Managing Services and Security: DNS, SSH, Web Server Configuration
VerifiedAdded on 2023/06/04
|19
|1665
|145
Practical Assignment
AI Summary
This assignment details the setup and configuration of two virtual machines using VMware Workstation Player. The first VM, running CentOS, is configured as a DNS and SSH server, utilizing BIND to manage the saffioti.org.au domain and implementing firewall rules for security. The second VM, based on Ubuntu, serves as a web server with LAMP installed, hosting a website and an FTP server. The assignment covers installing and configuring Apache, MySQL, and PHP, along with hardening the web server using IPTables to restrict access to essential services. It also addresses challenges encountered during firewall configuration, including troubleshooting and implementing specific rules for various protocols. Additionally, the assignment includes setting up a secondary DNS server, generating self-signed certificates for secure web services, and configuring FTP access for remote file transfer. The report also includes detailed steps, commands, and screenshots for each configuration step.

Managing Services and Security
Name
Institution
Name
Institution
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

Introduction
In this assignment, two virtual machine running Ubuntu and CentOS were installed and
configured on a VMware Workstation Player. The first machine was installed with a BIND,
to provide DNS & SSH services, while the second one was installed with a Web Server. The
name server on virtual machine 1 was configured to manage the domain saffioti.org.au. A
zone was also set up for the reverse zone and hardened by use of firewall rules, which
allowed access to the services. The virtual machine running Ubuntu OS was the web server,
where LAMP was installed. The Apache Web Server in the LAMP software was used to host
a website. Additionally, an FTP server was configured on the same virtual machine.
Part 1: Virtual Machine One – DNS & SSH Server
This virtual machine was installed with CentOs, and a BIND (DNS) installed and configured
on it. The name server was configured to manage the domain;
saffioti.org.au
Step 1: Install Bind
sudo yum install bind bind-utils
Step 2: Configure DNS
The namde.conf file was edited as shown below.
nano -w /etc/named.conf
In this assignment, two virtual machine running Ubuntu and CentOS were installed and
configured on a VMware Workstation Player. The first machine was installed with a BIND,
to provide DNS & SSH services, while the second one was installed with a Web Server. The
name server on virtual machine 1 was configured to manage the domain saffioti.org.au. A
zone was also set up for the reverse zone and hardened by use of firewall rules, which
allowed access to the services. The virtual machine running Ubuntu OS was the web server,
where LAMP was installed. The Apache Web Server in the LAMP software was used to host
a website. Additionally, an FTP server was configured on the same virtual machine.
Part 1: Virtual Machine One – DNS & SSH Server
This virtual machine was installed with CentOs, and a BIND (DNS) installed and configured
on it. The name server was configured to manage the domain;
saffioti.org.au
Step 1: Install Bind
sudo yum install bind bind-utils
Step 2: Configure DNS
The namde.conf file was edited as shown below.
nano -w /etc/named.conf
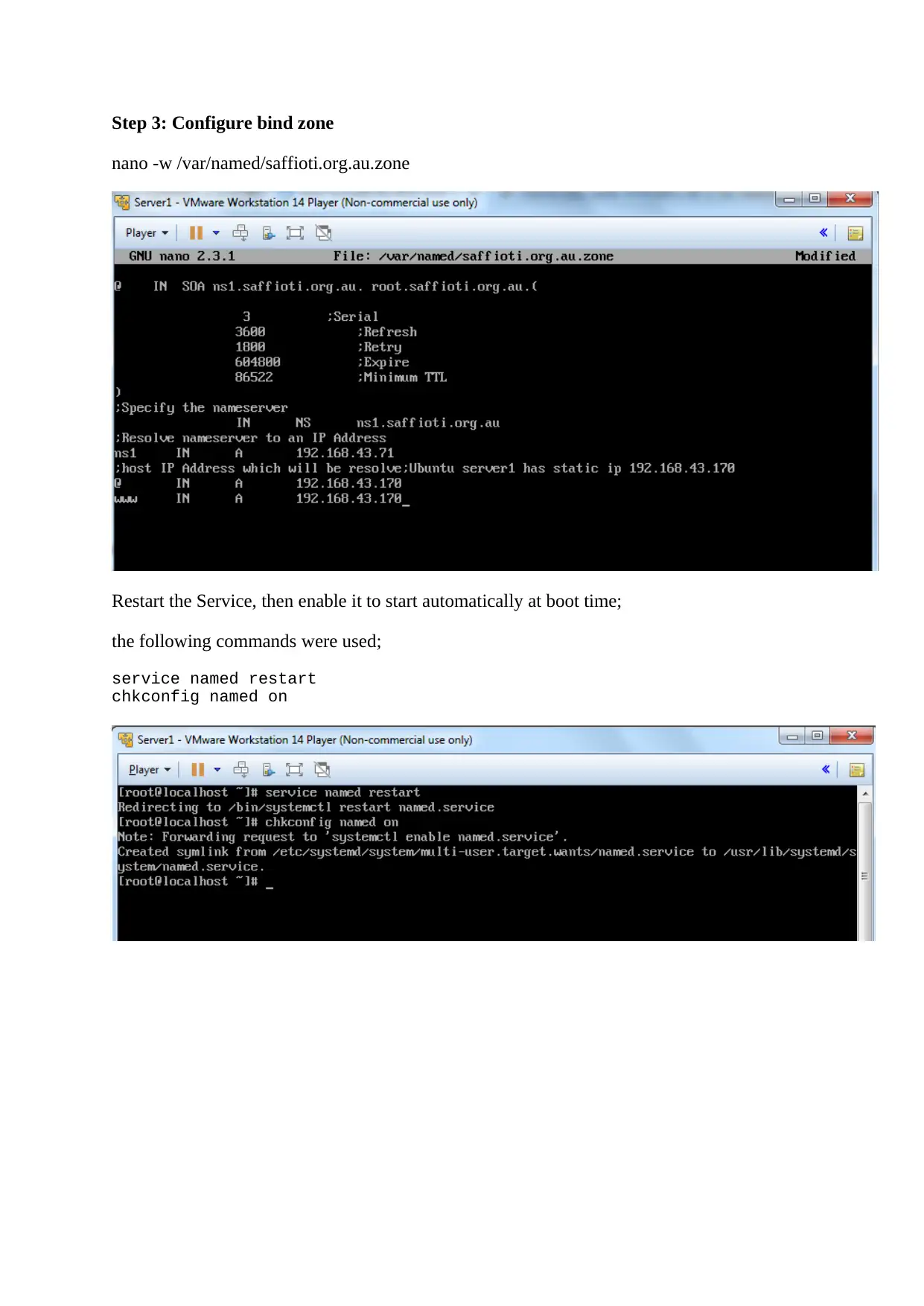
Step 3: Configure bind zone
nano -w /var/named/saffioti.org.au.zone
Restart the Service, then enable it to start automatically at boot time;
the following commands were used;
service named restart
chkconfig named on
nano -w /var/named/saffioti.org.au.zone
Restart the Service, then enable it to start automatically at boot time;
the following commands were used;
service named restart
chkconfig named on
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
Part 2: Virtual Machine Two: Server2
Ubuntu Operating system was installed on this virtual machine, and used as a web server. To
enable it server as a web server, LAMP was installed.
By definition LAMP is a stack of open source software tools, that are normally installed
together to facilitate hosting of dynamic websites and web applications. LAMP translates to
Linux, Apache, MySQL, PHP. The three software are installed on Linux along each other to
facilitate web hosting. In this exercise, the software were installed in a series of steps as
outlined below.
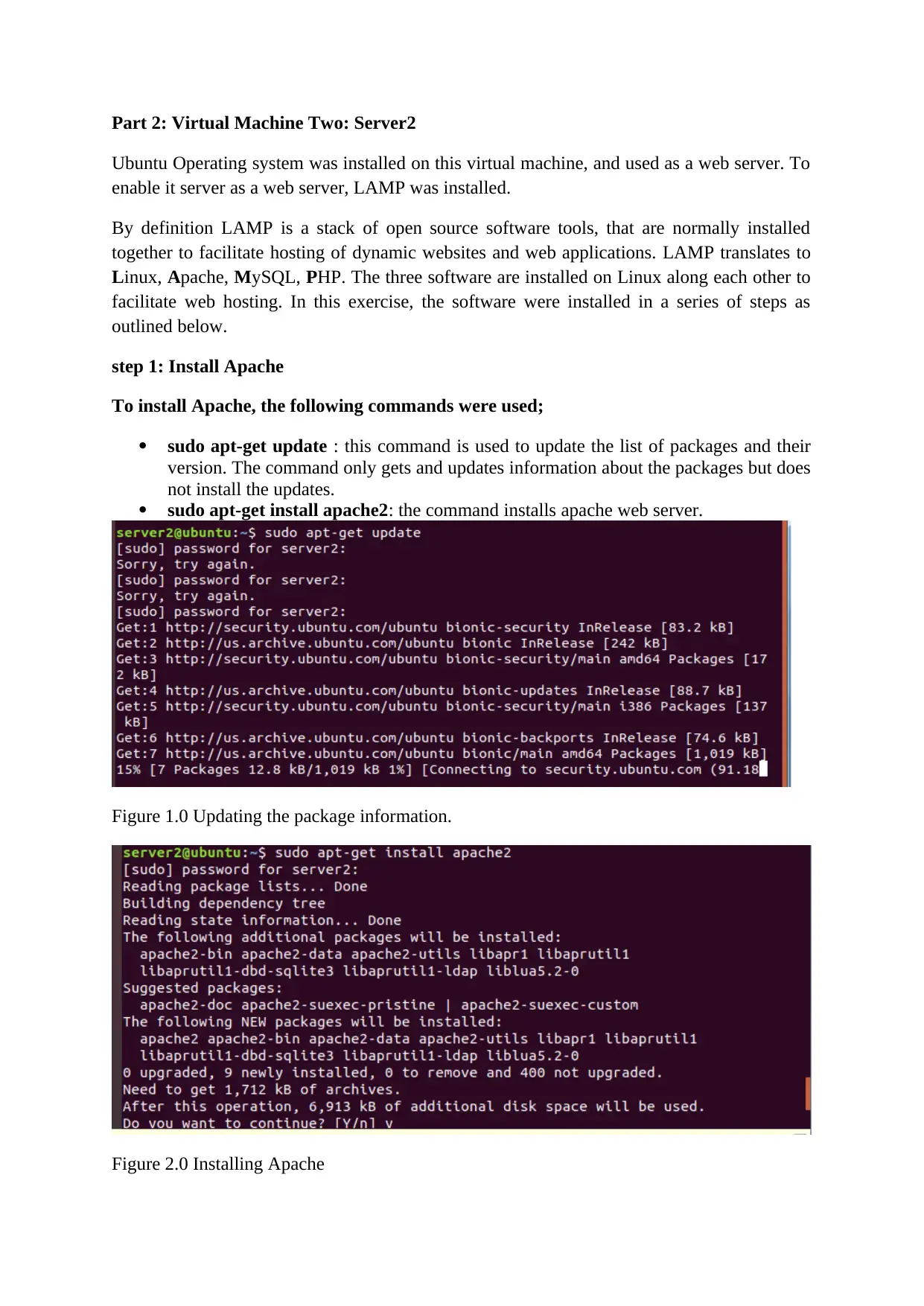
step 1: Install Apache
To install Apache, the following commands were used;
sudo apt-get update : this command is used to update the list of packages and their
version. The command only gets and updates information about the packages but does
not install the updates.
sudo apt-get install apache2: the command installs apache web server.
Figure 1.0 Updating the package information.
Figure 2.0 Installing Apache
Ubuntu Operating system was installed on this virtual machine, and used as a web server. To
enable it server as a web server, LAMP was installed.
By definition LAMP is a stack of open source software tools, that are normally installed
together to facilitate hosting of dynamic websites and web applications. LAMP translates to
Linux, Apache, MySQL, PHP. The three software are installed on Linux along each other to
facilitate web hosting. In this exercise, the software were installed in a series of steps as
outlined below.
step 1: Install Apache
To install Apache, the following commands were used;
sudo apt-get update : this command is used to update the list of packages and their
version. The command only gets and updates information about the packages but does
not install the updates.
sudo apt-get install apache2: the command installs apache web server.
Figure 1.0 Updating the package information.
Figure 2.0 Installing Apache
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
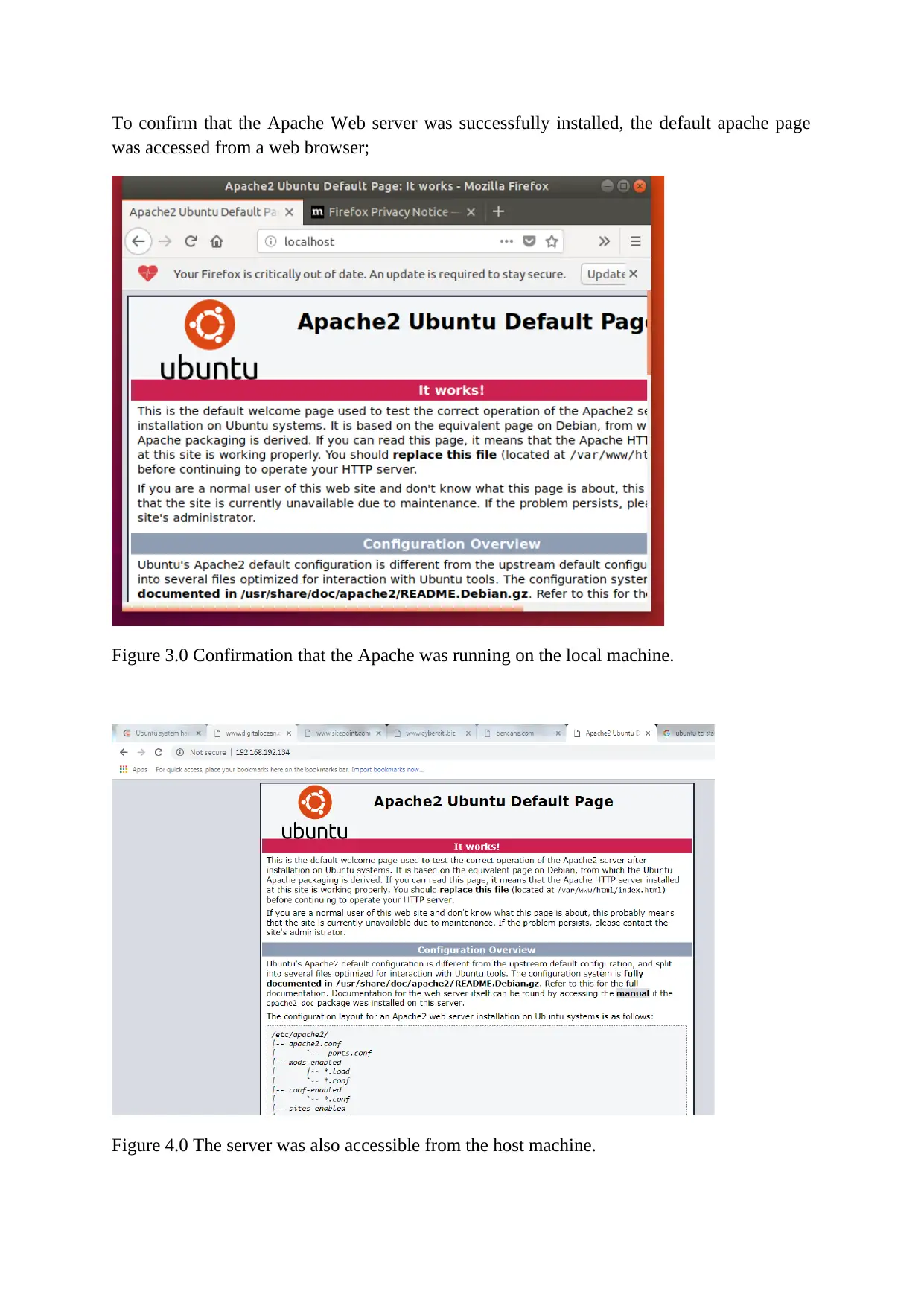
To confirm that the Apache Web server was successfully installed, the default apache page
was accessed from a web browser;
Figure 3.0 Confirmation that the Apache was running on the local machine.
Figure 4.0 The server was also accessible from the host machine.
was accessed from a web browser;
Figure 3.0 Confirmation that the Apache was running on the local machine.
Figure 4.0 The server was also accessible from the host machine.
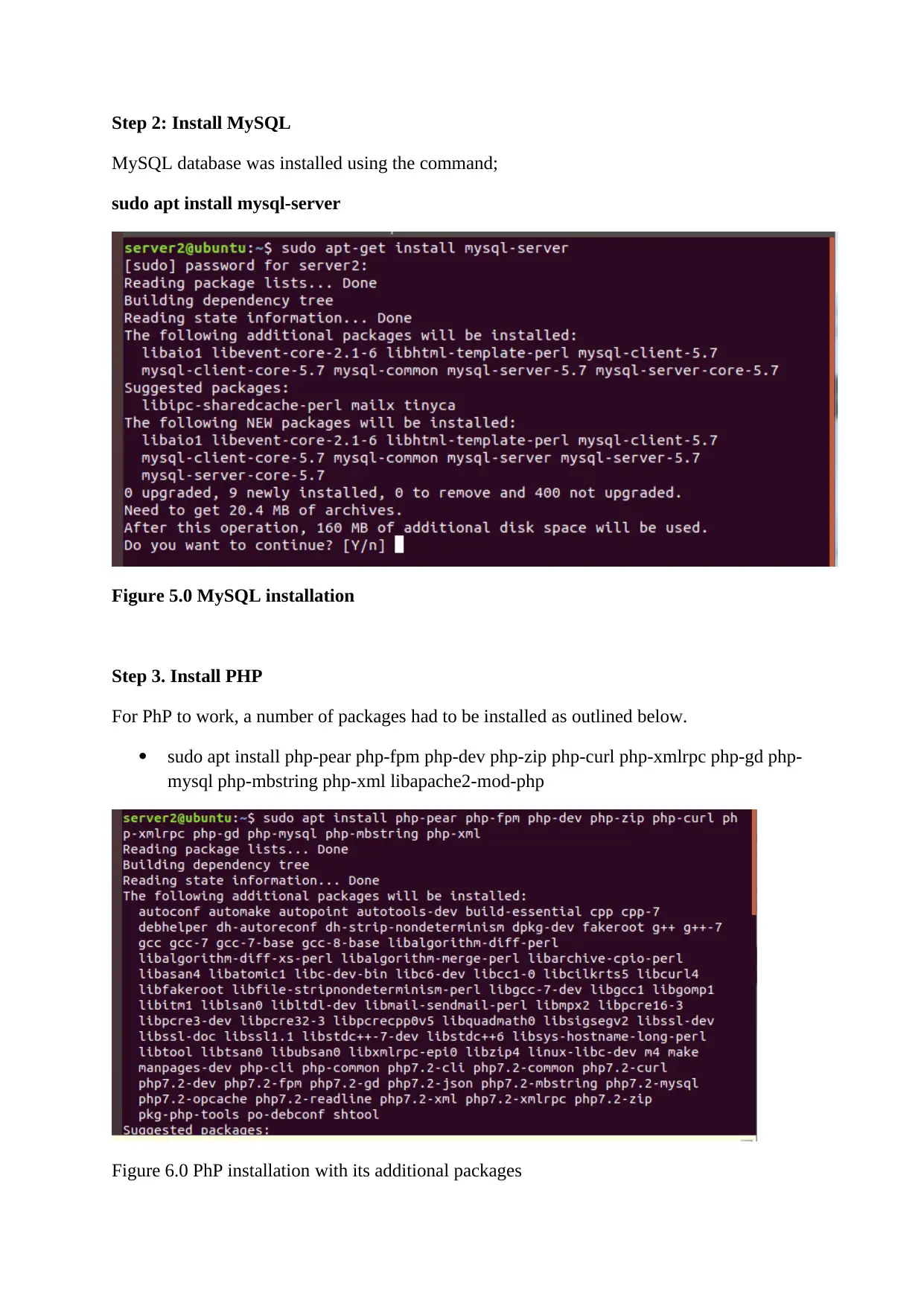
Step 2: Install MySQL
MySQL database was installed using the command;
sudo apt install mysql-server
Figure 5.0 MySQL installation
Step 3. Install PHP
For PhP to work, a number of packages had to be installed as outlined below.
sudo apt install php-pear php-fpm php-dev php-zip php-curl php-xmlrpc php-gd php-
mysql php-mbstring php-xml libapache2-mod-php
Figure 6.0 PhP installation with its additional packages
MySQL database was installed using the command;
sudo apt install mysql-server
Figure 5.0 MySQL installation
Step 3. Install PHP
For PhP to work, a number of packages had to be installed as outlined below.
sudo apt install php-pear php-fpm php-dev php-zip php-curl php-xmlrpc php-gd php-
mysql php-mbstring php-xml libapache2-mod-php
Figure 6.0 PhP installation with its additional packages
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
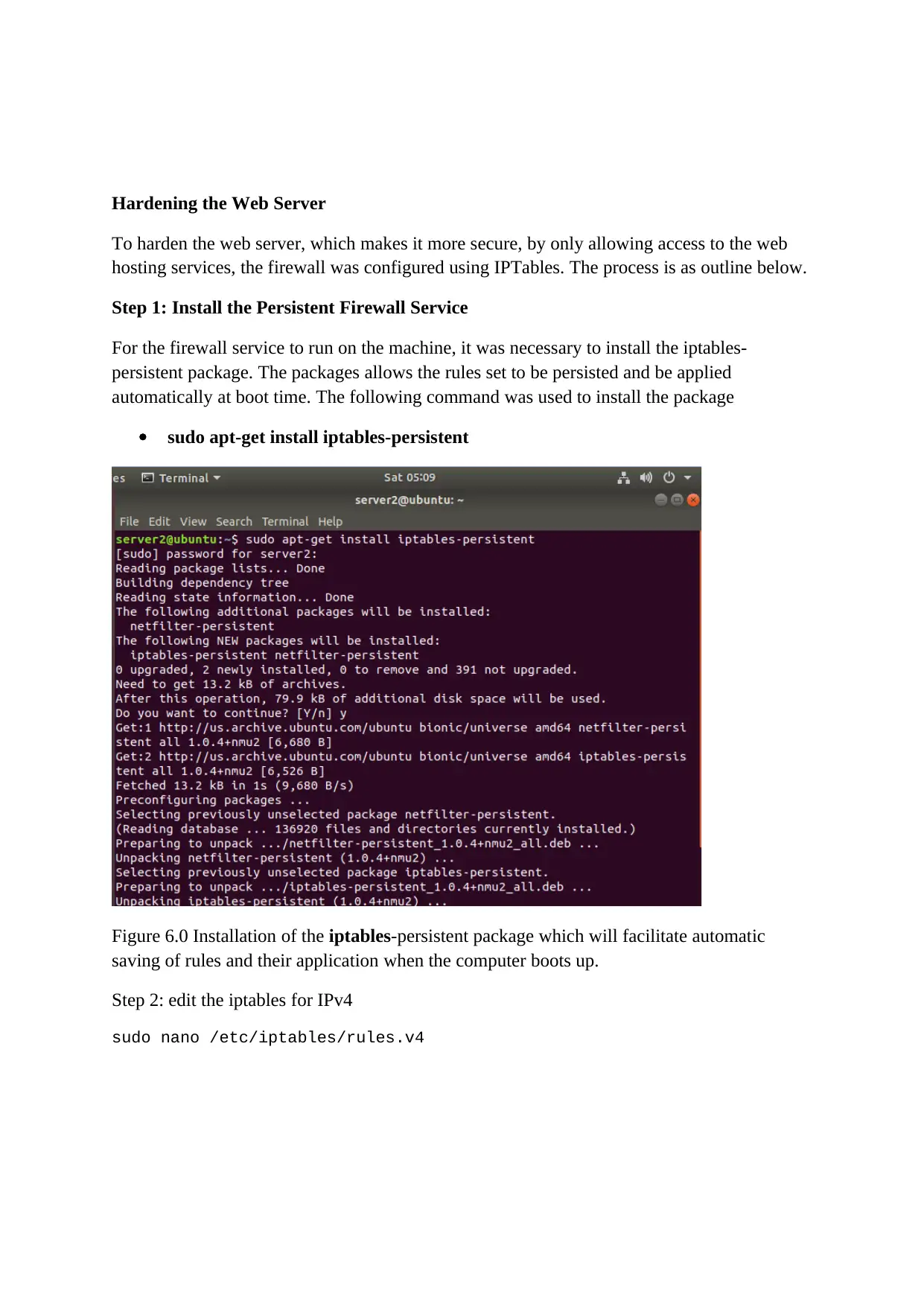
Hardening the Web Server
To harden the web server, which makes it more secure, by only allowing access to the web
hosting services, the firewall was configured using IPTables. The process is as outline below.
Step 1: Install the Persistent Firewall Service
For the firewall service to run on the machine, it was necessary to install the iptables-
persistent package. The packages allows the rules set to be persisted and be applied
automatically at boot time. The following command was used to install the package
sudo apt-get install iptables-persistent
Figure 6.0 Installation of the iptables-persistent package which will facilitate automatic
saving of rules and their application when the computer boots up.
Step 2: edit the iptables for IPv4
sudo nano /etc/iptables/rules.v4
To harden the web server, which makes it more secure, by only allowing access to the web
hosting services, the firewall was configured using IPTables. The process is as outline below.
Step 1: Install the Persistent Firewall Service
For the firewall service to run on the machine, it was necessary to install the iptables-
persistent package. The packages allows the rules set to be persisted and be applied
automatically at boot time. The following command was used to install the package
sudo apt-get install iptables-persistent
Figure 6.0 Installation of the iptables-persistent package which will facilitate automatic
saving of rules and their application when the computer boots up.
Step 2: edit the iptables for IPv4
sudo nano /etc/iptables/rules.v4
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
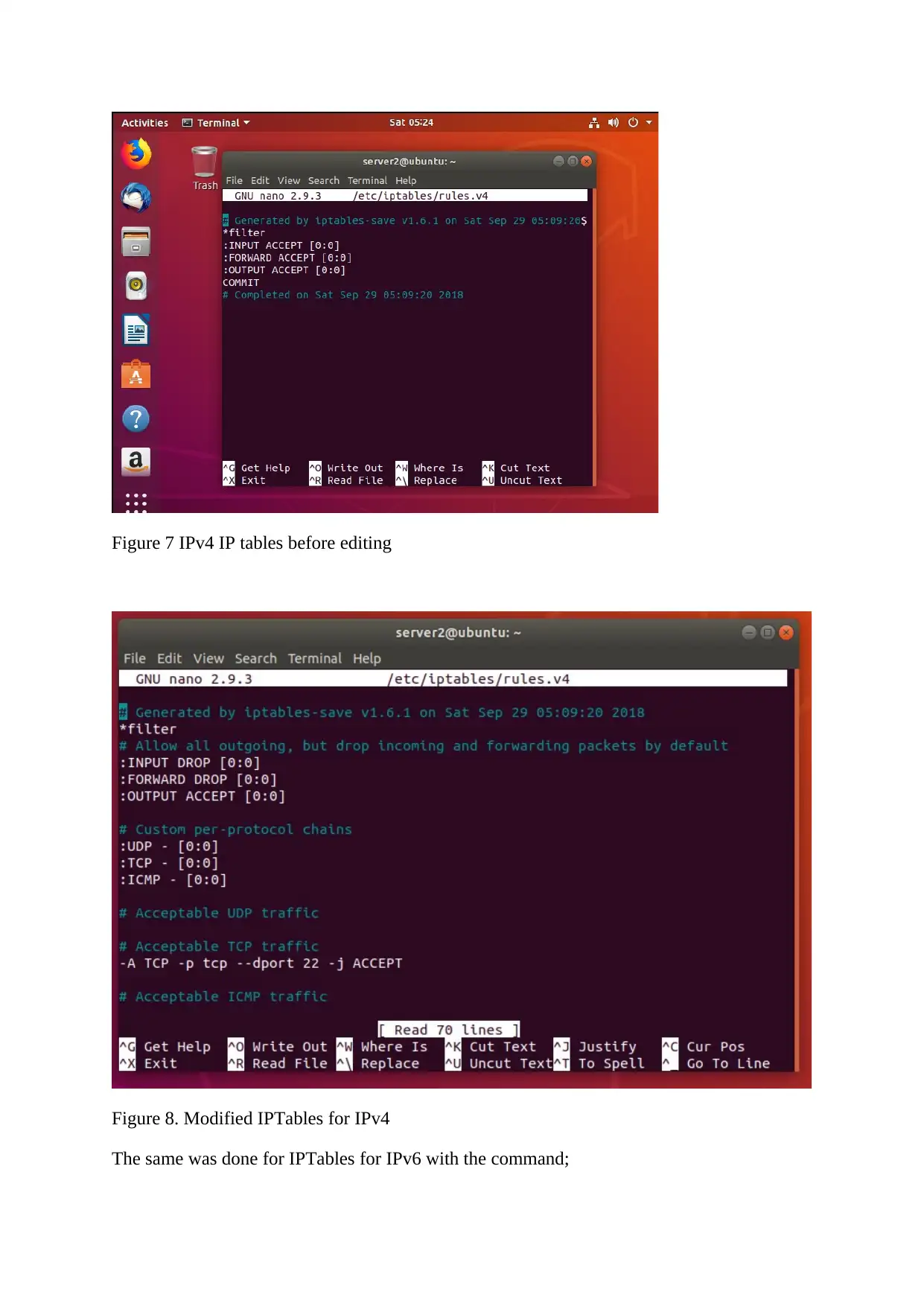
Figure 7 IPv4 IP tables before editing
Figure 8. Modified IPTables for IPv4
The same was done for IPTables for IPv6 with the command;
Figure 8. Modified IPTables for IPv4
The same was done for IPTables for IPv6 with the command;
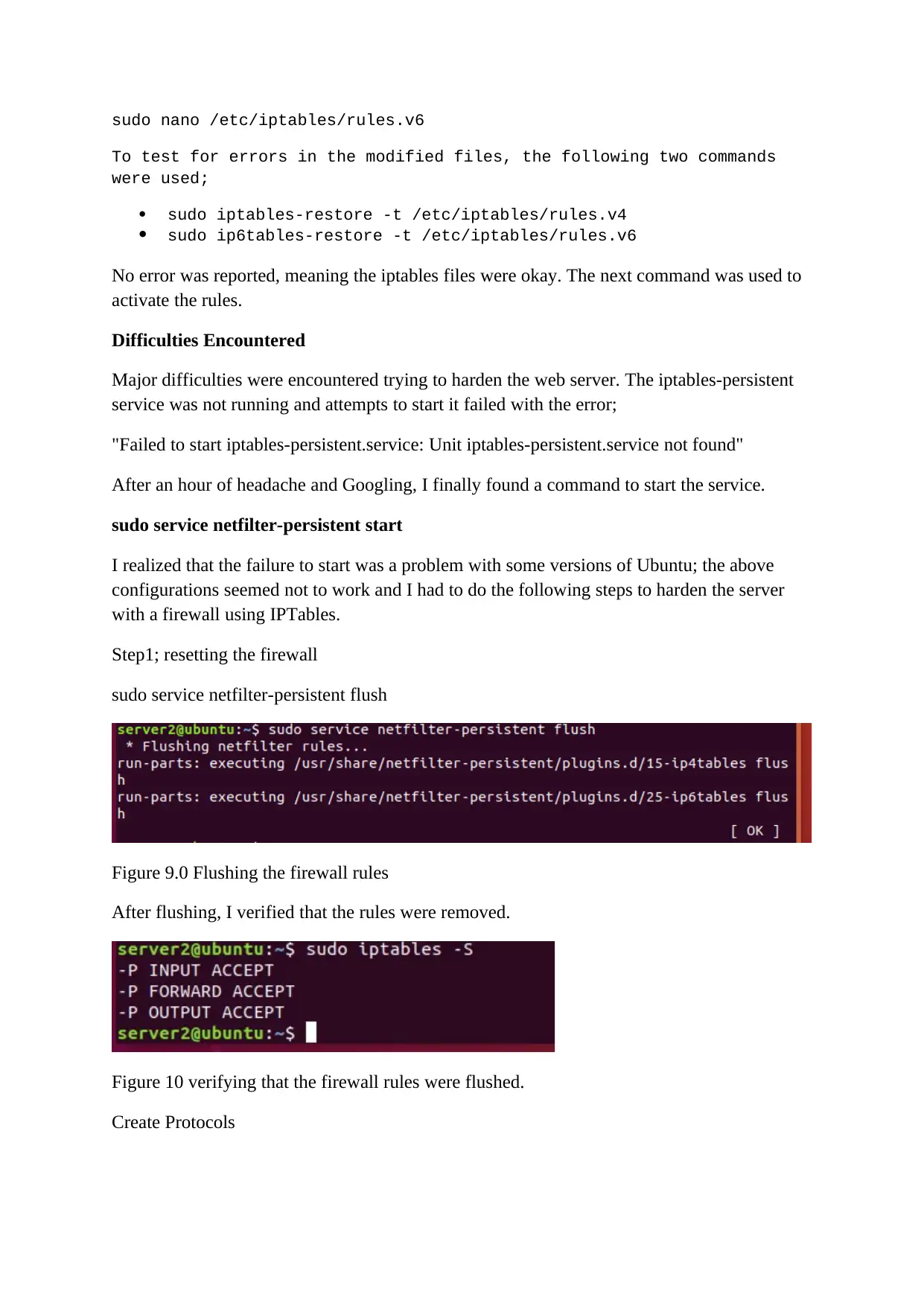
sudo nano /etc/iptables/rules.v6
To test for errors in the modified files, the following two commands
were used;
sudo iptables-restore -t /etc/iptables/rules.v4
sudo ip6tables-restore -t /etc/iptables/rules.v6
No error was reported, meaning the iptables files were okay. The next command was used to
activate the rules.
Difficulties Encountered
Major difficulties were encountered trying to harden the web server. The iptables-persistent
service was not running and attempts to start it failed with the error;
"Failed to start iptables-persistent.service: Unit iptables-persistent.service not found"
After an hour of headache and Googling, I finally found a command to start the service.
sudo service netfilter-persistent start
I realized that the failure to start was a problem with some versions of Ubuntu; the above
configurations seemed not to work and I had to do the following steps to harden the server
with a firewall using IPTables.
Step1; resetting the firewall
sudo service netfilter-persistent flush
Figure 9.0 Flushing the firewall rules
After flushing, I verified that the rules were removed.
Figure 10 verifying that the firewall rules were flushed.
Create Protocols
To test for errors in the modified files, the following two commands
were used;
sudo iptables-restore -t /etc/iptables/rules.v4
sudo ip6tables-restore -t /etc/iptables/rules.v6
No error was reported, meaning the iptables files were okay. The next command was used to
activate the rules.
Difficulties Encountered
Major difficulties were encountered trying to harden the web server. The iptables-persistent
service was not running and attempts to start it failed with the error;
"Failed to start iptables-persistent.service: Unit iptables-persistent.service not found"
After an hour of headache and Googling, I finally found a command to start the service.
sudo service netfilter-persistent start
I realized that the failure to start was a problem with some versions of Ubuntu; the above
configurations seemed not to work and I had to do the following steps to harden the server
with a firewall using IPTables.
Step1; resetting the firewall
sudo service netfilter-persistent flush
Figure 9.0 Flushing the firewall rules
After flushing, I verified that the rules were removed.
Figure 10 verifying that the firewall rules were flushed.
Create Protocols
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
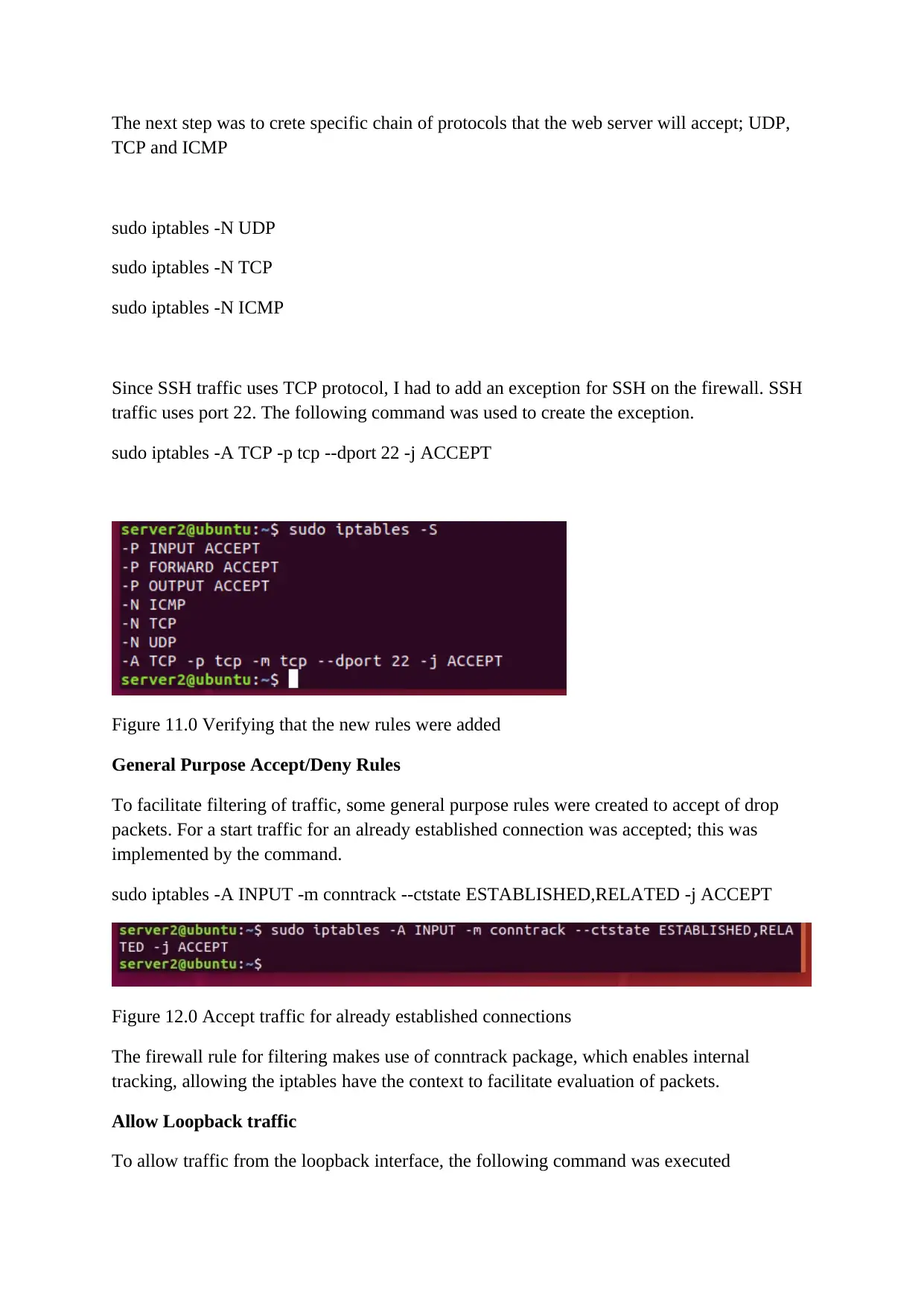
The next step was to crete specific chain of protocols that the web server will accept; UDP,
TCP and ICMP
sudo iptables -N UDP
sudo iptables -N TCP
sudo iptables -N ICMP
Since SSH traffic uses TCP protocol, I had to add an exception for SSH on the firewall. SSH
traffic uses port 22. The following command was used to create the exception.
sudo iptables -A TCP -p tcp --dport 22 -j ACCEPT
Figure 11.0 Verifying that the new rules were added
General Purpose Accept/Deny Rules
To facilitate filtering of traffic, some general purpose rules were created to accept of drop
packets. For a start traffic for an already established connection was accepted; this was
implemented by the command.
sudo iptables -A INPUT -m conntrack --ctstate ESTABLISHED,RELATED -j ACCEPT
Figure 12.0 Accept traffic for already established connections
The firewall rule for filtering makes use of conntrack package, which enables internal
tracking, allowing the iptables have the context to facilitate evaluation of packets.
Allow Loopback traffic
To allow traffic from the loopback interface, the following command was executed
TCP and ICMP
sudo iptables -N UDP
sudo iptables -N TCP
sudo iptables -N ICMP
Since SSH traffic uses TCP protocol, I had to add an exception for SSH on the firewall. SSH
traffic uses port 22. The following command was used to create the exception.
sudo iptables -A TCP -p tcp --dport 22 -j ACCEPT
Figure 11.0 Verifying that the new rules were added
General Purpose Accept/Deny Rules
To facilitate filtering of traffic, some general purpose rules were created to accept of drop
packets. For a start traffic for an already established connection was accepted; this was
implemented by the command.
sudo iptables -A INPUT -m conntrack --ctstate ESTABLISHED,RELATED -j ACCEPT
Figure 12.0 Accept traffic for already established connections
The firewall rule for filtering makes use of conntrack package, which enables internal
tracking, allowing the iptables have the context to facilitate evaluation of packets.
Allow Loopback traffic
To allow traffic from the loopback interface, the following command was executed
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
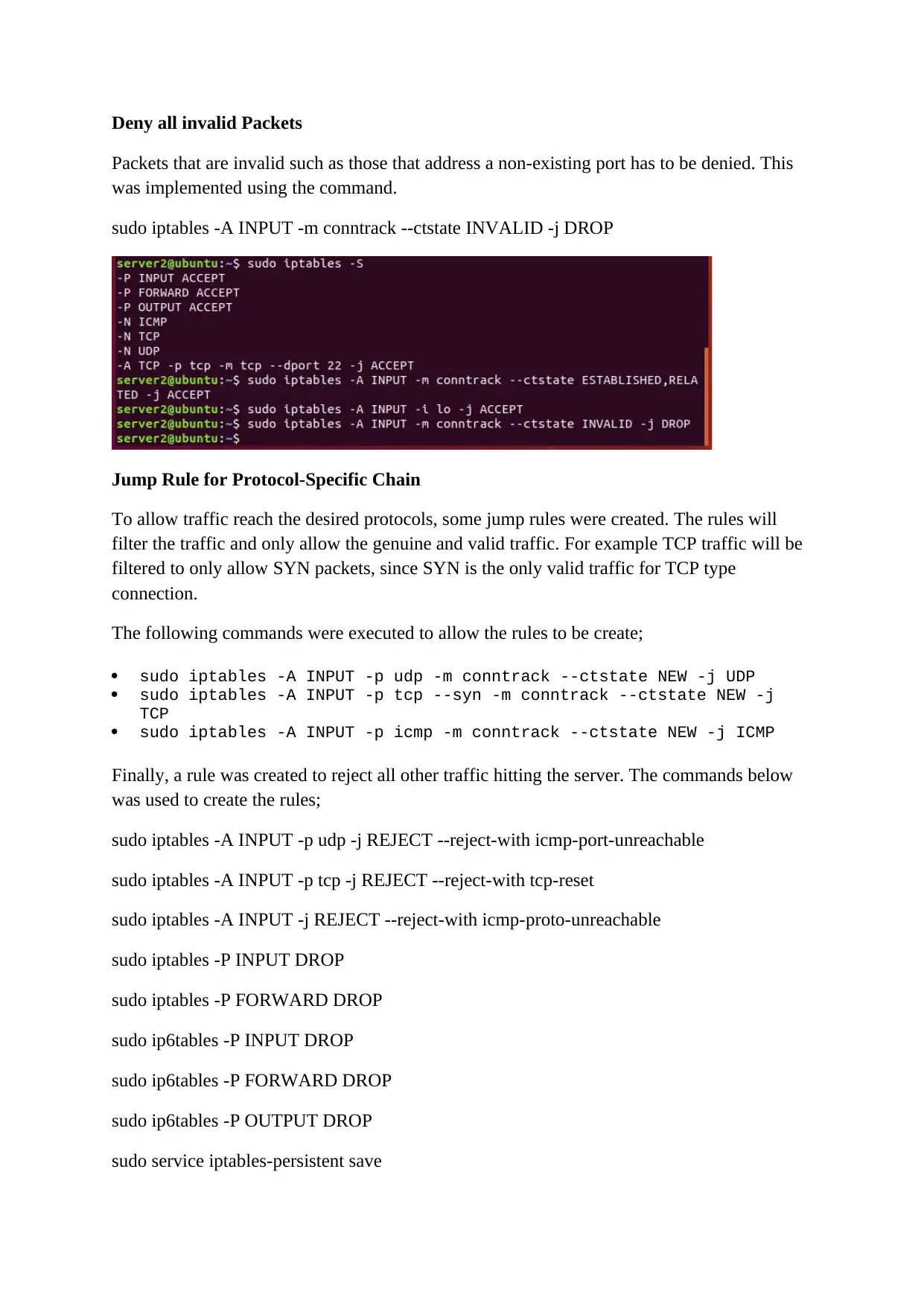
Deny all invalid Packets
Packets that are invalid such as those that address a non-existing port has to be denied. This
was implemented using the command.
sudo iptables -A INPUT -m conntrack --ctstate INVALID -j DROP
Jump Rule for Protocol-Specific Chain
To allow traffic reach the desired protocols, some jump rules were created. The rules will
filter the traffic and only allow the genuine and valid traffic. For example TCP traffic will be
filtered to only allow SYN packets, since SYN is the only valid traffic for TCP type
connection.
The following commands were executed to allow the rules to be create;
sudo iptables -A INPUT -p udp -m conntrack --ctstate NEW -j UDP
sudo iptables -A INPUT -p tcp --syn -m conntrack --ctstate NEW -j
TCP
sudo iptables -A INPUT -p icmp -m conntrack --ctstate NEW -j ICMP
Finally, a rule was created to reject all other traffic hitting the server. The commands below
was used to create the rules;
sudo iptables -A INPUT -p udp -j REJECT --reject-with icmp-port-unreachable
sudo iptables -A INPUT -p tcp -j REJECT --reject-with tcp-reset
sudo iptables -A INPUT -j REJECT --reject-with icmp-proto-unreachable
sudo iptables -P INPUT DROP
sudo iptables -P FORWARD DROP
sudo ip6tables -P INPUT DROP
sudo ip6tables -P FORWARD DROP
sudo ip6tables -P OUTPUT DROP
sudo service iptables-persistent save
Packets that are invalid such as those that address a non-existing port has to be denied. This
was implemented using the command.
sudo iptables -A INPUT -m conntrack --ctstate INVALID -j DROP
Jump Rule for Protocol-Specific Chain
To allow traffic reach the desired protocols, some jump rules were created. The rules will
filter the traffic and only allow the genuine and valid traffic. For example TCP traffic will be
filtered to only allow SYN packets, since SYN is the only valid traffic for TCP type
connection.
The following commands were executed to allow the rules to be create;
sudo iptables -A INPUT -p udp -m conntrack --ctstate NEW -j UDP
sudo iptables -A INPUT -p tcp --syn -m conntrack --ctstate NEW -j
TCP
sudo iptables -A INPUT -p icmp -m conntrack --ctstate NEW -j ICMP
Finally, a rule was created to reject all other traffic hitting the server. The commands below
was used to create the rules;
sudo iptables -A INPUT -p udp -j REJECT --reject-with icmp-port-unreachable
sudo iptables -A INPUT -p tcp -j REJECT --reject-with tcp-reset
sudo iptables -A INPUT -j REJECT --reject-with icmp-proto-unreachable
sudo iptables -P INPUT DROP
sudo iptables -P FORWARD DROP
sudo ip6tables -P INPUT DROP
sudo ip6tables -P FORWARD DROP
sudo ip6tables -P OUTPUT DROP
sudo service iptables-persistent save
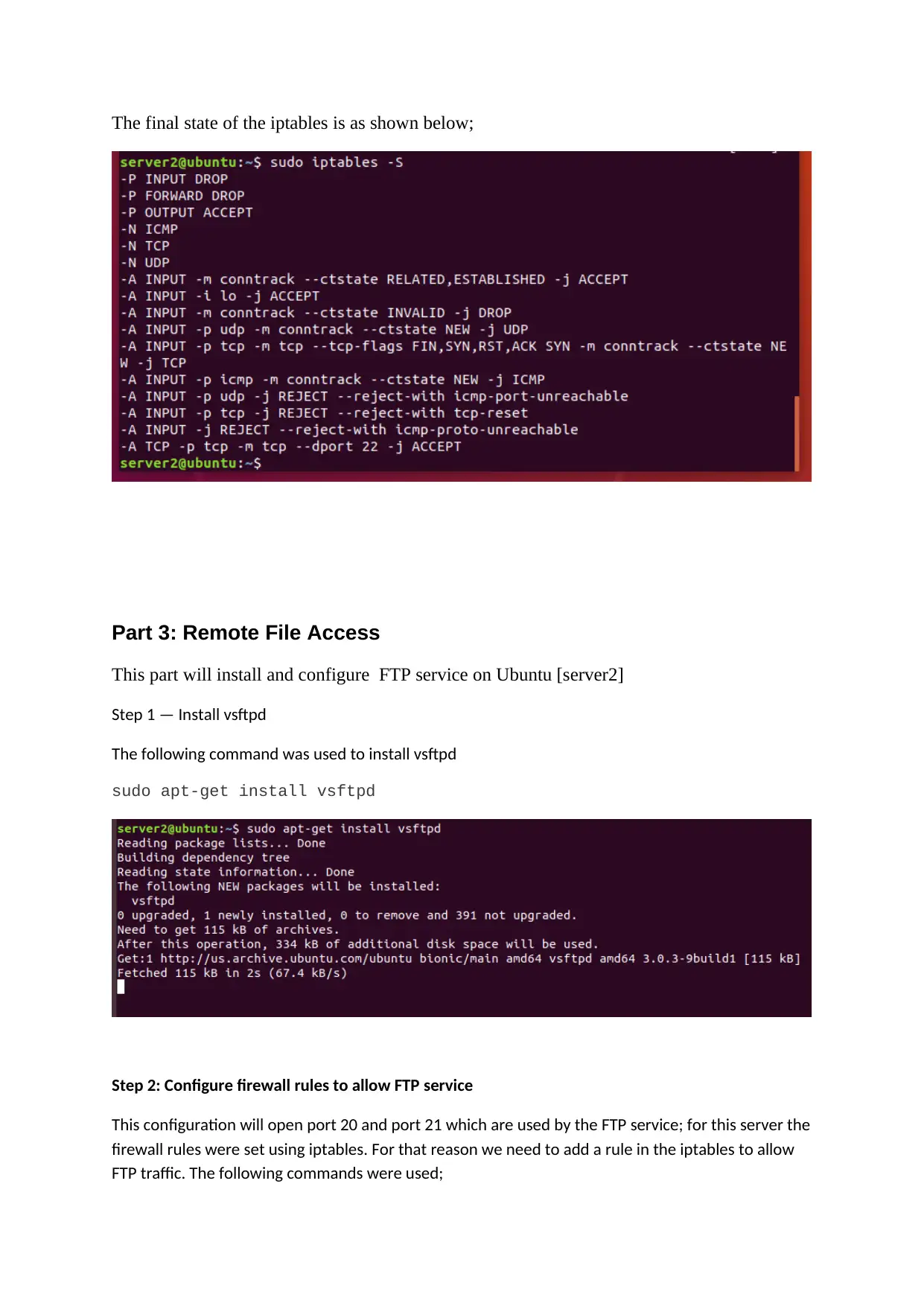
The final state of the iptables is as shown below;
Part 3: Remote File Access
This part will install and configure FTP service on Ubuntu [server2]
Step 1 — Install vsftpd
The following command was used to install vsftpd
sudo apt-get install vsftpd
Step 2: Configure firewall rules to allow FTP service
This configuration will open port 20 and port 21 which are used by the FTP service; for this server the
firewall rules were set using iptables. For that reason we need to add a rule in the iptables to allow
FTP traffic. The following commands were used;
Part 3: Remote File Access
This part will install and configure FTP service on Ubuntu [server2]
Step 1 — Install vsftpd
The following command was used to install vsftpd
sudo apt-get install vsftpd
Step 2: Configure firewall rules to allow FTP service
This configuration will open port 20 and port 21 which are used by the FTP service; for this server the
firewall rules were set using iptables. For that reason we need to add a rule in the iptables to allow
FTP traffic. The following commands were used;
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
1 out of 19
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.




