Information Security Policy and Employee Adherence
VerifiedAdded on 2021/04/21
|91
|25023
|43
AI Summary
This assignment requires a comprehensive analysis of information security policy and its implications on employee behavior. It involves researching various studies, theories, and methodologies related to information security policy enforcement and employee compliance. The assignment also explores the significance of information security policies in modern workplaces and their impact on organizational performance.
Contribute Materials
Your contribution can guide someone’s learning journey. Share your
documents today.

Running head: MINIMIZING THE AFFECT OF HUMAN BEHAVIOUR RISKS RELATED
TO INFORMATION SECURITY
Minimizing the affect of human behaviour risks related to information security
Name of the Student:
Name of the University:
TO INFORMATION SECURITY
Minimizing the affect of human behaviour risks related to information security
Name of the Student:
Name of the University:
Secure Best Marks with AI Grader
Need help grading? Try our AI Grader for instant feedback on your assignments.

1
MINIMIZING THE AFFECT OF HUMAN BEHAVIOUR RISKS RELATED TO
INFORMATION SECURITY
Abstract
Into the information security practices, there are various numerous security breaches which are
caused due to human errors. One of the main contributions into this particular research study is
to make changes into holistic management of the information security for establishment of the
information security cultures. There are lack of research is done on role as well as impact of the
organizational cultural dimensions on the information security. The human factors are
uncontrollable forces which interact with the technological elements to secure of the information
system. The human errors occur due to inadequate skills, lack of information security awareness,
intentional as well as unintentional errors to pose the risks towards the information security.
MINIMIZING THE AFFECT OF HUMAN BEHAVIOUR RISKS RELATED TO
INFORMATION SECURITY
Abstract
Into the information security practices, there are various numerous security breaches which are
caused due to human errors. One of the main contributions into this particular research study is
to make changes into holistic management of the information security for establishment of the
information security cultures. There are lack of research is done on role as well as impact of the
organizational cultural dimensions on the information security. The human factors are
uncontrollable forces which interact with the technological elements to secure of the information
system. The human errors occur due to inadequate skills, lack of information security awareness,
intentional as well as unintentional errors to pose the risks towards the information security.

2
MINIMIZING THE AFFECT OF HUMAN BEHAVIOUR RISKS RELATED TO
INFORMATION SECURITY
Table of Contents
Chapter 1: Developing the research agenda/Introduction...............................................................8
1.1 Introduction............................................................................................................................8
1.2 Research Background..........................................................................................................10
1.2.1 Human factors for information security.......................................................................11
1.3 Research problem statement................................................................................................13
1.4 Research questions...............................................................................................................14
1.5 Research aim and objectives................................................................................................14
1.6 Research scope.....................................................................................................................15
1.7 Research hypothesis.............................................................................................................16
1.8 Importance of the research...................................................................................................17
1.9 Research plan.......................................................................................................................18
1.10 Thesis structure..................................................................................................................18
1.11 Research novelty and contribution....................................................................................20
1.12 Summary............................................................................................................................22
Chapter 2: Development of theoretical background/ Literature review on human behaviour risks
related to information security.......................................................................................................23
2.1 Introduction..........................................................................................................................23
2.2 What is Information Security...............................................................................................23
MINIMIZING THE AFFECT OF HUMAN BEHAVIOUR RISKS RELATED TO
INFORMATION SECURITY
Table of Contents
Chapter 1: Developing the research agenda/Introduction...............................................................8
1.1 Introduction............................................................................................................................8
1.2 Research Background..........................................................................................................10
1.2.1 Human factors for information security.......................................................................11
1.3 Research problem statement................................................................................................13
1.4 Research questions...............................................................................................................14
1.5 Research aim and objectives................................................................................................14
1.6 Research scope.....................................................................................................................15
1.7 Research hypothesis.............................................................................................................16
1.8 Importance of the research...................................................................................................17
1.9 Research plan.......................................................................................................................18
1.10 Thesis structure..................................................................................................................18
1.11 Research novelty and contribution....................................................................................20
1.12 Summary............................................................................................................................22
Chapter 2: Development of theoretical background/ Literature review on human behaviour risks
related to information security.......................................................................................................23
2.1 Introduction..........................................................................................................................23
2.2 What is Information Security...............................................................................................23

3
MINIMIZING THE AFFECT OF HUMAN BEHAVIOUR RISKS RELATED TO
INFORMATION SECURITY
2.3 Background to Information Security...................................................................................24
2.4 Information Security Principles...........................................................................................25
2.5 Relevant Theories and Methods..........................................................................................26
2.6 Threats to Information Security: Human Behavior a constant risk.....................................33
2.6.1 Threats with information security.................................................................................33
2.6.2 Human Behavior as aspect of information security......................................................35
2.7 Information Security Standards and Guidelines..................................................................36
2.7.1 COBIT..........................................................................................................................36
2.8 Human factors have implications to end user’s behavior....................................................38
2.9 Human behaviour risks related to information security......................................................42
2.10 Organization Information Security Culture.......................................................................43
2.10.1 Organizational culture................................................................................................43
2.10.2 Information security culture.......................................................................................44
2.10.3 Cultural Change..........................................................................................................45
2.10.4 Cultural Impact on Human Behavior..........................................................................45
2.11 Information Security Policy...............................................................................................46
2.11.1 What is an Information Security Policy......................................................................46
2.11.2 The Needs for Information Security Policy................................................................47
2.11.3 Compliance with information security policy............................................................48
2.12 Human Computer Interaction (HCI) and Behaviors Change............................................49
MINIMIZING THE AFFECT OF HUMAN BEHAVIOUR RISKS RELATED TO
INFORMATION SECURITY
2.3 Background to Information Security...................................................................................24
2.4 Information Security Principles...........................................................................................25
2.5 Relevant Theories and Methods..........................................................................................26
2.6 Threats to Information Security: Human Behavior a constant risk.....................................33
2.6.1 Threats with information security.................................................................................33
2.6.2 Human Behavior as aspect of information security......................................................35
2.7 Information Security Standards and Guidelines..................................................................36
2.7.1 COBIT..........................................................................................................................36
2.8 Human factors have implications to end user’s behavior....................................................38
2.9 Human behaviour risks related to information security......................................................42
2.10 Organization Information Security Culture.......................................................................43
2.10.1 Organizational culture................................................................................................43
2.10.2 Information security culture.......................................................................................44
2.10.3 Cultural Change..........................................................................................................45
2.10.4 Cultural Impact on Human Behavior..........................................................................45
2.11 Information Security Policy...............................................................................................46
2.11.1 What is an Information Security Policy......................................................................46
2.11.2 The Needs for Information Security Policy................................................................47
2.11.3 Compliance with information security policy............................................................48
2.12 Human Computer Interaction (HCI) and Behaviors Change............................................49
Secure Best Marks with AI Grader
Need help grading? Try our AI Grader for instant feedback on your assignments.

4
MINIMIZING THE AFFECT OF HUMAN BEHAVIOUR RISKS RELATED TO
INFORMATION SECURITY
2.13 Insider Threats Behavior....................................................................................................51
2.14 Modeling human behavior to anticipate of insider attacks................................................52
2.15 Intrinsic and Extrinsic Motivators in Information Security Behavior...............................54
2.16 Insider Misuse and Incident Responses.............................................................................57
Chapter 3: Research Conceptual Framework................................................................................59
3.1 Introduction..........................................................................................................................59
3.2 Conceptual framework of the research study......................................................................59
3.3 Internal threat into Small and medium size enterprise........................................................61
3.4 Human’s behavior and information security system...........................................................63
3.5 Information security countermeasures.................................................................................64
3.6 Human security culture........................................................................................................66
3.7 Human behavior theory.......................................................................................................69
3.8 Summary..............................................................................................................................70
Chapter 4: Research Methodology................................................................................................72
4.1 Introduction..........................................................................................................................72
4.2 Research philosophy............................................................................................................72
4.3 Research approach...............................................................................................................74
4.4 Research design...................................................................................................................75
4.5 Data collection process........................................................................................................76
4.5.1 Data sources..................................................................................................................76
MINIMIZING THE AFFECT OF HUMAN BEHAVIOUR RISKS RELATED TO
INFORMATION SECURITY
2.13 Insider Threats Behavior....................................................................................................51
2.14 Modeling human behavior to anticipate of insider attacks................................................52
2.15 Intrinsic and Extrinsic Motivators in Information Security Behavior...............................54
2.16 Insider Misuse and Incident Responses.............................................................................57
Chapter 3: Research Conceptual Framework................................................................................59
3.1 Introduction..........................................................................................................................59
3.2 Conceptual framework of the research study......................................................................59
3.3 Internal threat into Small and medium size enterprise........................................................61
3.4 Human’s behavior and information security system...........................................................63
3.5 Information security countermeasures.................................................................................64
3.6 Human security culture........................................................................................................66
3.7 Human behavior theory.......................................................................................................69
3.8 Summary..............................................................................................................................70
Chapter 4: Research Methodology................................................................................................72
4.1 Introduction..........................................................................................................................72
4.2 Research philosophy............................................................................................................72
4.3 Research approach...............................................................................................................74
4.4 Research design...................................................................................................................75
4.5 Data collection process........................................................................................................76
4.5.1 Data sources..................................................................................................................76

5
MINIMIZING THE AFFECT OF HUMAN BEHAVIOUR RISKS RELATED TO
INFORMATION SECURITY
4.5.2 Data techniques.............................................................................................................77
4.6 Sampling method.................................................................................................................78
4.7 Ethical considerations..........................................................................................................79
4.8 Limitations of the research study.........................................................................................79
4.9 Time horizons......................................................................................................................81
4.10 Summary............................................................................................................................82
References......................................................................................................................................84
MINIMIZING THE AFFECT OF HUMAN BEHAVIOUR RISKS RELATED TO
INFORMATION SECURITY
4.5.2 Data techniques.............................................................................................................77
4.6 Sampling method.................................................................................................................78
4.7 Ethical considerations..........................................................................................................79
4.8 Limitations of the research study.........................................................................................79
4.9 Time horizons......................................................................................................................81
4.10 Summary............................................................................................................................82
References......................................................................................................................................84

6
MINIMIZING THE AFFECT OF HUMAN BEHAVIOUR RISKS RELATED TO
INFORMATION SECURITY
Table of Figures
Figure 1.1: Research plan process.................................................................................................18
Figure 2.1: Theory of reasoned action...........................................................................................29
Figure 2.2: Theory of planned behavior........................................................................................30
Figure 2.3: Protection motivation theory.......................................................................................31
Figure 2.4: General Deterrence Theory.........................................................................................32
Figure 2.5: Technology acceptance theory....................................................................................33
Figure 3.1: Conceptual framework of research study....................................................................60
Figure 3.2: Relations among threat countermeasures and human behavior..................................62
MINIMIZING THE AFFECT OF HUMAN BEHAVIOUR RISKS RELATED TO
INFORMATION SECURITY
Table of Figures
Figure 1.1: Research plan process.................................................................................................18
Figure 2.1: Theory of reasoned action...........................................................................................29
Figure 2.2: Theory of planned behavior........................................................................................30
Figure 2.3: Protection motivation theory.......................................................................................31
Figure 2.4: General Deterrence Theory.........................................................................................32
Figure 2.5: Technology acceptance theory....................................................................................33
Figure 3.1: Conceptual framework of research study....................................................................60
Figure 3.2: Relations among threat countermeasures and human behavior..................................62
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

7
MINIMIZING THE AFFECT OF HUMAN BEHAVIOUR RISKS RELATED TO
INFORMATION SECURITY
Table of Tables
Table 2.1: Intrinsic and Extrinsic Motivators in Information Security Behavior..........................56
Table 3.1: Human security culture.................................................................................................68
MINIMIZING THE AFFECT OF HUMAN BEHAVIOUR RISKS RELATED TO
INFORMATION SECURITY
Table of Tables
Table 2.1: Intrinsic and Extrinsic Motivators in Information Security Behavior..........................56
Table 3.1: Human security culture.................................................................................................68

8
MINIMIZING THE AFFECT OF HUMAN BEHAVIOUR RISKS RELATED TO
INFORMATION SECURITY
Chapter 1: Developing the research agenda/Introduction
1.1 Introduction
The experts of information security should consider human information security behavior
as well as technology in aspects of the information security for secure environment. According to
Malekian, Hayati and Aarts (2017), the users are delayed complying with password change as
they are considered to change unnecessary interruption. Safa, Von Solms and Furnell (2016)
noted that the employees are failed to perform security behaviors which put in place for
protecting the information assets. Kim, Yang and Park (2014) pointed that the users can
understand severe consequences of breach into password protection but it is not changing
attitudes as well as resistance behavior towards implementation of the information security
policy. Kampas et al. (2016) demonstrated that the awareness of information security provide
significant effects on information security attitude towards the positive behavior. Pearlson,
Saunders and Galletta (2016) highlighted importance of the information security awareness to
influence security changes behaviors among the employees. In this research study, the
participants are viewed people’s management as strategy to minimize the threats of information
security on the business performance.
Managing of the information security is a challenge for the IT organizations those use of
information technology as part of the business. Sheeran and Rivis (2017) illustrated that human
work into mitigating the information security issues fall under four categories such as individual,
customer, team and management. The human factors are uncontrollable forces which interact
with the technological elements to secure of the information system. The human errors occur due
to inadequate skills, lack of information security awareness, intentional as well as unintentional
MINIMIZING THE AFFECT OF HUMAN BEHAVIOUR RISKS RELATED TO
INFORMATION SECURITY
Chapter 1: Developing the research agenda/Introduction
1.1 Introduction
The experts of information security should consider human information security behavior
as well as technology in aspects of the information security for secure environment. According to
Malekian, Hayati and Aarts (2017), the users are delayed complying with password change as
they are considered to change unnecessary interruption. Safa, Von Solms and Furnell (2016)
noted that the employees are failed to perform security behaviors which put in place for
protecting the information assets. Kim, Yang and Park (2014) pointed that the users can
understand severe consequences of breach into password protection but it is not changing
attitudes as well as resistance behavior towards implementation of the information security
policy. Kampas et al. (2016) demonstrated that the awareness of information security provide
significant effects on information security attitude towards the positive behavior. Pearlson,
Saunders and Galletta (2016) highlighted importance of the information security awareness to
influence security changes behaviors among the employees. In this research study, the
participants are viewed people’s management as strategy to minimize the threats of information
security on the business performance.
Managing of the information security is a challenge for the IT organizations those use of
information technology as part of the business. Sheeran and Rivis (2017) illustrated that human
work into mitigating the information security issues fall under four categories such as individual,
customer, team and management. The human factors are uncontrollable forces which interact
with the technological elements to secure of the information system. The human errors occur due
to inadequate skills, lack of information security awareness, intentional as well as unintentional

9
MINIMIZING THE AFFECT OF HUMAN BEHAVIOUR RISKS RELATED TO
INFORMATION SECURITY
errors to pose the risks towards the information security. Venkatesh, Thong and Xu (2016)
suggested that there is required to understand the human factors based on their impacts on
effective implementation of the information security management system. The purpose of this
research studies us to review the human factors into the information security as well as discuss of
how the information security becomes major tool to overcome with the human issues
(Katzenbeisser and Petitcolas 2016). There is an increase into threats of the information
technology which brought new solutions, while the human factors related to this research are
being limited. Information security is human factors issue which remains unaddressed (Abbasi,
Sarker and Chiang 2016). The cultural dimensions become important part of strategy of
organization for promotion of performance as well as productivity.
The researcher selected this research topic to develop various theories related to
information security. The researcher also conducted various studies on role of cultural
dimensions on the society. Saunders and Galletta (2016) argued that the organization is required
to make changes into the information security which establish of effective informational security
culture. Crossler et al. (2014) argued that the information security is required to focus on the
human behaviors to mitigate the risks and issues. It is indicated that information security aware
culture reduces the risks to the information assets which reduce the rate of human misbehavior.
The information is being protected by two of the strategies such as use of technology for
protection of valuable information. Second is based on human elements, where the user can
abuse the information by passing to the third party without consent of the informational owners
(Mishra, Akman and Mishra 2014). The research study is focused on role of human elements
culture on the information security. The key significant reason behind role of the human along
MINIMIZING THE AFFECT OF HUMAN BEHAVIOUR RISKS RELATED TO
INFORMATION SECURITY
errors to pose the risks towards the information security. Venkatesh, Thong and Xu (2016)
suggested that there is required to understand the human factors based on their impacts on
effective implementation of the information security management system. The purpose of this
research studies us to review the human factors into the information security as well as discuss of
how the information security becomes major tool to overcome with the human issues
(Katzenbeisser and Petitcolas 2016). There is an increase into threats of the information
technology which brought new solutions, while the human factors related to this research are
being limited. Information security is human factors issue which remains unaddressed (Abbasi,
Sarker and Chiang 2016). The cultural dimensions become important part of strategy of
organization for promotion of performance as well as productivity.
The researcher selected this research topic to develop various theories related to
information security. The researcher also conducted various studies on role of cultural
dimensions on the society. Saunders and Galletta (2016) argued that the organization is required
to make changes into the information security which establish of effective informational security
culture. Crossler et al. (2014) argued that the information security is required to focus on the
human behaviors to mitigate the risks and issues. It is indicated that information security aware
culture reduces the risks to the information assets which reduce the rate of human misbehavior.
The information is being protected by two of the strategies such as use of technology for
protection of valuable information. Second is based on human elements, where the user can
abuse the information by passing to the third party without consent of the informational owners
(Mishra, Akman and Mishra 2014). The research study is focused on role of human elements
culture on the information security. The key significant reason behind role of the human along
Secure Best Marks with AI Grader
Need help grading? Try our AI Grader for instant feedback on your assignments.

10
MINIMIZING THE AFFECT OF HUMAN BEHAVIOUR RISKS RELATED TO
INFORMATION SECURITY
with human factors is challenge to monitor as well as control. Proper control over the human
errors is required to mitigate the risks into information security management system.
1.2 Research Background
Montano and Kasprzyk (2015) stated that the IT organization is implemented of
information security strategies for reducing risks on the information security breaches. Mishra,
Akman and Mishra (2014) indicated that the user’s behavior is required factors to consider
guarantee into secured environment for the information. Kautonen, Gelderen and Fink (2015)
stated that the organization is utilized of various approaches for protecting information system
assets as well as resources. In this particular study, the participants are implemented of different
information security strategies for minimizing consequences of the information security threats
on business sustainability. According to Chen and Tung (2014), human issue is main difficulty
into risk management of the information security. There are some security problems which are
caused due to human behaviors such as act of human error and failure, compromise to the
intellectual property, blackmail of the disclosure of information, unauthorized access to
information and illegal confiscation of the equipments.
Over the last 25 years, the information security management is growing and it is common
as well as regular into the public domains. Most of the information security issues are occurred
due to human errors. Based on the observations, the researcher focuses on human factors of the
information security assurance. Cheng, Zhai and Smyth (2014) stated that despite interest as well
as acceptance into the information security management, the information security appears to be a
gap as well as weakness into the industry. Venkatesh, Thong and Xu (2016) discussed that due to
large number of security breaches as well as data breaches, the main concern is human as errors
are occurred due to lack of awareness of information security. The technology related breaches
MINIMIZING THE AFFECT OF HUMAN BEHAVIOUR RISKS RELATED TO
INFORMATION SECURITY
with human factors is challenge to monitor as well as control. Proper control over the human
errors is required to mitigate the risks into information security management system.
1.2 Research Background
Montano and Kasprzyk (2015) stated that the IT organization is implemented of
information security strategies for reducing risks on the information security breaches. Mishra,
Akman and Mishra (2014) indicated that the user’s behavior is required factors to consider
guarantee into secured environment for the information. Kautonen, Gelderen and Fink (2015)
stated that the organization is utilized of various approaches for protecting information system
assets as well as resources. In this particular study, the participants are implemented of different
information security strategies for minimizing consequences of the information security threats
on business sustainability. According to Chen and Tung (2014), human issue is main difficulty
into risk management of the information security. There are some security problems which are
caused due to human behaviors such as act of human error and failure, compromise to the
intellectual property, blackmail of the disclosure of information, unauthorized access to
information and illegal confiscation of the equipments.
Over the last 25 years, the information security management is growing and it is common
as well as regular into the public domains. Most of the information security issues are occurred
due to human errors. Based on the observations, the researcher focuses on human factors of the
information security assurance. Cheng, Zhai and Smyth (2014) stated that despite interest as well
as acceptance into the information security management, the information security appears to be a
gap as well as weakness into the industry. Venkatesh, Thong and Xu (2016) discussed that due to
large number of security breaches as well as data breaches, the main concern is human as errors
are occurred due to lack of awareness of information security. The technology related breaches

11
MINIMIZING THE AFFECT OF HUMAN BEHAVIOUR RISKS RELATED TO
INFORMATION SECURITY
are occurred due to malicious individuals exploit the vulnerabilities into the technology on daily
basis and it is expected to continue as the security hacks are appeared into the media because of
general public interests. Cheng, Zhai and Smyth (2014) argued that there are various information
security standards into existence as well as operations which support towards the cyber security
assurances.
1.2.1 Human factors for information security
People are at centre of the technological design along with use of designed products. It is
an asset as well as threat. The organization addressed the human elements to deal with the
incidents of information security (Katzenbeisser and Petitcolas 2016). The researcher highlighted
it as number of human related security incidents. Into the organizational policies as well as
standards, there are codes of conducts which are being designed for people to follow up. People
are executers of the organizational information security policies. The human factors are major
forces which are behind effectiveness as well as failure of the security systems. Mishra, Akman
and Mishra (2014) stated that the technical solutions are not sufficed as the insider threats are
become fundamental issues. There is evidence that the human factors are undermine in addition
to underdeveloped. The direct factors are those who dependent on the individual’s characteristics
and have significant impact on the information security management system. Sheeran and Rivis
(2017) discussed that the indirect factors are based on external issues like the organizational
issues those have adequate budget as well as enforcement of policies which have proper
influence to the direct factors and the information security system.
The human errors are defined as divergence into the system which works properly. The
incidents of information system will happen with proper hard approaches to the human
behaviors. Tsai et al. (2016) conducted that the security policies are being designed to restraint
MINIMIZING THE AFFECT OF HUMAN BEHAVIOUR RISKS RELATED TO
INFORMATION SECURITY
are occurred due to malicious individuals exploit the vulnerabilities into the technology on daily
basis and it is expected to continue as the security hacks are appeared into the media because of
general public interests. Cheng, Zhai and Smyth (2014) argued that there are various information
security standards into existence as well as operations which support towards the cyber security
assurances.
1.2.1 Human factors for information security
People are at centre of the technological design along with use of designed products. It is
an asset as well as threat. The organization addressed the human elements to deal with the
incidents of information security (Katzenbeisser and Petitcolas 2016). The researcher highlighted
it as number of human related security incidents. Into the organizational policies as well as
standards, there are codes of conducts which are being designed for people to follow up. People
are executers of the organizational information security policies. The human factors are major
forces which are behind effectiveness as well as failure of the security systems. Mishra, Akman
and Mishra (2014) stated that the technical solutions are not sufficed as the insider threats are
become fundamental issues. There is evidence that the human factors are undermine in addition
to underdeveloped. The direct factors are those who dependent on the individual’s characteristics
and have significant impact on the information security management system. Sheeran and Rivis
(2017) discussed that the indirect factors are based on external issues like the organizational
issues those have adequate budget as well as enforcement of policies which have proper
influence to the direct factors and the information security system.
The human errors are defined as divergence into the system which works properly. The
incidents of information system will happen with proper hard approaches to the human
behaviors. Tsai et al. (2016) conducted that the security policies are being designed to restraint

12
MINIMIZING THE AFFECT OF HUMAN BEHAVIOUR RISKS RELATED TO
INFORMATION SECURITY
the behaviors to eliminate the human errors. The human behavior is hard to define measure as
well as control the organization. The organizations are apprehensive to the employees in order to
follow the rules of information security like the security policies. It is clear that when there is gap
into the research, there is effective along with adequate programmes to educate the employees of
IT organization so that they can aware of information security (Martins, Oliveira and Popovic
2014). Adequate as well as improper skilled staffs are contributed to weak performance into the
policy of information security. When people into the sales department are not aware of how to
use of email encryption, then it ends unencrypted emails to the customers those contain of
confidential information. Kautonen, Gelderen and Fink (2015) analyzed that unsecure
information is being exposed to the pubic domains and then it is obtained by the criminals. The
organizations are not focused people with the technological competency. The training
programmes are to be provided adequate skills in order to confront with the challenges of
information security.
Williams, Rana and Dwivedi (2015) stated that the human behavior is affected by the
cultural dimensions. Data security culture is a piece of the hierarchical culture as the security of
data turns into an authoritative capacity. In order to get a secured domain for the data resources,
the acts of data security turns into a piece of corporate culture inside the association. The data
security culture consists of human properties like practices, demeanors and in addition
convictions held by the association. This could affect the security of the association which might
be or not might be express connected to the effect (Mishra, Akman and Mishra 2014). Culture is
utilized to clarify the human conduct; therefore there is comprehension of the social attributes
which impacts the conduct. The way of life is taken a gander at the general public's conviction
framework, laws, language and in addition attitudinal factors that make individuals inventive
MINIMIZING THE AFFECT OF HUMAN BEHAVIOUR RISKS RELATED TO
INFORMATION SECURITY
the behaviors to eliminate the human errors. The human behavior is hard to define measure as
well as control the organization. The organizations are apprehensive to the employees in order to
follow the rules of information security like the security policies. It is clear that when there is gap
into the research, there is effective along with adequate programmes to educate the employees of
IT organization so that they can aware of information security (Martins, Oliveira and Popovic
2014). Adequate as well as improper skilled staffs are contributed to weak performance into the
policy of information security. When people into the sales department are not aware of how to
use of email encryption, then it ends unencrypted emails to the customers those contain of
confidential information. Kautonen, Gelderen and Fink (2015) analyzed that unsecure
information is being exposed to the pubic domains and then it is obtained by the criminals. The
organizations are not focused people with the technological competency. The training
programmes are to be provided adequate skills in order to confront with the challenges of
information security.
Williams, Rana and Dwivedi (2015) stated that the human behavior is affected by the
cultural dimensions. Data security culture is a piece of the hierarchical culture as the security of
data turns into an authoritative capacity. In order to get a secured domain for the data resources,
the acts of data security turns into a piece of corporate culture inside the association. The data
security culture consists of human properties like practices, demeanors and in addition
convictions held by the association. This could affect the security of the association which might
be or not might be express connected to the effect (Mishra, Akman and Mishra 2014). Culture is
utilized to clarify the human conduct; therefore there is comprehension of the social attributes
which impacts the conduct. The way of life is taken a gander at the general public's conviction
framework, laws, language and in addition attitudinal factors that make individuals inventive
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

13
MINIMIZING THE AFFECT OF HUMAN BEHAVIOUR RISKS RELATED TO
INFORMATION SECURITY
from others. Culture assumes a key huge part into turning of society plus also nation (Soomro,
Shah and Ahmed 2016). Powerful IT security arrangement is a model for hierarchical culture
where the principles and additionally techniques are driven from the representative way to deal
with the data. It is such an archive for any association that is developed from human's points of
view on resilience of issues.
The security is being accomplished by two of the methodologies, for example, insurance
into the association's operational practices and in addition second approach is support alongside
control of information administration systems all through the project life cycle (Teh, Ahmed and
D'Arcy 2015). The arrangements educate the representatives of possess singular obligations, and
reveal to them what they can and cannot do in view of the sensitive data. The mistakes from
human side are unavoidable and the security of framework is being negotiated. The data security
strategy is moved down disciplinary activities and upheld case in official court of law. The
principle point of those arrangements is to outline and furnish the representatives with the rules
on secure the data assets while performing work into the data security (Mishra, Akman and
Mishra 2014). The consistence of representative is required to anticipate and in addition diminish
the abuse of data framework assets notwithstanding misuse by the insiders.
1.3 Research problem statement
There are various reasons behind the information security breaches such as
communication technology, policy computer science and achieve of success in areas is managing
as well as understanding the human factors. One of the main challenges is implementation of
information security policies due to occurrence of cultural changes. The information security
management system sets security framework and regulates way in which the information
technology reaches the resources (Martins, Oliveira and Popovic 2014). Human factors play key
MINIMIZING THE AFFECT OF HUMAN BEHAVIOUR RISKS RELATED TO
INFORMATION SECURITY
from others. Culture assumes a key huge part into turning of society plus also nation (Soomro,
Shah and Ahmed 2016). Powerful IT security arrangement is a model for hierarchical culture
where the principles and additionally techniques are driven from the representative way to deal
with the data. It is such an archive for any association that is developed from human's points of
view on resilience of issues.
The security is being accomplished by two of the methodologies, for example, insurance
into the association's operational practices and in addition second approach is support alongside
control of information administration systems all through the project life cycle (Teh, Ahmed and
D'Arcy 2015). The arrangements educate the representatives of possess singular obligations, and
reveal to them what they can and cannot do in view of the sensitive data. The mistakes from
human side are unavoidable and the security of framework is being negotiated. The data security
strategy is moved down disciplinary activities and upheld case in official court of law. The
principle point of those arrangements is to outline and furnish the representatives with the rules
on secure the data assets while performing work into the data security (Mishra, Akman and
Mishra 2014). The consistence of representative is required to anticipate and in addition diminish
the abuse of data framework assets notwithstanding misuse by the insiders.
1.3 Research problem statement
There are various reasons behind the information security breaches such as
communication technology, policy computer science and achieve of success in areas is managing
as well as understanding the human factors. One of the main challenges is implementation of
information security policies due to occurrence of cultural changes. The information security
management system sets security framework and regulates way in which the information
technology reaches the resources (Martins, Oliveira and Popovic 2014). Human factors play key

14
MINIMIZING THE AFFECT OF HUMAN BEHAVIOUR RISKS RELATED TO
INFORMATION SECURITY
role into the information security. The characteristics of human factors impact the information
security. This research study analyzes and influences effective information security management
systems. The researcher can understand drive as well as restrain of forces of the human issues
with obstacles of the information security. There are main implications of role of human factors
and challenges into process of information security (Siponen, Mahmood and Pahnila 2014). The
information security risks are consequences on operations of organization along with its assets.
There are problems into the research study which is lack of clear as well as effective regulations
which are used to protect the information security along with implementation of proper
protection policies. The main aim is to explore as well as identify the information security
culture with providing framework to enhance the information security.
1.4 Research questions
The main purpose of this research is to suggest of human behavior information security
risk model for supporting investigation and reasons of main features of the human behaviors into
context of the information security within organization. There are research questions such as:
1. What are main characteristics of human behavior within the information security
context?
2. How can we minimize effect of human behavior risks related to the information
security?
3. What are the cultural dimensions and sub-dimensions influencing the information
security?
MINIMIZING THE AFFECT OF HUMAN BEHAVIOUR RISKS RELATED TO
INFORMATION SECURITY
role into the information security. The characteristics of human factors impact the information
security. This research study analyzes and influences effective information security management
systems. The researcher can understand drive as well as restrain of forces of the human issues
with obstacles of the information security. There are main implications of role of human factors
and challenges into process of information security (Siponen, Mahmood and Pahnila 2014). The
information security risks are consequences on operations of organization along with its assets.
There are problems into the research study which is lack of clear as well as effective regulations
which are used to protect the information security along with implementation of proper
protection policies. The main aim is to explore as well as identify the information security
culture with providing framework to enhance the information security.
1.4 Research questions
The main purpose of this research is to suggest of human behavior information security
risk model for supporting investigation and reasons of main features of the human behaviors into
context of the information security within organization. There are research questions such as:
1. What are main characteristics of human behavior within the information security
context?
2. How can we minimize effect of human behavior risks related to the information
security?
3. What are the cultural dimensions and sub-dimensions influencing the information
security?

15
MINIMIZING THE AFFECT OF HUMAN BEHAVIOUR RISKS RELATED TO
INFORMATION SECURITY
1.5 Research aim and objectives
This research study is aimed to develop of framework for minimizing the risks which are
occurred due to human behavior into the information security. The study is conducted to find out
tools and approaches for development of positive human behavior related to the information
security. It is explored of reasons behind employee’s non-compliance with the security policy of
organization and recommendations on how to formulate security policies to encourage the
employee’s compliance. The study also investigates as well as analyzes role along with impact of
the cultural dimensions on the information management system securities. The objectives of this
particular research study leads to fulfill the research aim. Following are the objectives of this
particular research study such as:
To investigate on the human behaviors and attitudes which effect level of security
of the information
To investigate and analyze existing information security models for minimizing
the human behavior risks into the information security
To address the critical human behaviors in minimizing of information security
risks
To determine relations between critical human behavior and information security
risks
1.6 Research scope
The main scope of this research study is to cover the information security, risk
management as well as human behavior for increasing level of the security of information. The
aspects of human are used for investigation of behavior which leads to affect security of
MINIMIZING THE AFFECT OF HUMAN BEHAVIOUR RISKS RELATED TO
INFORMATION SECURITY
1.5 Research aim and objectives
This research study is aimed to develop of framework for minimizing the risks which are
occurred due to human behavior into the information security. The study is conducted to find out
tools and approaches for development of positive human behavior related to the information
security. It is explored of reasons behind employee’s non-compliance with the security policy of
organization and recommendations on how to formulate security policies to encourage the
employee’s compliance. The study also investigates as well as analyzes role along with impact of
the cultural dimensions on the information management system securities. The objectives of this
particular research study leads to fulfill the research aim. Following are the objectives of this
particular research study such as:
To investigate on the human behaviors and attitudes which effect level of security
of the information
To investigate and analyze existing information security models for minimizing
the human behavior risks into the information security
To address the critical human behaviors in minimizing of information security
risks
To determine relations between critical human behavior and information security
risks
1.6 Research scope
The main scope of this research study is to cover the information security, risk
management as well as human behavior for increasing level of the security of information. The
aspects of human are used for investigation of behavior which leads to affect security of
Secure Best Marks with AI Grader
Need help grading? Try our AI Grader for instant feedback on your assignments.

16
MINIMIZING THE AFFECT OF HUMAN BEHAVIOUR RISKS RELATED TO
INFORMATION SECURITY
information. The scope is to analyze level of impacts in security of information by the human
behavior along with mitigation plan for minimizing the effects (Pearlson, Saunders and Galletta
2016). The cyber security strategies are used to design of information security framework related
to the human behavior. As per the best practices, guidelines are recommended for training as
well as awareness about to use of internet services. There is a scope of using an information
security culture model in this research paper.
The model is developed based on the cultural dimensions identified as well as explored of
literature survey. The cultural model is identified as well as related to role of cultural dimensions
as well as sub-dimensions to the organizational culture along with behavior of staffs towards the
information security culture. The information security cultural model helps to develop the
security culture policies (Pearlson, Saunders and Galletta 2016). The affiliation manages
information security by completing of information security standards as well as rules. The
measures are used by relationship to guarantee that it can direct information security from the
comprehensive perspectives, and in this way restricting of perils and affirmation level of
information security social orders. Security mindfulness preparing is given to the staffs to vast
extent of individuals to keep from vindictive connections and additionally going by of suspect
sites (Martins, Oliveira and Popovic 2014). At the point when the approaches and additionally
preparing are critical, at that point there is have to better confirmation the innovation with the
end goal that when individuals foul up thing, at that point the malware are not running and
accomplishing the objectives.
1.7 Research hypothesis
The research hypotheses are as follows:
MINIMIZING THE AFFECT OF HUMAN BEHAVIOUR RISKS RELATED TO
INFORMATION SECURITY
information. The scope is to analyze level of impacts in security of information by the human
behavior along with mitigation plan for minimizing the effects (Pearlson, Saunders and Galletta
2016). The cyber security strategies are used to design of information security framework related
to the human behavior. As per the best practices, guidelines are recommended for training as
well as awareness about to use of internet services. There is a scope of using an information
security culture model in this research paper.
The model is developed based on the cultural dimensions identified as well as explored of
literature survey. The cultural model is identified as well as related to role of cultural dimensions
as well as sub-dimensions to the organizational culture along with behavior of staffs towards the
information security culture. The information security cultural model helps to develop the
security culture policies (Pearlson, Saunders and Galletta 2016). The affiliation manages
information security by completing of information security standards as well as rules. The
measures are used by relationship to guarantee that it can direct information security from the
comprehensive perspectives, and in this way restricting of perils and affirmation level of
information security social orders. Security mindfulness preparing is given to the staffs to vast
extent of individuals to keep from vindictive connections and additionally going by of suspect
sites (Martins, Oliveira and Popovic 2014). At the point when the approaches and additionally
preparing are critical, at that point there is have to better confirmation the innovation with the
end goal that when individuals foul up thing, at that point the malware are not running and
accomplishing the objectives.
1.7 Research hypothesis
The research hypotheses are as follows:

17
MINIMIZING THE AFFECT OF HUMAN BEHAVIOUR RISKS RELATED TO
INFORMATION SECURITY
Hypothesis 1: Organizational leadership is positively related to the employees’ attitude
towards the information security.
Hypothesis 2: Organizational culture is positively related to the employees’ attitude
towards the information security.
Hypothesis 3: Employee’s intention towards information security is positively related to
the employee’s attitude toward information security.
1.8 Importance of the research
Implementation of information security system becomes a key requirement of the IT
organizational services. There are huge amount of research which is focused on the technical
elements of the information security with clear understanding of the impact of culture into the
information security. There are challenges to establish as well as promote of proper information
security culture into the IT organization (Teh, Ahmed and D'Arcy 2015). The conceptual
framework of this particular research study is based on strategic planning on the information
security policies, training of employees along with structure and activities into the IT services.
Importance to maintain security as well as safety to handle the information is required to
maintain security policies into the organization (Siponen, Mahmood and Pahnila 2014). This
particular study is based to get comfortable with the human mistakes which impact the data
security.
Consequently, the human exercises are to be relieved with utilization of data security to
keep from the human conduct. The human conduct related hypotheses are broke down in this
examination for researching different speculations which are utilized to limit the human dangers
from the data framework. The human conduct is the part of data security. Prior studies into the
MINIMIZING THE AFFECT OF HUMAN BEHAVIOUR RISKS RELATED TO
INFORMATION SECURITY
Hypothesis 1: Organizational leadership is positively related to the employees’ attitude
towards the information security.
Hypothesis 2: Organizational culture is positively related to the employees’ attitude
towards the information security.
Hypothesis 3: Employee’s intention towards information security is positively related to
the employee’s attitude toward information security.
1.8 Importance of the research
Implementation of information security system becomes a key requirement of the IT
organizational services. There are huge amount of research which is focused on the technical
elements of the information security with clear understanding of the impact of culture into the
information security. There are challenges to establish as well as promote of proper information
security culture into the IT organization (Teh, Ahmed and D'Arcy 2015). The conceptual
framework of this particular research study is based on strategic planning on the information
security policies, training of employees along with structure and activities into the IT services.
Importance to maintain security as well as safety to handle the information is required to
maintain security policies into the organization (Siponen, Mahmood and Pahnila 2014). This
particular study is based to get comfortable with the human mistakes which impact the data
security.
Consequently, the human exercises are to be relieved with utilization of data security to
keep from the human conduct. The human conduct related hypotheses are broke down in this
examination for researching different speculations which are utilized to limit the human dangers
from the data framework. The human conduct is the part of data security. Prior studies into the
18
MINIMIZING THE AFFECT OF HUMAN BEHAVIOUR RISKS RELATED TO
INFORMATION SECURITY
Chapter 1:
Introduction
Chapter 2:
Literature
review
Chapter 3:
Conceptual
framework
Chapter 5:
Data Analysis
Chapter 6:
Developing IS culture
model
Chapter 7:
Discussion
Chapter 8:
Conclusion and
recommendations
Chapter 4:
Research
methodology
information security domain are being broad into nature which provides general overview of the
information security research (Martins, Oliveira and Popovic 2014). The studies not only
critically analyzed the behavior of user but also helped to understand information security
behavior of people.
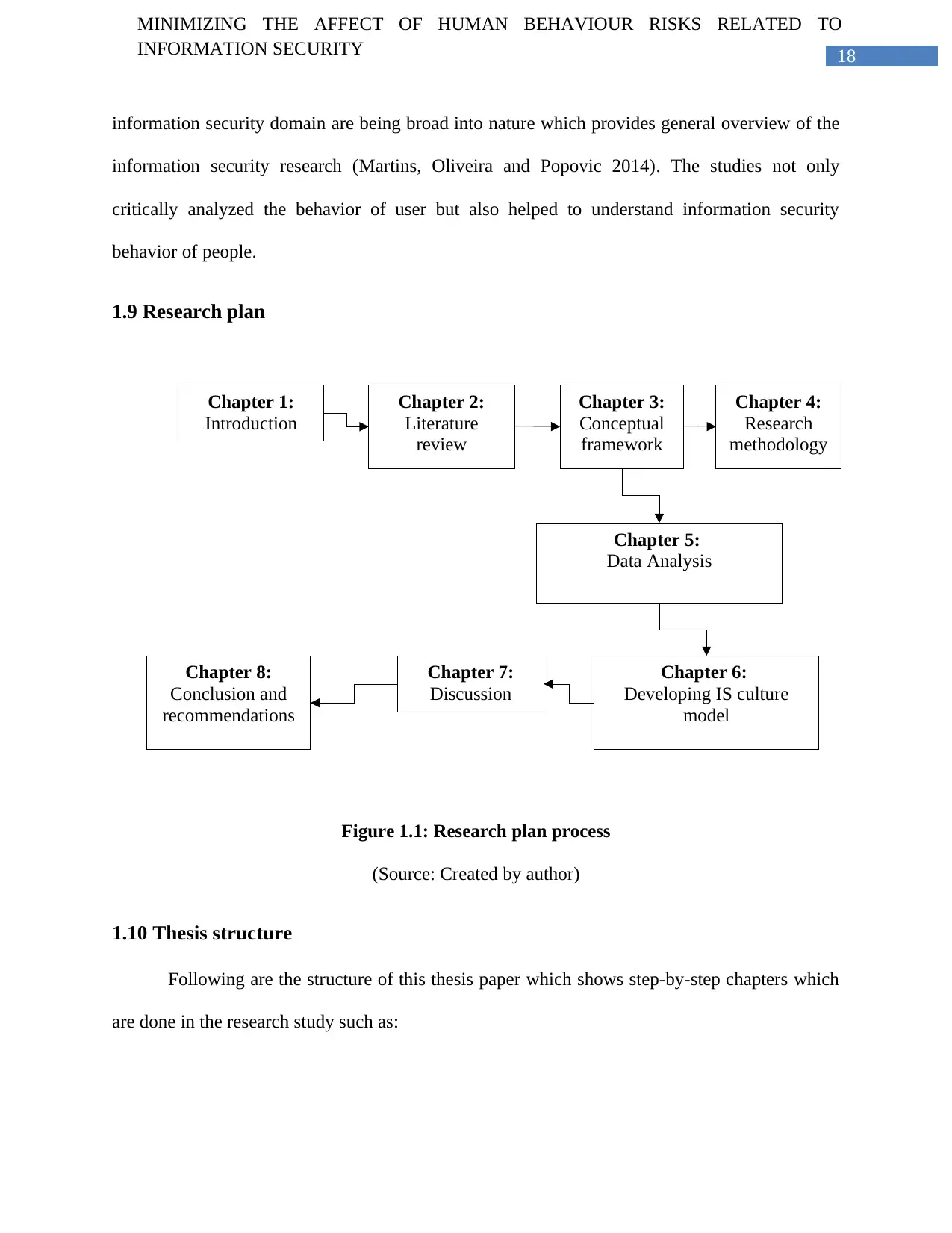
1.9 Research plan
Figure 1.1: Research plan process
(Source: Created by author)
1.10 Thesis structure
Following are the structure of this thesis paper which shows step-by-step chapters which
are done in the research study such as:
MINIMIZING THE AFFECT OF HUMAN BEHAVIOUR RISKS RELATED TO
INFORMATION SECURITY
Chapter 1:
Introduction
Chapter 2:
Literature
review
Chapter 3:
Conceptual
framework
Chapter 5:
Data Analysis
Chapter 6:
Developing IS culture
model
Chapter 7:
Discussion
Chapter 8:
Conclusion and
recommendations
Chapter 4:
Research
methodology
information security domain are being broad into nature which provides general overview of the
information security research (Martins, Oliveira and Popovic 2014). The studies not only
critically analyzed the behavior of user but also helped to understand information security
behavior of people.
1.9 Research plan
Figure 1.1: Research plan process
(Source: Created by author)
1.10 Thesis structure
Following are the structure of this thesis paper which shows step-by-step chapters which
are done in the research study such as:
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

19
MINIMIZING THE AFFECT OF HUMAN BEHAVIOUR RISKS RELATED TO
INFORMATION SECURITY
Chapter 1: Introduction: This particular chapter presents the aims as well as objectives
of the research study. It also provides justifications to carry out the research. The chapter also
provides research background along with the human factors into the information security. In this
particular chapter, the researcher identifies that human behavior is the main reason and aspect for
the information security.
Chapter 2: Literature review: This particular chapter reviews the literature on human
behaviour risks related to information security to establish of research framework. This chapter is
focused on the security culture along with the roles on implementation as well as development of
information security cultural polices. The human behaviour is being affected by the cultural
dimensions as well as sub-dimensions which influence the human errors. Mainly, due to human
errors, the information security risks are increased which affect the brand reputation of
organization.
Chapter 3: Conceptual framework: This chapter provides the structure and content for
the investigation based on the literature and to certain extend in-depth knowledge of the research
topic. The concepts and variables incorporate in the framework should be derived from the
literature. These should capture the underlying principles of the theories which are required to
investigate the research study. This particular chapter provides a framework with the
independent variable, mediating variable and dependent variable. There are two independent
variables such as the information security countermeasures and human perception of information
security countermeasures. One mediating variable is user’s behavior towards the information
security. The dependent variable is Human Information System Security.
MINIMIZING THE AFFECT OF HUMAN BEHAVIOUR RISKS RELATED TO
INFORMATION SECURITY
Chapter 1: Introduction: This particular chapter presents the aims as well as objectives
of the research study. It also provides justifications to carry out the research. The chapter also
provides research background along with the human factors into the information security. In this
particular chapter, the researcher identifies that human behavior is the main reason and aspect for
the information security.
Chapter 2: Literature review: This particular chapter reviews the literature on human
behaviour risks related to information security to establish of research framework. This chapter is
focused on the security culture along with the roles on implementation as well as development of
information security cultural polices. The human behaviour is being affected by the cultural
dimensions as well as sub-dimensions which influence the human errors. Mainly, due to human
errors, the information security risks are increased which affect the brand reputation of
organization.
Chapter 3: Conceptual framework: This chapter provides the structure and content for
the investigation based on the literature and to certain extend in-depth knowledge of the research
topic. The concepts and variables incorporate in the framework should be derived from the
literature. These should capture the underlying principles of the theories which are required to
investigate the research study. This particular chapter provides a framework with the
independent variable, mediating variable and dependent variable. There are two independent
variables such as the information security countermeasures and human perception of information
security countermeasures. One mediating variable is user’s behavior towards the information
security. The dependent variable is Human Information System Security.

20
MINIMIZING THE AFFECT OF HUMAN BEHAVIOUR RISKS RELATED TO
INFORMATION SECURITY
Chapter 4: Research methodology: This particular chapter is adopted to achieve of
research aims as well as objectives. It provides details justifications to adopt of tools, methods as
well as procedures used to collect data using primary data analysis method by use of online
questionnaire. This particular section presents as well as discusses the primary methods in order
to answer to the research questions. Literature survey is done to review the related literature.
Chapter 5: Data analysis: This particular chapter is presented of data analysis which is
intended to identify the information security cultural dimensions which influence the culture of
human behaviour.
Chapter 6: Information security culture model: This particular chapter is presented as
well as discussed the information security culture model which is based on outcomes of the data
analysis which are located into chapter 5 along with literature review in chapter 2. Various
researchers are evaluated into the theoretical part with aim to assess the human security culture
into the organization. Most of the studies have offered slight attention into the organizational
attitudes, human behaviors as well as contact among the individuals and its context.
Chapter 7: Discussion: This particular chapter discusses and evaluates critically the
main outcomes of research which provides answers to selected research questions as well as
research hypothesis.
Chapter 8: Conclusion and recommendations: This particular chapter is summarized
the outcomes along with contributions of the research study. This chapter also provides
recommendations in order to improve the information security culture. It provides suggestions
for the future research into areas of information security culture.
MINIMIZING THE AFFECT OF HUMAN BEHAVIOUR RISKS RELATED TO
INFORMATION SECURITY
Chapter 4: Research methodology: This particular chapter is adopted to achieve of
research aims as well as objectives. It provides details justifications to adopt of tools, methods as
well as procedures used to collect data using primary data analysis method by use of online
questionnaire. This particular section presents as well as discusses the primary methods in order
to answer to the research questions. Literature survey is done to review the related literature.
Chapter 5: Data analysis: This particular chapter is presented of data analysis which is
intended to identify the information security cultural dimensions which influence the culture of
human behaviour.
Chapter 6: Information security culture model: This particular chapter is presented as
well as discussed the information security culture model which is based on outcomes of the data
analysis which are located into chapter 5 along with literature review in chapter 2. Various
researchers are evaluated into the theoretical part with aim to assess the human security culture
into the organization. Most of the studies have offered slight attention into the organizational
attitudes, human behaviors as well as contact among the individuals and its context.
Chapter 7: Discussion: This particular chapter discusses and evaluates critically the
main outcomes of research which provides answers to selected research questions as well as
research hypothesis.
Chapter 8: Conclusion and recommendations: This particular chapter is summarized
the outcomes along with contributions of the research study. This chapter also provides
recommendations in order to improve the information security culture. It provides suggestions
for the future research into areas of information security culture.

21
MINIMIZING THE AFFECT OF HUMAN BEHAVIOUR RISKS RELATED TO
INFORMATION SECURITY
1.11 Research novelty and contribution
This research study is contributed to knowledge of information security by demonstration
of critical as well as importance role to the human factors in development of the information
security system processes (Siponen, Mahmood and Pahnila 2014). The contribution of this
particular study is practical as well as theoretical basis for the security of information in
recommendations of objective framework to assess, develop and model the human behavior
information security risk approaches. One of the main contributions into this particular research
study is to make changes into holistic management of the information security for establishment
of the information security cultures. There are lack of research is done on role as well as impact
of the organizational cultural dimensions on the information security (Pearlson, Saunders and
Galletta 2016). The information security is required to focus on the human behavior. There are
indication of information security culture which reduce the risks into the informational assets
with reduce rates into the human errors.
This particular thesis paper is made with the following articles such as:
1. It reviews current materials which are related to the information security breaches,
research as well as mechanism along with published findings.
2. It looks into significance of the human elements into the security assurance.
3. It is proposed of further research with use of non-standard information security
assurance mechanisms that are applied with fields as well as highlights of
implications.
The thesis paper is looked into published information security data breaches which move
on to define assurance as well as identify the current assurance methods adopted by the IT
MINIMIZING THE AFFECT OF HUMAN BEHAVIOUR RISKS RELATED TO
INFORMATION SECURITY
1.11 Research novelty and contribution
This research study is contributed to knowledge of information security by demonstration
of critical as well as importance role to the human factors in development of the information
security system processes (Siponen, Mahmood and Pahnila 2014). The contribution of this
particular study is practical as well as theoretical basis for the security of information in
recommendations of objective framework to assess, develop and model the human behavior
information security risk approaches. One of the main contributions into this particular research
study is to make changes into holistic management of the information security for establishment
of the information security cultures. There are lack of research is done on role as well as impact
of the organizational cultural dimensions on the information security (Pearlson, Saunders and
Galletta 2016). The information security is required to focus on the human behavior. There are
indication of information security culture which reduce the risks into the informational assets
with reduce rates into the human errors.
This particular thesis paper is made with the following articles such as:
1. It reviews current materials which are related to the information security breaches,
research as well as mechanism along with published findings.
2. It looks into significance of the human elements into the security assurance.
3. It is proposed of further research with use of non-standard information security
assurance mechanisms that are applied with fields as well as highlights of
implications.
The thesis paper is looked into published information security data breaches which move
on to define assurance as well as identify the current assurance methods adopted by the IT
Secure Best Marks with AI Grader
Need help grading? Try our AI Grader for instant feedback on your assignments.

22
MINIMIZING THE AFFECT OF HUMAN BEHAVIOUR RISKS RELATED TO
INFORMATION SECURITY
organization. The document is then progressed on the human factors pertain towards the
information security assurance and it is related to the human behavior which underpins the
research study. The thesis paper is moved on towards the mechanisms to measure as well as
assess used outside of the cyber security field which benefits the current state of the information
security on negative aspects of the published articles.
1.12 Summary
It is summarized that technological innovation is required to secure the data while human
is in charge of outlining, executing and working the mechanical instruments. People are
considered as the weakest connection into security of the information and data because of human
mistakes. The business is utilized of data security strategy to ensure the advanced resources
notwithstanding educated rights to keep the theft of the data. The significance of this research
study is to become familiar with the human errors which influences the information security.
Therefore, the human activities are to be mitigated with use of information security to prevent
from the human behavior. The human behavior related theories are analyzed in this study for
investigating various theories which are used to minimize the human risks from the information
system. The human behavior is the aspect of information security. All through the threats to the
data security alongside forms and additionally instruments, there is zone which stays steady
alongside predictable with the threats. Because of increment into internal and in addition external
digital threats, the human conduct and additionally mechanical vulnerability is stayed noticeable
obstacles into the corporate certainty. The association administers data security by actualizing of
data security norms and rules. The measures are utilized by association to ensure that it can
administer data security from the all encompassing viewpoints, and in this manner limiting of
MINIMIZING THE AFFECT OF HUMAN BEHAVIOUR RISKS RELATED TO
INFORMATION SECURITY
organization. The document is then progressed on the human factors pertain towards the
information security assurance and it is related to the human behavior which underpins the
research study. The thesis paper is moved on towards the mechanisms to measure as well as
assess used outside of the cyber security field which benefits the current state of the information
security on negative aspects of the published articles.
1.12 Summary
It is summarized that technological innovation is required to secure the data while human
is in charge of outlining, executing and working the mechanical instruments. People are
considered as the weakest connection into security of the information and data because of human
mistakes. The business is utilized of data security strategy to ensure the advanced resources
notwithstanding educated rights to keep the theft of the data. The significance of this research
study is to become familiar with the human errors which influences the information security.
Therefore, the human activities are to be mitigated with use of information security to prevent
from the human behavior. The human behavior related theories are analyzed in this study for
investigating various theories which are used to minimize the human risks from the information
system. The human behavior is the aspect of information security. All through the threats to the
data security alongside forms and additionally instruments, there is zone which stays steady
alongside predictable with the threats. Because of increment into internal and in addition external
digital threats, the human conduct and additionally mechanical vulnerability is stayed noticeable
obstacles into the corporate certainty. The association administers data security by actualizing of
data security norms and rules. The measures are utilized by association to ensure that it can
administer data security from the all encompassing viewpoints, and in this manner limiting of

23
MINIMIZING THE AFFECT OF HUMAN BEHAVIOUR RISKS RELATED TO
INFORMATION SECURITY
dangers and acknowledgment level of data security societies. The human conduct gives a higher
effect on progress and additionally inability to secure and ensure the data.
Chapter 2: Development of theoretical background/ Literature review on
human behaviour risks related to information security
2.1 Introduction
The research topic is based on minimizing the affect of human behaviour risks related to
information security. Human behaviours into the organization are considered as main threat into
the organization. Among it, security of information is considered as weakest link. It is hard to
create an information security culture and protect the data and information (Siponen, Mahmood
and Pahnila 2014). The protection of the information security promises along with prevents the
innovative technology along with understanding the human uses. In this chapter, the researcher
summarizes the background of the information security, its principles, and relevant theories
along with models, threats of information security and standards and guidelines of information
security (Peltier 2016). This literature chapter analyzes on the security of information and
computer data from the malicious intentions. Development of the theoretical model for the
information security is challenging work as there are diverse countermeasures, covering of
strategic as well as operational challenges based on legal and organizational perspectives.
2.2 What is Information Security
Safa, Von Solms and Furnell (2016) stated that information security is practice to prevent
the unauthorized access, disclosure, inspection and destruction of the information. Crossler et al.
MINIMIZING THE AFFECT OF HUMAN BEHAVIOUR RISKS RELATED TO
INFORMATION SECURITY
dangers and acknowledgment level of data security societies. The human conduct gives a higher
effect on progress and additionally inability to secure and ensure the data.
Chapter 2: Development of theoretical background/ Literature review on
human behaviour risks related to information security
2.1 Introduction
The research topic is based on minimizing the affect of human behaviour risks related to
information security. Human behaviours into the organization are considered as main threat into
the organization. Among it, security of information is considered as weakest link. It is hard to
create an information security culture and protect the data and information (Siponen, Mahmood
and Pahnila 2014). The protection of the information security promises along with prevents the
innovative technology along with understanding the human uses. In this chapter, the researcher
summarizes the background of the information security, its principles, and relevant theories
along with models, threats of information security and standards and guidelines of information
security (Peltier 2016). This literature chapter analyzes on the security of information and
computer data from the malicious intentions. Development of the theoretical model for the
information security is challenging work as there are diverse countermeasures, covering of
strategic as well as operational challenges based on legal and organizational perspectives.
2.2 What is Information Security
Safa, Von Solms and Furnell (2016) stated that information security is practice to prevent
the unauthorized access, disclosure, inspection and destruction of the information. Crossler et al.

24
MINIMIZING THE AFFECT OF HUMAN BEHAVIOUR RISKS RELATED TO
INFORMATION SECURITY
(2013) argued that security of information is required to protect the confidentiality as well as
data availability while focused on policies and standards of information security. It is achieved
through use of risk management process such as identification of assets, threat sources and
vulnerabilities. He et al. (2017) defined that information security is set of strategies to manage
the process, tools as well as policies to detect along with counter the threats to the digital
information. A proper cryptography tools are used to mitigate the security threats. The possible
responses to the security threats are implementation of countermeasures to reduce the
vulnerabilities, evaluate the countermeasures due to threats.
2.3 Background to Information Security
Earlier information security is identified as integrity, availability as well as
confidentiality as the security factors. The security term "CIA Triad" was being gotten from
these three words. The CIA Triad inevitably developed into the Parkerian Hexad. Aspects of the
Hexad incorporate secrecy or control, data integrity, utility, accessibility as well as authenticity.
The Hexad inclines intensely upon confirmation as well as cryptography with a specific end goal
to make preparations for the security threats (Malekian, Hayati and Aarts 2017). Throughout the
history, confidentiality of the information is playing a key role into the military conflict. Amid
the early years of the computing, the centralized servers utilized by the military were associated
through committed telephone lines to frame ARPANET, the ancestor to the advanced web.
While this permitted simple synchronization of data between server centers, it additionally gave
unsecure focuses between the server centers and people in general. This defenselessness was
tended to by securing physical areas and equipment.
A team shaped by “ARPA (Advanced Research Projects Agency)” to think about web
security in 1967 observed this technique to be insufficient, and the Rand Report R-609 decided
MINIMIZING THE AFFECT OF HUMAN BEHAVIOUR RISKS RELATED TO
INFORMATION SECURITY
(2013) argued that security of information is required to protect the confidentiality as well as
data availability while focused on policies and standards of information security. It is achieved
through use of risk management process such as identification of assets, threat sources and
vulnerabilities. He et al. (2017) defined that information security is set of strategies to manage
the process, tools as well as policies to detect along with counter the threats to the digital
information. A proper cryptography tools are used to mitigate the security threats. The possible
responses to the security threats are implementation of countermeasures to reduce the
vulnerabilities, evaluate the countermeasures due to threats.
2.3 Background to Information Security
Earlier information security is identified as integrity, availability as well as
confidentiality as the security factors. The security term "CIA Triad" was being gotten from
these three words. The CIA Triad inevitably developed into the Parkerian Hexad. Aspects of the
Hexad incorporate secrecy or control, data integrity, utility, accessibility as well as authenticity.
The Hexad inclines intensely upon confirmation as well as cryptography with a specific end goal
to make preparations for the security threats (Malekian, Hayati and Aarts 2017). Throughout the
history, confidentiality of the information is playing a key role into the military conflict. Amid
the early years of the computing, the centralized servers utilized by the military were associated
through committed telephone lines to frame ARPANET, the ancestor to the advanced web.
While this permitted simple synchronization of data between server centers, it additionally gave
unsecure focuses between the server centers and people in general. This defenselessness was
tended to by securing physical areas and equipment.
A team shaped by “ARPA (Advanced Research Projects Agency)” to think about web
security in 1967 observed this technique to be insufficient, and the Rand Report R-609 decided
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

25
MINIMIZING THE AFFECT OF HUMAN BEHAVIOUR RISKS RELATED TO
INFORMATION SECURITY
extra advances must be taken to enhance security. This research report denoted an imperative
stage in the improvement of the present data security (Ab Rahman and Choo 2015). Some of the
early security efforts concentrated on the centralized server working framework. “MULTICS
(Multiplexed Information and Computing Service)” was an exertion by MIT, Bell Labs as well
as General Electric to incorporate security with centralized server working frameworks utilizing
numerous security levels along with passwords. It ended up old when the time of PCs arrived.
Technology is required to secure the information while human is responsible for
designing, implementing and operating the technological tools. Humans are considered as the
weakest link into security of the data and information due to human errors. Into an information
security domain because of five of the human errors, it affects the security. First error is involved
with failure while changing of passwords. Second errors are involved with incorrect use of
procedure while writing down the password (Safa, Von Solms and Furnell 2016). Third error is
number of errors which are caused by some extraneous acts and fourth is caused due to
sequential acts. The final one is time errors which are caused due to people fails to do the task in
scheduled time. The business is employed of information security policy to protect the digital
assets in addition to intellectual rights to prevent the theft of the information (Gritzalis et al.
2014). Apart from this, information security principles are also used to mitigate the human errors
to prevent the associated risks. The information system is not dependent on preventing the
technical issues, but it is based on human those use of system and behave.
2.4 Information Security Principles
Safa and Von Solms (2016) stated that principles are the core requirement of information
security for the safe utilization along with flow of information. The storage of that information is
MINIMIZING THE AFFECT OF HUMAN BEHAVIOUR RISKS RELATED TO
INFORMATION SECURITY
extra advances must be taken to enhance security. This research report denoted an imperative
stage in the improvement of the present data security (Ab Rahman and Choo 2015). Some of the
early security efforts concentrated on the centralized server working framework. “MULTICS
(Multiplexed Information and Computing Service)” was an exertion by MIT, Bell Labs as well
as General Electric to incorporate security with centralized server working frameworks utilizing
numerous security levels along with passwords. It ended up old when the time of PCs arrived.
Technology is required to secure the information while human is responsible for
designing, implementing and operating the technological tools. Humans are considered as the
weakest link into security of the data and information due to human errors. Into an information
security domain because of five of the human errors, it affects the security. First error is involved
with failure while changing of passwords. Second errors are involved with incorrect use of
procedure while writing down the password (Safa, Von Solms and Furnell 2016). Third error is
number of errors which are caused by some extraneous acts and fourth is caused due to
sequential acts. The final one is time errors which are caused due to people fails to do the task in
scheduled time. The business is employed of information security policy to protect the digital
assets in addition to intellectual rights to prevent the theft of the information (Gritzalis et al.
2014). Apart from this, information security principles are also used to mitigate the human errors
to prevent the associated risks. The information system is not dependent on preventing the
technical issues, but it is based on human those use of system and behave.
2.4 Information Security Principles
Safa and Von Solms (2016) stated that principles are the core requirement of information
security for the safe utilization along with flow of information. The storage of that information is

26
MINIMIZING THE AFFECT OF HUMAN BEHAVIOUR RISKS RELATED TO
INFORMATION SECURITY
CIA triad, which stands for confidentiality, integrity as well as availability of the data. Based on
CIA model, there are three principles of information security which is summarized as follows:
Confidentiality: It means that the information is seen only by those who have authorized
access to see it. The bank protects the confidentiality of the information by entering a PIN which
is only known by the ATM users to check the balance or other banking activities (Gritzalis et al.
2014). It requires identification when someone can conduct transaction on the account.
Integrity: It involves ensuring that the information are not changed and removed without
the permission of the authorized person. The information is expected to be and when anyone
changed it, the user should know. The banks are putting safeguards to prevent the employees
from changing the balance without the knowledge (Taylor and Bean 2017). Most of the banks
are protected integrity of the information by letting an alert when any money is being withdrawn
from the account through the SMS on the phone. It also provides information from where the
money is being withdrawn. Therefore, there is no such problem at data integrity.
Availability: It ensures to get information when the authorized user requires taking it. It is
not good to have bank account when the user are not able to give information on how much
money was into the bank and what transactions are being occurred (Safa, Von Solms and Furnell
2016). The banks are giving the information into various ways such as online banking, inquiry of
ATM balance as well as monthly statement on the email.
2.5 Relevant Theories and Methods
Theory is characterized by Peltier (2016), as an arrangement of interrelated factors,
definitions, and recommendations that exhibits an orderly perspective of wonders by indicating
relations among factors, with the motivation behind clarifying common marvels. Another
MINIMIZING THE AFFECT OF HUMAN BEHAVIOUR RISKS RELATED TO
INFORMATION SECURITY
CIA triad, which stands for confidentiality, integrity as well as availability of the data. Based on
CIA model, there are three principles of information security which is summarized as follows:
Confidentiality: It means that the information is seen only by those who have authorized
access to see it. The bank protects the confidentiality of the information by entering a PIN which
is only known by the ATM users to check the balance or other banking activities (Gritzalis et al.
2014). It requires identification when someone can conduct transaction on the account.
Integrity: It involves ensuring that the information are not changed and removed without
the permission of the authorized person. The information is expected to be and when anyone
changed it, the user should know. The banks are putting safeguards to prevent the employees
from changing the balance without the knowledge (Taylor and Bean 2017). Most of the banks
are protected integrity of the information by letting an alert when any money is being withdrawn
from the account through the SMS on the phone. It also provides information from where the
money is being withdrawn. Therefore, there is no such problem at data integrity.
Availability: It ensures to get information when the authorized user requires taking it. It is
not good to have bank account when the user are not able to give information on how much
money was into the bank and what transactions are being occurred (Safa, Von Solms and Furnell
2016). The banks are giving the information into various ways such as online banking, inquiry of
ATM balance as well as monthly statement on the email.
2.5 Relevant Theories and Methods
Theory is characterized by Peltier (2016), as an arrangement of interrelated factors,
definitions, and recommendations that exhibits an orderly perspective of wonders by indicating
relations among factors, with the motivation behind clarifying common marvels. Another

27
MINIMIZING THE AFFECT OF HUMAN BEHAVIOUR RISKS RELATED TO
INFORMATION SECURITY
meaning of the hypothesis is finished by Malekian, Hayati and Aarts (2017), as a deliberate
clarification for the perceptions that identify with a specific part of life.
Socio-specialized hypothesis has at its center the plan and execution of any authoritative
framework must be comprehended and enhanced if both 'social' and 'specialized' perspectives are
united and regarded as associated parts of an intricate framework. Authoritative change programs
regularly come up short since they are excessively centered on one part of the framework,
generally innovation and neglect to break down and in addition comprehend the perplexing
interdependencies that exist (Safa, Von Solmsand Furnell 2016). This is straightforwardly
comparable to the plan of an unpredictable designing item, for example, a gas turbine motor.
Similarly as any change to this intricate designing framework needs to address the thump on
impacts through whatever is left of the motor, so too does any change inside an authoritative
framework.
Action hypothesis (AT) created in the Soviet Union in the 1920's and 1930's out of
endeavors to build up another way to deal with brain science that unified human awareness and
human movement. The comprehension was that human personalities exist, create, and must be
comprehended with regards to important, objective driven and socially-decided collaborations
amongst people and their condition (Taylorand Bean2017). All the more particularly, the
connection amongst people and their condition is interceded by instruments that is physical
curios, for example, advances and machines and signs that is representative antiquities, for
example, thoughts, dialect, social traditions and social practices. The objective driven part of
human action is critical, and ancient rarity interceded action is gone for accomplishing objects.
MINIMIZING THE AFFECT OF HUMAN BEHAVIOUR RISKS RELATED TO
INFORMATION SECURITY
meaning of the hypothesis is finished by Malekian, Hayati and Aarts (2017), as a deliberate
clarification for the perceptions that identify with a specific part of life.
Socio-specialized hypothesis has at its center the plan and execution of any authoritative
framework must be comprehended and enhanced if both 'social' and 'specialized' perspectives are
united and regarded as associated parts of an intricate framework. Authoritative change programs
regularly come up short since they are excessively centered on one part of the framework,
generally innovation and neglect to break down and in addition comprehend the perplexing
interdependencies that exist (Safa, Von Solmsand Furnell 2016). This is straightforwardly
comparable to the plan of an unpredictable designing item, for example, a gas turbine motor.
Similarly as any change to this intricate designing framework needs to address the thump on
impacts through whatever is left of the motor, so too does any change inside an authoritative
framework.
Action hypothesis (AT) created in the Soviet Union in the 1920's and 1930's out of
endeavors to build up another way to deal with brain science that unified human awareness and
human movement. The comprehension was that human personalities exist, create, and must be
comprehended with regards to important, objective driven and socially-decided collaborations
amongst people and their condition (Taylorand Bean2017). All the more particularly, the
connection amongst people and their condition is interceded by instruments that is physical
curios, for example, advances and machines and signs that is representative antiquities, for
example, thoughts, dialect, social traditions and social practices. The objective driven part of
human action is critical, and ancient rarity interceded action is gone for accomplishing objects.
Secure Best Marks with AI Grader
Need help grading? Try our AI Grader for instant feedback on your assignments.

28
MINIMIZING THE AFFECT OF HUMAN BEHAVIOUR RISKS RELATED TO
INFORMATION SECURITY
Human behavior theories are the set of theories which are being used to describe various
kinds of cognitive situations. In order to conduct study in this research, there is requirement of
those theories is to understand the characteristics of human behavior within the information
security context (Montano and Kasprzyk 2015). The human behavior risks are to be minimized
which are related to the information security. There are group of theories which are required to
be presented which helps to understand the research topic properly. Those theories are required
to be more attentive from the organization in regards of the human elements along with
organizational context of human interaction (Mishra, Akman and Mishra 2014). The human
behavior theories are theory of reasoned action (TRA), theory planned behavior (TPB),
protection motivation theory (PMT), general deterrence theory (GDT) and technology
acceptance theory (TAT). Those are chosen as point of departure for this study as it has explicit
focus on the behavioral intention. According to Paul, Modi and Patel (2016), there are five
dominant applied behavioral theories which are used into context of the information technology
which are explained below:
Theory of Reasoned Action (TRA): This theory was being introduced by Fishbien and
Ajzen in the year 1975. Kautonen, Gelderen and Fink (2015) stated that this theory is used into
the communication for disclosure as theory of understanding. This particular theory is aimed to
illustrate relationship among attitudes as well as behaviors into the human actions. TRA theory is
used for predicting the individuals based on pre-existing attitudes as well as behavioral
intentions. The decision of individuals for engaging into the human behavior is concerned on
outcomes of the individual expectations will come as result to perform the behavior. Montano
and Kasprzyk (2015) argued that using this theory the individuals are motivated to perform
actions to minimize the human factors from the context of information security. According to
MINIMIZING THE AFFECT OF HUMAN BEHAVIOUR RISKS RELATED TO
INFORMATION SECURITY
Human behavior theories are the set of theories which are being used to describe various
kinds of cognitive situations. In order to conduct study in this research, there is requirement of
those theories is to understand the characteristics of human behavior within the information
security context (Montano and Kasprzyk 2015). The human behavior risks are to be minimized
which are related to the information security. There are group of theories which are required to
be presented which helps to understand the research topic properly. Those theories are required
to be more attentive from the organization in regards of the human elements along with
organizational context of human interaction (Mishra, Akman and Mishra 2014). The human
behavior theories are theory of reasoned action (TRA), theory planned behavior (TPB),
protection motivation theory (PMT), general deterrence theory (GDT) and technology
acceptance theory (TAT). Those are chosen as point of departure for this study as it has explicit
focus on the behavioral intention. According to Paul, Modi and Patel (2016), there are five
dominant applied behavioral theories which are used into context of the information technology
which are explained below:
Theory of Reasoned Action (TRA): This theory was being introduced by Fishbien and
Ajzen in the year 1975. Kautonen, Gelderen and Fink (2015) stated that this theory is used into
the communication for disclosure as theory of understanding. This particular theory is aimed to
illustrate relationship among attitudes as well as behaviors into the human actions. TRA theory is
used for predicting the individuals based on pre-existing attitudes as well as behavioral
intentions. The decision of individuals for engaging into the human behavior is concerned on
outcomes of the individual expectations will come as result to perform the behavior. Montano
and Kasprzyk (2015) argued that using this theory the individuals are motivated to perform
actions to minimize the human factors from the context of information security. According to

29
MINIMIZING THE AFFECT OF HUMAN BEHAVIOUR RISKS RELATED TO
INFORMATION SECURITY
Attitude toward
actor behaviour
Subjective norms
Behavioural
intention
Behavior
this theory, intention to do certain behavior precedes the definite behavior. The behavioral
intention is a key significant requirement to this theory as this intention is being determined by
attitudes to the behaviors along with subjective norms (De Leeuw et al. 2015). The theory
predicts that the behavioral intent is being created and caused by two of these factors. Fishbein
and Ajzen called it as the evaluation as well as strength of belief.
Figure 2.1: Theory of reasoned action
(Source: Montano and Kasprzyk, 2015, pp-97)
Theory of planned behavior (TPB): This theory was being developed by Ajzen in the
year 1991. The behavior of the employees influences the information security within the
organization. Sheeran and Rivis (2017) discussed that this theory is linked with one’s beliefs as
well as behavior. This theory was being developed from theory of reasoned action. It is mainly
predicts the intention of individual to engage into behavior at particular time as well as place.
Chen and Tung (2014) stated that this theory is dependent on motivation along with ability of
human. This theory is consists of six constructs. The first one is attitude which is referred to
degree to which the person consists of favorable as well as unfavorable evaluation of the human
MINIMIZING THE AFFECT OF HUMAN BEHAVIOUR RISKS RELATED TO
INFORMATION SECURITY
Attitude toward
actor behaviour
Subjective norms
Behavioural
intention
Behavior
this theory, intention to do certain behavior precedes the definite behavior. The behavioral
intention is a key significant requirement to this theory as this intention is being determined by
attitudes to the behaviors along with subjective norms (De Leeuw et al. 2015). The theory
predicts that the behavioral intent is being created and caused by two of these factors. Fishbein
and Ajzen called it as the evaluation as well as strength of belief.
Figure 2.1: Theory of reasoned action
(Source: Montano and Kasprzyk, 2015, pp-97)
Theory of planned behavior (TPB): This theory was being developed by Ajzen in the
year 1991. The behavior of the employees influences the information security within the
organization. Sheeran and Rivis (2017) discussed that this theory is linked with one’s beliefs as
well as behavior. This theory was being developed from theory of reasoned action. It is mainly
predicts the intention of individual to engage into behavior at particular time as well as place.
Chen and Tung (2014) stated that this theory is dependent on motivation along with ability of
human. This theory is consists of six constructs. The first one is attitude which is referred to
degree to which the person consists of favorable as well as unfavorable evaluation of the human

30
MINIMIZING THE AFFECT OF HUMAN BEHAVIOUR RISKS RELATED TO
INFORMATION SECURITY
Attitudes
Subjective norms
Perceived behavioural control
Intention Behaviour
behavior. Mullan et al. (2015) illustrated that second is behavioral intention referred to as the
motivational factor which influences on behavior where there is requirement of stronger
intention of behavior. Third is a subjective norm which is based on approval and disapproval of
behavior. Fourth is social norms are codes of behavior into group of people and cultural contexts.
Fifth is perceived power, which facilitates the performance of human behavior in mitigating of
risks into information security (Crossler et al. 2014). The sixth construct is perceived behavioral
control which is referred to the perception of person in ease and difficulty to perform behavior of
interests. This theory is mainly explained the intention of individuals to perform the behavior.
Therefore, it postulates that behavior which can be explained by behavioral beliefs, normative
beliefs, and self-efficacy as antecedents of attitudes, subjective norms, and perceived behavioral
control, respectively.
Figure 2.2: Theory of planned behavior
(Source: Sheeran and Rivis 2017, pp-61)
MINIMIZING THE AFFECT OF HUMAN BEHAVIOUR RISKS RELATED TO
INFORMATION SECURITY
Attitudes
Subjective norms
Perceived behavioural control
Intention Behaviour
behavior. Mullan et al. (2015) illustrated that second is behavioral intention referred to as the
motivational factor which influences on behavior where there is requirement of stronger
intention of behavior. Third is a subjective norm which is based on approval and disapproval of
behavior. Fourth is social norms are codes of behavior into group of people and cultural contexts.
Fifth is perceived power, which facilitates the performance of human behavior in mitigating of
risks into information security (Crossler et al. 2014). The sixth construct is perceived behavioral
control which is referred to the perception of person in ease and difficulty to perform behavior of
interests. This theory is mainly explained the intention of individuals to perform the behavior.
Therefore, it postulates that behavior which can be explained by behavioral beliefs, normative
beliefs, and self-efficacy as antecedents of attitudes, subjective norms, and perceived behavioral
control, respectively.
Figure 2.2: Theory of planned behavior
(Source: Sheeran and Rivis 2017, pp-61)
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

31
MINIMIZING THE AFFECT OF HUMAN BEHAVIOUR RISKS RELATED TO
INFORMATION SECURITY
Perceived severity
Perceived vulnerability
Threat Coping
Perceived response efficacy
Perceived self-efficacyIntention
Behaviour
+
+ +
Protection Motivation Theory (PMT): This theory is most important as it proposes that
people can protect themselves based on some factors such as “perceived severity of the
threatening events, perceived probability of occurrence, efficacy of recommended preventive
behavior as well as perceived self efficacy”. This model explains why people are engaged into
the risk practices and provides suggestions to change the human behavior. The first prevention
step is to take measures to mitigate the risks and second prevention step is to prevent to enter into
worse conditions. Tsai et al. (2016) explained that this theory is concerned on how the
individuals are processing the threats along with selecting the responses to cope with the threats.
Crossler et al. (2014) concluded that this particular theory is used as framework to understand
use of protective measures into the information security.
Figure 2.3: Protection motivation theory
(Source: Tsai et al. 2016, pp-141)
MINIMIZING THE AFFECT OF HUMAN BEHAVIOUR RISKS RELATED TO
INFORMATION SECURITY
Perceived severity
Perceived vulnerability
Threat Coping
Perceived response efficacy
Perceived self-efficacyIntention
Behaviour
+
+ +
Protection Motivation Theory (PMT): This theory is most important as it proposes that
people can protect themselves based on some factors such as “perceived severity of the
threatening events, perceived probability of occurrence, efficacy of recommended preventive
behavior as well as perceived self efficacy”. This model explains why people are engaged into
the risk practices and provides suggestions to change the human behavior. The first prevention
step is to take measures to mitigate the risks and second prevention step is to prevent to enter into
worse conditions. Tsai et al. (2016) explained that this theory is concerned on how the
individuals are processing the threats along with selecting the responses to cope with the threats.
Crossler et al. (2014) concluded that this particular theory is used as framework to understand
use of protective measures into the information security.
Figure 2.3: Protection motivation theory
(Source: Tsai et al. 2016, pp-141)

32
MINIMIZING THE AFFECT OF HUMAN BEHAVIOUR RISKS RELATED TO
INFORMATION SECURITY
Certainty of sanction
Clarity of sanction
Severity of sanction
Organizational deterranceInformation security breaches
General Deterrence Theory (GDT): It is a legal theory which is sending messages to the
general public about the risks which are raised from the information security risks due to human
factors. Cheng, Zhai and Smyth (2014) stated that this theory posits the individuals to dissuade
from commitment of antisocial actors throughout use of proper countermeasures. This theory is
used as countermeasures to eliminate the threats and mitigate them. The useful countermeasures
are education, training, backups and tools to mitigate the risks. Tittle (2018) argued that the
theory is used to prevent the threats into general population. This theory stated that the perceived
severity, certainty of the sanctions along with punishment of the influence to make decisions for
engagement of crime by balancing of both cost along with benefits. Martins, Oliveira and
Popovic (2014) studied that information security is focused on the countermeasures of security
and preventive strategies which impact the intention of employees in order to misuse.
Figure 2.4: General Deterrence Theory
(Source: Cheng, Zhai and Smyth 2014, pp-224)
MINIMIZING THE AFFECT OF HUMAN BEHAVIOUR RISKS RELATED TO
INFORMATION SECURITY
Certainty of sanction
Clarity of sanction
Severity of sanction
Organizational deterranceInformation security breaches
General Deterrence Theory (GDT): It is a legal theory which is sending messages to the
general public about the risks which are raised from the information security risks due to human
factors. Cheng, Zhai and Smyth (2014) stated that this theory posits the individuals to dissuade
from commitment of antisocial actors throughout use of proper countermeasures. This theory is
used as countermeasures to eliminate the threats and mitigate them. The useful countermeasures
are education, training, backups and tools to mitigate the risks. Tittle (2018) argued that the
theory is used to prevent the threats into general population. This theory stated that the perceived
severity, certainty of the sanctions along with punishment of the influence to make decisions for
engagement of crime by balancing of both cost along with benefits. Martins, Oliveira and
Popovic (2014) studied that information security is focused on the countermeasures of security
and preventive strategies which impact the intention of employees in order to misuse.
Figure 2.4: General Deterrence Theory
(Source: Cheng, Zhai and Smyth 2014, pp-224)

33
MINIMIZING THE AFFECT OF HUMAN BEHAVIOUR RISKS RELATED TO
INFORMATION SECURITY
External
variables
Perceived
usefulness
Perceived
ease of use
Behavioura
l intention
to use
Actual
system use
Technology acceptance theory (TAT): This theory was being introduced by Fred Davis
in the year 1986. Mishra, Akman and Mishra (2014) discussed that it is an information theory
which model how the users are come to accept as well as use of the technology. Venkatesh,
Thong and Xu (2016) suggested that when the users are being presented with new technology,
then there are various factors which influence the decisions about how as well as when it is used.
The aim of this theory is to study how the individual’s perceptions affect intentions to use of the
information technology along with its useful usages. Williams, Rana and Dwivedi (2015) stated
that this theory is an adaption of the theory of reasoned action into the field of information
security. It used of perceived usefulness, perceived ease of use for determining the intention of
individual’s to use of the system for serving the mediator of actual use of system. It is a degree to
which the person is believed that use of the system would raise the performance of the human
behavior (Peltier 2016). Therefore, it explains the interactions of users to use of the information
system along with usage of the human behavior.
MINIMIZING THE AFFECT OF HUMAN BEHAVIOUR RISKS RELATED TO
INFORMATION SECURITY
External
variables
Perceived
usefulness
Perceived
ease of use
Behavioura
l intention
to use
Actual
system use
Technology acceptance theory (TAT): This theory was being introduced by Fred Davis
in the year 1986. Mishra, Akman and Mishra (2014) discussed that it is an information theory
which model how the users are come to accept as well as use of the technology. Venkatesh,
Thong and Xu (2016) suggested that when the users are being presented with new technology,
then there are various factors which influence the decisions about how as well as when it is used.
The aim of this theory is to study how the individual’s perceptions affect intentions to use of the
information technology along with its useful usages. Williams, Rana and Dwivedi (2015) stated
that this theory is an adaption of the theory of reasoned action into the field of information
security. It used of perceived usefulness, perceived ease of use for determining the intention of
individual’s to use of the system for serving the mediator of actual use of system. It is a degree to
which the person is believed that use of the system would raise the performance of the human
behavior (Peltier 2016). Therefore, it explains the interactions of users to use of the information
system along with usage of the human behavior.
Secure Best Marks with AI Grader
Need help grading? Try our AI Grader for instant feedback on your assignments.

34
MINIMIZING THE AFFECT OF HUMAN BEHAVIOUR RISKS RELATED TO
INFORMATION SECURITY
Figure 2.5: Technology acceptance theory
(Source: Williams, Rana and Dwivedi 2015, pp-447)
2.6 Threats to Information Security: Human Behavior a constant risk
2.6.1 Threats with information security
Among evolving with the threats to the information security, the company is accounted
for one constant such as human error. The organizer arranged for the participants into few groups
to facilitate discussion on the threats to the information security (Soomro, Shah and Ahmed
2016). Throughout the threats to the information security along with processes as well as tools,
there is area which remains constant along with consistent with the risks. There are three
information security processes which can able to mitigate the human errors such as:
Classification and restriction access to the data: There are some types of data which are
sensitive than others. It is a way to protect the data of enterprises. The financial data are sensitive
which identifiable information for the clients is. It is the identifiable information for the clients.
After classification of the data, there is determination of requirements to access of sensitive data
(Soska and Christin 2015). There is define of criteria where there is use to segregate of data into
various classifications. There is personally identifiable information for the clients. There is bunch
of data which are not fully protected. Restriction for accessing the data needs to define data roles
as well as permissions (Siponen, Mahmoodand Pahnila 2014). Usually capacities, for example,
validation and session administration are wrongly executed, giving an approach to aggressors to
trade off qualifications, for example, passwords and logins, keys, or session tokens or accepting
another enrolled individual's character.
MINIMIZING THE AFFECT OF HUMAN BEHAVIOUR RISKS RELATED TO
INFORMATION SECURITY
Figure 2.5: Technology acceptance theory
(Source: Williams, Rana and Dwivedi 2015, pp-447)
2.6 Threats to Information Security: Human Behavior a constant risk
2.6.1 Threats with information security
Among evolving with the threats to the information security, the company is accounted
for one constant such as human error. The organizer arranged for the participants into few groups
to facilitate discussion on the threats to the information security (Soomro, Shah and Ahmed
2016). Throughout the threats to the information security along with processes as well as tools,
there is area which remains constant along with consistent with the risks. There are three
information security processes which can able to mitigate the human errors such as:
Classification and restriction access to the data: There are some types of data which are
sensitive than others. It is a way to protect the data of enterprises. The financial data are sensitive
which identifiable information for the clients is. It is the identifiable information for the clients.
After classification of the data, there is determination of requirements to access of sensitive data
(Soska and Christin 2015). There is define of criteria where there is use to segregate of data into
various classifications. There is personally identifiable information for the clients. There is bunch
of data which are not fully protected. Restriction for accessing the data needs to define data roles
as well as permissions (Siponen, Mahmoodand Pahnila 2014). Usually capacities, for example,
validation and session administration are wrongly executed, giving an approach to aggressors to
trade off qualifications, for example, passwords and logins, keys, or session tokens or accepting
another enrolled individual's character.

35
MINIMIZING THE AFFECT OF HUMAN BEHAVIOUR RISKS RELATED TO
INFORMATION SECURITY
Restriction access to sensitive data: There is implementation of process as well as tools
to login for accessing of data. It implies that there is rid to generic user accounts such as admin
accounts. In order to regular access reviews, there should be review to access what data are
required to access the data properly (Teh, Ahmed and D'Arcy 2015). There is review of access
logs for refining to access rules. In some of the information system, there is way around generic
admin accounts which defeat goals to know who can access to the data. The key information
management system in that in which the admin can check to use of generic admin accounts. The
management wants to know who can access to the sensitive data.
Review ways to pass around the sensitive client and financial data: There is review of
ways which can pass around sensitive client as well as financial data. When someone asks
question about accounts for the client, then an email is being sent which provides details of
account which is never sent via use of email (Kampas et al. 2016). It is helpful for spending time
with the client services as well as accounts receivable teams to observe how exchange of
information is done with each others. It is also an issue, where implementation of secure
approach is done for exchange of information.
2.6.2 Human Behavior as aspect of information security
Almost 97 percent of the practitioners of IT security are agreed that the human behavior
is considered as largest security threats by the organizations. Due to increase into internal as well
as external cyber threats, the human behavior as well as technological uncertainty is remained
prominent barriers into the corporate confidence. There is greatest vulnerability of information
security was the human behavior. The percentage is increased from 93 percent in the year 2013
as well as 88% in the year 2014 (Safa, Von Solms and Furnell 2016). The entire program is
being designed for account to the human behavior, and then the company is provided training to
MINIMIZING THE AFFECT OF HUMAN BEHAVIOUR RISKS RELATED TO
INFORMATION SECURITY
Restriction access to sensitive data: There is implementation of process as well as tools
to login for accessing of data. It implies that there is rid to generic user accounts such as admin
accounts. In order to regular access reviews, there should be review to access what data are
required to access the data properly (Teh, Ahmed and D'Arcy 2015). There is review of access
logs for refining to access rules. In some of the information system, there is way around generic
admin accounts which defeat goals to know who can access to the data. The key information
management system in that in which the admin can check to use of generic admin accounts. The
management wants to know who can access to the sensitive data.
Review ways to pass around the sensitive client and financial data: There is review of
ways which can pass around sensitive client as well as financial data. When someone asks
question about accounts for the client, then an email is being sent which provides details of
account which is never sent via use of email (Kampas et al. 2016). It is helpful for spending time
with the client services as well as accounts receivable teams to observe how exchange of
information is done with each others. It is also an issue, where implementation of secure
approach is done for exchange of information.
2.6.2 Human Behavior as aspect of information security
Almost 97 percent of the practitioners of IT security are agreed that the human behavior
is considered as largest security threats by the organizations. Due to increase into internal as well
as external cyber threats, the human behavior as well as technological uncertainty is remained
prominent barriers into the corporate confidence. There is greatest vulnerability of information
security was the human behavior. The percentage is increased from 93 percent in the year 2013
as well as 88% in the year 2014 (Safa, Von Solms and Furnell 2016). The entire program is
being designed for account to the human behavior, and then the company is provided training to

36
MINIMIZING THE AFFECT OF HUMAN BEHAVIOUR RISKS RELATED TO
INFORMATION SECURITY
show the individuals how to act to the policies in place for guiding them (Kim, Yangand Park
2014). Unless the staffs are trained for identification of scams as well as avoid of risks, then
there is elimination of information security issues. Education awareness is not rest for the
internal staffs, and then it rests to the customers as well (Malekian, Hayati and Aarts 2017). In
order to reduce vulnerabilities, 24 percent of the respondents are used of fear, 41 percent are
included of best practices and 83percent are encouraging their employees throughout policies,
awareness as well as training to become part of cyber security solutions (Soomro, Shah and
Ahmed 2016). Security awareness training is provided to the staffs to large proportion of people
to prevent from malicious attachments as well as visiting of suspect websites. When the policies
as well as training are crucial, then there is need to better proof the technology such that when
people do wrong thing, then the malware are not running and achieving the goals (Siponen,
Mahmood and Pahnila 2014). When associated with human conduct aspect of the cyber security,
then it undertakes risky behavior where people can undertake activities as known with risk
associated with actions.
2.7 Information Security Standards and Guidelines
The information security culture is developed into the organization due to some actions
by IT organization. The management of organization implements of information security
components like policies as well as technical security measures which the employees are
interacted. The employees are developed of human behaviors like reporting of security incidents
and sharing of password which lead to threat for secure of information assets (Heckmann, Comes
and Nickel 2015). The organization governs information security by implementing of
information security standards and guidelines. The standards are used by organization to make
sure that it can govern information security from the holistic perspectives, and therefore
MINIMIZING THE AFFECT OF HUMAN BEHAVIOUR RISKS RELATED TO
INFORMATION SECURITY
show the individuals how to act to the policies in place for guiding them (Kim, Yangand Park
2014). Unless the staffs are trained for identification of scams as well as avoid of risks, then
there is elimination of information security issues. Education awareness is not rest for the
internal staffs, and then it rests to the customers as well (Malekian, Hayati and Aarts 2017). In
order to reduce vulnerabilities, 24 percent of the respondents are used of fear, 41 percent are
included of best practices and 83percent are encouraging their employees throughout policies,
awareness as well as training to become part of cyber security solutions (Soomro, Shah and
Ahmed 2016). Security awareness training is provided to the staffs to large proportion of people
to prevent from malicious attachments as well as visiting of suspect websites. When the policies
as well as training are crucial, then there is need to better proof the technology such that when
people do wrong thing, then the malware are not running and achieving the goals (Siponen,
Mahmood and Pahnila 2014). When associated with human conduct aspect of the cyber security,
then it undertakes risky behavior where people can undertake activities as known with risk
associated with actions.
2.7 Information Security Standards and Guidelines
The information security culture is developed into the organization due to some actions
by IT organization. The management of organization implements of information security
components like policies as well as technical security measures which the employees are
interacted. The employees are developed of human behaviors like reporting of security incidents
and sharing of password which lead to threat for secure of information assets (Heckmann, Comes
and Nickel 2015). The organization governs information security by implementing of
information security standards and guidelines. The standards are used by organization to make
sure that it can govern information security from the holistic perspectives, and therefore
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

37
MINIMIZING THE AFFECT OF HUMAN BEHAVIOUR RISKS RELATED TO
INFORMATION SECURITY
minimizing of risks and acceptance level of information security cultures (Pearlson, Saundersand
Galletta 2016).
2.7.1 COBIT
COBIT remains for Control Objectives for Information and Related Technology. It is a
structure made by the ISACA (Information Systems Audit and Control Association) for IT
administration and administration. It was intended to be a steady device for chiefs and permits
crossing over the vital hole between specialized issues, business dangers, and control
prerequisites (Sheeran and Rivis 2017). COBIT is a completely perceived rule that can be
connected to any association in any industry. In general, COBIT guarantees quality, control, and
dependability of data frameworks in association, which is additionally the most imperative part
of each cutting edge business. Today, COBIT is utilized all-inclusive by all IT business process
supervisors to furnish them with a model to convey an incentive to the association and practice
better hazard administration rehearses related with the IT forms (Abbasi, Sarkerand Chiang
2016). The COBIT control show ensures the trustworthiness of the data framework. COBIT is an
IT administration system and supporting toolset that enables chiefs to conquer any hindrance
between control necessities, specialized issues and business dangers. COBIT empowers clear
strategy improvement and great practice for IT control all through associations (Hsu et al. 2015).
COBIT underlines administrative consistence, causes associations to expand the esteem
accomplished from IT, empowers arrangement and improves usage of the endeavors' IT
administration and control system.
COBIT standard helps the IT professionals to fulfill IT governance as well as
management responsibilities particularly in areas of security, control and risk within the
business. This standard is focused on human factors to protect the organization from the
MINIMIZING THE AFFECT OF HUMAN BEHAVIOUR RISKS RELATED TO
INFORMATION SECURITY
minimizing of risks and acceptance level of information security cultures (Pearlson, Saundersand
Galletta 2016).
2.7.1 COBIT
COBIT remains for Control Objectives for Information and Related Technology. It is a
structure made by the ISACA (Information Systems Audit and Control Association) for IT
administration and administration. It was intended to be a steady device for chiefs and permits
crossing over the vital hole between specialized issues, business dangers, and control
prerequisites (Sheeran and Rivis 2017). COBIT is a completely perceived rule that can be
connected to any association in any industry. In general, COBIT guarantees quality, control, and
dependability of data frameworks in association, which is additionally the most imperative part
of each cutting edge business. Today, COBIT is utilized all-inclusive by all IT business process
supervisors to furnish them with a model to convey an incentive to the association and practice
better hazard administration rehearses related with the IT forms (Abbasi, Sarkerand Chiang
2016). The COBIT control show ensures the trustworthiness of the data framework. COBIT is an
IT administration system and supporting toolset that enables chiefs to conquer any hindrance
between control necessities, specialized issues and business dangers. COBIT empowers clear
strategy improvement and great practice for IT control all through associations (Hsu et al. 2015).
COBIT underlines administrative consistence, causes associations to expand the esteem
accomplished from IT, empowers arrangement and improves usage of the endeavors' IT
administration and control system.
COBIT standard helps the IT professionals to fulfill IT governance as well as
management responsibilities particularly in areas of security, control and risk within the
business. This standard is focused on human factors to protect the organization from the

38
MINIMIZING THE AFFECT OF HUMAN BEHAVIOUR RISKS RELATED TO
INFORMATION SECURITY
malicious insider (Pearlson, Saunders and Galletta 2016). Organization development is required
by making changes into the actual behavior of the workforces. Basic training is required for the
human to integrate security awareness in addition to understanding the organizational culture.
Insiders change the human behavior to protect access to the information and confidential data
(Abbasi, Sarker and Chiang 2016). This standard requires increasing awareness of the staffs and
gaining a security value culture among the humans.
Safa et al. (2015) stated that most of the information security risks are related to the
human behavioral weakness which is mitigated with security education as well as controls.
Mishra, Akman and Mishra (2014) argued that social engineering is one tactic to trick the
employees for opening of files and click on links which trigger installation of malware as well as
sharing of sensitive information. With use of right policies as well as tools, it becomes easier to
protect the organization from actions which are intentional as well as unintentional in nature
(Vance et al. 2014). Improvement of risks and encouragement of the employees take role to
maintain of cyber security and help to reduce acts of human errors. Hajliand Lin (2016)
discussed that there are organizations those are concerned with the technical tools for addressing
the human factors. The implication of this study is that awareness of information security
mitigates the security threats which are caused due to human errors and behaviors.
Soomro, Shah and Ahmed (2016) stated that there is value of security behaviors which
are require in culture. Security starts as well as ends with each person those are involved into the
infrastructures, businesses as well as services (Taylor and Bean 2017). In addition to all this,
security policies as well as standards help to educate the employees about importance of
information security awareness which is key significant priority of organization. When the
computers as well as technologies are failed, then it is the responsibility of people those are
MINIMIZING THE AFFECT OF HUMAN BEHAVIOUR RISKS RELATED TO
INFORMATION SECURITY
malicious insider (Pearlson, Saunders and Galletta 2016). Organization development is required
by making changes into the actual behavior of the workforces. Basic training is required for the
human to integrate security awareness in addition to understanding the organizational culture.
Insiders change the human behavior to protect access to the information and confidential data
(Abbasi, Sarker and Chiang 2016). This standard requires increasing awareness of the staffs and
gaining a security value culture among the humans.
Safa et al. (2015) stated that most of the information security risks are related to the
human behavioral weakness which is mitigated with security education as well as controls.
Mishra, Akman and Mishra (2014) argued that social engineering is one tactic to trick the
employees for opening of files and click on links which trigger installation of malware as well as
sharing of sensitive information. With use of right policies as well as tools, it becomes easier to
protect the organization from actions which are intentional as well as unintentional in nature
(Vance et al. 2014). Improvement of risks and encouragement of the employees take role to
maintain of cyber security and help to reduce acts of human errors. Hajliand Lin (2016)
discussed that there are organizations those are concerned with the technical tools for addressing
the human factors. The implication of this study is that awareness of information security
mitigates the security threats which are caused due to human errors and behaviors.
Soomro, Shah and Ahmed (2016) stated that there is value of security behaviors which
are require in culture. Security starts as well as ends with each person those are involved into the
infrastructures, businesses as well as services (Taylor and Bean 2017). In addition to all this,
security policies as well as standards help to educate the employees about importance of
information security awareness which is key significant priority of organization. When the
computers as well as technologies are failed, then it is the responsibility of people those are

39
MINIMIZING THE AFFECT OF HUMAN BEHAVIOUR RISKS RELATED TO
INFORMATION SECURITY
dependent on the services which are provided by the infrastructure (Abbasi, Sarker and Chiang
2016). The human factors are main reason behind issues into the information security system
(Kim, Yang and Park 2014). Information security awareness among the employees of IT
organization helps people to prevent from the issues as well as risks. COBIT standards help to
mitigate the human behavior risks which are occurred into the information security systems.
2.8 Human factors have implications to end user’s behavior
Among the identified threats into the information security, the human behavior is
considered as constant risk. The insider threats are become malicious due to human factors. It is
required to monitor human behavior outside the threat domain to better inform on the mitigation
of threat. Safa, Von Solms and Furnell (2016) stated that technology lowers barrier to malicious
insider activities. Stealing of files from the USB drive are all the human factors and it is caused
due to behavior and attitudes of the human towards the information security risks (Siponen,
Mahmood and Pahnila 2014). The human behavior provides a higher impact on success as well
as failure to secure and protect the information. According to Gerber et al. (2016), human error is
stated as greatest security weakness followed by the technology. The human factors are divided
into two groups such as factors which belong to the management and factors related to end users.
Following are the human factors which have implications to the end user’s behavior such as:
Lack of motivation: Gritzalis et al. (2014) believed that the human are motivated to
adopt secured behaviors and management required to identify what motivates the employees.
Motivation into human behavior is required when the security risks are shared and the users are
involved into decision making to follow the security methods. Layton (2016) believed that the
employees are required to motivate for adoption of secure human behaviors as well as practices
with management require being able to identify what motivates the staffs. According to Sinha
MINIMIZING THE AFFECT OF HUMAN BEHAVIOUR RISKS RELATED TO
INFORMATION SECURITY
dependent on the services which are provided by the infrastructure (Abbasi, Sarker and Chiang
2016). The human factors are main reason behind issues into the information security system
(Kim, Yang and Park 2014). Information security awareness among the employees of IT
organization helps people to prevent from the issues as well as risks. COBIT standards help to
mitigate the human behavior risks which are occurred into the information security systems.
2.8 Human factors have implications to end user’s behavior
Among the identified threats into the information security, the human behavior is
considered as constant risk. The insider threats are become malicious due to human factors. It is
required to monitor human behavior outside the threat domain to better inform on the mitigation
of threat. Safa, Von Solms and Furnell (2016) stated that technology lowers barrier to malicious
insider activities. Stealing of files from the USB drive are all the human factors and it is caused
due to behavior and attitudes of the human towards the information security risks (Siponen,
Mahmood and Pahnila 2014). The human behavior provides a higher impact on success as well
as failure to secure and protect the information. According to Gerber et al. (2016), human error is
stated as greatest security weakness followed by the technology. The human factors are divided
into two groups such as factors which belong to the management and factors related to end users.
Following are the human factors which have implications to the end user’s behavior such as:
Lack of motivation: Gritzalis et al. (2014) believed that the human are motivated to
adopt secured behaviors and management required to identify what motivates the employees.
Motivation into human behavior is required when the security risks are shared and the users are
involved into decision making to follow the security methods. Layton (2016) believed that the
employees are required to motivate for adoption of secure human behaviors as well as practices
with management require being able to identify what motivates the staffs. According to Sinha
Secure Best Marks with AI Grader
Need help grading? Try our AI Grader for instant feedback on your assignments.

40
MINIMIZING THE AFFECT OF HUMAN BEHAVIOUR RISKS RELATED TO
INFORMATION SECURITY
(2015), motivation happens when the security issues are being shared and the users are involved
into making of decisions to follow security procedures.
Lack of awareness: It is related to lack of knowledge about the attacks. The human have
no knowledge on how to see the sign of spyware on the computer and how it is specified the
strong password (Taylor and Bean 2017). It is not protected from identification of theft and the
human have no understanding about how to control access to the computer. Gritzalis et al.
(2014) stated that it is related with lack of knowledge of the human attacks. The examples are
that the users do not know how to see sign of spyware on the computer, and specification of
stronger password. The employees are not aware of how to control of others to computer.
Improper human behavior: Siponen, Mahmood and Pahnila (2014) told that behavior is
interpreted as the behavior of human are not good. Hsu et al. (2015) claimed that documented
requirements of expected behavior of information security provide small effect on the behavior
of users. The users are considered as user involving approach to become effective to influence
the awareness of user in addition to behavior. It is interpreted as the risky behavior of users and
loss of prevention of human behavior. Vance et al. (2014) claimed that documented requirements
of expected information security behaviors provide few effects on the user behavior. The users
are considered user involving approach to become more effective to influence the user awareness
as well as behavior.
Inadequate use of technology: The technology is not succeeding to solve the risks
related to information security without cooperation of human along with effective use of the
technology (Abbasi, Sarker and Chiang 2016). The examples of the technology risks are
unauthorized re-configuration of the information system, access to the passwords, retrieve of the
MINIMIZING THE AFFECT OF HUMAN BEHAVIOUR RISKS RELATED TO
INFORMATION SECURITY
(2015), motivation happens when the security issues are being shared and the users are involved
into making of decisions to follow security procedures.
Lack of awareness: It is related to lack of knowledge about the attacks. The human have
no knowledge on how to see the sign of spyware on the computer and how it is specified the
strong password (Taylor and Bean 2017). It is not protected from identification of theft and the
human have no understanding about how to control access to the computer. Gritzalis et al.
(2014) stated that it is related with lack of knowledge of the human attacks. The examples are
that the users do not know how to see sign of spyware on the computer, and specification of
stronger password. The employees are not aware of how to control of others to computer.
Improper human behavior: Siponen, Mahmood and Pahnila (2014) told that behavior is
interpreted as the behavior of human are not good. Hsu et al. (2015) claimed that documented
requirements of expected behavior of information security provide small effect on the behavior
of users. The users are considered as user involving approach to become effective to influence
the awareness of user in addition to behavior. It is interpreted as the risky behavior of users and
loss of prevention of human behavior. Vance et al. (2014) claimed that documented requirements
of expected information security behaviors provide few effects on the user behavior. The users
are considered user involving approach to become more effective to influence the user awareness
as well as behavior.
Inadequate use of technology: The technology is not succeeding to solve the risks
related to information security without cooperation of human along with effective use of the
technology (Abbasi, Sarker and Chiang 2016). The examples of the technology risks are
unauthorized re-configuration of the information system, access to the passwords, retrieve of the

41
MINIMIZING THE AFFECT OF HUMAN BEHAVIOUR RISKS RELATED TO
INFORMATION SECURITY
improper information and others. The technology is not succeeding to solve the problems related
to information technology without human cooperation and use of technology. Examples of
improper use of technology are making of unauthorized reconfigurations of the systems, access
to the other’s password as well as retrieve of improper information. Kautonen, Gelderen and
Fink (2015) believed that the IT security basics such as threats, risks allow the individuals to
adapt of constant changes and allow predicting expected behavior.
Belief: Abbasi, Sarker and Chiang (2016) conducted qualitative study about user’s view
on the information security as well as beliefs. The users believed that installation of anti-virus
software are not crucial to the information. The users are ready to click on links when they
receive email from the unknown persons.
Computer security risks: There are some factors which are computer security risk factors
such as error and omission, denial of services, unauthorized access, and identification of theft,
malware as well as unauthorized copy (Sheeran and Rivis 2017).
In the past decades, the information security as well as human behavior is focused on the
behavioral models and theories. In most of the theories, intentions rather than actual human
behavior are to be assessed due to difficulty to observe the security behaviors (Pearlson,
Saunders and Galletta 2016). The theory of reasoned action is based on two notions such as
people those are reasonable, make use of information when deciding among the human
behaviors. It is also based on people those consider implications of the human behaviors. Errors
from the human side are constant among the threats into the information security. Safa, Von
Solms and Furnell (2016) analyzed that most of the respondents agreed to the statement that
biggest vulnerabilities is the human behavior. This theory is being designed to account towards
MINIMIZING THE AFFECT OF HUMAN BEHAVIOUR RISKS RELATED TO
INFORMATION SECURITY
improper information and others. The technology is not succeeding to solve the problems related
to information technology without human cooperation and use of technology. Examples of
improper use of technology are making of unauthorized reconfigurations of the systems, access
to the other’s password as well as retrieve of improper information. Kautonen, Gelderen and
Fink (2015) believed that the IT security basics such as threats, risks allow the individuals to
adapt of constant changes and allow predicting expected behavior.
Belief: Abbasi, Sarker and Chiang (2016) conducted qualitative study about user’s view
on the information security as well as beliefs. The users believed that installation of anti-virus
software are not crucial to the information. The users are ready to click on links when they
receive email from the unknown persons.
Computer security risks: There are some factors which are computer security risk factors
such as error and omission, denial of services, unauthorized access, and identification of theft,
malware as well as unauthorized copy (Sheeran and Rivis 2017).
In the past decades, the information security as well as human behavior is focused on the
behavioral models and theories. In most of the theories, intentions rather than actual human
behavior are to be assessed due to difficulty to observe the security behaviors (Pearlson,
Saunders and Galletta 2016). The theory of reasoned action is based on two notions such as
people those are reasonable, make use of information when deciding among the human
behaviors. It is also based on people those consider implications of the human behaviors. Errors
from the human side are constant among the threats into the information security. Safa, Von
Solms and Furnell (2016) analyzed that most of the respondents agreed to the statement that
biggest vulnerabilities is the human behavior. This theory is being designed to account towards

42
MINIMIZING THE AFFECT OF HUMAN BEHAVIOUR RISKS RELATED TO
INFORMATION SECURITY
the human behavior, then the organization is provided training to the individuals on how to act as
well as place the information security policies to guide them. The organization is required to
concern about the human behavior tools require addressing the human factors. In order to
improve the information security, human behavior is required to be changed (Abbasi, Sarker and
Chiang 2016). The decision of individuals for engaging into the human behavior is concerned on
outcomes of the individual expectations will come as result to perform the behavior. With use of
this particular theory, the individuals are motivated to perform actions to minimize the human
factors from the context of information security. According to this theory, intention to do certain
behavior precedes the definite behavior (Safa, Von Solms and Furnell 2016). The behavioral
intention is a key significant requirement to this theory as this intention is being determined by
attitudes to the human behaviors along with subjective norms.
2.9 Human behaviour risks related to information security
As organizations are made up of people, therefore human related threats are pervasive at
these levels. Siponen, Mahmood and Pahnila (2014) stated that degree of human related risks is
inevitable, therefore the proper way to mitigate the structure of organization such that no single
person causes critical damages. Following are the information security risks which are identified
into most of the organization such as:
Lack of management support: Soska and Christin (2015) stated that the values which
create stronger security environment come from the management and organizational culture.
Investment into the IT security reduces the cost of organizational finances along with reputation
when any human related breaches are occurred (Safa, Von Solms and Furnell 2016). It is also
termed as insider threats as the members of management are not interested to support and
communicate throughout the organization.
MINIMIZING THE AFFECT OF HUMAN BEHAVIOUR RISKS RELATED TO
INFORMATION SECURITY
the human behavior, then the organization is provided training to the individuals on how to act as
well as place the information security policies to guide them. The organization is required to
concern about the human behavior tools require addressing the human factors. In order to
improve the information security, human behavior is required to be changed (Abbasi, Sarker and
Chiang 2016). The decision of individuals for engaging into the human behavior is concerned on
outcomes of the individual expectations will come as result to perform the behavior. With use of
this particular theory, the individuals are motivated to perform actions to minimize the human
factors from the context of information security. According to this theory, intention to do certain
behavior precedes the definite behavior (Safa, Von Solms and Furnell 2016). The behavioral
intention is a key significant requirement to this theory as this intention is being determined by
attitudes to the human behaviors along with subjective norms.
2.9 Human behaviour risks related to information security
As organizations are made up of people, therefore human related threats are pervasive at
these levels. Siponen, Mahmood and Pahnila (2014) stated that degree of human related risks is
inevitable, therefore the proper way to mitigate the structure of organization such that no single
person causes critical damages. Following are the information security risks which are identified
into most of the organization such as:
Lack of management support: Soska and Christin (2015) stated that the values which
create stronger security environment come from the management and organizational culture.
Investment into the IT security reduces the cost of organizational finances along with reputation
when any human related breaches are occurred (Safa, Von Solms and Furnell 2016). It is also
termed as insider threats as the members of management are not interested to support and
communicate throughout the organization.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

43
MINIMIZING THE AFFECT OF HUMAN BEHAVIOUR RISKS RELATED TO
INFORMATION SECURITY
Provide password to any unauthorized person: The unauthorized person can access to
the information when any human provide their password details to them (Ab Rahman and Choo
2015). The person can hack the information across the internet by stealing of the account or
database passwords. It causes loss of the data in addition to information from the database
system. The personal as well as financial information are into the documents of the computer,
and then at that instant it is possible that someone hacks or steals it from the computer through
use of some hacking software (Siponen, Mahmood and Pahnila 2014).
Unaware of information security policies: Any careless and uninformed staffs impact
the security of company as it causes a serious security breaches. Sometimes, the employees are
not aware of the fact that whom they will provide the information about any confidential data
and information (Kim, Yang and Park 2014). The staffs are not aware of the information security
policies; therefore they share information with others.
2.10 Organization Information Security Culture
Into the organization, there is requirement of strong security culture into the mode of
operation of the organization. Malekian, Hayati and Aarts (2017) stated that a sustainable
security culture is required to secure the information in addition to the data. When the security
culture is being sustainable, then it is transforming the security from one of the event to the
lifecycle which generates of security. The information security is not relying on the technology
(Siponen, Mahmood and Pahnila 2014). The culture is encouraged the employees for complying
the informational policies related to collect in addition to manage the information which will
improve the information security.
MINIMIZING THE AFFECT OF HUMAN BEHAVIOUR RISKS RELATED TO
INFORMATION SECURITY
Provide password to any unauthorized person: The unauthorized person can access to
the information when any human provide their password details to them (Ab Rahman and Choo
2015). The person can hack the information across the internet by stealing of the account or
database passwords. It causes loss of the data in addition to information from the database
system. The personal as well as financial information are into the documents of the computer,
and then at that instant it is possible that someone hacks or steals it from the computer through
use of some hacking software (Siponen, Mahmood and Pahnila 2014).
Unaware of information security policies: Any careless and uninformed staffs impact
the security of company as it causes a serious security breaches. Sometimes, the employees are
not aware of the fact that whom they will provide the information about any confidential data
and information (Kim, Yang and Park 2014). The staffs are not aware of the information security
policies; therefore they share information with others.
2.10 Organization Information Security Culture
Into the organization, there is requirement of strong security culture into the mode of
operation of the organization. Malekian, Hayati and Aarts (2017) stated that a sustainable
security culture is required to secure the information in addition to the data. When the security
culture is being sustainable, then it is transforming the security from one of the event to the
lifecycle which generates of security. The information security is not relying on the technology
(Siponen, Mahmood and Pahnila 2014). The culture is encouraged the employees for complying
the informational policies related to collect in addition to manage the information which will
improve the information security.

44
MINIMIZING THE AFFECT OF HUMAN BEHAVIOUR RISKS RELATED TO
INFORMATION SECURITY
2.10.1 Organizational culture
Pearlson, Saunders and Galletta (2016) stated that organizational culture is included of
expectations of organization, experiences as well as values which hold together, interactions into
the outside world along with future expectations. The organizational culture is affected its
productivity, performance along with guidelines on the customer cares. For each of the
organization, organizational culture is different and one of the critical things is to change.
2.10.2 Information security culture
Siponen, Mahmood and Pahnila (2014) discussed that information security culture is
based on how the things are to be done within the organization regards to the information
security, with aim to protect the information assets along with influence of the employee’s
security behavior. Information security culture is a part of the organizational culture as the
security of information becomes an organizational function. In order to gain a secured
environment for the information assets, the practices of information security becomes a part of
corporate culture within the organization (Kim, Yang and Park 2014). The culture guides
activities within the organization and the employees by placing of constraints on the
organizational activities and behavior of employees. The culture influences the human behavior;
therefore there is a requirement to establish information security behavior of the organizational
employees. Malekian, Hayati and Aarts (2017) defined that information security culture as
perceptions, attitudes along with assumptions accepted by employees within the organization
based on information security. The culture is developed as result of employee’s interactions with
the information security controls.
Abbasi, Sarker and Chiang (2016) suggested that the information security culture is
considered as accepted behavior as well as actions by the employees. The culture is involved of
MINIMIZING THE AFFECT OF HUMAN BEHAVIOUR RISKS RELATED TO
INFORMATION SECURITY
2.10.1 Organizational culture
Pearlson, Saunders and Galletta (2016) stated that organizational culture is included of
expectations of organization, experiences as well as values which hold together, interactions into
the outside world along with future expectations. The organizational culture is affected its
productivity, performance along with guidelines on the customer cares. For each of the
organization, organizational culture is different and one of the critical things is to change.
2.10.2 Information security culture
Siponen, Mahmood and Pahnila (2014) discussed that information security culture is
based on how the things are to be done within the organization regards to the information
security, with aim to protect the information assets along with influence of the employee’s
security behavior. Information security culture is a part of the organizational culture as the
security of information becomes an organizational function. In order to gain a secured
environment for the information assets, the practices of information security becomes a part of
corporate culture within the organization (Kim, Yang and Park 2014). The culture guides
activities within the organization and the employees by placing of constraints on the
organizational activities and behavior of employees. The culture influences the human behavior;
therefore there is a requirement to establish information security behavior of the organizational
employees. Malekian, Hayati and Aarts (2017) defined that information security culture as
perceptions, attitudes along with assumptions accepted by employees within the organization
based on information security. The culture is developed as result of employee’s interactions with
the information security controls.
Abbasi, Sarker and Chiang (2016) suggested that the information security culture is
considered as accepted behavior as well as actions by the employees. The culture is involved of

45
MINIMIZING THE AFFECT OF HUMAN BEHAVIOUR RISKS RELATED TO
INFORMATION SECURITY
identifying the security related issues, beliefs along with values of group that shape the security
related behaviors. Safa, Von Solmsand Furnell (2016) defined the information security culture as
totality of the human attributes like behaviors, attitudes as well as beliefs held by the
organization. This could impact the security of the organization which may be or not may be
explicit linked to the impact (Siponen, Mahmood and Pahnila 2014). The procedures which the
employees are using into their daily work represent weakest link into the chain of information
security. It is required to develop as well as improve the information security culture throughout
structured model to address the human behavior.
2.10.3 Cultural Change
Cultural change is such a term which is used into policy making emphasizes influence of
the cultural capital on the individuals along with community behavior. Vance et al. (2014) stated
that it places of stress on social along with cultural capital determinants of the decision making to
interact with the employees (Pearlson, Saunders and Galletta 2016). The cultural capital
influences include role of the management.
2.10.4 Cultural Impact on Human Behavior
Culture is an influence into the human behavior as the human culture is based on belief,
practices, laws, language and attributes that make people unique from each other people. Culture
plays a key significant role to determine how the individuals are behaving in the business
environment. Layton (2016) argued that human behavior is being affected by the culture. Abbasi,
Sarker and Chiang (2016) suggested that culture is used to explain the human behavior; therefore
there is understanding of the cultural traits which impacts the behavior. The culture is looked at
the society’s belief system, laws, language as well as attitudinal variables that make people
innovative from others. Culture plays a key significant role into shaping society as well as
MINIMIZING THE AFFECT OF HUMAN BEHAVIOUR RISKS RELATED TO
INFORMATION SECURITY
identifying the security related issues, beliefs along with values of group that shape the security
related behaviors. Safa, Von Solmsand Furnell (2016) defined the information security culture as
totality of the human attributes like behaviors, attitudes as well as beliefs held by the
organization. This could impact the security of the organization which may be or not may be
explicit linked to the impact (Siponen, Mahmood and Pahnila 2014). The procedures which the
employees are using into their daily work represent weakest link into the chain of information
security. It is required to develop as well as improve the information security culture throughout
structured model to address the human behavior.
2.10.3 Cultural Change
Cultural change is such a term which is used into policy making emphasizes influence of
the cultural capital on the individuals along with community behavior. Vance et al. (2014) stated
that it places of stress on social along with cultural capital determinants of the decision making to
interact with the employees (Pearlson, Saunders and Galletta 2016). The cultural capital
influences include role of the management.
2.10.4 Cultural Impact on Human Behavior
Culture is an influence into the human behavior as the human culture is based on belief,
practices, laws, language and attributes that make people unique from each other people. Culture
plays a key significant role to determine how the individuals are behaving in the business
environment. Layton (2016) argued that human behavior is being affected by the culture. Abbasi,
Sarker and Chiang (2016) suggested that culture is used to explain the human behavior; therefore
there is understanding of the cultural traits which impacts the behavior. The culture is looked at
the society’s belief system, laws, language as well as attitudinal variables that make people
innovative from others. Culture plays a key significant role into shaping society as well as
Secure Best Marks with AI Grader
Need help grading? Try our AI Grader for instant feedback on your assignments.

46
MINIMIZING THE AFFECT OF HUMAN BEHAVIOUR RISKS RELATED TO
INFORMATION SECURITY
country. Taylor and Bean (2017) carried out a research study to understand role of organizational
culture to enhance the organizational health. Heckmann, Comes and Nickel (2015) suggested
that it is ability to achieve of goals based on environment which seeks to improve the
organizational performance along with support the employee’s well-being. Safa, Von Solms and
Furnell (2016) examined that the organizational culture is required changes into the
organization’s culture in order to avoid tensions as well as conflict into the organization.
Pearlson, Saunders and Galletta (2016) observed that the political and conflict are being
associated with the organizational culture. Siponen, Mahmood and Pahnila (2014) stressed that
the individual behavior into the organization is being driven by individual’s employee’s
motivation. Cheng, Zhai and Smyth (2014) highlighted the culture of organization is being
opened to change into human behavior. Mishra, Akman and Mishra (2014) investigated that
organizational culture is based on perspectives of organization’s values as well as norms.
2.11 Information Security Policy
2.11.1 What is an Information Security Policy
Ifinedo (2014) stated that information security policy is the set of policies which are
issued by the organization to make sure that the users of information technology is complied
with the rules and guidelines related to security of information stored at any point within the
network. Each of the organization is required to protect their data and control those data which
are distributed within as well as without the organizational boundaries. Gerber et al. (2016)
argued that the policies are used to ensure the users and networks that the stored data are secured
into the organizational boundaries. It is a method which defines how the information is being
protected and consequences violated the rules to maintain access to the information. Siponen,
Mahmood and Pahnila (2014) discussed that effective IT security policy is a model for
MINIMIZING THE AFFECT OF HUMAN BEHAVIOUR RISKS RELATED TO
INFORMATION SECURITY
country. Taylor and Bean (2017) carried out a research study to understand role of organizational
culture to enhance the organizational health. Heckmann, Comes and Nickel (2015) suggested
that it is ability to achieve of goals based on environment which seeks to improve the
organizational performance along with support the employee’s well-being. Safa, Von Solms and
Furnell (2016) examined that the organizational culture is required changes into the
organization’s culture in order to avoid tensions as well as conflict into the organization.
Pearlson, Saunders and Galletta (2016) observed that the political and conflict are being
associated with the organizational culture. Siponen, Mahmood and Pahnila (2014) stressed that
the individual behavior into the organization is being driven by individual’s employee’s
motivation. Cheng, Zhai and Smyth (2014) highlighted the culture of organization is being
opened to change into human behavior. Mishra, Akman and Mishra (2014) investigated that
organizational culture is based on perspectives of organization’s values as well as norms.
2.11 Information Security Policy
2.11.1 What is an Information Security Policy
Ifinedo (2014) stated that information security policy is the set of policies which are
issued by the organization to make sure that the users of information technology is complied
with the rules and guidelines related to security of information stored at any point within the
network. Each of the organization is required to protect their data and control those data which
are distributed within as well as without the organizational boundaries. Gerber et al. (2016)
argued that the policies are used to ensure the users and networks that the stored data are secured
into the organizational boundaries. It is a method which defines how the information is being
protected and consequences violated the rules to maintain access to the information. Siponen,
Mahmood and Pahnila (2014) discussed that effective IT security policy is a model for

47
MINIMIZING THE AFFECT OF HUMAN BEHAVIOUR RISKS RELATED TO
INFORMATION SECURITY
organizational culture where the rules as well as procedures are driven from the employee’s
approach to the information. It is such a document for any organization that is cultivated from
human’s perspectives on tolerance of risks.
The main objective of IT security policy is confidentiality, integrity as well as availability
of the information used by the organizational staffs. The information security policies is linked
with the subjective norms and attributes as change into the policy may affect an organizational
change which may be result into violation within the organization (Teh, Ahmed and D'Arcy
2015). The personal norms, information security standards, benefits, attitudes as well as values
matter how the employees are perceived into the information security issues those related to the
information security policies. The privacy is being achieved by two of the approaches such as
protection into the organization’s operational practices as well as second approach is
maintenance along with control of data management procedures throughout the product life cycle
(Crossler et al. 2013). The approaches are used to promote the employee’s informational security
awareness which is implemented of effective educational program. Training is provided to
promote in addition to enhance informational security.
2.11.2 The Needs for Information Security Policy
Information is always an important asset into the organization and therefore it is required
to implement information security policy to protect the data along with strengthen position into
the market (Heckmann, Comes and Nickel 2015). There are four main reasons behind
implementation of information security policy into the organization. With the policy into
information security, all the employees should bring to speed with the company guidelines and
increased the organizational efficiency (Kim, Yang and Park 2014). The policies inform the
employees of own individual duties, and tell them what they can as well as cannot do based on
MINIMIZING THE AFFECT OF HUMAN BEHAVIOUR RISKS RELATED TO
INFORMATION SECURITY
organizational culture where the rules as well as procedures are driven from the employee’s
approach to the information. It is such a document for any organization that is cultivated from
human’s perspectives on tolerance of risks.
The main objective of IT security policy is confidentiality, integrity as well as availability
of the information used by the organizational staffs. The information security policies is linked
with the subjective norms and attributes as change into the policy may affect an organizational
change which may be result into violation within the organization (Teh, Ahmed and D'Arcy
2015). The personal norms, information security standards, benefits, attitudes as well as values
matter how the employees are perceived into the information security issues those related to the
information security policies. The privacy is being achieved by two of the approaches such as
protection into the organization’s operational practices as well as second approach is
maintenance along with control of data management procedures throughout the product life cycle
(Crossler et al. 2013). The approaches are used to promote the employee’s informational security
awareness which is implemented of effective educational program. Training is provided to
promote in addition to enhance informational security.
2.11.2 The Needs for Information Security Policy
Information is always an important asset into the organization and therefore it is required
to implement information security policy to protect the data along with strengthen position into
the market (Heckmann, Comes and Nickel 2015). There are four main reasons behind
implementation of information security policy into the organization. With the policy into
information security, all the employees should bring to speed with the company guidelines and
increased the organizational efficiency (Kim, Yang and Park 2014). The policies inform the
employees of own individual duties, and tell them what they can as well as cannot do based on

48
MINIMIZING THE AFFECT OF HUMAN BEHAVIOUR RISKS RELATED TO
INFORMATION SECURITY
the sensitive information. The errors from human side are inevitable and the security of system is
being compromised. The information security policy is backed up disciplinary actions and
supported case in court of law (Teh, Ahmed and D'Arcy 2015). It is acted as contract which
proves that the organization should take steps to protect the intellectual property. The policy
related to information security ensures that the information is being accessible only to the
authorized person those have access to the data. It protects the assets against the illegal
disclosure (Hsu et al. 2015). It is required to safe accuracy along with completeness of the
information. A well organized information security policy is an educational document for the
organizational employees that inform them about important responsibilities to be taken to protect
the organizational data.
2.11.3 Compliance with information security policy
The information security policy compliance is protecting the information assets into the
organizations. The information security has significant effect on the attitudes of employee
towards the compliance into the organizational security policies (Sinha 2015). The attitude of
employee has significant effect on behavioral intention regarding the compliance of information
security. Kampas et al. (2016) illustrated that it is a key factor to reduce the risks. Understanding
of employee’s compliance behavior is a step to leverage worker assets towards reduction of
risks. The main aim of those policies is to design and provide the employees with the guidelines
on secure the information resources while performing job into the information security. The
compliance of employee is required to prevent as well as reduce the misuse of information
system resources in addition to abuse by the insiders (Safa, Von Solms and Furnell 2016).
Behavioral theories are employed to study the human’s compliance intentions with prevention of
MINIMIZING THE AFFECT OF HUMAN BEHAVIOUR RISKS RELATED TO
INFORMATION SECURITY
the sensitive information. The errors from human side are inevitable and the security of system is
being compromised. The information security policy is backed up disciplinary actions and
supported case in court of law (Teh, Ahmed and D'Arcy 2015). It is acted as contract which
proves that the organization should take steps to protect the intellectual property. The policy
related to information security ensures that the information is being accessible only to the
authorized person those have access to the data. It protects the assets against the illegal
disclosure (Hsu et al. 2015). It is required to safe accuracy along with completeness of the
information. A well organized information security policy is an educational document for the
organizational employees that inform them about important responsibilities to be taken to protect
the organizational data.
2.11.3 Compliance with information security policy
The information security policy compliance is protecting the information assets into the
organizations. The information security has significant effect on the attitudes of employee
towards the compliance into the organizational security policies (Sinha 2015). The attitude of
employee has significant effect on behavioral intention regarding the compliance of information
security. Kampas et al. (2016) illustrated that it is a key factor to reduce the risks. Understanding
of employee’s compliance behavior is a step to leverage worker assets towards reduction of
risks. The main aim of those policies is to design and provide the employees with the guidelines
on secure the information resources while performing job into the information security. The
compliance of employee is required to prevent as well as reduce the misuse of information
system resources in addition to abuse by the insiders (Safa, Von Solms and Furnell 2016).
Behavioral theories are employed to study the human’s compliance intentions with prevention of
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

49
MINIMIZING THE AFFECT OF HUMAN BEHAVIOUR RISKS RELATED TO
INFORMATION SECURITY
misuse of information system. Therefore, proper actions are taken by the organization to comply
with the associated information security issues.
Pearlson, Saunders and Galletta (2016) stated that the professionals are being dedicated
to maintain confidentiality with the organizational information but it resistant to maintain
information security environments. Misuse of information security is deterrence as well as
compliance to promote factors which affect the information security complaints behavior (Soska
and Christin 2015). Based on the theory of planned behavior, protection motivation theory, the
behavioral factors are identified which influence the compliance with the information security
policy. Based on theory of planned behavior, the human’s attitudes towards compliance and
belief are believed to determine intention for complying with information security policy.
Dependent on the protection motivation theory, expected efficacy impacts intentions of
compliance. Taylor, Fritsch and Liederbach (2014) mentioned that main requirement of this
research study is to identify the human factors perspectives of information security that connect
end users behaviors along with compliance with the information security policy within the
organization. Mistakes and human errors are to be mitigated so as to get a proper information
security policy.
2.12 Human Computer Interaction (HCI) and Behaviors Change
Despite the huge rise into the media reporting of the information security, the human
behaviors are demonstrated lack of information security awareness. The human-computer
interaction is required in the organization to aware the individuals about the security threats
which are raised due to human errors (Montano and Kasprzyk 2015). The HCI researchers are
engaged into design of such a system which is required for the behavior changes: how the
interventions for the behavior changes are evaluated based on context of HCI research. Mishra,
MINIMIZING THE AFFECT OF HUMAN BEHAVIOUR RISKS RELATED TO
INFORMATION SECURITY
misuse of information system. Therefore, proper actions are taken by the organization to comply
with the associated information security issues.
Pearlson, Saunders and Galletta (2016) stated that the professionals are being dedicated
to maintain confidentiality with the organizational information but it resistant to maintain
information security environments. Misuse of information security is deterrence as well as
compliance to promote factors which affect the information security complaints behavior (Soska
and Christin 2015). Based on the theory of planned behavior, protection motivation theory, the
behavioral factors are identified which influence the compliance with the information security
policy. Based on theory of planned behavior, the human’s attitudes towards compliance and
belief are believed to determine intention for complying with information security policy.
Dependent on the protection motivation theory, expected efficacy impacts intentions of
compliance. Taylor, Fritsch and Liederbach (2014) mentioned that main requirement of this
research study is to identify the human factors perspectives of information security that connect
end users behaviors along with compliance with the information security policy within the
organization. Mistakes and human errors are to be mitigated so as to get a proper information
security policy.
2.12 Human Computer Interaction (HCI) and Behaviors Change
Despite the huge rise into the media reporting of the information security, the human
behaviors are demonstrated lack of information security awareness. The human-computer
interaction is required in the organization to aware the individuals about the security threats
which are raised due to human errors (Montano and Kasprzyk 2015). The HCI researchers are
engaged into design of such a system which is required for the behavior changes: how the
interventions for the behavior changes are evaluated based on context of HCI research. Mishra,

50
MINIMIZING THE AFFECT OF HUMAN BEHAVIOUR RISKS RELATED TO
INFORMATION SECURITY
Akman and Mishra (2014) concluded that behavioral changes are required in an organization so
that all the individuals should aware of the information security threats. Kautonen, Gelderen and
Fink (2015) stated that behavior changes are referred to the transformational in addition to
modifications of the human behavior. In this research study, behavioral change theories are to be
explained to make the behaviors changes among people of organization. Each of the theories is
focused on various factors to attempt and explain the behavioral changes. Self-efficacy is the
impression of individuals to perform and demand the challenging tasks (Sheeran and Rivis
2017). The individual’s impression is based on some factors such as individual’s prior success
into the task, physiological state of the individuals along with outside sources of the persuasions.
Tsai et al. (2016) argued that self-efficacy is predictive of amount of efforts of individuals which
will expand to initiate along with maintain behavioral changes.
Martins, Oliveira and Popovic (2014) stated that theory of reasoned actions is assumed
that the individuals are considered consequences of behavior before performing the specific
human behavior. The result of this theory is that intention is a factor to determine behavior along
with the behavioral changes. The intention is developed from the perceptions of individuals of
behavior as positive as well as negative together with the impression of individuals. Therefore,
the personal attitude as well as social pressure shapes the intention that is required to perform the
behavior along with the behavioral changes (Williams, Rana and Dwivedi 2015). As per the
theory of planned behavior, it is based on role of intention within human behavior performance;
however it is intended to cover the cases in which the persons are not under control of factors to
affect the actual performance of the behavior. This theory stated that incidence of actual behavior
performance is to be proportional to the amount of control as the individual processes over the
human behavior along with strength of the individual’s intention to perform the behavior
MINIMIZING THE AFFECT OF HUMAN BEHAVIOUR RISKS RELATED TO
INFORMATION SECURITY
Akman and Mishra (2014) concluded that behavioral changes are required in an organization so
that all the individuals should aware of the information security threats. Kautonen, Gelderen and
Fink (2015) stated that behavior changes are referred to the transformational in addition to
modifications of the human behavior. In this research study, behavioral change theories are to be
explained to make the behaviors changes among people of organization. Each of the theories is
focused on various factors to attempt and explain the behavioral changes. Self-efficacy is the
impression of individuals to perform and demand the challenging tasks (Sheeran and Rivis
2017). The individual’s impression is based on some factors such as individual’s prior success
into the task, physiological state of the individuals along with outside sources of the persuasions.
Tsai et al. (2016) argued that self-efficacy is predictive of amount of efforts of individuals which
will expand to initiate along with maintain behavioral changes.
Martins, Oliveira and Popovic (2014) stated that theory of reasoned actions is assumed
that the individuals are considered consequences of behavior before performing the specific
human behavior. The result of this theory is that intention is a factor to determine behavior along
with the behavioral changes. The intention is developed from the perceptions of individuals of
behavior as positive as well as negative together with the impression of individuals. Therefore,
the personal attitude as well as social pressure shapes the intention that is required to perform the
behavior along with the behavioral changes (Williams, Rana and Dwivedi 2015). As per the
theory of planned behavior, it is based on role of intention within human behavior performance;
however it is intended to cover the cases in which the persons are not under control of factors to
affect the actual performance of the behavior. This theory stated that incidence of actual behavior
performance is to be proportional to the amount of control as the individual processes over the
human behavior along with strength of the individual’s intention to perform the behavior

51
MINIMIZING THE AFFECT OF HUMAN BEHAVIOUR RISKS RELATED TO
INFORMATION SECURITY
(Katzenbeisser and Petitcolas 2016). The most important theory is technology acceptance theory
which is adapted for reasoned action into the field of information security. It is being used of
perceived usefulness, perceived ease of use for determining the intention of individual’s to use of
the system for serving the mediator of actual use of system (Safa, Von Solms and Furnell 2016).
It is a degree to which the person is believed that use of the system would raise the performance
of the human behavior.
2.13 Insider Threats Behavior
The issues which the insiders pose into the IT organization are greater concern as well as
focus on research. In this particular section, the researcher is interested to understand information
use behavior of the malicious insiders. The insider may be employee, contractor, vendor as well
as visitor those are access of internal privileges (Safa, Von Solms and Furnell 2016). The insider
threat is such people those can authorize access to the confidential resources such as facilities,
networks, systems as well as equipments those use access to harm the security of the sensitive
data. The insider threat concerns are related to criminal activities include of theft as well as
fraud, safety include of active shooter incidents and financial harms by stealing of organizational
sensitive data (Alexander 2014). The insider threats are not limited to only contractors as well as
employees. The business is required to develop the close relationships with the third party
vendors as well as partners who need access to the information (Kim, Yang and Park 2014).
Most of the organizations are not aware of the consequences of risks with respect to the data
breaches. The insider threats provide an impact on the sensitive data. The security of the
enterprise is focused on safeguarding to prevent the hackers from penetrating the network as well
as gain of access to the data (Taylor and Bean 2017). The insider threats are taking place when
the trusted insider with access to the organization trusted data negatively compromise to safety as
MINIMIZING THE AFFECT OF HUMAN BEHAVIOUR RISKS RELATED TO
INFORMATION SECURITY
(Katzenbeisser and Petitcolas 2016). The most important theory is technology acceptance theory
which is adapted for reasoned action into the field of information security. It is being used of
perceived usefulness, perceived ease of use for determining the intention of individual’s to use of
the system for serving the mediator of actual use of system (Safa, Von Solms and Furnell 2016).
It is a degree to which the person is believed that use of the system would raise the performance
of the human behavior.
2.13 Insider Threats Behavior
The issues which the insiders pose into the IT organization are greater concern as well as
focus on research. In this particular section, the researcher is interested to understand information
use behavior of the malicious insiders. The insider may be employee, contractor, vendor as well
as visitor those are access of internal privileges (Safa, Von Solms and Furnell 2016). The insider
threat is such people those can authorize access to the confidential resources such as facilities,
networks, systems as well as equipments those use access to harm the security of the sensitive
data. The insider threat concerns are related to criminal activities include of theft as well as
fraud, safety include of active shooter incidents and financial harms by stealing of organizational
sensitive data (Alexander 2014). The insider threats are not limited to only contractors as well as
employees. The business is required to develop the close relationships with the third party
vendors as well as partners who need access to the information (Kim, Yang and Park 2014).
Most of the organizations are not aware of the consequences of risks with respect to the data
breaches. The insider threats provide an impact on the sensitive data. The security of the
enterprise is focused on safeguarding to prevent the hackers from penetrating the network as well
as gain of access to the data (Taylor and Bean 2017). The insider threats are taking place when
the trusted insider with access to the organization trusted data negatively compromise to safety as
Secure Best Marks with AI Grader
Need help grading? Try our AI Grader for instant feedback on your assignments.

52
MINIMIZING THE AFFECT OF HUMAN BEHAVIOUR RISKS RELATED TO
INFORMATION SECURITY
well as security of the information. The insider threats are minimized when the data are moved
outside the firewall. The business is required to secure and exchange of sensitive information
with the external third parties on daily basis (Safa, Von Solms and Furnell 2016).
Hajli and Lin (2016) stated that the insider threats impact on access to the account
information. There is unauthorized access to the sensitive data which is a data breach into
securing of information on the network. As a solution to this threat, data encryption is used to
transfer of data from one computer to another within the organization so that no other person can
able to hack and access to the data (Siponen, Mahmood and Pahnila 2014). IT is able to limit the
authorized users to access to the database which are of sensitive information. It process will
become vulnerable to the insiders as there are malicious intercept along with abuse of the
protected information. The data encryption prevents the unauthorized users from being misused
if they can gain access to the underlying files storage. The organization should contain policies
regards to the employee conducts that define the expectations of what the employees are reported
regards to the potential insider threat behaviors (Safa et al. 2015). Most of the incidents which
are caused by the insiders are result o employee’s negligence. The malicious insider threats are
hard to detect as it is based on trust of employees as well as their honesty. Working with the
sensitive data is part of job, and then it is difficult to determine if the employees are doing
anything malicious (Siponen, Mahmood and Pahnila 2014). When the suspect malicious is
intent, then it is easier for the employees to claim of they have made any mistakes. It is not
possible to provide guilt in these cases, as it is pretty easier for the employees, such as tech savvy
to cover the tracks.
MINIMIZING THE AFFECT OF HUMAN BEHAVIOUR RISKS RELATED TO
INFORMATION SECURITY
well as security of the information. The insider threats are minimized when the data are moved
outside the firewall. The business is required to secure and exchange of sensitive information
with the external third parties on daily basis (Safa, Von Solms and Furnell 2016).
Hajli and Lin (2016) stated that the insider threats impact on access to the account
information. There is unauthorized access to the sensitive data which is a data breach into
securing of information on the network. As a solution to this threat, data encryption is used to
transfer of data from one computer to another within the organization so that no other person can
able to hack and access to the data (Siponen, Mahmood and Pahnila 2014). IT is able to limit the
authorized users to access to the database which are of sensitive information. It process will
become vulnerable to the insiders as there are malicious intercept along with abuse of the
protected information. The data encryption prevents the unauthorized users from being misused
if they can gain access to the underlying files storage. The organization should contain policies
regards to the employee conducts that define the expectations of what the employees are reported
regards to the potential insider threat behaviors (Safa et al. 2015). Most of the incidents which
are caused by the insiders are result o employee’s negligence. The malicious insider threats are
hard to detect as it is based on trust of employees as well as their honesty. Working with the
sensitive data is part of job, and then it is difficult to determine if the employees are doing
anything malicious (Siponen, Mahmood and Pahnila 2014). When the suspect malicious is
intent, then it is easier for the employees to claim of they have made any mistakes. It is not
possible to provide guilt in these cases, as it is pretty easier for the employees, such as tech savvy
to cover the tracks.

53
MINIMIZING THE AFFECT OF HUMAN BEHAVIOUR RISKS RELATED TO
INFORMATION SECURITY
2.14 Modeling human behavior to anticipate of insider attacks
Abbasi, Sarker and Chiang (2016) discussed that the insider threat such as espionage as
well as leakage of data involves of computer networks, which is among pressing of challenges of
information security which threaten the governmental as well as industry information
infrastructures. Today, unfortunately there is no such single intrusion detection and assessment
of insider threats techniques for the insider threat problems (Kautonen, Gelderen and Fink 2015).
Predictive modeling approach to mitigation of insider threats are aimed to incorporate diverse set
of data sources which will not address cyber domain. The assessment of threat framework
automates detection of higher risk, concern on human behaviors on which it is focused and
informed analysis of the information security personnel (Heckmann, Comes and Nickel 2015).
Incorporation of psychosocial data into cyber data analysis is offered additional dimensions to
assess potential insider threats and integrate of threat analysis framework.
Current practices tend to become reactive as it is focused on detection of malicious acts
after it occurs. The insider threat analysis process is put in greater demand on analysis to
correlate various sources along with data patterns for recognize of potential threats (Kim, Yang
and Park 2014). The insider threats are deemed to cost as well as damage to the organization.
Into the operational context, the security analyst should review as well as interpret large amount
of data for drawing of conclusions about the human behaviours which indicate of policies
violations as well as malicious activities (Safa, Von Solms and Furnell 2016). The employees are
applied domain knowledge for perceive as well as recognize of data patterns. The research
analyst uses number of tools for monitoring of various types of data in order to provide alerts in
addition to reports about the suspicious activities. The research analyst integrates of analysis as
well as sense making across various domains (Siponen, Mahmood and Pahnila 2014). No
MINIMIZING THE AFFECT OF HUMAN BEHAVIOUR RISKS RELATED TO
INFORMATION SECURITY
2.14 Modeling human behavior to anticipate of insider attacks
Abbasi, Sarker and Chiang (2016) discussed that the insider threat such as espionage as
well as leakage of data involves of computer networks, which is among pressing of challenges of
information security which threaten the governmental as well as industry information
infrastructures. Today, unfortunately there is no such single intrusion detection and assessment
of insider threats techniques for the insider threat problems (Kautonen, Gelderen and Fink 2015).
Predictive modeling approach to mitigation of insider threats are aimed to incorporate diverse set
of data sources which will not address cyber domain. The assessment of threat framework
automates detection of higher risk, concern on human behaviors on which it is focused and
informed analysis of the information security personnel (Heckmann, Comes and Nickel 2015).
Incorporation of psychosocial data into cyber data analysis is offered additional dimensions to
assess potential insider threats and integrate of threat analysis framework.
Current practices tend to become reactive as it is focused on detection of malicious acts
after it occurs. The insider threat analysis process is put in greater demand on analysis to
correlate various sources along with data patterns for recognize of potential threats (Kim, Yang
and Park 2014). The insider threats are deemed to cost as well as damage to the organization.
Into the operational context, the security analyst should review as well as interpret large amount
of data for drawing of conclusions about the human behaviours which indicate of policies
violations as well as malicious activities (Safa, Von Solms and Furnell 2016). The employees are
applied domain knowledge for perceive as well as recognize of data patterns. The research
analyst uses number of tools for monitoring of various types of data in order to provide alerts in
addition to reports about the suspicious activities. The research analyst integrates of analysis as
well as sense making across various domains (Siponen, Mahmood and Pahnila 2014). No

54
MINIMIZING THE AFFECT OF HUMAN BEHAVIOUR RISKS RELATED TO
INFORMATION SECURITY
systematic methods are being developed to provide complete along with effective solutions to
the insider threats. The goal of insider threat is to develop, adapt as well as apply of technology
to the challenges of insider threats (Gerber et al. 2016). The rationale of this approach is to
integrate across various domains of the data on body of scientific research as well as case studies
into the field of insider threats, cyber security and human behaviours from which it is concluded
that the behavioural indicates of threat risks which are taken into account by the insider threats.
2.15 Intrinsic and Extrinsic Motivators in Information Security Behavior
Teh, Ahmed and D'Arcy (2015) developed the information security behavior compliance
model such as intrinsic and extrinsic motivation models which influence the individual’s
intention or IT organization to comply with the information security policies as well as intention
to lead complaint behaviors. The extrinsic motivation model includes of penalties as well as
social pressure for compliance of employees with the information security (Taylor, Fritsch and
Liederbach 2014). Social pressure consists of peer behavior, normative beliefs. Apart from this,
intrinsic motivation model includes of perceived effectiveness of penalties, perceived ownership,
perceived self-efficacy as well as perceived value congruence for the policy compliances.
Motivation Factors Description Theory used
Extrinsic
Sanctions The IT organization should comply with
the security policies for avoiding the
penalties.
General
Deterrence
Theory (GDT)
MINIMIZING THE AFFECT OF HUMAN BEHAVIOUR RISKS RELATED TO
INFORMATION SECURITY
systematic methods are being developed to provide complete along with effective solutions to
the insider threats. The goal of insider threat is to develop, adapt as well as apply of technology
to the challenges of insider threats (Gerber et al. 2016). The rationale of this approach is to
integrate across various domains of the data on body of scientific research as well as case studies
into the field of insider threats, cyber security and human behaviours from which it is concluded
that the behavioural indicates of threat risks which are taken into account by the insider threats.
2.15 Intrinsic and Extrinsic Motivators in Information Security Behavior
Teh, Ahmed and D'Arcy (2015) developed the information security behavior compliance
model such as intrinsic and extrinsic motivation models which influence the individual’s
intention or IT organization to comply with the information security policies as well as intention
to lead complaint behaviors. The extrinsic motivation model includes of penalties as well as
social pressure for compliance of employees with the information security (Taylor, Fritsch and
Liederbach 2014). Social pressure consists of peer behavior, normative beliefs. Apart from this,
intrinsic motivation model includes of perceived effectiveness of penalties, perceived ownership,
perceived self-efficacy as well as perceived value congruence for the policy compliances.
Motivation Factors Description Theory used
Extrinsic
Sanctions The IT organization should comply with
the security policies for avoiding the
penalties.
General
Deterrence
Theory (GDT)
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
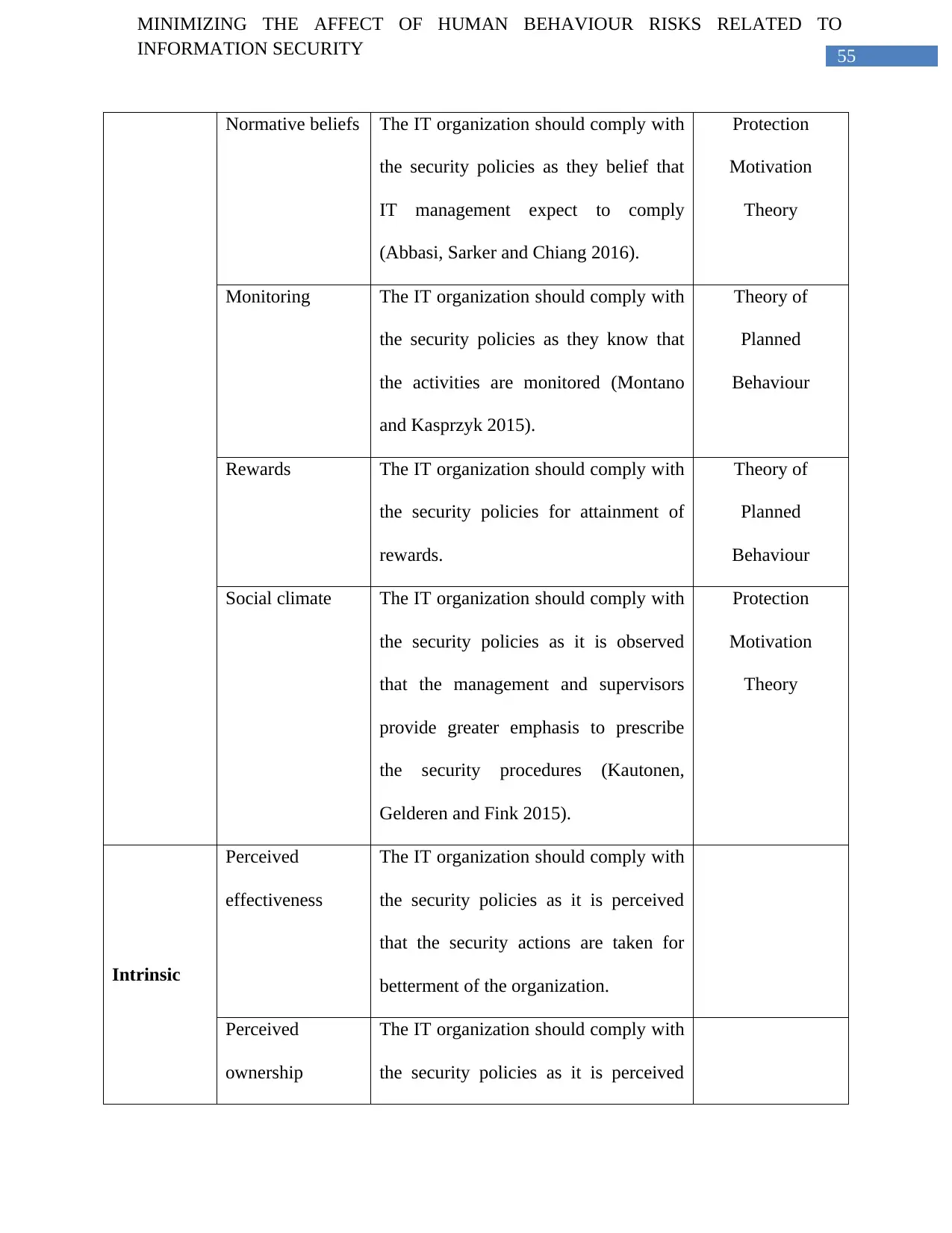
55
MINIMIZING THE AFFECT OF HUMAN BEHAVIOUR RISKS RELATED TO
INFORMATION SECURITY
Normative beliefs The IT organization should comply with
the security policies as they belief that
IT management expect to comply
(Abbasi, Sarker and Chiang 2016).
Protection
Motivation
Theory
Monitoring The IT organization should comply with
the security policies as they know that
the activities are monitored (Montano
and Kasprzyk 2015).
Theory of
Planned
Behaviour
Rewards The IT organization should comply with
the security policies for attainment of
rewards.
Theory of
Planned
Behaviour
Social climate The IT organization should comply with
the security policies as it is observed
that the management and supervisors
provide greater emphasis to prescribe
the security procedures (Kautonen,
Gelderen and Fink 2015).
Protection
Motivation
Theory
Intrinsic
Perceived
effectiveness
The IT organization should comply with
the security policies as it is perceived
that the security actions are taken for
betterment of the organization.
Perceived
ownership
The IT organization should comply with
the security policies as it is perceived
MINIMIZING THE AFFECT OF HUMAN BEHAVIOUR RISKS RELATED TO
INFORMATION SECURITY
Normative beliefs The IT organization should comply with
the security policies as they belief that
IT management expect to comply
(Abbasi, Sarker and Chiang 2016).
Protection
Motivation
Theory
Monitoring The IT organization should comply with
the security policies as they know that
the activities are monitored (Montano
and Kasprzyk 2015).
Theory of
Planned
Behaviour
Rewards The IT organization should comply with
the security policies for attainment of
rewards.
Theory of
Planned
Behaviour
Social climate The IT organization should comply with
the security policies as it is observed
that the management and supervisors
provide greater emphasis to prescribe
the security procedures (Kautonen,
Gelderen and Fink 2015).
Protection
Motivation
Theory
Intrinsic
Perceived
effectiveness
The IT organization should comply with
the security policies as it is perceived
that the security actions are taken for
betterment of the organization.
Perceived
ownership
The IT organization should comply with
the security policies as it is perceived
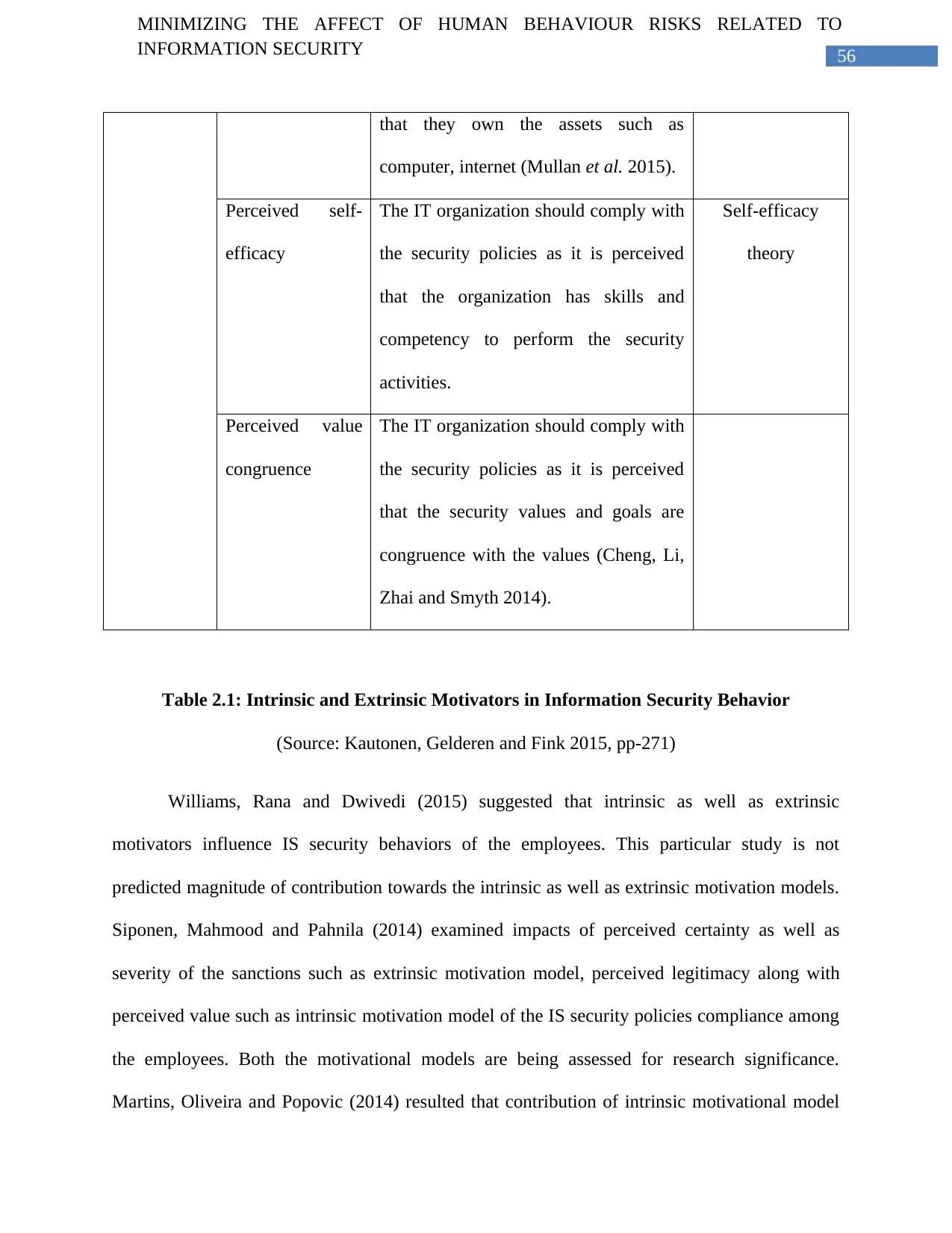
56
MINIMIZING THE AFFECT OF HUMAN BEHAVIOUR RISKS RELATED TO
INFORMATION SECURITY
that they own the assets such as
computer, internet (Mullan et al. 2015).
Perceived self-
efficacy
The IT organization should comply with
the security policies as it is perceived
that the organization has skills and
competency to perform the security
activities.
Self-efficacy
theory
Perceived value
congruence
The IT organization should comply with
the security policies as it is perceived
that the security values and goals are
congruence with the values (Cheng, Li,
Zhai and Smyth 2014).
Table 2.1: Intrinsic and Extrinsic Motivators in Information Security Behavior
(Source: Kautonen, Gelderen and Fink 2015, pp-271)
Williams, Rana and Dwivedi (2015) suggested that intrinsic as well as extrinsic
motivators influence IS security behaviors of the employees. This particular study is not
predicted magnitude of contribution towards the intrinsic as well as extrinsic motivation models.
Siponen, Mahmood and Pahnila (2014) examined impacts of perceived certainty as well as
severity of the sanctions such as extrinsic motivation model, perceived legitimacy along with
perceived value such as intrinsic motivation model of the IS security policies compliance among
the employees. Both the motivational models are being assessed for research significance.
Martins, Oliveira and Popovic (2014) resulted that contribution of intrinsic motivational model
MINIMIZING THE AFFECT OF HUMAN BEHAVIOUR RISKS RELATED TO
INFORMATION SECURITY
that they own the assets such as
computer, internet (Mullan et al. 2015).
Perceived self-
efficacy
The IT organization should comply with
the security policies as it is perceived
that the organization has skills and
competency to perform the security
activities.
Self-efficacy
theory
Perceived value
congruence
The IT organization should comply with
the security policies as it is perceived
that the security values and goals are
congruence with the values (Cheng, Li,
Zhai and Smyth 2014).
Table 2.1: Intrinsic and Extrinsic Motivators in Information Security Behavior
(Source: Kautonen, Gelderen and Fink 2015, pp-271)
Williams, Rana and Dwivedi (2015) suggested that intrinsic as well as extrinsic
motivators influence IS security behaviors of the employees. This particular study is not
predicted magnitude of contribution towards the intrinsic as well as extrinsic motivation models.
Siponen, Mahmood and Pahnila (2014) examined impacts of perceived certainty as well as
severity of the sanctions such as extrinsic motivation model, perceived legitimacy along with
perceived value such as intrinsic motivation model of the IS security policies compliance among
the employees. Both the motivational models are being assessed for research significance.
Martins, Oliveira and Popovic (2014) resulted that contribution of intrinsic motivational model

57
MINIMIZING THE AFFECT OF HUMAN BEHAVIOUR RISKS RELATED TO
INFORMATION SECURITY
exceeds the extrinsic motivation. It is proposed that the intrinsic motivation model generates
explanations and solutions for the compliance with the organizational IS security policies. The IT
organization should raise emphasis on the intrinsic motivational based approaches and it is relied
less on the extrinsic based approaches.
The current research into IS security policies compliance is focused on the value of
employees of extrinsic rewards where the employees are tend to value of intrinsic in addition to
extrinsic rewards. The factors of intrinsic motivational are self-efficacy, perceived effectiveness,
perceived value congruence as well as psychological ownership which influence the decisions of
employees that intrinsic factors explain of information security policies compliance than the
extrinsic factors. Williams, Rana and Dwivedi (2015) acknowledged that strategies drivers such
as security training, security climate enhance the intrinsic motivation of employees. Montano and
Kasprzyk (2015) conceptualized empowerment as the intrinsic tasks motivation. The
empowerment is referred to set of cognitions for reflecting the perceptions about the tasks and its
ability to control shape as well as influence the tasks (Sheeran and Rivis 2017). The contract
between two of the motivational theories are focused on the managerial practices which share
power with the employees. In other words, the individuals are being considered as intrinsic
motivated when they would experience the cognitions. Siponen, Mahmood and Pahnila (2014)
discussed of various practices which indicated of structural empowerment such as access to the
opportunity, access to the information, as well as participation into making of decisions.
2.16 Insider Misuse and Incident Responses
The cultural aversion is lead to IT organizations for avoiding the solid incident response
plans. The human behavior risks are to be mitigated by incident response plan which helps to
identify the possible incidents which lead to information security risks due to human errors,
MINIMIZING THE AFFECT OF HUMAN BEHAVIOUR RISKS RELATED TO
INFORMATION SECURITY
exceeds the extrinsic motivation. It is proposed that the intrinsic motivation model generates
explanations and solutions for the compliance with the organizational IS security policies. The IT
organization should raise emphasis on the intrinsic motivational based approaches and it is relied
less on the extrinsic based approaches.
The current research into IS security policies compliance is focused on the value of
employees of extrinsic rewards where the employees are tend to value of intrinsic in addition to
extrinsic rewards. The factors of intrinsic motivational are self-efficacy, perceived effectiveness,
perceived value congruence as well as psychological ownership which influence the decisions of
employees that intrinsic factors explain of information security policies compliance than the
extrinsic factors. Williams, Rana and Dwivedi (2015) acknowledged that strategies drivers such
as security training, security climate enhance the intrinsic motivation of employees. Montano and
Kasprzyk (2015) conceptualized empowerment as the intrinsic tasks motivation. The
empowerment is referred to set of cognitions for reflecting the perceptions about the tasks and its
ability to control shape as well as influence the tasks (Sheeran and Rivis 2017). The contract
between two of the motivational theories are focused on the managerial practices which share
power with the employees. In other words, the individuals are being considered as intrinsic
motivated when they would experience the cognitions. Siponen, Mahmood and Pahnila (2014)
discussed of various practices which indicated of structural empowerment such as access to the
opportunity, access to the information, as well as participation into making of decisions.
2.16 Insider Misuse and Incident Responses
The cultural aversion is lead to IT organizations for avoiding the solid incident response
plans. The human behavior risks are to be mitigated by incident response plan which helps to
identify the possible incidents which lead to information security risks due to human errors,
Secure Best Marks with AI Grader
Need help grading? Try our AI Grader for instant feedback on your assignments.

58
MINIMIZING THE AFFECT OF HUMAN BEHAVIOUR RISKS RELATED TO
INFORMATION SECURITY
causes and control factors to prevent from the risks. Malekian, Hayati and Aarts (2017) stated
that the incident responses understand security incidents. The security events are to be
compromised with confidentiality as well as availability of information assets. The incident is
included of attacks, which is intentional attempts to gain of unauthorized access to damage as
well as destroy of the network. Siponen, Mahmood and Pahnila (2014) suggested that the
incident responses are formal as well as organized approaches to deal with kinds of the security
incidents. It is involved of incident response plan which lies out of the steps that the company
should follow after the incident has occurred. The plan is included of incident response process
for common types of the incidents. Safa, Von Solms and Furnell (2016) discussed that the insider
incident response plans define responses that include of extended teams such as legal, human
resources along with departmental management when the employees are involved. The security
program helps to evaluate entire state of organization’s security by providing of objective view
of the organization’s policies, control as well as processes.
Gritzalis et al. (2014) illustrated that development of threat vulnerability along with
information security management programs help to identify the vulnerabilities expose to the
organization’s malicious activities. There is assessment to determine whether the malicious
activities are taking place into the network. Gerber et al. (2016) argued that it is regularly
scheduled as part of the vulnerability management practices along with integration of the
incident response capabilities. The organizational as well as cultural factors affect insider
responses to the security environments. Soomro, Shah and Ahmed (2016) stated that the
technical approaches use of system policies to identify as well as minimize the damages which
are done by threatening of insiders. Incident response techniques are used to reduce the insider
threats which reduce the risks. The information security policies are based on motivation of the
MINIMIZING THE AFFECT OF HUMAN BEHAVIOUR RISKS RELATED TO
INFORMATION SECURITY
causes and control factors to prevent from the risks. Malekian, Hayati and Aarts (2017) stated
that the incident responses understand security incidents. The security events are to be
compromised with confidentiality as well as availability of information assets. The incident is
included of attacks, which is intentional attempts to gain of unauthorized access to damage as
well as destroy of the network. Siponen, Mahmood and Pahnila (2014) suggested that the
incident responses are formal as well as organized approaches to deal with kinds of the security
incidents. It is involved of incident response plan which lies out of the steps that the company
should follow after the incident has occurred. The plan is included of incident response process
for common types of the incidents. Safa, Von Solms and Furnell (2016) discussed that the insider
incident response plans define responses that include of extended teams such as legal, human
resources along with departmental management when the employees are involved. The security
program helps to evaluate entire state of organization’s security by providing of objective view
of the organization’s policies, control as well as processes.
Gritzalis et al. (2014) illustrated that development of threat vulnerability along with
information security management programs help to identify the vulnerabilities expose to the
organization’s malicious activities. There is assessment to determine whether the malicious
activities are taking place into the network. Gerber et al. (2016) argued that it is regularly
scheduled as part of the vulnerability management practices along with integration of the
incident response capabilities. The organizational as well as cultural factors affect insider
responses to the security environments. Soomro, Shah and Ahmed (2016) stated that the
technical approaches use of system policies to identify as well as minimize the damages which
are done by threatening of insiders. Incident response techniques are used to reduce the insider
threats which reduce the risks. The information security policies are based on motivation of the

59
MINIMIZING THE AFFECT OF HUMAN BEHAVIOUR RISKS RELATED TO
INFORMATION SECURITY
insiders. The attitude of employees towards the information security is main challenges for
implementation of information security policies (Siponen, Mahmood and Pahnila 2014). The
understanding of employees along with awareness of information security issues with
implementation of information security policies play a key significant role to protect
organization’s information. In this literature study, various information security dimensions are
concluded such as culture.
Chapter 3: Research Conceptual Framework
3.1 Introduction
This particular chapter contains description of the conceptual framework which is used
into the research study. The conceptual framework for this particular study is being derived from
the literature review above. The literature review helps the researcher to understand the problems
as well as guides the data gathering as well as analysis. The conceptual framework is described
of two variables independent, one dependent variable and mediating variable about how it is
related and impacted the human behavior (AlHogail 2015). The relation between two of the
variables is used to answer to the mentioned research questions. This particular research is
carried out into two phases such as into the first phase, the information security countermeasures
are to be identified to minimize the human threats. Into the second phase, the human perception
of information security countermeasures is analyzed (Safa and Von Solms 2016). The conceptual
framework is analyzed that there are various countermeasures which influence the information
security human behavior and empirical study is to be performed to provide both negative as well
as positive influences.
MINIMIZING THE AFFECT OF HUMAN BEHAVIOUR RISKS RELATED TO
INFORMATION SECURITY
insiders. The attitude of employees towards the information security is main challenges for
implementation of information security policies (Siponen, Mahmood and Pahnila 2014). The
understanding of employees along with awareness of information security issues with
implementation of information security policies play a key significant role to protect
organization’s information. In this literature study, various information security dimensions are
concluded such as culture.
Chapter 3: Research Conceptual Framework
3.1 Introduction
This particular chapter contains description of the conceptual framework which is used
into the research study. The conceptual framework for this particular study is being derived from
the literature review above. The literature review helps the researcher to understand the problems
as well as guides the data gathering as well as analysis. The conceptual framework is described
of two variables independent, one dependent variable and mediating variable about how it is
related and impacted the human behavior (AlHogail 2015). The relation between two of the
variables is used to answer to the mentioned research questions. This particular research is
carried out into two phases such as into the first phase, the information security countermeasures
are to be identified to minimize the human threats. Into the second phase, the human perception
of information security countermeasures is analyzed (Safa and Von Solms 2016). The conceptual
framework is analyzed that there are various countermeasures which influence the information
security human behavior and empirical study is to be performed to provide both negative as well
as positive influences.

60
MINIMIZING THE AFFECT OF HUMAN BEHAVIOUR RISKS RELATED TO
INFORMATION SECURITY
3.2 Conceptual framework of the research study
Into this research study, there are two independent variables such as the information
security countermeasures and human perception of information security countermeasures. One
mediating variable is user’s behavior towards the information security. The dependent variable is
Human Information System Security. The information security countermeasures are
recommended as the practice for protecting the organizational data. Most of the research study is
found that the employees have low awareness of human in addition to understanding the
information security (Nelson and Staggers 2016). The conceptual framework in this particular
study is being conceptualized by protection motivation theory as well as technology acceptance
theory. Both the theories are used into the human behavior studies which are significant for
predicting the human behavior. The critical factors which influence the behavior of human
towards the information security are included. The concepts as well as variables are derived from
the literature review. It captures the underlying principles of the theories which are required to
investigate the research study.
MINIMIZING THE AFFECT OF HUMAN BEHAVIOUR RISKS RELATED TO
INFORMATION SECURITY
3.2 Conceptual framework of the research study
Into this research study, there are two independent variables such as the information
security countermeasures and human perception of information security countermeasures. One
mediating variable is user’s behavior towards the information security. The dependent variable is
Human Information System Security. The information security countermeasures are
recommended as the practice for protecting the organizational data. Most of the research study is
found that the employees have low awareness of human in addition to understanding the
information security (Nelson and Staggers 2016). The conceptual framework in this particular
study is being conceptualized by protection motivation theory as well as technology acceptance
theory. Both the theories are used into the human behavior studies which are significant for
predicting the human behavior. The critical factors which influence the behavior of human
towards the information security are included. The concepts as well as variables are derived from
the literature review. It captures the underlying principles of the theories which are required to
investigate the research study.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

61
MINIMIZING THE AFFECT OF HUMAN BEHAVIOUR RISKS RELATED TO
INFORMATION SECURITY
Information security
countermeasures
Human perception of
information security
countermeasures
User’s behaviour
towards the
information
security
Human
Information
System Security
Independent variable Mediating variable Dependent variable
Figure 3.1: Conceptual framework of research study
(Source: Created by author)
The research study is based on three hypotheses such as: Hypothesis 1: Organizational
leadership is positively related to the employees’ attitude towards the information security.
Hypothesis 2: Organizational culture is positively related to the employees’ attitude towards the
information security. Hypothesis 3: Employee’s intention towards information security is
positively related to the employee’s attitude toward information security. The information
security principles are also used to lessen the human errors to avoid the connected risks. The
behavior of human is offered of higher impact on success along with failure for securing and
MINIMIZING THE AFFECT OF HUMAN BEHAVIOUR RISKS RELATED TO
INFORMATION SECURITY
Information security
countermeasures
Human perception of
information security
countermeasures
User’s behaviour
towards the
information
security
Human
Information
System Security
Independent variable Mediating variable Dependent variable
Figure 3.1: Conceptual framework of research study
(Source: Created by author)
The research study is based on three hypotheses such as: Hypothesis 1: Organizational
leadership is positively related to the employees’ attitude towards the information security.
Hypothesis 2: Organizational culture is positively related to the employees’ attitude towards the
information security. Hypothesis 3: Employee’s intention towards information security is
positively related to the employee’s attitude toward information security. The information
security principles are also used to lessen the human errors to avoid the connected risks. The
behavior of human is offered of higher impact on success along with failure for securing and

62
MINIMIZING THE AFFECT OF HUMAN BEHAVIOUR RISKS RELATED TO
INFORMATION SECURITY
protecting the information (Mishra, Akman and Mishra 2014). The users are measured as user
involving approach to happen to helpful to manipulate the consciousness of user in addition to
behavior. It is taken as the risky behavior of users furthermore thrashing of prevention of human
behavior. The resources related to human are responsible to make use of both physical as well as
natural resources in order to transform traditional economics into the modern economics (Safa
and Von Solms 2016). Differences into the economic development provide a huge reflection into
the quality of the human resources. The term managing of the human resources is encompassed
of various ideas. Most of the time success of any organization is based on the human resources
who lead to motivate as well as encourage of teamwork.
3.3 Internal threat into Small and medium size enterprise
After review of the literature, the research paper analyzes the problem area to identify the
information security threats into the organization due to human behaviors such as:
Lack of understanding of the human about the insider threats and issues (Libby
2017).
There are limited human resources for the management of security
There are lack of understanding about importance of the human factors
There is lack of priorities of the information security (Safa et al. 2015).
As a result of the literature review, there are relationships which are detected to identify
the internal threats, countermeasures, human factors along with human behavior.
MINIMIZING THE AFFECT OF HUMAN BEHAVIOUR RISKS RELATED TO
INFORMATION SECURITY
protecting the information (Mishra, Akman and Mishra 2014). The users are measured as user
involving approach to happen to helpful to manipulate the consciousness of user in addition to
behavior. It is taken as the risky behavior of users furthermore thrashing of prevention of human
behavior. The resources related to human are responsible to make use of both physical as well as
natural resources in order to transform traditional economics into the modern economics (Safa
and Von Solms 2016). Differences into the economic development provide a huge reflection into
the quality of the human resources. The term managing of the human resources is encompassed
of various ideas. Most of the time success of any organization is based on the human resources
who lead to motivate as well as encourage of teamwork.
3.3 Internal threat into Small and medium size enterprise
After review of the literature, the research paper analyzes the problem area to identify the
information security threats into the organization due to human behaviors such as:
Lack of understanding of the human about the insider threats and issues (Libby
2017).
There are limited human resources for the management of security
There are lack of understanding about importance of the human factors
There is lack of priorities of the information security (Safa et al. 2015).
As a result of the literature review, there are relationships which are detected to identify
the internal threats, countermeasures, human factors along with human behavior.

63
MINIMIZING THE AFFECT OF HUMAN BEHAVIOUR RISKS RELATED TO
INFORMATION SECURITY
Information security internal threat
Information security countermeasures
Human factors
Security behaviour
Figure 3.2: Relations among threat countermeasures and human behavior
(Source: Safa et al. 2015, pp-71)
In order to reduce the internal threats into small and medium size enterprise due to human
errors, different countermeasures are to be implemented as well as maintained but the employees
should understand the countermeasures which influence the human behavior which are not
properly clear. Into this research perception of the countermeasures of information security by
the end users are to be researched (Tsohou, Karyda and Kokolakis 2015). Into the IT
organization, there are insider threats which are provided a huge impact on the sensitive as well
as confidential data. The implementation of information security system into the enterprise is
based on safeguarding the hackers from penetrating the network along with access to the data
(Kautonen, Gelderen and Fink 2015). The insider threats also provide impact on the account
information. There is some unauthorized access to the sensitive data that causes data breach,
therefore the organization is required to secure information on the network. The analysis of
MINIMIZING THE AFFECT OF HUMAN BEHAVIOUR RISKS RELATED TO
INFORMATION SECURITY
Information security internal threat
Information security countermeasures
Human factors
Security behaviour
Figure 3.2: Relations among threat countermeasures and human behavior
(Source: Safa et al. 2015, pp-71)
In order to reduce the internal threats into small and medium size enterprise due to human
errors, different countermeasures are to be implemented as well as maintained but the employees
should understand the countermeasures which influence the human behavior which are not
properly clear. Into this research perception of the countermeasures of information security by
the end users are to be researched (Tsohou, Karyda and Kokolakis 2015). Into the IT
organization, there are insider threats which are provided a huge impact on the sensitive as well
as confidential data. The implementation of information security system into the enterprise is
based on safeguarding the hackers from penetrating the network along with access to the data
(Kautonen, Gelderen and Fink 2015). The insider threats also provide impact on the account
information. There is some unauthorized access to the sensitive data that causes data breach,
therefore the organization is required to secure information on the network. The analysis of
Secure Best Marks with AI Grader
Need help grading? Try our AI Grader for instant feedback on your assignments.

64
MINIMIZING THE AFFECT OF HUMAN BEHAVIOUR RISKS RELATED TO
INFORMATION SECURITY
insider threat is correlated with various sources used to recognize the potential threats (Siponen,
Mahmood and Pahnila 2014). The research analyst uses various monitoring tool to alert about
the suspicious activities. The specialized methodologies utilization of framework approaches to
recognize and in addition limit the harms which are finished by undermining of insiders. Episode
reaction procedures are utilized to lessen the insider dangers which decrease the dangers. The
data security arrangements depend on inspiration of the insiders. The state of mind of
representatives towards the data security is primary difficulties for usage of data security
approaches (Siponen, Mahmood and Pahnila 2014). The comprehension of representatives
alongside consciousness of data security issues with execution of data security arrangements
assumes a key critical part to ensure association's data.
3.4 Human’s behavior and information security system
In order to examine the research question 1, different researchers are reviewed into the
conceptual part with aim to recognize as well as evaluate for minimizing the effects of human
behavior related to the information security. Most of the literatures stated that the information
security system is based on the human behavior. Navimipour et al. (2015) stated that the human
are proactive on the information security. When the organization are recommended to use of
information security measures then level of human awareness is increased as well as impacted
the success of implementation of information system. The security of information are defined as
capability of the information system measures for protecting against the unauthorized as well as
misuse of assets for the information system (Lowry and Moody 2015). This particular study
believes that the information security is acceptable, and the securities incidents are to be
decreased as well as effectiveness of the information system are to be increased. The acceptable
human behavior will increase effectiveness of the human information security system. As per the
MINIMIZING THE AFFECT OF HUMAN BEHAVIOUR RISKS RELATED TO
INFORMATION SECURITY
insider threat is correlated with various sources used to recognize the potential threats (Siponen,
Mahmood and Pahnila 2014). The research analyst uses various monitoring tool to alert about
the suspicious activities. The specialized methodologies utilization of framework approaches to
recognize and in addition limit the harms which are finished by undermining of insiders. Episode
reaction procedures are utilized to lessen the insider dangers which decrease the dangers. The
data security arrangements depend on inspiration of the insiders. The state of mind of
representatives towards the data security is primary difficulties for usage of data security
approaches (Siponen, Mahmood and Pahnila 2014). The comprehension of representatives
alongside consciousness of data security issues with execution of data security arrangements
assumes a key critical part to ensure association's data.
3.4 Human’s behavior and information security system
In order to examine the research question 1, different researchers are reviewed into the
conceptual part with aim to recognize as well as evaluate for minimizing the effects of human
behavior related to the information security. Most of the literatures stated that the information
security system is based on the human behavior. Navimipour et al. (2015) stated that the human
are proactive on the information security. When the organization are recommended to use of
information security measures then level of human awareness is increased as well as impacted
the success of implementation of information system. The security of information are defined as
capability of the information system measures for protecting against the unauthorized as well as
misuse of assets for the information system (Lowry and Moody 2015). This particular study
believes that the information security is acceptable, and the securities incidents are to be
decreased as well as effectiveness of the information system are to be increased. The acceptable
human behavior will increase effectiveness of the human information security system. As per the

65
MINIMIZING THE AFFECT OF HUMAN BEHAVIOUR RISKS RELATED TO
INFORMATION SECURITY
organizational policies along with standards, there are various codes of conducts which are
required to design people for the follow up. People are executed about the organizational
information security policies which help the users to prevent and minimize the human activities
which lead to issues of information system (Safa, Von Solms and Furnell 2016). The human
factors are major forces which are behind effectiveness as well as failure of the security systems.
3.5 Information security countermeasures
In order to examine the research question 2, different researchers are reviewed into the
conceptual part with aim to recognize as well as evaluate for minimizing the effects of human
behavior related to the information security. For answering the research question, the employees
are perceived the countermeasures which are analyzed into the literature part such as:
Documentation related to the information security: Each of the organization should
have documentation whose objective is to influence the human behavior. Documented norms
should describe the responsibilities of the employee, authorized use of confidential information
as well as organizational system, what the human behavior is being prohibited as well as
consequences the violation (Tsohou, Karyda and Kokolakis 2015). Therefore, the organization
should follow of organizational rules and regulations to implement a good culture in the working
environment.
Training and awareness: It is provided to the human to raise knowledge about the
security issues and influences the emotional aspects of how the information security is being
perceived by the employees (Ngai, Tao and Moon 2015). Proper training is provided to all the
employees to make them aware of good human behavior which is required for any organization.
MINIMIZING THE AFFECT OF HUMAN BEHAVIOUR RISKS RELATED TO
INFORMATION SECURITY
organizational policies along with standards, there are various codes of conducts which are
required to design people for the follow up. People are executed about the organizational
information security policies which help the users to prevent and minimize the human activities
which lead to issues of information system (Safa, Von Solms and Furnell 2016). The human
factors are major forces which are behind effectiveness as well as failure of the security systems.
3.5 Information security countermeasures
In order to examine the research question 2, different researchers are reviewed into the
conceptual part with aim to recognize as well as evaluate for minimizing the effects of human
behavior related to the information security. For answering the research question, the employees
are perceived the countermeasures which are analyzed into the literature part such as:
Documentation related to the information security: Each of the organization should
have documentation whose objective is to influence the human behavior. Documented norms
should describe the responsibilities of the employee, authorized use of confidential information
as well as organizational system, what the human behavior is being prohibited as well as
consequences the violation (Tsohou, Karyda and Kokolakis 2015). Therefore, the organization
should follow of organizational rules and regulations to implement a good culture in the working
environment.
Training and awareness: It is provided to the human to raise knowledge about the
security issues and influences the emotional aspects of how the information security is being
perceived by the employees (Ngai, Tao and Moon 2015). Proper training is provided to all the
employees to make them aware of good human behavior which is required for any organization.

66
MINIMIZING THE AFFECT OF HUMAN BEHAVIOUR RISKS RELATED TO
INFORMATION SECURITY
Reward: Each of the organization should have some reward process for preventing the
employees from the unacceptable human behavior. When the information security incidents as
well as reaction to the incidents are being integrated, therefore the process becomes effective,
then the employees are improved the security behavior (Nelson and Staggers 2016). Reward
system encourages the employees to work properly and motivates them to work more so that
they are recognized by others.
Internal security culture: Hodgson (2017) concluded that there are cultural dimensions
which are used into the conceptual framework for identifying and assessing the internal culture
into the organization. The management as well as employees is believed about importance of the
information security, motivation of human behavior, changes into the organizational, social
interaction as well as responsibility of employees to minimize the information security risks.
Culture plays a key significant role into shaping society as well as country (Yang et al. 2015).
The culture is developed as result of employee’s interactions with the information security
controls. The above mentioned cultural factors would influence the end users human behavior.
Access limitations: There are effective methods to reduce the internal threats are to
implement of access rights which is based on need to know with the internal information system.
The internal limitations are used for reducing the possibility of the information leakages (Silic
and Back 2014). The limitations to physical access are helping to secure the information from the
physical threats.
Identification and authentication: A strict user name, password as well as technological
countermeasures are used into the small and medium size enterprise for identifying the end users
MINIMIZING THE AFFECT OF HUMAN BEHAVIOUR RISKS RELATED TO
INFORMATION SECURITY
Reward: Each of the organization should have some reward process for preventing the
employees from the unacceptable human behavior. When the information security incidents as
well as reaction to the incidents are being integrated, therefore the process becomes effective,
then the employees are improved the security behavior (Nelson and Staggers 2016). Reward
system encourages the employees to work properly and motivates them to work more so that
they are recognized by others.
Internal security culture: Hodgson (2017) concluded that there are cultural dimensions
which are used into the conceptual framework for identifying and assessing the internal culture
into the organization. The management as well as employees is believed about importance of the
information security, motivation of human behavior, changes into the organizational, social
interaction as well as responsibility of employees to minimize the information security risks.
Culture plays a key significant role into shaping society as well as country (Yang et al. 2015).
The culture is developed as result of employee’s interactions with the information security
controls. The above mentioned cultural factors would influence the end users human behavior.
Access limitations: There are effective methods to reduce the internal threats are to
implement of access rights which is based on need to know with the internal information system.
The internal limitations are used for reducing the possibility of the information leakages (Silic
and Back 2014). The limitations to physical access are helping to secure the information from the
physical threats.
Identification and authentication: A strict user name, password as well as technological
countermeasures are used into the small and medium size enterprise for identifying the end users
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

67
MINIMIZING THE AFFECT OF HUMAN BEHAVIOUR RISKS RELATED TO
INFORMATION SECURITY
along with authenticate for enforce access to the research limitations as well as offer of
accountability (Khaitan and McCalley 2015).
Therefore, the conceptual framework is showing the countermeasures to prevent as well
as mitigate the internal threats which are required for user perception as well as human security
behavior to make sure that the internal threat levels are not raised due to implemented mitigation
steps.
3.6 Human security culture
In order to examine the research question 3, different researchers are reviewed into the
conceptual part with aim to evaluate the human security culture into the organization. Most of
the studies have provided little attention into the organizational attitudes, human behaviors as
well as interaction among the individuals and its context (Shropshire, Warkentin and Sharma
2015). The interaction is contributed to the beliefs of individuals along with values about the
information security. There are various cultural components towards the personal culture among
the human and the values are better to promote the human behavior. Based on the literature
review findings, the framework of four modes are analyzed on three cases (Ahmad, Maynard and
Park 2014). Based on the three cases, the participants are asked to recognize the causes of the
security incidents and obstacles to achieve improved information security compliances into the
organization. The following table shows the four modes of the information security behavior
which are presented into three cases which are related to four modes.
Modes Case A Case B Case C
Mode 1: Not
knowing-not
Some of the employees
are not sharing related
Most of the humans are
not aware of information
Most of the humans are not
aware of information security
MINIMIZING THE AFFECT OF HUMAN BEHAVIOUR RISKS RELATED TO
INFORMATION SECURITY
along with authenticate for enforce access to the research limitations as well as offer of
accountability (Khaitan and McCalley 2015).
Therefore, the conceptual framework is showing the countermeasures to prevent as well
as mitigate the internal threats which are required for user perception as well as human security
behavior to make sure that the internal threat levels are not raised due to implemented mitigation
steps.
3.6 Human security culture
In order to examine the research question 3, different researchers are reviewed into the
conceptual part with aim to evaluate the human security culture into the organization. Most of
the studies have provided little attention into the organizational attitudes, human behaviors as
well as interaction among the individuals and its context (Shropshire, Warkentin and Sharma
2015). The interaction is contributed to the beliefs of individuals along with values about the
information security. There are various cultural components towards the personal culture among
the human and the values are better to promote the human behavior. Based on the literature
review findings, the framework of four modes are analyzed on three cases (Ahmad, Maynard and
Park 2014). Based on the three cases, the participants are asked to recognize the causes of the
security incidents and obstacles to achieve improved information security compliances into the
organization. The following table shows the four modes of the information security behavior
which are presented into three cases which are related to four modes.
Modes Case A Case B Case C
Mode 1: Not
knowing-not
Some of the employees
are not sharing related
Most of the humans are
not aware of information
Most of the humans are not
aware of information security
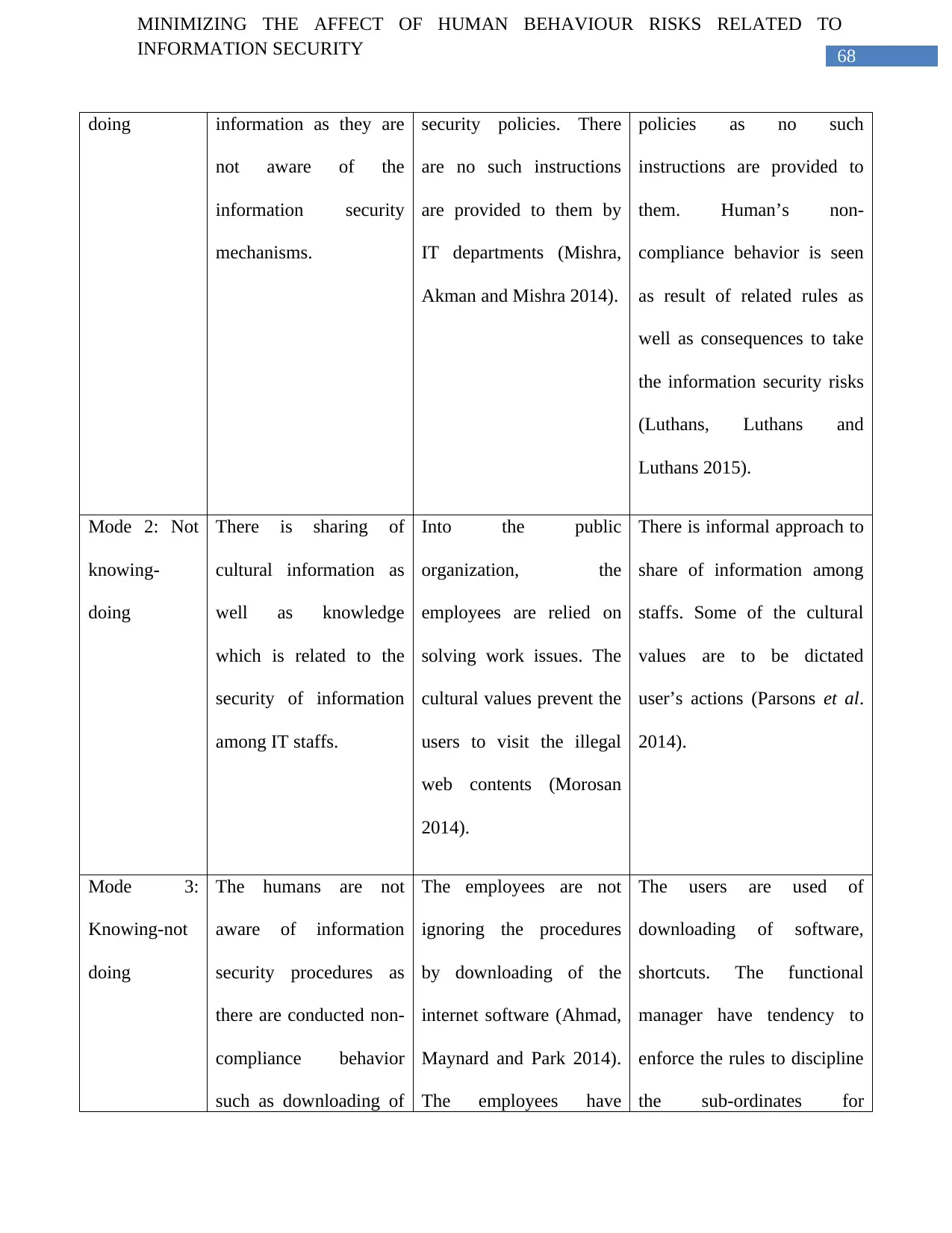
68
MINIMIZING THE AFFECT OF HUMAN BEHAVIOUR RISKS RELATED TO
INFORMATION SECURITY
doing information as they are
not aware of the
information security
mechanisms.
security policies. There
are no such instructions
are provided to them by
IT departments (Mishra,
Akman and Mishra 2014).
policies as no such
instructions are provided to
them. Human’s non-
compliance behavior is seen
as result of related rules as
well as consequences to take
the information security risks
(Luthans, Luthans and
Luthans 2015).
Mode 2: Not
knowing-
doing
There is sharing of
cultural information as
well as knowledge
which is related to the
security of information
among IT staffs.
Into the public
organization, the
employees are relied on
solving work issues. The
cultural values prevent the
users to visit the illegal
web contents (Morosan
2014).
There is informal approach to
share of information among
staffs. Some of the cultural
values are to be dictated
user’s actions (Parsons et al.
2014).
Mode 3:
Knowing-not
doing
The humans are not
aware of information
security procedures as
there are conducted non-
compliance behavior
such as downloading of
The employees are not
ignoring the procedures
by downloading of the
internet software (Ahmad,
Maynard and Park 2014).
The employees have
The users are used of
downloading of software,
shortcuts. The functional
manager have tendency to
enforce the rules to discipline
the sub-ordinates for
MINIMIZING THE AFFECT OF HUMAN BEHAVIOUR RISKS RELATED TO
INFORMATION SECURITY
doing information as they are
not aware of the
information security
mechanisms.
security policies. There
are no such instructions
are provided to them by
IT departments (Mishra,
Akman and Mishra 2014).
policies as no such
instructions are provided to
them. Human’s non-
compliance behavior is seen
as result of related rules as
well as consequences to take
the information security risks
(Luthans, Luthans and
Luthans 2015).
Mode 2: Not
knowing-
doing
There is sharing of
cultural information as
well as knowledge
which is related to the
security of information
among IT staffs.
Into the public
organization, the
employees are relied on
solving work issues. The
cultural values prevent the
users to visit the illegal
web contents (Morosan
2014).
There is informal approach to
share of information among
staffs. Some of the cultural
values are to be dictated
user’s actions (Parsons et al.
2014).
Mode 3:
Knowing-not
doing
The humans are not
aware of information
security procedures as
there are conducted non-
compliance behavior
such as downloading of
The employees are not
ignoring the procedures
by downloading of the
internet software (Ahmad,
Maynard and Park 2014).
The employees have
The users are used of
downloading of software,
shortcuts. The functional
manager have tendency to
enforce the rules to discipline
the sub-ordinates for

69
MINIMIZING THE AFFECT OF HUMAN BEHAVIOUR RISKS RELATED TO
INFORMATION SECURITY
internet software
(Khaitan and McCalley
2015).
tendency not to report
violation for sake of their
group’s image.
protection concerns (Tsohou,
Karyda and Kokolakis 2015)
Mode 4:
Knowing-
doing
There is level of information security culture which is indicted that most of the
members are into the three cases fit into the modes.
Table 3.1: Human security culture
(Source: Tsohou, Karyda and Kokolakis 2015, pp-134)
From the above table, the data indicates that the cultural values are impacted to the
individual’s security related behavior and it influenced the information security culture into
proper manner.
3.7 Human behavior theory
The conceptual framework in this particular study is being conceptualized by protection
motivation theory as well as technology acceptance theory. Both the theories are used into the
human behavior studies which are significant for predicting the human behavior. The protection
motivation theory is referred to how people are changing the attitudes as well as behaviors of
human in response to the human risk. This particular theory explains if the threats are perceived
by people as they are preventing the possible threats (Tsai et al. 2016). The research study found
that most of the factors like the perceived severity as well as self-efficacy influenced the users
for practicing the security behavior. This theory is based on four factors which are believed to be
motivated the users to protect themselves such as “perceived severity, perceived vulnerability,
MINIMIZING THE AFFECT OF HUMAN BEHAVIOUR RISKS RELATED TO
INFORMATION SECURITY
internet software
(Khaitan and McCalley
2015).
tendency not to report
violation for sake of their
group’s image.
protection concerns (Tsohou,
Karyda and Kokolakis 2015)
Mode 4:
Knowing-
doing
There is level of information security culture which is indicted that most of the
members are into the three cases fit into the modes.
Table 3.1: Human security culture
(Source: Tsohou, Karyda and Kokolakis 2015, pp-134)
From the above table, the data indicates that the cultural values are impacted to the
individual’s security related behavior and it influenced the information security culture into
proper manner.
3.7 Human behavior theory
The conceptual framework in this particular study is being conceptualized by protection
motivation theory as well as technology acceptance theory. Both the theories are used into the
human behavior studies which are significant for predicting the human behavior. The protection
motivation theory is referred to how people are changing the attitudes as well as behaviors of
human in response to the human risk. This particular theory explains if the threats are perceived
by people as they are preventing the possible threats (Tsai et al. 2016). The research study found
that most of the factors like the perceived severity as well as self-efficacy influenced the users
for practicing the security behavior. This theory is based on four factors which are believed to be
motivated the users to protect themselves such as “perceived severity, perceived vulnerability,
Secure Best Marks with AI Grader
Need help grading? Try our AI Grader for instant feedback on your assignments.

70
MINIMIZING THE AFFECT OF HUMAN BEHAVIOUR RISKS RELATED TO
INFORMATION SECURITY
perceived benefits in addition to self efficacy”. This particular model is used to engage into risk
practices and offer suggestions to change into human behavior (Crossler et al. 2014). This theory
is concerned on how the individuals are processing the threats along with selecting the responses
to cope with the threats. The factors are divided into threat and copying appraisal. Threat
appraisal consists of perceived severity as well as perceived vulnerability and copying appraisal
includes of perceived benefits in addition to self efficacy. Threat appraisal is such that when
people have stronger perception on severity as well as vulnerability of the threats when it
motivates to avoid the security incidents (Mishra, Akman and Mishra 2014). Copying appraisal
is referred to capability of people for avoiding the security risks as well as belief which are
recommended security behavior.
Technology acceptance theory is used how the users are come to accept as well as use of
the technology. This theory is based on how the individual’s perceptions affect intentions to use
of the information technology. It is such a degree where person is to be believed that use of
information system raises the performance of the human behavior (Thong and Xu 2016). This
theory is used of perceived usefulness as well as perceived ease of use to determine the intention
of individual’s to use of the system for serving the mediator of actual use of system. This
particular theory is easier to apply across various research settings. It is consisted of security
factors in addition to it is used as mediator with direct as well as indirect relationship with the
factors and also consumer’s intention to use of single platform (Tsohou, Karyda and Kokolakis
2015). Few of the studies is made to present the models of the technology acceptance which is
used to evaluate the information system acceptances. Khaitan and McCalley (2015) stated that
TAM model is designed for comprehending the casual relationship among external variables of
MINIMIZING THE AFFECT OF HUMAN BEHAVIOUR RISKS RELATED TO
INFORMATION SECURITY
perceived benefits in addition to self efficacy”. This particular model is used to engage into risk
practices and offer suggestions to change into human behavior (Crossler et al. 2014). This theory
is concerned on how the individuals are processing the threats along with selecting the responses
to cope with the threats. The factors are divided into threat and copying appraisal. Threat
appraisal consists of perceived severity as well as perceived vulnerability and copying appraisal
includes of perceived benefits in addition to self efficacy. Threat appraisal is such that when
people have stronger perception on severity as well as vulnerability of the threats when it
motivates to avoid the security incidents (Mishra, Akman and Mishra 2014). Copying appraisal
is referred to capability of people for avoiding the security risks as well as belief which are
recommended security behavior.
Technology acceptance theory is used how the users are come to accept as well as use of
the technology. This theory is based on how the individual’s perceptions affect intentions to use
of the information technology. It is such a degree where person is to be believed that use of
information system raises the performance of the human behavior (Thong and Xu 2016). This
theory is used of perceived usefulness as well as perceived ease of use to determine the intention
of individual’s to use of the system for serving the mediator of actual use of system. This
particular theory is easier to apply across various research settings. It is consisted of security
factors in addition to it is used as mediator with direct as well as indirect relationship with the
factors and also consumer’s intention to use of single platform (Tsohou, Karyda and Kokolakis
2015). Few of the studies is made to present the models of the technology acceptance which is
used to evaluate the information system acceptances. Khaitan and McCalley (2015) stated that
TAM model is designed for comprehending the casual relationship among external variables of

71
MINIMIZING THE AFFECT OF HUMAN BEHAVIOUR RISKS RELATED TO
INFORMATION SECURITY
the acceptance of user along with real time use of the computer. It is required to understand the
user behavior throughout utility of the knowledge along with user facility perceived by the users.
3.8 Summary
It is summarized that the conceptual framework is synthesized from results of the
research investigation which argues that there are deliberate inclusion into the information
security throughout the strategic analysis. The research approaches in this paper suggested that
there are limitations of conducted investigations as well as direction towards the study.
Analyzing of the human behavior theories help to identify the human related factors which
become risks into the information security. The human factors are playing a key role towards the
information security. Human factors provide a high impact on the information security as it is
used to analyze and influence on the information security management system. The unsecured
information is being explored towards the public domains. The organization is not focused on
human factors with the technological competency. The human factors are dependent on the
individual’s characteristics which provide impact on the information system management. IT
security arrangement is such a model for the hierarchical culture where the values and methods
are driven from the representative way to deal with the data. This particular research also
influences as well as evaluates information security management system.
MINIMIZING THE AFFECT OF HUMAN BEHAVIOUR RISKS RELATED TO
INFORMATION SECURITY
the acceptance of user along with real time use of the computer. It is required to understand the
user behavior throughout utility of the knowledge along with user facility perceived by the users.
3.8 Summary
It is summarized that the conceptual framework is synthesized from results of the
research investigation which argues that there are deliberate inclusion into the information
security throughout the strategic analysis. The research approaches in this paper suggested that
there are limitations of conducted investigations as well as direction towards the study.
Analyzing of the human behavior theories help to identify the human related factors which
become risks into the information security. The human factors are playing a key role towards the
information security. Human factors provide a high impact on the information security as it is
used to analyze and influence on the information security management system. The unsecured
information is being explored towards the public domains. The organization is not focused on
human factors with the technological competency. The human factors are dependent on the
individual’s characteristics which provide impact on the information system management. IT
security arrangement is such a model for the hierarchical culture where the values and methods
are driven from the representative way to deal with the data. This particular research also
influences as well as evaluates information security management system.

72
MINIMIZING THE AFFECT OF HUMAN BEHAVIOUR RISKS RELATED TO
INFORMATION SECURITY
Chapter 4: Research Methodology
4.1 Introduction
The purpose of this chapter is to describe the research methodology which is used into
the research paper. There are two sections which describe the research purpose along with
research approaches (Clark and Creswell 2014). At end of this particular chapter, the research
data are gathered and analyzed the methods which are described. The purpose of this thesis paper
is to identify the countermeasures into the information security that the IT organization uses to
minimize and mitigate the internal threats. The researcher can able to understand the information
security issues along with countermeasures (Fletcher 2017). The knowledge related to the
internal threats as well as security countermeasures are being affected by the human factors
which help to choose the proper control mechanisms and reduce the level of risks and mitigate
the impacts. Flick (2015) determined that the research questions are required and considered as
important part to review existing literature. The main objective of research methodology is to
identify as well as justify the possible methods, data collection methods, research sample and
questionnaire using online survey. This particular section presents as well as discusses the
primary methods in order to answer to the research questions. Literature survey is done to review
the related literature (Humphries 2017). It is required to develop initial framework of this
research study as well as benefit from research which is related to the selected research topic for
covering the research objectives.
4.2 Research philosophy
Research philosophy is belief where the data about the phenomenon are gathered,
analyzed as well as utilized. Lewis (2015) expressed that examination rationality encourages the
MINIMIZING THE AFFECT OF HUMAN BEHAVIOUR RISKS RELATED TO
INFORMATION SECURITY
Chapter 4: Research Methodology
4.1 Introduction
The purpose of this chapter is to describe the research methodology which is used into
the research paper. There are two sections which describe the research purpose along with
research approaches (Clark and Creswell 2014). At end of this particular chapter, the research
data are gathered and analyzed the methods which are described. The purpose of this thesis paper
is to identify the countermeasures into the information security that the IT organization uses to
minimize and mitigate the internal threats. The researcher can able to understand the information
security issues along with countermeasures (Fletcher 2017). The knowledge related to the
internal threats as well as security countermeasures are being affected by the human factors
which help to choose the proper control mechanisms and reduce the level of risks and mitigate
the impacts. Flick (2015) determined that the research questions are required and considered as
important part to review existing literature. The main objective of research methodology is to
identify as well as justify the possible methods, data collection methods, research sample and
questionnaire using online survey. This particular section presents as well as discusses the
primary methods in order to answer to the research questions. Literature survey is done to review
the related literature (Humphries 2017). It is required to develop initial framework of this
research study as well as benefit from research which is related to the selected research topic for
covering the research objectives.
4.2 Research philosophy
Research philosophy is belief where the data about the phenomenon are gathered,
analyzed as well as utilized. Lewis (2015) expressed that examination rationality encourages the
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

73
MINIMIZING THE AFFECT OF HUMAN BEHAVIOUR RISKS RELATED TO
INFORMATION SECURITY
researcher to get a few data identified with chose inquire about theme and space being
contemplated. It additionally adds different measurements to the directed research think about.
Matthews and Ross (2014) initiated that determination of appropriate logic ensures that the
speculations and ideas are accessible to specialist to use the productivity of this particular
research. The theory enables the specialist to lead the examination into legitimate way. It deals
with sources, nature as well as development of the knowledge. McCusker and Gunaydin (2015)
argued that research philosophy address and involves with aware as well as formulate the beliefs
along with assumptions. There are three types of research philosophy such as positivism,
interpretivism and realism. Positivism is highly structured, larger samples along with
measurement of the collected data and information. Intrepretivism is referred to as smaller
samples which provide in-depth analysis of the research study (Neuman and Robson 2014). It
investigates collected data. Realism is the methods which are chosen to fit with the subject.
Justification for chosen research philosophy:
In this particular study; positivism is used as the research philosophy. Positivism is
believed that it is based on objective reality and is described from viewpoint of objective
(Simonsohn, Nelson and Simmons 2017). It contends phenomena which are isolated in addition
to the observations are repeatable. It involves of manipulation of reality with the variations into
single independent variable for identifying the regularities form relationships between
constituent elements of social world. Panneerselvam (2014) stated that positivism has rich
historical traditions.
MINIMIZING THE AFFECT OF HUMAN BEHAVIOUR RISKS RELATED TO
INFORMATION SECURITY
researcher to get a few data identified with chose inquire about theme and space being
contemplated. It additionally adds different measurements to the directed research think about.
Matthews and Ross (2014) initiated that determination of appropriate logic ensures that the
speculations and ideas are accessible to specialist to use the productivity of this particular
research. The theory enables the specialist to lead the examination into legitimate way. It deals
with sources, nature as well as development of the knowledge. McCusker and Gunaydin (2015)
argued that research philosophy address and involves with aware as well as formulate the beliefs
along with assumptions. There are three types of research philosophy such as positivism,
interpretivism and realism. Positivism is highly structured, larger samples along with
measurement of the collected data and information. Intrepretivism is referred to as smaller
samples which provide in-depth analysis of the research study (Neuman and Robson 2014). It
investigates collected data. Realism is the methods which are chosen to fit with the subject.
Justification for chosen research philosophy:
In this particular study; positivism is used as the research philosophy. Positivism is
believed that it is based on objective reality and is described from viewpoint of objective
(Simonsohn, Nelson and Simmons 2017). It contends phenomena which are isolated in addition
to the observations are repeatable. It involves of manipulation of reality with the variations into
single independent variable for identifying the regularities form relationships between
constituent elements of social world. Panneerselvam (2014) stated that positivism has rich
historical traditions.

74
MINIMIZING THE AFFECT OF HUMAN BEHAVIOUR RISKS RELATED TO
INFORMATION SECURITY
4.3 Research approach
The researcher is adopted of various methodological approaches for collecting of data. It
includes of quantitative as well as qualitative data for supporting the research outcome analysis.
This research approach helps to provide data and information from various resources for
achieving of research aims as well as objectives to answer the research questions. Taylor,
Bogdan and DeVault (2015) discussed that research philosophy is concerned with the views
about the world works with the academic subject which is based on reality and knowledge. There
are two types of research approach such as inductive and deductive approach. Inductive approach
is such an approach which starts with observation as well as end results of the research study is
theory (Vaioleti 2016). This particular approach has no hypothesis. Deductive approach is
approach for the research which starts with proposition of the research hypothesis and end results
of this research is confirmation or rejection. As there are shortage of time in this research study,
therefore depth analysis for larger samples are unattainable.
Justification for chosen research approach:
Deductive approach is chosen for this particular research study as this research is based
on three hypotheses. This approach is one which is associated with the scientific investigations
(Matthews and Ross 2014). The research study reads the existing theories of research
phenomenon where the research hypothesis is tested from the theories. This particular approach
is beginning with the hypothesis which is emphasized on causality. It also designs of research
strategy for testing the research hypothesis. It is explained by means of research hypothesis that
are derived from the propositions of existing theory. Viswanadham (2017) stated that deductive
approach is concerned with deduction of conclusions for finding the research patterns with them.
MINIMIZING THE AFFECT OF HUMAN BEHAVIOUR RISKS RELATED TO
INFORMATION SECURITY
4.3 Research approach
The researcher is adopted of various methodological approaches for collecting of data. It
includes of quantitative as well as qualitative data for supporting the research outcome analysis.
This research approach helps to provide data and information from various resources for
achieving of research aims as well as objectives to answer the research questions. Taylor,
Bogdan and DeVault (2015) discussed that research philosophy is concerned with the views
about the world works with the academic subject which is based on reality and knowledge. There
are two types of research approach such as inductive and deductive approach. Inductive approach
is such an approach which starts with observation as well as end results of the research study is
theory (Vaioleti 2016). This particular approach has no hypothesis. Deductive approach is
approach for the research which starts with proposition of the research hypothesis and end results
of this research is confirmation or rejection. As there are shortage of time in this research study,
therefore depth analysis for larger samples are unattainable.
Justification for chosen research approach:
Deductive approach is chosen for this particular research study as this research is based
on three hypotheses. This approach is one which is associated with the scientific investigations
(Matthews and Ross 2014). The research study reads the existing theories of research
phenomenon where the research hypothesis is tested from the theories. This particular approach
is beginning with the hypothesis which is emphasized on causality. It also designs of research
strategy for testing the research hypothesis. It is explained by means of research hypothesis that
are derived from the propositions of existing theory. Viswanadham (2017) stated that deductive
approach is concerned with deduction of conclusions for finding the research patterns with them.

75
MINIMIZING THE AFFECT OF HUMAN BEHAVIOUR RISKS RELATED TO
INFORMATION SECURITY
4.4 Research design
Clark and Creswell (2014) discussed that utilization of research configuration creates
system to gather and in addition break down the information. Appropriate utilization of research
plan strategy uncovers the examples alongside sources of information. There are three types of
research design such as descriptive, explanatory and explanatory. Exploratory research design is
provided insights in as well as comprehensive of the research issues along with situations (Flick
2015). It is such type of research which is conducted because of the issues which are not clearly
defined. It helps to determine proper research design, method of data collection along with
selection of research subjects. Descriptive research is defined as the statistical research which
describes the data as well as characteristics related to the population along with phenomenon
which are studied (Humphries 2017). It answers to the research questions, and based on one of
the research design for present study, it is required to gauge different projects which are specific
to the risks which impact the projects and understand the dynamics of the climate of organization
on the projects (Clark and Creswell 2014). Explanatory research design is being conducted for
the problems that are not well researched and provided better researcher model.
Justification for chosen research design:
Descriptive research design is adopted due to nature of this research study. It is a research
design which is used to depict the participants in proper way. It is about describing people those
are taken part into the research study. There are three procedures the researcher can do the
descriptive research study such as observational, case study and survey. McCusker and Gunaydin
(2015) discussed that this type of research design collects information from the target population
in order to describe the preferences, characteristics as well as practices. The example of
descriptive survey is questionnaire which used to solicit the information from the participants
MINIMIZING THE AFFECT OF HUMAN BEHAVIOUR RISKS RELATED TO
INFORMATION SECURITY
4.4 Research design
Clark and Creswell (2014) discussed that utilization of research configuration creates
system to gather and in addition break down the information. Appropriate utilization of research
plan strategy uncovers the examples alongside sources of information. There are three types of
research design such as descriptive, explanatory and explanatory. Exploratory research design is
provided insights in as well as comprehensive of the research issues along with situations (Flick
2015). It is such type of research which is conducted because of the issues which are not clearly
defined. It helps to determine proper research design, method of data collection along with
selection of research subjects. Descriptive research is defined as the statistical research which
describes the data as well as characteristics related to the population along with phenomenon
which are studied (Humphries 2017). It answers to the research questions, and based on one of
the research design for present study, it is required to gauge different projects which are specific
to the risks which impact the projects and understand the dynamics of the climate of organization
on the projects (Clark and Creswell 2014). Explanatory research design is being conducted for
the problems that are not well researched and provided better researcher model.
Justification for chosen research design:
Descriptive research design is adopted due to nature of this research study. It is a research
design which is used to depict the participants in proper way. It is about describing people those
are taken part into the research study. There are three procedures the researcher can do the
descriptive research study such as observational, case study and survey. McCusker and Gunaydin
(2015) discussed that this type of research design collects information from the target population
in order to describe the preferences, characteristics as well as practices. The example of
descriptive survey is questionnaire which used to solicit the information from the participants
Secure Best Marks with AI Grader
Need help grading? Try our AI Grader for instant feedback on your assignments.

76
MINIMIZING THE AFFECT OF HUMAN BEHAVIOUR RISKS RELATED TO
INFORMATION SECURITY
based on selected research topic. The descriptive statistical techniques consist of three purposes
such as describe the relationships among the variables, describe the variables and describe the
distributions (Matthews and Ross 2014). The descriptive design is accurate for this particular
study as it minimizes the affect of human behavior risks related to the information security.
4.5 Data collection process
While doing work into the examination consider, the information is being accounted as
most critical data which is required for this specific investigation. Sensitive information is
valuable to give knowledge information in view of selected topic. Matthews and Ross (2014)
indicated that use of the best possible data is significant to the investigation resource for convey
exactness of information while keeping up of the standard research examine. At the time of
collecting of survey data, it is required to verify the research settings which are discussed in
chapter 3 into the conceptual research framework. The tools as well as techniques of data
collection help to collect of required data (Clark and Creswell 2014). With help of the data
collection tools, it is required to transfer facts from the fields into the data as well as tables. Into
the process of collection, there is possibility of loss of some of the data information (McCusker
and Gunaydin 2015). Proper information is being collected as well as utilized for purpose of data
analysis as well as interpretation.
4.5.1 Data sources
The chose information source for this specific research study is essential primary data
collection method. Into this particular data collection method, one can able to ask questions
related to the problems which are being investigated (Clark and Creswell 2014). People can
make observations related to the research questions which are identified in Chapter 1. One can
able to utilize the existing records as well as data which are gathered by others. The collection of
MINIMIZING THE AFFECT OF HUMAN BEHAVIOUR RISKS RELATED TO
INFORMATION SECURITY
based on selected research topic. The descriptive statistical techniques consist of three purposes
such as describe the relationships among the variables, describe the variables and describe the
distributions (Matthews and Ross 2014). The descriptive design is accurate for this particular
study as it minimizes the affect of human behavior risks related to the information security.
4.5 Data collection process
While doing work into the examination consider, the information is being accounted as
most critical data which is required for this specific investigation. Sensitive information is
valuable to give knowledge information in view of selected topic. Matthews and Ross (2014)
indicated that use of the best possible data is significant to the investigation resource for convey
exactness of information while keeping up of the standard research examine. At the time of
collecting of survey data, it is required to verify the research settings which are discussed in
chapter 3 into the conceptual research framework. The tools as well as techniques of data
collection help to collect of required data (Clark and Creswell 2014). With help of the data
collection tools, it is required to transfer facts from the fields into the data as well as tables. Into
the process of collection, there is possibility of loss of some of the data information (McCusker
and Gunaydin 2015). Proper information is being collected as well as utilized for purpose of data
analysis as well as interpretation.
4.5.1 Data sources
The chose information source for this specific research study is essential primary data
collection method. Into this particular data collection method, one can able to ask questions
related to the problems which are being investigated (Clark and Creswell 2014). People can
make observations related to the research questions which are identified in Chapter 1. One can
able to utilize the existing records as well as data which are gathered by others. The collection of

77
MINIMIZING THE AFFECT OF HUMAN BEHAVIOUR RISKS RELATED TO
INFORMATION SECURITY
primary data is involved of making oneself ready for the physically to collect the primary data
from the field situations (Simonsohn, Nelson and Simmons 2017). The participants can also keep
a field of book to record all the important as well as relevant information related to the research
study. They also write down all the records of occurrence of the situations at proper time
intervals. Administering of the research questionnaire schedule is to target the groups of area
people across the sampled sites. It also verifies the facts throughout the checks into the answers
along with the ground realities (McCusker and Gunaydin 2015). The research study integrates
the observations, responses as well as records the facts into proper as well as logical framework.
For motivation behind this examination consider, survey technique is utilized as the information
gathering process. Overview strategy is an individual and additionally unstructured technique
whose point is to perceive the feelings of the members, emotions alongside suppositions with
respect to the exploration subject (Matthews and Ross 2014). To the extent the data collection
tools are concerned, the exploration is directed with utilization of organized polls which is
imparted to the chosen members online. Some particular inquiries are readied; in this way the
analyst leads the online overview towards the fulfillment of research goals. The overview is
utilized to gather the first information to depict the populace too expensive for watching
straightforwardly.
4.5.2 Data techniques
A mixed approach is used in this particular study includes collecting qualitative and
quantitative data. The data from the research fieldwork such as UAE’s IT services are required to
provide raw data used to recognize as well as explore of information security culture. It also
explores the challenges to promote as well as enhance the information security culture.
McCusker and Gunaydin (2015) stated that data collection process is aimed to provide raw data
MINIMIZING THE AFFECT OF HUMAN BEHAVIOUR RISKS RELATED TO
INFORMATION SECURITY
primary data is involved of making oneself ready for the physically to collect the primary data
from the field situations (Simonsohn, Nelson and Simmons 2017). The participants can also keep
a field of book to record all the important as well as relevant information related to the research
study. They also write down all the records of occurrence of the situations at proper time
intervals. Administering of the research questionnaire schedule is to target the groups of area
people across the sampled sites. It also verifies the facts throughout the checks into the answers
along with the ground realities (McCusker and Gunaydin 2015). The research study integrates
the observations, responses as well as records the facts into proper as well as logical framework.
For motivation behind this examination consider, survey technique is utilized as the information
gathering process. Overview strategy is an individual and additionally unstructured technique
whose point is to perceive the feelings of the members, emotions alongside suppositions with
respect to the exploration subject (Matthews and Ross 2014). To the extent the data collection
tools are concerned, the exploration is directed with utilization of organized polls which is
imparted to the chosen members online. Some particular inquiries are readied; in this way the
analyst leads the online overview towards the fulfillment of research goals. The overview is
utilized to gather the first information to depict the populace too expensive for watching
straightforwardly.
4.5.2 Data techniques
A mixed approach is used in this particular study includes collecting qualitative and
quantitative data. The data from the research fieldwork such as UAE’s IT services are required to
provide raw data used to recognize as well as explore of information security culture. It also
explores the challenges to promote as well as enhance the information security culture.
McCusker and Gunaydin (2015) stated that data collection process is aimed to provide raw data

78
MINIMIZING THE AFFECT OF HUMAN BEHAVIOUR RISKS RELATED TO
INFORMATION SECURITY
as well as information which help to develop the information security model culture. This
particular stage is involved to distribute the semi-structured questionnaire to the organization. It
involves conducting of in-depth analysis of the key personnel feedback. The key personnel give
their opinions as well as attitudes towards the information security culture along with the factors
influence the information security culture. The main purpose of questionnaire method is to
explore as well as identify the culture help with development of initial information security
culture model (Simonsohn, Nelson and Simmons 2017). The main outcome of this particular
project stage is to combine with the outcomes of the literature review which helps to develop
initial security culture model. The model is required to achieve of the research objectives.
Quantitative information method is utilized which is built of measurable models to clarify
the gathered information (Matthews and Ross 2014). The scientist is utilized of poll for gathering
the numerical information. The parts of this exploration think about are composed appropriately
before the information is gathered. It gives exact estimation and additionally investigation of the
objective ideas, for example, utilization of review and survey (Simonsohn, Nelson and Simmons
2017). It is stressed of target estimations alongside numerical investigation of the gathered
information. This information method will control the previous information with utilization of
exceed expectations sheet. The information are centered on factual information alongside
speculation over the gatherings of members to clarify the chose inquire about subject.
4.6 Sampling method
The technique for sampling is chosen for this examination think about is non-likelihood
inspecting where the sample members are chosen in light of their insight, connections and
additionally ability into the exploration branch of knowledge. Into this current research study
inquires about examination, the sample members those are chosen has uncommon association
MINIMIZING THE AFFECT OF HUMAN BEHAVIOUR RISKS RELATED TO
INFORMATION SECURITY
as well as information which help to develop the information security model culture. This
particular stage is involved to distribute the semi-structured questionnaire to the organization. It
involves conducting of in-depth analysis of the key personnel feedback. The key personnel give
their opinions as well as attitudes towards the information security culture along with the factors
influence the information security culture. The main purpose of questionnaire method is to
explore as well as identify the culture help with development of initial information security
culture model (Simonsohn, Nelson and Simmons 2017). The main outcome of this particular
project stage is to combine with the outcomes of the literature review which helps to develop
initial security culture model. The model is required to achieve of the research objectives.
Quantitative information method is utilized which is built of measurable models to clarify
the gathered information (Matthews and Ross 2014). The scientist is utilized of poll for gathering
the numerical information. The parts of this exploration think about are composed appropriately
before the information is gathered. It gives exact estimation and additionally investigation of the
objective ideas, for example, utilization of review and survey (Simonsohn, Nelson and Simmons
2017). It is stressed of target estimations alongside numerical investigation of the gathered
information. This information method will control the previous information with utilization of
exceed expectations sheet. The information are centered on factual information alongside
speculation over the gatherings of members to clarify the chose inquire about subject.
4.6 Sampling method
The technique for sampling is chosen for this examination think about is non-likelihood
inspecting where the sample members are chosen in light of their insight, connections and
additionally ability into the exploration branch of knowledge. Into this current research study
inquires about examination, the sample members those are chosen has uncommon association
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

79
MINIMIZING THE AFFECT OF HUMAN BEHAVIOUR RISKS RELATED TO
INFORMATION SECURITY
with marvel under the examination and pertinent work understanding into the IT organization
(McCusker and Gunaydin 2015).
4.7 Ethical considerations
The current research study looks into think about is liable to moral issues. While
conducting out the information gathering alongside information examination, the researcher
requires thinking about various issues to keep up the exploration morals. The researcher is
required to distinguish the contrasts between wrong and in addition right arrangement of the
human practices require leading this specific investigation. The members are educated with
respect to the examination destinations, as they are consoled that the reactions of the members
are dealt with secret and also utilized for the scholarly purposes and for this specific research
just. The information are being put away are being ensured by strict codes of morals. The
specialist comprises of lawful access to the data. McCusker and Gunaydin (2015) indicated that
entrance the data acquired from this investigation depends on essential sources which shield the
specialists for fake purposes. The scientist guarantees that the information and in addition data
utilized into this examination consider are not utilized industrially. The analyst cannot furnish
standard process alongside methods to assess the chose inquire about point. The researcher keeps
up code of morals to give expected standard to the examination think about (Simonsohn, Nelson
and Simmons 2017). The optional information is being referred to by utilization of Harvard
referencing. The secondary information is as a rule entirely assessed to precision alongside
legitimacy with basic appraisal of the exploration approach.
4.8 Limitations of the research study
In a portion of the cases, the members are declined to talk against their association and
they are not willing to give any data of their association. There are different researches
MINIMIZING THE AFFECT OF HUMAN BEHAVIOUR RISKS RELATED TO
INFORMATION SECURITY
with marvel under the examination and pertinent work understanding into the IT organization
(McCusker and Gunaydin 2015).
4.7 Ethical considerations
The current research study looks into think about is liable to moral issues. While
conducting out the information gathering alongside information examination, the researcher
requires thinking about various issues to keep up the exploration morals. The researcher is
required to distinguish the contrasts between wrong and in addition right arrangement of the
human practices require leading this specific investigation. The members are educated with
respect to the examination destinations, as they are consoled that the reactions of the members
are dealt with secret and also utilized for the scholarly purposes and for this specific research
just. The information are being put away are being ensured by strict codes of morals. The
specialist comprises of lawful access to the data. McCusker and Gunaydin (2015) indicated that
entrance the data acquired from this investigation depends on essential sources which shield the
specialists for fake purposes. The scientist guarantees that the information and in addition data
utilized into this examination consider are not utilized industrially. The analyst cannot furnish
standard process alongside methods to assess the chose inquire about point. The researcher keeps
up code of morals to give expected standard to the examination think about (Simonsohn, Nelson
and Simmons 2017). The optional information is being referred to by utilization of Harvard
referencing. The secondary information is as a rule entirely assessed to precision alongside
legitimacy with basic appraisal of the exploration approach.
4.8 Limitations of the research study
In a portion of the cases, the members are declined to talk against their association and
they are not willing to give any data of their association. There are different researches

80
MINIMIZING THE AFFECT OF HUMAN BEHAVIOUR RISKS RELATED TO
INFORMATION SECURITY
limitations which affect the structure of this examination consider alongside nature of
investigation. As indicated by Clark and Creswell (2014), an exploration work is restricted to a
few research limitations which are normal alongside helps to characterize notwithstanding
confined extent of embraced consider. Following are the examination impediments to direct the
exploration concentrate, for example,
Time constraint: The scheduled time to perform this particular research study along with
minimization of affects of human behavior risks related to information security. Because of the
research limitations, the researcher is required to conduct the cross sectional study. This
particular study is being limited to conduct a detailed analysis along with evaluate the hidden
details of selected topic. Because of the time limitation, the researcher is conducted this research
study based on the IT organization only and the research study is mainly based on primary data.
The researcher tries to end the research study within the scheduled time so that there is no such
possibility of any deadline missed or any kind of delays into the project.
Data reliability: The data are collected from the employees of IT organization in the form
of online questionnaire which is gathered through use of survey. The respondents are being one-
sided towards the association while getting input which impacts the consequences of this
examination think about. To lead the information for this examination, the scientist should
utilization of essential information investigation to take a review. Each of the data is to be kept
into confidential place so that no other unauthorized person can able to access to those data.
Therefore, each of the data is kept into the database system with password protected.
Budget limitations: This specific research contemplates is being given constrained
spending which comprises of confined extent of this examination. Into tight research spending
MINIMIZING THE AFFECT OF HUMAN BEHAVIOUR RISKS RELATED TO
INFORMATION SECURITY
limitations which affect the structure of this examination consider alongside nature of
investigation. As indicated by Clark and Creswell (2014), an exploration work is restricted to a
few research limitations which are normal alongside helps to characterize notwithstanding
confined extent of embraced consider. Following are the examination impediments to direct the
exploration concentrate, for example,
Time constraint: The scheduled time to perform this particular research study along with
minimization of affects of human behavior risks related to information security. Because of the
research limitations, the researcher is required to conduct the cross sectional study. This
particular study is being limited to conduct a detailed analysis along with evaluate the hidden
details of selected topic. Because of the time limitation, the researcher is conducted this research
study based on the IT organization only and the research study is mainly based on primary data.
The researcher tries to end the research study within the scheduled time so that there is no such
possibility of any deadline missed or any kind of delays into the project.
Data reliability: The data are collected from the employees of IT organization in the form
of online questionnaire which is gathered through use of survey. The respondents are being one-
sided towards the association while getting input which impacts the consequences of this
examination think about. To lead the information for this examination, the scientist should
utilization of essential information investigation to take a review. Each of the data is to be kept
into confidential place so that no other unauthorized person can able to access to those data.
Therefore, each of the data is kept into the database system with password protected.
Budget limitations: This specific research contemplates is being given constrained
spending which comprises of confined extent of this examination. Into tight research spending
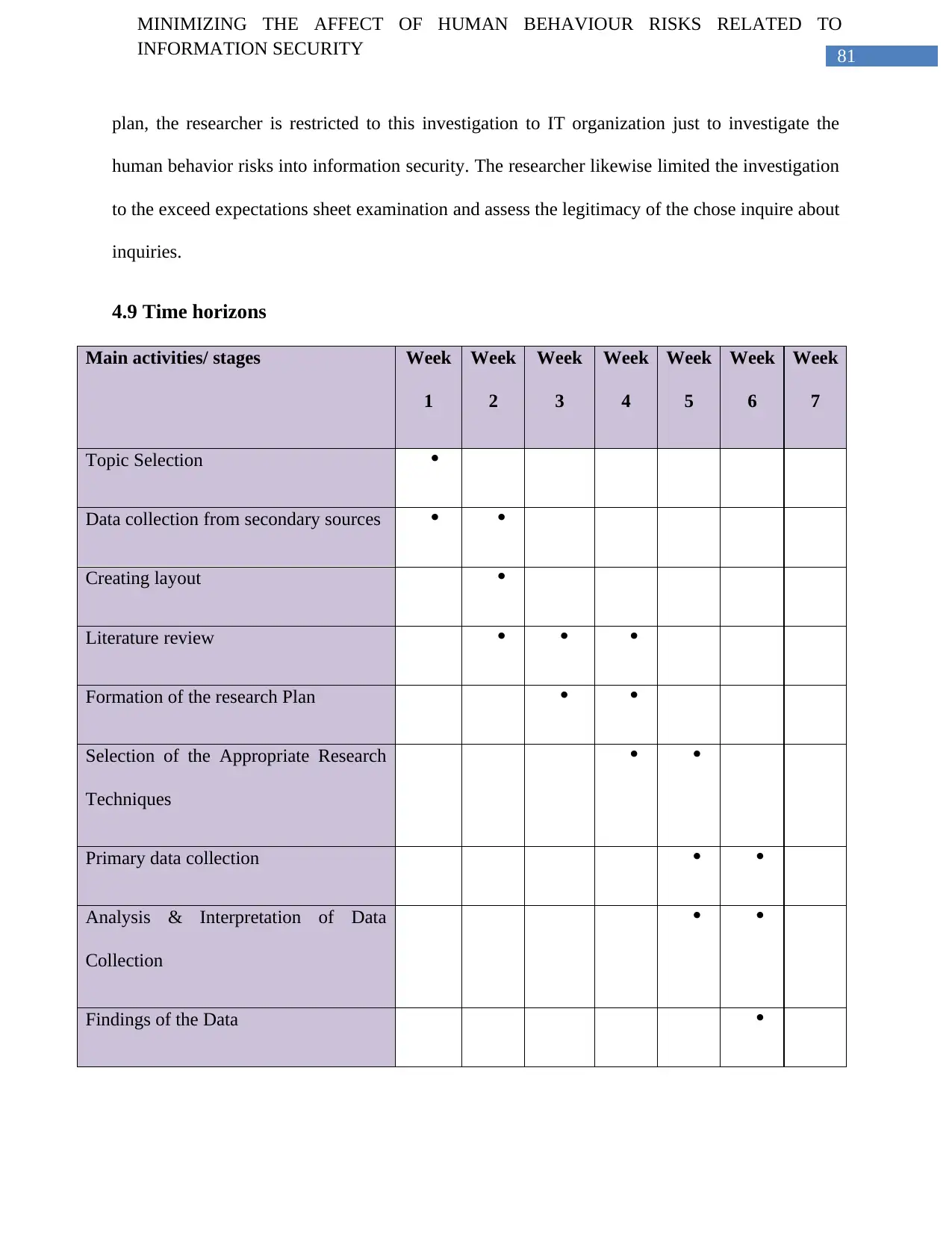
81
MINIMIZING THE AFFECT OF HUMAN BEHAVIOUR RISKS RELATED TO
INFORMATION SECURITY
plan, the researcher is restricted to this investigation to IT organization just to investigate the
human behavior risks into information security. The researcher likewise limited the investigation
to the exceed expectations sheet examination and assess the legitimacy of the chose inquire about
inquiries.
4.9 Time horizons
Main activities/ stages Week
1
Week
2
Week
3
Week
4
Week
5
Week
6
Week
7
Topic Selection
Data collection from secondary sources
Creating layout
Literature review
Formation of the research Plan
Selection of the Appropriate Research
Techniques
Primary data collection
Analysis & Interpretation of Data
Collection
Findings of the Data
MINIMIZING THE AFFECT OF HUMAN BEHAVIOUR RISKS RELATED TO
INFORMATION SECURITY
plan, the researcher is restricted to this investigation to IT organization just to investigate the
human behavior risks into information security. The researcher likewise limited the investigation
to the exceed expectations sheet examination and assess the legitimacy of the chose inquire about
inquiries.
4.9 Time horizons
Main activities/ stages Week
1
Week
2
Week
3
Week
4
Week
5
Week
6
Week
7
Topic Selection
Data collection from secondary sources
Creating layout
Literature review
Formation of the research Plan
Selection of the Appropriate Research
Techniques
Primary data collection
Analysis & Interpretation of Data
Collection
Findings of the Data
Secure Best Marks with AI Grader
Need help grading? Try our AI Grader for instant feedback on your assignments.
82
MINIMIZING THE AFFECT OF HUMAN BEHAVIOUR RISKS RELATED TO
INFORMATION SECURITY
Conclusion of the Study
Formation of Rough Draft
Submission of Final Work
4.10 Summary
It is summarized that collected data are analyzed for providing results which are used for
supporting the research as well as argue to the main findings regards to the information security
cultural dimensions. The chapter is identified as well as justified the research methodology, data
collection methods, research sample along with questionnaire of the research. The next charter is
analyzed in the future which include of tools for analyzing collected data from the fieldwork.
This specific part depicts of different research strategy apparatuses which are utilized to direct
better examination on chose inquire about subject. The researcher is attempted to adjust the idea
of this examination think about with variable for different research procedures to such an extent
that best research strategies are to be confined. The examination devices are appropriate for
dissecting the ideas of minimizing the human behavior risks related to information security.
Essential and in addition secondary information accumulation strategies betters examine the
exploration think about with the goal that the examiner should better comprehend the chosen
research topic. The entire research study is mainly based on the primary data collection method
where all the data are collected through use of online survey, and the participants those are
interested into the study are only considered to provide their feedback based on the
questionnaire. The data collection process is aimed to provide raw data as well as information
MINIMIZING THE AFFECT OF HUMAN BEHAVIOUR RISKS RELATED TO
INFORMATION SECURITY
Conclusion of the Study
Formation of Rough Draft
Submission of Final Work
4.10 Summary
It is summarized that collected data are analyzed for providing results which are used for
supporting the research as well as argue to the main findings regards to the information security
cultural dimensions. The chapter is identified as well as justified the research methodology, data
collection methods, research sample along with questionnaire of the research. The next charter is
analyzed in the future which include of tools for analyzing collected data from the fieldwork.
This specific part depicts of different research strategy apparatuses which are utilized to direct
better examination on chose inquire about subject. The researcher is attempted to adjust the idea
of this examination think about with variable for different research procedures to such an extent
that best research strategies are to be confined. The examination devices are appropriate for
dissecting the ideas of minimizing the human behavior risks related to information security.
Essential and in addition secondary information accumulation strategies betters examine the
exploration think about with the goal that the examiner should better comprehend the chosen
research topic. The entire research study is mainly based on the primary data collection method
where all the data are collected through use of online survey, and the participants those are
interested into the study are only considered to provide their feedback based on the
questionnaire. The data collection process is aimed to provide raw data as well as information
83
MINIMIZING THE AFFECT OF HUMAN BEHAVIOUR RISKS RELATED TO
INFORMATION SECURITY
which help to develop the information security model culture. This particular stage is involved to
distribute the semi-structured questionnaire to the organization.
MINIMIZING THE AFFECT OF HUMAN BEHAVIOUR RISKS RELATED TO
INFORMATION SECURITY
which help to develop the information security model culture. This particular stage is involved to
distribute the semi-structured questionnaire to the organization.

84
MINIMIZING THE AFFECT OF HUMAN BEHAVIOUR RISKS RELATED TO
INFORMATION SECURITY
References
Ab Rahman, N.H. and Choo, K.K.R., 2015. A survey of information security incident
handling in the cloud. Computers & Security, 49, pp.45-69.
Abbasi, A., Sarker, S. and Chiang, R.H., 2016. Big data research in information systems:
Toward an inclusive research agenda. Journal of the Association for Information
Systems, 17(2).
Alexander, D.E., 2014. Social media in disaster risk reduction and crisis
management. Science and engineering ethics, 20(3), pp.717-733.
Chen, M.F. and Tung, P.J., 2014. Developing an extended theory of planned behavior model
to predict consumers’ intention to visit green hotels. International journal of hospitality
management, 36, pp.221-230.
Cheng, L., Li, W., Zhai, Q. and Smyth, R., 2014. Understanding personal use of the Internet
at work: An integrated model of neutralization techniques and general deterrence
theory. Computers in Human Behavior, 38, pp.220-228.
Clark, V.L.P. and Creswell, J.W., 2014. Understanding research: A consumer's guide.
Pearson Higher Ed.
Crossler, R.E., Johnston, A.C., Lowry, P.B., Hu, Q., Warkentin, M. and Baskerville, R.,
2013. Future directions for behavioral information security research. computers &
security, 32, pp.90-101.
MINIMIZING THE AFFECT OF HUMAN BEHAVIOUR RISKS RELATED TO
INFORMATION SECURITY
References
Ab Rahman, N.H. and Choo, K.K.R., 2015. A survey of information security incident
handling in the cloud. Computers & Security, 49, pp.45-69.
Abbasi, A., Sarker, S. and Chiang, R.H., 2016. Big data research in information systems:
Toward an inclusive research agenda. Journal of the Association for Information
Systems, 17(2).
Alexander, D.E., 2014. Social media in disaster risk reduction and crisis
management. Science and engineering ethics, 20(3), pp.717-733.
Chen, M.F. and Tung, P.J., 2014. Developing an extended theory of planned behavior model
to predict consumers’ intention to visit green hotels. International journal of hospitality
management, 36, pp.221-230.
Cheng, L., Li, W., Zhai, Q. and Smyth, R., 2014. Understanding personal use of the Internet
at work: An integrated model of neutralization techniques and general deterrence
theory. Computers in Human Behavior, 38, pp.220-228.
Clark, V.L.P. and Creswell, J.W., 2014. Understanding research: A consumer's guide.
Pearson Higher Ed.
Crossler, R.E., Johnston, A.C., Lowry, P.B., Hu, Q., Warkentin, M. and Baskerville, R.,
2013. Future directions for behavioral information security research. computers &
security, 32, pp.90-101.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

85
MINIMIZING THE AFFECT OF HUMAN BEHAVIOUR RISKS RELATED TO
INFORMATION SECURITY
Crossler, R.E., Long, J.H., Loraas, T.M. and Trinkle, B.S., 2014. Understanding compliance
with bring your own device policies utilizing protection motivation theory: Bridging the
intention-behavior gap. Journal of Information Systems, 28(1), pp.209-226.
De Leeuw, A., Valois, P., Ajzen, I. and Schmidt, P., 2015. Using the theory of planned
behavior to identify key beliefs underlying pro-environmental behavior in high-school
students: Implications for educational interventions. Journal of Environmental
Psychology, 42, pp.128-138.
Fletcher, A.J., 2017. Applying critical realism in qualitative research: methodology meets
method. International Journal of Social Research Methodology, 20(2), pp.181-194.
Flick, U., 2015. Introducing research methodology: A beginner's guide to doing a research
project. Sage.
Gerber, N., McDermott, R., Volkamer, M. and Vogt, J., 2016. Understanding Information
Security Compliance-Why Goal Setting and Rewards Might be a Bad Idea. In HAISA (pp.
145-155).
Gritzalis, D., Kandias, M., Stavrou, V. and Mitrou, L., 2014. History of information: the case
of privacy and security in social media. In Proc. of the History of Information
Conference(pp. 283-310).
Hajli, N. and Lin, X., 2016. Exploring the security of information sharing on social
networking sites: The role of perceived control of information. Journal of Business
Ethics, 133(1), pp.111-123.
He, D., Zeadally, S., Kumar, N. and Lee, J.H., 2017. Anonymous authentication for wireless
MINIMIZING THE AFFECT OF HUMAN BEHAVIOUR RISKS RELATED TO
INFORMATION SECURITY
Crossler, R.E., Long, J.H., Loraas, T.M. and Trinkle, B.S., 2014. Understanding compliance
with bring your own device policies utilizing protection motivation theory: Bridging the
intention-behavior gap. Journal of Information Systems, 28(1), pp.209-226.
De Leeuw, A., Valois, P., Ajzen, I. and Schmidt, P., 2015. Using the theory of planned
behavior to identify key beliefs underlying pro-environmental behavior in high-school
students: Implications for educational interventions. Journal of Environmental
Psychology, 42, pp.128-138.
Fletcher, A.J., 2017. Applying critical realism in qualitative research: methodology meets
method. International Journal of Social Research Methodology, 20(2), pp.181-194.
Flick, U., 2015. Introducing research methodology: A beginner's guide to doing a research
project. Sage.
Gerber, N., McDermott, R., Volkamer, M. and Vogt, J., 2016. Understanding Information
Security Compliance-Why Goal Setting and Rewards Might be a Bad Idea. In HAISA (pp.
145-155).
Gritzalis, D., Kandias, M., Stavrou, V. and Mitrou, L., 2014. History of information: the case
of privacy and security in social media. In Proc. of the History of Information
Conference(pp. 283-310).
Hajli, N. and Lin, X., 2016. Exploring the security of information sharing on social
networking sites: The role of perceived control of information. Journal of Business
Ethics, 133(1), pp.111-123.
He, D., Zeadally, S., Kumar, N. and Lee, J.H., 2017. Anonymous authentication for wireless

86
MINIMIZING THE AFFECT OF HUMAN BEHAVIOUR RISKS RELATED TO
INFORMATION SECURITY
body area networks with provable security. IEEE Systems Journal, 11(4), pp.2590-2601.
Heckmann, I., Comes, T. and Nickel, S., 2015. A critical review on supply chain risk–
Definition, measure and modeling. Omega, 52, pp.119-132.
Hsu, J.S.C., Shih, S.P., Hung, Y.W. and Lowry, P.B., 2015. The role of extra-role behaviors
and social controls in information security policy effectiveness. Information Systems
Research, 26(2), pp.282-300.
Humphries, B., 2017. Re-thinking social research: anti-discriminatory approaches in
research methodology. Taylor & Francis.
Ifinedo, P., 2014. Information systems security policy compliance: An empirical study of the
effects of socialisation, influence, and cognition. Information & Management, 51(1), pp.69-
79.
Kampas, S.R., Tarkowski, A.R., Portell, C.M. and Bhatti, N., Accenture Global Services Ltd,
2016. System and method for cloud enterprise services. U.S. Patent 9,235,442.
Katzenbeisser, S. and Petitcolas, F., 2016. Information hiding. Artech house.
Kautonen, T., Gelderen, M. and Fink, M., 2015. Robustness of the theory of planned
behavior in predicting entrepreneurial intentions and actions. Entrepreneurship Theory and
Practice, 39(3), pp.655-674.
Kim, S.H., Yang, K.H. and Park, S., 2014. An integrative behavioral model of information
security policy compliance. The Scientific World Journal, 2014.
Layton, T.P., 2016. Information Security: Design, implementation, measurement, and
MINIMIZING THE AFFECT OF HUMAN BEHAVIOUR RISKS RELATED TO
INFORMATION SECURITY
body area networks with provable security. IEEE Systems Journal, 11(4), pp.2590-2601.
Heckmann, I., Comes, T. and Nickel, S., 2015. A critical review on supply chain risk–
Definition, measure and modeling. Omega, 52, pp.119-132.
Hsu, J.S.C., Shih, S.P., Hung, Y.W. and Lowry, P.B., 2015. The role of extra-role behaviors
and social controls in information security policy effectiveness. Information Systems
Research, 26(2), pp.282-300.
Humphries, B., 2017. Re-thinking social research: anti-discriminatory approaches in
research methodology. Taylor & Francis.
Ifinedo, P., 2014. Information systems security policy compliance: An empirical study of the
effects of socialisation, influence, and cognition. Information & Management, 51(1), pp.69-
79.
Kampas, S.R., Tarkowski, A.R., Portell, C.M. and Bhatti, N., Accenture Global Services Ltd,
2016. System and method for cloud enterprise services. U.S. Patent 9,235,442.
Katzenbeisser, S. and Petitcolas, F., 2016. Information hiding. Artech house.
Kautonen, T., Gelderen, M. and Fink, M., 2015. Robustness of the theory of planned
behavior in predicting entrepreneurial intentions and actions. Entrepreneurship Theory and
Practice, 39(3), pp.655-674.
Kim, S.H., Yang, K.H. and Park, S., 2014. An integrative behavioral model of information
security policy compliance. The Scientific World Journal, 2014.
Layton, T.P., 2016. Information Security: Design, implementation, measurement, and

87
MINIMIZING THE AFFECT OF HUMAN BEHAVIOUR RISKS RELATED TO
INFORMATION SECURITY
compliance. CRC Press.
Lewis, S., 2015. Qualitative inquiry and research design: Choosing among five
approaches. Health promotion practice, 16(4), pp.473-475.
Malekian, A., Hayati, D. and Aarts, N., 2017. Conceptualizations of water security in the
agricultural sector: Perceptions, practices, and paradigms. Journal of Hydrology, 544,
pp.224-232.
Martins, C., Oliveira, T. and Popovič, A., 2014. Understanding the Internet banking
adoption: A unified theory of acceptance and use of technology and perceived risk
application. International Journal of Information Management, 34(1), pp.1-13.
Matthews, B. and Ross, L., 2014. Research methods. Pearson Higher Ed.
McCusker, K. and Gunaydin, S., 2015. Research using qualitative, quantitative or mixed
methods and choice based on the research. Perfusion, 30(7), pp.537-542.
Mishra, D., Akman, I. and Mishra, A., 2014. Theory of reasoned action application for green
information technology acceptance. Computers in human behavior, 36, pp.29-40.
Mishra, D., Akman, I. and Mishra, A., 2014. Theory of reasoned action application for green
information technology acceptance. Computers in human behavior, 36, pp.29-40.
Montano, D.E. and Kasprzyk, D., 2015. Theory of reasoned action, theory of planned
behavior, and the integrated behavioral model. Health behavior: Theory, research and
practice, pp.95-124.
Montano, D.E. and Kasprzyk, D., 2015. Theory of reasoned action, theory of planned
MINIMIZING THE AFFECT OF HUMAN BEHAVIOUR RISKS RELATED TO
INFORMATION SECURITY
compliance. CRC Press.
Lewis, S., 2015. Qualitative inquiry and research design: Choosing among five
approaches. Health promotion practice, 16(4), pp.473-475.
Malekian, A., Hayati, D. and Aarts, N., 2017. Conceptualizations of water security in the
agricultural sector: Perceptions, practices, and paradigms. Journal of Hydrology, 544,
pp.224-232.
Martins, C., Oliveira, T. and Popovič, A., 2014. Understanding the Internet banking
adoption: A unified theory of acceptance and use of technology and perceived risk
application. International Journal of Information Management, 34(1), pp.1-13.
Matthews, B. and Ross, L., 2014. Research methods. Pearson Higher Ed.
McCusker, K. and Gunaydin, S., 2015. Research using qualitative, quantitative or mixed
methods and choice based on the research. Perfusion, 30(7), pp.537-542.
Mishra, D., Akman, I. and Mishra, A., 2014. Theory of reasoned action application for green
information technology acceptance. Computers in human behavior, 36, pp.29-40.
Mishra, D., Akman, I. and Mishra, A., 2014. Theory of reasoned action application for green
information technology acceptance. Computers in human behavior, 36, pp.29-40.
Montano, D.E. and Kasprzyk, D., 2015. Theory of reasoned action, theory of planned
behavior, and the integrated behavioral model. Health behavior: Theory, research and
practice, pp.95-124.
Montano, D.E. and Kasprzyk, D., 2015. Theory of reasoned action, theory of planned
Secure Best Marks with AI Grader
Need help grading? Try our AI Grader for instant feedback on your assignments.

88
MINIMIZING THE AFFECT OF HUMAN BEHAVIOUR RISKS RELATED TO
INFORMATION SECURITY
behavior, and the integrated behavioral model.
Mullan, B., Norman, P., Boer, H. and Seydel, E., 2015. Protection motivation theory.
In Predicting and changing health behaviour: Research and practice with social cognition
models (pp. x-x). Open University Press.
Panneerselvam, R., 2014. Research methodology. PHI Learning Pvt. Ltd..
Paul, J., Modi, A. and Patel, J., 2016. Predicting green product consumption using theory of
planned behavior and reasoned action. Journal of Retailing and Consumer Services, 29,
pp.123-134.
Pearlson, K.E., Saunders, C.S. and Galletta, D.F., 2016. Managing and Using Information
Systems, Binder Ready Version: A Strategic Approach. John Wiley & Sons.
Peltier, T.R., 2016. Information Security Policies, Procedures, and Standards: guidelines for
effective information security management. CRC Press.
Peltier, T.R., 2016. Information Security Policies, Procedures, and Standards: guidelines for
effective information security management. CRC Press.
Safa, N.S., Sookhak, M., Von Solms, R., Furnell, S., Ghani, N.A. and Herawan, T., 2015.
Information security conscious care behaviour formation in organizations. Computers &
Security, 53, pp.65-78.
Safa, N.S., Von Solms, R. and Furnell, S., 2016. Information security policy compliance
model in organizations. Computers & Security, 56, pp.70-82.
Safa, N.S., Von Solms, R. and Furnell, S., 2016. Information security policy compliance
MINIMIZING THE AFFECT OF HUMAN BEHAVIOUR RISKS RELATED TO
INFORMATION SECURITY
behavior, and the integrated behavioral model.
Mullan, B., Norman, P., Boer, H. and Seydel, E., 2015. Protection motivation theory.
In Predicting and changing health behaviour: Research and practice with social cognition
models (pp. x-x). Open University Press.
Panneerselvam, R., 2014. Research methodology. PHI Learning Pvt. Ltd..
Paul, J., Modi, A. and Patel, J., 2016. Predicting green product consumption using theory of
planned behavior and reasoned action. Journal of Retailing and Consumer Services, 29,
pp.123-134.
Pearlson, K.E., Saunders, C.S. and Galletta, D.F., 2016. Managing and Using Information
Systems, Binder Ready Version: A Strategic Approach. John Wiley & Sons.
Peltier, T.R., 2016. Information Security Policies, Procedures, and Standards: guidelines for
effective information security management. CRC Press.
Peltier, T.R., 2016. Information Security Policies, Procedures, and Standards: guidelines for
effective information security management. CRC Press.
Safa, N.S., Sookhak, M., Von Solms, R., Furnell, S., Ghani, N.A. and Herawan, T., 2015.
Information security conscious care behaviour formation in organizations. Computers &
Security, 53, pp.65-78.
Safa, N.S., Von Solms, R. and Furnell, S., 2016. Information security policy compliance
model in organizations. Computers & Security, 56, pp.70-82.
Safa, N.S., Von Solms, R. and Furnell, S., 2016. Information security policy compliance

89
MINIMIZING THE AFFECT OF HUMAN BEHAVIOUR RISKS RELATED TO
INFORMATION SECURITY
model in organizations. Computers & Security, 56, pp.70-82.
Safa, N.S., Von Solms, R. and Furnell, S., 2016. Information security policy compliance
model in organizations. Computers & Security, 56, pp.70-82.
Sheeran, P. and Rivis, A., 2017. Descriptive norms as an additional predictor in the theory of
planned behavior: A meta-analysis. In Planned Behavior (pp. 49-68). Routledge.
Simonsohn, U., Nelson, L. and Simmons, J., 2017. Research Methodology, Design, and
Analysis. Annual Review of Psychology, 69(1).
Sinha, A., Zscaler Inc, 2015. Cloud based mobile device security and policy enforcement.
U.S. Patent 9,119,017.
Siponen, M., Mahmood, M.A. and Pahnila, S., 2014. Employees’ adherence to information
security policies: An exploratory field study. Information & management, 51(2), pp.217-224.
Siponen, M., Mahmood, M.A. and Pahnila, S., 2014. Employees’ adherence to information
security policies: An exploratory field study. Information & management, 51(2), pp.217-224.
Siponen, M., Mahmood, M.A. and Pahnila, S., 2014. Employees’ adherence to information
security policies: An exploratory field study. Information & management, 51(2), pp.217-224.
Smith, J.A. ed., 2015. Qualitative psychology: A practical guide to research methods. Sage.
Soomro, Z.A., Shah, M.H. and Ahmed, J., 2016. Information security management needs
more holistic approach: A literature review. International Journal of Information
Management, 36(2), pp.215-225.
MINIMIZING THE AFFECT OF HUMAN BEHAVIOUR RISKS RELATED TO
INFORMATION SECURITY
model in organizations. Computers & Security, 56, pp.70-82.
Safa, N.S., Von Solms, R. and Furnell, S., 2016. Information security policy compliance
model in organizations. Computers & Security, 56, pp.70-82.
Sheeran, P. and Rivis, A., 2017. Descriptive norms as an additional predictor in the theory of
planned behavior: A meta-analysis. In Planned Behavior (pp. 49-68). Routledge.
Simonsohn, U., Nelson, L. and Simmons, J., 2017. Research Methodology, Design, and
Analysis. Annual Review of Psychology, 69(1).
Sinha, A., Zscaler Inc, 2015. Cloud based mobile device security and policy enforcement.
U.S. Patent 9,119,017.
Siponen, M., Mahmood, M.A. and Pahnila, S., 2014. Employees’ adherence to information
security policies: An exploratory field study. Information & management, 51(2), pp.217-224.
Siponen, M., Mahmood, M.A. and Pahnila, S., 2014. Employees’ adherence to information
security policies: An exploratory field study. Information & management, 51(2), pp.217-224.
Siponen, M., Mahmood, M.A. and Pahnila, S., 2014. Employees’ adherence to information
security policies: An exploratory field study. Information & management, 51(2), pp.217-224.
Smith, J.A. ed., 2015. Qualitative psychology: A practical guide to research methods. Sage.
Soomro, Z.A., Shah, M.H. and Ahmed, J., 2016. Information security management needs
more holistic approach: A literature review. International Journal of Information
Management, 36(2), pp.215-225.

90
MINIMIZING THE AFFECT OF HUMAN BEHAVIOUR RISKS RELATED TO
INFORMATION SECURITY
Soska, K. and Christin, N., 2015, August. Measuring the Longitudinal Evolution of the
Online Anonymous Marketplace Ecosystem. In USENIX Security Symposium (pp. 33-48).
Taylor, B.C. and Bean, H., 2017. Conceptualizing multicultural discourses of security:
introduction to the special issue. Journal of Multicultural Discourses, 12(4), pp.312-331.
Taylor, R.W., Fritsch, E.J. and Liederbach, J., 2014. Digital crime and digital terrorism.
Prentice Hall Press.
Taylor, S.J., Bogdan, R. and DeVault, M., 2015. Introduction to qualitative research
methods: A guidebook and resource. John Wiley & Sons.
Teh, P.L., Ahmed, P.K. and D'Arcy, J., 2015. What Drives Information Security Policy
Violations among Banking Employees?: Insights from Neutralization and Social Exchange
Theory. Journal of Global Information Management (JGIM), 23(1), pp.44-64.
Tittle, C.R., 2018. Control balance: Toward a general theory of deviance. Routledge.
Tsai, H.Y.S., Jiang, M., Alhabash, S., LaRose, R., Rifon, N.J. and Cotten, S.R., 2016.
Understanding online safety behaviors: A protection motivation theory
perspective. Computers & Security, 59, pp.138-150.
Vaioleti, T.M., 2016. Talanoa research methodology: A developing position on Pacific
research. Waikato Journal of Education, 12(1).
Vance, A., Anderson, B., Kirwan, C.B. and Eargle, D., 2014. Using measures of risk
perception to predict information security behavior: Insights from electroencephalography
(EEG). Association for Information Systems.
MINIMIZING THE AFFECT OF HUMAN BEHAVIOUR RISKS RELATED TO
INFORMATION SECURITY
Soska, K. and Christin, N., 2015, August. Measuring the Longitudinal Evolution of the
Online Anonymous Marketplace Ecosystem. In USENIX Security Symposium (pp. 33-48).
Taylor, B.C. and Bean, H., 2017. Conceptualizing multicultural discourses of security:
introduction to the special issue. Journal of Multicultural Discourses, 12(4), pp.312-331.
Taylor, R.W., Fritsch, E.J. and Liederbach, J., 2014. Digital crime and digital terrorism.
Prentice Hall Press.
Taylor, S.J., Bogdan, R. and DeVault, M., 2015. Introduction to qualitative research
methods: A guidebook and resource. John Wiley & Sons.
Teh, P.L., Ahmed, P.K. and D'Arcy, J., 2015. What Drives Information Security Policy
Violations among Banking Employees?: Insights from Neutralization and Social Exchange
Theory. Journal of Global Information Management (JGIM), 23(1), pp.44-64.
Tittle, C.R., 2018. Control balance: Toward a general theory of deviance. Routledge.
Tsai, H.Y.S., Jiang, M., Alhabash, S., LaRose, R., Rifon, N.J. and Cotten, S.R., 2016.
Understanding online safety behaviors: A protection motivation theory
perspective. Computers & Security, 59, pp.138-150.
Vaioleti, T.M., 2016. Talanoa research methodology: A developing position on Pacific
research. Waikato Journal of Education, 12(1).
Vance, A., Anderson, B., Kirwan, C.B. and Eargle, D., 2014. Using measures of risk
perception to predict information security behavior: Insights from electroencephalography
(EEG). Association for Information Systems.
1 out of 91
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
© 2024 | Zucol Services PVT LTD | All rights reserved.





