Comprehensive System Security Report: Great Northern Hotel, Melbourne
VerifiedAdded on 2022/11/09
|15
|1941
|334
Report
AI Summary
This report analyzes the current system security of The Great Northern Hotel Pvt. Ltd, a 4-star luxury hotel in Melbourne, addressing vulnerabilities and recommending improvements to protect against cyber threats. The analysis includes an evaluation of the existing system, risk analysis, and identification of system threats such as phishing, ransomware, and data breaches. The report assesses the human interaction with the information system, categorizes risks based on internal, strategic, and external factors, and proposes matching risk plans. It details effective controls to manage and monitor risks, procedures for user access management, and the importance of system policies and training. The report also covers high-risk categories, network breakdown templates, system security plans, and recovery plan design, with a focus on minimizing risks associated with human interaction and identifying security benchmarks. Finally, it outlines plans for system re-evaluation and the implementation of security functions, providing a comprehensive framework for enhancing the hotel's security posture and protecting its customers' data.

Running Head: MANAGE SYSTEM SECURITY
Manage System Security
Name of the Student
Name of the University
Author Note
Manage System Security
Name of the Student
Name of the University
Author Note
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

1MANAGE SYSTEM SECURITY
Executive Summary:
The purpose of this report is to analyse the existing system of The Great Northern Hotel Pvt. Ltd
and analyses the existing risks measures and factors and come up with a better Information system as well
as a network that is Intrusion Free and safe and secure. The report highlights the causes of risks occurring
and measures to control and mitigate them. This report also focuses on the strategic development of all
the procedures and plans that need to be added or changed. The plans and procedures can help the Great
Northern to succeed as well as full assets security for customers as well as the organisation itself.
Executive Summary:
The purpose of this report is to analyse the existing system of The Great Northern Hotel Pvt. Ltd
and analyses the existing risks measures and factors and come up with a better Information system as well
as a network that is Intrusion Free and safe and secure. The report highlights the causes of risks occurring
and measures to control and mitigate them. This report also focuses on the strategic development of all
the procedures and plans that need to be added or changed. The plans and procedures can help the Great
Northern to succeed as well as full assets security for customers as well as the organisation itself.

2MANAGE SYSTEM SECURITY
Table of Contents
Introduction:....................................................................................................................................4
Discussion:...................................................................................................................................5
Evaluation of the current system as per enterprise guidelines and procedures.............5
Risk Analysis of The Great Northern Hotel Pvt.Ltd.....................................................5
System Threats:.............................................................................................................5
Information system of the hotel and Human Interactions with it..................................6
Assessment of the current system with regards to categorization of risks....................6
Categorizing the risks based on the case study and analysis.........................................6
Assessment of risk on the operations related to humans and the interaction to the
system......................................................................................................................................6
Categorization of risks based on the assessment performed.........................................6
Matching risk plans with categories of risks.................................................................7
Effective controls that can manage and monitor risks..................................................7
Procedures to manage user access system with policies...............................................7
Effective usage of system policies and the training requirements................................7
Identifying high-risk categories.....................................................................................8
A network breakdown and record system template:.....................................................9
System security plans and procedures...........................................................................9
Designing and documenting the recovery plan for security........................................10
Identifying and documenting the controls for risks minimization of human interaction
with the system......................................................................................................................10
Security benchmarks identification from the vendors, specialists related to security
and reviews of the organisation.............................................................................................11
Table of Contents
Introduction:....................................................................................................................................4
Discussion:...................................................................................................................................5
Evaluation of the current system as per enterprise guidelines and procedures.............5
Risk Analysis of The Great Northern Hotel Pvt.Ltd.....................................................5
System Threats:.............................................................................................................5
Information system of the hotel and Human Interactions with it..................................6
Assessment of the current system with regards to categorization of risks....................6
Categorizing the risks based on the case study and analysis.........................................6
Assessment of risk on the operations related to humans and the interaction to the
system......................................................................................................................................6
Categorization of risks based on the assessment performed.........................................6
Matching risk plans with categories of risks.................................................................7
Effective controls that can manage and monitor risks..................................................7
Procedures to manage user access system with policies...............................................7
Effective usage of system policies and the training requirements................................7
Identifying high-risk categories.....................................................................................8
A network breakdown and record system template:.....................................................9
System security plans and procedures...........................................................................9
Designing and documenting the recovery plan for security........................................10
Identifying and documenting the controls for risks minimization of human interaction
with the system......................................................................................................................10
Security benchmarks identification from the vendors, specialists related to security
and reviews of the organisation.............................................................................................11
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

3MANAGE SYSTEM SECURITY
Creating plans to uncover the system re-evaluation with regards to new threats.......12
Implementing and managing the security functions with its descriptions..................12
Conclusion:....................................................................................................................................13
Creating plans to uncover the system re-evaluation with regards to new threats.......12
Implementing and managing the security functions with its descriptions..................12
Conclusion:....................................................................................................................................13
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

4MANAGE SYSTEM SECURITY
Introduction:
The Great Northern Pvt. Ltd is a 4-star hotel that is luxurious in Melbourne. The
rapid client growth of this firm in the last seven years needs the company to make changes to the
Information system that is existing and add new strategies and implement the same to meet the
initial goals. Since the internet is growing every day and lots of data is generated from the same,
it is a need for the company to provide the customers their confidentiality and security of their
credentials. To do so, the Great Northern needs to implement an Intrusion free and manageable
network. There is also a need to create a new strategic plan for the implementation of the new
systems. This report focuses on the risks management, Human resource management and the
strategic development of the new system being implemented along with the position
improvement of the Great Northern.
Introduction:
The Great Northern Pvt. Ltd is a 4-star hotel that is luxurious in Melbourne. The
rapid client growth of this firm in the last seven years needs the company to make changes to the
Information system that is existing and add new strategies and implement the same to meet the
initial goals. Since the internet is growing every day and lots of data is generated from the same,
it is a need for the company to provide the customers their confidentiality and security of their
credentials. To do so, the Great Northern needs to implement an Intrusion free and manageable
network. There is also a need to create a new strategic plan for the implementation of the new
systems. This report focuses on the risks management, Human resource management and the
strategic development of the new system being implemented along with the position
improvement of the Great Northern.

5MANAGE SYSTEM SECURITY
Discussion:
Evaluation of the current system as per enterprise guidelines and procedures:
Evaluation of the existing system with regards to the guidelines and procedures can be done
by enlarging the importance of the asset, that is information and also by taking measures for
threats that could occur. The treats can include, malware, cyber-crimes, and terrorism after
stealing credentials are the most significant concern of The Great Northern Hotel Pvt.Ltd.
The current Information system has no strong encryption and breaches could happen from
anywhere in the network.
Risk Analysis of The Great Northern Hotel Pvt.Ltd:
In the globalised and competitive world, the hotel issues related to the security of their data
and changes can affect the clients and not just the Great Northern. The risk that may occur or
has already occurred can be:
Stealing of credentials and identity theft (example: fake credit cards)
Silent invasions, hackers performing cybercrimes that could hamper the whole
Information System of the hotel
Security audit cycles that are non-existent
Competitive advantage and security incidents that are major
The documentation of the risk analysis phase should include the following plans of management:
i. Risks identification
ii. Elimination of risks
iii. Identifying tasks among departments
iv. Contingencies to be planned for recovery of any information that can be lost
System Threats:
The system threats may include social engineerings such as Phishing attacks, Ransom wares,
Distributed Denial of service or (DDoS), Payment cards stealth/ attacks, Dark hotel Hacking and
Identity theft of the clients. The customers want the hotel to be safe, secure and private and
expect the similar protection when it comes to the digital assets that they trust the hotel with,
Discussion:
Evaluation of the current system as per enterprise guidelines and procedures:
Evaluation of the existing system with regards to the guidelines and procedures can be done
by enlarging the importance of the asset, that is information and also by taking measures for
threats that could occur. The treats can include, malware, cyber-crimes, and terrorism after
stealing credentials are the most significant concern of The Great Northern Hotel Pvt.Ltd.
The current Information system has no strong encryption and breaches could happen from
anywhere in the network.
Risk Analysis of The Great Northern Hotel Pvt.Ltd:
In the globalised and competitive world, the hotel issues related to the security of their data
and changes can affect the clients and not just the Great Northern. The risk that may occur or
has already occurred can be:
Stealing of credentials and identity theft (example: fake credit cards)
Silent invasions, hackers performing cybercrimes that could hamper the whole
Information System of the hotel
Security audit cycles that are non-existent
Competitive advantage and security incidents that are major
The documentation of the risk analysis phase should include the following plans of management:
i. Risks identification
ii. Elimination of risks
iii. Identifying tasks among departments
iv. Contingencies to be planned for recovery of any information that can be lost
System Threats:
The system threats may include social engineerings such as Phishing attacks, Ransom wares,
Distributed Denial of service or (DDoS), Payment cards stealth/ attacks, Dark hotel Hacking and
Identity theft of the clients. The customers want the hotel to be safe, secure and private and
expect the similar protection when it comes to the digital assets that they trust the hotel with,
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

6MANAGE SYSTEM SECURITY
hence it is important for the hotel to reassure its guests by having a properly functioning
information system.
Information system of the hotel and Human Interactions with it:
The Human Resource Management team of the Great Northern takes care of the human
interaction to the IS which are used to collect, record, store, analyse and retrieve data. The
importance of this is it is multifaceted which ranges from the collection of operational assistance
to simplifying the procedures and having control of the available data. Positive results are gained
if the Hotel focuses on providing information on daily basis to the HRM and deal with the
possible causes.
Assessment of the current system with regards to the categorization of risks:
Hotel assessment of risk is a fundamental part of the measures for security and safety of the
hotels; this helps avoid hazards that are intentional as well as unintentional. Risk assessment of
the current system had many drawbacks and once improved could protect the reputation and
branding of the Great Northern.
Categorising the risks based on the case study and analysis:
i. The risk that is competitive: This risk shows the advantages the competing
organisations will gain over the Great Northern
ii. Economic risks
iii. Operational risk
iv. Risks that are legal and reputational
v. Risks that are compliance and strategic
Assessment of risk on the operations related to humans and the interaction to the
system:
The human-machine interaction has a significant role in the assessment of risk of the great
Northern systems because there is an impact that is a director on the professionals to recognise a
scenario and decide with the measures for avoidance or mitigation of risks occurring or those
risks that may occur.
hence it is important for the hotel to reassure its guests by having a properly functioning
information system.
Information system of the hotel and Human Interactions with it:
The Human Resource Management team of the Great Northern takes care of the human
interaction to the IS which are used to collect, record, store, analyse and retrieve data. The
importance of this is it is multifaceted which ranges from the collection of operational assistance
to simplifying the procedures and having control of the available data. Positive results are gained
if the Hotel focuses on providing information on daily basis to the HRM and deal with the
possible causes.
Assessment of the current system with regards to the categorization of risks:
Hotel assessment of risk is a fundamental part of the measures for security and safety of the
hotels; this helps avoid hazards that are intentional as well as unintentional. Risk assessment of
the current system had many drawbacks and once improved could protect the reputation and
branding of the Great Northern.
Categorising the risks based on the case study and analysis:
i. The risk that is competitive: This risk shows the advantages the competing
organisations will gain over the Great Northern
ii. Economic risks
iii. Operational risk
iv. Risks that are legal and reputational
v. Risks that are compliance and strategic
Assessment of risk on the operations related to humans and the interaction to the
system:
The human-machine interaction has a significant role in the assessment of risk of the great
Northern systems because there is an impact that is a director on the professionals to recognise a
scenario and decide with the measures for avoidance or mitigation of risks occurring or those
risks that may occur.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

7MANAGE SYSTEM SECURITY
The categorisation of risks based on the assessment performed:
Internal risks: Controllable risks.
Strategic risks: Are risks taken up by the hotel to gain value.
External risks: Risks beyond control like Natural Disasters.
Matching risk plans with categories of risks:
Internal risks are controlled by controlling privileges of the employees by the administrator.
Strategic risks can be controlled by developing a management system that satisfies the
customers as well as has no negative impact on the goals of the organisation. External risks
are inevitable however measures such as information backup and emergency contingencies
can be looked upon.
Effective controls that can manage and monitor risks:
The internal control system controls the effectiveness of the internal systems that
automatically adds up to the branding and customer satisfaction that results in the branding
and reputational increase of the hotel. Monitoring risks can be done by the HRM of the hotel
and can avoid risks such as economy sharing, changing customer demands and meeting these
demands, experienced personnel demands, customers perception of risks, technology that are
guest focused and regulations that are new.
Procedures to manage user access system with policies:
i. Technical Access Control AC-1Access Control Policy
ii. NIST 800-100 NIST 800-12 Technical Access Control AC-2 Account
Management P1
iii. Technical Access Control AC-3 Access Enforcement P1
iv. Technical Access Control AC-5 Separation of Duties P1
v. Technical Access Control AC-7 Unsuccessful login attempts P2
vi. Technical Access Control AC-14 Permitted Actions Without identification
Effective usage of system policies and the training requirements:
The categorisation of risks based on the assessment performed:
Internal risks: Controllable risks.
Strategic risks: Are risks taken up by the hotel to gain value.
External risks: Risks beyond control like Natural Disasters.
Matching risk plans with categories of risks:
Internal risks are controlled by controlling privileges of the employees by the administrator.
Strategic risks can be controlled by developing a management system that satisfies the
customers as well as has no negative impact on the goals of the organisation. External risks
are inevitable however measures such as information backup and emergency contingencies
can be looked upon.
Effective controls that can manage and monitor risks:
The internal control system controls the effectiveness of the internal systems that
automatically adds up to the branding and customer satisfaction that results in the branding
and reputational increase of the hotel. Monitoring risks can be done by the HRM of the hotel
and can avoid risks such as economy sharing, changing customer demands and meeting these
demands, experienced personnel demands, customers perception of risks, technology that are
guest focused and regulations that are new.
Procedures to manage user access system with policies:
i. Technical Access Control AC-1Access Control Policy
ii. NIST 800-100 NIST 800-12 Technical Access Control AC-2 Account
Management P1
iii. Technical Access Control AC-3 Access Enforcement P1
iv. Technical Access Control AC-5 Separation of Duties P1
v. Technical Access Control AC-7 Unsuccessful login attempts P2
vi. Technical Access Control AC-14 Permitted Actions Without identification
Effective usage of system policies and the training requirements:
8MANAGE SYSTEM SECURITY
The effective training requirement is the one which has documentation of the scopes, and well-
crafted policies and procedures can abolish a lot of guess-work and have a well-defined phase for
a specific task to accomplish them. The entire training process will highlight the processes that
need to implement to get the efficiency of the training. To manage the processes and give an
overview of the trainees of the new information system it is essential to focus on the basics of the
documentation of the scope and the plans.
Identifying high-risk categories:
Level 1 Level 2 Level 3
Plan Move
Internal Risks
Technological Risk
Loss or damage of assets and resources
Internal market conditions.
External Risks
Economic Risk/ Political risks
Natural disasters
Strategic Risks
Competitive and Regulatory Risks
Change Risks
Operational Risks
Business Risks
Protocols Risks
The effective training requirement is the one which has documentation of the scopes, and well-
crafted policies and procedures can abolish a lot of guess-work and have a well-defined phase for
a specific task to accomplish them. The entire training process will highlight the processes that
need to implement to get the efficiency of the training. To manage the processes and give an
overview of the trainees of the new information system it is essential to focus on the basics of the
documentation of the scope and the plans.
Identifying high-risk categories:
Level 1 Level 2 Level 3
Plan Move
Internal Risks
Technological Risk
Loss or damage of assets and resources
Internal market conditions.
External Risks
Economic Risk/ Political risks
Natural disasters
Strategic Risks
Competitive and Regulatory Risks
Change Risks
Operational Risks
Business Risks
Protocols Risks
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
9MANAGE SYSTEM SECURITY
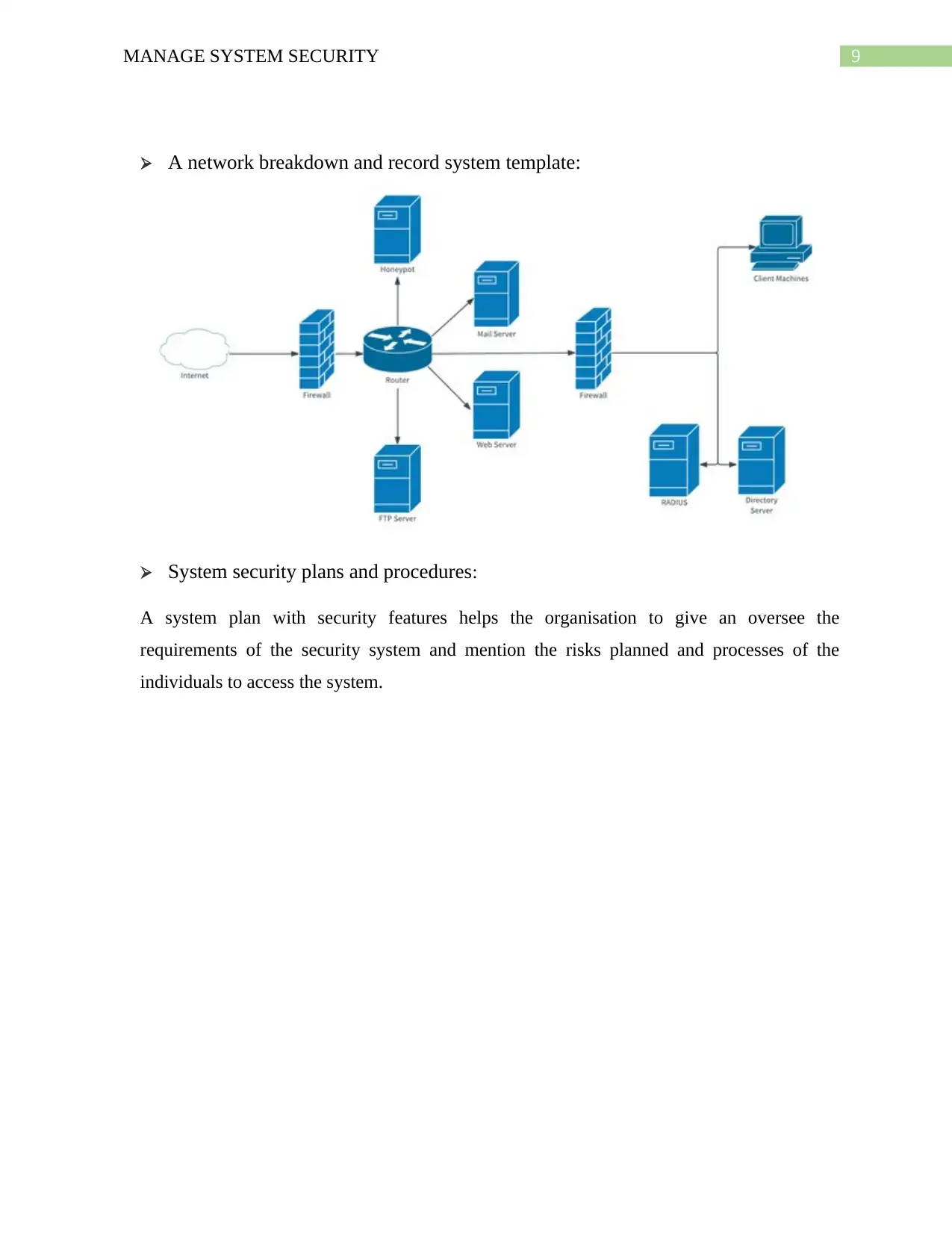
A network breakdown and record system template:
System security plans and procedures:
A system plan with security features helps the organisation to give an oversee the
requirements of the security system and mention the risks planned and processes of the
individuals to access the system.
A network breakdown and record system template:
System security plans and procedures:
A system plan with security features helps the organisation to give an oversee the
requirements of the security system and mention the risks planned and processes of the
individuals to access the system.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
10MANAGE SYSTEM SECURITY
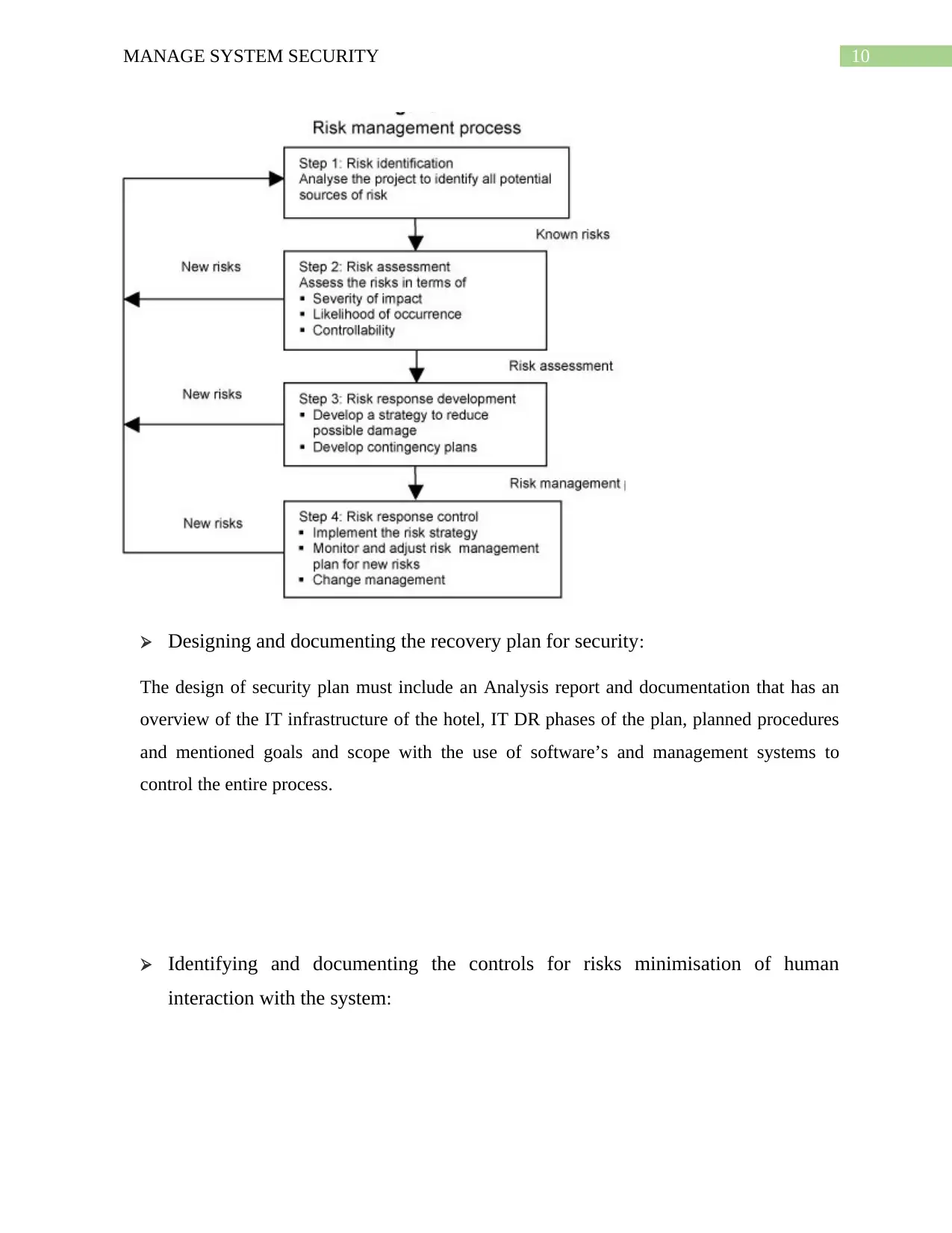
Designing and documenting the recovery plan for security:
The design of security plan must include an Analysis report and documentation that has an
overview of the IT infrastructure of the hotel, IT DR phases of the plan, planned procedures
and mentioned goals and scope with the use of software’s and management systems to
control the entire process.
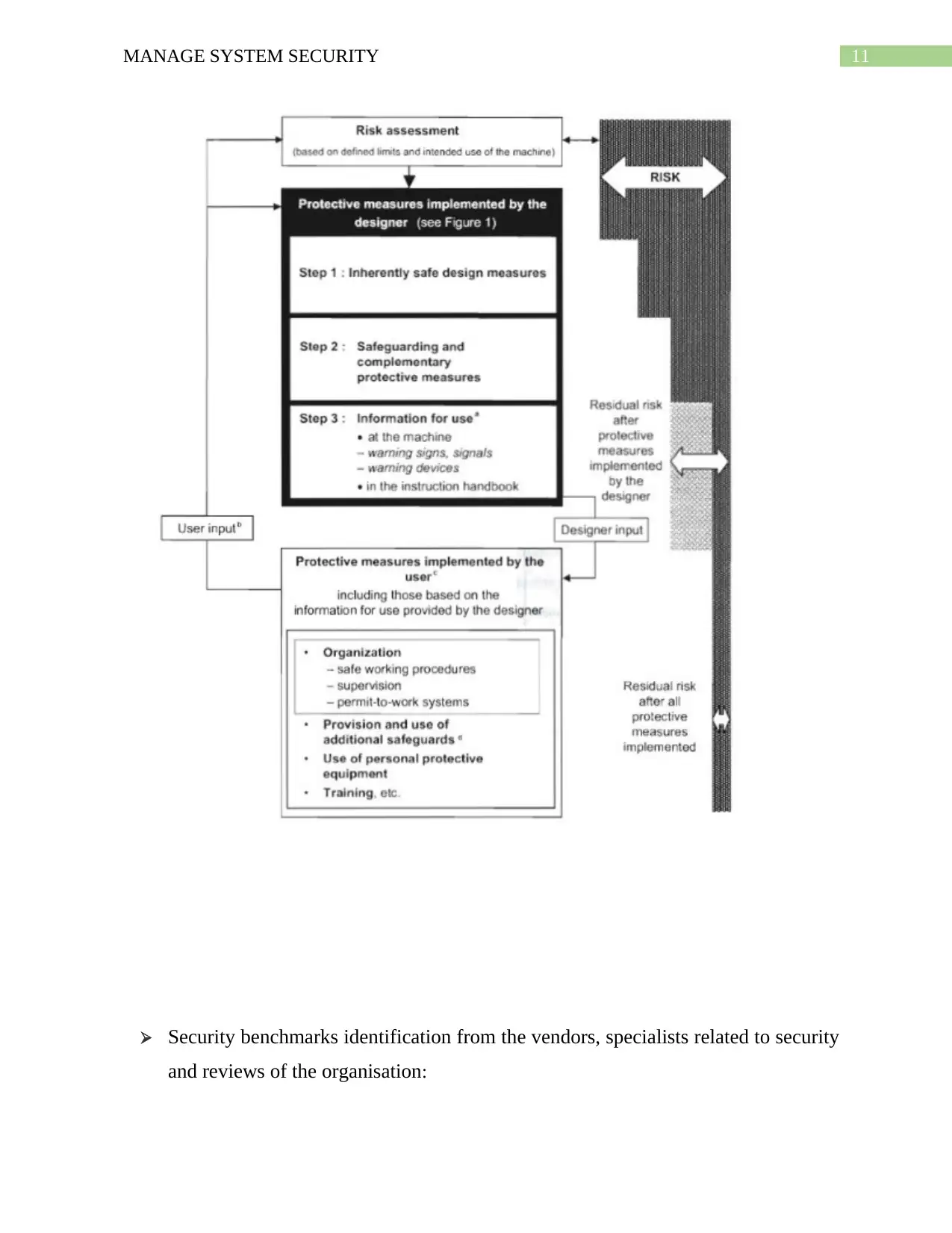
Identifying and documenting the controls for risks minimisation of human
interaction with the system:
Designing and documenting the recovery plan for security:
The design of security plan must include an Analysis report and documentation that has an
overview of the IT infrastructure of the hotel, IT DR phases of the plan, planned procedures
and mentioned goals and scope with the use of software’s and management systems to
control the entire process.
Identifying and documenting the controls for risks minimisation of human
interaction with the system:
11MANAGE SYSTEM SECURITY
Security benchmarks identification from the vendors, specialists related to security
and reviews of the organisation:
Security benchmarks identification from the vendors, specialists related to security
and reviews of the organisation:
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
1 out of 15
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.



