Facebook Data Privacy, GDPR, and E-Business Models Analysis
VerifiedAdded on 2023/01/12
|19
|6748
|64
Report
AI Summary
This report is divided into two parts, examining Facebook's data privacy crisis, including steps taken to address it, the purpose of GDPR, and its e-business and revenue models, along with associated benefits and challenges. The report also covers challenges faced by social networking websites. Part two delves into mobile applications, data vs. information, the UPS tracking system, RFID applications, GIS and CRM components, Porter's Five Forces, ethical concerns, security threats, OLAP, and other MIS software. The report provides a comprehensive overview of Facebook's data privacy issues and related topics.

MANAGEMENT
INFORMATION
SYSTEM
INFORMATION
SYSTEM
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

Table of Contents
INTRODUCTION...........................................................................................................................1
PART A...........................................................................................................................................1
Explanation of steps Facebook took to overcome data privacy crisis....................................1
Explanation of purpose of GDPR and description of privacy and data protection requirements
................................................................................................................................................2
Description of Facebook’s e-business and revenue models, their benefits and challenges.. .3
Evaluation of challenges faced by social networking websites and preparation for the same5
PART 2............................................................................................................................................6
Ques1. Examples of Mobile Applications and their business functions................................6
Ques2. Distinguishing between data and information............................................................7
Ques3. Features of the system chosen and reasons behind choice........................................8
Ques4. Description of input, processing, and output of the UPS’s package tracking system8
Ques5. Three examples of RFID for three business...............................................................9
Geographical information system.......................................................................................9
Three primary component of customer relationship management.................................9
Ques6. Comparison of numbers and application of Porter’s Five Forces and Competitive
Strategies..............................................................................................................................10
Ques7. Ethical Concerns and Security threats, Challenges and Vulnerabilities of Website 11
Ques8. Description of OLAP, Cloud Computing and other MIS software..........................13
CONCLUSION..............................................................................................................................14
REFERENCES..............................................................................................................................16
INTRODUCTION...........................................................................................................................1
PART A...........................................................................................................................................1
Explanation of steps Facebook took to overcome data privacy crisis....................................1
Explanation of purpose of GDPR and description of privacy and data protection requirements
................................................................................................................................................2
Description of Facebook’s e-business and revenue models, their benefits and challenges.. .3
Evaluation of challenges faced by social networking websites and preparation for the same5
PART 2............................................................................................................................................6
Ques1. Examples of Mobile Applications and their business functions................................6
Ques2. Distinguishing between data and information............................................................7
Ques3. Features of the system chosen and reasons behind choice........................................8
Ques4. Description of input, processing, and output of the UPS’s package tracking system8
Ques5. Three examples of RFID for three business...............................................................9
Geographical information system.......................................................................................9
Three primary component of customer relationship management.................................9
Ques6. Comparison of numbers and application of Porter’s Five Forces and Competitive
Strategies..............................................................................................................................10
Ques7. Ethical Concerns and Security threats, Challenges and Vulnerabilities of Website 11
Ques8. Description of OLAP, Cloud Computing and other MIS software..........................13
CONCLUSION..............................................................................................................................14
REFERENCES..............................................................................................................................16

INTRODUCTION
Management Information System refers to information system that is associated with
decision making within companies, along with analysing, control and coordination of
information available with the firm. With rise in digitalisation, it is one of the most crucial
systems which could be incorporated in an organisation, due to its effectiveness in managing a
range of information, which is necessary for the company to sustain, as well as grow within their
respective sectors. Furthermore, it also provides effective assistance to companies in regards to
using a range of technological alternatives that could dynamically and flexibly be used within
their respective organisations (Paré and et. al., 2015).
Therefore, in regards to the report below is divided into two parts. The first one is
associated with the case study of Facebook in relation to their Data Privacy issue, which includes
the steps which were taken by the organisation to overcome its data privacy crisis. Along with
this, it also includes purpose of GDPR and its several key requirements. Moreover, the overall e-
Business model of the company has been covered, including evaluation of key challenges which
social networking sites face. As for the report’s second part, it covers purposes of several mobile
applications, difference between data and information, an insight within the UPS tracking
system, examples related to RFID and information about GIS and CRM. Along with this, the
second part of this report also includes application of Porter’s Five Forces and Competitive
Strategies, along with ethical concerns related to storing and analysis of data and details about
OLAP and DBMS systems/
PART A
Explanation of steps Facebook took to overcome data privacy crisis
As per the case, it is clear that Facebook breached the privacy concerns of a lot of
individuals and surely jeopardised their personal and confidential information. However, in this
regard, the company took certain steps that are being explained below:
Restriction on Data Access: Facebook restricted the access of data that could have been
accessed by developers. The reason for this is because this data could also be hacked by
unethical parties, which could lead to breach of privacy (Chatterjee and et, al., 2015).
“Access Your Information” feature: Another step which the company took to overcome
its privacy issue is associated providing a feature to individuals in context of accessing
1
Management Information System refers to information system that is associated with
decision making within companies, along with analysing, control and coordination of
information available with the firm. With rise in digitalisation, it is one of the most crucial
systems which could be incorporated in an organisation, due to its effectiveness in managing a
range of information, which is necessary for the company to sustain, as well as grow within their
respective sectors. Furthermore, it also provides effective assistance to companies in regards to
using a range of technological alternatives that could dynamically and flexibly be used within
their respective organisations (Paré and et. al., 2015).
Therefore, in regards to the report below is divided into two parts. The first one is
associated with the case study of Facebook in relation to their Data Privacy issue, which includes
the steps which were taken by the organisation to overcome its data privacy crisis. Along with
this, it also includes purpose of GDPR and its several key requirements. Moreover, the overall e-
Business model of the company has been covered, including evaluation of key challenges which
social networking sites face. As for the report’s second part, it covers purposes of several mobile
applications, difference between data and information, an insight within the UPS tracking
system, examples related to RFID and information about GIS and CRM. Along with this, the
second part of this report also includes application of Porter’s Five Forces and Competitive
Strategies, along with ethical concerns related to storing and analysis of data and details about
OLAP and DBMS systems/
PART A
Explanation of steps Facebook took to overcome data privacy crisis
As per the case, it is clear that Facebook breached the privacy concerns of a lot of
individuals and surely jeopardised their personal and confidential information. However, in this
regard, the company took certain steps that are being explained below:
Restriction on Data Access: Facebook restricted the access of data that could have been
accessed by developers. The reason for this is because this data could also be hacked by
unethical parties, which could lead to breach of privacy (Chatterjee and et, al., 2015).
“Access Your Information” feature: Another step which the company took to overcome
its privacy issue is associated providing a feature to individuals in context of accessing
1
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

whatever activity they have performed on the website, as well as ways in which they
could manage their personal information and induce restrictions for third parties to view
specific information about them (Walsham, 2015).
Investigation of Applications: Another prominent step which was taken by this
organisation to overcome its data crisis issue is related to effective investigation
applications that has been using the data of customers through Facebook. This led the
company in taking action against the parties which are suspicious and deals in unethical
activities.
Hence, the company has taken effective steps in context of overcoming the data crisis issue
and providing safe and appropriate alternatives to customers who shares their personal
information with the company. Apart from this, the firm’s privacy policy is quite effective when
it comes to assisting individuals of managing and deleting their personal data. Both these
elements are explored as under:
Managing Data: In terms of managing the data, Facebook allow its users to have access
to their posts, profile, friend lists, comments, search histories, news feeds, as well as
locations. This provides the power to individuals in managing their own data, as well as
regulates the same in context of being seen or accessed by third parties.
Delete their Own Information: Facebook also provides its customers with the feature
associated with deleting their own personal information. It could be associated with their
posts, pictures, timelines, shares, likes, friends and even the search history, which
enhances the level of privacy and security for the customers and provides them with full
control and autonomy in relation to deleting the information they wish to (Vom Brocke
and Rosemann, 2014).
Explanation of purpose of GDPR and description of privacy and data protection requirements
GDPR refers to General Data Protection Regulation, which is a law imposed upon
protection of data and information, along with privacy of individuals within the European Union,
as well as European Economic Area. Through this regulation is imposed on people living in
these areas only, however, it also regulates the transfer of data from these geographical locations.
There are several purposes which GDPR fulfils for people in these areas, some of these are
explored below:
2
could manage their personal information and induce restrictions for third parties to view
specific information about them (Walsham, 2015).
Investigation of Applications: Another prominent step which was taken by this
organisation to overcome its data crisis issue is related to effective investigation
applications that has been using the data of customers through Facebook. This led the
company in taking action against the parties which are suspicious and deals in unethical
activities.
Hence, the company has taken effective steps in context of overcoming the data crisis issue
and providing safe and appropriate alternatives to customers who shares their personal
information with the company. Apart from this, the firm’s privacy policy is quite effective when
it comes to assisting individuals of managing and deleting their personal data. Both these
elements are explored as under:
Managing Data: In terms of managing the data, Facebook allow its users to have access
to their posts, profile, friend lists, comments, search histories, news feeds, as well as
locations. This provides the power to individuals in managing their own data, as well as
regulates the same in context of being seen or accessed by third parties.
Delete their Own Information: Facebook also provides its customers with the feature
associated with deleting their own personal information. It could be associated with their
posts, pictures, timelines, shares, likes, friends and even the search history, which
enhances the level of privacy and security for the customers and provides them with full
control and autonomy in relation to deleting the information they wish to (Vom Brocke
and Rosemann, 2014).
Explanation of purpose of GDPR and description of privacy and data protection requirements
GDPR refers to General Data Protection Regulation, which is a law imposed upon
protection of data and information, along with privacy of individuals within the European Union,
as well as European Economic Area. Through this regulation is imposed on people living in
these areas only, however, it also regulates the transfer of data from these geographical locations.
There are several purposes which GDPR fulfils for people in these areas, some of these are
explored below:
2
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

Rules Data Protection: The most appropriate purpose which GDPR fulfils is associated
with imposing rules for data protection. It imposes several norms for organisations, as
well as for customers to share their information to other websites or portals, which allows
exercising effective protection of information that is shared by the public (Prat, Comyn-
Wattiau and Akoka, 2015).
Law Enforcement: Another prominent purpose of GDPR is that it imposes several laws
and policies over sharing, receiving and using data and information that is available
online. It further helps in restricting the users or developers to unethically use these
information for their own personal objectives.
Alongside the purpose, it is also necessary to understand several privacy and data protection
requirements of the GDPR to further elaborate the working of this regulation. Therefore, few of
these requirements are described below:
Consent: The most crucial requirements of GDPR in relation to privacy and data
protection is that it is crucial that consent of parties is acquired before processing the
data that is directly related to them.
Anonymous Status: Another crucial requirement of GDPR is related to changing the
status of the acquired information as anonymous so that crucial information of
individuals could appropriately and effectively be protected from misuse.
Notifications: This is yet another crucial requirement in relation to privacy and data
protection that is practiced by GDPR is related to the fact that proper and timely
notifications be provided to individuals in case their data is being accessed by third
party, or is being used anonymously. This would provide better and more effective
protection to the people as well as to their personal data and information.
Data Protection Officers: GDPR is very particular when it comes to advising and
suggesting companies towards data protection and privacy and hence, one requirement
of this regulation is that firms must appoint data protection officers within the companies
to enhance the safety and security provided to the personal information of individuals
(Galliers and Leidner, 2014).
Description of Facebook’s e-business and revenue models, their benefits and challenges
Facebook’s E-business Model:
3
with imposing rules for data protection. It imposes several norms for organisations, as
well as for customers to share their information to other websites or portals, which allows
exercising effective protection of information that is shared by the public (Prat, Comyn-
Wattiau and Akoka, 2015).
Law Enforcement: Another prominent purpose of GDPR is that it imposes several laws
and policies over sharing, receiving and using data and information that is available
online. It further helps in restricting the users or developers to unethically use these
information for their own personal objectives.
Alongside the purpose, it is also necessary to understand several privacy and data protection
requirements of the GDPR to further elaborate the working of this regulation. Therefore, few of
these requirements are described below:
Consent: The most crucial requirements of GDPR in relation to privacy and data
protection is that it is crucial that consent of parties is acquired before processing the
data that is directly related to them.
Anonymous Status: Another crucial requirement of GDPR is related to changing the
status of the acquired information as anonymous so that crucial information of
individuals could appropriately and effectively be protected from misuse.
Notifications: This is yet another crucial requirement in relation to privacy and data
protection that is practiced by GDPR is related to the fact that proper and timely
notifications be provided to individuals in case their data is being accessed by third
party, or is being used anonymously. This would provide better and more effective
protection to the people as well as to their personal data and information.
Data Protection Officers: GDPR is very particular when it comes to advising and
suggesting companies towards data protection and privacy and hence, one requirement
of this regulation is that firms must appoint data protection officers within the companies
to enhance the safety and security provided to the personal information of individuals
(Galliers and Leidner, 2014).
Description of Facebook’s e-business and revenue models, their benefits and challenges
Facebook’s E-business Model:
3

The e-business model of Facebook is very diverse, as it provides a range of services to
the customers worldwide. For instance, it has a social media handle by the name Facebook, as
well as a messaging application by the name of Facebook Messenger, which allows customers to
share messages, pictures, videos and animations to one another. Moreover, this attention based
business model also has companies associated with the same like Whatsapp, Instagram and
Oculus, which are very effective in providing services to individuals (Liang, and et. al., 2015).
Facebook’s Revenue Model:
Facebook has a vast revenue model as it generates its revenue from a range of methods.
For example, it generates revenue from advertisements from other companies, along with the
payments which individuals provide to the company for their business operations through the
portal. Moreover, it also generates revenue through Oculus and using social media as a
workplace.
There are several benefits and challenges that are related to Facebook and are necessary to
be understood. Some of these elements are described below:
Benefits:
Social Integration: On an individual level, the major business benefit of Facebook is
related to social integration. It allows individuals from global ends to integrate socially
through this web portal, which provides a two-way benefit. For the firm, it means higher
individuals are attached form the company, which brings in more revenue. As for the
people, it becomes the means of networking, which helps them in enhancing their
business and corporate operations globally.
Promotion: Another prominent business benefit of Facebook is that it has transformed as
a means of promotion for various national and multinational organisations. Hence, with
every promotional material, this portal earns high profit which allows it to sustain and
grow within the marketplace. As for the companies which promote their offerings,
Facebook provides an opportunity for them to enhance their brand awareness which is
effective to increase their sales and revenue numbers (D'Arcy, Herath and Shoss, 2014).
Challenges:
Time Constraint: Setting and running up pages on Facebook requires a lot of time, as
well as investment to ensure that their brand awareness and likings are enhancing and is
4
the customers worldwide. For instance, it has a social media handle by the name Facebook, as
well as a messaging application by the name of Facebook Messenger, which allows customers to
share messages, pictures, videos and animations to one another. Moreover, this attention based
business model also has companies associated with the same like Whatsapp, Instagram and
Oculus, which are very effective in providing services to individuals (Liang, and et. al., 2015).
Facebook’s Revenue Model:
Facebook has a vast revenue model as it generates its revenue from a range of methods.
For example, it generates revenue from advertisements from other companies, along with the
payments which individuals provide to the company for their business operations through the
portal. Moreover, it also generates revenue through Oculus and using social media as a
workplace.
There are several benefits and challenges that are related to Facebook and are necessary to
be understood. Some of these elements are described below:
Benefits:
Social Integration: On an individual level, the major business benefit of Facebook is
related to social integration. It allows individuals from global ends to integrate socially
through this web portal, which provides a two-way benefit. For the firm, it means higher
individuals are attached form the company, which brings in more revenue. As for the
people, it becomes the means of networking, which helps them in enhancing their
business and corporate operations globally.
Promotion: Another prominent business benefit of Facebook is that it has transformed as
a means of promotion for various national and multinational organisations. Hence, with
every promotional material, this portal earns high profit which allows it to sustain and
grow within the marketplace. As for the companies which promote their offerings,
Facebook provides an opportunity for them to enhance their brand awareness which is
effective to increase their sales and revenue numbers (D'Arcy, Herath and Shoss, 2014).
Challenges:
Time Constraint: Setting and running up pages on Facebook requires a lot of time, as
well as investment to ensure that their brand awareness and likings are enhancing and is
4
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

preferred by customers. However, this could be a very big challenge for small companies
which don’t have ample human resources and effective time to ensure this aspect.
Reputation: When it comes to data privacy, the new policies have been effective, but it
does not stop individuals to criticise a brand. People sometimes go to extremes to defame
a brand which then gets viral and becomes negative for its reputation.
Evaluation of challenges faced by social networking websites and preparation for the same
There are several social networking websites available for individuals to socialise and
develop a personal and professional network on. However, these social networking sites face
several challenges which are crucial to be understood and dealt with in order to enhance their
sustainability and smooth business functioning within the marketplace.
Hence, in regards to this, below are certain challenges and preparations for the same:
Privacy Concerns: One of the major challenges which social networking websites is facing
is related to privacy. There are several individuals and corporations that share crucial and
confidential data with the websites which is later used for either the firm’s business purposes
or for other corporate function. However, this data could be hacked or could be accessed due
to weaker encryption and protection that could jeopardise the safety and privacy of the
information. In order to prepare for the same, the companies must ensure proper encryption
associated with their personal data, along with hiring professionals which could track the
usage of data and any unauthorised access as well.
Competition: Another prominent challenge related to social networking websites is
associated with enhanced competition within the social media. There are several websites
which have now grabbed the attention of individuals globally that makes tough for
companies to sometimes track, which leads to wastage of efforts and investment. Hence, in
order to deal with the same, it is very crucial for the firms to keep a track on the web traffic
of each of the networking sites, as well as ensure that it has a presence of each of the major
social networking portals to enhance the customer base and gain a competitive edge.
Brand Name: As mentioned above, social networking sites could be a source of promotion
as well as could present challenges in terms of brand name of the country. This could be
done by competitive organisations, critics or other individuals who might have had negative
experiences with the company. to prepare from this, firm must prepare communication
channels which could ensure that a constant medium of information exchanges be
5
which don’t have ample human resources and effective time to ensure this aspect.
Reputation: When it comes to data privacy, the new policies have been effective, but it
does not stop individuals to criticise a brand. People sometimes go to extremes to defame
a brand which then gets viral and becomes negative for its reputation.
Evaluation of challenges faced by social networking websites and preparation for the same
There are several social networking websites available for individuals to socialise and
develop a personal and professional network on. However, these social networking sites face
several challenges which are crucial to be understood and dealt with in order to enhance their
sustainability and smooth business functioning within the marketplace.
Hence, in regards to this, below are certain challenges and preparations for the same:
Privacy Concerns: One of the major challenges which social networking websites is facing
is related to privacy. There are several individuals and corporations that share crucial and
confidential data with the websites which is later used for either the firm’s business purposes
or for other corporate function. However, this data could be hacked or could be accessed due
to weaker encryption and protection that could jeopardise the safety and privacy of the
information. In order to prepare for the same, the companies must ensure proper encryption
associated with their personal data, along with hiring professionals which could track the
usage of data and any unauthorised access as well.
Competition: Another prominent challenge related to social networking websites is
associated with enhanced competition within the social media. There are several websites
which have now grabbed the attention of individuals globally that makes tough for
companies to sometimes track, which leads to wastage of efforts and investment. Hence, in
order to deal with the same, it is very crucial for the firms to keep a track on the web traffic
of each of the networking sites, as well as ensure that it has a presence of each of the major
social networking portals to enhance the customer base and gain a competitive edge.
Brand Name: As mentioned above, social networking sites could be a source of promotion
as well as could present challenges in terms of brand name of the country. This could be
done by competitive organisations, critics or other individuals who might have had negative
experiences with the company. to prepare from this, firm must prepare communication
channels which could ensure that a constant medium of information exchanges be
5
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

appropriately and effectively formulated and is used. This would help companies to resolve
customer queries and enhance transparency (Abdul-Hamid, 2014).
PART 2
Ques1. Examples of Mobile Applications and their business functions
Mobile applications are now become one of the crucial parts of everyone’s life, where it
supports people to simplify their day to day work, it also helps businesses to improve their
operations by getting connected over a network to their stakeholders. There are number of
mobile applications that are used within business functions such as LinkedIn which support in
performing recruitment business functions, Hootsuite that help in monitoring marketing function
and google analytical app that support in performing market research function of an organisation
(Kim, 2015). These all are the mobile based application which support a business in decision
making, improving its efficiency and solving the business problem which can be better
understood using following description,
LinkedIn: This is an application which help in connecting the business and job aspirants at a
single platform. An organisation can pool talent from LinkedIn which allow it in assessing
range of people having different skills and expertise to make better decision over
recruitment that further help in enhancing performance of organisation.
Hootsuite: It is an application which allows a business to access all its social media pages
over a single application. This saves time and allows the marketer to put their focuses
toward the marketing strategies or stuff without rooming around different applications which
support in improving operational efficiency. Other than this by assessing all app at single
platform it becomes easier to identify gap that are creating issues so that appropriate
decision can be undertaken to resolve them.
Google Analytical App: It helps in keeping track of the people that visit website of
organisation and product which is being viewed by people. This helps it in making decision
to represent the new arrivals with the product that capture their decision (Shi, Lee. and
Whinston, 2016). Other than this analytic data will further support in assessing the areas
where a business is lacking behind so that effective strategies can be formulated to resolve
those problems in timely manner which further support in improving efficiency.
6
customer queries and enhance transparency (Abdul-Hamid, 2014).
PART 2
Ques1. Examples of Mobile Applications and their business functions
Mobile applications are now become one of the crucial parts of everyone’s life, where it
supports people to simplify their day to day work, it also helps businesses to improve their
operations by getting connected over a network to their stakeholders. There are number of
mobile applications that are used within business functions such as LinkedIn which support in
performing recruitment business functions, Hootsuite that help in monitoring marketing function
and google analytical app that support in performing market research function of an organisation
(Kim, 2015). These all are the mobile based application which support a business in decision
making, improving its efficiency and solving the business problem which can be better
understood using following description,
LinkedIn: This is an application which help in connecting the business and job aspirants at a
single platform. An organisation can pool talent from LinkedIn which allow it in assessing
range of people having different skills and expertise to make better decision over
recruitment that further help in enhancing performance of organisation.
Hootsuite: It is an application which allows a business to access all its social media pages
over a single application. This saves time and allows the marketer to put their focuses
toward the marketing strategies or stuff without rooming around different applications which
support in improving operational efficiency. Other than this by assessing all app at single
platform it becomes easier to identify gap that are creating issues so that appropriate
decision can be undertaken to resolve them.
Google Analytical App: It helps in keeping track of the people that visit website of
organisation and product which is being viewed by people. This helps it in making decision
to represent the new arrivals with the product that capture their decision (Shi, Lee. and
Whinston, 2016). Other than this analytic data will further support in assessing the areas
where a business is lacking behind so that effective strategies can be formulated to resolve
those problems in timely manner which further support in improving efficiency.
6

Ques2. Distinguishing between data and information
Information system is basically defined as the software which support in organising and
analysing the raw data and convert it into a more meaningful information so that it can be used as
a base to take effective decision for the functioning of a business. The data and information are
different from one another that can be understood using following information,
Data Information
Data is a raw ands unorganised facts which is
required to be proceed in order to extract
meaning behind it as gathered data is useless
until it gets organised.
For example, when an organisation gathered
data regarding number of responses it get from
customers within particular set of time period.
When a gathered data is being processed,
structured, organised and presented within a
given context so that it can be become more
useful, then it is known as information.
For example, when the gathered data is
characterised in term of sales order, sources
through customers access and positive or
negative feedback, then it became the
information which help in formulating
decision.
The information system is mainly consisting of three dimensions such as organisational,
management and technological dimensions. Among them organisational dimension of
information system consists of functional specialties, culture, business process, organisational
hierarchy and political interest group which all support in planning and executing the
information system effectively (Al-Mamary. and et. al.,2014). On other side, management
dimension involves strategy, leadership and management behaviour that support in coordinating
and monitoring different work so that; organisational objectives can be achieved. While,
technological dimension involves computer software, hardware, technology and networking for
carrying out functions effectively. These all technologies mainly represent the resources that are
being shared in whole organisation and constitute an information technology infrastructure
which ensure smooth execution of operations as it help an organisation in building up a specific
system which provide a smooth flow of information and execution of actions effectively.
7
Information system is basically defined as the software which support in organising and
analysing the raw data and convert it into a more meaningful information so that it can be used as
a base to take effective decision for the functioning of a business. The data and information are
different from one another that can be understood using following information,
Data Information
Data is a raw ands unorganised facts which is
required to be proceed in order to extract
meaning behind it as gathered data is useless
until it gets organised.
For example, when an organisation gathered
data regarding number of responses it get from
customers within particular set of time period.
When a gathered data is being processed,
structured, organised and presented within a
given context so that it can be become more
useful, then it is known as information.
For example, when the gathered data is
characterised in term of sales order, sources
through customers access and positive or
negative feedback, then it became the
information which help in formulating
decision.
The information system is mainly consisting of three dimensions such as organisational,
management and technological dimensions. Among them organisational dimension of
information system consists of functional specialties, culture, business process, organisational
hierarchy and political interest group which all support in planning and executing the
information system effectively (Al-Mamary. and et. al.,2014). On other side, management
dimension involves strategy, leadership and management behaviour that support in coordinating
and monitoring different work so that; organisational objectives can be achieved. While,
technological dimension involves computer software, hardware, technology and networking for
carrying out functions effectively. These all technologies mainly represent the resources that are
being shared in whole organisation and constitute an information technology infrastructure
which ensure smooth execution of operations as it help an organisation in building up a specific
system which provide a smooth flow of information and execution of actions effectively.
7
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

Ques3. Features of the system chosen and reasons behind choice
By evaluating the problem of VES manufacturer it has been identified that Transaction
processing system would be more beneficial for the company as it help in keeping track with all
the transactions being performed. It is mainly a information processing system for a business
which involves the collection, modification as well as retrieval of all the transaction data. This
support in keeping track of all the data consolidated within a single system that help in ensuring
better management of data for effective functioning of business. The main reason behind
adopting this information system is that VES as it purchases majority of its vacuum part from
overseas suppliers which require it to keep track of all the transaction which make it easier to
keep record of order processing, billing, payment etc. Other than this it also maintains three
warehouses where stock is required to be tracked so that them remain product available as per
demand.
The Transaction processing system consider to be helpful as it is a system designed for
keeping track of transaction program and more helpful when deal is made over internet or
without a direct interaction among dealer as in case of VES. Its beneficial features are rapid
response, as TPS system help in providing quicker responses about product delivery so that
customers are not required to wait for longer period to get their product. Another important
feature is that it is a stock control system which process all the movement into within or outside
the business. It also acts as a system that support in tracking the record for requirement of raw
material in term of production process so that delay in work can be avoided.
Ques4. Description of input, processing, and output of the UPS’s package tracking system
It is an automated packaging tracking system which support in monitoring the packages
throughout the whole delivery process. This processing system mainly contains of three stages
such as input, processing and output. Among them Input stage includes the information related
with packaging, customer signature, delivery, current location, billing, time-card data as well as
clearance documentation. On other side, processing stage involve transition of data from central
computer and storage for its retrieval. This storage of data further helps in tracking the customer
account, drivers and other criteria for ensuring effective delivery of product. At last output stage
involve pickup and delivery time, location, route and package recipient. Additionally, it also
includes several reports such as packages for specific account or driver route for preparing a
management report.
8
By evaluating the problem of VES manufacturer it has been identified that Transaction
processing system would be more beneficial for the company as it help in keeping track with all
the transactions being performed. It is mainly a information processing system for a business
which involves the collection, modification as well as retrieval of all the transaction data. This
support in keeping track of all the data consolidated within a single system that help in ensuring
better management of data for effective functioning of business. The main reason behind
adopting this information system is that VES as it purchases majority of its vacuum part from
overseas suppliers which require it to keep track of all the transaction which make it easier to
keep record of order processing, billing, payment etc. Other than this it also maintains three
warehouses where stock is required to be tracked so that them remain product available as per
demand.
The Transaction processing system consider to be helpful as it is a system designed for
keeping track of transaction program and more helpful when deal is made over internet or
without a direct interaction among dealer as in case of VES. Its beneficial features are rapid
response, as TPS system help in providing quicker responses about product delivery so that
customers are not required to wait for longer period to get their product. Another important
feature is that it is a stock control system which process all the movement into within or outside
the business. It also acts as a system that support in tracking the record for requirement of raw
material in term of production process so that delay in work can be avoided.
Ques4. Description of input, processing, and output of the UPS’s package tracking system
It is an automated packaging tracking system which support in monitoring the packages
throughout the whole delivery process. This processing system mainly contains of three stages
such as input, processing and output. Among them Input stage includes the information related
with packaging, customer signature, delivery, current location, billing, time-card data as well as
clearance documentation. On other side, processing stage involve transition of data from central
computer and storage for its retrieval. This storage of data further helps in tracking the customer
account, drivers and other criteria for ensuring effective delivery of product. At last output stage
involve pickup and delivery time, location, route and package recipient. Additionally, it also
includes several reports such as packages for specific account or driver route for preparing a
management report.
8
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

There are three main dimensions on which UPS tracking system depends such as
organisational, management and technological dimension. Among them organisational
dimension involves a procedure of tracking packages as well as managing inventory and
providing information to centres (Ming, eBay Inc, 2014). This all help in organising all the
activities at one end to ensure efficient delivery. Management dimension help the people
working at service level by enhancing the ease of sending a package through UPS and checking
delivery status. Technology dimension involve software, network and compute system that
provide access to worldwide and provide better services.
Ques5. Three examples of RFID for three business
A Radio frequency identification is mainly used by several retailers in order to enhance the
customer shopping experience by simplifying their purchasing process. For example, Luxury
retailer Neiman Marcus uses RIFD as MemoMi memory mirror which allow the shoppers to get
a 360-degree view of product and its appearance in term of colour, pattern etc. Another example
of RFID can be seen as ‘Amazon GO store’ which allow the customers to grab item from store
and leave, the payment will automatically be deducted from their registered account. Another
example of RIFD can be seen as a minimising the issue of out of stock situation, as it help in
keeping track of stock items from warehouse shelves to sales floor (Shin and Eksioglu, 2014).
Geographical information system
It is a computer-based system used for capturing, checking, storing and displaying the data
related with the position on earth’s surface. GIS help in showing different kind of data on a
single map such as building, street etc. which enable people to easily analyse as well as
understand the pattern and relationship among different things.
Three primary component of customer relationship management
The customers relationship management is a software that act as a gateway for getting business
from customers by improving sale. There are three main components of CRM, such as,
Marketing Automation: CRM automatize several marketing practices such as streaming
marketing campaign across email, website etc, lead analytics and ensuring a better flow
of information to customers that help in attracting them to organisational offers.
Sales Force Automation: It provide a link between marketing and sales department,
where by arranging campaign the marketing can push leads to sale team which then help
9
organisational, management and technological dimension. Among them organisational
dimension involves a procedure of tracking packages as well as managing inventory and
providing information to centres (Ming, eBay Inc, 2014). This all help in organising all the
activities at one end to ensure efficient delivery. Management dimension help the people
working at service level by enhancing the ease of sending a package through UPS and checking
delivery status. Technology dimension involve software, network and compute system that
provide access to worldwide and provide better services.
Ques5. Three examples of RFID for three business
A Radio frequency identification is mainly used by several retailers in order to enhance the
customer shopping experience by simplifying their purchasing process. For example, Luxury
retailer Neiman Marcus uses RIFD as MemoMi memory mirror which allow the shoppers to get
a 360-degree view of product and its appearance in term of colour, pattern etc. Another example
of RFID can be seen as ‘Amazon GO store’ which allow the customers to grab item from store
and leave, the payment will automatically be deducted from their registered account. Another
example of RIFD can be seen as a minimising the issue of out of stock situation, as it help in
keeping track of stock items from warehouse shelves to sales floor (Shin and Eksioglu, 2014).
Geographical information system
It is a computer-based system used for capturing, checking, storing and displaying the data
related with the position on earth’s surface. GIS help in showing different kind of data on a
single map such as building, street etc. which enable people to easily analyse as well as
understand the pattern and relationship among different things.
Three primary component of customer relationship management
The customers relationship management is a software that act as a gateway for getting business
from customers by improving sale. There are three main components of CRM, such as,
Marketing Automation: CRM automatize several marketing practices such as streaming
marketing campaign across email, website etc, lead analytics and ensuring a better flow
of information to customers that help in attracting them to organisational offers.
Sales Force Automation: It provide a link between marketing and sales department,
where by arranging campaign the marketing can push leads to sale team which then help
9
in converting them into customer with appropriate strategy (Fan, Tao, Deng and Li,
2015).
Customer Services: It is most effective component that help a company in keeping
customers satisfied by tracking their responses and feedback to resolve their issues and
provide after sale services.
Ques6. Comparison of numbers and application of Porter’s Five Forces and Competitive
Strategies
Comparison and Interpretation of numbers in relation to above mentioned numbers
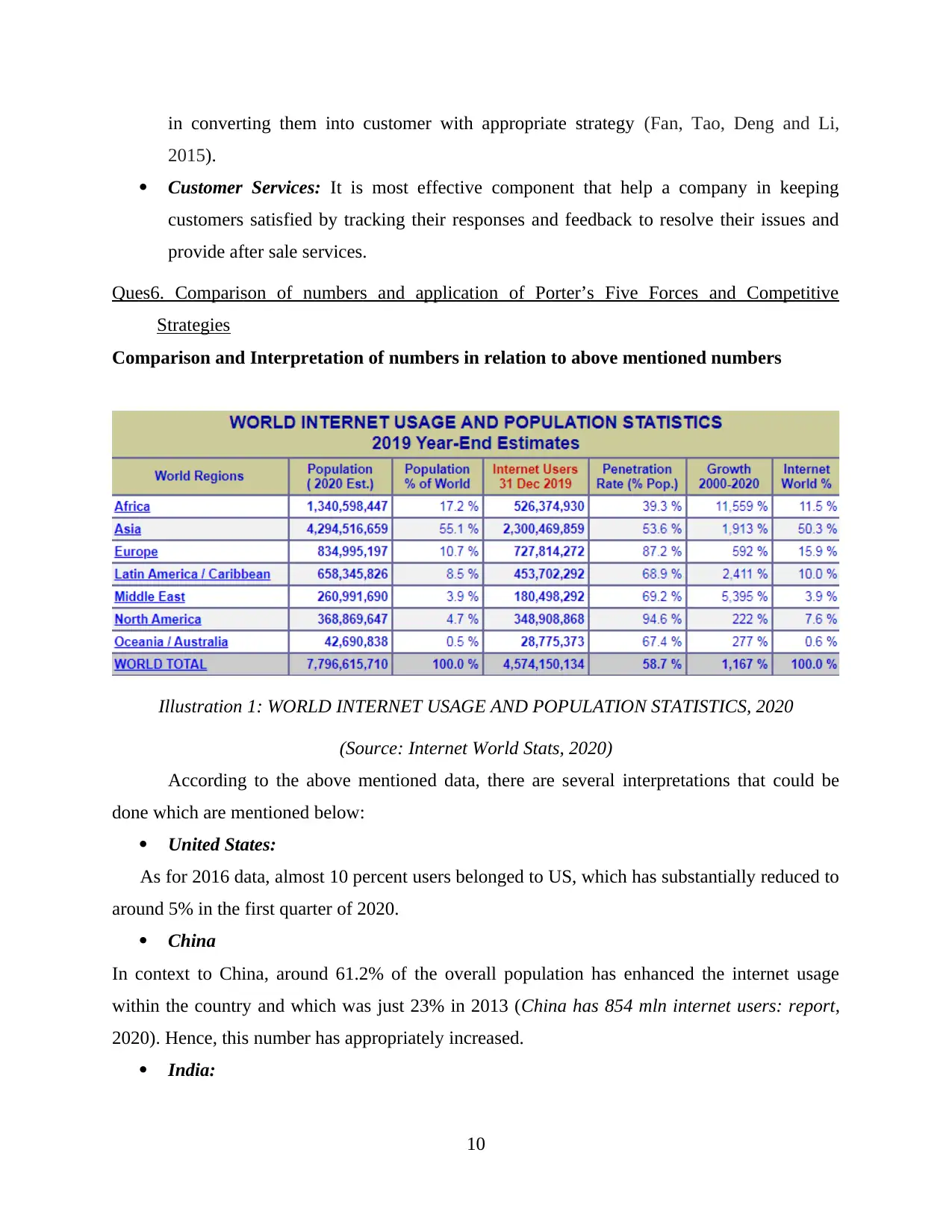
Illustration 1: WORLD INTERNET USAGE AND POPULATION STATISTICS, 2020
(Source: Internet World Stats, 2020)
According to the above mentioned data, there are several interpretations that could be
done which are mentioned below:
United States:
As for 2016 data, almost 10 percent users belonged to US, which has substantially reduced to
around 5% in the first quarter of 2020.
China
In context to China, around 61.2% of the overall population has enhanced the internet usage
within the country and which was just 23% in 2013 (China has 854 mln internet users: report,
2020). Hence, this number has appropriately increased.
India:
10
2015).
Customer Services: It is most effective component that help a company in keeping
customers satisfied by tracking their responses and feedback to resolve their issues and
provide after sale services.
Ques6. Comparison of numbers and application of Porter’s Five Forces and Competitive
Strategies
Comparison and Interpretation of numbers in relation to above mentioned numbers
Illustration 1: WORLD INTERNET USAGE AND POPULATION STATISTICS, 2020
(Source: Internet World Stats, 2020)
According to the above mentioned data, there are several interpretations that could be
done which are mentioned below:
United States:
As for 2016 data, almost 10 percent users belonged to US, which has substantially reduced to
around 5% in the first quarter of 2020.
China
In context to China, around 61.2% of the overall population has enhanced the internet usage
within the country and which was just 23% in 2013 (China has 854 mln internet users: report,
2020). Hence, this number has appropriately increased.
India:
10
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
1 out of 19
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.




