Mobile Network & Wireless Communication: A Comprehensive Analysis
VerifiedAdded on 2024/06/21
|13
|1953
|217
AI Summary
This document delves into the intricacies of mobile networks and wireless communication, exploring key concepts like media access control, spread spectrum techniques, and the architecture of AARNet, a prominent Australian research network. It further analyzes the strengths and weaknesses of Bluetooth and WiFi technologies in the context of IoT applications. The document concludes with a practical analysis of wireless access points using the inSSIDer app, highlighting signal strength and network security considerations.
Contribute Materials
Your contribution can guide someone’s learning journey. Share your
documents today.

Mobile Network & Wireless Communication1
Mobile Network & Wireless Communication
By: Students Name
Class
Professor’s Name
University Name
Date
Mobile Network & Wireless Communication
By: Students Name
Class
Professor’s Name
University Name
Date
Secure Best Marks with AI Grader
Need help grading? Try our AI Grader for instant feedback on your assignments.

Mobile Network & Wireless Communication2
Q1.a) what is media access control, and why is it important?
Media Access Control
Medium Access Control is an OSI reference template data communication sub-layer that controls
data packets' transmission to a network interface or from one network to another through specific
protocols (Dibaei and Ghaffari, 2020). Regulation of media access is a crucial mechanism to
resolve processes and channel control, allowing successful communications between wireless
devices and the network. MAC also helps determine how a communication node may reach the
shared channel and settle disputes between communications nodes. In comparison, defects in the
physical layer are impossible to repair without the MAC mechanism.
b) Give one example each of the controlled access methods and contention-based media
access methods?
Contention media access management requires the transfer of nodes at all times to allow for
collisions. Carrier Sense Multiple Access is an example of a complex strategy. This technique
involves a network system to predict when the network medium transmits or idles before it
attempts to transmit its data. This method is used along with an approach to settle medium
conflicts to prevent a collision. This process is known as the identification of collisions. The
overall process is thus referred to as Carrier Sense Multiple Access Collision Detection CSMA /
CD (Collision Detection Multiple Access CSMA / CD). Nodes can be distributed without
triggering collisions in a medium simultaneously. Rate Division Multiple Access is an example
of this strategy. This technique splits the spectrum into many frequency bands from which the
exchange of data between two pairs of nodes happens.
c) When might one access method be preferred over another in a network, and why?
Q1.a) what is media access control, and why is it important?
Media Access Control
Medium Access Control is an OSI reference template data communication sub-layer that controls
data packets' transmission to a network interface or from one network to another through specific
protocols (Dibaei and Ghaffari, 2020). Regulation of media access is a crucial mechanism to
resolve processes and channel control, allowing successful communications between wireless
devices and the network. MAC also helps determine how a communication node may reach the
shared channel and settle disputes between communications nodes. In comparison, defects in the
physical layer are impossible to repair without the MAC mechanism.
b) Give one example each of the controlled access methods and contention-based media
access methods?
Contention media access management requires the transfer of nodes at all times to allow for
collisions. Carrier Sense Multiple Access is an example of a complex strategy. This technique
involves a network system to predict when the network medium transmits or idles before it
attempts to transmit its data. This method is used along with an approach to settle medium
conflicts to prevent a collision. This process is known as the identification of collisions. The
overall process is thus referred to as Carrier Sense Multiple Access Collision Detection CSMA /
CD (Collision Detection Multiple Access CSMA / CD). Nodes can be distributed without
triggering collisions in a medium simultaneously. Rate Division Multiple Access is an example
of this strategy. This technique splits the spectrum into many frequency bands from which the
exchange of data between two pairs of nodes happens.
c) When might one access method be preferred over another in a network, and why?

Mobile Network & Wireless Communication3
A variety of variables depend upon the choice of the media access management technique.
Efficiency is first required in the use of machine resources. The choice of a form of media access
management is often influenced by durability and latency.
d) Under what conditions do contention‐based media access control techniques outperform
controlled‐access techniques (i.e., have lower response time)? Explain.
Since managed access methods delegate resources to a communication node, overheads are
created compared with dispute based methods. For wider networks in which there are several
nodes, managed approaches are also preferable. They are not appropriate for small networks,
however, since they create resource depletion. Therefore, contended methods have low latency
for narrower networks, which ensures they transcend controlled access methods.
Q2.a) show how each receiver can retrieve its own data using the corresponding spreading
code. b) Show how each receiver can retrieve its own data using the corresponding
spreading code.
a) Encode ‘1’ as ‘+1’ and ‘0’ as ‘-1’ User 1> R1 1111 000
A variety of variables depend upon the choice of the media access management technique.
Efficiency is first required in the use of machine resources. The choice of a form of media access
management is often influenced by durability and latency.
d) Under what conditions do contention‐based media access control techniques outperform
controlled‐access techniques (i.e., have lower response time)? Explain.
Since managed access methods delegate resources to a communication node, overheads are
created compared with dispute based methods. For wider networks in which there are several
nodes, managed approaches are also preferable. They are not appropriate for small networks,
however, since they create resource depletion. Therefore, contended methods have low latency
for narrower networks, which ensures they transcend controlled access methods.
Q2.a) show how each receiver can retrieve its own data using the corresponding spreading
code. b) Show how each receiver can retrieve its own data using the corresponding
spreading code.
a) Encode ‘1’ as ‘+1’ and ‘0’ as ‘-1’ User 1> R1 1111 000

Mobile Network & Wireless Communication4
Secure Best Marks with AI Grader
Need help grading? Try our AI Grader for instant feedback on your assignments.

Mobile Network & Wireless Communication5
Q3. This is an incredibly quick network that links Australia's science and education population to
the public Internet, the global education and research population, and other selected Australian
information and services. AARNet's connectivity facilitates interconnections with international
education and science networking networks between Australian universities and organizations,
typically between 10 and 100 gigabits per second, via ultra-high-speed cables. This network
Q3. This is an incredibly quick network that links Australia's science and education population to
the public Internet, the global education and research population, and other selected Australian
information and services. AARNet's connectivity facilitates interconnections with international
education and science networking networks between Australian universities and organizations,
typically between 10 and 100 gigabits per second, via ultra-high-speed cables. This network

Mobile Network & Wireless Communication6
architecture offers high flexibility to satisfy the needs of in-depth study in various business and
technology fields. As a national network and an international network, AARNet is open.
AARNet provides 80 wavelengths, each with a national IP network of 100Gbps, routed across a
range of networks, and nationwide fiber communication capability.
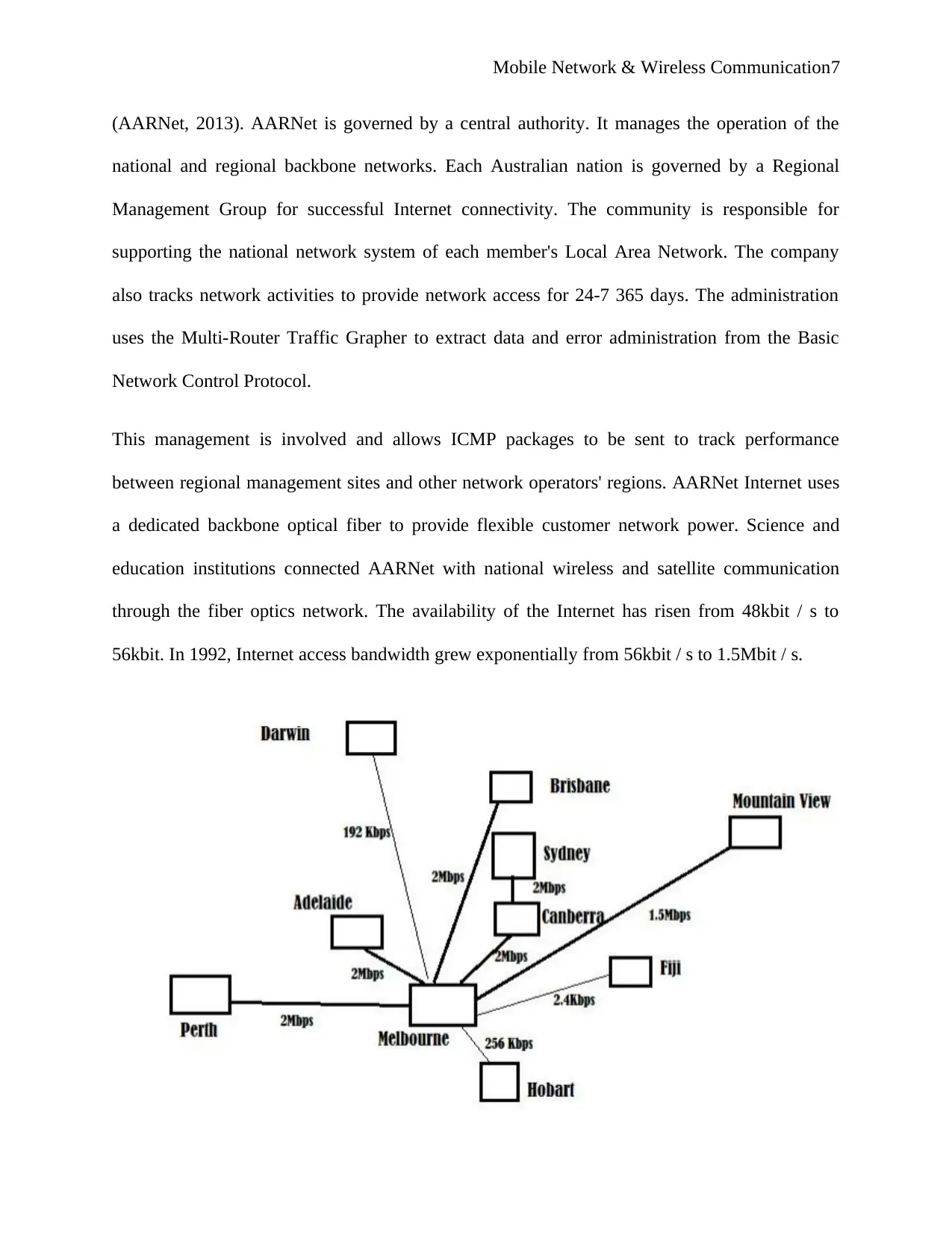
AARNet National Network
The network stretches from Perth to Hobart, Cairns to Darwin, across the Australian continent. It
also has different geographical access points in all Australian cities, offering coverage in these
cities and providing significant network power for industrial, remote, and regional sections.
From Brisbane to Perth, this national network was built, and each link was 48kbit / s. The
relation proved to be a core at Melbourne University. This network was first created as a multi-
protocol network. The speed was later improved to 2 Mbps so that about 40.000 machines could
be wired to the AARNet. The national network collaborates with suppliers of internet
connectivity and other external content distributors to improve network capacity and
performance. Customers are supported over an extensive backbone network capability of 1 to
10Gbit / s, with up to 1Gbit / s Ethernet access, and WiFi enabled.
AARNet International
The network is highly capable of serving two continents: North America and Asia. This network
enables Australia's education and research ecosystems to interconnect with more than 120 other
global education and research networks. At 240 Gbit / s link capabilities, the regional backbone
network fiber communication functions at six interconnections in North America and Singapore.
AARNet is currently running a regional backbone on three continents: North America, Europe,
and Asia. The network runs in 120Gbit / s in North America, linking 5Gbit / s to Asia globally
architecture offers high flexibility to satisfy the needs of in-depth study in various business and
technology fields. As a national network and an international network, AARNet is open.
AARNet provides 80 wavelengths, each with a national IP network of 100Gbps, routed across a
range of networks, and nationwide fiber communication capability.
AARNet National Network
The network stretches from Perth to Hobart, Cairns to Darwin, across the Australian continent. It
also has different geographical access points in all Australian cities, offering coverage in these
cities and providing significant network power for industrial, remote, and regional sections.
From Brisbane to Perth, this national network was built, and each link was 48kbit / s. The
relation proved to be a core at Melbourne University. This network was first created as a multi-
protocol network. The speed was later improved to 2 Mbps so that about 40.000 machines could
be wired to the AARNet. The national network collaborates with suppliers of internet
connectivity and other external content distributors to improve network capacity and
performance. Customers are supported over an extensive backbone network capability of 1 to
10Gbit / s, with up to 1Gbit / s Ethernet access, and WiFi enabled.
AARNet International
The network is highly capable of serving two continents: North America and Asia. This network
enables Australia's education and research ecosystems to interconnect with more than 120 other
global education and research networks. At 240 Gbit / s link capabilities, the regional backbone
network fiber communication functions at six interconnections in North America and Singapore.
AARNet is currently running a regional backbone on three continents: North America, Europe,
and Asia. The network runs in 120Gbit / s in North America, linking 5Gbit / s to Asia globally
Mobile Network & Wireless Communication7
(AARNet, 2013). AARNet is governed by a central authority. It manages the operation of the
national and regional backbone networks. Each Australian nation is governed by a Regional
Management Group for successful Internet connectivity. The community is responsible for
supporting the national network system of each member's Local Area Network. The company
also tracks network activities to provide network access for 24-7 365 days. The administration
uses the Multi-Router Traffic Grapher to extract data and error administration from the Basic
Network Control Protocol.
This management is involved and allows ICMP packages to be sent to track performance
between regional management sites and other network operators' regions. AARNet Internet uses
a dedicated backbone optical fiber to provide flexible customer network power. Science and
education institutions connected AARNet with national wireless and satellite communication
through the fiber optics network. The availability of the Internet has risen from 48kbit / s to
56kbit. In 1992, Internet access bandwidth grew exponentially from 56kbit / s to 1.5Mbit / s.
(AARNet, 2013). AARNet is governed by a central authority. It manages the operation of the
national and regional backbone networks. Each Australian nation is governed by a Regional
Management Group for successful Internet connectivity. The community is responsible for
supporting the national network system of each member's Local Area Network. The company
also tracks network activities to provide network access for 24-7 365 days. The administration
uses the Multi-Router Traffic Grapher to extract data and error administration from the Basic
Network Control Protocol.
This management is involved and allows ICMP packages to be sent to track performance
between regional management sites and other network operators' regions. AARNet Internet uses
a dedicated backbone optical fiber to provide flexible customer network power. Science and
education institutions connected AARNet with national wireless and satellite communication
through the fiber optics network. The availability of the Internet has risen from 48kbit / s to
56kbit. In 1992, Internet access bandwidth grew exponentially from 56kbit / s to 1.5Mbit / s.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

Mobile Network & Wireless Communication8
4) Yes, Bluetooth is a staple in wireless technologies for short-distance data transmission. It
functions on radio UHF waves. The RSS cables were planned as a replacement. Introduced
Bluetooth 4 Low Energy (BLE) specification. This latest model is commonly used in IoT
because it ideally suits in this case with low power consumption. WiFi is the local mobile
networking technology for radio wireless radio based on IEEE standards 802.11. WiFi runs on
2.4Ghz and 5Ghz frequencies and normally operates longer than Bluetooth over long distances.
The New WiFi HaLow protocol was released in 2017. Produced explicitly for IoT, the energy
consumption and transmission range is smaller than previous standards, but not widely yet. The
Bluetooth range depends mostly on the hurdles, so it varies according to where you choose to use
it. BLE was meant to relay tiny data chunks (Kemp et al., 2019). This makes it ideally suited for
the transition of lightweight measurements from sensors, for example, numeric values. BLE can
supply only around one Mbps of bandwidth. Classic Bluetooth is 2-3 times quicker. Even weaker
WiFi protocols, like HaLow, can transmit data up to 347 Mbps, and higher data over 1.3 Gbps
can be sent. WiFi is also ideal for intense data transfers such as images, images, etc.There are
also several Bluetooth modules, and the default range is limited. It's usually around 40 to 400 m.
However, you can again conceive of modules with an extended range of 1000 m (Kemp et al.,
2019).
The typical 2.4 GHz wireless routers are generally up to 45 meters indoors and 92 meters
outdoors. 5 GHz WiFi is more resistant than 2.4 GHz to obstructions. However, WiFi HaLow,
intended to travel long distances, runs on a sub1 GHz frequency and can travel up to 1 km.
Bluetooth had historically had significant security bugs, but more modern requirements
overcame most. In most cases, the highest protection practices are also not being enforced, but a
connection can be protected with the right configuration. On the other hand, WiFi has
4) Yes, Bluetooth is a staple in wireless technologies for short-distance data transmission. It
functions on radio UHF waves. The RSS cables were planned as a replacement. Introduced
Bluetooth 4 Low Energy (BLE) specification. This latest model is commonly used in IoT
because it ideally suits in this case with low power consumption. WiFi is the local mobile
networking technology for radio wireless radio based on IEEE standards 802.11. WiFi runs on
2.4Ghz and 5Ghz frequencies and normally operates longer than Bluetooth over long distances.
The New WiFi HaLow protocol was released in 2017. Produced explicitly for IoT, the energy
consumption and transmission range is smaller than previous standards, but not widely yet. The
Bluetooth range depends mostly on the hurdles, so it varies according to where you choose to use
it. BLE was meant to relay tiny data chunks (Kemp et al., 2019). This makes it ideally suited for
the transition of lightweight measurements from sensors, for example, numeric values. BLE can
supply only around one Mbps of bandwidth. Classic Bluetooth is 2-3 times quicker. Even weaker
WiFi protocols, like HaLow, can transmit data up to 347 Mbps, and higher data over 1.3 Gbps
can be sent. WiFi is also ideal for intense data transfers such as images, images, etc.There are
also several Bluetooth modules, and the default range is limited. It's usually around 40 to 400 m.
However, you can again conceive of modules with an extended range of 1000 m (Kemp et al.,
2019).
The typical 2.4 GHz wireless routers are generally up to 45 meters indoors and 92 meters
outdoors. 5 GHz WiFi is more resistant than 2.4 GHz to obstructions. However, WiFi HaLow,
intended to travel long distances, runs on a sub1 GHz frequency and can travel up to 1 km.
Bluetooth had historically had significant security bugs, but more modern requirements
overcame most. In most cases, the highest protection practices are also not being enforced, but a
connection can be protected with the right configuration. On the other hand, WiFi has
Mobile Network & Wireless Communication9
historically been concerned with stability, so it established the WEP, WPA, WPA2, and WPA3
protection protocols. The current encryption protocol, WPA3, is preferable. In most cases,
setting Bluetooth link protection is reasonable, but if your data is highly sensitive and you want
extra security, then tries using WiFi (Yu, et al., 2016).
Part B – Scanning Wireless Access Points
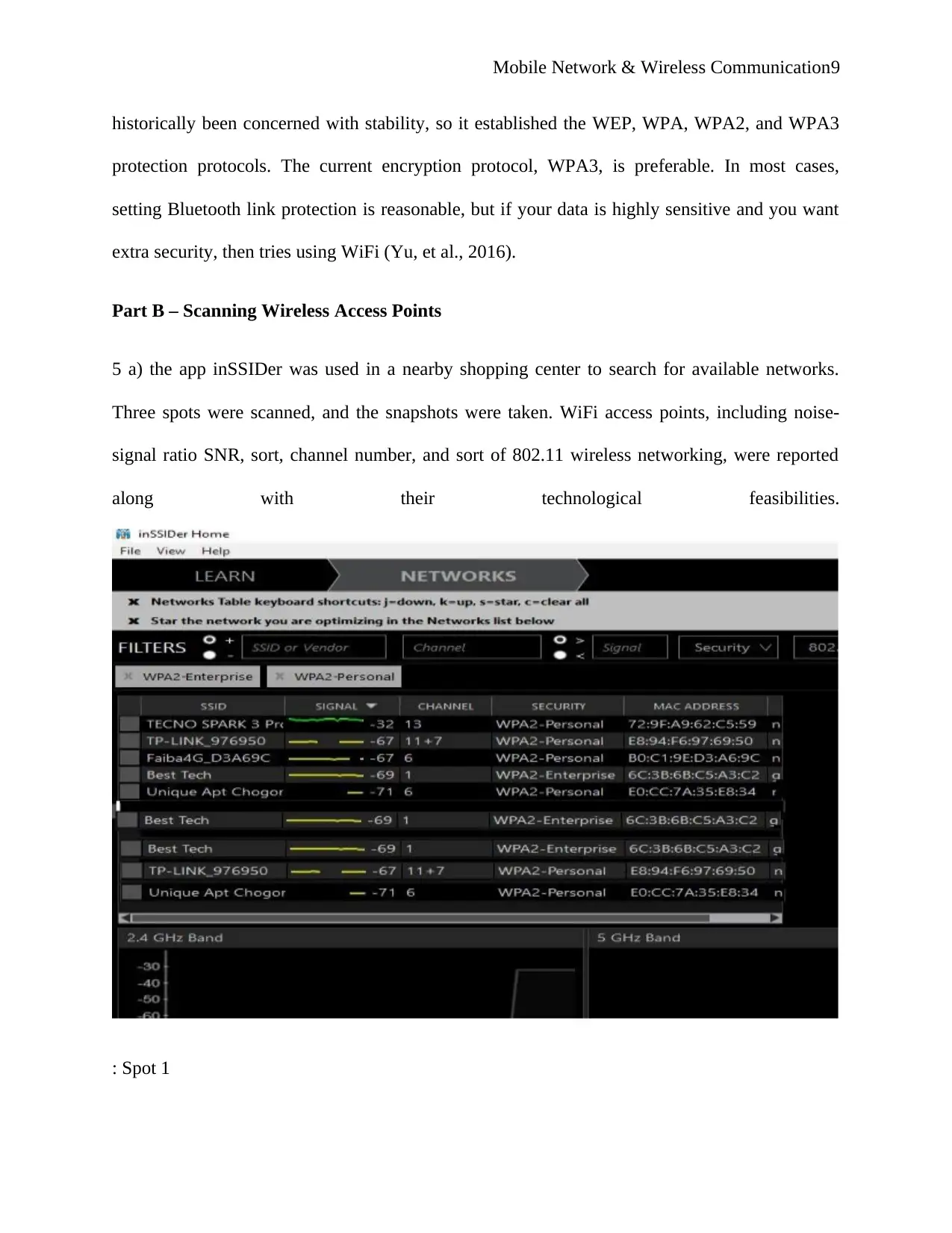
5 a) the app inSSIDer was used in a nearby shopping center to search for available networks.
Three spots were scanned, and the snapshots were taken. WiFi access points, including noise-
signal ratio SNR, sort, channel number, and sort of 802.11 wireless networking, were reported
along with their technological feasibilities.
: Spot 1
historically been concerned with stability, so it established the WEP, WPA, WPA2, and WPA3
protection protocols. The current encryption protocol, WPA3, is preferable. In most cases,
setting Bluetooth link protection is reasonable, but if your data is highly sensitive and you want
extra security, then tries using WiFi (Yu, et al., 2016).
Part B – Scanning Wireless Access Points
5 a) the app inSSIDer was used in a nearby shopping center to search for available networks.
Three spots were scanned, and the snapshots were taken. WiFi access points, including noise-
signal ratio SNR, sort, channel number, and sort of 802.11 wireless networking, were reported
along with their technological feasibilities.
: Spot 1
Mobile Network & Wireless Communication10
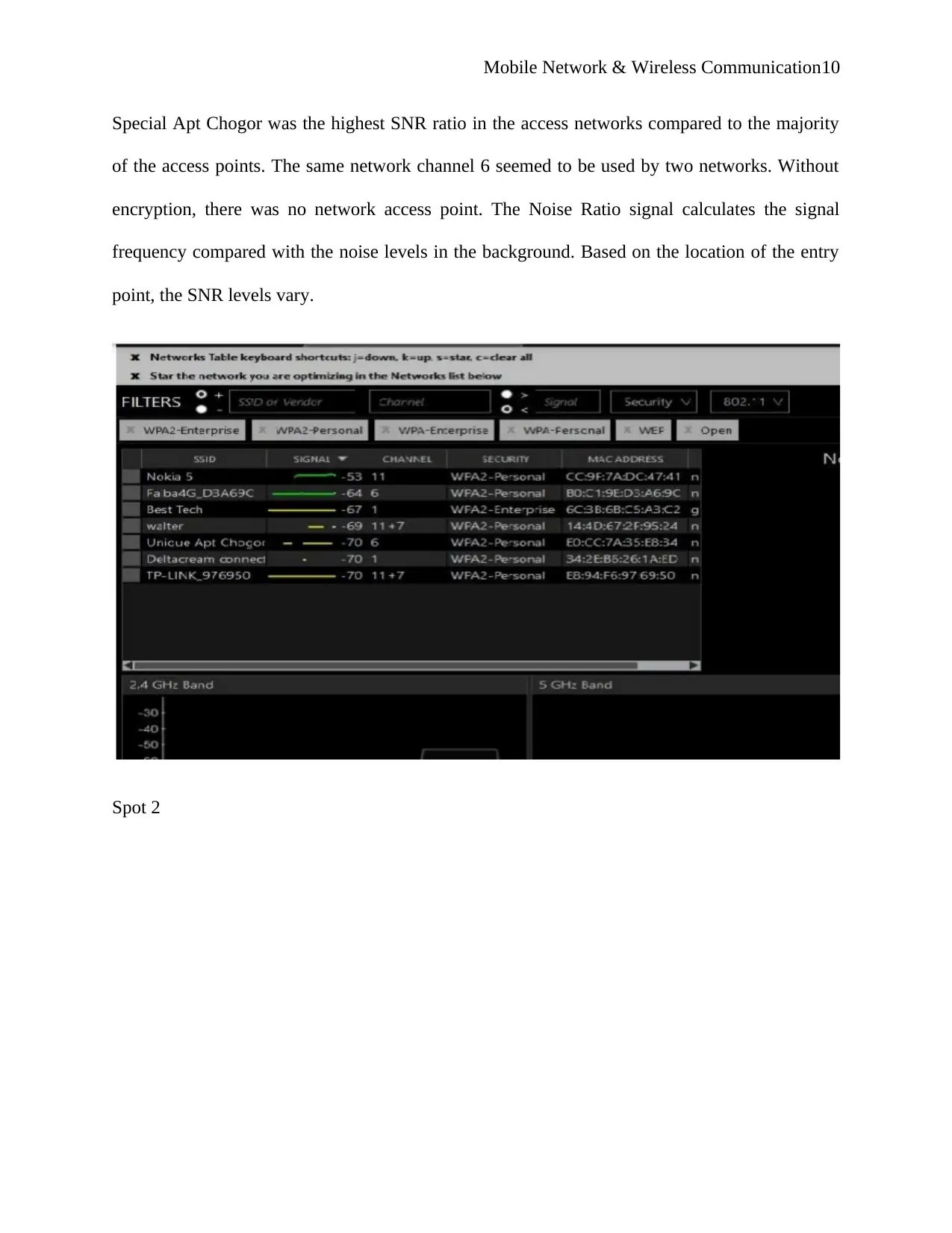
Special Apt Chogor was the highest SNR ratio in the access networks compared to the majority
of the access points. The same network channel 6 seemed to be used by two networks. Without
encryption, there was no network access point. The Noise Ratio signal calculates the signal
frequency compared with the noise levels in the background. Based on the location of the entry
point, the SNR levels vary.
Spot 2
Special Apt Chogor was the highest SNR ratio in the access networks compared to the majority
of the access points. The same network channel 6 seemed to be used by two networks. Without
encryption, there was no network access point. The Noise Ratio signal calculates the signal
frequency compared with the noise levels in the background. Based on the location of the entry
point, the SNR levels vary.
Spot 2
Secure Best Marks with AI Grader
Need help grading? Try our AI Grader for instant feedback on your assignments.
Mobile Network & Wireless Communication11
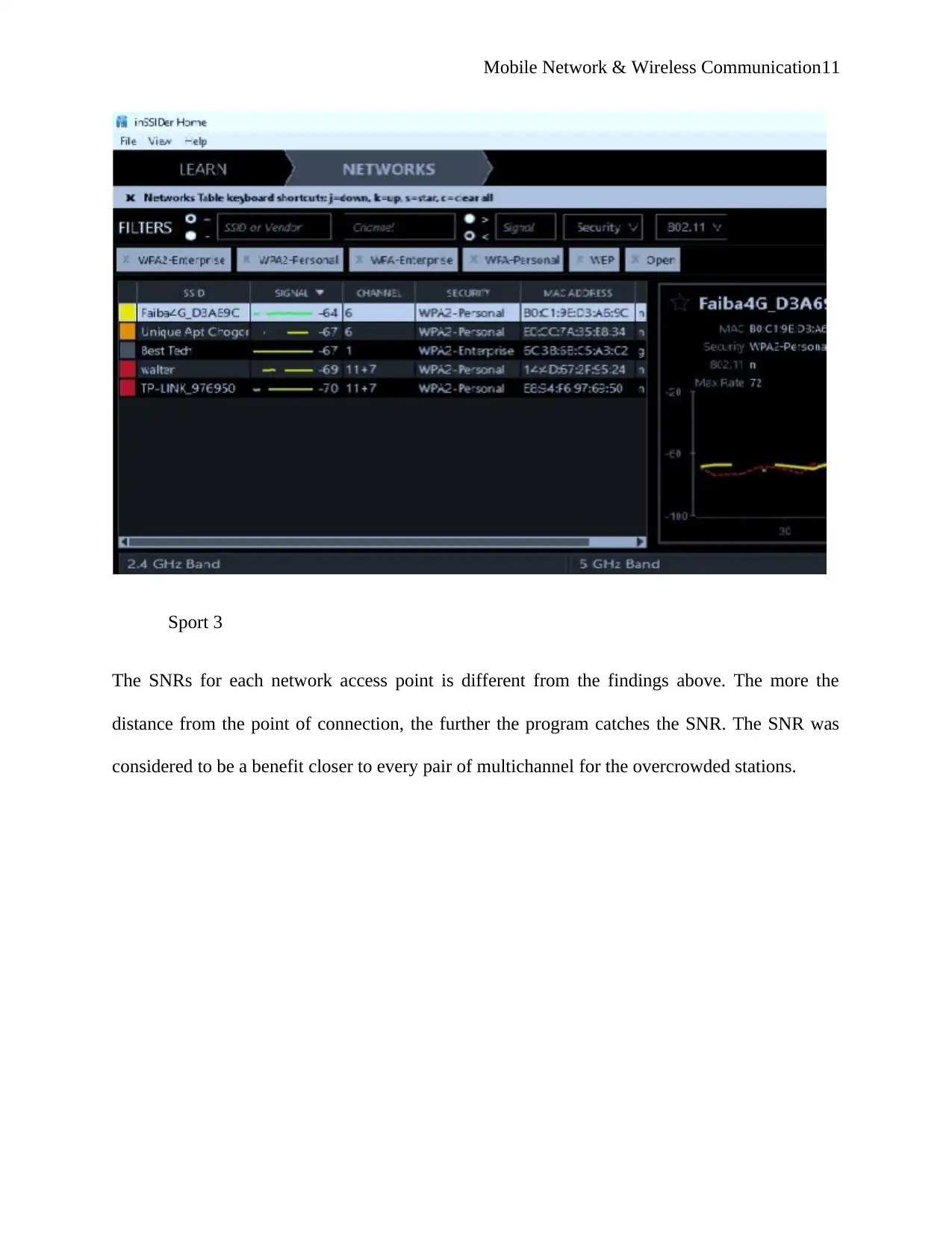
Sport 3
The SNRs for each network access point is different from the findings above. The more the
distance from the point of connection, the further the program catches the SNR. The SNR was
considered to be a benefit closer to every pair of multichannel for the overcrowded stations.
Sport 3
The SNRs for each network access point is different from the findings above. The more the
distance from the point of connection, the further the program catches the SNR. The SNR was
considered to be a benefit closer to every pair of multichannel for the overcrowded stations.
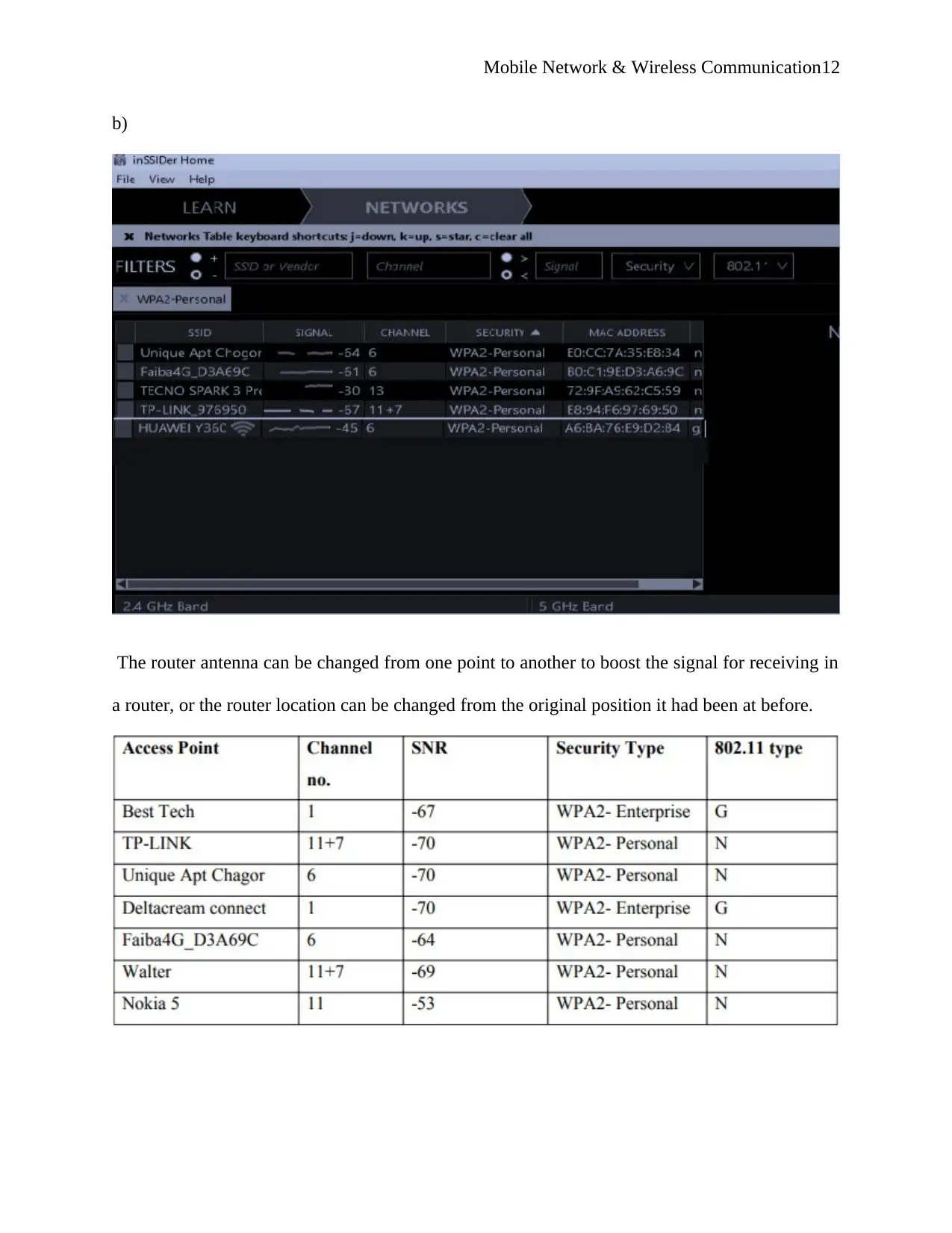
Mobile Network & Wireless Communication12
b)
The router antenna can be changed from one point to another to boost the signal for receiving in
a router, or the router location can be changed from the original position it had been at before.
b)
The router antenna can be changed from one point to another to boost the signal for receiving in
a router, or the router location can be changed from the original position it had been at before.

Mobile Network & Wireless Communication13
Reference List
AARNet. (2013). AARNet Annual Reports
Dibaei, M. and Ghaffari, A., 2020. Full-duplex medium access control protocols in wireless
networks: a survey. Wireless Networks, pp.1-19.
Yu, M. and Ansari, N., 2016. Smart grid communications. Journal of Network and Computer
Applications, 59(C), pp.247-249.
Kemp, C., Aben, G., Ip, A. and Mason, I., 2019, January. Working towards a cross-disciplinary
National FAIR Research Data Infrastructure. In Geophysical Research Abstracts (Vol. 21).
Reference List
AARNet. (2013). AARNet Annual Reports
Dibaei, M. and Ghaffari, A., 2020. Full-duplex medium access control protocols in wireless
networks: a survey. Wireless Networks, pp.1-19.
Yu, M. and Ansari, N., 2016. Smart grid communications. Journal of Network and Computer
Applications, 59(C), pp.247-249.
Kemp, C., Aben, G., Ip, A. and Mason, I., 2019, January. Working towards a cross-disciplinary
National FAIR Research Data Infrastructure. In Geophysical Research Abstracts (Vol. 21).
1 out of 13
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
© 2024 | Zucol Services PVT LTD | All rights reserved.




