CST 610: Cyber Security and Cyber Security Foundation Report Analysis
VerifiedAdded on 2022/08/24
|19
|3346
|30
Report
AI Summary
This report provides a comprehensive analysis of cybersecurity threats and vulnerabilities within the financial sector. It begins with an introduction to network security, outlining the importance of policies and procedures for mitigating risks, including malicious codes and direct attacks. The report delves into mission-critical systems and their components, such as perimeter routers, DMZs, DNS servers, web servers, and email servers, detailing their functions and configuration steps. It then explores network security measures, including penetration testing, and examines the specific threats faced by the financial sector, such as unencrypted data, automation technology vulnerabilities, unprotected third-party services, and unsecured mobile banking. The report highlights the importance of information sharing, the role of Industrial Control Systems (ICS), and concludes by emphasizing the dynamic nature of cyber threats and the need for robust security measures. This report is a result of collaborative work by a team of students for a cybersecurity project, providing situational awareness on a current network breach and cyberattack against several financial service institutions.

Running head: CST 610 9043 Cyberspace and Cyber security Foundation
CST 610 9043 Cyberspace and Cyber security Foundation
Name of the Student
Name of the University
Author Note
CST 610 9043 Cyberspace and Cyber security Foundation
Name of the Student
Name of the University
Author Note
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

CST 610 9043 Cyberspace and Cyber security Foundation 1
Table of Contents
Introduction:...............................................................................................................................3
Assess suspicious activity:.........................................................................................................3
Mission critical systems:........................................................................................................3
Perimeter router:.................................................................................................................4
DMZ:..................................................................................................................................5
DNS server:........................................................................................................................6
Web server:........................................................................................................................8
Email server:....................................................................................................................10
Central switches:..............................................................................................................11
Network security:.................................................................................................................11
Penetration testing:...............................................................................................................11
The Financial Sector:...............................................................................................................13
Unencrypted data:................................................................................................................14
New automation technology without Security:....................................................................14
Unprotected Third Party Services:.......................................................................................15
Unsecured Mobile banking:.................................................................................................15
A constantly changing threat landscape:..............................................................................15
Financial services information sharing and analysis centre:....................................................15
Industrial control systems:.......................................................................................................16
Table of Contents
Introduction:...............................................................................................................................3
Assess suspicious activity:.........................................................................................................3
Mission critical systems:........................................................................................................3
Perimeter router:.................................................................................................................4
DMZ:..................................................................................................................................5
DNS server:........................................................................................................................6
Web server:........................................................................................................................8
Email server:....................................................................................................................10
Central switches:..............................................................................................................11
Network security:.................................................................................................................11
Penetration testing:...............................................................................................................11
The Financial Sector:...............................................................................................................13
Unencrypted data:................................................................................................................14
New automation technology without Security:....................................................................14
Unprotected Third Party Services:.......................................................................................15
Unsecured Mobile banking:.................................................................................................15
A constantly changing threat landscape:..............................................................................15
Financial services information sharing and analysis centre:....................................................15
Industrial control systems:.......................................................................................................16

2CST 610 9043 Cyberspace and Cyber security Foundation
Supervisory Control and Data Acquisition (SCADA):........................................................16
Distributed Control System (DCS):.....................................................................................16
Actual ICS implementation:.................................................................................................16
Conclusion:..............................................................................................................................17
References:...............................................................................................................................17
Supervisory Control and Data Acquisition (SCADA):........................................................16
Distributed Control System (DCS):.....................................................................................16
Actual ICS implementation:.................................................................................................16
Conclusion:..............................................................................................................................17
References:...............................................................................................................................17
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

3CST 610 9043 Cyberspace and Cyber security Foundation
Introduction:
The United States critical infrastructure: water, power, natural gas and oil, financial
systems, military systems have become the target of physical and cyber attacks as much more
complex system frameworks are integrated with the web as well as with some of the other
control systems that are digital. The network security stands for all of the procedures and
policies which is used by a network administrator for mitigating the risks that can come to a
network. It includes policies for recording and finding a possible breach and policies that is
needed to make response to the events (Perlman, Kaufman & Speciner, 2016). An enacted
and well written network security effort will make response to the variety of threats. The
threats can include malicious codes, direct attacks and internal threats. In the computer
security, the threat is basically a possible danger which is able to exploit a vulnerability to the
security breach as well as therefore it can be reason for the possible harm. The purpose of this
paper is to provide situational awareness about the present security breach as well as cyber
attacks that is against various financial service institution.
Assess suspicious activity:
The financial world is littered with the organisations which have paid huge amount of
fines for the failures of them around the AML (anti money laundering) legislation.
Mission critical systems:
The mission critical system is basically a name for a system which is having functions
that are very much critical as well as complex to the survival of an institution. The systems
are required for the basic day to day operations in most of the cases. The time when the
systems fail or the communications with the other systems are blocked then the business may
suffer for a set back that is serious.
Introduction:
The United States critical infrastructure: water, power, natural gas and oil, financial
systems, military systems have become the target of physical and cyber attacks as much more
complex system frameworks are integrated with the web as well as with some of the other
control systems that are digital. The network security stands for all of the procedures and
policies which is used by a network administrator for mitigating the risks that can come to a
network. It includes policies for recording and finding a possible breach and policies that is
needed to make response to the events (Perlman, Kaufman & Speciner, 2016). An enacted
and well written network security effort will make response to the variety of threats. The
threats can include malicious codes, direct attacks and internal threats. In the computer
security, the threat is basically a possible danger which is able to exploit a vulnerability to the
security breach as well as therefore it can be reason for the possible harm. The purpose of this
paper is to provide situational awareness about the present security breach as well as cyber
attacks that is against various financial service institution.
Assess suspicious activity:
The financial world is littered with the organisations which have paid huge amount of
fines for the failures of them around the AML (anti money laundering) legislation.
Mission critical systems:
The mission critical system is basically a name for a system which is having functions
that are very much critical as well as complex to the survival of an institution. The systems
are required for the basic day to day operations in most of the cases. The time when the
systems fail or the communications with the other systems are blocked then the business may
suffer for a set back that is serious.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
4CST 610 9043 Cyberspace and Cyber security Foundation
Mission-Critical Components of a LAN:
A LAN must be having several components in the place which needs to be function
efficiently and correctly. There are various mission critical components that are included in
LAN. They are as follows:
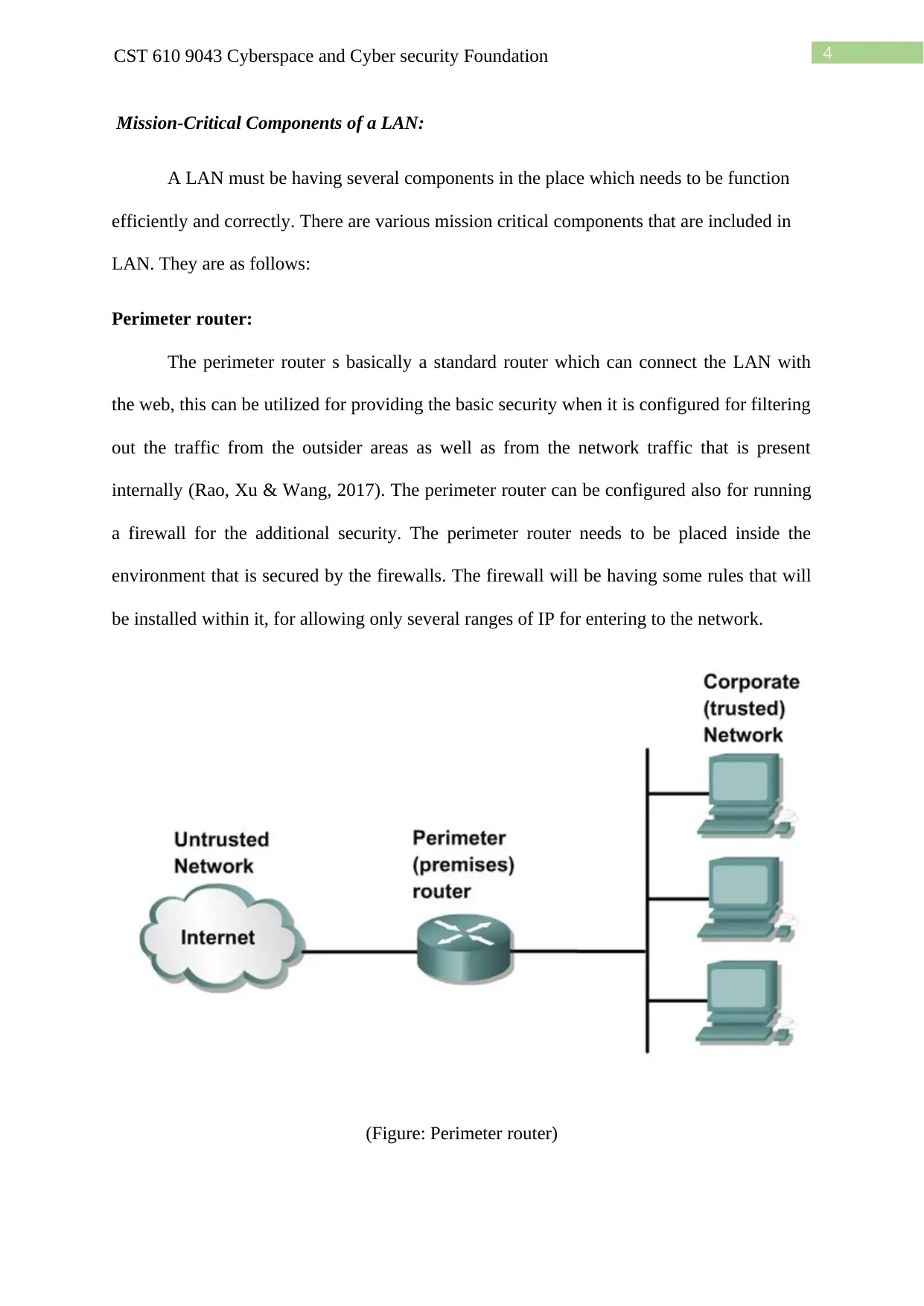
Perimeter router:
The perimeter router s basically a standard router which can connect the LAN with
the web, this can be utilized for providing the basic security when it is configured for filtering
out the traffic from the outsider areas as well as from the network traffic that is present
internally (Rao, Xu & Wang, 2017). The perimeter router can be configured also for running
a firewall for the additional security. The perimeter router needs to be placed inside the
environment that is secured by the firewalls. The firewall will be having some rules that will
be installed within it, for allowing only several ranges of IP for entering to the network.
(Figure: Perimeter router)
Mission-Critical Components of a LAN:
A LAN must be having several components in the place which needs to be function
efficiently and correctly. There are various mission critical components that are included in
LAN. They are as follows:
Perimeter router:
The perimeter router s basically a standard router which can connect the LAN with
the web, this can be utilized for providing the basic security when it is configured for filtering
out the traffic from the outsider areas as well as from the network traffic that is present
internally (Rao, Xu & Wang, 2017). The perimeter router can be configured also for running
a firewall for the additional security. The perimeter router needs to be placed inside the
environment that is secured by the firewalls. The firewall will be having some rules that will
be installed within it, for allowing only several ranges of IP for entering to the network.
(Figure: Perimeter router)

5CST 610 9043 Cyberspace and Cyber security Foundation
The segments of the router that are existed in the network can connect to the internal servers.
The configuring steps of the perimeter router are as follows:
1. Set a hostname.
2. Enable password protection.
3. Enable User Datagram Protocol (UDP) and Transmission Control Protocol (TCP)
network services.
4. Configure console and network access.
5. Configure serial and Ethernet interfaces.
6. Add IP routes and set a default route.
7. Configure frame relay.
DMZ:
For securing the network servers, DMZ is required. The DMZ is an isolated and
separate network which cushions the network of the organisation from the chaos of the
Internet. The internal networks that are installed within an organisations, might be considered
as one of the trusted networks (Luskind, Zeng & Dias, 2019). A distinct network is thought
by DMZ which utilizes a separate set of the IP addresses, that are belong to the institution.
The DMZ existed behind the firewall, however it is not as secure as the Internet. The main
activity of the DMZ is preventing the attacks that happens within the trusted network of the
organisations.
The segments of the router that are existed in the network can connect to the internal servers.
The configuring steps of the perimeter router are as follows:
1. Set a hostname.
2. Enable password protection.
3. Enable User Datagram Protocol (UDP) and Transmission Control Protocol (TCP)
network services.
4. Configure console and network access.
5. Configure serial and Ethernet interfaces.
6. Add IP routes and set a default route.
7. Configure frame relay.
DMZ:
For securing the network servers, DMZ is required. The DMZ is an isolated and
separate network which cushions the network of the organisation from the chaos of the
Internet. The internal networks that are installed within an organisations, might be considered
as one of the trusted networks (Luskind, Zeng & Dias, 2019). A distinct network is thought
by DMZ which utilizes a separate set of the IP addresses, that are belong to the institution.
The DMZ existed behind the firewall, however it is not as secure as the Internet. The main
activity of the DMZ is preventing the attacks that happens within the trusted network of the
organisations.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
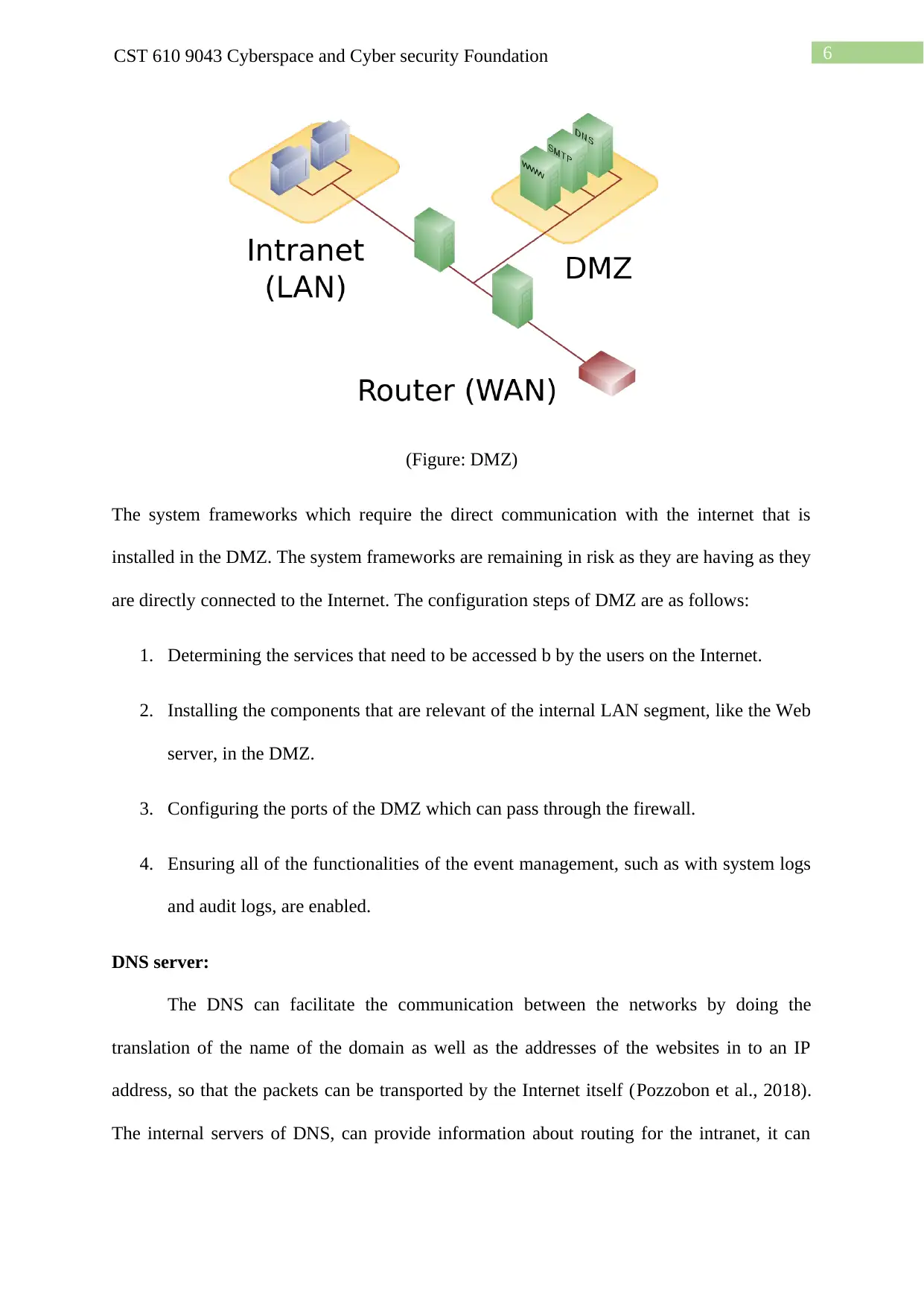
6CST 610 9043 Cyberspace and Cyber security Foundation
(Figure: DMZ)
The system frameworks which require the direct communication with the internet that is
installed in the DMZ. The system frameworks are remaining in risk as they are having as they
are directly connected to the Internet. The configuration steps of DMZ are as follows:
1. Determining the services that need to be accessed b by the users on the Internet.
2. Installing the components that are relevant of the internal LAN segment, like the Web
server, in the DMZ.
3. Configuring the ports of the DMZ which can pass through the firewall.
4. Ensuring all of the functionalities of the event management, such as with system logs
and audit logs, are enabled.
DNS server:
The DNS can facilitate the communication between the networks by doing the
translation of the name of the domain as well as the addresses of the websites in to an IP
address, so that the packets can be transported by the Internet itself (Pozzobon et al., 2018).
The internal servers of DNS, can provide information about routing for the intranet, it can
(Figure: DMZ)
The system frameworks which require the direct communication with the internet that is
installed in the DMZ. The system frameworks are remaining in risk as they are having as they
are directly connected to the Internet. The configuration steps of DMZ are as follows:
1. Determining the services that need to be accessed b by the users on the Internet.
2. Installing the components that are relevant of the internal LAN segment, like the Web
server, in the DMZ.
3. Configuring the ports of the DMZ which can pass through the firewall.
4. Ensuring all of the functionalities of the event management, such as with system logs
and audit logs, are enabled.
DNS server:
The DNS can facilitate the communication between the networks by doing the
translation of the name of the domain as well as the addresses of the websites in to an IP
address, so that the packets can be transported by the Internet itself (Pozzobon et al., 2018).
The internal servers of DNS, can provide information about routing for the intranet, it can
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
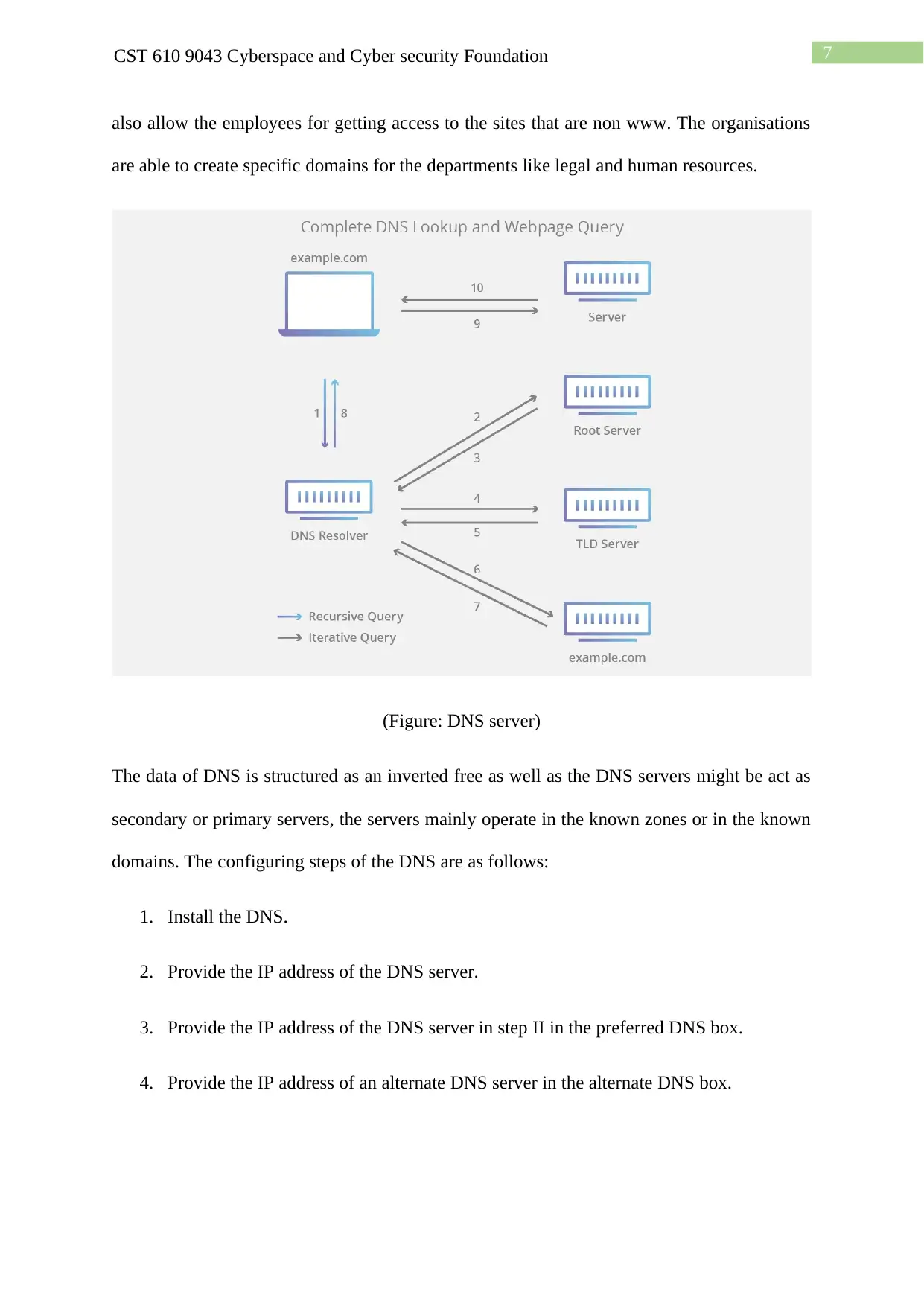
7CST 610 9043 Cyberspace and Cyber security Foundation
also allow the employees for getting access to the sites that are non www. The organisations
are able to create specific domains for the departments like legal and human resources.
(Figure: DNS server)
The data of DNS is structured as an inverted free as well as the DNS servers might be act as
secondary or primary servers, the servers mainly operate in the known zones or in the known
domains. The configuring steps of the DNS are as follows:
1. Install the DNS.
2. Provide the IP address of the DNS server.
3. Provide the IP address of the DNS server in step II in the preferred DNS box.
4. Provide the IP address of an alternate DNS server in the alternate DNS box.
also allow the employees for getting access to the sites that are non www. The organisations
are able to create specific domains for the departments like legal and human resources.
(Figure: DNS server)
The data of DNS is structured as an inverted free as well as the DNS servers might be act as
secondary or primary servers, the servers mainly operate in the known zones or in the known
domains. The configuring steps of the DNS are as follows:
1. Install the DNS.
2. Provide the IP address of the DNS server.
3. Provide the IP address of the DNS server in step II in the preferred DNS box.
4. Provide the IP address of an alternate DNS server in the alternate DNS box.

8CST 610 9043 Cyberspace and Cyber security Foundation
5. Create a forward lookup zone. This zone is referred to whenever an IP address is
requested. All the IP address and hostname correlations are stored in the forward
lookup zone.
6. Provide the IP address of the current system.
7. Provide a name for the DNS zone.
8. Select the update mode.
9. Provide the IP address of the Internet Service Provider (ISP) DNS server so as to
resolve the hostnames outside the network.
Web server:
The web server is another component that is also needed for securing the network
security. The web servers can deliver web based contents to the users for computing the
devices by several protocols like HTTP (Hypertext Transfer Protocol), HTTPS (Hypertext
Transfer Protocol secure) as well as FTP (File Transfer protocol).
5. Create a forward lookup zone. This zone is referred to whenever an IP address is
requested. All the IP address and hostname correlations are stored in the forward
lookup zone.
6. Provide the IP address of the current system.
7. Provide a name for the DNS zone.
8. Select the update mode.
9. Provide the IP address of the Internet Service Provider (ISP) DNS server so as to
resolve the hostnames outside the network.
Web server:
The web server is another component that is also needed for securing the network
security. The web servers can deliver web based contents to the users for computing the
devices by several protocols like HTTP (Hypertext Transfer Protocol), HTTPS (Hypertext
Transfer Protocol secure) as well as FTP (File Transfer protocol).
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
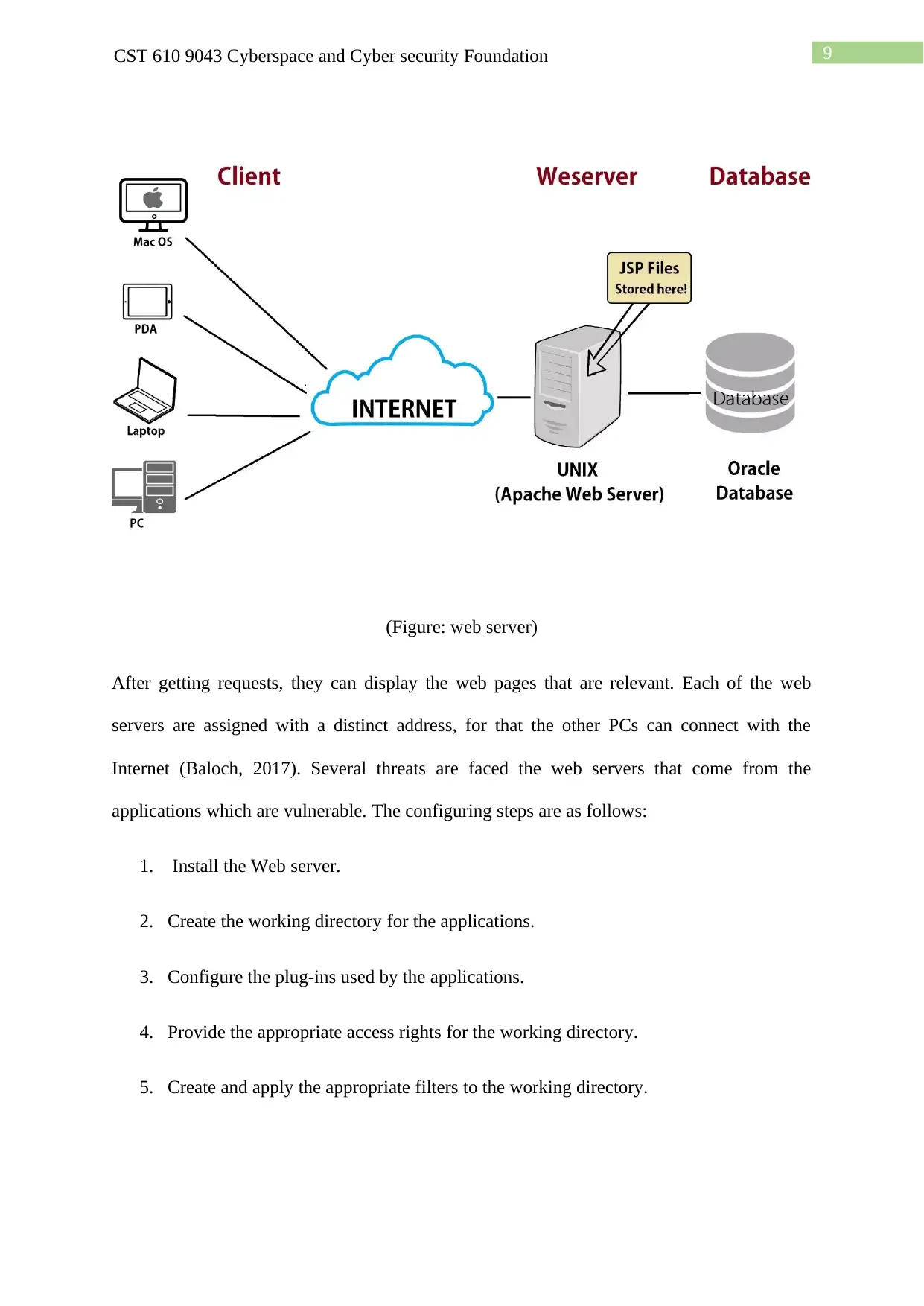
9CST 610 9043 Cyberspace and Cyber security Foundation
(Figure: web server)
After getting requests, they can display the web pages that are relevant. Each of the web
servers are assigned with a distinct address, for that the other PCs can connect with the
Internet (Baloch, 2017). Several threats are faced the web servers that come from the
applications which are vulnerable. The configuring steps are as follows:
1. Install the Web server.
2. Create the working directory for the applications.
3. Configure the plug-ins used by the applications.
4. Provide the appropriate access rights for the working directory.
5. Create and apply the appropriate filters to the working directory.
(Figure: web server)
After getting requests, they can display the web pages that are relevant. Each of the web
servers are assigned with a distinct address, for that the other PCs can connect with the
Internet (Baloch, 2017). Several threats are faced the web servers that come from the
applications which are vulnerable. The configuring steps are as follows:
1. Install the Web server.
2. Create the working directory for the applications.
3. Configure the plug-ins used by the applications.
4. Provide the appropriate access rights for the working directory.
5. Create and apply the appropriate filters to the working directory.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

10CST 610 9043 Cyberspace and Cyber security Foundation
Email server:
The email server another important part of the network security. The email servers is
actually an application which receives email messages from the email related services.
(Figure: Email server)
The configuration steps of email servers are as follows:
1. Install the SMTP service.
2. Define the default directory for the mail configuration file.
3. Configure the connection filters and port numbers.
4. Define the access rights for the server. Here, you specify who can access the server
with what rights.
5. Define the maximum number of recipients.
6. Configure the main exchange (MX) records to perform reverse DNS (rDNS) lookup.
rDNS refers to the host-to-IP conversion, which involves the conversion of the IP
address to its host name.
Email server:
The email server another important part of the network security. The email servers is
actually an application which receives email messages from the email related services.
(Figure: Email server)
The configuration steps of email servers are as follows:
1. Install the SMTP service.
2. Define the default directory for the mail configuration file.
3. Configure the connection filters and port numbers.
4. Define the access rights for the server. Here, you specify who can access the server
with what rights.
5. Define the maximum number of recipients.
6. Configure the main exchange (MX) records to perform reverse DNS (rDNS) lookup.
rDNS refers to the host-to-IP conversion, which involves the conversion of the IP
address to its host name.

11CST 610 9043 Cyberspace and Cyber security Foundation
Central switches:
There are many types of the switches. The switches can be vulnerable for the DoS
attack. The configuring steps of central switches are as follow:
1. Configure the switch hostname.
2. Enable the password.
3. Define the console logins.
4. Encrypt the password.
5. Define the default gateway.
Network security:
The network security stands for all of the procedures and policies which is used by a
network administrator for mitigating the risks that can come to a network. It includes policies
for recording and finding a possible breach and policies that is needed to make response to
the events. An enacted and well written network security effort will make response to the
variety of threats (Acemoglu, Malekian & Ozdaglar, 2016). The threats can include malicious
codes, direct attacks and internal threats. The network security is the combination of multiple
defence layers at the edge as well as in the network. Each of the layers network security can
implement controls and policies. The users who are authorised can gain access to the
resources of the networks, however the malicious actors are blocked from carrying out the
threats and exploits.
Penetration testing:
The penetration testing is also known as ethical hacking or pen testing. It is actually
the practice of testing network, computer system or web based application for finding the
security vulnerabilities which an attacker could exploit. The pen testing can process
Central switches:
There are many types of the switches. The switches can be vulnerable for the DoS
attack. The configuring steps of central switches are as follow:
1. Configure the switch hostname.
2. Enable the password.
3. Define the console logins.
4. Encrypt the password.
5. Define the default gateway.
Network security:
The network security stands for all of the procedures and policies which is used by a
network administrator for mitigating the risks that can come to a network. It includes policies
for recording and finding a possible breach and policies that is needed to make response to
the events. An enacted and well written network security effort will make response to the
variety of threats (Acemoglu, Malekian & Ozdaglar, 2016). The threats can include malicious
codes, direct attacks and internal threats. The network security is the combination of multiple
defence layers at the edge as well as in the network. Each of the layers network security can
implement controls and policies. The users who are authorised can gain access to the
resources of the networks, however the malicious actors are blocked from carrying out the
threats and exploits.
Penetration testing:
The penetration testing is also known as ethical hacking or pen testing. It is actually
the practice of testing network, computer system or web based application for finding the
security vulnerabilities which an attacker could exploit. The pen testing can process
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
1 out of 19
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.





