MITS5003: Exploring Modulation, Error Detection & WLAN Technologies
VerifiedAdded on 2023/04/03
|16
|1420
|253
Homework Assignment
AI Summary
This assignment solution covers various aspects of digital communication, including modulation techniques such as Amplitude Shift Keying (ASK), Frequency Shift Keying (FSK), and Phase Shift Keying (PSK) at different levels. It details the computation of frequency assignments for 16-level FSK, illustrates analog and frequency modulation waveforms, and presents the 16 QAM constellation diagram. Furthermore, it explains and demonstrates the error detection process using Cyclic Redundancy Check (CRC) with examples. The solution also discusses Direct Sequence Spread Spectrum (DSSS) and compares infrastructure and ad hoc modes in WLAN, highlighting their differences and network configurations. Finally, it provides a comparison of the OSI and TCP/IP models, outlining the layers and protocols used in each, and explains the preference for hexagonal cells in cellular systems.

MITS5003
By Name
Course
Instructor
Institution
Location
Date
By Name
Course
Instructor
Institution
Location
Date
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

Question 1
Two level amplitude shifting key is also called On-OFF keying or BASK
(a) The analog carrier amplitude varies with bit stream
(b) The sinusoidal carrier shifts between two discrete values. Ther frequencies there in are fH for
binary 1 and fLfor binary 0
(c)They are also known as binary phase shift keying and uses opposite signals.
Two level amplitude shifting key is also called On-OFF keying or BASK
(a) The analog carrier amplitude varies with bit stream
(b) The sinusoidal carrier shifts between two discrete values. Ther frequencies there in are fH for
binary 1 and fLfor binary 0
(c)They are also known as binary phase shift keying and uses opposite signals.

(d) Differential phase shift keying combines two basic operations namely differential encoding
as well as phase shift keying. The sequence of the binaru bits is such that next bit relies on
previous one
(e) M=2m
Where M =4 levels then m=2 bit ; the four levels are 00, 01, 10 and 11. The input
binary is divided into 2 since m=2
as well as phase shift keying. The sequence of the binaru bits is such that next bit relies on
previous one
(e) M=2m
Where M =4 levels then m=2 bit ; the four levels are 00, 01, 10 and 11. The input
binary is divided into 2 since m=2
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

(f) Four phase in this level are0o, 90o, 180o and270o
(f) In eight levels ASK, the carrier signal amplitude varies with the input 3bit symbol. Here
M=8 since m=3 bits
(f) In eight levels ASK, the carrier signal amplitude varies with the input 3bit symbol. Here
M=8 since m=3 bits
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

Question 2
Assign 16 different frequencies to the 4 bit input data combinations. This means it is 16 levels
FSK. Here, the carrier frequency is given as fc=500 kHz , frequency difference fd =25 kHz
M=16 and L=4
Output =cos (2 π fct+ Mfdt ) where M=1, 2, 16
M L OUT PUT
1 0000 cos (1000 πt+25 t )
2 0001 cos (1000 πt+50 t )
3 0010 cos (1000 πt+75 t )
4 0011 cos (1000 πt+100 t )
5 0100 cos (1000 πt+125 t )
6 0101 cos (1000 πt+150 t )
7 0110 cos (1000 πt+175 t )
8 0111 cos (1000 πt +200 t )
9 1000 cos (1000 πt+225 t )
10 1001 cos (1000 πt +250 t )
11 1010 cos (1000 πt+275 t )
12 1011 cos (1000 πt+300 t )
13 1100 cos (1000 πt+325 t )
14 1101 cos (1000 πt+350 t )
15 1110 cos (1000 πt+375 t )
16 1111 cos (1000 πt + 400 t )
Question 3
For Amplitude modulation, amplitude of carrier signal varies according to amplitude of the
modulating signal.
Assign 16 different frequencies to the 4 bit input data combinations. This means it is 16 levels
FSK. Here, the carrier frequency is given as fc=500 kHz , frequency difference fd =25 kHz
M=16 and L=4
Output =cos (2 π fct+ Mfdt ) where M=1, 2, 16
M L OUT PUT
1 0000 cos (1000 πt+25 t )
2 0001 cos (1000 πt+50 t )
3 0010 cos (1000 πt+75 t )
4 0011 cos (1000 πt+100 t )
5 0100 cos (1000 πt+125 t )
6 0101 cos (1000 πt+150 t )
7 0110 cos (1000 πt+175 t )
8 0111 cos (1000 πt +200 t )
9 1000 cos (1000 πt+225 t )
10 1001 cos (1000 πt +250 t )
11 1010 cos (1000 πt+275 t )
12 1011 cos (1000 πt+300 t )
13 1100 cos (1000 πt+325 t )
14 1101 cos (1000 πt+350 t )
15 1110 cos (1000 πt+375 t )
16 1111 cos (1000 πt + 400 t )
Question 3
For Amplitude modulation, amplitude of carrier signal varies according to amplitude of the
modulating signal.
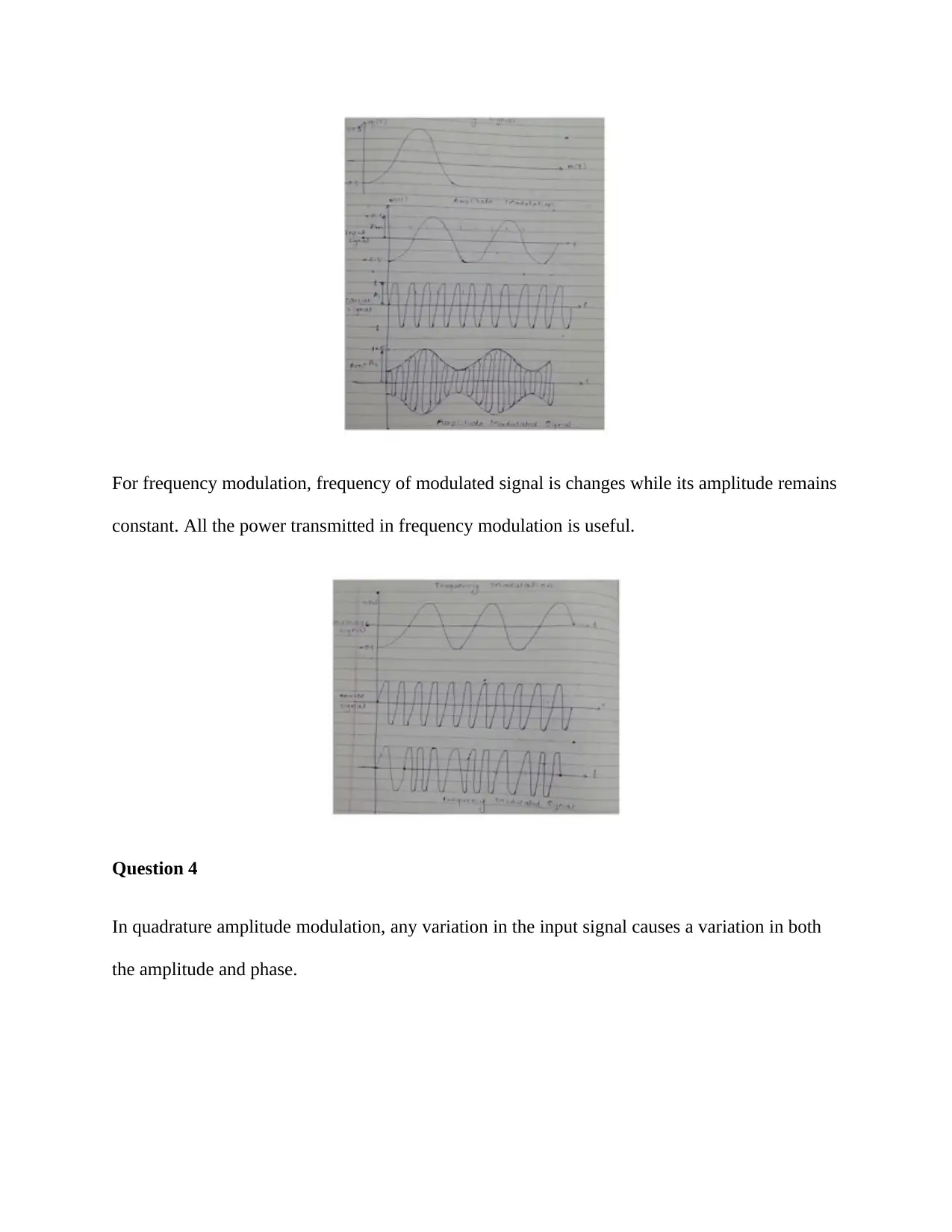
For frequency modulation, frequency of modulated signal is changes while its amplitude remains
constant. All the power transmitted in frequency modulation is useful.
Question 4
In quadrature amplitude modulation, any variation in the input signal causes a variation in both
the amplitude and phase.
constant. All the power transmitted in frequency modulation is useful.
Question 4
In quadrature amplitude modulation, any variation in the input signal causes a variation in both
the amplitude and phase.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

Question 5
CRC is one of most reliable tools for detection of error which is pegged on binary division.
In error detection process from algebraic polynomial general a bit pattern
Cyclic redundancy check tends to be reliable since it is able to sense single bit errors as well as
most of large burst error at relatively high chances
CRC is one of most reliable tools for detection of error which is pegged on binary division.
In error detection process from algebraic polynomial general a bit pattern
Cyclic redundancy check tends to be reliable since it is able to sense single bit errors as well as
most of large burst error at relatively high chances
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

CRC process of error detection
For instance
1110110 as the bit stream
11011 is taken as divisor i.e. generator polynomial
Suppose m=Number of bits within generator; append (m-1) zero bit to data
There is 5 bit in generator polynomial hence string having 4 0s to bit stream
The data is appended by dividend with generator with the sue of 11101100000
(m-1) bits remainder would thus be the CRC
Code word=Data bits+ CRC bits
Finally Cyclic Redundancy Check would be generated as illustrated
Cyclic Redundancy Check is 1011 hence the send sends 11101101011 to the receiver
For instance
1110110 as the bit stream
11011 is taken as divisor i.e. generator polynomial
Suppose m=Number of bits within generator; append (m-1) zero bit to data
There is 5 bit in generator polynomial hence string having 4 0s to bit stream
The data is appended by dividend with generator with the sue of 11101100000
(m-1) bits remainder would thus be the CRC
Code word=Data bits+ CRC bits
Finally Cyclic Redundancy Check would be generated as illustrated
Cyclic Redundancy Check is 1011 hence the send sends 11101101011 to the receiver

Question 6
Cyclic Redundancy Check algorithm is the most widely used algorithm for frame check
Hence in this case CRC is adopted
Assuming 10111100 as bit stream
11011 is the divisor
There are 5 bits n the divisor hence string has 4 0’s to be appended to bit stream for transmission
Hence the final bit stream becomes 101111000000
The binary is thus performed as shown below
CRC is hence 0010
Cyclic Redundancy Check algorithm is the most widely used algorithm for frame check
Hence in this case CRC is adopted
Assuming 10111100 as bit stream
11011 is the divisor
There are 5 bits n the divisor hence string has 4 0’s to be appended to bit stream for transmission
Hence the final bit stream becomes 101111000000
The binary is thus performed as shown below
CRC is hence 0010
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

The code intended to be transmitted is got by substituting the last four zeros in 101111000000
using CRC
Hence the receiver would receive 101111000000 as the transmitted code
Question 7
DSSS provided protection against external generated interfering signal called jamming signals
The DSSS is averaging system
DSSS given data sequence converted into binary NRZ sequence
Spread spectrum signal also known as m (t) is a product of Binary NRZ sequence also called b
(t) and the PN sequence, abbreviated as c (t)
T is the time period for single bit of input data signal and Tc the time period for single bit of PN
sequence
T=3Tc as shown below
using CRC
Hence the receiver would receive 101111000000 as the transmitted code
Question 7
DSSS provided protection against external generated interfering signal called jamming signals
The DSSS is averaging system
DSSS given data sequence converted into binary NRZ sequence
Spread spectrum signal also known as m (t) is a product of Binary NRZ sequence also called b
(t) and the PN sequence, abbreviated as c (t)
T is the time period for single bit of input data signal and Tc the time period for single bit of PN
sequence
T=3Tc as shown below
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

Question 8
There are only stations in Adhoc mode WLAN network
There are stations alongside a single or more access points in infrastructure mode
There is direct communication between stations in Adhoc mode which is as well related in the
form of independent typical service set or even peer-to-peer mode
Access points of mode in infrastructure device is as base stations that are employed in cellular
system
There is no need for physical infrastructure for the case of Adhoc mode
Infrastructure mode need physical infrastructure in order to operate
MAC protocols for instance CSMA are often adopted in most of the WLAN connections based
on Adhoc
Protocols based on TDMA are mostly used in infrastructure mode
There is direct communication in Adhoc mode over radio waves that are wireless
There are only stations in Adhoc mode WLAN network
There are stations alongside a single or more access points in infrastructure mode
There is direct communication between stations in Adhoc mode which is as well related in the
form of independent typical service set or even peer-to-peer mode
Access points of mode in infrastructure device is as base stations that are employed in cellular
system
There is no need for physical infrastructure for the case of Adhoc mode
Infrastructure mode need physical infrastructure in order to operate
MAC protocols for instance CSMA are often adopted in most of the WLAN connections based
on Adhoc
Protocols based on TDMA are mostly used in infrastructure mode
There is direct communication in Adhoc mode over radio waves that are wireless
Communication between the accesses points for instance PCs and router in the case of
infrastructure mode is through access points.
Question 9
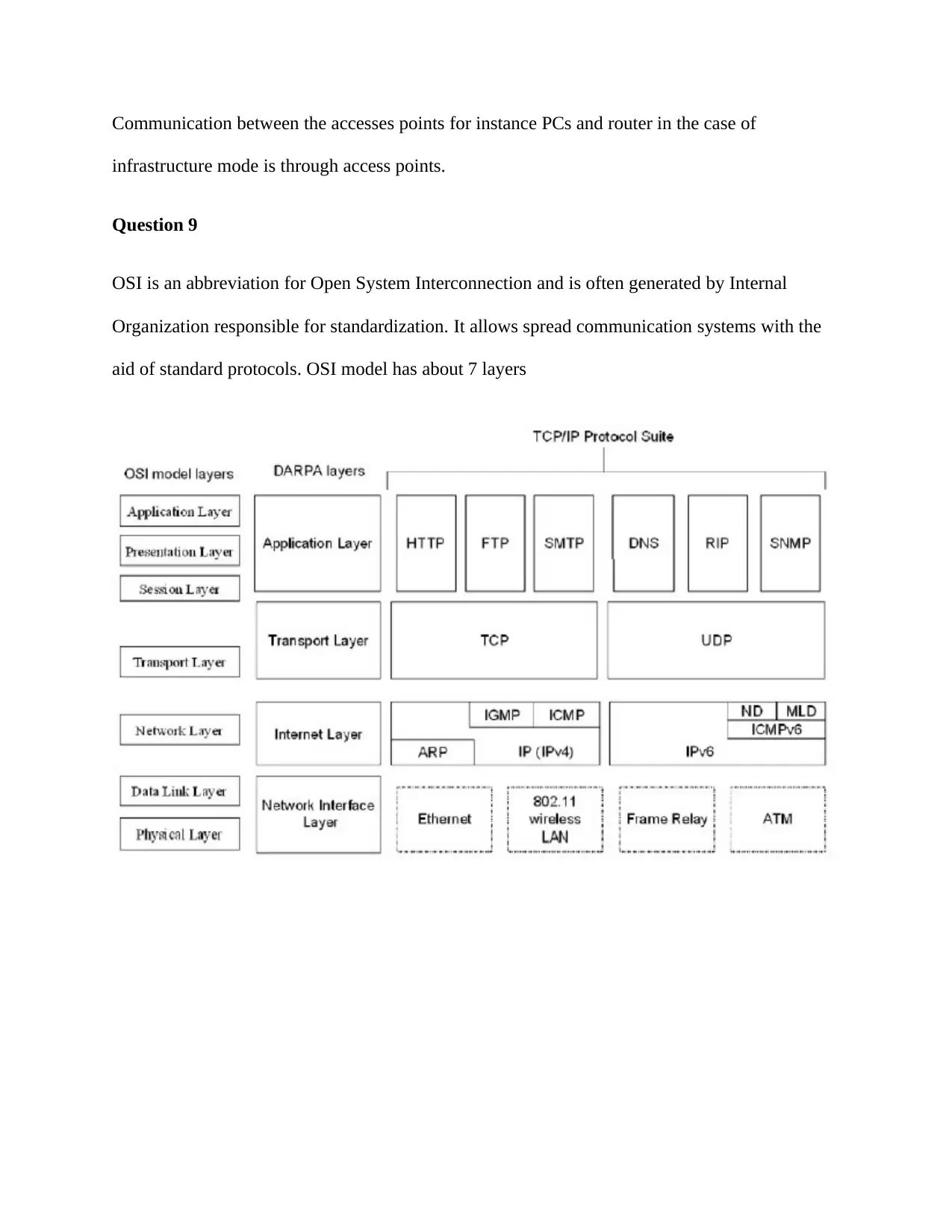
OSI is an abbreviation for Open System Interconnection and is often generated by Internal
Organization responsible for standardization. It allows spread communication systems with the
aid of standard protocols. OSI model has about 7 layers
infrastructure mode is through access points.
Question 9
OSI is an abbreviation for Open System Interconnection and is often generated by Internal
Organization responsible for standardization. It allows spread communication systems with the
aid of standard protocols. OSI model has about 7 layers
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
1 out of 16
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2025 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.





