Master's Research Proposal: Machine Learning for IoT Applications
VerifiedAdded on 2022/08/21
|10
|2219
|10
Project
AI Summary
This research proposal, submitted for a Master's degree in Data Analytics at Dublin Business School, investigates the potential of machine learning to enhance Internet of Things (IoT) applications. The proposal begins by outlining the research hypothesis, which posits that machine learning techniques can improve IoT applications. It then introduces the challenges associated with IoT devices, such as scalability, interoperability, and data security issues, and highlights the potential of machine learning algorithms to address these problems. The literature review synthesizes existing research, examining how machine learning can tackle IoT challenges. The methodology section outlines a non-probabilistic sampling method and hypothesis testing. The proposal also details the data collection process, including the use of questionnaires and consent procedures, and addresses data ownership and security. The future work section anticipates enhancements in the accuracy of predictive outcomes and the resolution of technical challenges in IoT devices through machine learning advancements. References to relevant academic journals are included.

MASTER RESEARCH PROPOSAL
IN DATA ANALYTICS
Faculty of Data
Analytics Dublin
Business school
1
IN DATA ANALYTICS
Faculty of Data
Analytics Dublin
Business school
1
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

Author: Nishkriya Janakiraman Supervisor:
E-mail: 10525020@mydbs.ie E-mail:
Phone: +353 894029551 Phone:
Defense
Planned:
List of Contents
Proposed Topic................................................................................................................... 3
Research hypothesis.......................................................................................................... 3
Introduction to the research............................................................................................ 3
Overview of literature review........................................................................................... 4
Literature review................................................................................................................ 4
Literature Gap..................................................................................................................... 5
Methodology and Implementation................................................................................... 6
Future work......................................................................................................................... 6
References........................................................................................................................... 7
2
E-mail: 10525020@mydbs.ie E-mail:
Phone: +353 894029551 Phone:
Defense
Planned:
List of Contents
Proposed Topic................................................................................................................... 3
Research hypothesis.......................................................................................................... 3
Introduction to the research............................................................................................ 3
Overview of literature review........................................................................................... 4
Literature review................................................................................................................ 4
Literature Gap..................................................................................................................... 5
Methodology and Implementation................................................................................... 6
Future work......................................................................................................................... 6
References........................................................................................................................... 7
2

Proposed Topic
Use of machine learning to improve the Internet of Things based applications
Research hypothesis
Research hypothesis is defined as the type of statement which helps in
understanding the probable (Kumar and Gandhi 2018) outcome of a research
paper. The testable proposition of a research is also identified with the help of
research hypothesis (Lade, Ghosh and Srinivasan 2017). There are diverse
categories of research hypothesis which are considered in research proposals such
as the null hypothesis (H0) and alternative hypothesis (H1).
The hypothesis of this research is as follows:
H0: Machine Learning techniques have no impact on the IoT based devices.
H1: Machine Learning techniques can improve the IoT based applications.
Introduction to the research
There are diverse categories of challenges related with the use of IoT based devices
such as the scalability issues, interoperability issues, and data security issues (Lee
et al. 2016). Each of these issues is having a direct adverse impact on the
performance of the IoT devices (Outchakoucht, Hamza and Leroy 2017).
Machine learning algorithms is very much useful to improve the capability of any
advanced system these days such as the Management Information System (Lee et
al. 2018).
The notable determination of this poster is to identify whether the challenges of IoT
devices can be resolved using Machine Learning techniques or not. Secondary data
collection procedure shall be considered in this research.
3
Use of machine learning to improve the Internet of Things based applications
Research hypothesis
Research hypothesis is defined as the type of statement which helps in
understanding the probable (Kumar and Gandhi 2018) outcome of a research
paper. The testable proposition of a research is also identified with the help of
research hypothesis (Lade, Ghosh and Srinivasan 2017). There are diverse
categories of research hypothesis which are considered in research proposals such
as the null hypothesis (H0) and alternative hypothesis (H1).
The hypothesis of this research is as follows:
H0: Machine Learning techniques have no impact on the IoT based devices.
H1: Machine Learning techniques can improve the IoT based applications.
Introduction to the research
There are diverse categories of challenges related with the use of IoT based devices
such as the scalability issues, interoperability issues, and data security issues (Lee
et al. 2016). Each of these issues is having a direct adverse impact on the
performance of the IoT devices (Outchakoucht, Hamza and Leroy 2017).
Machine learning algorithms is very much useful to improve the capability of any
advanced system these days such as the Management Information System (Lee et
al. 2018).
The notable determination of this poster is to identify whether the challenges of IoT
devices can be resolved using Machine Learning techniques or not. Secondary data
collection procedure shall be considered in this research.
3
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
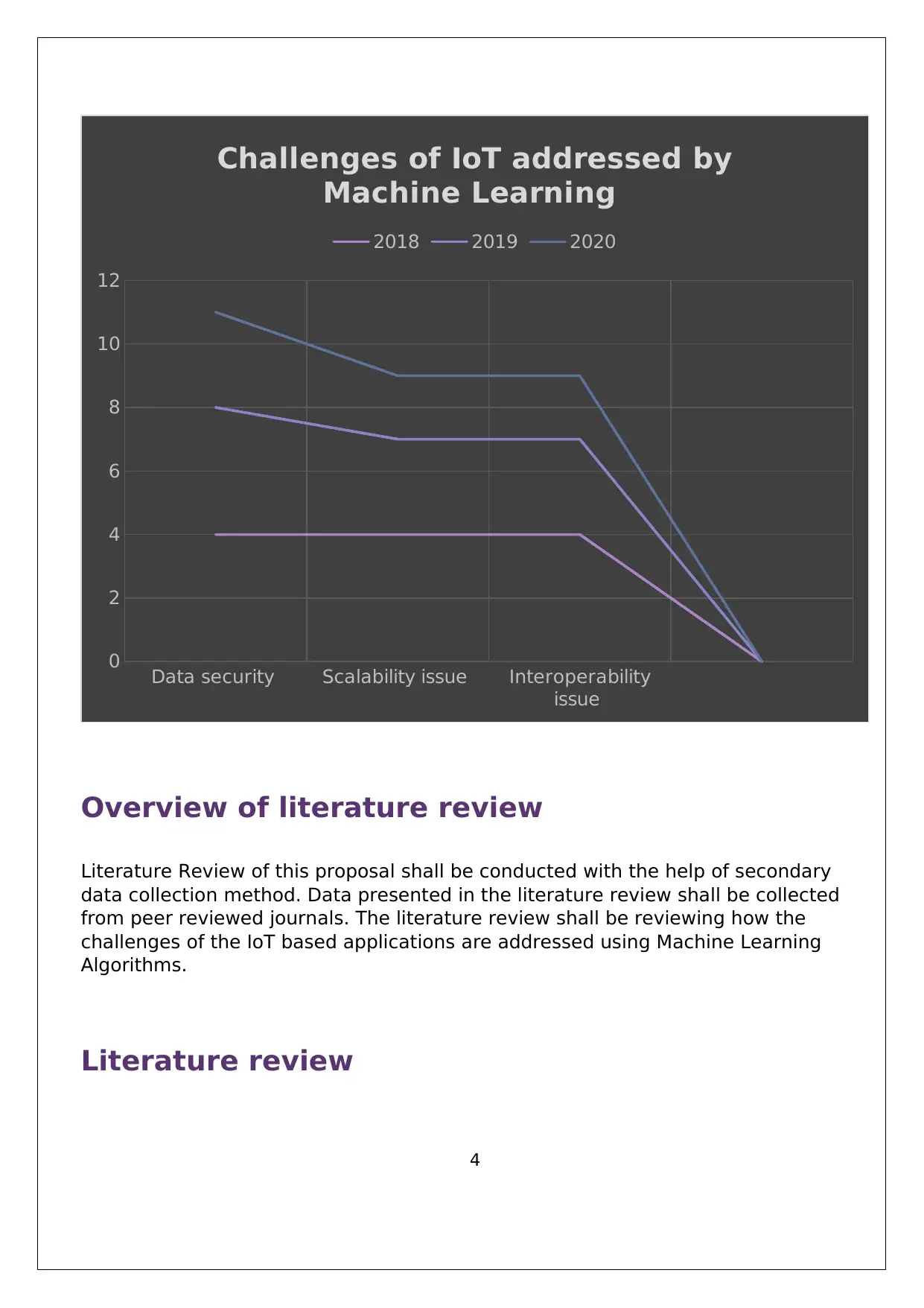
Data security Scalability issue Interoperability
issue
0
2
4
6
8
10
12
Challenges of IoT addressed by
Machine Learning
2018 2019 2020
Overview of literature review
Literature Review of this proposal shall be conducted with the help of secondary
data collection method. Data presented in the literature review shall be collected
from peer reviewed journals. The literature review shall be reviewing how the
challenges of the IoT based applications are addressed using Machine Learning
Algorithms.
Literature review
4
issue
0
2
4
6
8
10
12
Challenges of IoT addressed by
Machine Learning
2018 2019 2020
Overview of literature review
Literature Review of this proposal shall be conducted with the help of secondary
data collection method. Data presented in the literature review shall be collected
from peer reviewed journals. The literature review shall be reviewing how the
challenges of the IoT based applications are addressed using Machine Learning
Algorithms.
Literature review
4
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

As stated by Alam et al. (2016), scalability, interoperability and data security
are the prime issues in IoT based devices such as smart televisions, smart
appliances, commercial security systems, smart wearable, and smart city
technologies.
According to Chin, Callaghan and Lam (2017), machine learning algorithms
(MLA) are very much essential to address the threat coming from the
scalability issue of the IoT devices used in construction projects. The
researcher of this journal highlighted that networking and storage
architecture of the IoT device can also be secured with the help of MLA (Lade,
Ghosh and Srinivasan 2017). Supporting the above discussion as elaborated
by Diro and Chilamkurti (2018), interoperability issues in IoT based
applications such as the server issues, infrastructure issues, power supply
issues and the file formatting issues can be addressed in the first place with
the help of the MLA. The journal also stated that the use of public key
architecture using MLA can reduce the data security issues in the IoT based
applications (Kumar and Gandhi 2018).
At the same time, as mentioned by Doshi, Apthorpe and Feamster (2018),
data security issues in the IoT based applications such as fake data
generation, presence of untrusted mappers, sensitive information mining,
struggle of granular access control, data proven difficulties and security
issues of the database which are linked with the IoT based devices can also
be addressed using the MLA. As mentioned by Earley (2015), continuous
improvement of IoT based devices can be maintained with the help of MLA.
The journal helped in understanding that the trends and patters of the IoT
devices can also be analysed with the help of the MLA (Mahdavinejad et al.
2018).
On the other hand, as mentioned by Jeschke et al. (2017), there are few
limitations related with the use of MLA in IoT based devices as well such as
the requirement of requiring larger data sets. The journal explained that data
interpretation ability of the IoT devices might get affected due to the addition
of MLA (Kumar, Saurabh and Manik 2017). The other limitation of MLA in IoT
based devices is the high error susceptibility (Luo et al. 2016).
Literature Gap
o Data security issue in IoT can be solved with the help of IoT security analytics.
o Avoiding single point of failure in IoT devices can address the scalability
issues in IoT based devices.
5
are the prime issues in IoT based devices such as smart televisions, smart
appliances, commercial security systems, smart wearable, and smart city
technologies.
According to Chin, Callaghan and Lam (2017), machine learning algorithms
(MLA) are very much essential to address the threat coming from the
scalability issue of the IoT devices used in construction projects. The
researcher of this journal highlighted that networking and storage
architecture of the IoT device can also be secured with the help of MLA (Lade,
Ghosh and Srinivasan 2017). Supporting the above discussion as elaborated
by Diro and Chilamkurti (2018), interoperability issues in IoT based
applications such as the server issues, infrastructure issues, power supply
issues and the file formatting issues can be addressed in the first place with
the help of the MLA. The journal also stated that the use of public key
architecture using MLA can reduce the data security issues in the IoT based
applications (Kumar and Gandhi 2018).
At the same time, as mentioned by Doshi, Apthorpe and Feamster (2018),
data security issues in the IoT based applications such as fake data
generation, presence of untrusted mappers, sensitive information mining,
struggle of granular access control, data proven difficulties and security
issues of the database which are linked with the IoT based devices can also
be addressed using the MLA. As mentioned by Earley (2015), continuous
improvement of IoT based devices can be maintained with the help of MLA.
The journal helped in understanding that the trends and patters of the IoT
devices can also be analysed with the help of the MLA (Mahdavinejad et al.
2018).
On the other hand, as mentioned by Jeschke et al. (2017), there are few
limitations related with the use of MLA in IoT based devices as well such as
the requirement of requiring larger data sets. The journal explained that data
interpretation ability of the IoT devices might get affected due to the addition
of MLA (Kumar, Saurabh and Manik 2017). The other limitation of MLA in IoT
based devices is the high error susceptibility (Luo et al. 2016).
Literature Gap
o Data security issue in IoT can be solved with the help of IoT security analytics.
o Avoiding single point of failure in IoT devices can address the scalability
issues in IoT based devices.
5
o Development of a data strategy can address the interoperability issue in IoT
based applications.
Methodology and Implementation
• Non probabilistic sampling method shall be considered in this proposal.
• Hypothesis testing research shall be considered as the type of investigation in
this proposal.
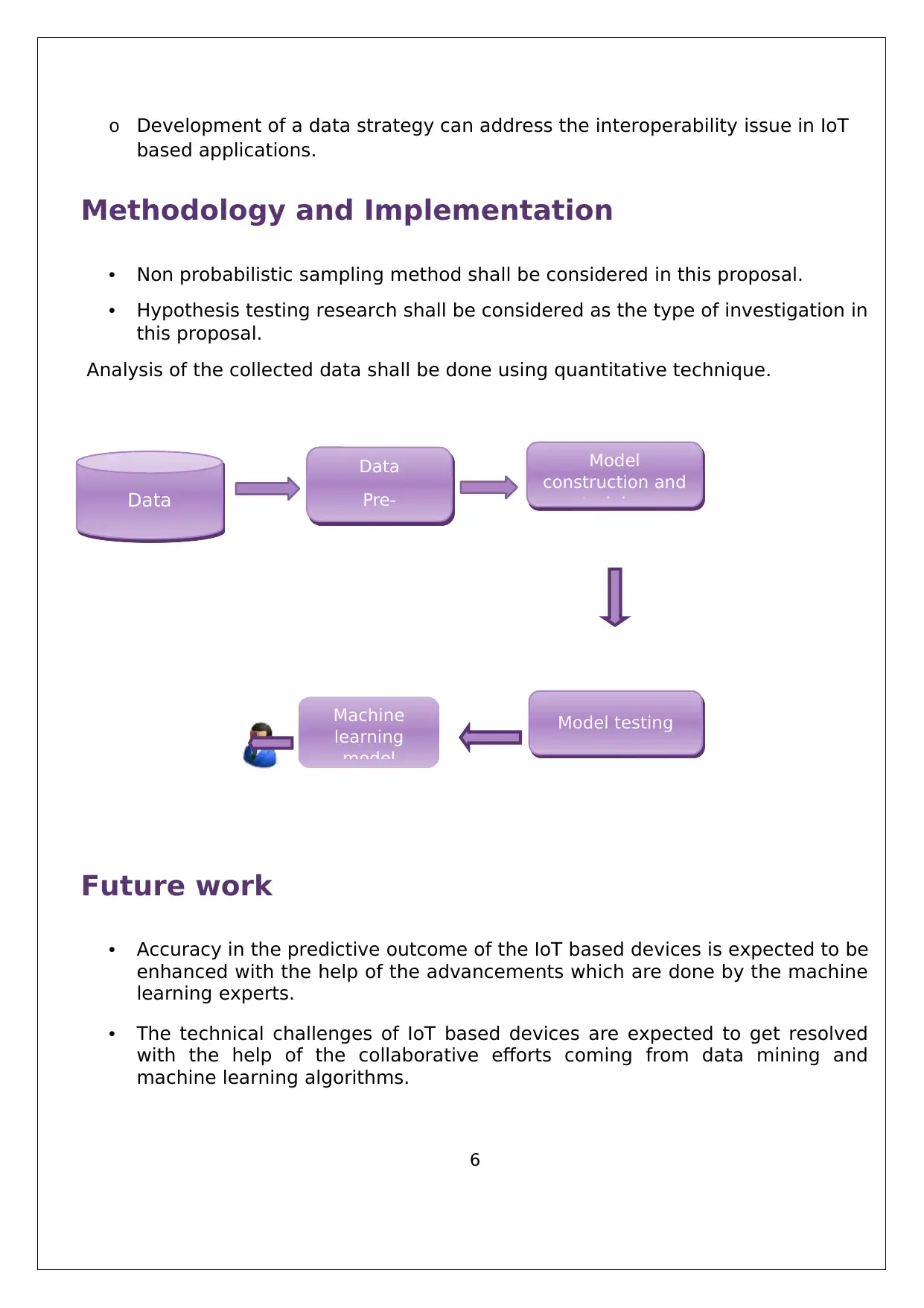
Analysis of the collected data shall be done using quantitative technique.
Future work
• Accuracy in the predictive outcome of the IoT based devices is expected to be
enhanced with the help of the advancements which are done by the machine
learning experts.
• The technical challenges of IoT based devices are expected to get resolved
with the help of the collaborative efforts coming from data mining and
machine learning algorithms.
6
Data
Machine
learning
model
Data
Pre-
processing
Model testing
Model
construction and
training
based applications.
Methodology and Implementation
• Non probabilistic sampling method shall be considered in this proposal.
• Hypothesis testing research shall be considered as the type of investigation in
this proposal.
Analysis of the collected data shall be done using quantitative technique.
Future work
• Accuracy in the predictive outcome of the IoT based devices is expected to be
enhanced with the help of the advancements which are done by the machine
learning experts.
• The technical challenges of IoT based devices are expected to get resolved
with the help of the collaborative efforts coming from data mining and
machine learning algorithms.
6
Data
Machine
learning
model
Data
Pre-
processing
Model testing
Model
construction and
training
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

• Accessing algorithm intelligence will be much easier in the coming years due
to the use of machine learning language.
References
1. Alam, F., Mehmood, R., Katib, I. and Albeshri, A., 2016. Analysis of eight data
mining algorithms for smarter Internet of Things (IoT). Procedia Computer
Science, 98, pp.437-442
2. Chin, J., Callaghan, V. and Lam, I., 2017, June. Understanding and
personalising smart city services using machine learning, the internet-of-
things and big data. In 2017 IEEE 26th International Symposium on Industrial
Electronics (ISIE) (pp. 2050-2055). IEEE.
3. Diro, A.A. and Chilamkurti, N., 2018. Distributed attack detection scheme
using deep learning approach for Internet of Things. Future Generation
Computer Systems, 82, pp.761-768.
4. Doshi, R., Apthorpe, N. and Feamster, N., 2018, May. Machine learning ddos
detection for consumer internet of things devices. In 2018 IEEE Security and
Privacy Workshops (SPW) (pp. 29-35). IEEE.
5. Earley, S., 2015. Analytics, machine learning, and the internet of things. IT
Professional, 17(1), pp.10-13.
6. Jeschke, S., Brecher, C., Meisen, T., Özdemir, D. and Eschert, T., 2017.
Industrial internet of things and cyber manufacturing systems. In Industrial
internet of things (pp. 3-19). Springer, Cham.
7. Kumar, Ashish, Saurabh Goyal, and Manik Varma. "Resource-efficient machine
learning in 2 KB RAM for the internet of things." In Proceedings of the 34th
International Conference on Machine Learning-Volume 70, pp. 1935-1944.
JMLR. org, 2017.
8. Kumar, P.M. and Gandhi, U.D., 2018. A novel three-tier Internet of Things
architecture with machine learning algorithm for early detection of heart
diseases. Computers & Electrical Engineering, 65, pp.222-235.
9. Lade, P., Ghosh, R. and Srinivasan, S., 2017. Manufacturing analytics and
industrial internet of things. IEEE Intelligent Systems, 32(3), pp.74-79.
10.Lee, J., Stanley, M., Spanias, A. and Tepedelenlioglu, C., 2016, December.
Integrating machine learning in embedded sensor systems for Internet-of-
Things applications. In 2016 IEEE international symposium on signal
processing and information technology (ISSPIT) (pp. 290-294). IEEE.
11.Li, H., Ota, K. and Dong, M., 2018. Learning IoT in edge: Deep learning for the
Internet of Things with edge computing. IEEE network, 32(1), pp.96-101.
12.Luo, X., Liu, J., Zhang, D. and Chang, X., 2016. A large-scale web QoS
prediction scheme for the Industrial Internet of Things based on a kernel
machine learning algorithm. Computer Networks, 101, pp.81-89.
13.Mahdavinejad, M.S., Rezvan, M., Barekatain, M., Adibi, P., Barnaghi, P. and
Sheth, A.P., 2018. Machine learning for Internet of Things data analysis: A
survey. Digital Communications and Networks, 4(3), pp.161-175.
7
to the use of machine learning language.
References
1. Alam, F., Mehmood, R., Katib, I. and Albeshri, A., 2016. Analysis of eight data
mining algorithms for smarter Internet of Things (IoT). Procedia Computer
Science, 98, pp.437-442
2. Chin, J., Callaghan, V. and Lam, I., 2017, June. Understanding and
personalising smart city services using machine learning, the internet-of-
things and big data. In 2017 IEEE 26th International Symposium on Industrial
Electronics (ISIE) (pp. 2050-2055). IEEE.
3. Diro, A.A. and Chilamkurti, N., 2018. Distributed attack detection scheme
using deep learning approach for Internet of Things. Future Generation
Computer Systems, 82, pp.761-768.
4. Doshi, R., Apthorpe, N. and Feamster, N., 2018, May. Machine learning ddos
detection for consumer internet of things devices. In 2018 IEEE Security and
Privacy Workshops (SPW) (pp. 29-35). IEEE.
5. Earley, S., 2015. Analytics, machine learning, and the internet of things. IT
Professional, 17(1), pp.10-13.
6. Jeschke, S., Brecher, C., Meisen, T., Özdemir, D. and Eschert, T., 2017.
Industrial internet of things and cyber manufacturing systems. In Industrial
internet of things (pp. 3-19). Springer, Cham.
7. Kumar, Ashish, Saurabh Goyal, and Manik Varma. "Resource-efficient machine
learning in 2 KB RAM for the internet of things." In Proceedings of the 34th
International Conference on Machine Learning-Volume 70, pp. 1935-1944.
JMLR. org, 2017.
8. Kumar, P.M. and Gandhi, U.D., 2018. A novel three-tier Internet of Things
architecture with machine learning algorithm for early detection of heart
diseases. Computers & Electrical Engineering, 65, pp.222-235.
9. Lade, P., Ghosh, R. and Srinivasan, S., 2017. Manufacturing analytics and
industrial internet of things. IEEE Intelligent Systems, 32(3), pp.74-79.
10.Lee, J., Stanley, M., Spanias, A. and Tepedelenlioglu, C., 2016, December.
Integrating machine learning in embedded sensor systems for Internet-of-
Things applications. In 2016 IEEE international symposium on signal
processing and information technology (ISSPIT) (pp. 290-294). IEEE.
11.Li, H., Ota, K. and Dong, M., 2018. Learning IoT in edge: Deep learning for the
Internet of Things with edge computing. IEEE network, 32(1), pp.96-101.
12.Luo, X., Liu, J., Zhang, D. and Chang, X., 2016. A large-scale web QoS
prediction scheme for the Industrial Internet of Things based on a kernel
machine learning algorithm. Computer Networks, 101, pp.81-89.
13.Mahdavinejad, M.S., Rezvan, M., Barekatain, M., Adibi, P., Barnaghi, P. and
Sheth, A.P., 2018. Machine learning for Internet of Things data analysis: A
survey. Digital Communications and Networks, 4(3), pp.161-175.
7
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

14.Outchakoucht, A., Hamza, E.S. and Leroy, J.P., 2017. Dynamic access control
policy based on blockchain and machine learning for the internet of things.
Int. J. Adv. Comput. Sci. Appl., 8(7), pp.417-424.
8
policy based on blockchain and machine learning for the internet of things.
Int. J. Adv. Comput. Sci. Appl., 8(7), pp.417-424.
8

Please outline the proposed sample group, including any specific criteria
Data of this proposal shall be collected from IoT experts working in commercial
establishments all over Ireland. Each participant of the data collection procedure must be
having at least 2 years of experience working with IoT based application. The selected
participants must also be aware of the capabilities of machine learning and the changes it
can have on an IoT base application. Both male and female participants irrespective of
their cultural backgrounds shall be allowed to take part in the data collection procedure.
The qualifying criteria of the sample group is master’s degree in the field of electronics or
electrical technology.
Describe how the proposed sample group will be formulated:
The strategy which shall be considered in the sampling procedure of this proposal is
the purposive sampling procedure. The proposal shall be looking forward to look for
participants who have completed their master’s degree from reputed universities in Ireland
such as University of Limerick, University of College Cork, University of College Dublin,
Trinity College and the National University of Ireland. Non probabilistic sampling method
shall be considered while sampling the data of this proposal. Hence, it can be said that a
wide sampling group shall be considered in the data collection procedure of this proposal
so that the validity of the data is maintained.
Indicate clearly what the involvement of the sample group will be in the research
process, How their consent will be obtained, potential risks to them, Anonymity
of data being collected
The primary step of the data collection process is the creation of a questionnaire in
Google Forms and likert scale shall be used for the creation of the questionnaire. After the
questionnaire is created it shall be distributed among the participants using email. Hence,
an online survey shall be considered to involve the sample group in the data collection
procedure.
After the participants sends backs the answers in the same thread consents shall be
obtained from them. A separate consent form shall be created by the analyst of this
proposal which shall be provided to the participants before and after the conduction of the
online survey.
There will be no risks for the participants who will be taking part in this online survey
due to the transparency which shall be maintained by the analyst of this research.
Anonymity of data shall be maintained as the identity of the respondent shall not be
disclosed by the analyst of this proposal.
Indicate any potential risks to people using the product how you propose to
minimize these:
There are no risks involved in the data collection procedure for the participants who
shall be considered in this proposal. None of the details of the survey shall be accessed by
any outsider who is not involved in this proposal.
Ownership of data collected
9
Data of this proposal shall be collected from IoT experts working in commercial
establishments all over Ireland. Each participant of the data collection procedure must be
having at least 2 years of experience working with IoT based application. The selected
participants must also be aware of the capabilities of machine learning and the changes it
can have on an IoT base application. Both male and female participants irrespective of
their cultural backgrounds shall be allowed to take part in the data collection procedure.
The qualifying criteria of the sample group is master’s degree in the field of electronics or
electrical technology.
Describe how the proposed sample group will be formulated:
The strategy which shall be considered in the sampling procedure of this proposal is
the purposive sampling procedure. The proposal shall be looking forward to look for
participants who have completed their master’s degree from reputed universities in Ireland
such as University of Limerick, University of College Cork, University of College Dublin,
Trinity College and the National University of Ireland. Non probabilistic sampling method
shall be considered while sampling the data of this proposal. Hence, it can be said that a
wide sampling group shall be considered in the data collection procedure of this proposal
so that the validity of the data is maintained.
Indicate clearly what the involvement of the sample group will be in the research
process, How their consent will be obtained, potential risks to them, Anonymity
of data being collected
The primary step of the data collection process is the creation of a questionnaire in
Google Forms and likert scale shall be used for the creation of the questionnaire. After the
questionnaire is created it shall be distributed among the participants using email. Hence,
an online survey shall be considered to involve the sample group in the data collection
procedure.
After the participants sends backs the answers in the same thread consents shall be
obtained from them. A separate consent form shall be created by the analyst of this
proposal which shall be provided to the participants before and after the conduction of the
online survey.
There will be no risks for the participants who will be taking part in this online survey
due to the transparency which shall be maintained by the analyst of this research.
Anonymity of data shall be maintained as the identity of the respondent shall not be
disclosed by the analyst of this proposal.
Indicate any potential risks to people using the product how you propose to
minimize these:
There are no risks involved in the data collection procedure for the participants who
shall be considered in this proposal. None of the details of the survey shall be accessed by
any outsider who is not involved in this proposal.
Ownership of data collected
9
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

The analyst of this proposal shall be held responsible for the ownership of the data
which shall be collected from the participants. Even Google forms which was used for the
creation of the questionnaires shall not be having the ownership of the data collected from
the participants. All the legal rights of the data shall be on the hands of the analyst of this
survey and data of this proposal shall be protected on the basis of the Data Protection Act
which was introduced in the Irish society in the year 2018. Hence the collected data from
the participants shall be kept secured from the data security threats.
10
which shall be collected from the participants. Even Google forms which was used for the
creation of the questionnaires shall not be having the ownership of the data collected from
the participants. All the legal rights of the data shall be on the hands of the analyst of this
survey and data of this proposal shall be protected on the basis of the Data Protection Act
which was introduced in the Irish society in the year 2018. Hence the collected data from
the participants shall be kept secured from the data security threats.
10
1 out of 10
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2025 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.



