Mobile Computing Opportunities in Business: A Literature Review
VerifiedAdded on 2023/06/04
|13
|3285
|170
Report
AI Summary
This report explores the opportunities presented by mobile computing within a business context, examining its impact on efficiency and management. It begins with an introduction to mobile computing and its evolution, highlighting the prevalence of mobile technology in modern business operations. The report outlines the project's objectives and scope, focusing on the advantages of mobile computing technologies. A comprehensive literature review covers the importance of mobile computing in business, including its applications in various sectors, such as e-commerce. The report also addresses the limitations of mobile computing, such as bandwidth issues, security concerns, and power consumption. The research methodology includes both quantitative and qualitative approaches, with details on sample size, variables, data collection, and analysis. The expected outcomes and conclusions are discussed, along with the reliability and validity of the research. The report emphasizes the potential of mobile computing to enhance business performance, offering insights into its application for SMEs and international operations. The study aims to identify challenges and explore mobile computing techniques for different business firms.

1
OPPORTUNITIES OF MOBILE COMPUTING IN BUSINESS
Student Name
Institute Name
OPPORTUNITIES OF MOBILE COMPUTING IN BUSINESS
Student Name
Institute Name
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

OPPORTUNITIES OF MOBILE COMPUTING IN BUSINESS 2
Contents
Introduction................................................................................................................................4
Project objective.........................................................................................................................4
Project scope..............................................................................................................................4
Literature review........................................................................................................................5
Justification................................................................................................................................7
Research questions/hypothesis...................................................................................................8
Primary research question......................................................................................................8
Secondary research question..................................................................................................8
Research design and methodology.............................................................................................8
Quantitative research..............................................................................................................8
Qualitative research................................................................................................................8
Sample size.............................................................................................................................9
Variables.................................................................................................................................9
Data collection........................................................................................................................9
Data analysis.........................................................................................................................10
Expected outcome/conclusion..............................................................................................10
Reliability and validity.........................................................................................................10
Research limitations.............................................................................................................11
Time plan.................................................................................................................................11
Reference..................................................................................................................................12
Contents
Introduction................................................................................................................................4
Project objective.........................................................................................................................4
Project scope..............................................................................................................................4
Literature review........................................................................................................................5
Justification................................................................................................................................7
Research questions/hypothesis...................................................................................................8
Primary research question......................................................................................................8
Secondary research question..................................................................................................8
Research design and methodology.............................................................................................8
Quantitative research..............................................................................................................8
Qualitative research................................................................................................................8
Sample size.............................................................................................................................9
Variables.................................................................................................................................9
Data collection........................................................................................................................9
Data analysis.........................................................................................................................10
Expected outcome/conclusion..............................................................................................10
Reliability and validity.........................................................................................................10
Research limitations.............................................................................................................11
Time plan.................................................................................................................................11
Reference..................................................................................................................................12

OPPORTUNITIES OF MOBILE COMPUTING IN BUSINESS 3
Introduction
The mobile computing is based on the usage of the normal data which helps in easy
transmission of the data and then involves the mobile communication. It includes the network
ad hoc setup and the infrastructure which is mainly for mobile applications. The mobile
computing helps in working with sufficient processing and physical capability to operate in a
movable environment. The quality of service is for the network connectivity where the
availability of network is maintained at a higher level and through a minimal amount of the
lag or the downtime (Yadav, 2016). The interactivity and individuality are for the connection
of the nodes to mobile network that helps in adapting to the new technology for catering the
nodes as well. Presently, the concept of mobile technology that has taken the same place in
day to day life as a part of project by different researchers. The concept of mobile computing
technology can be found many machineries like wireless data association, communication,
machineries presentation, smartphone and readers (Ahmed, 2017). The machines are
compact, small and one can access anywhere by any human being. The change as well as
effectivity of mobile computing technology that have given it with the capacity to function
with business to business or consumer entity.
Project objective
The main objective of the report is to highlight about the mobile computing factors and its
importance in the organisation. The report will focus on recognizing the concept and different
opportunities of mobile computing-based technology. Along with it, the report will also
discuss the different elements of mobile computing technology and will evaluate the overall
dimensions of the data as well as kind via mobile computing technologies.
Introduction
The mobile computing is based on the usage of the normal data which helps in easy
transmission of the data and then involves the mobile communication. It includes the network
ad hoc setup and the infrastructure which is mainly for mobile applications. The mobile
computing helps in working with sufficient processing and physical capability to operate in a
movable environment. The quality of service is for the network connectivity where the
availability of network is maintained at a higher level and through a minimal amount of the
lag or the downtime (Yadav, 2016). The interactivity and individuality are for the connection
of the nodes to mobile network that helps in adapting to the new technology for catering the
nodes as well. Presently, the concept of mobile technology that has taken the same place in
day to day life as a part of project by different researchers. The concept of mobile computing
technology can be found many machineries like wireless data association, communication,
machineries presentation, smartphone and readers (Ahmed, 2017). The machines are
compact, small and one can access anywhere by any human being. The change as well as
effectivity of mobile computing technology that have given it with the capacity to function
with business to business or consumer entity.
Project objective
The main objective of the report is to highlight about the mobile computing factors and its
importance in the organisation. The report will focus on recognizing the concept and different
opportunities of mobile computing-based technology. Along with it, the report will also
discuss the different elements of mobile computing technology and will evaluate the overall
dimensions of the data as well as kind via mobile computing technologies.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

OPPORTUNITIES OF MOBILE COMPUTING IN BUSINESS 4
Project scope
In the current time where the competition is fierce, organizations and business are constantly
exploring many alternatives that can make the process of business functions simple and
further improve the overall performance. It further focuses on developing a competitive edge
for the organization. The most crucial part of mobile computing technology is based on the
capacity to gain access as well as share data even when people is on the mobility. Therefore,
it is vital part of the study and focus on the overall effectiveness of mobile computing
alternatives that will assist the students to learn better and more related to application of
mobile technology as well as the business executives based on more options that will add by
mobile computing technology to any form of business.
Literature review
The mobile computing technology is considered to be the technology that is mainly to be
used in smartphones. Here, the study is about considering the technology that is mainly for
handling the transmission of voice and set of data through portable devices with using the
wireless networks (Ali, 2015). There are different sectors where the technology is used for
the ecommerce sites that can use the technology for the credit card verification system. The
mobile computing comes with portability, where the signification is about the devices that are
connected to the system. The connectivity is other fact that comes under the consideration
where quality of service is set with network connectivity. The mobile computing environment
needs to have a higher network connectivity with maintaining the smoothness of processing.
The nodes are connected to mobile computing environment where interactivity is about
focusing on effective communication process with maintaining the data set and healthy
transmission (Dahlberg et al., 2015).
Importance of Mobile Computing in Business
Project scope
In the current time where the competition is fierce, organizations and business are constantly
exploring many alternatives that can make the process of business functions simple and
further improve the overall performance. It further focuses on developing a competitive edge
for the organization. The most crucial part of mobile computing technology is based on the
capacity to gain access as well as share data even when people is on the mobility. Therefore,
it is vital part of the study and focus on the overall effectiveness of mobile computing
alternatives that will assist the students to learn better and more related to application of
mobile technology as well as the business executives based on more options that will add by
mobile computing technology to any form of business.
Literature review
The mobile computing technology is considered to be the technology that is mainly to be
used in smartphones. Here, the study is about considering the technology that is mainly for
handling the transmission of voice and set of data through portable devices with using the
wireless networks (Ali, 2015). There are different sectors where the technology is used for
the ecommerce sites that can use the technology for the credit card verification system. The
mobile computing comes with portability, where the signification is about the devices that are
connected to the system. The connectivity is other fact that comes under the consideration
where quality of service is set with network connectivity. The mobile computing environment
needs to have a higher network connectivity with maintaining the smoothness of processing.
The nodes are connected to mobile computing environment where interactivity is about
focusing on effective communication process with maintaining the data set and healthy
transmission (Dahlberg et al., 2015).
Importance of Mobile Computing in Business
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

OPPORTUNITIES OF MOBILE COMPUTING IN BUSINESS 5
Mobile computing system helps in communicating with core information structure. The range
and system bandwidth require a major security standard which is other factor that needs to be
taken into consideration (Chiang, 2016.). Hence, it is important to focus on mitigating the
issues of security through upgrading the technology and developing the software products
that will lead to improving the safety of mobile computing environment for the individuals
and business organisations. The use of antivirus can directly lead to the mitigation of the
major security related issues, where the vendor needs to be completely reliable enough about
the privacy and issues of security (Guo, 2015.). The enhancement in the technology has been
able to increase the different opportunities for the business organisations that have a
competitive advantage in the globalised market. The organisations tend to make use of
different web-based applications that are for maintaining the business operations. The aim is
to evaluate the study and provide the scope of entire project through research designing and
methodology that requires to conduct a study in a successful manner (Han, 2015)
Limitations of Mobile Computing in Business
There are certain limitations which are:
a. The problem with the system bandwidth and the range
b. The security standards are considered to be another factor which needs to be
considered.
c. The power consumptions where the mobile computers are depending upon the battery
power with no availability of the portable generator.
d. Human Interfaces with devices includes the problems related to the screens and
keyboards that are getting smaller day by day which is hard to use.
There are different limitations of mobile computing where VPN is directly vulnerable enough
that anyone can attack the larger number of the networks which are connected to it. There are
Mobile computing system helps in communicating with core information structure. The range
and system bandwidth require a major security standard which is other factor that needs to be
taken into consideration (Chiang, 2016.). Hence, it is important to focus on mitigating the
issues of security through upgrading the technology and developing the software products
that will lead to improving the safety of mobile computing environment for the individuals
and business organisations. The use of antivirus can directly lead to the mitigation of the
major security related issues, where the vendor needs to be completely reliable enough about
the privacy and issues of security (Guo, 2015.). The enhancement in the technology has been
able to increase the different opportunities for the business organisations that have a
competitive advantage in the globalised market. The organisations tend to make use of
different web-based applications that are for maintaining the business operations. The aim is
to evaluate the study and provide the scope of entire project through research designing and
methodology that requires to conduct a study in a successful manner (Han, 2015)
Limitations of Mobile Computing in Business
There are certain limitations which are:
a. The problem with the system bandwidth and the range
b. The security standards are considered to be another factor which needs to be
considered.
c. The power consumptions where the mobile computers are depending upon the battery
power with no availability of the portable generator.
d. Human Interfaces with devices includes the problems related to the screens and
keyboards that are getting smaller day by day which is hard to use.
There are different limitations of mobile computing where VPN is directly vulnerable enough
that anyone can attack the larger number of the networks which are connected to it. There are

OPPORTUNITIES OF MOBILE COMPUTING IN BUSINESS 6
problems related to the mobile computers that depends on no availability of the portable
generator. The smartphones and the computers are the target of attacks, where the security
threats can also lead to exploiting the vulnerabilities. They are related to the software that are
being used in the mobile devices.
The study is about the detailed descriptions about the time that is needed to complete the
study Here, the focus is on the identification of the challenges and the mobile computing
techniques for different firms of business (Rahimi, 2014.)
Justification
With the upgradation of technology, the mobile computing is important for the business and
its improvement. The implementation is based on the enhancement of the business
performance, where the focus is on how the devices can be effectively used for the business
organisations. The mobile computing structure can be used via many media of
communication that are improving with constant operation and can function in constant
operation that decrease the airtime and related charges. Also, the system when disconnected
can be used for storage, schedule, measurement maintenance and many other motives. This is
why, while using wireless communication, the process of mobile computing can help the
process of business in many recognized manners (Sanaei, n.d.). The project helps in
providing the range of mobile computing devices that can be used for mobile computing
devices along with the advantages. The focus is on allowing the business personnel to handle
the amount of knowledge with the different computing factors that will help in enhancing the
business performance as well, in the competitive world (Baran, 2014).
Research questions/hypothesis
Primary research question
problems related to the mobile computers that depends on no availability of the portable
generator. The smartphones and the computers are the target of attacks, where the security
threats can also lead to exploiting the vulnerabilities. They are related to the software that are
being used in the mobile devices.
The study is about the detailed descriptions about the time that is needed to complete the
study Here, the focus is on the identification of the challenges and the mobile computing
techniques for different firms of business (Rahimi, 2014.)
Justification
With the upgradation of technology, the mobile computing is important for the business and
its improvement. The implementation is based on the enhancement of the business
performance, where the focus is on how the devices can be effectively used for the business
organisations. The mobile computing structure can be used via many media of
communication that are improving with constant operation and can function in constant
operation that decrease the airtime and related charges. Also, the system when disconnected
can be used for storage, schedule, measurement maintenance and many other motives. This is
why, while using wireless communication, the process of mobile computing can help the
process of business in many recognized manners (Sanaei, n.d.). The project helps in
providing the range of mobile computing devices that can be used for mobile computing
devices along with the advantages. The focus is on allowing the business personnel to handle
the amount of knowledge with the different computing factors that will help in enhancing the
business performance as well, in the competitive world (Baran, 2014).
Research questions/hypothesis
Primary research question
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

OPPORTUNITIES OF MOBILE COMPUTING IN BUSINESS 7
1. How mobile computing can impact the efficiency of management for a specific business?
Secondary research question
1. How mobile computing impact the small and the medium scale enterprises (SMEs)?
2. How it impacts the efficiency of the workers and enhance the productivity?
3. Explain the role of mobile computing in collating the information mainly for the
operations for a business at international level?
Research design and methodology
The research methodology is important to help the research in getting the feasible instruction
with evaluating the findings of research issue. In order to satisfy the objectives, the research
is held for the small samples while the outcomes are not measurable and quantifiable. The
basic advantage is that it serves the basic research that offers a complete description of the
analysis without limitation of the scope research and the participant response.
Qualitative research
The aim is about the complete and detailed description where the researcher needs to
understand about what he/she is looking for. There are recommendations at the early phases
of the research project and the design emerges when there is an unfold of study. The data is
mainly in forms of words and the pictures, which is subjective of the individual’s
interpretation of events which is important. The qualitative data is rich with time consuming
where the researcher tends to work with immersing in the subject matter. (Soyata, n.d.). The
qualitative research is used for working on detailed questionnaire with the open and the
closed ended questions.
Quantitative research
1. How mobile computing can impact the efficiency of management for a specific business?
Secondary research question
1. How mobile computing impact the small and the medium scale enterprises (SMEs)?
2. How it impacts the efficiency of the workers and enhance the productivity?
3. Explain the role of mobile computing in collating the information mainly for the
operations for a business at international level?
Research design and methodology
The research methodology is important to help the research in getting the feasible instruction
with evaluating the findings of research issue. In order to satisfy the objectives, the research
is held for the small samples while the outcomes are not measurable and quantifiable. The
basic advantage is that it serves the basic research that offers a complete description of the
analysis without limitation of the scope research and the participant response.
Qualitative research
The aim is about the complete and detailed description where the researcher needs to
understand about what he/she is looking for. There are recommendations at the early phases
of the research project and the design emerges when there is an unfold of study. The data is
mainly in forms of words and the pictures, which is subjective of the individual’s
interpretation of events which is important. The qualitative data is rich with time consuming
where the researcher tends to work with immersing in the subject matter. (Soyata, n.d.). The
qualitative research is used for working on detailed questionnaire with the open and the
closed ended questions.
Quantitative research
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

OPPORTUNITIES OF MOBILE COMPUTING IN BUSINESS 8
For quantitative methods, the aim is to work on classifying the features with counting them
and constructing the different statistical models. The research requires to focus on different
phases of the research project, where the aspects of study are designed before the data could
be collected. The data is mainly in the form of numbers and the statistics, where objectives
seeks precise measurements and the analysis of the target concepts with the surveys and
questionnaires etc.
Sample size
The method of sampling is mainly for developing the research under discussion. According to
the analysis, there are categories of non-probability sampling techniques, where the sample
members are selected mainly on the basis of the knowledge and the relationships with
expertise on a particular research subject. The current sample members who are selected are
having a special relation with the investigation and work experience, active involvement and
partnership with proven research background. They are representation of the population and
then being studied. The findings of the sample population could easily be used for the
research in the study population. Within the context, the participants of the study include 6
people who are using the technique of mobile computing in their business.
Sampling
The study will cover simple yet random sample options that will be utilised to interview
respondents, reply the research queries and evaluate the hypothesis. A pilot study will be
conducted right before the important study to decide the overall effectiveness of data
collection techniques before the main survey (Han, 2015)
Variables
For quantitative methods, the aim is to work on classifying the features with counting them
and constructing the different statistical models. The research requires to focus on different
phases of the research project, where the aspects of study are designed before the data could
be collected. The data is mainly in the form of numbers and the statistics, where objectives
seeks precise measurements and the analysis of the target concepts with the surveys and
questionnaires etc.
Sample size
The method of sampling is mainly for developing the research under discussion. According to
the analysis, there are categories of non-probability sampling techniques, where the sample
members are selected mainly on the basis of the knowledge and the relationships with
expertise on a particular research subject. The current sample members who are selected are
having a special relation with the investigation and work experience, active involvement and
partnership with proven research background. They are representation of the population and
then being studied. The findings of the sample population could easily be used for the
research in the study population. Within the context, the participants of the study include 6
people who are using the technique of mobile computing in their business.
Sampling
The study will cover simple yet random sample options that will be utilised to interview
respondents, reply the research queries and evaluate the hypothesis. A pilot study will be
conducted right before the important study to decide the overall effectiveness of data
collection techniques before the main survey (Han, 2015)
Variables

OPPORTUNITIES OF MOBILE COMPUTING IN BUSINESS 9
The elements of the research will further be diversified as dependent as well as independent
variables. The dependent variable will consist of age and gender of the respondents. On the
other hand, the independent variables will consist of the basic nature of the organization,
whether they utilise the standard mobile computing technology.
Data collection
After selecting the sample for the current study, kinds of informed consent along with the
study of the candidates on electronic platform and by hand delivery. The motive of the study
will be well explained to the respondents and further will be promised to make it confidential
and only be combined with opinions of other contestants to form more general conclusions
along with various recommendation (Han, 2015). The questionnaires here will be sent to the
respondents through email address while many other can deliver by research associates. The
candidate will be further asking question to submit the filled questionnaire which will go
back to the researcher in just three days’ time. The participants have been asked to submit the
questionnaires with the researchers, where the responses that are received from the different
questionnaires and the interviews are then sent to the Microsoft excel, edited and properly
coded as needed. Here, the data is then exported into SPSS version for 17 data analysis
software, with proper analysis and the presentation through descriptive statistics like the
means, mode percentage with the 5 Likert scale and standard deviations. The summaries are
defined with tables, charts and graphs. The multilinear regression model will then be used for
further details in organisations.
Data analysis
The answers received from questionnaires will be entered in Microsoft excel, coded and
edited rightly. The information will then be exported into a version called as SPSS along
The elements of the research will further be diversified as dependent as well as independent
variables. The dependent variable will consist of age and gender of the respondents. On the
other hand, the independent variables will consist of the basic nature of the organization,
whether they utilise the standard mobile computing technology.
Data collection
After selecting the sample for the current study, kinds of informed consent along with the
study of the candidates on electronic platform and by hand delivery. The motive of the study
will be well explained to the respondents and further will be promised to make it confidential
and only be combined with opinions of other contestants to form more general conclusions
along with various recommendation (Han, 2015). The questionnaires here will be sent to the
respondents through email address while many other can deliver by research associates. The
candidate will be further asking question to submit the filled questionnaire which will go
back to the researcher in just three days’ time. The participants have been asked to submit the
questionnaires with the researchers, where the responses that are received from the different
questionnaires and the interviews are then sent to the Microsoft excel, edited and properly
coded as needed. Here, the data is then exported into SPSS version for 17 data analysis
software, with proper analysis and the presentation through descriptive statistics like the
means, mode percentage with the 5 Likert scale and standard deviations. The summaries are
defined with tables, charts and graphs. The multilinear regression model will then be used for
further details in organisations.
Data analysis
The answers received from questionnaires will be entered in Microsoft excel, coded and
edited rightly. The information will then be exported into a version called as SPSS along
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

OPPORTUNITIES OF MOBILE COMPUTING IN BUSINESS 10
seventeen software for data analysis and presented with the use of descriptive statistics like
means, standard deviations, 5-likert scale and many more (Sanaei, n.d.). All the summaries of
the outcome will be presented visually in kinds of charts, tables as well as graphs. The
regression model is used for the finding out of the effectiveness and then working on the
controlling of effects on the independent variables, where one tends to offer the information
that concerns about the effects which are relevant to the independent variables.
Expected outcome/conclusion
Rise in the field of technology has further increased the set of options for the business
company to have some competitive edge in the international market. Thus, the researchers
consist of business companies that are mainly moving in the direction of technological
advancement to increase the productivity level. Before, the companies utilise varied web-
related application to maintain the process of business (Ali, 2015). But, the rise in usage of
Smartphone further brings the usage of mobile technologies into current business operations.
Reliability and validity
The usage of mixed methodology in research is related with varied threats towards the
concept of validity and reliability of obtained outcome. In primary data, an evaluation for
validity and reliability will be performed to actually find out whether the same outcome is
reproducible or not (Ahmed, 2017). The secondary data is not needed for the test because the
data will be already published and signed for the different organisations.
Research limitations
Some of the restrictions of methodology in the current research will be related to long time as
well as efforts needed. Also, the research will need more amount of resources to gather
seventeen software for data analysis and presented with the use of descriptive statistics like
means, standard deviations, 5-likert scale and many more (Sanaei, n.d.). All the summaries of
the outcome will be presented visually in kinds of charts, tables as well as graphs. The
regression model is used for the finding out of the effectiveness and then working on the
controlling of effects on the independent variables, where one tends to offer the information
that concerns about the effects which are relevant to the independent variables.
Expected outcome/conclusion
Rise in the field of technology has further increased the set of options for the business
company to have some competitive edge in the international market. Thus, the researchers
consist of business companies that are mainly moving in the direction of technological
advancement to increase the productivity level. Before, the companies utilise varied web-
related application to maintain the process of business (Ali, 2015). But, the rise in usage of
Smartphone further brings the usage of mobile technologies into current business operations.
Reliability and validity
The usage of mixed methodology in research is related with varied threats towards the
concept of validity and reliability of obtained outcome. In primary data, an evaluation for
validity and reliability will be performed to actually find out whether the same outcome is
reproducible or not (Ahmed, 2017). The secondary data is not needed for the test because the
data will be already published and signed for the different organisations.
Research limitations
Some of the restrictions of methodology in the current research will be related to long time as
well as efforts needed. Also, the research will need more amount of resources to gather
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
OPPORTUNITIES OF MOBILE COMPUTING IN BUSINESS 11
enough data to answer the set questions of research (Soyata, n.d.). There are many sources of
data and will be utilised to stay more confident with current research findings which will
most probably cover data obtained that might not be very collaborative and therefore can
have the possibility of the current discrepancies of the outcomes.
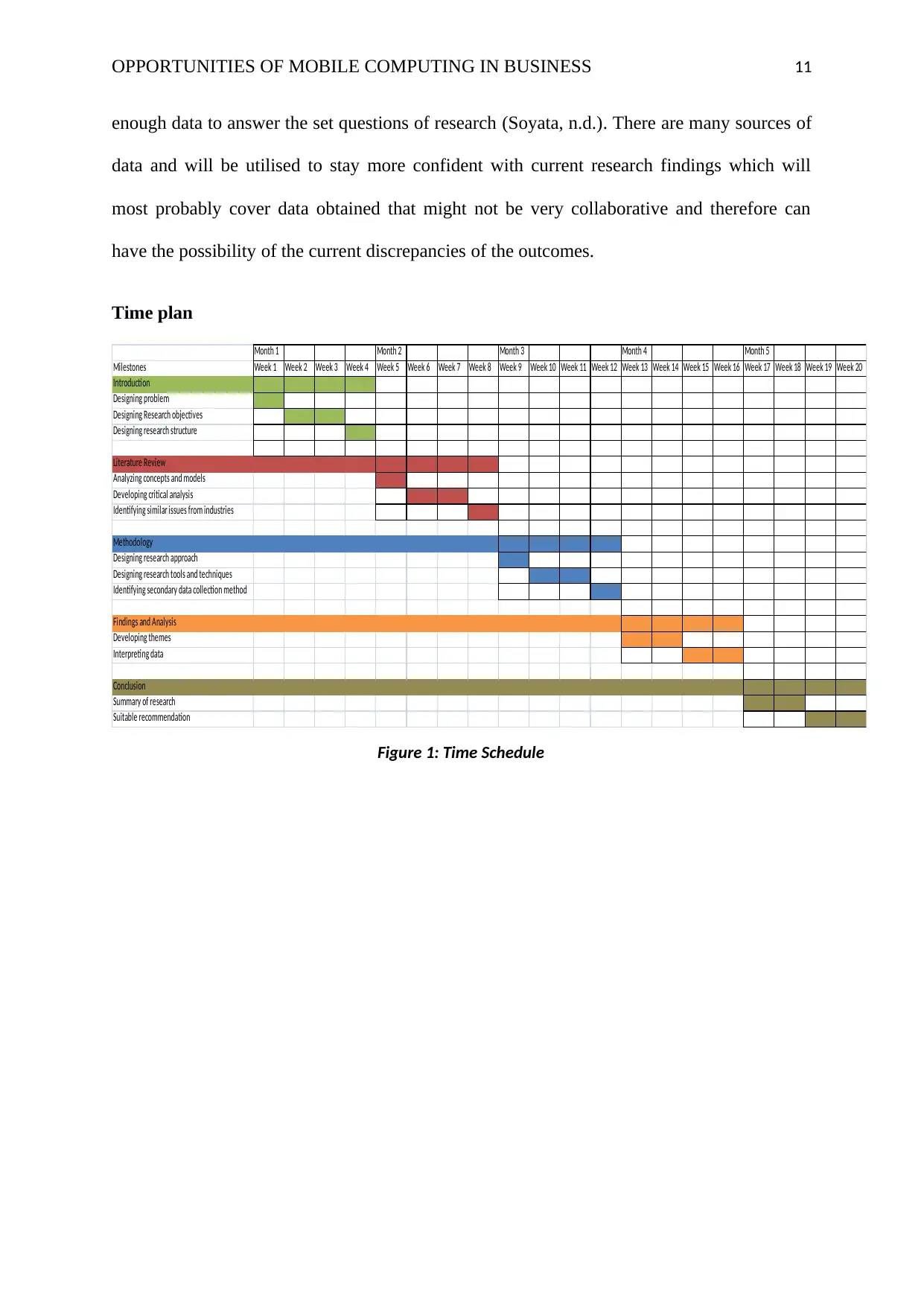
Time plan
Month 1 Month 2 Month 3 Month 4 Month 5
Milestones Week 1 Week 2 Week 3 Week 4 Week 5 Week 6 Week 7 Week 8 Week 9 Week 10 Week 11 Week 12 Week 13 Week 14 Week 15 Week 16 Week 17 Week 18 Week 19 Week 20
Introduction
Designing problem
Designing Research objectives
Designing research structure
Literature Review
Analyzing concepts and models
Developing critical analysis
Identifying similar issues from industries
Methodology
Designing research approach
Designing research tools and techniques
Identifying secondary data collection method
Findings and Analysis
Developing themes
Interpreting data
Conclusion
Summary of research
Suitable recommendation
Figure 1: Time Schedule
enough data to answer the set questions of research (Soyata, n.d.). There are many sources of
data and will be utilised to stay more confident with current research findings which will
most probably cover data obtained that might not be very collaborative and therefore can
have the possibility of the current discrepancies of the outcomes.
Time plan
Month 1 Month 2 Month 3 Month 4 Month 5
Milestones Week 1 Week 2 Week 3 Week 4 Week 5 Week 6 Week 7 Week 8 Week 9 Week 10 Week 11 Week 12 Week 13 Week 14 Week 15 Week 16 Week 17 Week 18 Week 19 Week 20
Introduction
Designing problem
Designing Research objectives
Designing research structure
Literature Review
Analyzing concepts and models
Developing critical analysis
Identifying similar issues from industries
Methodology
Designing research approach
Designing research tools and techniques
Identifying secondary data collection method
Findings and Analysis
Developing themes
Interpreting data
Conclusion
Summary of research
Suitable recommendation
Figure 1: Time Schedule

OPPORTUNITIES OF MOBILE COMPUTING IN BUSINESS 12
References
Ahmed, E. a. R. M., 2017. Mobile edge computing: opportunities, solutions, and challenges..
s.l.:s.n.
Ali, M. K. S. a. V. A., 2015. Security in cloud computing: Opportunities and challenges.
Information sciences, 305, pp.357-383. ed. s.l.:s.n.
Baran, E., 2014. A review of research on mobile learning in teacher education. Journal of
Educational Technology & Society, 17(4), p.17.
Chiang, M. a. Z. T., 2016.. Fog and IoT: An overview of research opportunities. IEEE
Internet of Things Journal, 3(6), , pp. pp.854-864..
Dahlberg, T., Guo, J. and Ondrus, J., 2015. A critical review of mobile payment
research. Electronic Commerce Research and Applications, 14(5), pp.265-284.
Guo, B. W. Z. Y. Z. W. Y. Y. N. H. R. a. Z. X., 2015.. Mobile crowd sensing and computing:
The review of an emerging human-powered sensing paradigm.. ACM Computing Surveys
(CSUR),, pp. 48(1), p.7..
Han, B. G. V. J. L. a. L. S., 2015. Network function virtualization: Challenges and
opportunities for innovations.. IEEE Communications Magazine, , Volume 53(2),, pp. pp.90-
97..
Hu, Y. P. M. S. D. S. N. a. Y. V., 2015. Mobile edge computing—A key technology towards
5G. 11(11), ( ETSI white paper), pp. pp.1-16..
Rahimi, M. R. J. L. C. V. A. a. V. N., 2014.. Mobile cloud computing: A survey, state of art
and future directions.. Mobile Networks and Applications, Volume 19(2), , pp. pp.133-143..
Sanaei, Z. A. S. G. A. a. B. R. 2., n.d. Heterogeneity in mobile cloud computing: taxonomy
and open challenges.. IEEE Communications Surveys & Tutorials, Volume 16(1),, pp.
pp.369-392..
Soyata, T. B. H. H. W. K. M. a. S. J. 2., n.d. Accelerating mobile-cloud computing: A
survey.. IGI Global., Volume Cloud Technology: Concepts, Methodologies, Tools, and
Applications , pp. (pp. 1933-1955).
Yadav, R., Sharma, S.K. and Tarhini, A., 2016. A multi-analytical approach to understand
and predict the mobile commerce adoption. Journal of enterprise information
References
Ahmed, E. a. R. M., 2017. Mobile edge computing: opportunities, solutions, and challenges..
s.l.:s.n.
Ali, M. K. S. a. V. A., 2015. Security in cloud computing: Opportunities and challenges.
Information sciences, 305, pp.357-383. ed. s.l.:s.n.
Baran, E., 2014. A review of research on mobile learning in teacher education. Journal of
Educational Technology & Society, 17(4), p.17.
Chiang, M. a. Z. T., 2016.. Fog and IoT: An overview of research opportunities. IEEE
Internet of Things Journal, 3(6), , pp. pp.854-864..
Dahlberg, T., Guo, J. and Ondrus, J., 2015. A critical review of mobile payment
research. Electronic Commerce Research and Applications, 14(5), pp.265-284.
Guo, B. W. Z. Y. Z. W. Y. Y. N. H. R. a. Z. X., 2015.. Mobile crowd sensing and computing:
The review of an emerging human-powered sensing paradigm.. ACM Computing Surveys
(CSUR),, pp. 48(1), p.7..
Han, B. G. V. J. L. a. L. S., 2015. Network function virtualization: Challenges and
opportunities for innovations.. IEEE Communications Magazine, , Volume 53(2),, pp. pp.90-
97..
Hu, Y. P. M. S. D. S. N. a. Y. V., 2015. Mobile edge computing—A key technology towards
5G. 11(11), ( ETSI white paper), pp. pp.1-16..
Rahimi, M. R. J. L. C. V. A. a. V. N., 2014.. Mobile cloud computing: A survey, state of art
and future directions.. Mobile Networks and Applications, Volume 19(2), , pp. pp.133-143..
Sanaei, Z. A. S. G. A. a. B. R. 2., n.d. Heterogeneity in mobile cloud computing: taxonomy
and open challenges.. IEEE Communications Surveys & Tutorials, Volume 16(1),, pp.
pp.369-392..
Soyata, T. B. H. H. W. K. M. a. S. J. 2., n.d. Accelerating mobile-cloud computing: A
survey.. IGI Global., Volume Cloud Technology: Concepts, Methodologies, Tools, and
Applications , pp. (pp. 1933-1955).
Yadav, R., Sharma, S.K. and Tarhini, A., 2016. A multi-analytical approach to understand
and predict the mobile commerce adoption. Journal of enterprise information
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
1 out of 13
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.





