Analyzing Machine Learning for Cybersecurity Threat Prediction
VerifiedAdded on 2023/06/11
|8
|2087
|217
Project
AI Summary
This project report investigates the effectiveness of machine learning (ML) in predicting cyber security threats. It begins by introducing the concept of cyber threats and the role of AI and ML in addressing them. The research background highlights the increasing cyber-attack risks and the adoption of ML for threat analysis in the UK. Key research questions explore the concept of ML, its effectiveness in cyber security (CS), its use in predicting CS threats, and strategies to cope with these threats. The project aims to analyze the effectiveness of ML for cyber security threat prediction, with objectives including developing an understanding of ML, assessing its effectiveness in cyber security, investigating ML approaches for predicting threats, and suggesting ML strategies for overcoming these threats. Deliverables include a comprehensive understanding of machine learning and a time-scaled project plan. Academic challenges include data collection difficulties, data quality issues, project delivery timelines, resource costs, and computational resource demands. The report outlines a plan of work with activities such as research aim and objective formation, resource gathering, methodology development, literature review, sampling, data collection, and data analysis. Resources required include accurate data sets and access to published articles and online information. The report concludes with a list of references.

MACHINE LEARNING FOR
CYBER SECURITY
THREAT PREDICTION
1
CYBER SECURITY
THREAT PREDICTION
1
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

TABLE OF CONTENTS
1.INTRODUCTION........................................................................................................................3
2.Research Background...............................................................................................................3
3.Research question.....................................................................................................................5
4.Aim:..........................................................................................................................................5
5. Objective..................................................................................................................................5
6.Deliverables..............................................................................................................................5
7. Academic Challenges..............................................................................................................6
8.Plan of Work.............................................................................................................................6
9. Resources.................................................................................................................................7
REFERENCES................................................................................................................................7
1.INTRODUCTION........................................................................................................................3
2.Research Background...............................................................................................................3
3.Research question.....................................................................................................................5
4.Aim:..........................................................................................................................................5
5. Objective..................................................................................................................................5
6.Deliverables..............................................................................................................................5
7. Academic Challenges..............................................................................................................6
8.Plan of Work.............................................................................................................................6
9. Resources.................................................................................................................................7
REFERENCES................................................................................................................................7

1.INTRODUCTION
Cyber security threats refer to any malicious attack that generally aim for unlawfully access
to the information, it disrupts the information as well as damage the human life. It is becoming a
biggest issue which every sector is facing in every aspect, they are getting malicious link just by
clicking it hackers got the all data and they use it for their purpose, thus these are the life
threatening situation to anyone (Ghafir and et.al 2018). Development of the machines and tools
are efficient in making any task effective and productive, new technology emergence making the
work not only efficient but it also aims to reduce the chances for the errors and capable of
working better than human power. Artificial intelligence is the wide range of technology which
is adopted by many businesses, it is the ability of the computer and bot that is managed by the
computer system to lay out the task which is previously done by the humans as it needed the
human intelligence. Where the AI technology enables the machines and devices to simulate the
human behaviour and machine learning technology is the sub part of AI. ML allows the
machines to efficiently learns the past data instead of programming explicitly, as the main
purpose of AI is to make the computer system much smarter like human beings to solve any
problem without making of any errors (Tahsien, Karimipour, and Spachos, 2020). ML begins
with the data which can be numbers, images and other type of information, thus the data is being
prepared and analysed for using it as a training data so that Ml model can be trained on.
Cyber threats are easily seen now a day’s hackers become more active to attack the
organisational system to demand for ransom, they use various techniques to break the cyber
security layer which is causing problems in terms of life threatening issues. Emergence of the
new technologies are developed to challenge the threat attacks, in such ML is the technology that
is heavily implemented by the cyber team to predict the threats chances, it helps in obtaining the
patterns from the information so it can be used in mitigation strategy. This research report will
cover the structure where it discusses the background of study, aim, objectives, to discuss the
effectiveness of ML for predicting the cyber security threats.
2.Research Background
In UK, it is found that risk for the cyber-attacks are continually increasing, most of the
companies are claiming that they are becoming a victim of such activity. Such risks have led to
introduce some preventive measures to deal with it. Thus ML technology is being used by cyber
security team to analyse the patterns that helps in predicting the cyber security threats. ML can
3
Cyber security threats refer to any malicious attack that generally aim for unlawfully access
to the information, it disrupts the information as well as damage the human life. It is becoming a
biggest issue which every sector is facing in every aspect, they are getting malicious link just by
clicking it hackers got the all data and they use it for their purpose, thus these are the life
threatening situation to anyone (Ghafir and et.al 2018). Development of the machines and tools
are efficient in making any task effective and productive, new technology emergence making the
work not only efficient but it also aims to reduce the chances for the errors and capable of
working better than human power. Artificial intelligence is the wide range of technology which
is adopted by many businesses, it is the ability of the computer and bot that is managed by the
computer system to lay out the task which is previously done by the humans as it needed the
human intelligence. Where the AI technology enables the machines and devices to simulate the
human behaviour and machine learning technology is the sub part of AI. ML allows the
machines to efficiently learns the past data instead of programming explicitly, as the main
purpose of AI is to make the computer system much smarter like human beings to solve any
problem without making of any errors (Tahsien, Karimipour, and Spachos, 2020). ML begins
with the data which can be numbers, images and other type of information, thus the data is being
prepared and analysed for using it as a training data so that Ml model can be trained on.
Cyber threats are easily seen now a day’s hackers become more active to attack the
organisational system to demand for ransom, they use various techniques to break the cyber
security layer which is causing problems in terms of life threatening issues. Emergence of the
new technologies are developed to challenge the threat attacks, in such ML is the technology that
is heavily implemented by the cyber team to predict the threats chances, it helps in obtaining the
patterns from the information so it can be used in mitigation strategy. This research report will
cover the structure where it discusses the background of study, aim, objectives, to discuss the
effectiveness of ML for predicting the cyber security threats.
2.Research Background
In UK, it is found that risk for the cyber-attacks are continually increasing, most of the
companies are claiming that they are becoming a victim of such activity. Such risks have led to
introduce some preventive measures to deal with it. Thus ML technology is being used by cyber
security team to analyse the patterns that helps in predicting the cyber security threats. ML can
3
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

be descriptive as the system utilises the data for explaining the cause as predictive means system
uses the information to predict what will happen in future so that strategies can be made. ML in
cyber security makes the team more proficient in identifying the threats so that suitable action
can be taken out. It increases the security processes and also make the team to easily analyse and
prioritize the processes in order to remediate the attacks. It helps in automating the repetitive
tasks which are malware analysis so that tasks can be carried out in efficient manners. It analyses
the data sets of the security process and obtain the patterns for the malicious activities, thus same
events can be identified and it can be efficiently deal with the trained Ml machine. If there is
more data that feeds to machine, then there will be better chances for the programs. However, it
is found that Machine learning requires the large data to trains the machines which consumes
more time to generate the data.
Alhawi, Baldwin and Dehghantanha, (2018) said that as use of such technology mainly
impact the financial resources, that means companies have to invest large amount on using such
machines. However it is also found that technical skills are more important to operate with the
ML normal human cannot be able to deal with such technology, thus organisation must have to
conducts the training session to train their employees to develop the knowledge to approach with
ML. Schratz and et.al (2019) has said that ML enables the software to offer more accurate
prediction outcomes, it uses the historical or past data for predicting the new result. In short ML
enable the cyber security to be simpler and less expensive and more effective, and to predict the
result so that threats can be identified and preventive measures can be taken out.
Martínez Torres, Iglesias Comesaña and García-Nieto, (2019) proposed that Machine
learning requires the large data to trains the machines which consumes more time to generate the
data. It also let the algorithm to develop understanding about the data to reach the purpose, it also
needed a distinct resource for functioning, thus additional requirements can also have made
while using the ML algorithms. As the previous threat data is feed to the machine so that new
information can be developed to deal with the malicious attacks. Gupta, (2018) stated that
Traditional processes for detecting the phishing consumes more time, but with the help of ML
strategies predictive URL model helps in recognising the patterns so that it can give the
information about the malicious emails and links. ML machine acts in a way so that it can easily
differentiate between the malicious and in normal behaviour. Tang and et.al (2019) Proposed the
novel ML approach for the spam detection in the content based elements, they said that proposed
uses the information to predict what will happen in future so that strategies can be made. ML in
cyber security makes the team more proficient in identifying the threats so that suitable action
can be taken out. It increases the security processes and also make the team to easily analyse and
prioritize the processes in order to remediate the attacks. It helps in automating the repetitive
tasks which are malware analysis so that tasks can be carried out in efficient manners. It analyses
the data sets of the security process and obtain the patterns for the malicious activities, thus same
events can be identified and it can be efficiently deal with the trained Ml machine. If there is
more data that feeds to machine, then there will be better chances for the programs. However, it
is found that Machine learning requires the large data to trains the machines which consumes
more time to generate the data.
Alhawi, Baldwin and Dehghantanha, (2018) said that as use of such technology mainly
impact the financial resources, that means companies have to invest large amount on using such
machines. However it is also found that technical skills are more important to operate with the
ML normal human cannot be able to deal with such technology, thus organisation must have to
conducts the training session to train their employees to develop the knowledge to approach with
ML. Schratz and et.al (2019) has said that ML enables the software to offer more accurate
prediction outcomes, it uses the historical or past data for predicting the new result. In short ML
enable the cyber security to be simpler and less expensive and more effective, and to predict the
result so that threats can be identified and preventive measures can be taken out.
Martínez Torres, Iglesias Comesaña and García-Nieto, (2019) proposed that Machine
learning requires the large data to trains the machines which consumes more time to generate the
data. It also let the algorithm to develop understanding about the data to reach the purpose, it also
needed a distinct resource for functioning, thus additional requirements can also have made
while using the ML algorithms. As the previous threat data is feed to the machine so that new
information can be developed to deal with the malicious attacks. Gupta, (2018) stated that
Traditional processes for detecting the phishing consumes more time, but with the help of ML
strategies predictive URL model helps in recognising the patterns so that it can give the
information about the malicious emails and links. ML machine acts in a way so that it can easily
differentiate between the malicious and in normal behaviour. Tang and et.al (2019) Proposed the
novel ML approach for the spam detection in the content based elements, they said that proposed
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

neural networks are more efficient in terms of ML techniques as they give the accurate result on
same dataset.
It is found that commonly machine learning techniques that is K nearest neighbours,
decision trees and other support vector machines are used for laying out any task. However, it is
found that deep learning which is the sub class of ML is being used to recognise the patterns. As
it helps in implementing the ML to image recognition, such system finds the object edge,
structure its type and object itself to predict based on data patterns. Haji and Ameen, (2021)
analysed the use of different ML techniques in malware detection and other threat detection, they
claimed that there are no effective ML techniques are found which is not vulnerable to
cyberattacks. As every ML Approach is struggling to maintain the pace with regularly updating
cybercrimes.
3.Research question
What is the concept of machine learning?
What are some ML’s effectiveness in CS?
How ML can be used in predicting CS threats?
What are ML strategies to cope up with CS threats?
4.Aim:
To analyse the effectiveness of Machine learning for cyber security threat prediction. This
will help the businesses to predict the threats in order to reduce the misuse of information.
5. Objective
To develop the understanding of Machine learning
To assess the effectiveness of ML in cyber security
To investigate the ML approach in predicting cyber security threats
To suggest the ML strategies for overcoming the cyber security threats
6.Deliverables
Deliverables are the outputs which is initially planned and strategies, they are quantifiable
services which is required to be given at distinct stages of the project. It helps in best utilisation
of the resources so it gives optimum results. For this project in the end it will helps in developing
the greater understanding about the machine learning, with this threat prediction can be made
5
same dataset.
It is found that commonly machine learning techniques that is K nearest neighbours,
decision trees and other support vector machines are used for laying out any task. However, it is
found that deep learning which is the sub class of ML is being used to recognise the patterns. As
it helps in implementing the ML to image recognition, such system finds the object edge,
structure its type and object itself to predict based on data patterns. Haji and Ameen, (2021)
analysed the use of different ML techniques in malware detection and other threat detection, they
claimed that there are no effective ML techniques are found which is not vulnerable to
cyberattacks. As every ML Approach is struggling to maintain the pace with regularly updating
cybercrimes.
3.Research question
What is the concept of machine learning?
What are some ML’s effectiveness in CS?
How ML can be used in predicting CS threats?
What are ML strategies to cope up with CS threats?
4.Aim:
To analyse the effectiveness of Machine learning for cyber security threat prediction. This
will help the businesses to predict the threats in order to reduce the misuse of information.
5. Objective
To develop the understanding of Machine learning
To assess the effectiveness of ML in cyber security
To investigate the ML approach in predicting cyber security threats
To suggest the ML strategies for overcoming the cyber security threats
6.Deliverables
Deliverables are the outputs which is initially planned and strategies, they are quantifiable
services which is required to be given at distinct stages of the project. It helps in best utilisation
of the resources so it gives optimum results. For this project in the end it will helps in developing
the greater understanding about the machine learning, with this threat prediction can be made
5
easily to avoid any misuse of data (Doshi, Apthorpe and Feamster, 2018). This project will lay
out the time scale plan to show the overall project plan along with the final project report.
7. Academic Challenges
Major challenges can be seen in terms of the data collection as accessing the data set
regarding machine learning is quite difficult it is not adapted at large scale. Poor quality of the
data is also causing a barrier as it is not efficient and profitable to predict the threat. Also other
challenge can be to deliver the project on time, as the resources for this project is expensive due
to its technological aspect, thus it can cause impact over the financial resources. Another
challenge is to train the data through different distributed sources mainly consumes the huge
amount of computational resources that cost more (Khan and et.al 2019). ML algorithm utilises
the significant amount of the data to train the machines, identification of the right data set and to
set its amount is also a big challenge that linked with the engineering problem.
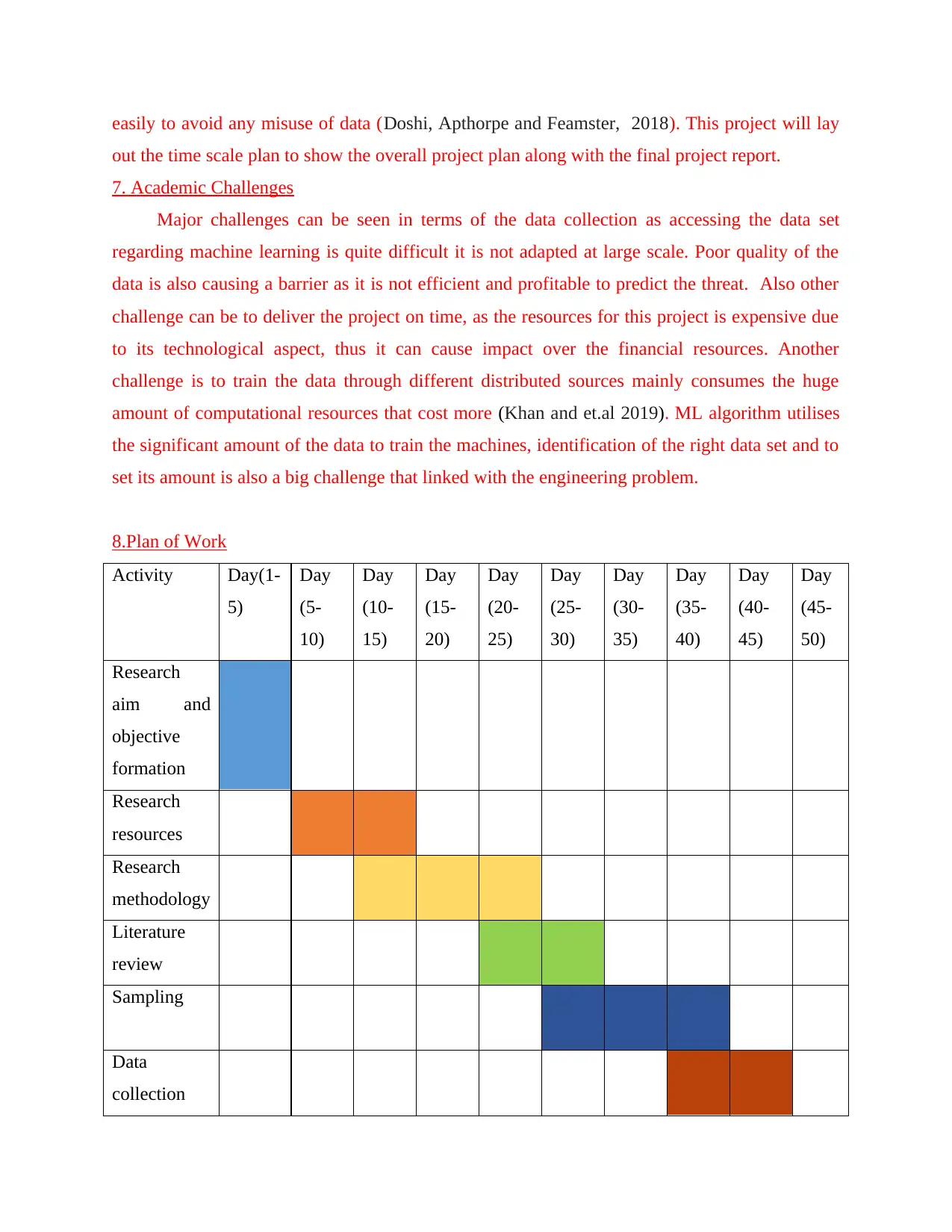
8.Plan of Work
Activity Day(1-
5)
Day
(5-
10)
Day
(10-
15)
Day
(15-
20)
Day
(20-
25)
Day
(25-
30)
Day
(30-
35)
Day
(35-
40)
Day
(40-
45)
Day
(45-
50)
Research
aim and
objective
formation
Research
resources
Research
methodology
Literature
review
Sampling
Data
collection
out the time scale plan to show the overall project plan along with the final project report.
7. Academic Challenges
Major challenges can be seen in terms of the data collection as accessing the data set
regarding machine learning is quite difficult it is not adapted at large scale. Poor quality of the
data is also causing a barrier as it is not efficient and profitable to predict the threat. Also other
challenge can be to deliver the project on time, as the resources for this project is expensive due
to its technological aspect, thus it can cause impact over the financial resources. Another
challenge is to train the data through different distributed sources mainly consumes the huge
amount of computational resources that cost more (Khan and et.al 2019). ML algorithm utilises
the significant amount of the data to train the machines, identification of the right data set and to
set its amount is also a big challenge that linked with the engineering problem.
8.Plan of Work
Activity Day(1-
5)
Day
(5-
10)
Day
(10-
15)
Day
(15-
20)
Day
(20-
25)
Day
(25-
30)
Day
(30-
35)
Day
(35-
40)
Day
(40-
45)
Day
(45-
50)
Research
aim and
objective
formation
Research
resources
Research
methodology
Literature
review
Sampling
Data
collection
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
Data
analysis
9. Resources
For this project to analyse the ML effectiveness accurate data sets are required which helps
the ML to detect the patterns for threat identification. To understand its effectiveness, there will
be use of latest published articles, information present on internet, website will be utilised.
7
analysis
9. Resources
For this project to analyse the ML effectiveness accurate data sets are required which helps
the ML to detect the patterns for threat identification. To understand its effectiveness, there will
be use of latest published articles, information present on internet, website will be utilised.
7
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

REFERENCES
Books and journals
Alhawi, O.M., Baldwin, J. and Dehghantanha, A., 2018. Leveraging machine learning
techniques for windows ransomware network traffic detection. In Cyber threat
intelligence (pp. 93-106). Springer, Cham.
Ghafir, I. and et.al 2018. Detection of advanced persistent threat using machine-learning
correlation analysis. Future Generation Computer Systems. 89. pp.349-359.
Gupta, B.B. ed., 2018. Computer and cyber security: principles, algorithm, applications, and
perspectives. CRC Press.
Haji, S.H. and Ameen, S.Y., 2021. Attack and anomaly detection in iot networks using machine
learning techniques: A review. Asian journal of research in computer science. 9(2).
pp.30-46.
Khan, R.U. and et.al 2019. An adaptive multi-layer botnet detection technique using machine
learning classifiers. Applied Sciences. 9(11). p.2375.
Martínez Torres, J., Iglesias Comesaña, C. and García-Nieto, P.J., 2019. Machine learning
techniques applied to cybersecurity. International Journal of Machine Learning and
Cybernetics. 10(10). pp.2823-2836.
Schratz, P. and et.al 2019. Hyperparameter tuning and performance assessment of statistical and
machine-learning algorithms using spatial data. Ecological Modelling. 406. pp.109-120.
Tahsien, S.M., Karimipour, H. and Spachos, P., 2020. Machine learning based solutions for
security of Internet of Things (IoT): A survey. Journal of Network and Computer
Applications. 161. p.102630.
Tang, F. and et.al 2019. Future intelligent and secure vehicular network toward 6G: Machine-
learning approaches. Proceedings of the IEEE. 108(2). pp.292-307.
Doshi, R., Apthorpe, N. and Feamster, N., 2018, May. Machine learning ddos detection for
consumer internet of things devices. In 2018 IEEE Security and Privacy Workshops
(SPW) (pp. 29-35). IEEE.
Books and journals
Alhawi, O.M., Baldwin, J. and Dehghantanha, A., 2018. Leveraging machine learning
techniques for windows ransomware network traffic detection. In Cyber threat
intelligence (pp. 93-106). Springer, Cham.
Ghafir, I. and et.al 2018. Detection of advanced persistent threat using machine-learning
correlation analysis. Future Generation Computer Systems. 89. pp.349-359.
Gupta, B.B. ed., 2018. Computer and cyber security: principles, algorithm, applications, and
perspectives. CRC Press.
Haji, S.H. and Ameen, S.Y., 2021. Attack and anomaly detection in iot networks using machine
learning techniques: A review. Asian journal of research in computer science. 9(2).
pp.30-46.
Khan, R.U. and et.al 2019. An adaptive multi-layer botnet detection technique using machine
learning classifiers. Applied Sciences. 9(11). p.2375.
Martínez Torres, J., Iglesias Comesaña, C. and García-Nieto, P.J., 2019. Machine learning
techniques applied to cybersecurity. International Journal of Machine Learning and
Cybernetics. 10(10). pp.2823-2836.
Schratz, P. and et.al 2019. Hyperparameter tuning and performance assessment of statistical and
machine-learning algorithms using spatial data. Ecological Modelling. 406. pp.109-120.
Tahsien, S.M., Karimipour, H. and Spachos, P., 2020. Machine learning based solutions for
security of Internet of Things (IoT): A survey. Journal of Network and Computer
Applications. 161. p.102630.
Tang, F. and et.al 2019. Future intelligent and secure vehicular network toward 6G: Machine-
learning approaches. Proceedings of the IEEE. 108(2). pp.292-307.
Doshi, R., Apthorpe, N. and Feamster, N., 2018, May. Machine learning ddos detection for
consumer internet of things devices. In 2018 IEEE Security and Privacy Workshops
(SPW) (pp. 29-35). IEEE.
1 out of 8
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.





