Manage Network and Data Integrity
VerifiedAdded on 2023/04/21
|18
|2078
|261
AI Summary
This audit report results to security audit of Comtech Company. The evaluation of hardware and software has been conducted so as to identify weaknesses which can be misused by attackers. The results of this security assessment audit report will lead to the implementation of basic IT security within the organization.
Contribute Materials
Your contribution can guide someone’s learning journey. Share your
documents today.

Running head: MANAGE NETWORK AND DATA INTERITY
ICTNWK403: MANAGE NETWORK AND DATA INTERGITY
(Student’s Name)
(Institutional Affiliation)
(Date)
ICTNWK403: MANAGE NETWORK AND DATA INTERGITY
(Student’s Name)
(Institutional Affiliation)
(Date)
Secure Best Marks with AI Grader
Need help grading? Try our AI Grader for instant feedback on your assignments.

MANAGE NETWORK AND DATA INTEGRITY 2
Executive summary
This audit report results to security audit of Comtech Company. The evaluation of
hardware and software has been conducted so as to identify weaknesses which can be misused
by attackers. The results of this security assessment audit report will lead to the implementation
of basic IT security within the organization.
Assessment 1: Project
Introduction
Comtech is an IT based company located in Melbourne. The company is involved in the
provision of professional IT services and support. The company has been operating since 2000
with various branches in Australia. The company has about twenty computers, two modems, and
two printers. As a system asset auditor, I will prepare an IT asset audit record for the company
which will comprise of a list of software and hardware.
Major security issues
The first line of defense for an organization is a firewall which has to be properly set with
separation between database servers and web servers known as DMZ network zone (Blanc &
Cotton, 2014).
List of hardware
Web-server
The security risk is very high considering the many web attacks. Some of the attacks
include SQL injections
Executive summary
This audit report results to security audit of Comtech Company. The evaluation of
hardware and software has been conducted so as to identify weaknesses which can be misused
by attackers. The results of this security assessment audit report will lead to the implementation
of basic IT security within the organization.
Assessment 1: Project
Introduction
Comtech is an IT based company located in Melbourne. The company is involved in the
provision of professional IT services and support. The company has been operating since 2000
with various branches in Australia. The company has about twenty computers, two modems, and
two printers. As a system asset auditor, I will prepare an IT asset audit record for the company
which will comprise of a list of software and hardware.
Major security issues
The first line of defense for an organization is a firewall which has to be properly set with
separation between database servers and web servers known as DMZ network zone (Blanc &
Cotton, 2014).
List of hardware
Web-server
The security risk is very high considering the many web attacks. Some of the attacks
include SQL injections

MANAGE NETWORK AND DATA INTEGRITY 3
DNS server
The security risk is very high as several IIS installation display very severe security
patches like MDAC RDS weaknesses, various ISAPI filters, and IIS/FrontPage extensions
vulnerabilities
Computers
The security risk is medium
Routers
The security risk is high due as routers sit in between a firewall and a switch.
Switches
The security risk is very low where logging is not implemented considering the limited switches
features.
SMTP server
The security risk is very high where malicious users or employees are able to send
unsolicited mail to 3rd parties using what is known as mail.Acme.com
SQL server
The security risk for this hardware is medium. An organization needs to remove all
employee users who are within the local admin group who don’t need to have the local admin
rights. One can also remove the built-in administrator group on the SL server (Odom, 2009).
List of software
File system software
The security risk is very high where the company is required not to allow world-writable
files particularly those owned by the root. One is also required to look for suspicious SGID and
DNS server
The security risk is very high as several IIS installation display very severe security
patches like MDAC RDS weaknesses, various ISAPI filters, and IIS/FrontPage extensions
vulnerabilities
Computers
The security risk is medium
Routers
The security risk is high due as routers sit in between a firewall and a switch.
Switches
The security risk is very low where logging is not implemented considering the limited switches
features.
SMTP server
The security risk is very high where malicious users or employees are able to send
unsolicited mail to 3rd parties using what is known as mail.Acme.com
SQL server
The security risk for this hardware is medium. An organization needs to remove all
employee users who are within the local admin group who don’t need to have the local admin
rights. One can also remove the built-in administrator group on the SL server (Odom, 2009).
List of software
File system software
The security risk is very high where the company is required not to allow world-writable
files particularly those owned by the root. One is also required to look for suspicious SGID and

MANAGE NETWORK AND DATA INTEGRITY 4
SUID files. In addition, one is supposed to occasionally monitor the organization file system for
the various file types.
Windows operating system
The security risk is very high and one is supposed to always keep the Windows operating
system up to date on the latest security patches. In addition, an organization is required to
analyze the various file permissions and rights to make sure that the appropriate permissions are
applied (Kurose & Ross, 2016).
Anti-virus software
Kaspersky’s anti-virus software ought to be installed in both the windows server and all
the user computers. On the windows server, the anti-virus needs to be configured in such a way
that the server software is able to download the anti-virus definitions on a regular basis.
The recommended processes so as to prevent anti-virus problems
The organization need to run corporate standard
The company need to never open macros or any files attached to an email from untrusted,
suspicious or unknown sources
The company need to delete junk, spam, and chain email without forwarding, in with
Comtech Company
Always scan USB drives or any other external drive before opening it on both user
computers
The organization ought to periodically check lab anti-virus and the recommended
processes (CiscoNetworkingAcademy, 2014).
Network security policy
User account and password policies
SUID files. In addition, one is supposed to occasionally monitor the organization file system for
the various file types.
Windows operating system
The security risk is very high and one is supposed to always keep the Windows operating
system up to date on the latest security patches. In addition, an organization is required to
analyze the various file permissions and rights to make sure that the appropriate permissions are
applied (Kurose & Ross, 2016).
Anti-virus software
Kaspersky’s anti-virus software ought to be installed in both the windows server and all
the user computers. On the windows server, the anti-virus needs to be configured in such a way
that the server software is able to download the anti-virus definitions on a regular basis.
The recommended processes so as to prevent anti-virus problems
The organization need to run corporate standard
The company need to never open macros or any files attached to an email from untrusted,
suspicious or unknown sources
The company need to delete junk, spam, and chain email without forwarding, in with
Comtech Company
Always scan USB drives or any other external drive before opening it on both user
computers
The organization ought to periodically check lab anti-virus and the recommended
processes (CiscoNetworkingAcademy, 2014).
Network security policy
User account and password policies
Secure Best Marks with AI Grader
Need help grading? Try our AI Grader for instant feedback on your assignments.

MANAGE NETWORK AND DATA INTEGRITY 5
The security risk is very high. All the user account ought to be set-up using the domain
security policy. User password should have a combination of characters, numbers, and special
characters. In addition, the organization is supposed to lock-out unsuccessful logon attempts. All
those accounts which are set-up not to expire should be deleted; all the accounts ought to be set-
up in such a way that the passwords expire on a regular basis.
All the guests and administrator accounts ought to be renamed which makes more
problematic for an attacker to gain unlawful access into the organizational network. This should
be done also to the local administrator accounts and domain administrator.
When the similar password is being used for the various local administrator on the
various member servers, the user ought not to be prompted for passwords when accessing
another organization server when they have logged in using an administrator account. This
allows a user to access the organization network resources on multiple user computers by only
logging in once.
All computer screen savers ought to be configured so as to password protect the screen
after five minutes of inactivity. In case a user forgets to lock or to log off the terminal then this
ought to be done automatically within two minutes of inactivity.
General password policies
The system-level passwords like NT admin, the application administration accounts, and
the root ought to be changed on a quarterly basis
All the user-level passwords like web, desktop computer and email ought to be changed
after every three months
The security risk is very high. All the user account ought to be set-up using the domain
security policy. User password should have a combination of characters, numbers, and special
characters. In addition, the organization is supposed to lock-out unsuccessful logon attempts. All
those accounts which are set-up not to expire should be deleted; all the accounts ought to be set-
up in such a way that the passwords expire on a regular basis.
All the guests and administrator accounts ought to be renamed which makes more
problematic for an attacker to gain unlawful access into the organizational network. This should
be done also to the local administrator accounts and domain administrator.
When the similar password is being used for the various local administrator on the
various member servers, the user ought not to be prompted for passwords when accessing
another organization server when they have logged in using an administrator account. This
allows a user to access the organization network resources on multiple user computers by only
logging in once.
All computer screen savers ought to be configured so as to password protect the screen
after five minutes of inactivity. In case a user forgets to lock or to log off the terminal then this
ought to be done automatically within two minutes of inactivity.
General password policies
The system-level passwords like NT admin, the application administration accounts, and
the root ought to be changed on a quarterly basis
All the user-level passwords like web, desktop computer and email ought to be changed
after every three months

MANAGE NETWORK AND DATA INTEGRITY 6
Password protection standards
Comtech employees need not reveal a password over the phone or sharing passwords
with anyone which includes administrative assistants. In addition, one need not format password
with family names.
Data sharing policy
Clients data is not to be shared with other clients or to any with any other individual
unless when stated. The company needs to have ethical review procedures between the
organization partners. In addition, the organization needs to have common contracting
procedures, but the company needs to treat every dataset and contract as unique. Before sharing
of data between various users one ought to identify potential risks which are related to data
sharing.
Disaster recover policy for the company
The organization ought to create have a contingency plan. Some of the plans the
company need to have computer emergency plan, data study plan, a succession plan, a critical
review of service lists, and a succession plan which describes a flow of responsibility when
normal company staff is unavailable. Also, these contingency plans need to explain the order of
long-term and short-term timeframes. The organization data should be backed on daily basis on
offsite storage.
Policy compliance
Password protection standards
Comtech employees need not reveal a password over the phone or sharing passwords
with anyone which includes administrative assistants. In addition, one need not format password
with family names.
Data sharing policy
Clients data is not to be shared with other clients or to any with any other individual
unless when stated. The company needs to have ethical review procedures between the
organization partners. In addition, the organization needs to have common contracting
procedures, but the company needs to treat every dataset and contract as unique. Before sharing
of data between various users one ought to identify potential risks which are related to data
sharing.
Disaster recover policy for the company
The organization ought to create have a contingency plan. Some of the plans the
company need to have computer emergency plan, data study plan, a succession plan, a critical
review of service lists, and a succession plan which describes a flow of responsibility when
normal company staff is unavailable. Also, these contingency plans need to explain the order of
long-term and short-term timeframes. The organization data should be backed on daily basis on
offsite storage.
Policy compliance

MANAGE NETWORK AND DATA INTEGRITY 7
Comtech Company IT team need to verify the compliance of all the policies by the
employees. This will be done on periodic walk-thrus, internal and external audits. Employees
who will be found to have violated the company policies need to be subjected to a disciplinary
action.
List of the current standard tools for networking
Some of the current standard tools for networking include:
Wireshark network tool which is used as a network analyzer
iPerf tool, this is a tool which is used to ping two nodes
Nmap tool, this is a tool used as a network scanner (Blanc & Cotton, 2014)
Assessment 2: Observation
Windows server is widely used in most of the organizations. To install windows server,
one to have a minimum of 1.4 GHz processor, a minimum of 512 MB and disk space of 32 GB
(Shinder, et al., 2018). This section will take one through on how to manage system security in a
windows environment. Mainly this task will involve windows domain controller and a Windows
XP client.
Windows server 2012 installation
First is to install windows server 2012 DVD and wait for a period of time as the system all the
necessary files. This as shown by the below screenshots
Figure 1: After inserting DVD into the computer (Shinder, et al., 2018)
Figure 2: After pressing any key (Shinder, et al., 2018)
Comtech Company IT team need to verify the compliance of all the policies by the
employees. This will be done on periodic walk-thrus, internal and external audits. Employees
who will be found to have violated the company policies need to be subjected to a disciplinary
action.
List of the current standard tools for networking
Some of the current standard tools for networking include:
Wireshark network tool which is used as a network analyzer
iPerf tool, this is a tool which is used to ping two nodes
Nmap tool, this is a tool used as a network scanner (Blanc & Cotton, 2014)
Assessment 2: Observation
Windows server is widely used in most of the organizations. To install windows server,
one to have a minimum of 1.4 GHz processor, a minimum of 512 MB and disk space of 32 GB
(Shinder, et al., 2018). This section will take one through on how to manage system security in a
windows environment. Mainly this task will involve windows domain controller and a Windows
XP client.
Windows server 2012 installation
First is to install windows server 2012 DVD and wait for a period of time as the system all the
necessary files. This as shown by the below screenshots
Figure 1: After inserting DVD into the computer (Shinder, et al., 2018)
Figure 2: After pressing any key (Shinder, et al., 2018)
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

MANAGE NETWORK AND DATA INTEGRITY 8
Once the set-up has been loaded, the set-up the installation process as shown the screenshots
below
Figure 3: Windows server installation start (Shinder, et al., 2018)
Once the set-up has been loaded, the set-up the installation process as shown the screenshots
below
Figure 3: Windows server installation start (Shinder, et al., 2018)
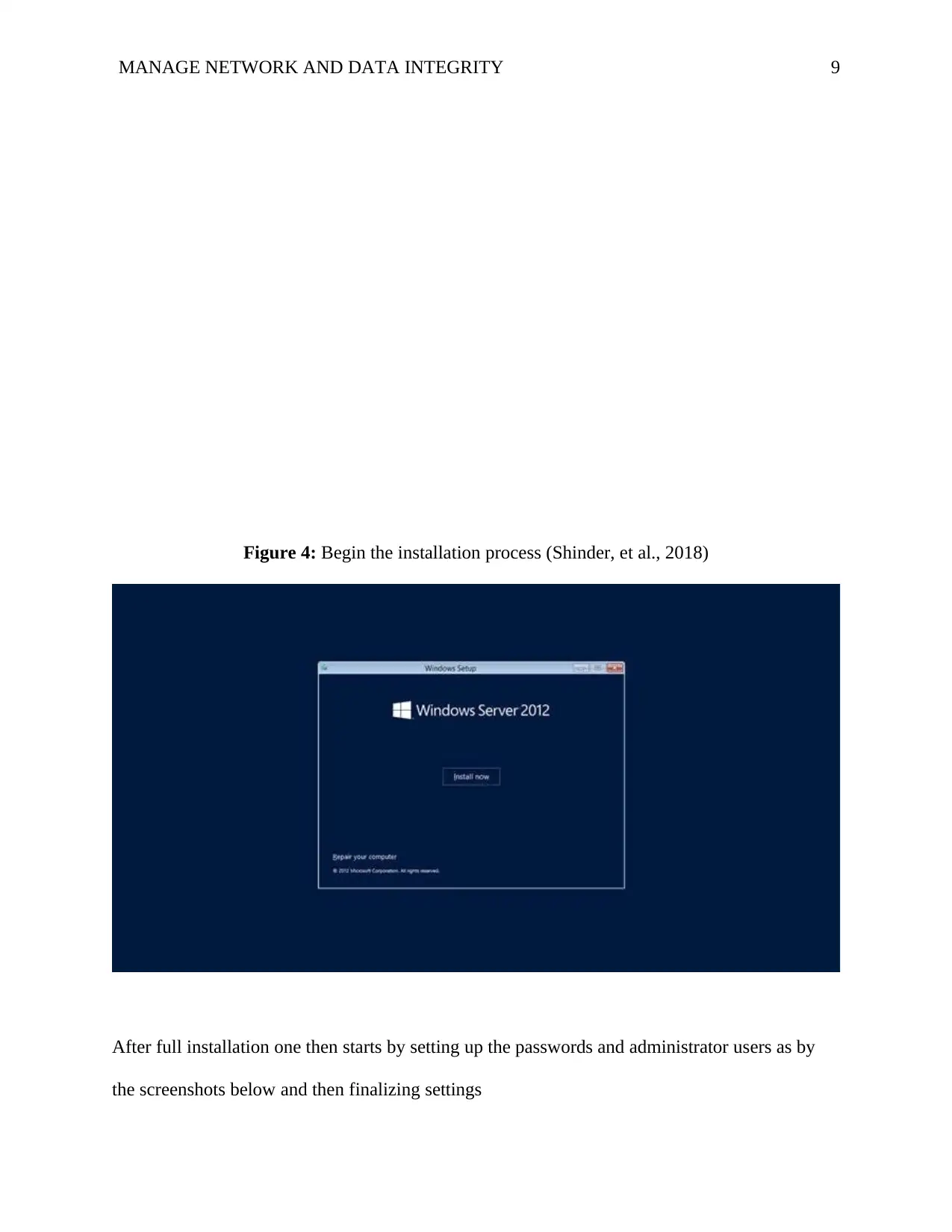
MANAGE NETWORK AND DATA INTEGRITY 9
Figure 4: Begin the installation process (Shinder, et al., 2018)
After full installation one then starts by setting up the passwords and administrator users as by
the screenshots below and then finalizing settings
Figure 4: Begin the installation process (Shinder, et al., 2018)
After full installation one then starts by setting up the passwords and administrator users as by
the screenshots below and then finalizing settings
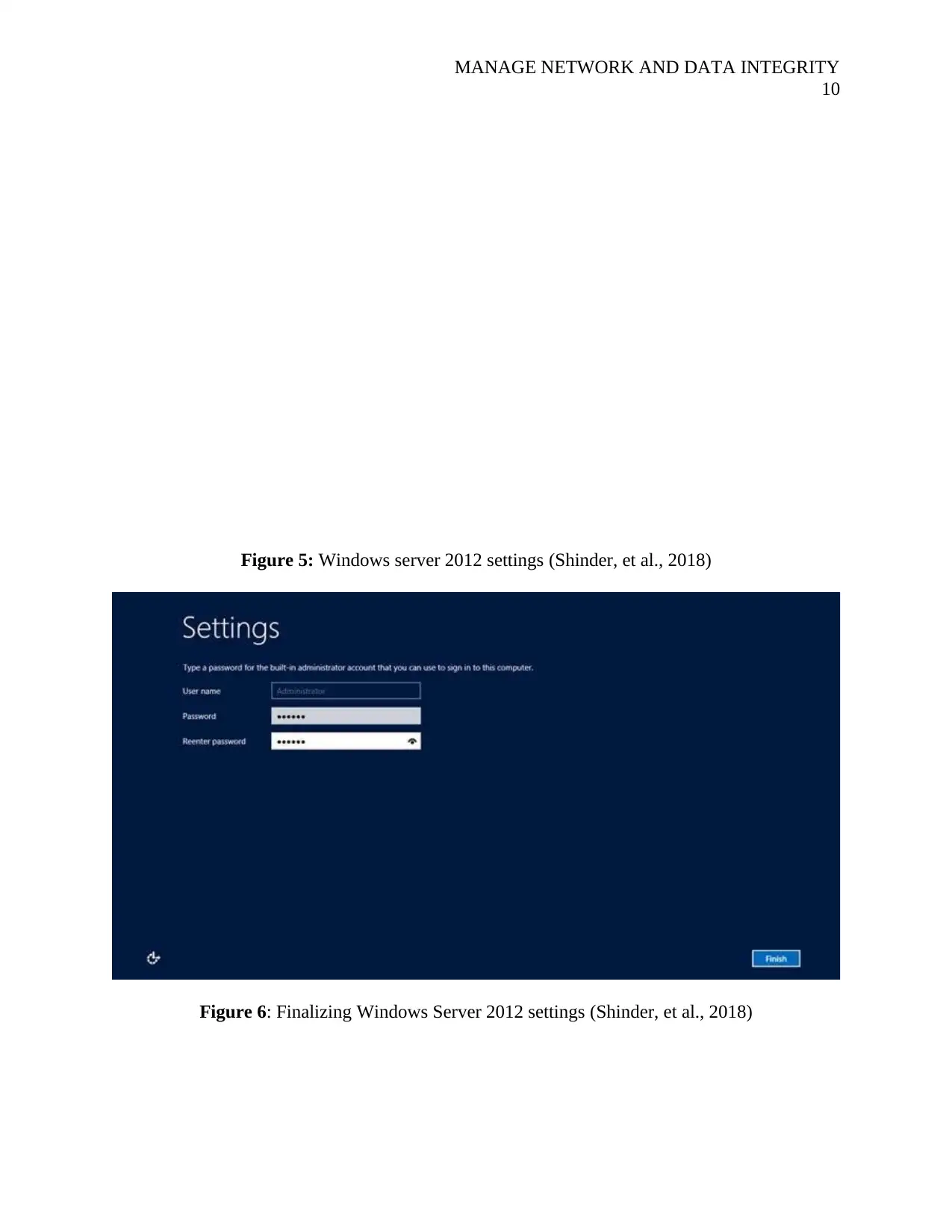
MANAGE NETWORK AND DATA INTEGRITY
10
Figure 5: Windows server 2012 settings (Shinder, et al., 2018)
Figure 6: Finalizing Windows Server 2012 settings (Shinder, et al., 2018)
10
Figure 5: Windows server 2012 settings (Shinder, et al., 2018)
Figure 6: Finalizing Windows Server 2012 settings (Shinder, et al., 2018)
Secure Best Marks with AI Grader
Need help grading? Try our AI Grader for instant feedback on your assignments.

MANAGE NETWORK AND DATA INTEGRITY
11
Group policy settings
After windows server installation one then proceeds to use group policy feature to
manage office XP editions and the windows clients. The very first step is to right click on the
organization unit and then clicking on create and link group policy so as to create a group policy
object. This is shown by the screenshot shown below
Figure 7: Creating Group policy (Krause, 2017)
11
Group policy settings
After windows server installation one then proceeds to use group policy feature to
manage office XP editions and the windows clients. The very first step is to right click on the
organization unit and then clicking on create and link group policy so as to create a group policy
object. This is shown by the screenshot shown below
Figure 7: Creating Group policy (Krause, 2017)
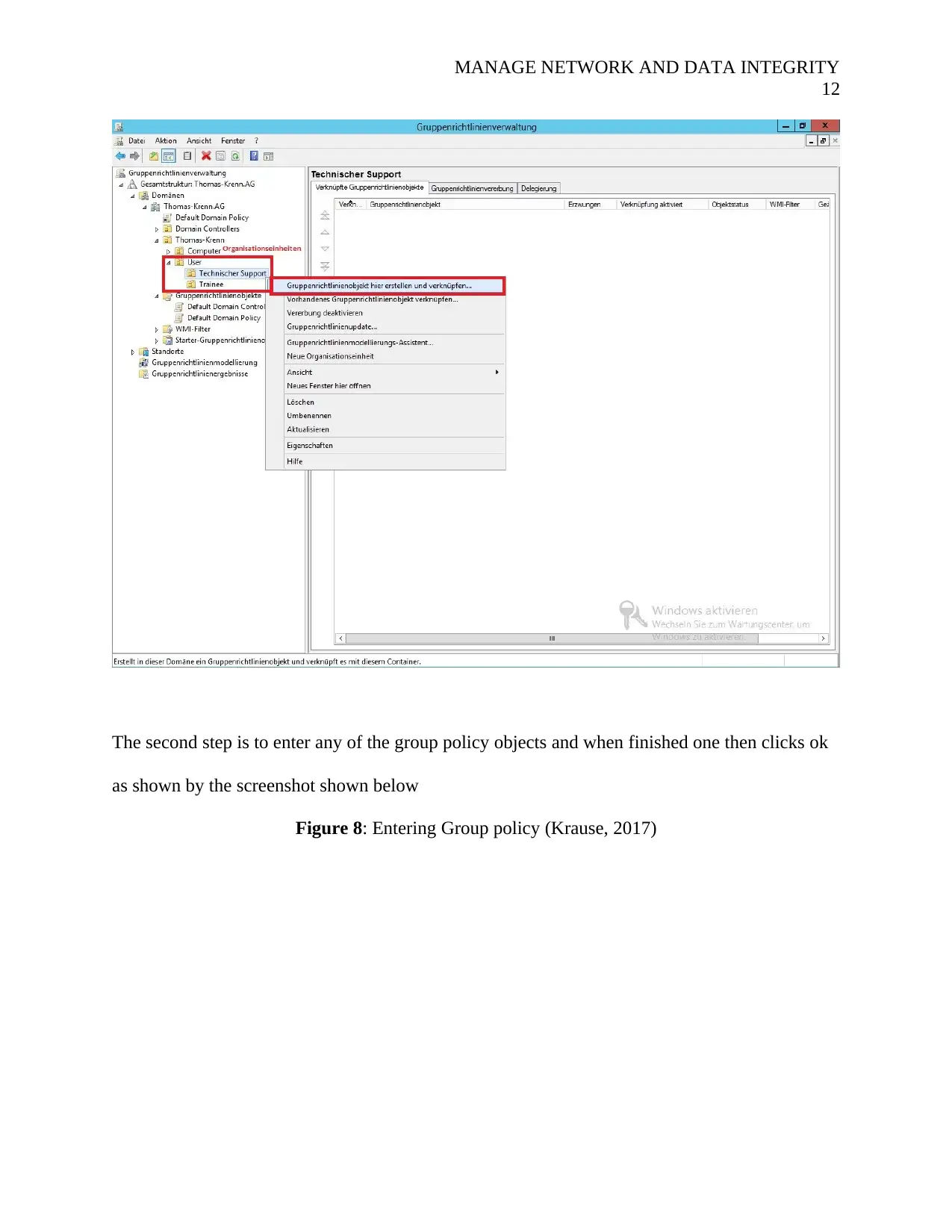
MANAGE NETWORK AND DATA INTEGRITY
12
The second step is to enter any of the group policy objects and when finished one then clicks ok
as shown by the screenshot shown below
Figure 8: Entering Group policy (Krause, 2017)
12
The second step is to enter any of the group policy objects and when finished one then clicks ok
as shown by the screenshot shown below
Figure 8: Entering Group policy (Krause, 2017)
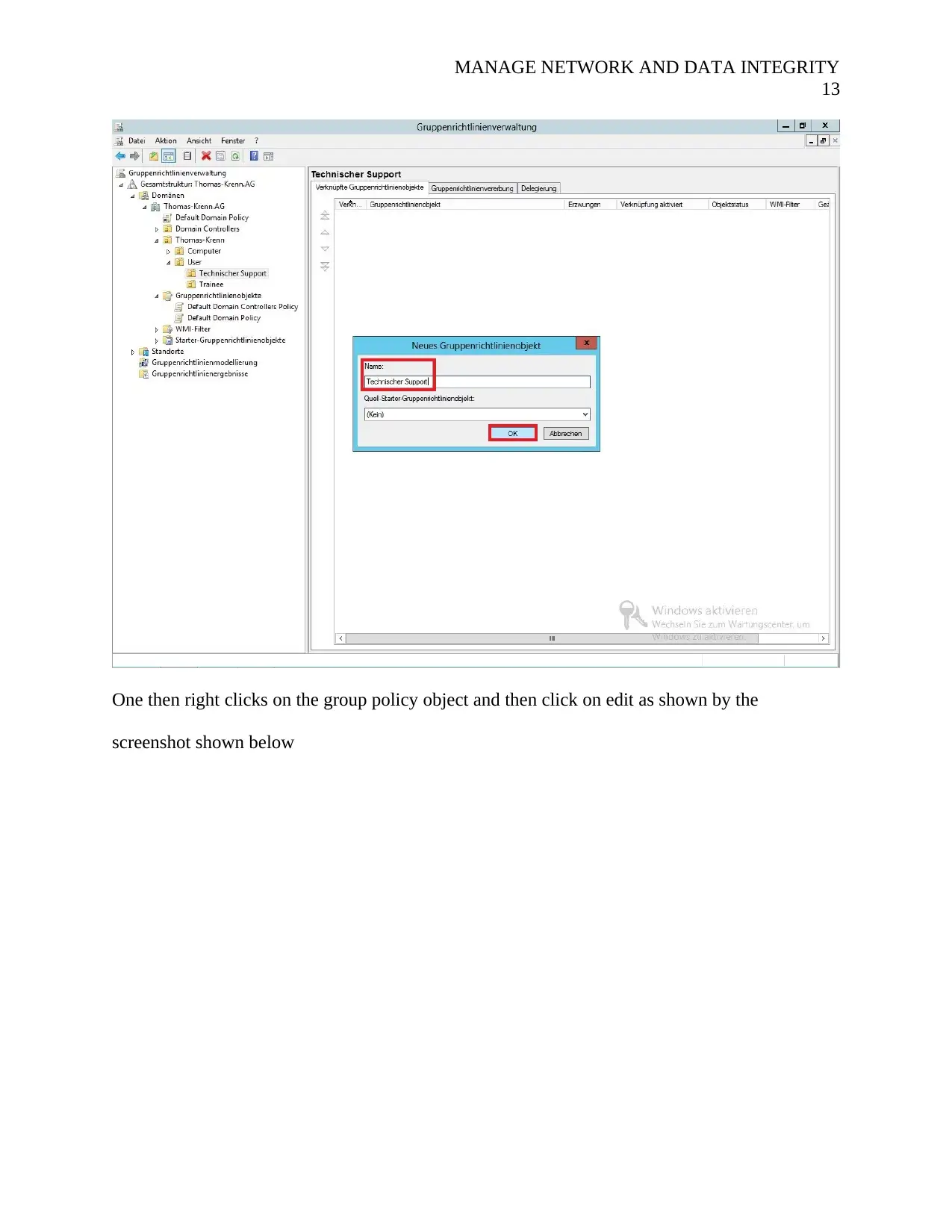
MANAGE NETWORK AND DATA INTEGRITY
13
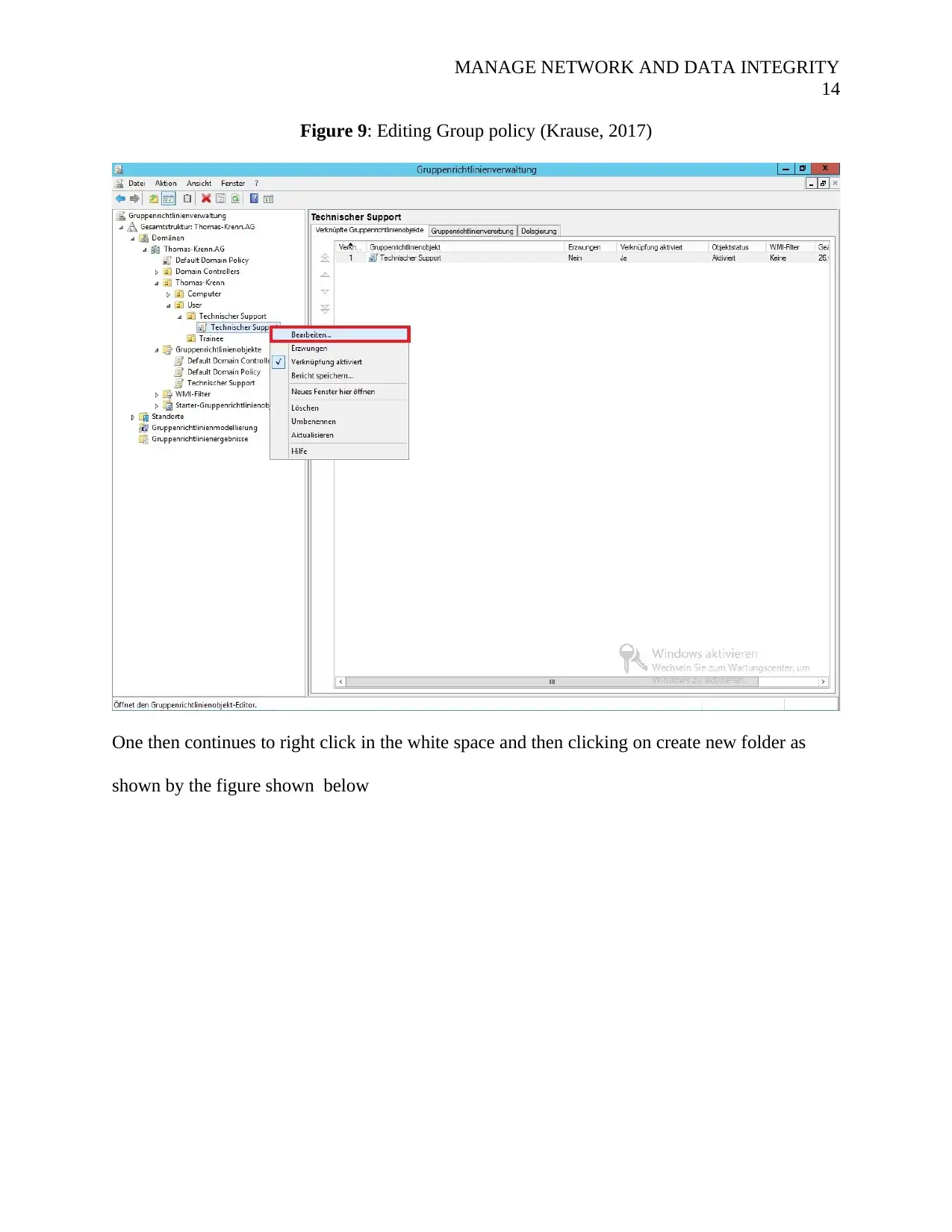
One then right clicks on the group policy object and then click on edit as shown by the
screenshot shown below
13
One then right clicks on the group policy object and then click on edit as shown by the
screenshot shown below
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
MANAGE NETWORK AND DATA INTEGRITY
14
Figure 9: Editing Group policy (Krause, 2017)
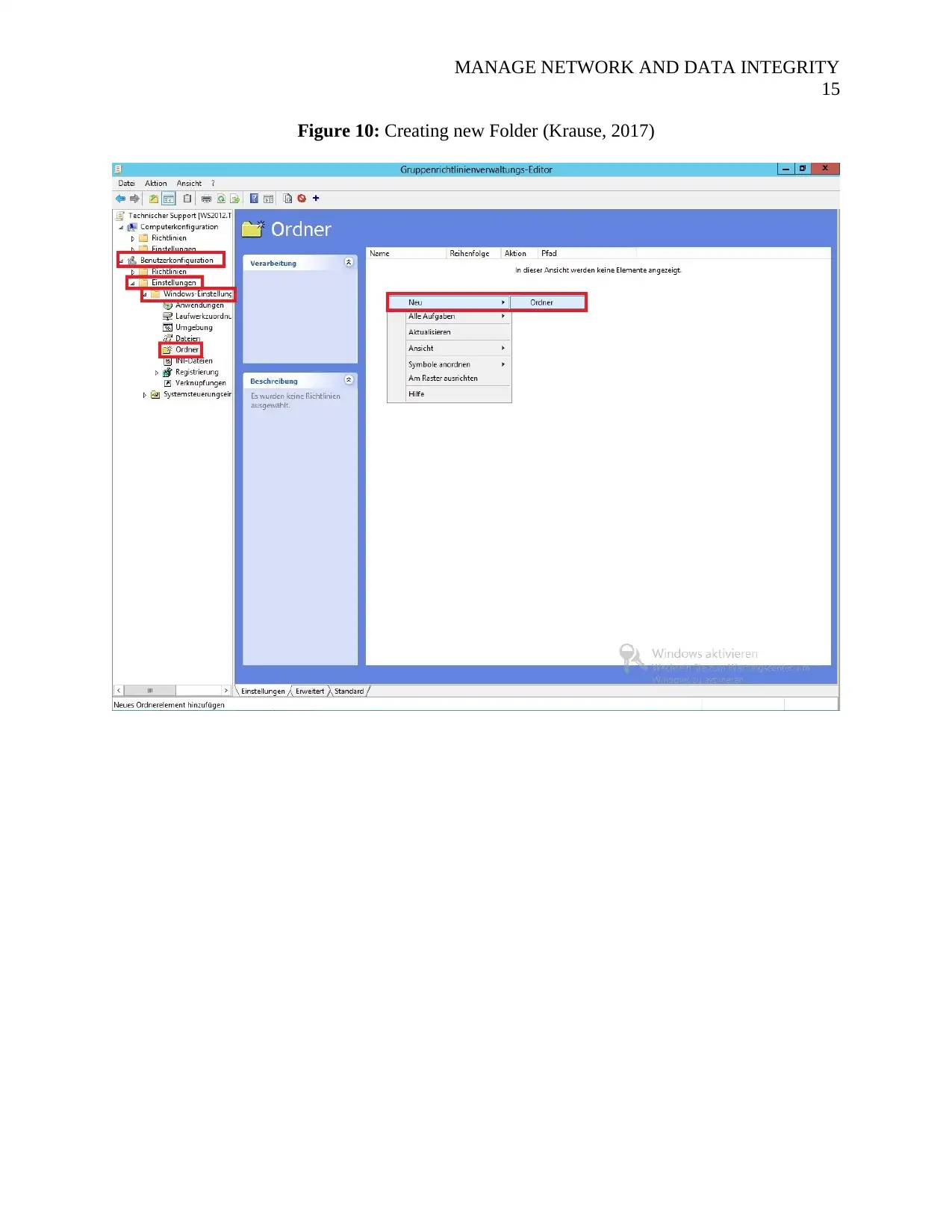
One then continues to right click in the white space and then clicking on create new folder as
shown by the figure shown below
14
Figure 9: Editing Group policy (Krause, 2017)
One then continues to right click in the white space and then clicking on create new folder as
shown by the figure shown below
MANAGE NETWORK AND DATA INTEGRITY
15
Figure 10: Creating new Folder (Krause, 2017)
15
Figure 10: Creating new Folder (Krause, 2017)
MANAGE NETWORK AND DATA INTEGRITY
16
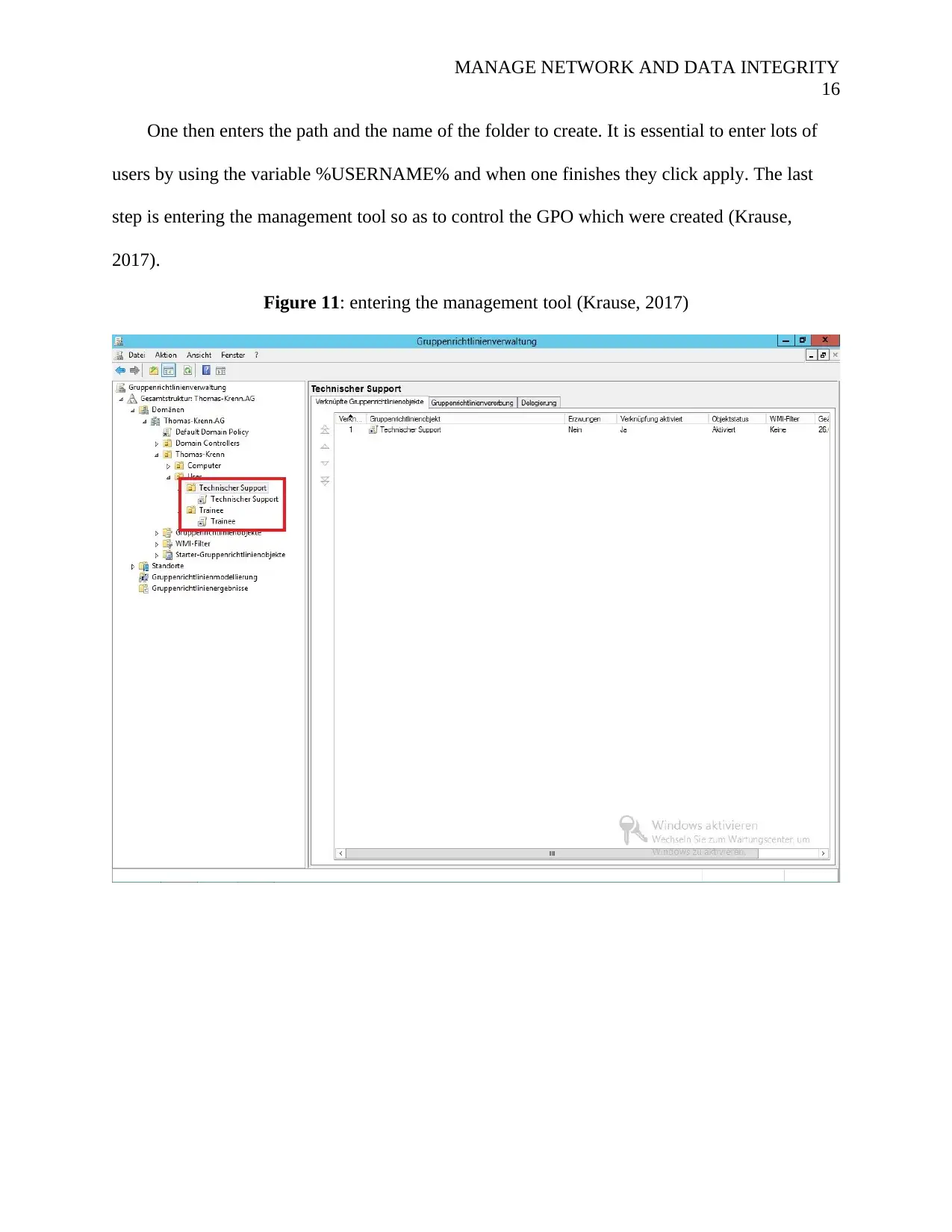
One then enters the path and the name of the folder to create. It is essential to enter lots of
users by using the variable %USERNAME% and when one finishes they click apply. The last
step is entering the management tool so as to control the GPO which were created (Krause,
2017).
Figure 11: entering the management tool (Krause, 2017)
16
One then enters the path and the name of the folder to create. It is essential to enter lots of
users by using the variable %USERNAME% and when one finishes they click apply. The last
step is entering the management tool so as to control the GPO which were created (Krause,
2017).
Figure 11: entering the management tool (Krause, 2017)
Secure Best Marks with AI Grader
Need help grading? Try our AI Grader for instant feedback on your assignments.

MANAGE NETWORK AND DATA INTEGRITY
17
References
Blanc, R. P. & Cotton, I. W., 2014. Computer networking by Robert P Blanc. 2nd ed.
Amsterdam: RTU Publishing House.
CiscoNetworkingAcademy, 2014. Cisco Networking Academy's Introduction to Routing
Dynamically. [Online]
Available at: http://www.ciscopress.com/articles/article.asp?p=2180210&seqNum=5
[Accessed 31st August 2018].
Krause, J., 2017. Mastering Microsoft Windows Server 2012 : a comprehensive and practical
guide to Windows Server 2016. New York: John and wiley.
Kurose, J. F. & Ross, K. W., 2016. Computer networking : a top-down approach. 3rd ed.
Boston: Pearson.
Lammle, T. & Swartz, J., 2013. CCNA data center : introducing cisco data center networking
study guide : exam 640-911. 4th ed. London: Sybex.
Odom, W., 2009. Computer networking first-step by Wendell Odom. 3rd ed. New York: John &
Wiley Press.
Shinder, T. W., Diogenes, Y. & Shinder, D. L., 2018. Windows server 2012 security from end to
edge... by Thomas W Shinder. New York: John & Wiley Press.
17
References
Blanc, R. P. & Cotton, I. W., 2014. Computer networking by Robert P Blanc. 2nd ed.
Amsterdam: RTU Publishing House.
CiscoNetworkingAcademy, 2014. Cisco Networking Academy's Introduction to Routing
Dynamically. [Online]
Available at: http://www.ciscopress.com/articles/article.asp?p=2180210&seqNum=5
[Accessed 31st August 2018].
Krause, J., 2017. Mastering Microsoft Windows Server 2012 : a comprehensive and practical
guide to Windows Server 2016. New York: John and wiley.
Kurose, J. F. & Ross, K. W., 2016. Computer networking : a top-down approach. 3rd ed.
Boston: Pearson.
Lammle, T. & Swartz, J., 2013. CCNA data center : introducing cisco data center networking
study guide : exam 640-911. 4th ed. London: Sybex.
Odom, W., 2009. Computer networking first-step by Wendell Odom. 3rd ed. New York: John &
Wiley Press.
Shinder, T. W., Diogenes, Y. & Shinder, D. L., 2018. Windows server 2012 security from end to
edge... by Thomas W Shinder. New York: John & Wiley Press.

MANAGE NETWORK AND DATA INTEGRITY
18
18
1 out of 18
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
© 2024 | Zucol Services PVT LTD | All rights reserved.





