cyber Attack presentation 2022
VerifiedAdded on 2022/08/13
|11
|796
|49
Presentation
AI Summary
Contribute Materials
Your contribution can guide someone’s learning journey. Share your
documents today.

C Y B E R S E C U R I T Y:
M E LT D O W N A N D
S P E C T R E
V U L N E R A B I L I T I E S
N A M E O F T H E S T U D E N T
N A M E O F T H E U N I V E R S I T Y
M E LT D O W N A N D
S P E C T R E
V U L N E R A B I L I T I E S
N A M E O F T H E S T U D E N T
N A M E O F T H E U N I V E R S I T Y
Secure Best Marks with AI Grader
Need help grading? Try our AI Grader for instant feedback on your assignments.

INTRODUCTION:
• Generally the cyber attacks aimed at changing,
accessing as well as destroying the data and
information that are confidential or interruption in the
normal business process [1]. A successful approach of
cyber security is comprising of various protection
layers that are spread across the data, systems and
networks.
• One of the significant and popular type of
vulnerabilities is meltdown and spectre which could be
extremely vulnerable for a business or organisation.
• Generally the cyber attacks aimed at changing,
accessing as well as destroying the data and
information that are confidential or interruption in the
normal business process [1]. A successful approach of
cyber security is comprising of various protection
layers that are spread across the data, systems and
networks.
• One of the significant and popular type of
vulnerabilities is meltdown and spectre which could be
extremely vulnerable for a business or organisation.

MELTDOWN AND SPECTRE
VULNERABILITIES:
• The vulnerabilities and threats of cyber security are
having responsibility for conduction attacks on the
network, data and systems for gaining any types of
unauthenticated and unauthorized accessibility,
damages, disruption as well as stealing the IT assets,
computer networks and intellectual properties [2].
• Meltdown and Spectre is one of the specific hardware
related vulnerabilities that affects IBM POWER
processor, ARM based micro processor and Intel x86
microprocessor. It can enable a rough process to read
all of the various systems at the time of discloser [3].
VULNERABILITIES:
• The vulnerabilities and threats of cyber security are
having responsibility for conduction attacks on the
network, data and systems for gaining any types of
unauthenticated and unauthorized accessibility,
damages, disruption as well as stealing the IT assets,
computer networks and intellectual properties [2].
• Meltdown and Spectre is one of the specific hardware
related vulnerabilities that affects IBM POWER
processor, ARM based micro processor and Intel x86
microprocessor. It can enable a rough process to read
all of the various systems at the time of discloser [3].
CONTD.
• Different procedure are there to help in protecting
the host computers and other associated devices
from Meltdown and Spectre vulnerabilities. The
patches of Meltdown are having responsibility for
producing performance loss [4].
• The patches of Spectre are being reported for the
purpose of reducing performance. Basically on the
old systems as well as in the 8th gen core
platforms [5].
• Different procedure are there to help in protecting
the host computers and other associated devices
from Meltdown and Spectre vulnerabilities. The
patches of Meltdown are having responsibility for
producing performance loss [4].
• The patches of Spectre are being reported for the
purpose of reducing performance. Basically on the
old systems as well as in the 8th gen core
platforms [5].
Secure Best Marks with AI Grader
Need help grading? Try our AI Grader for instant feedback on your assignments.
EXAMPLES OF
VULNERABILITIES:
• One of the popular most examples for meltdown
vulnerability is invalidating the cache for each of the
addresses in the User mode attack buffer as well as it
also read a byte from the variable kernel data. For this,
a side channel attack will occur and the user will be
unable to stop that [6].
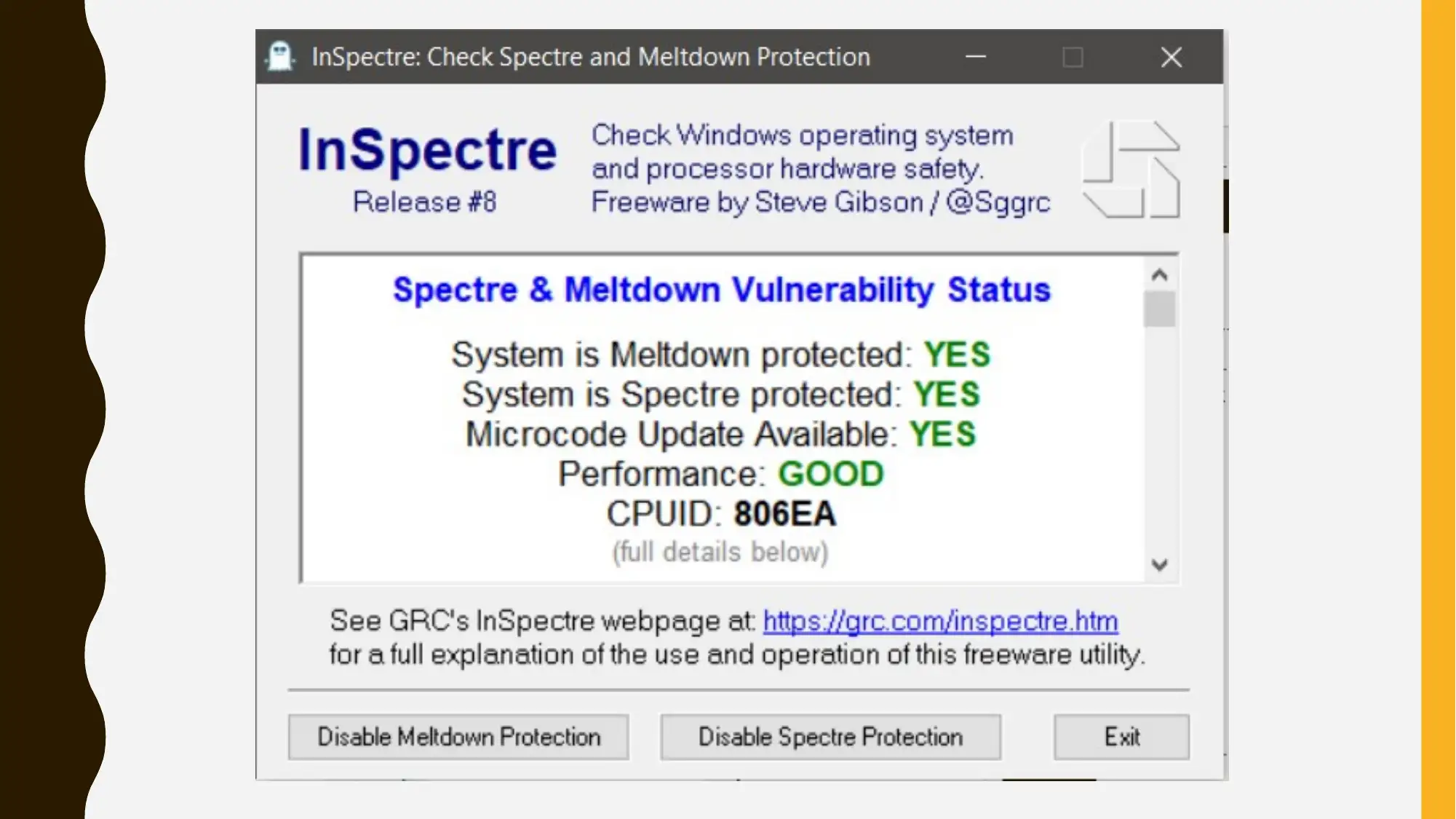
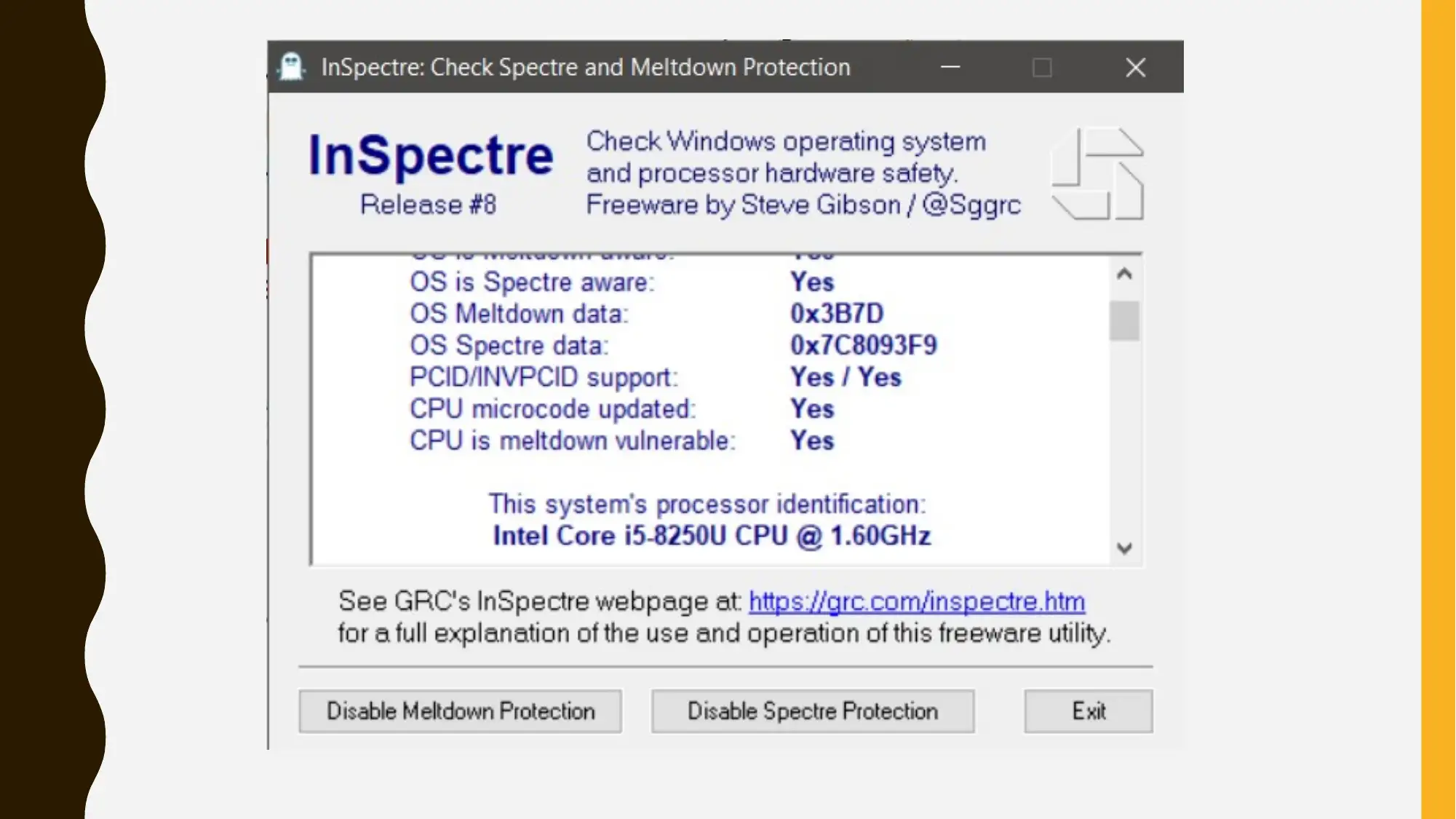
• Few of the important and significant software patches
can be introduced for minimizing the impacts of Spectre
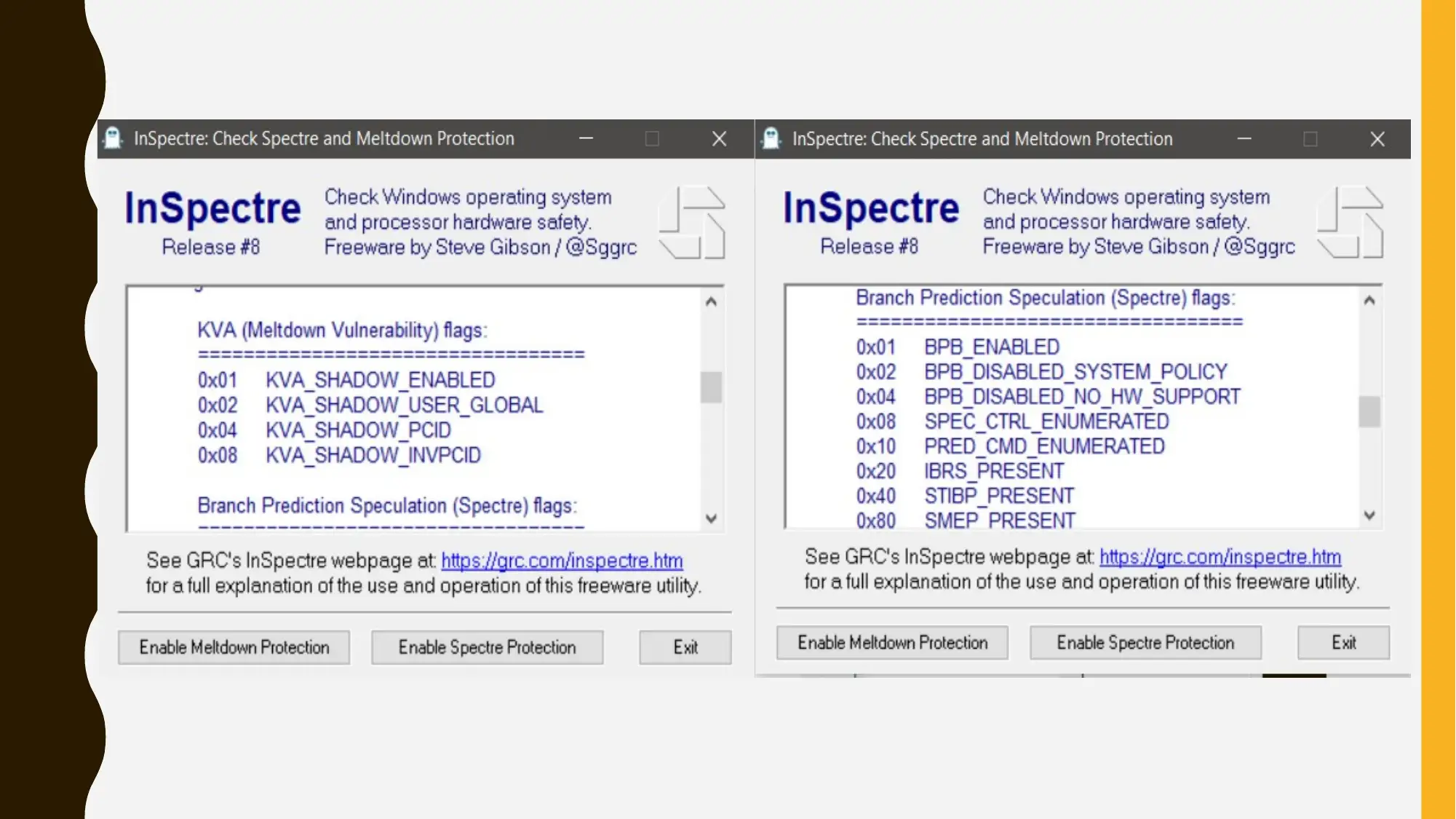
and Meltdown vulnerabilities. InSpectre is an
application can easily understand the examine the
capability of windows system for preventing Spectre
and meltdown attacks.
VULNERABILITIES:
• One of the popular most examples for meltdown
vulnerability is invalidating the cache for each of the
addresses in the User mode attack buffer as well as it
also read a byte from the variable kernel data. For this,
a side channel attack will occur and the user will be
unable to stop that [6].
• Few of the important and significant software patches
can be introduced for minimizing the impacts of Spectre
and Meltdown vulnerabilities. InSpectre is an
application can easily understand the examine the
capability of windows system for preventing Spectre
and meltdown attacks.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

CONCLUSION:
• The cyber security is basically the collection of various
technologies, procedures and practices which are
designed to protect the programs, networks and data
from any type of unauthorized damage, accessibility
and attack. This is extremely important as the
corporate and government sector remains secured and
safe without much complexity. Different types of DDoS
attacks, computerized viruses and data breaches are
involved in the cyber threats. The threats may occur
from the inside of an organisation by the trusted most
users as well as from the remote locations by several
unknown parties.
• The cyber security is basically the collection of various
technologies, procedures and practices which are
designed to protect the programs, networks and data
from any type of unauthorized damage, accessibility
and attack. This is extremely important as the
corporate and government sector remains secured and
safe without much complexity. Different types of DDoS
attacks, computerized viruses and data breaches are
involved in the cyber threats. The threats may occur
from the inside of an organisation by the trusted most
users as well as from the remote locations by several
unknown parties.

REFERENCES:
• [1] Meltdown and Spectre. [online]. Accessed from https://meltdownattack.com/ [Accessed on
10 January 2020]. 2020.
• [2] P., Kocher, J., Horn, A., Fogh, D., Genkin, D., Gruss, W., Haas, M., Hamburg, M., Lipp, S.,
Mangard, T. Prescher and M., Schwarz. Spectre attacks: Exploiting speculative execution.
In 2019 IEEE Symposium on Security and Privacy (SP) (pp. 1-19). IEEE. 2019, May.
• [3] M., Lipp, M., Schwarz, D., Gruss, T., Prescher, W., Haas, S., Mangard, P., Kocher, D., Genkin, Y.,
Yarom and M., Hamburg. Meltdown. arXiv preprint arXiv:1801.01207. 2018.
• [4] N.A., Simakov, M.D., Innus, M.D., Jones, J.P., White, S.M., Gallo, R.L., DeLeon and T.R., Furlani.
Effect of Meltdown and Spectre Patches on the Performance of HPC Applications. arXiv preprint
arXiv:1801.04329. 2018.
• [5] M., Lipp, M., Schwarz, D., Gruss, T., Prescher, W., Haas, A., Fogh, J., Horn, S., Mangard, P.,
Kocher, D., Genkin and Y., Yarom. Meltdown: Reading kernel memory from user space. In 27th
{USENIX} Security Symposium ({USENIX} Security 18) (pp. 973-990). 2018.
• [6] T.M., Conte, E.P., DeBenedictis, A., Mendelson and D. Milojičić. Rebooting computers to avoid
meltdown and spectre. Computer, 51(4), pp.74-77. 2018.
• [1] Meltdown and Spectre. [online]. Accessed from https://meltdownattack.com/ [Accessed on
10 January 2020]. 2020.
• [2] P., Kocher, J., Horn, A., Fogh, D., Genkin, D., Gruss, W., Haas, M., Hamburg, M., Lipp, S.,
Mangard, T. Prescher and M., Schwarz. Spectre attacks: Exploiting speculative execution.
In 2019 IEEE Symposium on Security and Privacy (SP) (pp. 1-19). IEEE. 2019, May.
• [3] M., Lipp, M., Schwarz, D., Gruss, T., Prescher, W., Haas, S., Mangard, P., Kocher, D., Genkin, Y.,
Yarom and M., Hamburg. Meltdown. arXiv preprint arXiv:1801.01207. 2018.
• [4] N.A., Simakov, M.D., Innus, M.D., Jones, J.P., White, S.M., Gallo, R.L., DeLeon and T.R., Furlani.
Effect of Meltdown and Spectre Patches on the Performance of HPC Applications. arXiv preprint
arXiv:1801.04329. 2018.
• [5] M., Lipp, M., Schwarz, D., Gruss, T., Prescher, W., Haas, A., Fogh, J., Horn, S., Mangard, P.,
Kocher, D., Genkin and Y., Yarom. Meltdown: Reading kernel memory from user space. In 27th
{USENIX} Security Symposium ({USENIX} Security 18) (pp. 973-990). 2018.
• [6] T.M., Conte, E.P., DeBenedictis, A., Mendelson and D. Milojičić. Rebooting computers to avoid
meltdown and spectre. Computer, 51(4), pp.74-77. 2018.
Secure Best Marks with AI Grader
Need help grading? Try our AI Grader for instant feedback on your assignments.

1 out of 11
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
© 2024 | Zucol Services PVT LTD | All rights reserved.




