization, is a nongovernmental organization
based in Geneva, Switzerland, that has representatives from about 130 countries and is
responsible for developing a variety of international standards in science and engineering. The
International Organization for Standardization (ISO), established in 1947, runs almost 3000
different working groups and committees covering a broad range of standards issues.
Page | 10
Paraphrase This Document

services and systems, to ensure quality, safety and efficiency. They are instrumental in
facilitating international trade. ISO has published 22782 International Standards and related
documents, covering almost every industry, from technology, to food safety, to agriculture and
healthcare. ISO International Standards impact everyone, everywhere.
https://networkencyclopedia.com/international-organization-for-standardization-iso/
IEEE (Institute of Electrical and Electronics Engineers)
IEEE 802 is a collection of networking standards that cover the physical and data-link layer
specifications for technologies such as Ethernet and wireless. These specifications apply to local
area networks (LAN) and metropolitan area networks (MAN). IEEE 802 also aids in ensuring
multi-vendor interoperability by promoting standards for vendors to follow. Essentially, the
IEEE 802 standards help make sure internet services and technologies follow a set of
recommended practices so network devices can all work together smoothly.
Without these standards, equipment suppliers could manufacture network hardware that would
only connect to certain computers. It would be much more difficult to connect to systems not
using the same set of networking equipment. Standardizing protocols help ensure that multiple
types of devices can connect to multiple network types. It also helps make sure network
management isn't the challenge it could be if it wasn't in place. IEEE 802 will also coordinate
with other international standards, such as ISO, to help maintain international standards. In
addition, the "802" in IEEE 802 does not stand for anything with high significance. 802 was just
the next numbered project.
Example of IEEE 802 uses: The IEEE 802 specifications can be used by commercial
organizations to ensure their products maintain any newly specified standards. So, for example,
the 802.11 specification that applies to Wi-Fi could be used to make sure Wi-Fi devices work
together under one standard. In the same way, IEE 802 can help maintain local area network
standards.
https://searchnetworking.techtarget.com/reference/IEEE-802-Wireless-Standards-Fast-Reference
Page | 11

To understand the nuances of network protocols, it's imperative to know about the Open Systems
Interconnection (OSI) model first. Considered the primary architectural model for internet
working communications, the majority of network protocols used today are structurally based on
the OSI model.
The OSI model splits the communication process between two network devices into 7 layers. A
task or group of tasks is assigned to each of these 7 layers. All the layers are self-contained, and
the tasks assigned to them can be executed independently.
Page | 12
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
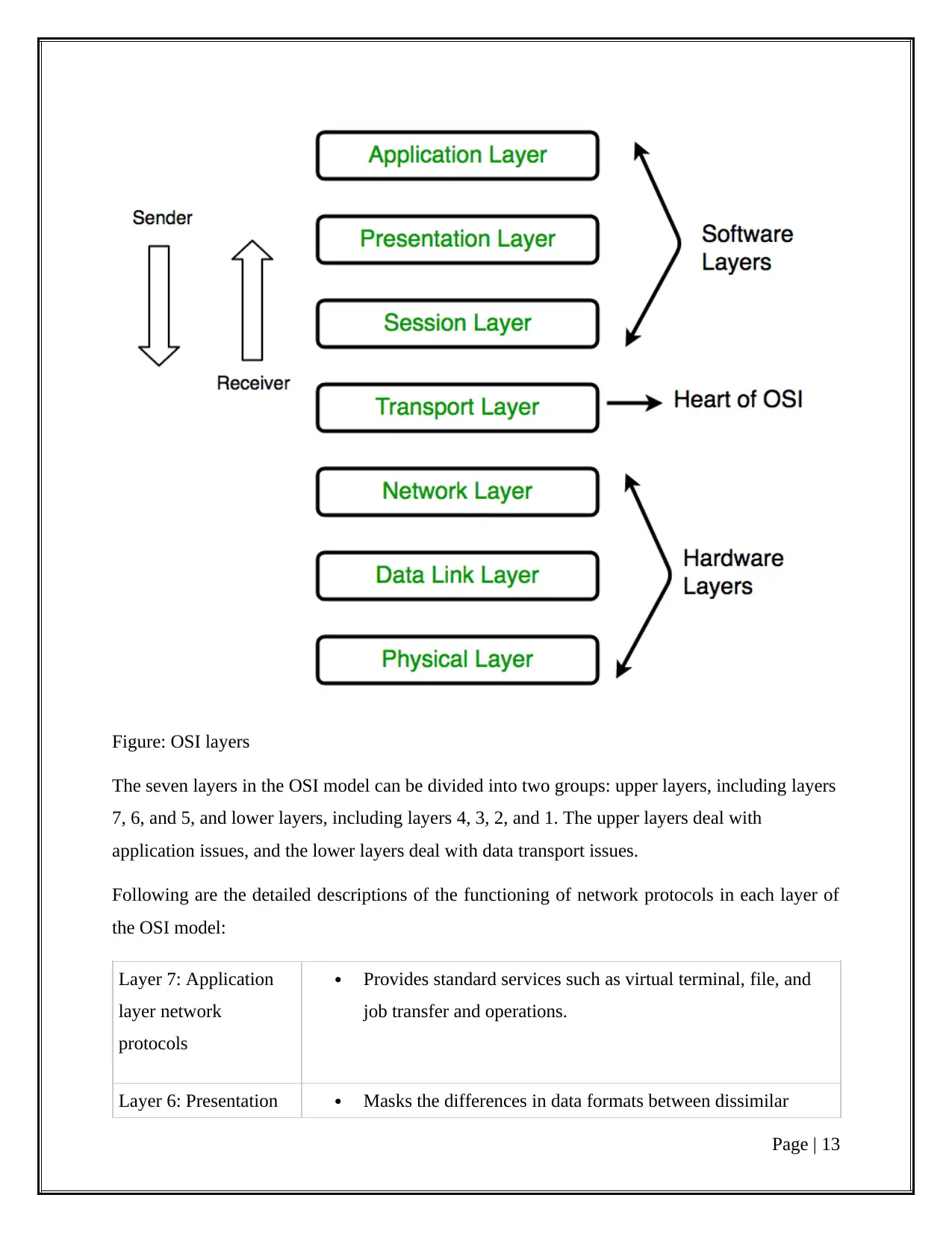
The seven layers in the OSI model can be divided into two groups: upper layers, including layers
7, 6, and 5, and lower layers, including layers 4, 3, 2, and 1. The upper layers deal with
application issues, and the lower layers deal with data transport issues.
Following are the detailed descriptions of the functioning of network protocols in each layer of
the OSI model:
Layer 7: Application
layer network
protocols
Provides standard services such as virtual terminal, file, and
job transfer and operations.
Layer 6: Presentation Masks the differences in data formats between dissimilar
Page | 13
Paraphrase This Document
protocols
systems.
Encodes and decodes data, encrypts and decrypts data, and
compresses and decompresses data.
Layer 5: Session layer
network protocols
Manages user sessions and dialogues.
Establishes and terminates sessions between users.
Layer 4: Transport
layer network
protocols
Manages end-to-end message delivery in networks.
Renders reliable and sequential packet delivery through error
recovery and flow control mechanisms.
Layer 3: Network layer
protocols
Routes packets according to unique network device addresses.
Renders flow and congestion control to prevent network
resource depletion.
Layer 2: Data link
layer network
protocols
Frames packets.
Detects and corrects packet transmit errors.
Layer 1: Physical layer
network protocols
Interfaces between network medium and devices.
Defines optical, electrical, and mechanical characteristics.
Table: Layers of OSI with their standards.
https://www.manageengine.com/network-monitoring/network-protocols.html
IANA
For the billions of devices and many thousands of networks that make up the Internet to connect
with each other, they must agree upon a variety of standards, protocols, and associated protocol
parameters (values or identifiers) which support that communication. For example, when you
send an email with an attachment the servers used to transmit and receive the message each have
an Internet protocol (IP) address. Your email address and the receiving email address each have a
domain name (everything after the “@” symbol). And, a specific protocol parameter value
indicates the kind of file attached so your email reader will know which program to use to open
Page | 14

and reached, that services are mediated, and errors are detected; and, in general, that the
transaction is successful.
IANA, the Internet Assigned Numbers Authority, is an administrative function of the Internet
that keeps track of IP addresses, domain names, and protocol parameter identifiers that are used
by Internet standards. Some of these identifiers are parameters, such as those used by Internet
protocols (like TCP, ICMP or UDP) to specify functions and behavior; some of them represent
Internet addresses; and others represent domain names. Regardless of the type of identifier, the
IANA function (IANA for short below) ensures that values are managed for uniqueness and
made available in publicly-accessible registries so there can be no confusion.
Basically, IANA is about managing and ensuring the global uniqueness of protocol parameters,
internet protocol addresses and internet domain names if internet identifiers.
https://www.internetsociety.org/resources/doc/2014/iana-functions-the-basics/
ICANN
To reach another person on the Internet you have to type an address into your computer - a name
or a number. That address has to be unique so computers know where to find each
other. ICANN coordinates these unique identifiers across the world. Without that coordination
we wouldn't have one global Internet.
ICANN was formed in 1998. It is a not-for-profit partnership of people from all over the world
dedicated to keeping the Internet secure, stable and interoperable. It promotes competition and
develops policy on the Internet’s unique identifiers.
ICANN doesn’t control content on the Internet. It cannot stop spam and it doesn’t deal with
access to the Internet. But through its coordination role of the Internet’s naming system, it does
have an important impact on the expansion and evolution of the Internet.
ICANN plays a similar administrative role with the IP addresses used by computers as it does
with the domain names used by humans. In the same way that you cannot have two domain
names the same (otherwise you never know where you would end up), for the same reason it is
also not possible for there to be two IP addresses the same.
Page | 15
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
supplied to avoid repetition or clashes. ICANN is also the central repository for IP addresses,
from which ranges are supplied to regional registries who in turn distribute them to network
providers.
https://www.icann.org/resources/pages/what-2012-02-25-en
Page | 16
Paraphrase This Document

I am choosing SNMP and RMON protocols for the analysis of their benefits and limitations.
SNMP
Simple Network Management Protocol (SNMP) is an application–layer protocol defined by the
Internet Architecture Board (IAB) in RFC1157 for exchanging management information
between network devices. It is a part of Transmission Control Protocol/Internet Protocol
(TCP/IP) protocol suite.
SNMP is one of the widely accepted network protocols to manage and monitor network
elements. Most of the professional–grade network elements come with bundled SNMP agent.
These agents have to be enabled and configured to communicate with the network monitoring
tools or network management system (NMS).
SNMP ports are utilized via UDP 161 for SNMP Managers communicating with SNMP Agents
(i.e. polling) and UDP 162 when agents send unsolicited Traps to the SNMP Manager.
Limitations of SNMP Management
One of the chief limitations of SNMP network management comes from its focus on device-
specific metrics. While these are essential to understanding device status, they are siloed from
other infrastructure data sets such as traffic flow records. In addition, SNMP monitoring doesn't
provide any insight into user experience or digital experience.
See how ThousandEyes' top rated network monitoring can help you to complement your current
internal network SNMP monitoring practices with a top-down approach to Digital Experience
Monitoring that incorporates app experience, end-to-end network metrics, network paths,
Internet routing and outage insights, plus SNMP device layer status and context.
https://www.thousandeyes.com/learning/techtorials/snmp-simple-network-management-protocol
The cons of SNMP, which are small compared to its openness, include security risks that are
normal whenever using an open standard. There is "security through obscurity" linked with any
little-used communications standard. Still, the release of SNMPv3 added new encryption and
privacy options that had never before existed within SNMP. SNMP is a rather detailed protocol.
Page | 17

rendered quite small in most applications, since bandwidth has skyrocketed in recent years.
https://www.dpstele.com/snmp/remote-monitoring.php
The advantages of SNMP
Odds are most, if not all, of the devices on your network are SNMP compatible. However, if you
haven’t already configured them for SNMP, it’s most likely not yet enabled on them. SNMP
requires that you manually turn it on for each device. This is to eliminate the security risk of
accidentally running an insecure SNMP protocol.
There are plenty of reasons to enable SNMP, however, including:
Standardized device monitoring, eliminating the need for complex monitoring
configurations
Vendor less monitoring (meaning devices from any manufacturer are recognized)
Automatic parameter monitoring
Real-time status updates
Centralized management location – all the data can be sent to and processed at one area on
your network
https://solutionsreview.com/network-monitoring/simple-network-management-protocol-the-
basics/
The main advantage of SNMP is that it is an open standard. Open protocols are designed to
combat the wasted effort and costs when one manufacturer develops its own "proprietary"
protocol that only it will support. Anyone who buys remote monitoring devices that use these
protocols is asking for trouble. The manufacturer may raise prices with little threat of damaging
sales volume, since they are "the only game in town." Worse yet, the manufacturer may close up
shop. At this point, there is no way to get new products or parts to add or repair your remote
monitoring system. You'll most likely end up suffering with a dead-end system rather then
switching over to a new system all at once. There's no way to gradually transition between
systems if one side doesn't work with the other.
Page | 18
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

In a mobile age, you and your staff are not always in a physical office. Sometimes you're in the
field. Sometimes you work from home. Maybe you have IT staff who work remotely and want
remote network monitoring access. Can you give key IT personnel access to your network
management tools from anywhere, without risking security breaches? Your organization needs
the benefits of remote monitoring.
RMON uses certain network devices, such as servers, and contains network management
applications that serve as clients. RMON controls the network by using its servers and
applications simultaneously. When a network packet is transmitted, RMON facilitates packet
status viewing and provides further information, in the event that a packet is blocked, terminated
or lost.
Advantages
You can monitor remote offices wherever they're located.
If your network span’s multiple locations, a remote network monitoring software allows you to
manage devices in every location. For instance, let's say you manage the network for a school
district with various campuses, or are monitoring local and regional branches of a financial
institution. Remote monitoring tools give you visibility into how devices in your central location,
as well as all the remote locations, are performing. You can also get alerts wherever and
whenever performance falters. To easily distinguish office or branch locations, you can set up
location-specific network maps tracking device statuses for that particular location.
Remote network management capabilities are especially helpful for companies who have a small
team stationed in one spot but are responsible for managing the entire network. With remote
network access, if a device goes down, you don’t have to travel to that location to troubleshoot.
This saves IT administrators time, increases your productivity, and enables you to rest easy
knowing the whole network is under your surveillance.
Consultants responsible for monitoring client networks and managed service providers (MSPs)
also benefit from the ability to monitor a remote location without being on site.
IT staff in other offices can monitor the network in real time.
Page | 19
Paraphrase This Document

network performance, remote access enables those IT staff in other offices, cities, branches, or
even countries to view network performance in real-time—even if the software server is installed
at headquarters.
This means if a device goes down at a remote location, a network guy located there can
troubleshoot without necessarily getting you involved. He also doesn’t have to bother you to ask
what you’re seeing on your end—he can see up-to-date network maps and metrics for himself.
You and your IT staff can be mobile without risking network neglect.
Having remote access to the network means your IT team doesn’t have to be on-site constantly.
If you need to work from the coffee shop or at home, with remote access to the network you can
still see the status of network devices on your laptop or mobile device. Mobile network
monitoring keeps network data at your fingertips so you never risk outages from lack of access.
Access levels can be managed to ensure security.
Some network administrators may balk at the idea of remote access because of potential security
threats to the network. One way to secure the network is to require encrypted authentication and
make sure that every user has to log in the same way.
Another safeguard against security issues is the ability to customize user access. Most remote
network monitoring tools allow you to give access at the admin or user level to certain maps or
dashboards. Managing access for your users helps tremendously to keep the connection secure.
Also, find a tool that will update and provide patches whenever security holes surface. Although
security threats are a fact of life, good tools will quickly notify users when a patch has been
released so you can take advantage of increased security measures as soon as possible.
With proper connectivity, you’ll always have access.
To get remote access benefits, it simply requires… access. As long as you have direct access to
the network via VPN connectivity or point to point, you’ll be able to manage and monitor all the
critical devices within your network. Regardless of where you or they are located.
Page | 20

yourself the kind of flexibility that the modern work world requires. You also gain peace of mind
that no matter where you are, you can see the whole network at a glance, whether it spans a city,
country, or the world.
If you’re managing the network across locations or on the go, it’s clear that remote monitoring is
essential. Do you have the right tools? Remote network monitoring software can give you the
visibility you need to monitor a widespread network.
https://www.helpsystems.com/resources/articles/top-5-benefits-remote-network-monitoring
Disadvantages of Remote Network Monitoring
The amount of information given to you will not be enough for you to fix every problem.
The system that you use to retrieve the data may be extremely slow. This means that the system
will not be kind to your allotted bandwidth. The remote network monitoring system registers
may be stored in 32-bit registers. This may not be enough for you.
Complete remote network monitoring support in your hardware is only available for dedicated
RISC processors. http://www.networkmonitoring.org/remote-network-monitoring/
Open-source network monitoring tools offer better reports than in the past, but some don't allow
for enough customization. In those cases, it can be difficult to export data to create external
reports. And, unlike their commercial counterparts, open-source network monitoring tools don't
typically come with an army of customer support specialists.
RMON features limitation by Huawei
If the alarm variables configured in RMON alarm function are MIB variables defined in
the statistics group or history group, the Ethernet or history statistics collection must be
configured on the monitored Ethernet interface first.
XGE interfaces connected to the ET1D2IPS0S00, ET1D2FW00S00, ET1D2FW00S01,
ET1D2FW00S02, or ACU2 cards do not support RMON and RMON2.
https://support.huawei.com/enterprise/en/doc/EDOC1000178113/4320ec/licensing-
requirements-and-limitations-for-rmon-and-rmon2
Page | 21
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
© 2024 | Zucol Services PVT LTD | All rights reserved.