University BN205 Project Management Risk Management Plan
VerifiedAdded on 2020/02/18
|7
|1459
|38
Project
AI Summary
This project presents a Risk Management Plan for a case study at Silicon Forest State University (SFSU). The plan addresses the transition of the IT department's ticketing system from separate front-end and back-end software to a unified system. The plan includes risk identification, focusing on threats like communication gaps and cost/schedule overruns, and opportunities like potential early project completion. Risk analysis assesses the probability and impact of each identified risk, followed by the development of a risk response plan to mitigate or enhance these factors. The plan also details monitoring and controlling mechanisms to track risks throughout the project lifecycle, ensuring the project's success. The document concludes with a justification of the risk management approach and emphasizes the importance of ongoing monitoring and new risk identification.
University name
BN205 Project Management
Risk Management Plan
Student’s Name:
BN205 Project Management
Risk Management Plan
Student’s Name:
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

BN205 RISK MANAGEMENT
Executive summary
The topic RISK MANAGEMENT is the tool which must be used by the controlling manager or the project
manager to envisage the presence of any threat or opportunity which may arise in future1. Not only the
items can be identified, the threats and opportunities can also be analyzed on the basis of its ‘impact’ of
happening and ‘probability’ of its occurring. Now after analyzing the items are categorized according to
the position obtained and the response plan is developed to ‘avoid’, ‘accept’, ‘share’ or ‘mitigate’. In
current report we shall study such steps with respect to the case study.
Table of Contents
Introduction.................................................................................................................................................2
Background of case study............................................................................................................................2
Risk Management Plan................................................................................................................................2
Risk Identification........................................................................................................................................3
Risk Analysis................................................................................................................................................3
Risk response plan.......................................................................................................................................4
Monitoring and Controlling Risk..................................................................................................................4
Evaluation / Justification.............................................................................................................................4
Conclusion...................................................................................................................................................4
References...................................................................................................................................................5
1
Executive summary
The topic RISK MANAGEMENT is the tool which must be used by the controlling manager or the project
manager to envisage the presence of any threat or opportunity which may arise in future1. Not only the
items can be identified, the threats and opportunities can also be analyzed on the basis of its ‘impact’ of
happening and ‘probability’ of its occurring. Now after analyzing the items are categorized according to
the position obtained and the response plan is developed to ‘avoid’, ‘accept’, ‘share’ or ‘mitigate’. In
current report we shall study such steps with respect to the case study.
Table of Contents
Introduction.................................................................................................................................................2
Background of case study............................................................................................................................2
Risk Management Plan................................................................................................................................2
Risk Identification........................................................................................................................................3
Risk Analysis................................................................................................................................................3
Risk response plan.......................................................................................................................................4
Monitoring and Controlling Risk..................................................................................................................4
Evaluation / Justification.............................................................................................................................4
Conclusion...................................................................................................................................................4
References...................................................................................................................................................5
1

BN205 RISK MANAGEMENT
Introduction
RISK MANAGEMENT technique provides the exposure of the team members to the possible threats and
opportunities which may come across the project life cycle and can put either negative or positive
impact on the three constraints of the project2. A risk always has a tendency to put impact on the time
schedule, budgeted cost or the scope of work and then obviously the quality requirement of the project.
So, it must be assessed properly as provided below.
Background of case study
In Silicon Forest State University (SFSU), all the bugs which ever are generated while working in any of
the department in University is being take care by the centralized IT department ‘Office of Information
and Technology’ (OIT). Bugs are being monitored and tracked by using ‘Remedy’ software based on
windows by the front end and ‘Request Tracker’ is used by the users of back end supported by UNIX. So
in the same university itself the front end and back end users uses different software for ticketing
purpose. It causes problem within the system due to manual data transfer from ‘Remedy’ to ‘Request
Tracker’. To avoid any such issue, Head OIT has decided to replace the software being used by front end
people by ‘Request Tracker’ to maintain harmony in the system. With this concept as background, Head
OIT has appointed Ron as the leader of the project and he shall be cooperated by Harry of equivalent
organizational level of Ron. Ron shall take care of the interface issue and Harry the back end support
issues.
Risk Management Plan
The RISK MANAGEMENT plan is the document which is being developed in planning stage to describe
the method or plan to deal with the possible threats and opportunities. This document becomes the
basis of all further calculations and assessment3. According to this plan, all the threats and opportunities
are required to be first identified by the front and back end both the users. After the identification is
done, the list of such items are required to be analyzed by the team on the basis of the probability and
impact of occurring the threat or opportunity and further on the basis of the positions the response plan
or the mitigation plan is required to be developed by the team member. That’s it, all the work related to
risk mitigation is over, but the administration is pending. As a part of monitoring and controlling, all the
listed threats and opportunities are required to be monitored in every review meeting and in case of
generation of any new risk, it must also be followed through the same route.
2
Introduction
RISK MANAGEMENT technique provides the exposure of the team members to the possible threats and
opportunities which may come across the project life cycle and can put either negative or positive
impact on the three constraints of the project2. A risk always has a tendency to put impact on the time
schedule, budgeted cost or the scope of work and then obviously the quality requirement of the project.
So, it must be assessed properly as provided below.
Background of case study
In Silicon Forest State University (SFSU), all the bugs which ever are generated while working in any of
the department in University is being take care by the centralized IT department ‘Office of Information
and Technology’ (OIT). Bugs are being monitored and tracked by using ‘Remedy’ software based on
windows by the front end and ‘Request Tracker’ is used by the users of back end supported by UNIX. So
in the same university itself the front end and back end users uses different software for ticketing
purpose. It causes problem within the system due to manual data transfer from ‘Remedy’ to ‘Request
Tracker’. To avoid any such issue, Head OIT has decided to replace the software being used by front end
people by ‘Request Tracker’ to maintain harmony in the system. With this concept as background, Head
OIT has appointed Ron as the leader of the project and he shall be cooperated by Harry of equivalent
organizational level of Ron. Ron shall take care of the interface issue and Harry the back end support
issues.
Risk Management Plan
The RISK MANAGEMENT plan is the document which is being developed in planning stage to describe
the method or plan to deal with the possible threats and opportunities. This document becomes the
basis of all further calculations and assessment3. According to this plan, all the threats and opportunities
are required to be first identified by the front and back end both the users. After the identification is
done, the list of such items are required to be analyzed by the team on the basis of the probability and
impact of occurring the threat or opportunity and further on the basis of the positions the response plan
or the mitigation plan is required to be developed by the team member. That’s it, all the work related to
risk mitigation is over, but the administration is pending. As a part of monitoring and controlling, all the
listed threats and opportunities are required to be monitored in every review meeting and in case of
generation of any new risk, it must also be followed through the same route.
2
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
BN205 RISK MANAGEMENT
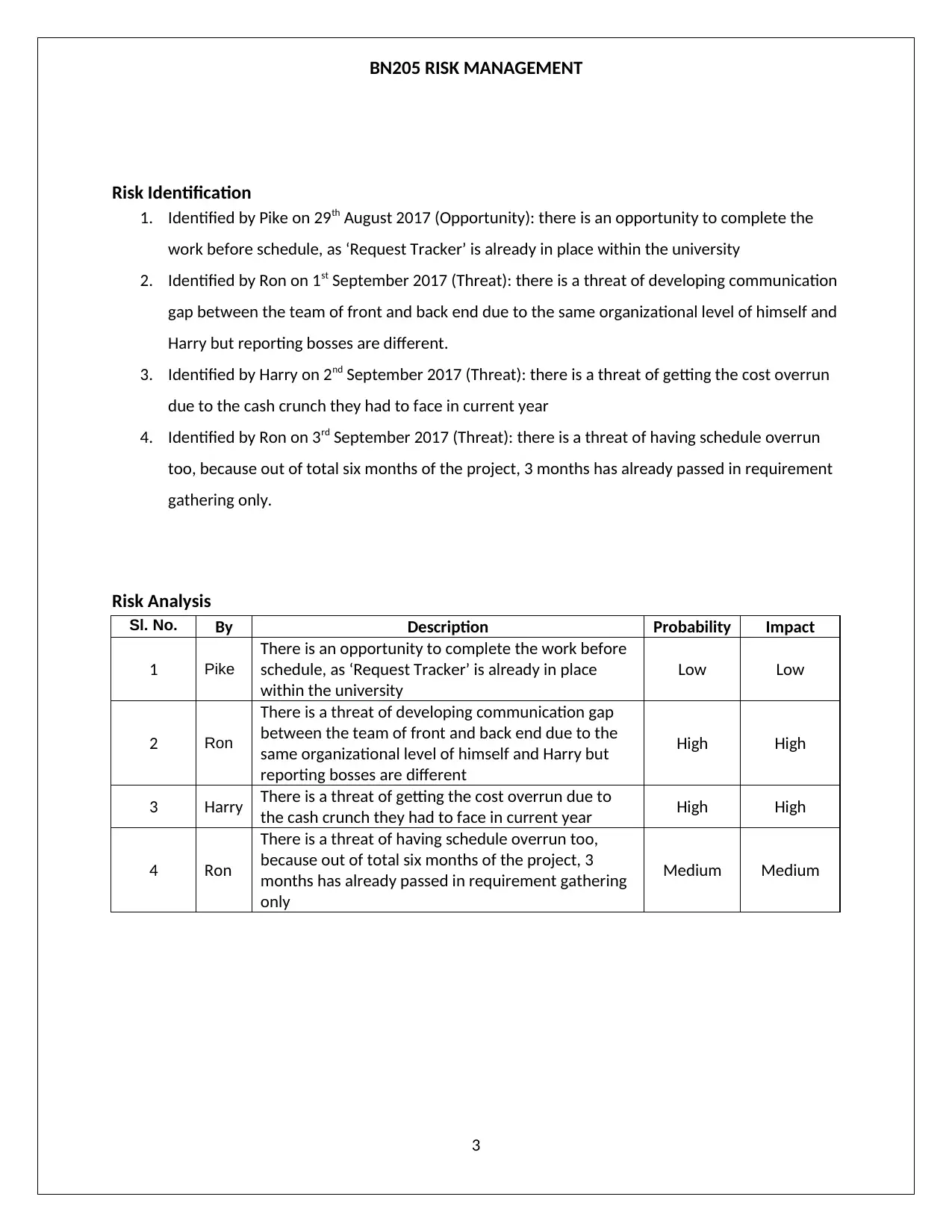
Risk Identification
1. Identified by Pike on 29th August 2017 (Opportunity): there is an opportunity to complete the
work before schedule, as ‘Request Tracker’ is already in place within the university
2. Identified by Ron on 1st September 2017 (Threat): there is a threat of developing communication
gap between the team of front and back end due to the same organizational level of himself and
Harry but reporting bosses are different.
3. Identified by Harry on 2nd September 2017 (Threat): there is a threat of getting the cost overrun
due to the cash crunch they had to face in current year
4. Identified by Ron on 3rd September 2017 (Threat): there is a threat of having schedule overrun
too, because out of total six months of the project, 3 months has already passed in requirement
gathering only.
Risk Analysis
Sl. No. By Description Probability Impact
1 Pike
There is an opportunity to complete the work before
schedule, as ‘Request Tracker’ is already in place
within the university
Low Low
2 Ron
There is a threat of developing communication gap
between the team of front and back end due to the
same organizational level of himself and Harry but
reporting bosses are different
High High
3 Harry There is a threat of getting the cost overrun due to
the cash crunch they had to face in current year High High
4 Ron
There is a threat of having schedule overrun too,
because out of total six months of the project, 3
months has already passed in requirement gathering
only
Medium Medium
3
Risk Identification
1. Identified by Pike on 29th August 2017 (Opportunity): there is an opportunity to complete the
work before schedule, as ‘Request Tracker’ is already in place within the university
2. Identified by Ron on 1st September 2017 (Threat): there is a threat of developing communication
gap between the team of front and back end due to the same organizational level of himself and
Harry but reporting bosses are different.
3. Identified by Harry on 2nd September 2017 (Threat): there is a threat of getting the cost overrun
due to the cash crunch they had to face in current year
4. Identified by Ron on 3rd September 2017 (Threat): there is a threat of having schedule overrun
too, because out of total six months of the project, 3 months has already passed in requirement
gathering only.
Risk Analysis
Sl. No. By Description Probability Impact
1 Pike
There is an opportunity to complete the work before
schedule, as ‘Request Tracker’ is already in place
within the university
Low Low
2 Ron
There is a threat of developing communication gap
between the team of front and back end due to the
same organizational level of himself and Harry but
reporting bosses are different
High High
3 Harry There is a threat of getting the cost overrun due to
the cash crunch they had to face in current year High High
4 Ron
There is a threat of having schedule overrun too,
because out of total six months of the project, 3
months has already passed in requirement gathering
only
Medium Medium
3
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
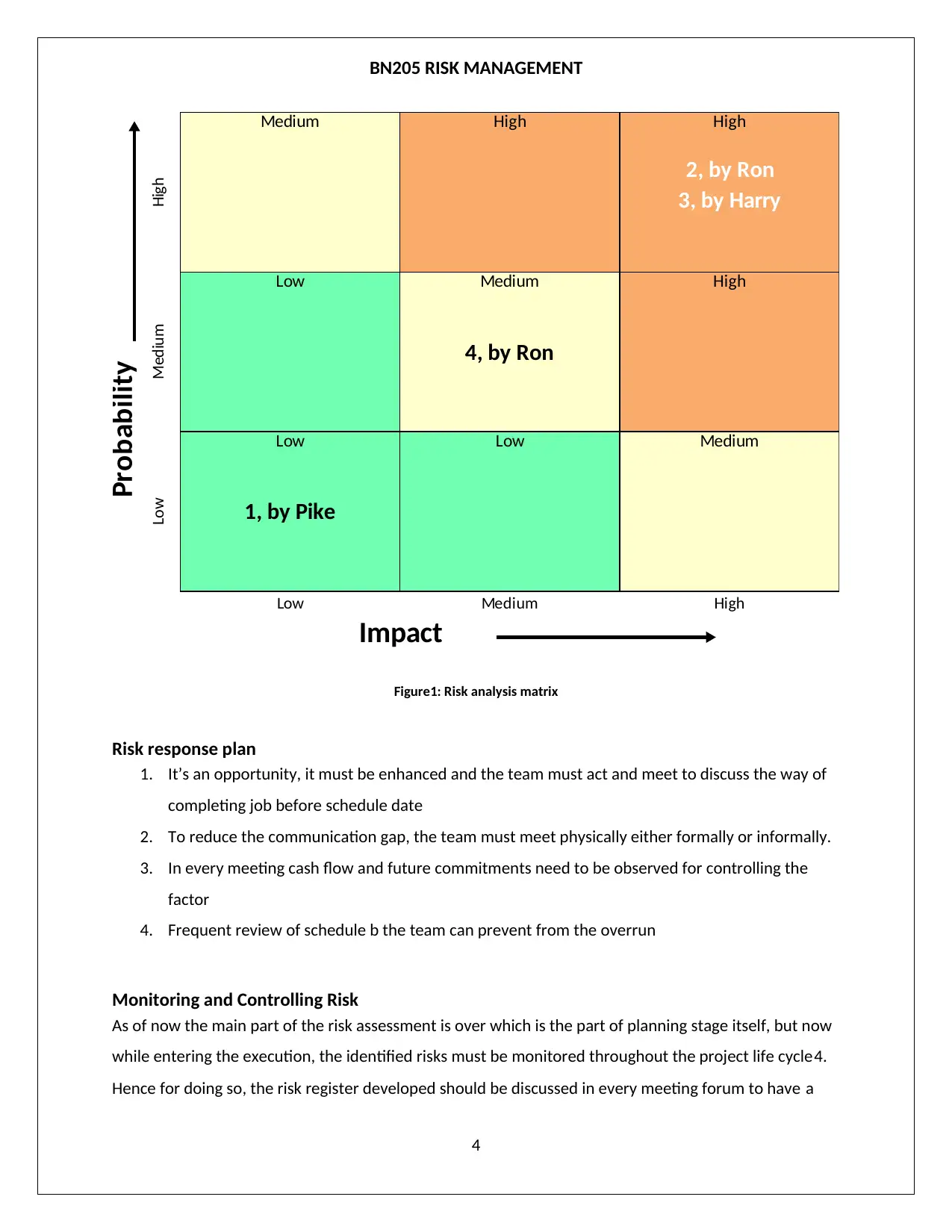
BN205 RISK MANAGEMENT
High
Medium High High
2, by Ron
3, by Harry
Medium
Low Medium
4, by Ron
High
Low
Low
1, by Pike
Low Medium
Low Medium High
Impact
Probability
Figure1: Risk analysis matrix
Risk response plan
1. It’s an opportunity, it must be enhanced and the team must act and meet to discuss the way of
completing job before schedule date
2. To reduce the communication gap, the team must meet physically either formally or informally.
3. In every meeting cash flow and future commitments need to be observed for controlling the
factor
4. Frequent review of schedule b the team can prevent from the overrun
Monitoring and Controlling Risk
As of now the main part of the risk assessment is over which is the part of planning stage itself, but now
while entering the execution, the identified risks must be monitored throughout the project life cycle4.
Hence for doing so, the risk register developed should be discussed in every meeting forum to have a
4
High
Medium High High
2, by Ron
3, by Harry
Medium
Low Medium
4, by Ron
High
Low
Low
1, by Pike
Low Medium
Low Medium High
Impact
Probability
Figure1: Risk analysis matrix
Risk response plan
1. It’s an opportunity, it must be enhanced and the team must act and meet to discuss the way of
completing job before schedule date
2. To reduce the communication gap, the team must meet physically either formally or informally.
3. In every meeting cash flow and future commitments need to be observed for controlling the
factor
4. Frequent review of schedule b the team can prevent from the overrun
Monitoring and Controlling Risk
As of now the main part of the risk assessment is over which is the part of planning stage itself, but now
while entering the execution, the identified risks must be monitored throughout the project life cycle4.
Hence for doing so, the risk register developed should be discussed in every meeting forum to have a
4

BN205 RISK MANAGEMENT
common understanding among the team regarding the current positions of the threats and
opportunities. Moreover, the search for new threats should not be stopped, all the team members must
be motivated enough to always report in case of any new risk arises and again the same process of
analysis and response planning is required to be done.
Justification
It is to be justified that the threats and opportunities identified are the actual facts of the case study,
these can happen in real world too. All the identified risks are analyzed properly using risk matrix
diagram and the response plan is also done correctly.
Conclusion
Finally it can be concluded that the risks are identified, analyzed, ranked and response plan are
developed as per the procedure mentioned in the RISK MANAGEMENT plan. So the threats and
opportunities are once mentioned should be now monitored or the whole life cycle5. By following the
procedure as mentioned the OIT can ensure to complete the project without having cost and schedule
overrun. Even the communication gap between the teams can also be reduced by following the
procedure mentioned in response plan. Moving further in execution phase, the risks must be monitored
and new search must be continued till project close-out.
References
x
[1] Australian Government. (2017) http://www.austrac.gov.au. [Online].
http://www.austrac.gov.au/risk-management-tool-small-medium-sized-businesses
[2] Institute of Risk Management. (2016) About Risk Management. [Online].
https://www.theirm.org/the-risk-profession/risk-management.aspx
[3] Victoria State Government, "Victorian Government Risk Management Framework," Risk
Management –Principles and Guidelines, 2016.
[4] et al. Wiley. (2017) 11.2 Risk Management Process. [Online]. https://pm4id.org/chapter/11-2-risk-
management-process/
[5] WordPress. (2009, July) Eight to Late: Cox’s risk matrix theorem and its implications for project risk
management. [Online]. https://eight2late.wordpress.com/2009/07/01/cox%E2%80%99s-risk-matrix-
5
common understanding among the team regarding the current positions of the threats and
opportunities. Moreover, the search for new threats should not be stopped, all the team members must
be motivated enough to always report in case of any new risk arises and again the same process of
analysis and response planning is required to be done.
Justification
It is to be justified that the threats and opportunities identified are the actual facts of the case study,
these can happen in real world too. All the identified risks are analyzed properly using risk matrix
diagram and the response plan is also done correctly.
Conclusion
Finally it can be concluded that the risks are identified, analyzed, ranked and response plan are
developed as per the procedure mentioned in the RISK MANAGEMENT plan. So the threats and
opportunities are once mentioned should be now monitored or the whole life cycle5. By following the
procedure as mentioned the OIT can ensure to complete the project without having cost and schedule
overrun. Even the communication gap between the teams can also be reduced by following the
procedure mentioned in response plan. Moving further in execution phase, the risks must be monitored
and new search must be continued till project close-out.
References
x
[1] Australian Government. (2017) http://www.austrac.gov.au. [Online].
http://www.austrac.gov.au/risk-management-tool-small-medium-sized-businesses
[2] Institute of Risk Management. (2016) About Risk Management. [Online].
https://www.theirm.org/the-risk-profession/risk-management.aspx
[3] Victoria State Government, "Victorian Government Risk Management Framework," Risk
Management –Principles and Guidelines, 2016.
[4] et al. Wiley. (2017) 11.2 Risk Management Process. [Online]. https://pm4id.org/chapter/11-2-risk-
management-process/
[5] WordPress. (2009, July) Eight to Late: Cox’s risk matrix theorem and its implications for project risk
management. [Online]. https://eight2late.wordpress.com/2009/07/01/cox%E2%80%99s-risk-matrix-
5
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

BN205 RISK MANAGEMENT
theorem-and-its-implications-for-project-risk-management/
x
6
theorem-and-its-implications-for-project-risk-management/
x
6
1 out of 7
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
© 2024 | Zucol Services PVT LTD | All rights reserved.





