Comprehensive Analysis of E-commerce and Information Security in MIS
VerifiedAdded on 2023/06/07
|15
|4287
|108
Report
AI Summary
This Management Information Systems (MIS) report provides a detailed overview of several key concepts, including cloud computing, customer relationship management (CRM), e-policies, information security, and e-commerce. It discusses the attributes, advantages, and disadvantages of cloud computing, elaborates on the components of a comprehensive CRM system, and emphasizes the importance of e-policies in protecting organizational information. The report also examines authentication technologies for preventing unauthorized access and analyzes the relationship between a firm's MIS infrastructure and its ability to provide services to customers, suppliers, and employees. Furthermore, it explores the unique features of e-commerce, digital markets, and digital goods, as well as the impact of e-commerce on business-to-business transactions. The document also touches on the ethical considerations in the information age and the importance of information ethics. This resource is available on Desklib, where students can find a wealth of solved assignments and past papers.

Mana ement n ormation temg I f Sys
Name of Student:
Name of College:
Authors Note:
Name of Student:
Name of College:
Authors Note:
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

Contents
PA T AR :.....................................................................................................................................................................3
TQUES ION 1..........................................................................................................................................................3
TQUES ION 2..........................................................................................................................................................4
TQUES ION 3..........................................................................................................................................................6
TQUES ION 4..........................................................................................................................................................7
TQUES ION 5..........................................................................................................................................................8
TQUES ION 6........................................................................................................................................................10
PA TR B:...................................................................................................................................................................11
TQUES ION 7........................................................................................................................................................11
e erenceR f s..........................................................................................................................................................14
PA T AR :.....................................................................................................................................................................3
TQUES ION 1..........................................................................................................................................................3
TQUES ION 2..........................................................................................................................................................4
TQUES ION 3..........................................................................................................................................................6
TQUES ION 4..........................................................................................................................................................7
TQUES ION 5..........................................................................................................................................................8
TQUES ION 6........................................................................................................................................................10
PA TR B:...................................................................................................................................................................11
TQUES ION 7........................................................................................................................................................11
e erenceR f s..........................................................................................................................................................14

PART A:
QUESTION 1
a. Cloud computing is a technology that allows universal, user friendly and on demand
network entrée to a common source of configurable resources which can be quickly managed
and set free with less management push or service provider synergy The significant attributes
of cloud computing are:
On demand service: a user can independently equip computing proficiency like server time,
network repository as required naturally without needing human intervention with service
provider. (Bhardwaj, et al., 2010)
Broad network access: potentiality is attainable over networks and permeated with standard
systems that improve usage with heterogeneous thin or thick client platform like mobiles,
laptops etc
Resource Pooling: the providers computing collaterals are pooled to provide service to more
than one user applying multi tenant archetypal with distinct physical and implicit collaterals
actively authorized and reauthorized as per interest. So there is a feel of location self reliance
where user commonly has no control or awareness of particular place of the given collaterals.
But they might be capable to determine place at high level of remoteness. Instance of
collaterals involve storage, processing, memory and network bandwidth (Bhardwaj, et al.,
2010)
Rapid elasticity: potentialities can be elastically administered and set off in few instances
naturally to reach to quick external and internal requests fitting to interest. For user
potentialities usable for administering majorly seems to be endless and can be allotted in any
amount anytime.
Measured service: cloud systems naturally govern and improve collateral usage by allowing
metering ability at certain level of consideration suitable to service nature such as storage,
bandwidth, active user account etc. Collateral use may be examined, restrained and disclosed
offering clarity for both provider and user of service (Bhardwaj, et al., 2010)
QUESTION 1
a. Cloud computing is a technology that allows universal, user friendly and on demand
network entrée to a common source of configurable resources which can be quickly managed
and set free with less management push or service provider synergy The significant attributes
of cloud computing are:
On demand service: a user can independently equip computing proficiency like server time,
network repository as required naturally without needing human intervention with service
provider. (Bhardwaj, et al., 2010)
Broad network access: potentiality is attainable over networks and permeated with standard
systems that improve usage with heterogeneous thin or thick client platform like mobiles,
laptops etc
Resource Pooling: the providers computing collaterals are pooled to provide service to more
than one user applying multi tenant archetypal with distinct physical and implicit collaterals
actively authorized and reauthorized as per interest. So there is a feel of location self reliance
where user commonly has no control or awareness of particular place of the given collaterals.
But they might be capable to determine place at high level of remoteness. Instance of
collaterals involve storage, processing, memory and network bandwidth (Bhardwaj, et al.,
2010)
Rapid elasticity: potentialities can be elastically administered and set off in few instances
naturally to reach to quick external and internal requests fitting to interest. For user
potentialities usable for administering majorly seems to be endless and can be allotted in any
amount anytime.
Measured service: cloud systems naturally govern and improve collateral usage by allowing
metering ability at certain level of consideration suitable to service nature such as storage,
bandwidth, active user account etc. Collateral use may be examined, restrained and disclosed
offering clarity for both provider and user of service (Bhardwaj, et al., 2010)
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

Running head: MIS
b. Downtime: as cloud system providers serve multiple users they sometime get affected and face technical
outage which can temporarily hang up the business process. Further in case there is internet connectivity
failure then user is unable to permeate to applications or servers functioning on cloud (Jadeja and Modi,
2012).
Susceptibility to attacks: as cloud system is public service which is open to all and as its elements are
apparent online so these are susceptible to attacks and security hacks.
Vendor lock in: though cloud system providers assure flexibility of usage and integration to cloud but
switching these services are still difficult as users may encounter hard time to switch their services from one
provider to other. Hosting and combing existing cloud applications on other platform may become difficult
due to support issues and incompatibility. Example, application developed on Microsoft development
framework (.net) may not function appropriately on Linux (Jadeja and Modi, 2012)
Limited control: as the cloud system is completely owned, administered and overseen by service provider so
it allows basic control to users and the users can only administer and regulate applications, data and services
operated on cloud and not the infrastructure. So prime administrative activities like server shell access,
updating and firmware control is not allowed from user end.
QUESTION 2
a. A sandwich shop has three major business processes which are primary, supportive and managerial. The
primary business processes are essential processes which depict the operations and routine tasks that are
performed in the shop to meet its mission and goals. These have direct correlation with customers as they are
most suitable for them and include product assembly process, quality assurance, corrective or preventive
maintenance, customer prospecting and production process. The other business process is supportive which
aids primary activities and adds value to final product but these processes are internal and not visible to
customer directly. Like HR process that includes hiring, training, paying employees as well as exit process
and information technology process. The third business process is management process that supports
coordination and control of activities inside the sandwich shop which means they support both primary and
support process (Zott, et al., 2011). Such as finance process that includes invoicing, billing and paying
suppliers, generating financial statements, payment of taxes and cash management process. It also includes
strategic planning process.
Yes, several of these business processes can be made effective and more coordinated with support of
information systems. For instance a local sandwich shop can be turned more effective with better
management of recorded data like finance process with integration of IS to better manage cash system,
payments to suppliers, invoicing and billing and effective risk management process by payment of
taxes and maintaining of safety audit and legal check process to ensure compliance.
4
b. Downtime: as cloud system providers serve multiple users they sometime get affected and face technical
outage which can temporarily hang up the business process. Further in case there is internet connectivity
failure then user is unable to permeate to applications or servers functioning on cloud (Jadeja and Modi,
2012).
Susceptibility to attacks: as cloud system is public service which is open to all and as its elements are
apparent online so these are susceptible to attacks and security hacks.
Vendor lock in: though cloud system providers assure flexibility of usage and integration to cloud but
switching these services are still difficult as users may encounter hard time to switch their services from one
provider to other. Hosting and combing existing cloud applications on other platform may become difficult
due to support issues and incompatibility. Example, application developed on Microsoft development
framework (.net) may not function appropriately on Linux (Jadeja and Modi, 2012)
Limited control: as the cloud system is completely owned, administered and overseen by service provider so
it allows basic control to users and the users can only administer and regulate applications, data and services
operated on cloud and not the infrastructure. So prime administrative activities like server shell access,
updating and firmware control is not allowed from user end.
QUESTION 2
a. A sandwich shop has three major business processes which are primary, supportive and managerial. The
primary business processes are essential processes which depict the operations and routine tasks that are
performed in the shop to meet its mission and goals. These have direct correlation with customers as they are
most suitable for them and include product assembly process, quality assurance, corrective or preventive
maintenance, customer prospecting and production process. The other business process is supportive which
aids primary activities and adds value to final product but these processes are internal and not visible to
customer directly. Like HR process that includes hiring, training, paying employees as well as exit process
and information technology process. The third business process is management process that supports
coordination and control of activities inside the sandwich shop which means they support both primary and
support process (Zott, et al., 2011). Such as finance process that includes invoicing, billing and paying
suppliers, generating financial statements, payment of taxes and cash management process. It also includes
strategic planning process.
Yes, several of these business processes can be made effective and more coordinated with support of
information systems. For instance a local sandwich shop can be turned more effective with better
management of recorded data like finance process with integration of IS to better manage cash system,
payments to suppliers, invoicing and billing and effective risk management process by payment of
taxes and maintaining of safety audit and legal check process to ensure compliance.
4
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

MIS
b. The three primary elements of comprehensive CRM system are:
Sales Force automation: this is vital components of customer relationship management and exists in all
business systems. This component involves predicting, recording sales processing and maintaining trail of
vital interactions. This component helps to interpret revenue creation possibilities which make it very
essential for business. Moreover sales force automation component of CRM evaluates sales predictions and
performance of employees so as to attain overall betterment in the growth and enhancement of industry
(Soltani and Navimipour, 2016).
Lead management: this is another component of CRM system that is essentially used to maintain trail of
sales lead and their distribution. These are mostly common in sales and marketing enterprises and customer
service centers. The lead management component includes proficient administration of campaigns,
developing personalized forms, finalizing mail list etc. Further a wide study of buying patterns of customers
and prospective sales lead allows seizing more amount of sales lead to enhance the sales.
Customer service: this component of CRM system helps to gather customer inputs and data, information on
their purchase and patterns. After the information is gathered these are distributed to appropriate
departments and hence customer service is a vital component of CRM. The information offered by this
component is used by all core departments such as sales and marketing, management teams to generate
awareness and interpretation of customer needs and their grievances (Eichorn, 2018).Thus this component
supports firms to respond to customers with suitable solutions and support promptly and effectively as well
as meeting their needs. Thus it aids in enhancing reliability and confidence of customers and people on the
business.
QUESTION 3
a. Organizations should execute certain e-policies to protect their information content as privacy; confidence
and security are closely connected as are laws and ethics. Hence protection of information contents privacy
and security provision preserves trust as violation comprises a risk and threat to information contents
security and disturbs confidence. Also it runs the risk of diluting security and exhibits disrespect to morality,
ethics and principles of law. In fact implementation of e-policies is urgent and essential need to protect
privacy of content and prevent misuse in the universally driven information intensive environment. The
leverage of e-policies implementation is that it makes information content security more transparent so that
people at workplace are better informed and policy practices are fairer (Hwang, et al., 2016). The
implementation of e-policies at workplace is also essential to protect from possible risks that emerges with
technology and human users like information warfare, cyber terrorism etc. So, e-policies need to be vitally
propelled for information content protection at corporate management level.
Also e-policies to protect information content are essential for need to protect data privacy because of multi-
directional demand. This has emerged as significant function that supports development and implementation
5
b. The three primary elements of comprehensive CRM system are:
Sales Force automation: this is vital components of customer relationship management and exists in all
business systems. This component involves predicting, recording sales processing and maintaining trail of
vital interactions. This component helps to interpret revenue creation possibilities which make it very
essential for business. Moreover sales force automation component of CRM evaluates sales predictions and
performance of employees so as to attain overall betterment in the growth and enhancement of industry
(Soltani and Navimipour, 2016).
Lead management: this is another component of CRM system that is essentially used to maintain trail of
sales lead and their distribution. These are mostly common in sales and marketing enterprises and customer
service centers. The lead management component includes proficient administration of campaigns,
developing personalized forms, finalizing mail list etc. Further a wide study of buying patterns of customers
and prospective sales lead allows seizing more amount of sales lead to enhance the sales.
Customer service: this component of CRM system helps to gather customer inputs and data, information on
their purchase and patterns. After the information is gathered these are distributed to appropriate
departments and hence customer service is a vital component of CRM. The information offered by this
component is used by all core departments such as sales and marketing, management teams to generate
awareness and interpretation of customer needs and their grievances (Eichorn, 2018).Thus this component
supports firms to respond to customers with suitable solutions and support promptly and effectively as well
as meeting their needs. Thus it aids in enhancing reliability and confidence of customers and people on the
business.
QUESTION 3
a. Organizations should execute certain e-policies to protect their information content as privacy; confidence
and security are closely connected as are laws and ethics. Hence protection of information contents privacy
and security provision preserves trust as violation comprises a risk and threat to information contents
security and disturbs confidence. Also it runs the risk of diluting security and exhibits disrespect to morality,
ethics and principles of law. In fact implementation of e-policies is urgent and essential need to protect
privacy of content and prevent misuse in the universally driven information intensive environment. The
leverage of e-policies implementation is that it makes information content security more transparent so that
people at workplace are better informed and policy practices are fairer (Hwang, et al., 2016). The
implementation of e-policies at workplace is also essential to protect from possible risks that emerges with
technology and human users like information warfare, cyber terrorism etc. So, e-policies need to be vitally
propelled for information content protection at corporate management level.
Also e-policies to protect information content are essential for need to protect data privacy because of multi-
directional demand. This has emerged as significant function that supports development and implementation
5
MIS
of approaches vital for information security to insure privacy policies and potential mitigation measures.
Further these guidelines and practices enhance standards to make employees comply with them with
effective communication (Fitzgerald, 2016).These e-policies should be technically effective, financially
sound, legally justifiable, ethically consistent and socially acceptable so that implementation does not find
problems and information contents security decisions become more regulated.
b. The authentication technologies that can be utilized to prevent hackers from gaining access
to organizational systems are combination of biometric with digital signatures or digital
certificate plus password.
Biometric plus digital signature: this is a considerably strong authentication method as biometric is ideal
physical or biological characteristics and accurate biometric is possibly the strongest way to identify user.
However as biometric is susceptible to capture and replay type attacks via network so it needs additional
security through combination of digital signatures. The digital signature is combination of data hashing with
public key based encryption (Chang, et al., 2016). So biometric plus digital signature are modified
encryption technologies that operate by capturing block of data at one time and frequently use scrabble
algorithms to improve the bits. So it is impossible for hackers to modify original data insuring same output
from has function as these hash based signatures utilize cryptographically secure has functions like MD-5 or
SHA.
Digital certificate: digital certificates comprise data that are applied for authentication and security of
communication particularly unsecured networks like internet. These certificates issue a public key to user
who has subsequent private key. These certificates are digital ID issued by certification agencies that are
trusted bodies which look for identity of user. These digital certificates are valid for specified time and are
digitally signed using private keys. Digital certificates are files that have various identification information
of users like name, contact, email, public key and digital sign of certificate authority. Moreover in digital
certificate it is essential to authenticate machine or device used by user for interaction so it is advanced
authentication technology (Chang, et al., 2016). These are credible as they are issued by recognized bodies
i.e. Certification authority after verification of validity of user who applies for it.
QUESTION 4
a.
Yes No √ Information
Yes No √ Research
Yes No √ Analysis
Yes No √ Data
Yes √ No Input
Yes No √ Technology
Yes √ No Organization
6
of approaches vital for information security to insure privacy policies and potential mitigation measures.
Further these guidelines and practices enhance standards to make employees comply with them with
effective communication (Fitzgerald, 2016).These e-policies should be technically effective, financially
sound, legally justifiable, ethically consistent and socially acceptable so that implementation does not find
problems and information contents security decisions become more regulated.
b. The authentication technologies that can be utilized to prevent hackers from gaining access
to organizational systems are combination of biometric with digital signatures or digital
certificate plus password.
Biometric plus digital signature: this is a considerably strong authentication method as biometric is ideal
physical or biological characteristics and accurate biometric is possibly the strongest way to identify user.
However as biometric is susceptible to capture and replay type attacks via network so it needs additional
security through combination of digital signatures. The digital signature is combination of data hashing with
public key based encryption (Chang, et al., 2016). So biometric plus digital signature are modified
encryption technologies that operate by capturing block of data at one time and frequently use scrabble
algorithms to improve the bits. So it is impossible for hackers to modify original data insuring same output
from has function as these hash based signatures utilize cryptographically secure has functions like MD-5 or
SHA.
Digital certificate: digital certificates comprise data that are applied for authentication and security of
communication particularly unsecured networks like internet. These certificates issue a public key to user
who has subsequent private key. These certificates are digital ID issued by certification agencies that are
trusted bodies which look for identity of user. These digital certificates are valid for specified time and are
digitally signed using private keys. Digital certificates are files that have various identification information
of users like name, contact, email, public key and digital sign of certificate authority. Moreover in digital
certificate it is essential to authenticate machine or device used by user for interaction so it is advanced
authentication technology (Chang, et al., 2016). These are credible as they are issued by recognized bodies
i.e. Certification authority after verification of validity of user who applies for it.
QUESTION 4
a.
Yes No √ Information
Yes No √ Research
Yes No √ Analysis
Yes No √ Data
Yes √ No Input
Yes No √ Technology
Yes √ No Organization
6
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
MIS
Yes √ No Output
Yes √ No Management
Yes √ No Processing
b.
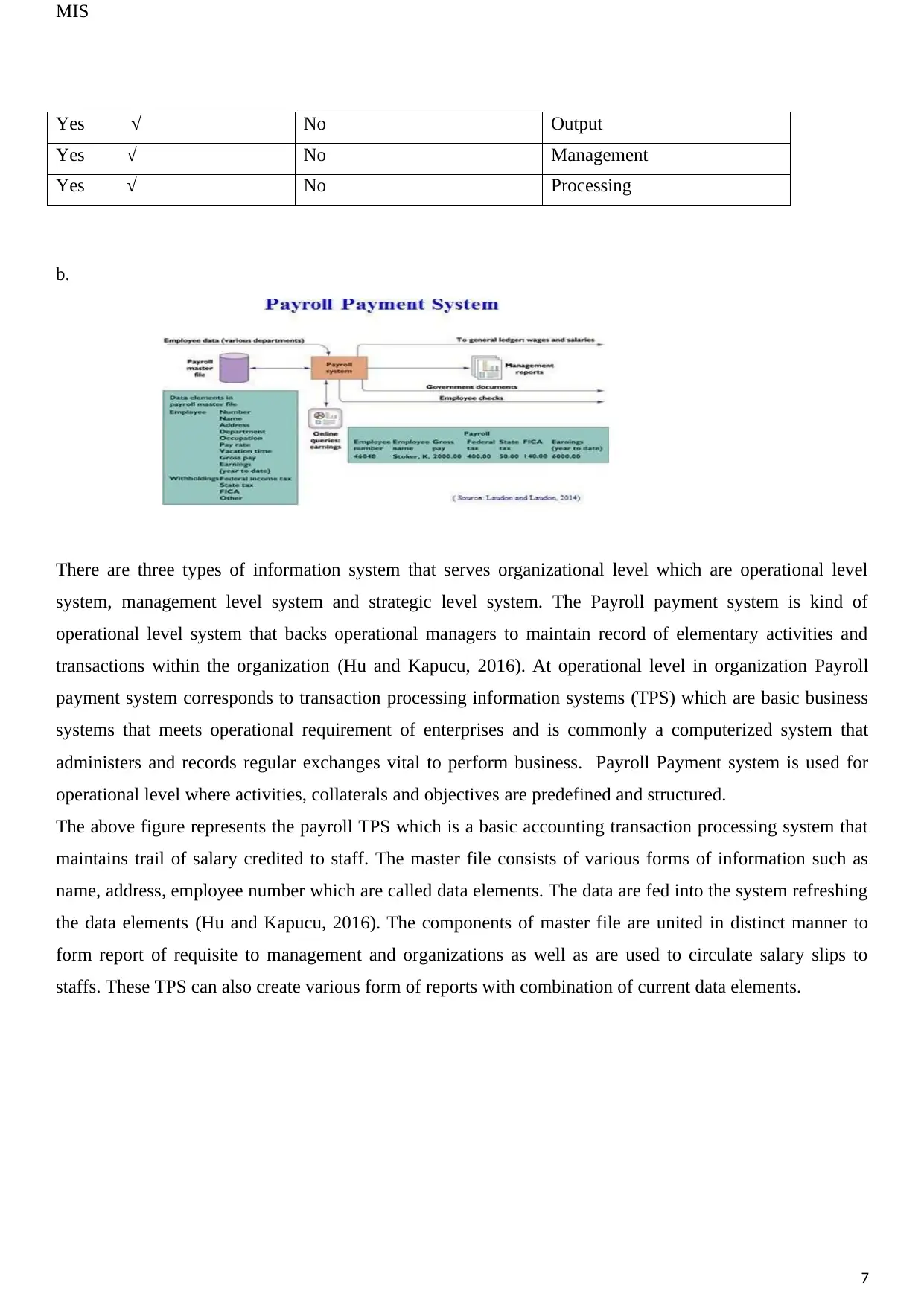
There are three types of information system that serves organizational level which are operational level
system, management level system and strategic level system. The Payroll payment system is kind of
operational level system that backs operational managers to maintain record of elementary activities and
transactions within the organization (Hu and Kapucu, 2016). At operational level in organization Payroll
payment system corresponds to transaction processing information systems (TPS) which are basic business
systems that meets operational requirement of enterprises and is commonly a computerized system that
administers and records regular exchanges vital to perform business. Payroll Payment system is used for
operational level where activities, collaterals and objectives are predefined and structured.
The above figure represents the payroll TPS which is a basic accounting transaction processing system that
maintains trail of salary credited to staff. The master file consists of various forms of information such as
name, address, employee number which are called data elements. The data are fed into the system refreshing
the data elements (Hu and Kapucu, 2016). The components of master file are united in distinct manner to
form report of requisite to management and organizations as well as are used to circulate salary slips to
staffs. These TPS can also create various form of reports with combination of current data elements.
7
Yes √ No Output
Yes √ No Management
Yes √ No Processing
b.
There are three types of information system that serves organizational level which are operational level
system, management level system and strategic level system. The Payroll payment system is kind of
operational level system that backs operational managers to maintain record of elementary activities and
transactions within the organization (Hu and Kapucu, 2016). At operational level in organization Payroll
payment system corresponds to transaction processing information systems (TPS) which are basic business
systems that meets operational requirement of enterprises and is commonly a computerized system that
administers and records regular exchanges vital to perform business. Payroll Payment system is used for
operational level where activities, collaterals and objectives are predefined and structured.
The above figure represents the payroll TPS which is a basic accounting transaction processing system that
maintains trail of salary credited to staff. The master file consists of various forms of information such as
name, address, employee number which are called data elements. The data are fed into the system refreshing
the data elements (Hu and Kapucu, 2016). The components of master file are united in distinct manner to
form report of requisite to management and organizations as well as are used to circulate salary slips to
staffs. These TPS can also create various form of reports with combination of current data elements.
7
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
MIS
QUESTION 5
a.
YES NO
The services a firm is capable of providing to its customers, suppliers, and
Employees are a direct function of its MIS infrastructure.
YES NO
The only service that will be affected by the quality of the MIS infrastructure is
the service provided to customers.
YES NO
Ideally, this infrastructure should support the firm’s business and information
Systems strategy.
YES NO
This infrastructure should support the firm’s information systems strategy,
Regardless of the business strategy.
YES NO
The above illustration focusses more than anything else on the relationship
Between Business Strategy and IT strategy.
YES NO
The above illustration represents the centrality of MIS infrastructure and
Services to the achievement of firm success.
Amazon is routinely sited as the most popular online shopping site. The main
YES NO reason for this is that Amazon has been in this business more than any other
Businesses.
YES NO
Ultimately, what the firm delivers to customers, its quality, is a direct function
Of the power of its infrastructure.
YES NO
New information technologies have a powerful impact on business and IT
Strategies, as well as the services that can be provided to customers.
8
QUESTION 5
a.
YES NO
The services a firm is capable of providing to its customers, suppliers, and
Employees are a direct function of its MIS infrastructure.
YES NO
The only service that will be affected by the quality of the MIS infrastructure is
the service provided to customers.
YES NO
Ideally, this infrastructure should support the firm’s business and information
Systems strategy.
YES NO
This infrastructure should support the firm’s information systems strategy,
Regardless of the business strategy.
YES NO
The above illustration focusses more than anything else on the relationship
Between Business Strategy and IT strategy.
YES NO
The above illustration represents the centrality of MIS infrastructure and
Services to the achievement of firm success.
Amazon is routinely sited as the most popular online shopping site. The main
YES NO reason for this is that Amazon has been in this business more than any other
Businesses.
YES NO
Ultimately, what the firm delivers to customers, its quality, is a direct function
Of the power of its infrastructure.
YES NO
New information technologies have a powerful impact on business and IT
Strategies, as well as the services that can be provided to customers.
8
MIS
b.
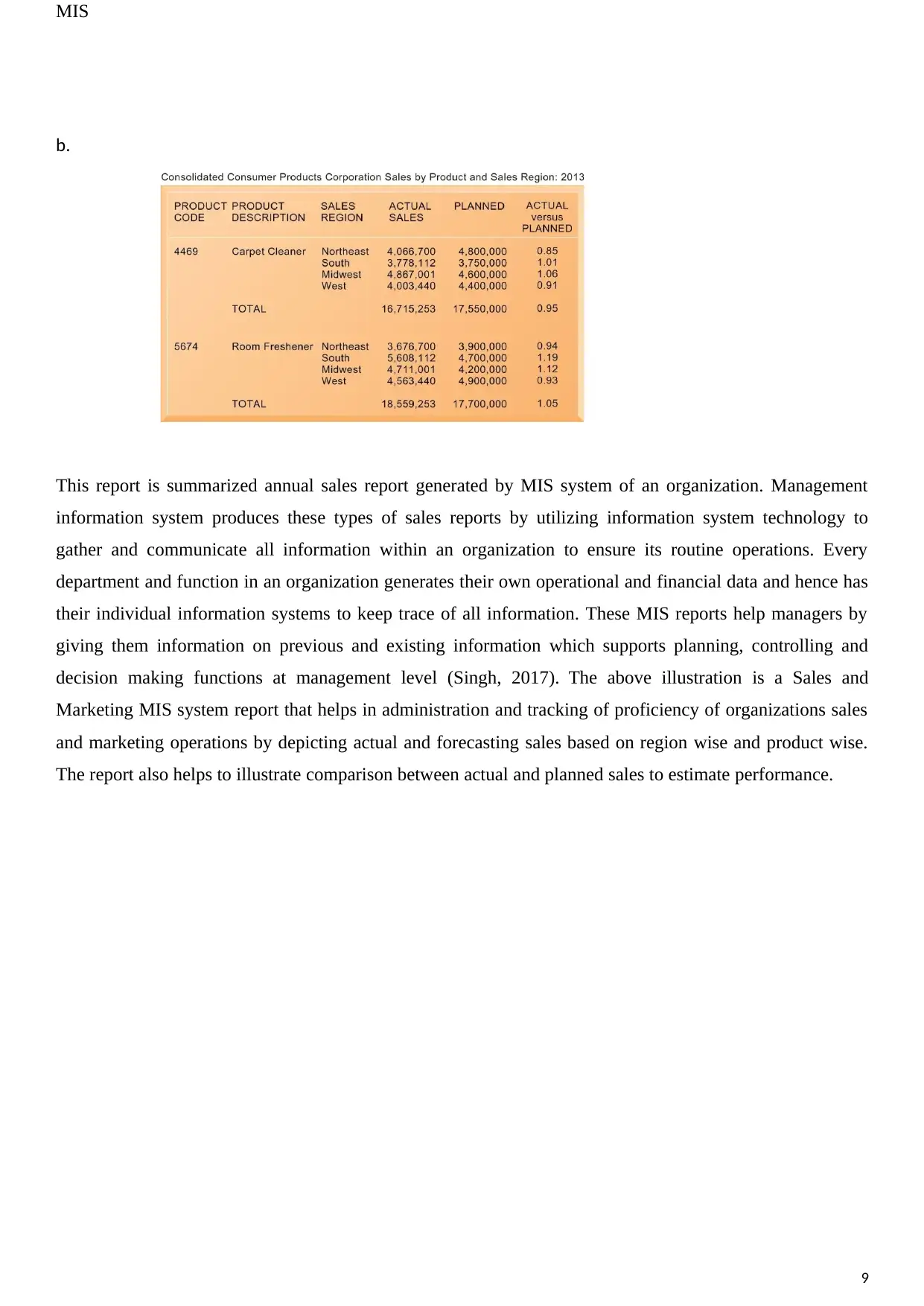
This report is summarized annual sales report generated by MIS system of an organization. Management
information system produces these types of sales reports by utilizing information system technology to
gather and communicate all information within an organization to ensure its routine operations. Every
department and function in an organization generates their own operational and financial data and hence has
their individual information systems to keep trace of all information. These MIS reports help managers by
giving them information on previous and existing information which supports planning, controlling and
decision making functions at management level (Singh, 2017). The above illustration is a Sales and
Marketing MIS system report that helps in administration and tracking of proficiency of organizations sales
and marketing operations by depicting actual and forecasting sales based on region wise and product wise.
The report also helps to illustrate comparison between actual and planned sales to estimate performance.
9
b.
This report is summarized annual sales report generated by MIS system of an organization. Management
information system produces these types of sales reports by utilizing information system technology to
gather and communicate all information within an organization to ensure its routine operations. Every
department and function in an organization generates their own operational and financial data and hence has
their individual information systems to keep trace of all information. These MIS reports help managers by
giving them information on previous and existing information which supports planning, controlling and
decision making functions at management level (Singh, 2017). The above illustration is a Sales and
Marketing MIS system report that helps in administration and tracking of proficiency of organizations sales
and marketing operations by depicting actual and forecasting sales based on region wise and product wise.
The report also helps to illustrate comparison between actual and planned sales to estimate performance.
9
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
MIS
QUESTION 6
Your order of Choice/s of Justification/s
Information Systems
Management information
system (MIS)
Executive Support System
(ESS)
MIS is management level information system that supports observing,
governing, management and decision making exercises. This will help
family owned business to interpret the working level of management
functions particularly operations with help of periodic performance reports.
Example, analysis of operations on sales management, inventory control,
production scheduling, profitability analysis etc. (Forrest and Nightingale,
2017).
ESS is strategic level information system that can be used by management
to develop strategies and solve strategic issues, long term trends that can
affect the business. It will help to identify and align capabilities of family
owned business with their external environment changes by analyzing cost
trends, sales forecast, operational planning for future, profit planning and
employment level planning (Forrest and Nightingale, 2017).
10
QUESTION 6
Your order of Choice/s of Justification/s
Information Systems
Management information
system (MIS)
Executive Support System
(ESS)
MIS is management level information system that supports observing,
governing, management and decision making exercises. This will help
family owned business to interpret the working level of management
functions particularly operations with help of periodic performance reports.
Example, analysis of operations on sales management, inventory control,
production scheduling, profitability analysis etc. (Forrest and Nightingale,
2017).
ESS is strategic level information system that can be used by management
to develop strategies and solve strategic issues, long term trends that can
affect the business. It will help to identify and align capabilities of family
owned business with their external environment changes by analyzing cost
trends, sales forecast, operational planning for future, profit planning and
employment level planning (Forrest and Nightingale, 2017).
10
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

MIS
PART B:
QUESTION 7
a. UPS made major transformation by embracing technologies like real time data, mobile,
connectivity, robotics, blockchain and sustainable technologies to combine their digital and
physical networks to regenerate efficiency, fleet and their improved management. Example UPS
created Advanced Technology Group (ATG) to make their logistics more technologically smart
and active (Singla, et al., 2017). These smart logistic networks delivers continual futuristic
development by conjoining shippers with receivers with data directed abilities. These help in
smart distribution, sorting, transport and delivery thus benefitting UPS to make their operations
faster and more lucid with customers. The ATG has improved visibility and effectiveness of UPS
through usage of data and analytics to develop decision making. UPS has also embraced On
Road Integrated Optimization and Navigation (ORION) system which is advanced technology
systems that has improved and reduced miles by optimizing routes. ORION makes alterations to
delivery track depending on real time information on traffic clogging, road conditions and
request for new package pickups to enhance efficiency. Also UPS is improving mobile
technology solutions by applying AI and advanced analytics to boost network with Network
Planning tools.
b. UPS with help of cloud technology can make their logistics networks more smart with
digitally and physically conjoined efficiencies, fleet and information systems. Cloud technology
will enable them to use real time data, AI, machine learning etc to optimize tracking and
processing of packages and freights. Moreover these also will help synchronize their
transportation fleet to enable operational and sustainable improvements with better exactness and
promptness for users from pickup to end destination. Example, UPS uses EDGE (Enhanced
Dynamic Global Execution) which is cloud based technology for facility optimization. These
improve their real time decision making of facilities (Satyanarayanan, 2017). EDGE program
describes where and how packages could be arranged and locates operational assets immediately.
c. UPS trucks have tracking technology whose outcomes are always not ethical as truckers get
de-motivated with constant monitoring through delivery information acquisition devices and
11
PART B:
QUESTION 7
a. UPS made major transformation by embracing technologies like real time data, mobile,
connectivity, robotics, blockchain and sustainable technologies to combine their digital and
physical networks to regenerate efficiency, fleet and their improved management. Example UPS
created Advanced Technology Group (ATG) to make their logistics more technologically smart
and active (Singla, et al., 2017). These smart logistic networks delivers continual futuristic
development by conjoining shippers with receivers with data directed abilities. These help in
smart distribution, sorting, transport and delivery thus benefitting UPS to make their operations
faster and more lucid with customers. The ATG has improved visibility and effectiveness of UPS
through usage of data and analytics to develop decision making. UPS has also embraced On
Road Integrated Optimization and Navigation (ORION) system which is advanced technology
systems that has improved and reduced miles by optimizing routes. ORION makes alterations to
delivery track depending on real time information on traffic clogging, road conditions and
request for new package pickups to enhance efficiency. Also UPS is improving mobile
technology solutions by applying AI and advanced analytics to boost network with Network
Planning tools.
b. UPS with help of cloud technology can make their logistics networks more smart with
digitally and physically conjoined efficiencies, fleet and information systems. Cloud technology
will enable them to use real time data, AI, machine learning etc to optimize tracking and
processing of packages and freights. Moreover these also will help synchronize their
transportation fleet to enable operational and sustainable improvements with better exactness and
promptness for users from pickup to end destination. Example, UPS uses EDGE (Enhanced
Dynamic Global Execution) which is cloud based technology for facility optimization. These
improve their real time decision making of facilities (Satyanarayanan, 2017). EDGE program
describes where and how packages could be arranged and locates operational assets immediately.
c. UPS trucks have tracking technology whose outcomes are always not ethical as truckers get
de-motivated with constant monitoring through delivery information acquisition devices and
11

MIS
sensors on delivery truck. This tracking creates devastation in lives of truckers and generates
workload stress as they track each detail including too much time spend on delivery stop,
keeping back of truck open for long etc which creates unethical pressure on truckers as they
potentially live threat of review or disciplinary actions. Also these tracking systems trace fuel
consumption and truckers are generally paid on miles covered, so sometimes these technology
systems create adverse ethical effects by creating burden for unpredictable delays on road that
could not be measured (Nebeker, et al., 2017).So truckers face a lot of risks and ethical
dilemmas. So the downside of these tracking systems is along with optimizing labor and making
process effective they create real havoc and wreck lives of truckers by establishing unpredictable
and unlivable schedules.
d. With use of tracking technology placed in trucks of UPS several security issues can be
encountered like potential malicious attacks on these which can prevent normal functioning of
vehicle and its tracking systems. Other security issues are theft, hijack and crash of data due to
intentional tampering with device that can interfere with normal functioning. The other issue is
tampering with functioning of device by insiders as UPS trucks are fitted with tracking systems
to monitor drivers and their usage (Delmonteil and Rancourt, 2017). Example positioning of GPS
antenna can be tampered by truckers that can disconnect signals received and as suck position of
trucks cannot be located.
e. Bargaining power of customer (low): customer base of UPS is huge and presence of
companies that can offer same services like UPS are less. Also UPS is well established globally
and delivers in almost all possible locations so more customers depend on UPS (Delmonteil and
Rancourt, 2017).
Threat of substitute (low): UPS service is used by several companies and people on
regular basis and they have not many substitutes for shipping products across country, so
substitute threat is low.
Threat of entrants (low): due to high investment cost barrier and large economies of scale
of UPS, they have low threat from new entry as with small volume of packages and large
capital required to run business they cannot compete with UPS.
12
sensors on delivery truck. This tracking creates devastation in lives of truckers and generates
workload stress as they track each detail including too much time spend on delivery stop,
keeping back of truck open for long etc which creates unethical pressure on truckers as they
potentially live threat of review or disciplinary actions. Also these tracking systems trace fuel
consumption and truckers are generally paid on miles covered, so sometimes these technology
systems create adverse ethical effects by creating burden for unpredictable delays on road that
could not be measured (Nebeker, et al., 2017).So truckers face a lot of risks and ethical
dilemmas. So the downside of these tracking systems is along with optimizing labor and making
process effective they create real havoc and wreck lives of truckers by establishing unpredictable
and unlivable schedules.
d. With use of tracking technology placed in trucks of UPS several security issues can be
encountered like potential malicious attacks on these which can prevent normal functioning of
vehicle and its tracking systems. Other security issues are theft, hijack and crash of data due to
intentional tampering with device that can interfere with normal functioning. The other issue is
tampering with functioning of device by insiders as UPS trucks are fitted with tracking systems
to monitor drivers and their usage (Delmonteil and Rancourt, 2017). Example positioning of GPS
antenna can be tampered by truckers that can disconnect signals received and as suck position of
trucks cannot be located.
e. Bargaining power of customer (low): customer base of UPS is huge and presence of
companies that can offer same services like UPS are less. Also UPS is well established globally
and delivers in almost all possible locations so more customers depend on UPS (Delmonteil and
Rancourt, 2017).
Threat of substitute (low): UPS service is used by several companies and people on
regular basis and they have not many substitutes for shipping products across country, so
substitute threat is low.
Threat of entrants (low): due to high investment cost barrier and large economies of scale
of UPS, they have low threat from new entry as with small volume of packages and large
capital required to run business they cannot compete with UPS.
12
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
1 out of 15
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.





