Managerial Decision Making
VerifiedAdded on 2023/04/21
|15
|3525
|198
AI Summary
This assignment discusses the problems faced by organizations in their operational level, specifically focusing on cyber security threats. It provides solutions to combat these threats and protect data.
Contribute Materials
Your contribution can guide someone’s learning journey. Share your
documents today.

Running head: MANAGERIAL DECISION MAKING
MANAGERIAL DECISION MAKING
Name of Student
Name of University
Author’s Note
MANAGERIAL DECISION MAKING
Name of Student
Name of University
Author’s Note
Secure Best Marks with AI Grader
Need help grading? Try our AI Grader for instant feedback on your assignments.

1MANAGERIAL DECISION MAKING
Executive summary
Organization faces various problems in numerous fields especially in their operational level. The
problems that are faced by the organizations in their operation level include managing overheads,
monitoring performances of employees, listening to the feedbacks received from employees as
well as customers and many more. For combating the sophisticated cyber attacks that had taken
place in Yahoo and meet their needs, they would need a multilayered approach to the prevention
of threat. The solution would help in detecting as well as preventing the vulnerabilities and
advanced threats with the help of various mechanisms.
Executive summary
Organization faces various problems in numerous fields especially in their operational level. The
problems that are faced by the organizations in their operation level include managing overheads,
monitoring performances of employees, listening to the feedbacks received from employees as
well as customers and many more. For combating the sophisticated cyber attacks that had taken
place in Yahoo and meet their needs, they would need a multilayered approach to the prevention
of threat. The solution would help in detecting as well as preventing the vulnerabilities and
advanced threats with the help of various mechanisms.

2MANAGERIAL DECISION MAKING
Table of Contents
Introduction..........................................................................................................................3
Discussion............................................................................................................................3
Problem background........................................................................................................3
Problem definition...........................................................................................................4
Solution generation..........................................................................................................5
Solution evaluation..........................................................................................................6
Implementation and action plan.......................................................................................7
Conclusion...........................................................................................................................8
References............................................................................................................................9
Table of Contents
Introduction..........................................................................................................................3
Discussion............................................................................................................................3
Problem background........................................................................................................3
Problem definition...........................................................................................................4
Solution generation..........................................................................................................5
Solution evaluation..........................................................................................................6
Implementation and action plan.......................................................................................7
Conclusion...........................................................................................................................8
References............................................................................................................................9

3MANAGERIAL DECISION MAKING
Introduction
Every organization faces numerous problems in various fields especially in their
operational level. The problems that are faced by the organizations in their operation level
include managing overheads, monitoring performances of employees, listening to the feedbacks
received from employees as well as customers, responding to the competition going on in the
market, compliance and regulation, uncertainty of various activities, cyber risks faced by the
organization, finding out the appropriate group of staffs, retaining customers, cash flow and
many more.
This assignment discusses regarding a particular risk faced by the operational team of the
organizations, the attack chosen for this assignment includes cyber risks faced by the
organization. Rather than just an IT issue, cyber security has been increasingly a major risk for
most of the businesses (Bazerman & Moore, 2013). In case an organization’s cyber security is
not well managed, businesses expose themselves to a great extent and the number of threats also
increase which might result in hacks, data theft and many other attacks.
Discussion
Problem background
Cyber security threat is one of the major threats faced by the organizations nowadays.
Organizations might face numerous ways of cyber security threats. Data breaches might prove to
be very dangerous for any organization (Wood, Cogin & Beckmann, 2009). Cyber security
breach might be caused by various ways; these include hacking or computer intrusion, insider
threat, data that is on the move, theft caused physically, errors caused by employees through
negligence, data lost or improper disposal of data, internet exposure, accidental web and
unauthorized access. These ways of data breaches can cause by several sources, they might be
external or internal sources. A specific organization that has been chosen for this assignment is
Yahoo (Butler, O'Broin & Lee, 2016). Yahoo had faced a serious cyber security threat in the year
of 2013-2014. This threat had affected accounts of around 3 billion users.
Introduction
Every organization faces numerous problems in various fields especially in their
operational level. The problems that are faced by the organizations in their operation level
include managing overheads, monitoring performances of employees, listening to the feedbacks
received from employees as well as customers, responding to the competition going on in the
market, compliance and regulation, uncertainty of various activities, cyber risks faced by the
organization, finding out the appropriate group of staffs, retaining customers, cash flow and
many more.
This assignment discusses regarding a particular risk faced by the operational team of the
organizations, the attack chosen for this assignment includes cyber risks faced by the
organization. Rather than just an IT issue, cyber security has been increasingly a major risk for
most of the businesses (Bazerman & Moore, 2013). In case an organization’s cyber security is
not well managed, businesses expose themselves to a great extent and the number of threats also
increase which might result in hacks, data theft and many other attacks.
Discussion
Problem background
Cyber security threat is one of the major threats faced by the organizations nowadays.
Organizations might face numerous ways of cyber security threats. Data breaches might prove to
be very dangerous for any organization (Wood, Cogin & Beckmann, 2009). Cyber security
breach might be caused by various ways; these include hacking or computer intrusion, insider
threat, data that is on the move, theft caused physically, errors caused by employees through
negligence, data lost or improper disposal of data, internet exposure, accidental web and
unauthorized access. These ways of data breaches can cause by several sources, they might be
external or internal sources. A specific organization that has been chosen for this assignment is
Yahoo (Butler, O'Broin & Lee, 2016). Yahoo had faced a serious cyber security threat in the year
of 2013-2014. This threat had affected accounts of around 3 billion users.
Secure Best Marks with AI Grader
Need help grading? Try our AI Grader for instant feedback on your assignments.

4MANAGERIAL DECISION MAKING
In the month of September, the most dominant giant of internet during its negotiations on
selling to Verizon announced that it had faced one of the biggest data breach in the entire history.
This attack was likely done by a specific state sponsor actor in the year of 2014. The attack had
resulted in compromising a huge number of real names, dates of birth, phone numbers and email
addresses of around 500 million users (Klein, 2016). The company had a vast majority of various
passwords that had been involved were hashed by the usage of robust bcrypt algorithm.
Few months later, in the month of December, the company had buried the previous
record with the disclosure of the fact that a breach that took place in 2013 by some other group
of cyber hackers had stolen data from accounts of around 1 billion users (Wolf, Weißenberger &
Claus Wehner, 2015). Along with the compromise of email addresses, passwords, dates of birth
and names which were not properly secured, the security questions as well as answers had also
been compromised. In the month of October, yahoo had revised that around 3 billion user
accounts were compromised.
The breach had knocked an estimate of $ 350 million of sale price of Yahoo. Verizon had
eventually paid around $4.48 billion for the business of Yahoo. The agreement had called for
two organizations for sharing their legal liabilities and regulatory from the breach that had taken
place (Abatecola, Caputo & Cristofaro, 2018). The sale had not included a specific reported
investment in the Group of Alibaba which had revenue of $41.3 billion as well as a particular
ownership interest in the organization venue of $41.3 billion as well as a particular ownership
interest in the organization of Yahoo of revenue $9.3 billion.
Problem definition
Yahoo had claimed that minimum of 500 million accounts of users had been hacked by
the data breach caused. According to a specific report created by Infoarmor Yahoo had
compromised in the year of 2014 by a specific group of black hats who were very professional in
their activities. These professionals were hired in order to compromise the database of customers
from a huge variety of various organizations (Hoefer & Green, 2016). Some of the targets were
linked with the large scale of data breaches of the networks of social media as well as online
services like MySpace, LinkedIn and Tumbler. Some more well known organizations were also
impacted by the activities of this specific group. In this case the data that had been stolen from
In the month of September, the most dominant giant of internet during its negotiations on
selling to Verizon announced that it had faced one of the biggest data breach in the entire history.
This attack was likely done by a specific state sponsor actor in the year of 2014. The attack had
resulted in compromising a huge number of real names, dates of birth, phone numbers and email
addresses of around 500 million users (Klein, 2016). The company had a vast majority of various
passwords that had been involved were hashed by the usage of robust bcrypt algorithm.
Few months later, in the month of December, the company had buried the previous
record with the disclosure of the fact that a breach that took place in 2013 by some other group
of cyber hackers had stolen data from accounts of around 1 billion users (Wolf, Weißenberger &
Claus Wehner, 2015). Along with the compromise of email addresses, passwords, dates of birth
and names which were not properly secured, the security questions as well as answers had also
been compromised. In the month of October, yahoo had revised that around 3 billion user
accounts were compromised.
The breach had knocked an estimate of $ 350 million of sale price of Yahoo. Verizon had
eventually paid around $4.48 billion for the business of Yahoo. The agreement had called for
two organizations for sharing their legal liabilities and regulatory from the breach that had taken
place (Abatecola, Caputo & Cristofaro, 2018). The sale had not included a specific reported
investment in the Group of Alibaba which had revenue of $41.3 billion as well as a particular
ownership interest in the organization venue of $41.3 billion as well as a particular ownership
interest in the organization of Yahoo of revenue $9.3 billion.
Problem definition
Yahoo had claimed that minimum of 500 million accounts of users had been hacked by
the data breach caused. According to a specific report created by Infoarmor Yahoo had
compromised in the year of 2014 by a specific group of black hats who were very professional in
their activities. These professionals were hired in order to compromise the database of customers
from a huge variety of various organizations (Hoefer & Green, 2016). Some of the targets were
linked with the large scale of data breaches of the networks of social media as well as online
services like MySpace, LinkedIn and Tumbler. Some more well known organizations were also
impacted by the activities of this specific group. In this case the data that had been stolen from

5MANAGERIAL DECISION MAKING
them was not at validation or sale in the underground. On the 15th of March in the year 2017, U.S
Justice Department had unsealed the indictments against the men who were blamed of the crime
of hacking into the account of around half billion users (Jarmolowicz, Reed & DiGennaro,
2016). Among the accused, two of them worked for a specific unit of Russian Federal Security
Service which serves as the point of FBI in Moscow on the cases of cyber crime.
In case of the data breach that had occurred in 2014, some of the experts in the field of
security had noted that most of the passwords of Yahoo used the algorithm of bcrypt hashing.
This algorithm is considered as very difficult to track. Rest of them used the algorithm of MD5
that can be broken very quickly (Hasan, Noor & Malik, 2018). This data especially the security
questions as well as answers might help hackers get access to the other online accounts owned by
the victims. This means that the hackers got access of not only the email accounts of the victims
but also the person al social media accounts owned by them.
Solution generation
In order to combat the sophisticated cyber attacks that had taken place in Yahoo and meet
their needs, they would need a multilayered approach to the prevention of threat. The solution
would help in detecting as well as preventing the vulnerabilities and advanced threats with the
help of various mechanisms (Huang & Tsai, 2015). Various ways by which Yahoo can prevent
the cyber security hacks and protect their data are as follows
Firewall: next generation firewall should be implemented, it would provide a
high quality of performance, complete visibility and an approach of multilayered
security, these are provided across the entire organization (Koch, D'mello &
Sackett, 2015). The next generation firewall implemented in Yahoo would help it
to adapt as various new threats come up, it then extends its protecting power in
order to prevent a single point introducing the vulnerability in the specific
network.
IPS: next generation Intrusion prevention system (NGIPS) can also be
implemented which would help the organization to detect as well as stop various
unknown threats that have high chances to pose significant risks to the network of
the organization. It would enable the clients to move deep inside in the form of a
them was not at validation or sale in the underground. On the 15th of March in the year 2017, U.S
Justice Department had unsealed the indictments against the men who were blamed of the crime
of hacking into the account of around half billion users (Jarmolowicz, Reed & DiGennaro,
2016). Among the accused, two of them worked for a specific unit of Russian Federal Security
Service which serves as the point of FBI in Moscow on the cases of cyber crime.
In case of the data breach that had occurred in 2014, some of the experts in the field of
security had noted that most of the passwords of Yahoo used the algorithm of bcrypt hashing.
This algorithm is considered as very difficult to track. Rest of them used the algorithm of MD5
that can be broken very quickly (Hasan, Noor & Malik, 2018). This data especially the security
questions as well as answers might help hackers get access to the other online accounts owned by
the victims. This means that the hackers got access of not only the email accounts of the victims
but also the person al social media accounts owned by them.
Solution generation
In order to combat the sophisticated cyber attacks that had taken place in Yahoo and meet
their needs, they would need a multilayered approach to the prevention of threat. The solution
would help in detecting as well as preventing the vulnerabilities and advanced threats with the
help of various mechanisms (Huang & Tsai, 2015). Various ways by which Yahoo can prevent
the cyber security hacks and protect their data are as follows
Firewall: next generation firewall should be implemented, it would provide a
high quality of performance, complete visibility and an approach of multilayered
security, these are provided across the entire organization (Koch, D'mello &
Sackett, 2015). The next generation firewall implemented in Yahoo would help it
to adapt as various new threats come up, it then extends its protecting power in
order to prevent a single point introducing the vulnerability in the specific
network.
IPS: next generation Intrusion prevention system (NGIPS) can also be
implemented which would help the organization to detect as well as stop various
unknown threats that have high chances to pose significant risks to the network of
the organization. It would enable the clients to move deep inside in the form of a

6MANAGERIAL DECISION MAKING
different layer for preventing various threats across the entire lifecycle of attack
through the capabilities of remediation. IPS solution would help Yahoo to
understand what is actually going on in their organizational environment as well
as respond to various incidents very effectively and quickly.
Secure Remote Access (VPN): various innovation solutions would allow the
organization to access the resources of organizations by using the Secure Remote
Access (VPN) solution. It ensures in protecting the sensitive data when it is
accessed from the devices outside the network of the organization (Hickson,
Butler & Wilson, 2017). With the help of this, clients would be able to customize
solution in order to help in meeting the needs of the organizational environment,
this helps in benefitting from various features offered by the planned solution.
Network Access Control (NAC): various ways of Network Access Control would
help the clients to authenticate devices and users in a specific network; it also
helps in restricting the availability of resources of that particular network to
various endpoint devices which would comply with the help of a security policy.
Solution evaluation
Solution evaluation can be carried out with the help of SWOT analysis. SWOT analysis
acts as an evaluation tool for the security solutions provided above. SWOT analysis is usually
designed as a specific strategic planning for providing information to match the resources as well
as competencies to the environment where it runs. This analysis is highly adaptive to selection
and evaluation of various other alternatives like strategic technology investment (Faisal, Khan &
Al-Aboud, 2017). SWOT analysis considers various strengths, weaknesses, opportunities and
threats within various options. This involved the identification of external as well as internal
factors which are favourable as well as unfavorable for achieving the project’s objectives.
Strengths: the strength of the planned solution can be considered as its
capabilities which increase their ability to exceed or even to meet their objectives
of acquisition (Mitchell, Weaver & Agle, 2016). Some examples would be
innovative technology and opportunities provided by the planned solution.
Weaknesses: in various cases, weaknesses might be a different side of the
strength. Weakness can be described as a certain attribute which might prevent
different layer for preventing various threats across the entire lifecycle of attack
through the capabilities of remediation. IPS solution would help Yahoo to
understand what is actually going on in their organizational environment as well
as respond to various incidents very effectively and quickly.
Secure Remote Access (VPN): various innovation solutions would allow the
organization to access the resources of organizations by using the Secure Remote
Access (VPN) solution. It ensures in protecting the sensitive data when it is
accessed from the devices outside the network of the organization (Hickson,
Butler & Wilson, 2017). With the help of this, clients would be able to customize
solution in order to help in meeting the needs of the organizational environment,
this helps in benefitting from various features offered by the planned solution.
Network Access Control (NAC): various ways of Network Access Control would
help the clients to authenticate devices and users in a specific network; it also
helps in restricting the availability of resources of that particular network to
various endpoint devices which would comply with the help of a security policy.
Solution evaluation
Solution evaluation can be carried out with the help of SWOT analysis. SWOT analysis
acts as an evaluation tool for the security solutions provided above. SWOT analysis is usually
designed as a specific strategic planning for providing information to match the resources as well
as competencies to the environment where it runs. This analysis is highly adaptive to selection
and evaluation of various other alternatives like strategic technology investment (Faisal, Khan &
Al-Aboud, 2017). SWOT analysis considers various strengths, weaknesses, opportunities and
threats within various options. This involved the identification of external as well as internal
factors which are favourable as well as unfavorable for achieving the project’s objectives.
Strengths: the strength of the planned solution can be considered as its
capabilities which increase their ability to exceed or even to meet their objectives
of acquisition (Mitchell, Weaver & Agle, 2016). Some examples would be
innovative technology and opportunities provided by the planned solution.
Weaknesses: in various cases, weaknesses might be a different side of the
strength. Weakness can be described as a certain attribute which might prevent
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

7MANAGERIAL DECISION MAKING
the acquisition’s achievement (Jiang, Ananthram & Li, 2018). Some examples
include unproven technology or a certain limited proven history and start up with
the limited financial history.
Opportunities: a certain factor that is external in nature and is able to increase or
optimize the acquisition’s value, some examples of opportunities include single
and secure the mechanism of authentication in all the platforms as well as devices
and usage of two-step authentication for preventing various security breaches.
Threats: a specific external factor which can decrease their value or decreasing
their chance of fulfilling the objectives of acquisition. Some examples of this are
meeting the requirements of compliance and untested technology.
Implementation and action plan
Implementation of the decided solution and its action plan can be divided into various
parts. In case these parts are solely followed, the organization would be able to overcome the
issues created by the hackers by stealing the data of a huge number of users. The steps are as
follows
Starting with a master plan: it is completely baseless if an organization spends
around $10,000 for protecting an asset worth of $10. Almost every security
remediation plan needs the knowledge of the importance of an asset to the
organization, this should be realized before money and time is spent in the asset
for securing it from attacks (Casali & Day, 2015). Risks must be management
intelligently, instead of reactions similar to knee-jerks to the various multitudes of
threats. Priorities must be set accordingly in order to understand which the most
important asset for the organizations is. If the asset which is not worth much is
hacked, it would not be intelligent to spend a lot of money and time in securing it
or retain it, hence a good master plan should be planned where it would be
decided whether or not to secure and retain the data.
Managing access: as far as the security technology has been advanced, passwords
can be the weakest link in the chain of security. Passwords can be considered as
the easiest way in which hackers would be able to access the data of an
organization. According to this, Yahoo must control access to its data. It should
the acquisition’s achievement (Jiang, Ananthram & Li, 2018). Some examples
include unproven technology or a certain limited proven history and start up with
the limited financial history.
Opportunities: a certain factor that is external in nature and is able to increase or
optimize the acquisition’s value, some examples of opportunities include single
and secure the mechanism of authentication in all the platforms as well as devices
and usage of two-step authentication for preventing various security breaches.
Threats: a specific external factor which can decrease their value or decreasing
their chance of fulfilling the objectives of acquisition. Some examples of this are
meeting the requirements of compliance and untested technology.
Implementation and action plan
Implementation of the decided solution and its action plan can be divided into various
parts. In case these parts are solely followed, the organization would be able to overcome the
issues created by the hackers by stealing the data of a huge number of users. The steps are as
follows
Starting with a master plan: it is completely baseless if an organization spends
around $10,000 for protecting an asset worth of $10. Almost every security
remediation plan needs the knowledge of the importance of an asset to the
organization, this should be realized before money and time is spent in the asset
for securing it from attacks (Casali & Day, 2015). Risks must be management
intelligently, instead of reactions similar to knee-jerks to the various multitudes of
threats. Priorities must be set accordingly in order to understand which the most
important asset for the organizations is. If the asset which is not worth much is
hacked, it would not be intelligent to spend a lot of money and time in securing it
or retain it, hence a good master plan should be planned where it would be
decided whether or not to secure and retain the data.
Managing access: as far as the security technology has been advanced, passwords
can be the weakest link in the chain of security. Passwords can be considered as
the easiest way in which hackers would be able to access the data of an
organization. According to this, Yahoo must control access to its data. It should

8MANAGERIAL DECISION MAKING
hence be decided by Yahoo regarding the visitors that can access the data of the
organization (Klein, 2016). The organization can set certain criteria for setting the
passwords of the users, these criteria should be set in such a way that they are
very tough to crack. Users must not be allowed to put easy passwords like date of
birth, name and data that are easy to guess.
Conclusion
From the above assignment, it can be concluded that the cyber security hack that took
place in Yahoo are presently one of the most dangerous and biggest hacks when the number of
users affected is considered. The hack represented that various parties like state sponsored
hackers might target a single business and most of them succeeded because the organizations did
not prepare well for the attack or they did not have sufficient measures to prevent the attacks
performed by cyber criminals. the response of these attacks are varying to a great extent along
with privacy and various financial organizations come up with different ways through which
they can force the companies to protect their information in a proper way. This would help them
to protect themselves against the data breaches as vast as this. This assignment discusses
regarding the problems faced by Yahoo during the cyber security hack faced by the company. It
also provides various solutions that could be applied in order to avoid the hacks.
hence be decided by Yahoo regarding the visitors that can access the data of the
organization (Klein, 2016). The organization can set certain criteria for setting the
passwords of the users, these criteria should be set in such a way that they are
very tough to crack. Users must not be allowed to put easy passwords like date of
birth, name and data that are easy to guess.
Conclusion
From the above assignment, it can be concluded that the cyber security hack that took
place in Yahoo are presently one of the most dangerous and biggest hacks when the number of
users affected is considered. The hack represented that various parties like state sponsored
hackers might target a single business and most of them succeeded because the organizations did
not prepare well for the attack or they did not have sufficient measures to prevent the attacks
performed by cyber criminals. the response of these attacks are varying to a great extent along
with privacy and various financial organizations come up with different ways through which
they can force the companies to protect their information in a proper way. This would help them
to protect themselves against the data breaches as vast as this. This assignment discusses
regarding the problems faced by Yahoo during the cyber security hack faced by the company. It
also provides various solutions that could be applied in order to avoid the hacks.

9MANAGERIAL DECISION MAKING
Appendices
Appendices
Secure Best Marks with AI Grader
Need help grading? Try our AI Grader for instant feedback on your assignments.
10MANAGERIAL DECISION MAKING
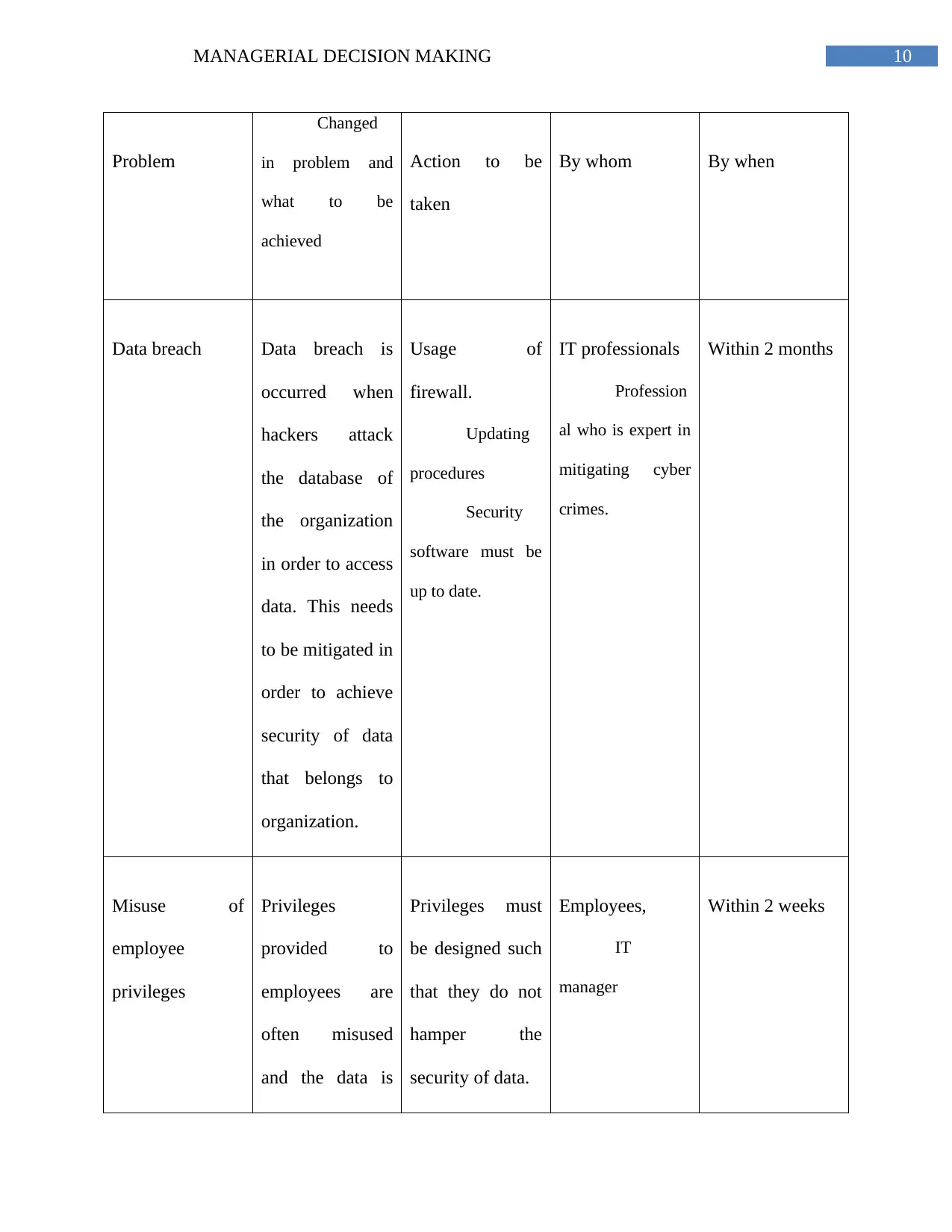
Problem
Changed
in problem and
what to be
achieved
Action to be
taken
By whom By when
Data breach Data breach is
occurred when
hackers attack
the database of
the organization
in order to access
data. This needs
to be mitigated in
order to achieve
security of data
that belongs to
organization.
Usage of
firewall.
Updating
procedures
Security
software must be
up to date.
IT professionals
Profession
al who is expert in
mitigating cyber
crimes.
Within 2 months
Misuse of
employee
privileges
Privileges
provided to
employees are
often misused
and the data is
Privileges must
be designed such
that they do not
hamper the
security of data.
Employees,
IT
manager
Within 2 weeks
Problem
Changed
in problem and
what to be
achieved
Action to be
taken
By whom By when
Data breach Data breach is
occurred when
hackers attack
the database of
the organization
in order to access
data. This needs
to be mitigated in
order to achieve
security of data
that belongs to
organization.
Usage of
firewall.
Updating
procedures
Security
software must be
up to date.
IT professionals
Profession
al who is expert in
mitigating cyber
crimes.
Within 2 months
Misuse of
employee
privileges
Privileges
provided to
employees are
often misused
and the data is
Privileges must
be designed such
that they do not
hamper the
security of data.
Employees,
IT
manager
Within 2 weeks
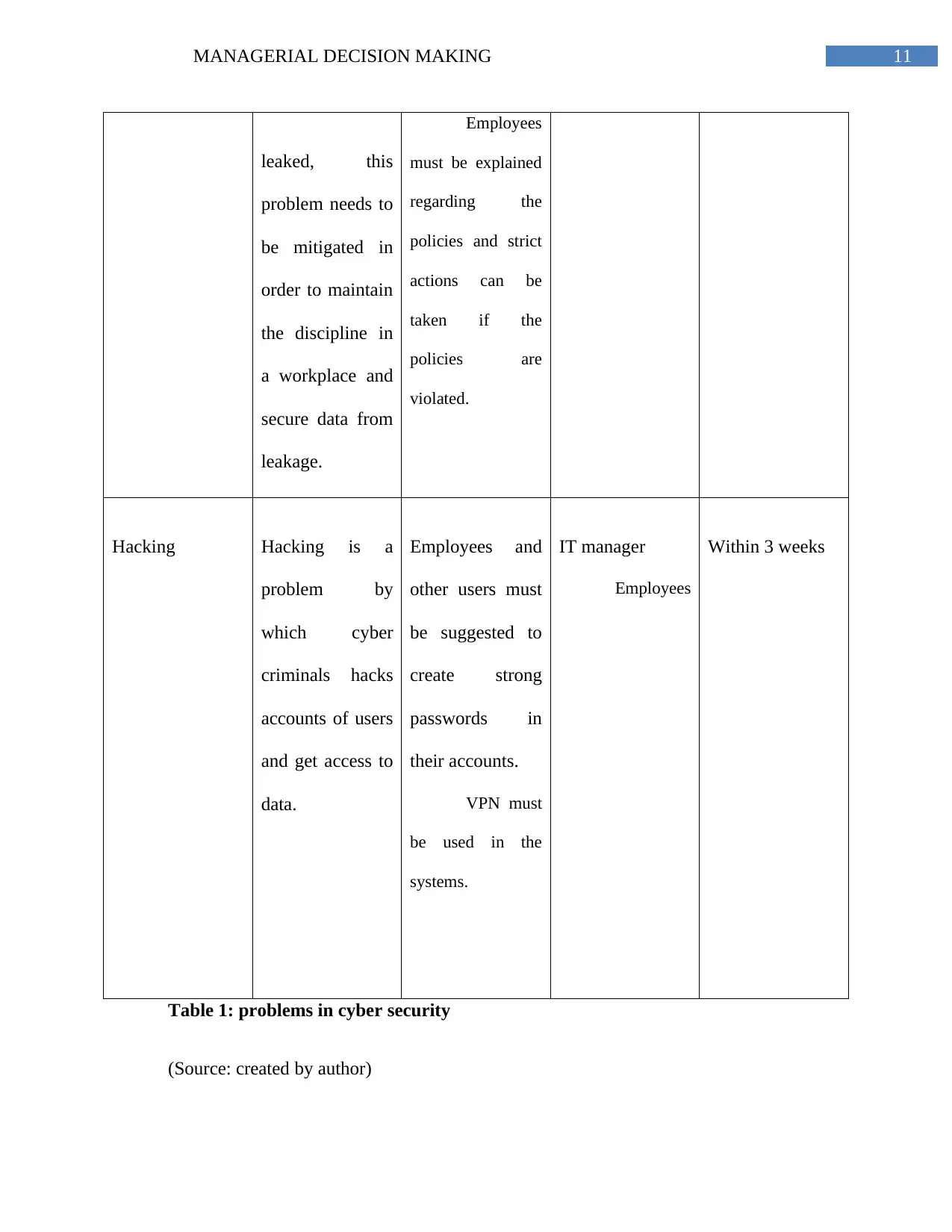
11MANAGERIAL DECISION MAKING
leaked, this
problem needs to
be mitigated in
order to maintain
the discipline in
a workplace and
secure data from
leakage.
Employees
must be explained
regarding the
policies and strict
actions can be
taken if the
policies are
violated.
Hacking Hacking is a
problem by
which cyber
criminals hacks
accounts of users
and get access to
data.
Employees and
other users must
be suggested to
create strong
passwords in
their accounts.
VPN must
be used in the
systems.
IT manager
Employees
Within 3 weeks
Table 1: problems in cyber security
(Source: created by author)
leaked, this
problem needs to
be mitigated in
order to maintain
the discipline in
a workplace and
secure data from
leakage.
Employees
must be explained
regarding the
policies and strict
actions can be
taken if the
policies are
violated.
Hacking Hacking is a
problem by
which cyber
criminals hacks
accounts of users
and get access to
data.
Employees and
other users must
be suggested to
create strong
passwords in
their accounts.
VPN must
be used in the
systems.
IT manager
Employees
Within 3 weeks
Table 1: problems in cyber security
(Source: created by author)
12MANAGERIAL DECISION MAKING
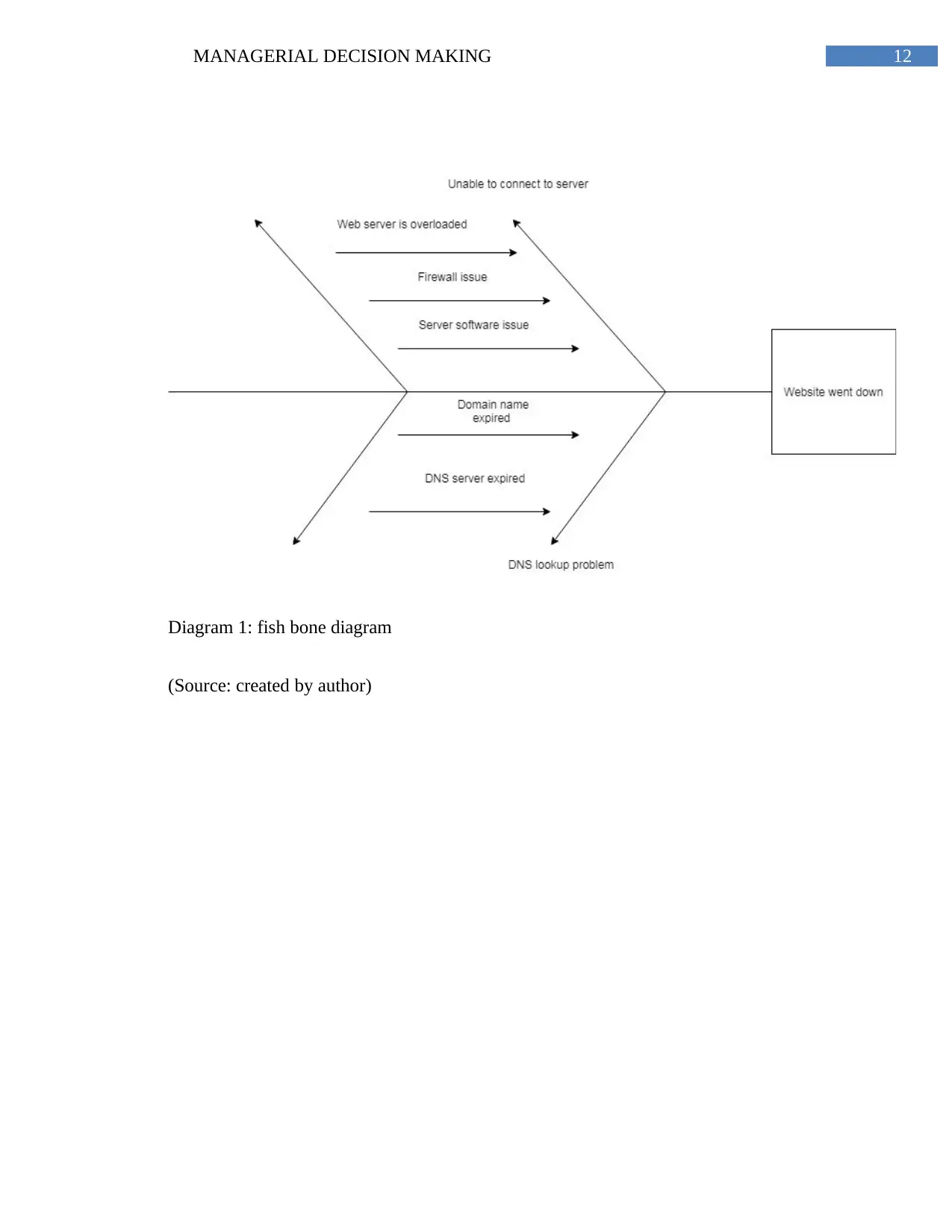
Diagram 1: fish bone diagram
(Source: created by author)
Diagram 1: fish bone diagram
(Source: created by author)
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

13MANAGERIAL DECISION MAKING
References
Abatecola, G., Caputo, A., & Cristofaro, M. (2018). Reviewing cognitive distortions in
managerial decision making: Toward an integrative co-evolutionary framework. Journal
of Management Development, 37(5), 409-424.
Bazerman, M. H. & Moore, D. A. (2013). Judgment in Managerial Decision Making (8th ed).
Hoboken, NJ: John Wiley & Sons.
Butler, M. J., O'Broin, H. L., Lee, N., & Senior, C. (2016). How organizational cognitive
neuroscience can deepen understanding of managerial decision‐making: A review of the
recent literature and future directions. International Journal of Management
Reviews, 18(4), 542-559.
Casali, G. L., & Day, G. E. (2015). A taxonomic approach to understanding managerial ethical
decision-making approaches of clinically and non-clinically trained healthcare managers
in Australia. Asia Pacific Journal of Health Management, 10(3), SI8.
Faisal, S. M., Khan, A. K., & Al-Aboud, O. A. (2017). Study of Managerial Decision Making
Linked to Operating and Financial Leverage. Accounting and Finance Research, 7(1),
139.
Hasan, N. N. B. A., Noor, K. B. M., Malik, A. A., & Ghani, Z. A. (2018). The proposed model
of the integration of the principle of maqasid al-shariah in managerial decision making
process in shariah-compliant securities. Journal of Islamic, 3(11), 36-50.
Hickson, D. J., Butler, R. J., & Wilson, D. C. (Eds.). (2017). Revival: The Bradford Studies of
Strategic Decision Making (2001). Routledge.
Hoefer, R. L., & Green Jr, S. E. (2016). A rhetorical model of institutional decision making: The
role of rhetoric in the formation and change of legitimacy judgments. Academy of
Management Review, 41(1), 130-150.
Huang, C. L., & Tsai, J. L. (2015). Managerial Morality and Philanthropic Decision-Making: A
Test of an Agency Model. Journal of business ethics, 132(4), 795-811.
References
Abatecola, G., Caputo, A., & Cristofaro, M. (2018). Reviewing cognitive distortions in
managerial decision making: Toward an integrative co-evolutionary framework. Journal
of Management Development, 37(5), 409-424.
Bazerman, M. H. & Moore, D. A. (2013). Judgment in Managerial Decision Making (8th ed).
Hoboken, NJ: John Wiley & Sons.
Butler, M. J., O'Broin, H. L., Lee, N., & Senior, C. (2016). How organizational cognitive
neuroscience can deepen understanding of managerial decision‐making: A review of the
recent literature and future directions. International Journal of Management
Reviews, 18(4), 542-559.
Casali, G. L., & Day, G. E. (2015). A taxonomic approach to understanding managerial ethical
decision-making approaches of clinically and non-clinically trained healthcare managers
in Australia. Asia Pacific Journal of Health Management, 10(3), SI8.
Faisal, S. M., Khan, A. K., & Al-Aboud, O. A. (2017). Study of Managerial Decision Making
Linked to Operating and Financial Leverage. Accounting and Finance Research, 7(1),
139.
Hasan, N. N. B. A., Noor, K. B. M., Malik, A. A., & Ghani, Z. A. (2018). The proposed model
of the integration of the principle of maqasid al-shariah in managerial decision making
process in shariah-compliant securities. Journal of Islamic, 3(11), 36-50.
Hickson, D. J., Butler, R. J., & Wilson, D. C. (Eds.). (2017). Revival: The Bradford Studies of
Strategic Decision Making (2001). Routledge.
Hoefer, R. L., & Green Jr, S. E. (2016). A rhetorical model of institutional decision making: The
role of rhetoric in the formation and change of legitimacy judgments. Academy of
Management Review, 41(1), 130-150.
Huang, C. L., & Tsai, J. L. (2015). Managerial Morality and Philanthropic Decision-Making: A
Test of an Agency Model. Journal of business ethics, 132(4), 795-811.

14MANAGERIAL DECISION MAKING
Jarmolowicz, D. P., Reed, D. D., DiGennaro Reed, F. D., & Bickel, W. K. (2016). The
behavioral and neuroeconomics of reinforcer pathologies: Implications for managerial
and health decision making. Managerial and Decision Economics, 37(4-5), 274-293.
Jiang, F., Ananthram, S., & Li, J. (2018). Global Mindset and Entry Mode Decisions:
Moderating Roles of Managers’ Decision-Making Style and Managerial
Experience. Management International Review, 58(3), 413-447.
Klein, B. D. (2016). Developing an Applied, Integrated MBA Managerial Decision Making
Course. Journal of the Midwest Association for Information Systems| Vol, 2016(2), 61.
Koch, A. J., D'mello, S. D., & Sackett, P. R. (2015). A meta-analysis of gender stereotypes and
bias in experimental simulations of employment decision making. Journal of Applied
Psychology, 100(1), 128.
Mitchell, R. K., Weaver, G. R., Agle, B. R., Bailey, A. D., & Carlson, J. (2016). Stakeholder
agency and social welfare: Pluralism and decision making in the multi-objective
corporation. Academy of Management Review, 41(2), 252-275.
Wolf, S., Weißenberger, B. E., Claus Wehner, M., & Kabst, R. (2015). Controllers as business
partners in managerial decision-making: Attitude, subjective norm, and internal
improvements. Journal of Accounting & Organizational Change, 11(1), 24-46.
Wood, R., Cogin, J. & Beckmann, J. (2009). Managerial Problem Solving: Frameworks, Tools,
Techniques. North Ryde: McGraw Hill, Australia.
Jarmolowicz, D. P., Reed, D. D., DiGennaro Reed, F. D., & Bickel, W. K. (2016). The
behavioral and neuroeconomics of reinforcer pathologies: Implications for managerial
and health decision making. Managerial and Decision Economics, 37(4-5), 274-293.
Jiang, F., Ananthram, S., & Li, J. (2018). Global Mindset and Entry Mode Decisions:
Moderating Roles of Managers’ Decision-Making Style and Managerial
Experience. Management International Review, 58(3), 413-447.
Klein, B. D. (2016). Developing an Applied, Integrated MBA Managerial Decision Making
Course. Journal of the Midwest Association for Information Systems| Vol, 2016(2), 61.
Koch, A. J., D'mello, S. D., & Sackett, P. R. (2015). A meta-analysis of gender stereotypes and
bias in experimental simulations of employment decision making. Journal of Applied
Psychology, 100(1), 128.
Mitchell, R. K., Weaver, G. R., Agle, B. R., Bailey, A. D., & Carlson, J. (2016). Stakeholder
agency and social welfare: Pluralism and decision making in the multi-objective
corporation. Academy of Management Review, 41(2), 252-275.
Wolf, S., Weißenberger, B. E., Claus Wehner, M., & Kabst, R. (2015). Controllers as business
partners in managerial decision-making: Attitude, subjective norm, and internal
improvements. Journal of Accounting & Organizational Change, 11(1), 24-46.
Wood, R., Cogin, J. & Beckmann, J. (2009). Managerial Problem Solving: Frameworks, Tools,
Techniques. North Ryde: McGraw Hill, Australia.
1 out of 15
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
© 2024 | Zucol Services PVT LTD | All rights reserved.





