Mobile network and wireless communication.1
VerifiedAdded on 2022/10/06
|5
|890
|16
Assignment
AI Summary
Contribute Materials
Your contribution can guide someone’s learning journey. Share your
documents today.

Mobile network and wireless communication
Student Name –
Student ID –
Part A
Solution 1: Access to Wireless Network ( e.g. Wifi)
a) Media Access Control
MAC ( media access control ) is a layer present in the DLL ( data link layer ) of the
OSI reference model ( which consists of 7 layers). It controls when the computers can
transmit. It helps to transmit the packets of data to the NIC ( network interface card )
and a remote shared channel and also from both of them. MAC sub layer can control
the hardware which helps to interact to various types of transmission media ( like
wired , wireless , optical etc. )
Importance :
It is important because it performs various functions like delimitation and recognising
the frame, destination station addressing, source station addressing, protects from
errors ( by generation as well as frame check sequence) , controls interaction with
transmission media and leads to transparent data transfer.
b) Example of controlled access methods :
Reservation, Polling , Token Passing.
Example of Contention based media access methods :
Ethernet uses the scheme CSMA/CD.
c) Preference of 1 access method over another in a network :
The method which is better depends on certain conditions of the network. Contention
based media access methods are preferred as compared to controlled access methods.
Student Name –
Student ID –
Part A
Solution 1: Access to Wireless Network ( e.g. Wifi)
a) Media Access Control
MAC ( media access control ) is a layer present in the DLL ( data link layer ) of the
OSI reference model ( which consists of 7 layers). It controls when the computers can
transmit. It helps to transmit the packets of data to the NIC ( network interface card )
and a remote shared channel and also from both of them. MAC sub layer can control
the hardware which helps to interact to various types of transmission media ( like
wired , wireless , optical etc. )
Importance :
It is important because it performs various functions like delimitation and recognising
the frame, destination station addressing, source station addressing, protects from
errors ( by generation as well as frame check sequence) , controls interaction with
transmission media and leads to transparent data transfer.
b) Example of controlled access methods :
Reservation, Polling , Token Passing.
Example of Contention based media access methods :
Ethernet uses the scheme CSMA/CD.
c) Preference of 1 access method over another in a network :
The method which is better depends on certain conditions of the network. Contention
based media access methods are preferred as compared to controlled access methods.
Secure Best Marks with AI Grader
Need help grading? Try our AI Grader for instant feedback on your assignments.
In this method , any of the computers present within a network has the capability of
data transmission at any given time. There is mechanism for collision detection ,
recovery and avoidance.
d) Contention based media access control techniques can outperform controlled access
techniques. It means they have lower response time. This happens under certain
conditions. It works better for small networks having small value of usage. In this
case, the collision probability is less. But incase of higher volume, the performance
can degrade.
Solution 2 :
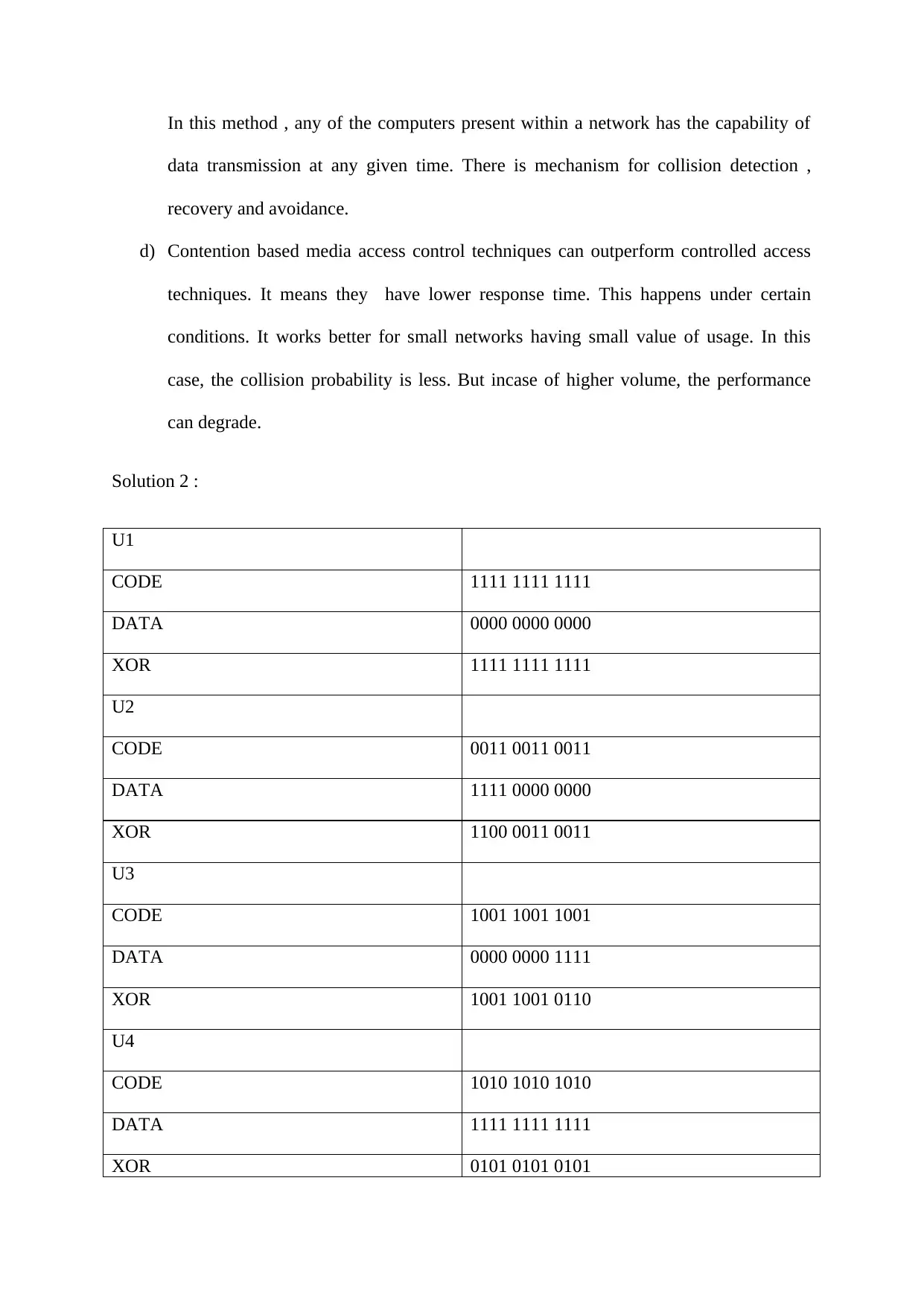
U1
CODE 1111 1111 1111
DATA 0000 0000 0000
XOR 1111 1111 1111
U2
CODE 0011 0011 0011
DATA 1111 0000 0000
XOR 1100 0011 0011
U3
CODE 1001 1001 1001
DATA 0000 0000 1111
XOR 1001 1001 0110
U4
CODE 1010 1010 1010
DATA 1111 1111 1111
XOR 0101 0101 0101
data transmission at any given time. There is mechanism for collision detection ,
recovery and avoidance.
d) Contention based media access control techniques can outperform controlled access
techniques. It means they have lower response time. This happens under certain
conditions. It works better for small networks having small value of usage. In this
case, the collision probability is less. But incase of higher volume, the performance
can degrade.
Solution 2 :
U1
CODE 1111 1111 1111
DATA 0000 0000 0000
XOR 1111 1111 1111
U2
CODE 0011 0011 0011
DATA 1111 0000 0000
XOR 1100 0011 0011
U3
CODE 1001 1001 1001
DATA 0000 0000 1111
XOR 1001 1001 0110
U4
CODE 1010 1010 1010
DATA 1111 1111 1111
XOR 0101 0101 0101
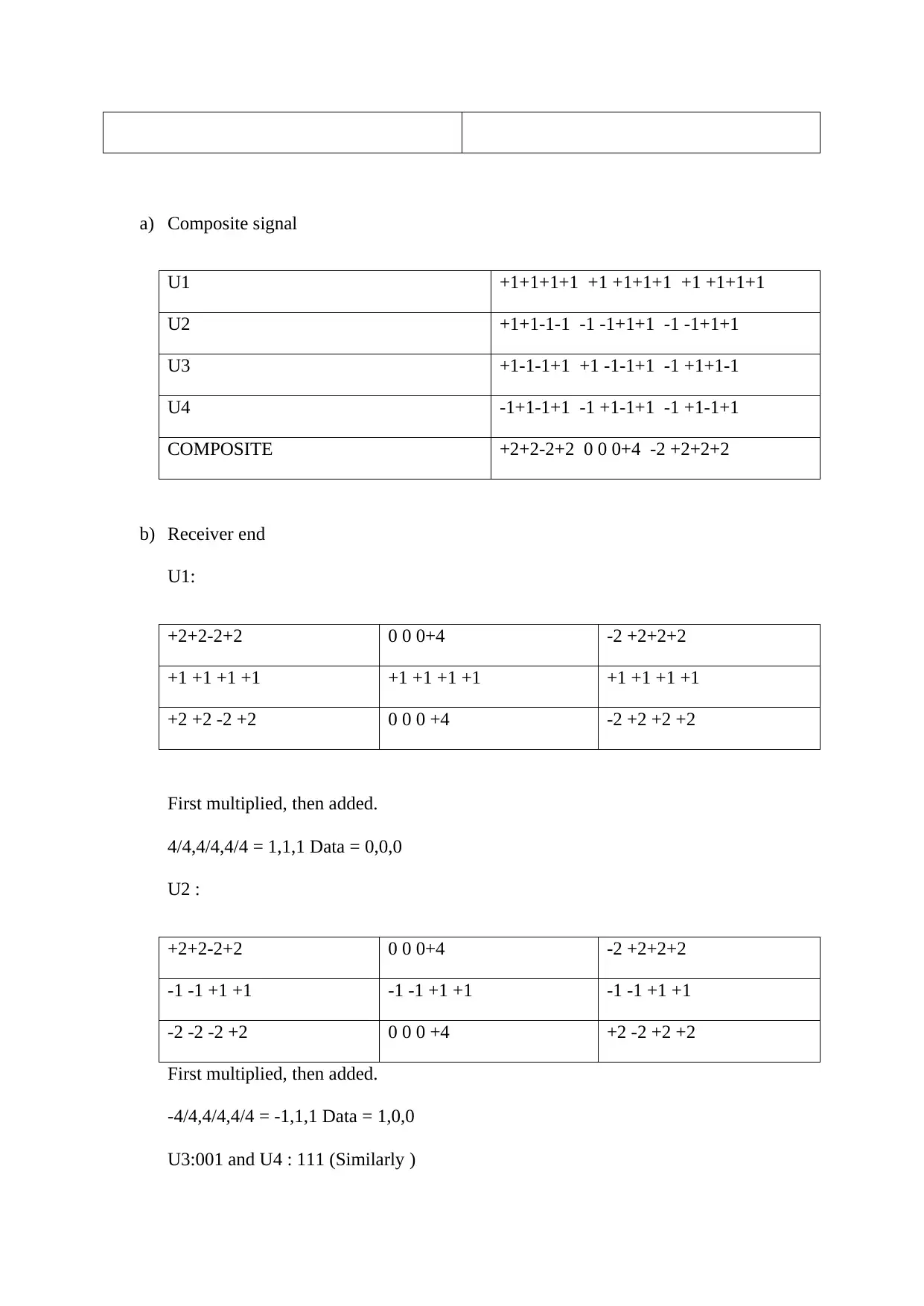
a) Composite signal
U1 +1+1+1+1 +1 +1+1+1 +1 +1+1+1
U2 +1+1-1-1 -1 -1+1+1 -1 -1+1+1
U3 +1-1-1+1 +1 -1-1+1 -1 +1+1-1
U4 -1+1-1+1 -1 +1-1+1 -1 +1-1+1
COMPOSITE +2+2-2+2 0 0 0+4 -2 +2+2+2
b) Receiver end
U1:
+2+2-2+2 0 0 0+4 -2 +2+2+2
+1 +1 +1 +1 +1 +1 +1 +1 +1 +1 +1 +1
+2 +2 -2 +2 0 0 0 +4 -2 +2 +2 +2
First multiplied, then added.
4/4,4/4,4/4 = 1,1,1 Data = 0,0,0
U2 :
+2+2-2+2 0 0 0+4 -2 +2+2+2
-1 -1 +1 +1 -1 -1 +1 +1 -1 -1 +1 +1
-2 -2 -2 +2 0 0 0 +4 +2 -2 +2 +2
First multiplied, then added.
-4/4,4/4,4/4 = -1,1,1 Data = 1,0,0
U3:001 and U4 : 111 (Similarly )
U1 +1+1+1+1 +1 +1+1+1 +1 +1+1+1
U2 +1+1-1-1 -1 -1+1+1 -1 -1+1+1
U3 +1-1-1+1 +1 -1-1+1 -1 +1+1-1
U4 -1+1-1+1 -1 +1-1+1 -1 +1-1+1
COMPOSITE +2+2-2+2 0 0 0+4 -2 +2+2+2
b) Receiver end
U1:
+2+2-2+2 0 0 0+4 -2 +2+2+2
+1 +1 +1 +1 +1 +1 +1 +1 +1 +1 +1 +1
+2 +2 -2 +2 0 0 0 +4 -2 +2 +2 +2
First multiplied, then added.
4/4,4/4,4/4 = 1,1,1 Data = 0,0,0
U2 :
+2+2-2+2 0 0 0+4 -2 +2+2+2
-1 -1 +1 +1 -1 -1 +1 +1 -1 -1 +1 +1
-2 -2 -2 +2 0 0 0 +4 +2 -2 +2 +2
First multiplied, then added.
-4/4,4/4,4/4 = -1,1,1 Data = 1,0,0
U3:001 and U4 : 111 (Similarly )
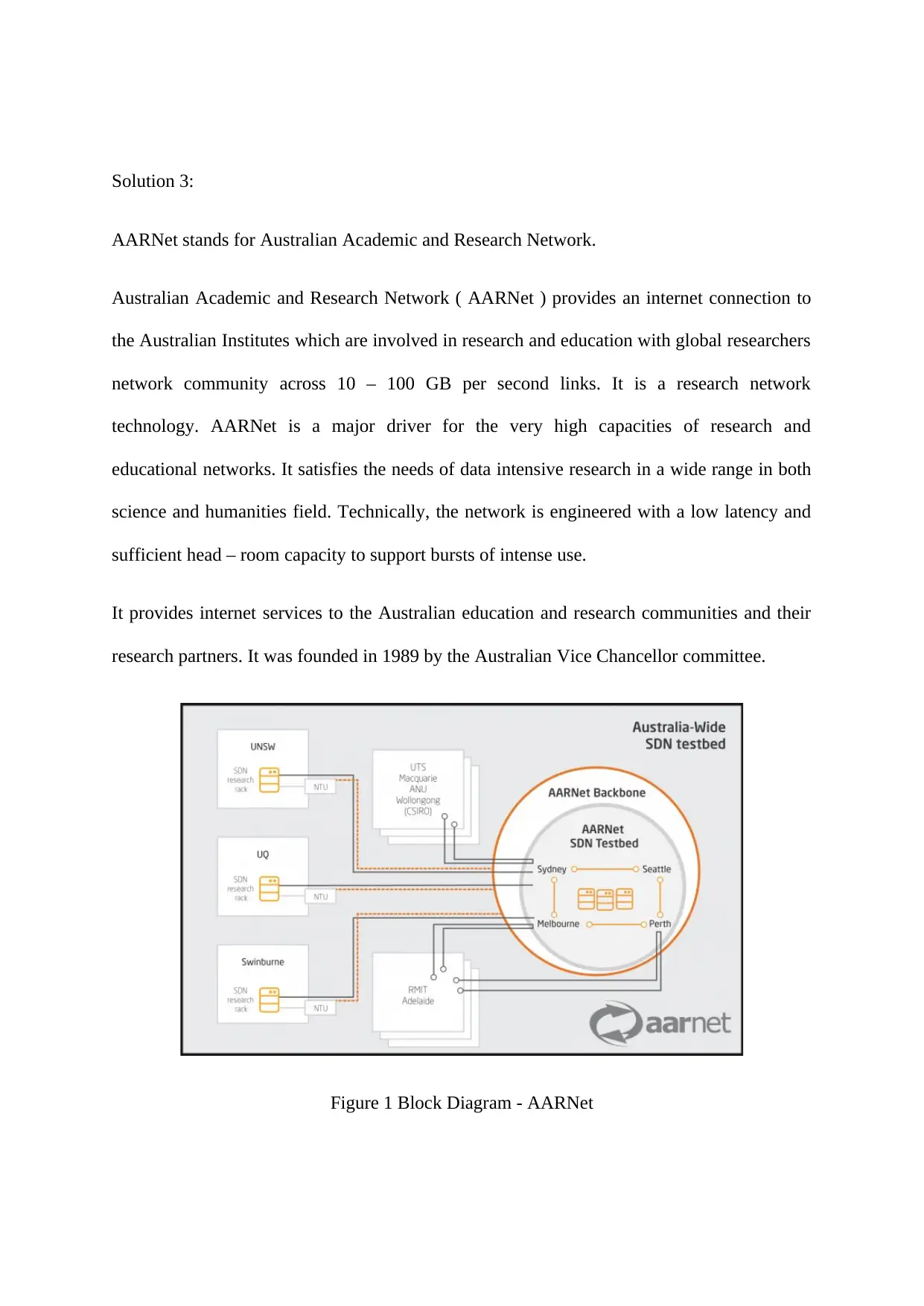
Solution 3:
AARNet stands for Australian Academic and Research Network.
Australian Academic and Research Network ( AARNet ) provides an internet connection to
the Australian Institutes which are involved in research and education with global researchers
network community across 10 – 100 GB per second links. It is a research network
technology. AARNet is a major driver for the very high capacities of research and
educational networks. It satisfies the needs of data intensive research in a wide range in both
science and humanities field. Technically, the network is engineered with a low latency and
sufficient head – room capacity to support bursts of intense use.
It provides internet services to the Australian education and research communities and their
research partners. It was founded in 1989 by the Australian Vice Chancellor committee.
Figure 1 Block Diagram - AARNet
AARNet stands for Australian Academic and Research Network.
Australian Academic and Research Network ( AARNet ) provides an internet connection to
the Australian Institutes which are involved in research and education with global researchers
network community across 10 – 100 GB per second links. It is a research network
technology. AARNet is a major driver for the very high capacities of research and
educational networks. It satisfies the needs of data intensive research in a wide range in both
science and humanities field. Technically, the network is engineered with a low latency and
sufficient head – room capacity to support bursts of intense use.
It provides internet services to the Australian education and research communities and their
research partners. It was founded in 1989 by the Australian Vice Chancellor committee.
Figure 1 Block Diagram - AARNet
Secure Best Marks with AI Grader
Need help grading? Try our AI Grader for instant feedback on your assignments.

AARNet provides high capacity , leading edge internet and other advanced networking and
communication services to the nation’s universities, health and other research organisations,
schools, vocational training providers and cultural institutions.
Speed – It provides in the multiples of 10 and 100 GB per second to the American’s Institute
of research and education.
Cloud Services – Cloud Store is an AARNet owned and operated service that provides fast ,
secure and easy to use cloud data storage and data transfer solutions for researchers, all
hosted on the AARNet network. 1 TB of storage is available to individual researchers at
AARNet connected institutions. Group storage is also available.
References
Ma, Z., Zhang, Z., Ding, Z., Fan, P., & Li, H. (2015). Key techniques for 5G wireless
communications: network architecture, physical layer, and MAC layer perspectives. Science
China information sciences, 58(4), 1-20.
Yang, N., Wang, L., Geraci, G., Elkashlan, M., Yuan, J., & Di Renzo, M. (2015).
Safeguarding 5G wireless communication networks using physical layer security. IEEE
Communications Magazine, 53(4), 20-27.
communication services to the nation’s universities, health and other research organisations,
schools, vocational training providers and cultural institutions.
Speed – It provides in the multiples of 10 and 100 GB per second to the American’s Institute
of research and education.
Cloud Services – Cloud Store is an AARNet owned and operated service that provides fast ,
secure and easy to use cloud data storage and data transfer solutions for researchers, all
hosted on the AARNet network. 1 TB of storage is available to individual researchers at
AARNet connected institutions. Group storage is also available.
References
Ma, Z., Zhang, Z., Ding, Z., Fan, P., & Li, H. (2015). Key techniques for 5G wireless
communications: network architecture, physical layer, and MAC layer perspectives. Science
China information sciences, 58(4), 1-20.
Yang, N., Wang, L., Geraci, G., Elkashlan, M., Yuan, J., & Di Renzo, M. (2015).
Safeguarding 5G wireless communication networks using physical layer security. IEEE
Communications Magazine, 53(4), 20-27.
1 out of 5
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
© 2024 | Zucol Services PVT LTD | All rights reserved.





