CO4509 Computer Security: Memcrashed Vulnerability Analysis
VerifiedAdded on 2023/04/25
|14
|3281
|184
Report
AI Summary
This report delves into the Memcrashed vulnerability, a significant security threat involving the misuse of memcached, a distributed memory object caching system. It begins with an introduction to memcached and its functionality, followed by an explanation of how the vulnerability works, including reflection and amplification attacks exploiting UDP packets. The report then details the Memcrashed exploit, specifically the large-scale DDoS attack on GitHub in 2018, providing insights into the attack's mechanics and impact. It further explores various solutions and mitigation strategies, such as configuring network infrastructure, hardening memcached servers, disabling UDP support, increasing bandwidth, building redundancy, configuring network hardware, protecting DNS servers, and deploying memcrashed protection appliances. The report concludes with predictions on the likely future importance of memcrashed and the effectiveness of the proposed solutions in preventing similar attacks.

Running head: COMPUTER SECURITY
COMPUTER SECURITY
Name of Student
Name of University
Author’s Note
COMPUTER SECURITY
Name of Student
Name of University
Author’s Note
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

1COMPUTER SECURITY
Table of Contents
Introduction..........................................................................................................................2
Discussion............................................................................................................................2
How the vulnerability works...........................................................................................2
Description of memcrashed exploit.................................................................................4
Solution to the exploit......................................................................................................6
Conclusion...........................................................................................................................9
References..........................................................................................................................10
Table of Contents
Introduction..........................................................................................................................2
Discussion............................................................................................................................2
How the vulnerability works...........................................................................................2
Description of memcrashed exploit.................................................................................4
Solution to the exploit......................................................................................................6
Conclusion...........................................................................................................................9
References..........................................................................................................................10

2COMPUTER SECURITY
Introduction
Memcrashed can be defined as the process where memcached is installed and security is
initiated against the vulnerability of memcached. Memcached is a specific memory object system
for caching that is used in order to speed up various applications of dynamic web. It is an open
source and it has been designed for working with huge number of open connections
(TechCrunch. 2019). Vulnerability in memcached had been discovered in the month of February
of 2018 which allows the attackers to launch as well as execute powerful DDoS amplification
attacks. This vulnerability was a new one in the concept of execution of DDoS attack. This
assignment describes regarding various vulnerabilities caused by memcached along with various
examples, it further describes the memcrashed exploit that took place within GitHub in the year
2018. The report also provides various solutions to the memcrashed exploit. These points are
described in details in the discussion part of the report.
Discussion
How the vulnerability works
In case the memcached server is not configured in a proper manner it might cause
numerous vulnerabilities to occur within it. These attacks can prove to seriously devastating as
well as dangerous (Hyder and Lung 2018). The misconfigured servers might also be vulnerable
to reflection along with amplification denial if service attacks through the internet. The limit up
to which data can be stored usually depends on the configuration and necessities of users but
generally it is set to 1MB. Memcached server that is exposed in nature are vulnerable to spoofed
UDP packet that is sent to the port 11211 that would request the 1MB value multiple times, this
Introduction
Memcrashed can be defined as the process where memcached is installed and security is
initiated against the vulnerability of memcached. Memcached is a specific memory object system
for caching that is used in order to speed up various applications of dynamic web. It is an open
source and it has been designed for working with huge number of open connections
(TechCrunch. 2019). Vulnerability in memcached had been discovered in the month of February
of 2018 which allows the attackers to launch as well as execute powerful DDoS amplification
attacks. This vulnerability was a new one in the concept of execution of DDoS attack. This
assignment describes regarding various vulnerabilities caused by memcached along with various
examples, it further describes the memcrashed exploit that took place within GitHub in the year
2018. The report also provides various solutions to the memcrashed exploit. These points are
described in details in the discussion part of the report.
Discussion
How the vulnerability works
In case the memcached server is not configured in a proper manner it might cause
numerous vulnerabilities to occur within it. These attacks can prove to seriously devastating as
well as dangerous (Hyder and Lung 2018). The misconfigured servers might also be vulnerable
to reflection along with amplification denial if service attacks through the internet. The limit up
to which data can be stored usually depends on the configuration and necessities of users but
generally it is set to 1MB. Memcached server that is exposed in nature are vulnerable to spoofed
UDP packet that is sent to the port 11211 that would request the 1MB value multiple times, this
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

3COMPUTER SECURITY
results in a massive traffic as well as a huge amplification factor, hence the amplification attack
occurs.
Reflection attack is one more attack that is a part of memcached vulnerability. In this type
of attack the attacker does not forward the get request to the present client, he directly forwards it
to a specific host of the machines (Kharchenko, Kolisnyk and Piskachova 2018). As a response
to this request, the machines reflects the request to actual clients, this as a result dumps the
networks with the help of flooding these requests.
The memcached attack takes place using a specific procedure, when a server gets a
memcached get request; the requested values are collected by the server from the memory in
order to form a response. This is then sent in the internet with the help of an uninterrupted stream
of various UDP packets. Every packet is usually the length of around 1.400 bytes. After this the
attacker is allowed to insert various records in the open memcached server (Sanz 2018). The
memcached is generally allowed to utilize a limit of 1MB for every stored value, but in this case
a specific attacker can insert large values because any user is allowed to configure the memory
on the basis of their changes. The attacker is allowed to demand duplicate or multiple keys with
just one request. This attacker is allowed to utilize large values in the data store and then utilize
them for the attacks. Due to this even with a single megabyte that is stored, the attacker can use a
specific spoofed UDP packet request for requesting the 1MB of data (Xu, Liu and Ren 2015).
This data is sent for hundreds of times for every request over the memcached’s default. As per
Akamai, this results in a huge implication factor in which 203 byte request have chances to result
to the response of 100 MB of the reflected traffic.
results in a massive traffic as well as a huge amplification factor, hence the amplification attack
occurs.
Reflection attack is one more attack that is a part of memcached vulnerability. In this type
of attack the attacker does not forward the get request to the present client, he directly forwards it
to a specific host of the machines (Kharchenko, Kolisnyk and Piskachova 2018). As a response
to this request, the machines reflects the request to actual clients, this as a result dumps the
networks with the help of flooding these requests.
The memcached attack takes place using a specific procedure, when a server gets a
memcached get request; the requested values are collected by the server from the memory in
order to form a response. This is then sent in the internet with the help of an uninterrupted stream
of various UDP packets. Every packet is usually the length of around 1.400 bytes. After this the
attacker is allowed to insert various records in the open memcached server (Sanz 2018). The
memcached is generally allowed to utilize a limit of 1MB for every stored value, but in this case
a specific attacker can insert large values because any user is allowed to configure the memory
on the basis of their changes. The attacker is allowed to demand duplicate or multiple keys with
just one request. This attacker is allowed to utilize large values in the data store and then utilize
them for the attacks. Due to this even with a single megabyte that is stored, the attacker can use a
specific spoofed UDP packet request for requesting the 1MB of data (Xu, Liu and Ren 2015).
This data is sent for hundreds of times for every request over the memcached’s default. As per
Akamai, this results in a huge implication factor in which 203 byte request have chances to result
to the response of 100 MB of the reflected traffic.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

4COMPUTER SECURITY
Description of memcrashed exploit
GitHub had revealed that it faced the greatest known DDoS attack that had ever occurred
in history. Distributes Denial of Service (DDoS) is a specific attack which brings various
websites along with web-based services down with the help of bombarding them with a huge
amount of traffic. This traffic results in producing difficulties in handling the traffic faced by
their services as well as infrastructure (O’Hare 2018). This tactic is usually implemented for
forcing targets offline. GitHub had been a common target of the attack which resulted in tippling
the scales at 1.35Tbps at the peak; this attack was suspected to be carried out by the Chinese
government in the year 2015. In a specific blog post the organization described that attackers had
hijacked something named memcaching that is a distributed system and is well known for its
good performance as well as demand, this helps the organization in massively amplifying the
traffic volumes that had been fired at the GitHub (Dietzel, Smaragdakis and Wichtlhuber 2018).
For doing this, the attacker spoofed the IP address of GitHub’s along with taking control over the
memcached instances. These instances, according to GitHub were inadvertently accessible in the
internet for public use.
Description of memcrashed exploit
GitHub had revealed that it faced the greatest known DDoS attack that had ever occurred
in history. Distributes Denial of Service (DDoS) is a specific attack which brings various
websites along with web-based services down with the help of bombarding them with a huge
amount of traffic. This traffic results in producing difficulties in handling the traffic faced by
their services as well as infrastructure (O’Hare 2018). This tactic is usually implemented for
forcing targets offline. GitHub had been a common target of the attack which resulted in tippling
the scales at 1.35Tbps at the peak; this attack was suspected to be carried out by the Chinese
government in the year 2015. In a specific blog post the organization described that attackers had
hijacked something named memcaching that is a distributed system and is well known for its
good performance as well as demand, this helps the organization in massively amplifying the
traffic volumes that had been fired at the GitHub (Dietzel, Smaragdakis and Wichtlhuber 2018).
For doing this, the attacker spoofed the IP address of GitHub’s along with taking control over the
memcached instances. These instances, according to GitHub were inadvertently accessible in the
internet for public use.
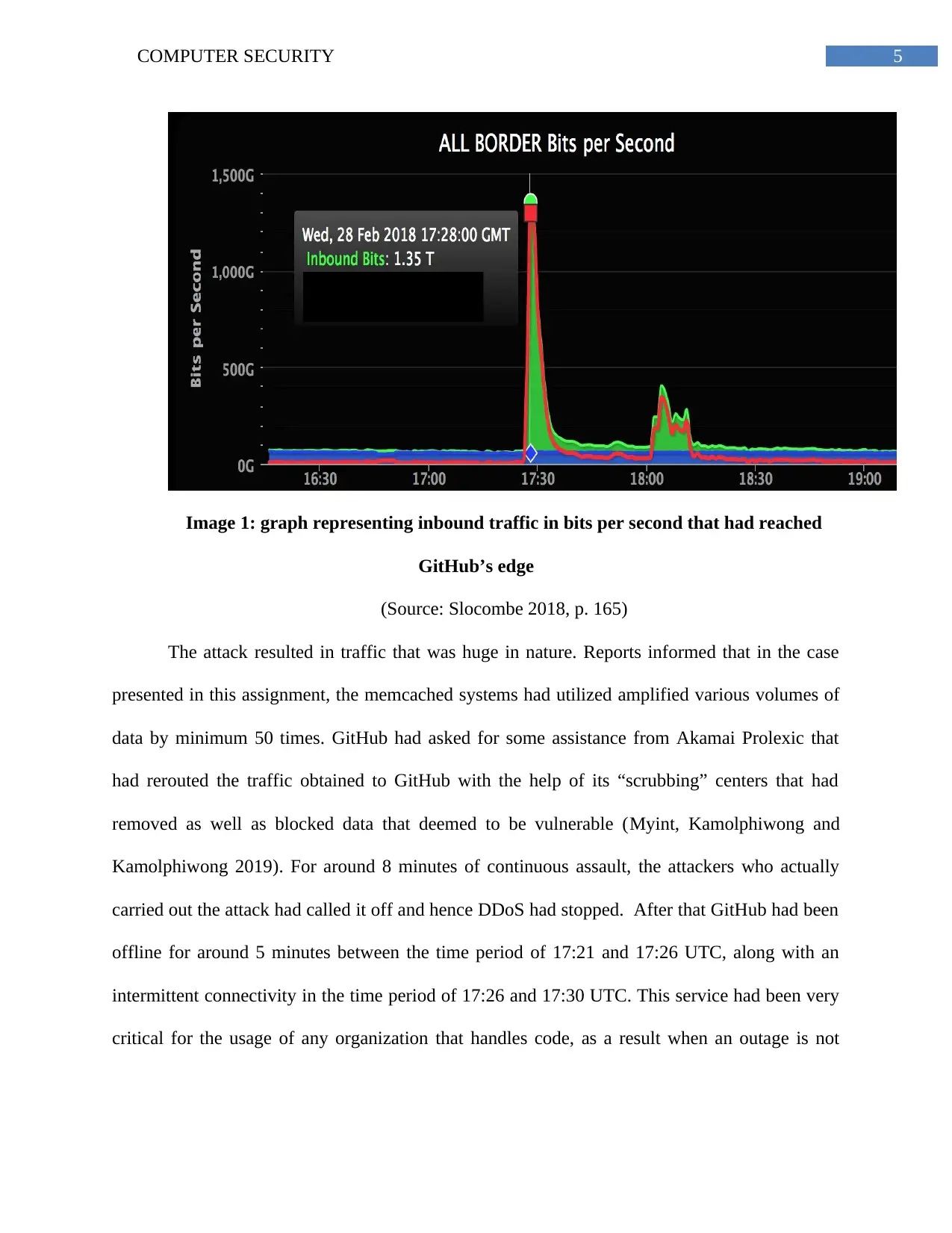
5COMPUTER SECURITY
Image 1: graph representing inbound traffic in bits per second that had reached
GitHub’s edge
(Source: Slocombe 2018, p. 165)
The attack resulted in traffic that was huge in nature. Reports informed that in the case
presented in this assignment, the memcached systems had utilized amplified various volumes of
data by minimum 50 times. GitHub had asked for some assistance from Akamai Prolexic that
had rerouted the traffic obtained to GitHub with the help of its “scrubbing” centers that had
removed as well as blocked data that deemed to be vulnerable (Myint, Kamolphiwong and
Kamolphiwong 2019). For around 8 minutes of continuous assault, the attackers who actually
carried out the attack had called it off and hence DDoS had stopped. After that GitHub had been
offline for around 5 minutes between the time period of 17:21 and 17:26 UTC, along with an
intermittent connectivity in the time period of 17:26 and 17:30 UTC. This service had been very
critical for the usage of any organization that handles code, as a result when an outage is not
Image 1: graph representing inbound traffic in bits per second that had reached
GitHub’s edge
(Source: Slocombe 2018, p. 165)
The attack resulted in traffic that was huge in nature. Reports informed that in the case
presented in this assignment, the memcached systems had utilized amplified various volumes of
data by minimum 50 times. GitHub had asked for some assistance from Akamai Prolexic that
had rerouted the traffic obtained to GitHub with the help of its “scrubbing” centers that had
removed as well as blocked data that deemed to be vulnerable (Myint, Kamolphiwong and
Kamolphiwong 2019). For around 8 minutes of continuous assault, the attackers who actually
carried out the attack had called it off and hence DDoS had stopped. After that GitHub had been
offline for around 5 minutes between the time period of 17:21 and 17:26 UTC, along with an
intermittent connectivity in the time period of 17:26 and 17:30 UTC. This service had been very
critical for the usage of any organization that handles code, as a result when an outage is not
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
6COMPUTER SECURITY
welcomed; the outcome received in the case, bodes very well and is very impressive. GitHub had
said that it analyses the attack and helps others to make sure that it is actually suitably defended.
GitHub had explained that in order to make its edge infrastructure even more resilient for
current as well as the future conditions of internet and it is lesser dependent on the involvement
of humans (Harrou, Bouyeddou and Sun 2018). This needs better automated intervention
according to the GitHub. The organization has claimed to investigate their use of monitoring
infrastructure for the automate enabling of mitigation providers of DDoS, this had been said to
continue measuring their response times to various incidents which aims in reducing mean time
for recovery. The organization had claimed in continuing to expand their edge network as well as
strive to identify as well as mitigate the new attack vendors before they even affect their
workflow on their website.
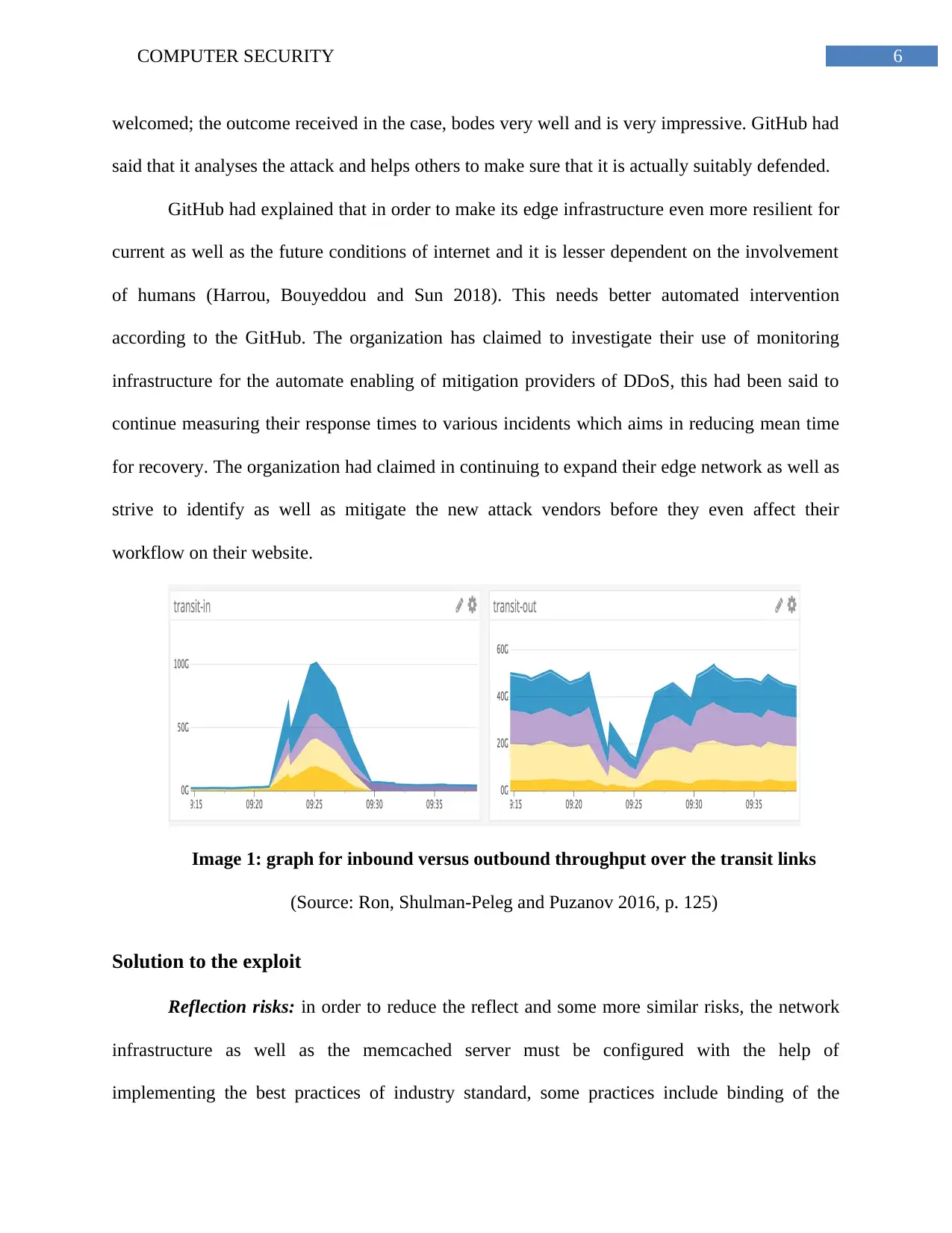
Image 1: graph for inbound versus outbound throughput over the transit links
(Source: Ron, Shulman-Peleg and Puzanov 2016, p. 125)
Solution to the exploit
Reflection risks: in order to reduce the reflect and some more similar risks, the network
infrastructure as well as the memcached server must be configured with the help of
implementing the best practices of industry standard, some practices include binding of the
welcomed; the outcome received in the case, bodes very well and is very impressive. GitHub had
said that it analyses the attack and helps others to make sure that it is actually suitably defended.
GitHub had explained that in order to make its edge infrastructure even more resilient for
current as well as the future conditions of internet and it is lesser dependent on the involvement
of humans (Harrou, Bouyeddou and Sun 2018). This needs better automated intervention
according to the GitHub. The organization has claimed to investigate their use of monitoring
infrastructure for the automate enabling of mitigation providers of DDoS, this had been said to
continue measuring their response times to various incidents which aims in reducing mean time
for recovery. The organization had claimed in continuing to expand their edge network as well as
strive to identify as well as mitigate the new attack vendors before they even affect their
workflow on their website.
Image 1: graph for inbound versus outbound throughput over the transit links
(Source: Ron, Shulman-Peleg and Puzanov 2016, p. 125)
Solution to the exploit
Reflection risks: in order to reduce the reflect and some more similar risks, the network
infrastructure as well as the memcached server must be configured with the help of
implementing the best practices of industry standard, some practices include binding of the
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

7COMPUTER SECURITY
memcached to a specific source IP (Tatar, Konoth and Athanasopoulos 2018). If the protection
that is taken while running the memcached services, the risks of addition, updating and deletion
would automatically decrease.
Hardening of memcached: In case an organization is running memcached on the basis of
SANS the organization should harden their memcached server by following few steps, these
steps are as follows
Step 1: first open or etc or memcached.conf in a specific text editor
Step 2: then locate the m parameter
Step 3: after locating the parameter, change the value to minimum 1GB
Step 4: then locate the l parameter
Step 5: then change the value to at least 127.0.01 or a local host
Step 6: after the value is set, save the changes to the memcached.conf and then exit the
text editor
Step 7: restart the memcached
Disable UDP support: in case an organization is running memchached, they must disable
UDP support if they are not utilizing it presently. In case it is being used by a specific developer
and the UDP is being used, they must respond with a strict packet size then the request. In case
this is not followed, the protocol has high chances to get abused. An organization must also close
off the port 11211 (White, Fisch and Pooch 2017). They must also look into the mitigation
services of DDoS from various companies like Akamai, Incapsula and CloudFlare.
Buying more bandwidth: there are numerous that can be utilized in order to prevent
memcrashed attack, the basic step that can be undertaken in order to prevent this attack include
ensuring that the organization has enough bandwidth for handling spikes in the traffic which
memcached to a specific source IP (Tatar, Konoth and Athanasopoulos 2018). If the protection
that is taken while running the memcached services, the risks of addition, updating and deletion
would automatically decrease.
Hardening of memcached: In case an organization is running memcached on the basis of
SANS the organization should harden their memcached server by following few steps, these
steps are as follows
Step 1: first open or etc or memcached.conf in a specific text editor
Step 2: then locate the m parameter
Step 3: after locating the parameter, change the value to minimum 1GB
Step 4: then locate the l parameter
Step 5: then change the value to at least 127.0.01 or a local host
Step 6: after the value is set, save the changes to the memcached.conf and then exit the
text editor
Step 7: restart the memcached
Disable UDP support: in case an organization is running memchached, they must disable
UDP support if they are not utilizing it presently. In case it is being used by a specific developer
and the UDP is being used, they must respond with a strict packet size then the request. In case
this is not followed, the protocol has high chances to get abused. An organization must also close
off the port 11211 (White, Fisch and Pooch 2017). They must also look into the mitigation
services of DDoS from various companies like Akamai, Incapsula and CloudFlare.
Buying more bandwidth: there are numerous that can be utilized in order to prevent
memcrashed attack, the basic step that can be undertaken in order to prevent this attack include
ensuring that the organization has enough bandwidth for handling spikes in the traffic which

8COMPUTER SECURITY
might be caused by any sort of malicious activity. Previously preventing these attacks was
possible by just making sure that the organization has higher level of bandwidth at their disposal
than any other attacker would have (Conklin, White and Cothren 2015). Along with the rise of
application attacks, this does not stay practical any more. Moreover buying bandwidth raises the
chances that the attackers would need to overcome before they are able to launch an attack that is
successful in nature.
Building redundancy in their infrastructure: in order to make it difficult for an attacker
to carry out a successful attack against their servers, the organization must ensure that they
spread themselves across numerous data centers along with a very good system for load
balancing. This would help them to distribute traffic between them (Stallings 2017). If possible
the organization must make these data centers to various countries or in various regions of a
specific country. In order to make this strategy more effective, it is important to make sure that
various data centers are interconnected to various networks and it must be considered that there
are no loopholes or a single point of failure in the network. If the organization distributes their
server topographically and geographically, it would be difficult for an attacker to launch a
successful attack in more than one portion of a server and leaving rest of servers without
affecting and taking some extra amount of traffic that those servers would be able to handle.
Configuring network hardware against the attack: there are numerous hardware
configuration changes that are simple in nature and can be utilized by the organization in order to
prevent memcrashed attack (Peltier 2016). For example, if the organization configures their
router or firewall to drop the incoming ICMP packets and block the DNS response that arrives
from external sourcesof the network, it would helpful for the organization to prevent various
DNS as well as memcrashed attacks.
might be caused by any sort of malicious activity. Previously preventing these attacks was
possible by just making sure that the organization has higher level of bandwidth at their disposal
than any other attacker would have (Conklin, White and Cothren 2015). Along with the rise of
application attacks, this does not stay practical any more. Moreover buying bandwidth raises the
chances that the attackers would need to overcome before they are able to launch an attack that is
successful in nature.
Building redundancy in their infrastructure: in order to make it difficult for an attacker
to carry out a successful attack against their servers, the organization must ensure that they
spread themselves across numerous data centers along with a very good system for load
balancing. This would help them to distribute traffic between them (Stallings 2017). If possible
the organization must make these data centers to various countries or in various regions of a
specific country. In order to make this strategy more effective, it is important to make sure that
various data centers are interconnected to various networks and it must be considered that there
are no loopholes or a single point of failure in the network. If the organization distributes their
server topographically and geographically, it would be difficult for an attacker to launch a
successful attack in more than one portion of a server and leaving rest of servers without
affecting and taking some extra amount of traffic that those servers would be able to handle.
Configuring network hardware against the attack: there are numerous hardware
configuration changes that are simple in nature and can be utilized by the organization in order to
prevent memcrashed attack (Peltier 2016). For example, if the organization configures their
router or firewall to drop the incoming ICMP packets and block the DNS response that arrives
from external sourcesof the network, it would helpful for the organization to prevent various
DNS as well as memcrashed attacks.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

9COMPUTER SECURITY
Protecting DNS servers: a malicious user might bring the web servers of an organization
offline by DDoSing their DNS servers. For this reason, it is vital that their DNS servers have a
particular amount of redundancy, and they are placed in various data centers behind the load
balancers (Ortmeier 2017). Moving to a cloud-based DN provider would be a better solution for
this which would be able to offer them with high bandwidth as well as numerous points of
presence in the data centers all over the world. The services have been designed by considering
the prevention of Memcrashed attacks.
Deploying a memcrashed protection appliance: numerous security vendors like
NetScout Arbor, CheckPoint, Radware, Cisco and Fortinet offer various appliances which
usually block the network firewall. They are designed for blocking these attacks before they
affect the network (Egelman and Peer 2015). This is done using various techniques such as
carrying out a traffic behavioral base lining and then blocks various abnormal traffic. The traffic
is blocked on the basis of attack signatures that have already been known. The main drawback of
this particular approach is that these appliances are very limited in amount of the traffic
throughput that can be handled by them. Various high-end appliances might be able to inspect
the traffic that comes at a specific rate of around 80 Gbps, or similar to that (Cullen 2018).
Nowadays the memcrashed attack is of a magnitude higher than 80 Gbps, hence various
appliances are generally used to prevent the attack.
Conclusion
From the report, it can be concluded that memcrashed works with the help of exploiting
the program of memcached. The Memcached is a specific open source, distributed, high-
performance and an object-caching system. This is commonly utilized by various social
Protecting DNS servers: a malicious user might bring the web servers of an organization
offline by DDoSing their DNS servers. For this reason, it is vital that their DNS servers have a
particular amount of redundancy, and they are placed in various data centers behind the load
balancers (Ortmeier 2017). Moving to a cloud-based DN provider would be a better solution for
this which would be able to offer them with high bandwidth as well as numerous points of
presence in the data centers all over the world. The services have been designed by considering
the prevention of Memcrashed attacks.
Deploying a memcrashed protection appliance: numerous security vendors like
NetScout Arbor, CheckPoint, Radware, Cisco and Fortinet offer various appliances which
usually block the network firewall. They are designed for blocking these attacks before they
affect the network (Egelman and Peer 2015). This is done using various techniques such as
carrying out a traffic behavioral base lining and then blocks various abnormal traffic. The traffic
is blocked on the basis of attack signatures that have already been known. The main drawback of
this particular approach is that these appliances are very limited in amount of the traffic
throughput that can be handled by them. Various high-end appliances might be able to inspect
the traffic that comes at a specific rate of around 80 Gbps, or similar to that (Cullen 2018).
Nowadays the memcrashed attack is of a magnitude higher than 80 Gbps, hence various
appliances are generally used to prevent the attack.
Conclusion
From the report, it can be concluded that memcrashed works with the help of exploiting
the program of memcached. The Memcached is a specific open source, distributed, high-
performance and an object-caching system. This is commonly utilized by various social
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

10COMPUTER SECURITY
networks like Facebook as well as its creator LiveJournal as a particular in-memory key-value
store for the small groups that are of the arbitrary data. It can be defined as a program which
enables them to take care of their huge amount of data. It can also be used in order to cache the
session data of the web server for speeding up the sites and this causes trouble. Many a times
incompetent system administrators expose the memcaches enabled servers in the internet.
Memcached must not be available on the internet; it does not have any authentication so it is
very easy to use. This assignment describes regarding the memcached attack that took place
within GitHub. It further discusses regarding various vulnerabilities caused due to attack, it also
discusses about the threats imposed by the attack and ways by which the threats can be
mitigated. The analysis of the likely future importance as well as effectiveness of the
memcrashed is also described. All the mentioned points have been discussed in details in the
discussion part of the report.
networks like Facebook as well as its creator LiveJournal as a particular in-memory key-value
store for the small groups that are of the arbitrary data. It can be defined as a program which
enables them to take care of their huge amount of data. It can also be used in order to cache the
session data of the web server for speeding up the sites and this causes trouble. Many a times
incompetent system administrators expose the memcaches enabled servers in the internet.
Memcached must not be available on the internet; it does not have any authentication so it is
very easy to use. This assignment describes regarding the memcached attack that took place
within GitHub. It further discusses regarding various vulnerabilities caused due to attack, it also
discusses about the threats imposed by the attack and ways by which the threats can be
mitigated. The analysis of the likely future importance as well as effectiveness of the
memcrashed is also described. All the mentioned points have been discussed in details in the
discussion part of the report.

11COMPUTER SECURITY
References
Conklin, W.A., White, G., Cothren, C., Davis, R. and Williams, D., 2015. Principles of computer
security. McGraw-Hill Education Group.
Cullen, D.T., 2018. Building a Computer Security Incident Response Team: Required Skills and
Characteristics (Doctoral dissertation, Northcentral University).
Dietzel, C., Smaragdakis, G., Wichtlhuber, M. and Feldmann, A., 2018, December. Stellar:
network attack mitigation using advanced blackholing. In Proceedings of the 14th International
Conference on emerging Networking EXperiments and Technologies (pp. 152-164). ACM.
Egelman, S. and Peer, E., 2015, April. Scaling the security wall: Developing a security behavior
intentions scale (sebis). In Proceedings of the 33rd Annual ACM Conference on Human Factors
in Computing Systems (pp. 2873-2882). ACM.
Harrou, F., Bouyeddou, B., Sun, Y. and Kadri, B., 2018, November. A Method to Detect DOS
and DDOS Attacks based on Generalized Likelihood Ratio Test. In 2018 International
Conference on Applied Smart Systems (ICASS)(pp. 1-6). IEEE.
Hyder, H.K. and Lung, C.H., 2018, December. Closed-Loop DDoS Mitigation System in
Software Defined Networks. In 2018 IEEE Conference on Dependable and Secure Computing
(DSC) (pp. 1-6). IEEE.
Kharchenko, V., Kolisnyk, M. and Piskachova, I., 2018, May. The research of the smart office
availability model considering patches on the router firewall software. In 2018 IEEE 9th
International Conference on Dependable Systems, Services and Technologies (DESSERT) (pp.
169-174). IEEE.
References
Conklin, W.A., White, G., Cothren, C., Davis, R. and Williams, D., 2015. Principles of computer
security. McGraw-Hill Education Group.
Cullen, D.T., 2018. Building a Computer Security Incident Response Team: Required Skills and
Characteristics (Doctoral dissertation, Northcentral University).
Dietzel, C., Smaragdakis, G., Wichtlhuber, M. and Feldmann, A., 2018, December. Stellar:
network attack mitigation using advanced blackholing. In Proceedings of the 14th International
Conference on emerging Networking EXperiments and Technologies (pp. 152-164). ACM.
Egelman, S. and Peer, E., 2015, April. Scaling the security wall: Developing a security behavior
intentions scale (sebis). In Proceedings of the 33rd Annual ACM Conference on Human Factors
in Computing Systems (pp. 2873-2882). ACM.
Harrou, F., Bouyeddou, B., Sun, Y. and Kadri, B., 2018, November. A Method to Detect DOS
and DDOS Attacks based on Generalized Likelihood Ratio Test. In 2018 International
Conference on Applied Smart Systems (ICASS)(pp. 1-6). IEEE.
Hyder, H.K. and Lung, C.H., 2018, December. Closed-Loop DDoS Mitigation System in
Software Defined Networks. In 2018 IEEE Conference on Dependable and Secure Computing
(DSC) (pp. 1-6). IEEE.
Kharchenko, V., Kolisnyk, M. and Piskachova, I., 2018, May. The research of the smart office
availability model considering patches on the router firewall software. In 2018 IEEE 9th
International Conference on Dependable Systems, Services and Technologies (DESSERT) (pp.
169-174). IEEE.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
1 out of 14
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.



