COCS71152 - Operating System Security: Mobile Security Best Practices
VerifiedAdded on 2023/06/13
|10
|2449
|490
Report
AI Summary
This research report highlights the critical need for mobile operating system security and privacy to protect confidential information from unauthorized access. It examines various mobile operating systems, including iOS and Android, and discusses essential security practices and policies for system developers. The report identifies security-level issues that can disrupt mobile OS applications, investigates security tools and policies for mitigation, and reviews industry standards. It also touches upon social, ethical, and legal considerations related to mobile OS security, emphasizing the importance of credential password usage, cryptography support, and antivirus software to safeguard against external threats and data breaches. The document concludes with recommendations for enhancing mobile operating system security.

Running head: OPERATING SYSTEM SECURITY
Operating System Security: Best security practices for securing mobile operating systems
Name of the student:
Name of the university:
Operating System Security: Best security practices for securing mobile operating systems
Name of the student:
Name of the university:
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

1OPERATING SYSTEM SECURITY
Introduction
This research report depicts the crucial necessity of security and privacy of mobile
operating system to keep the confidential information secured from unauthenticated externals.
Mobile operating system has high level build in security characteristics which can significantly
minimize the impact and frequency of the application security level issues. This particular
system is designed and modeled to ensure that the users can build the security app along with the
default system as well as the file permission. It helps to avoid different difficult decisions about
the operating system security. Besides
1.1 Aim
The aim of the research report is to identify different high level security and privacy
practices those are necessary for the OS developers to consider before its final application.
Different security tools and technologies are there that may help to avoid system threats, attack
trends and related statistics. Another aim of the research report is to identify the social, ethical
and legal issues associated to Mobile operating system.
1.2 Objectives
To identify all security level issues that may interrupt the running application of
mobile operating system
To investigate the security tools and policies those are helpful to mitigate the
operational issues of mobile OS
To examine and discuss all related standard industry level practices
Introduction
This research report depicts the crucial necessity of security and privacy of mobile
operating system to keep the confidential information secured from unauthenticated externals.
Mobile operating system has high level build in security characteristics which can significantly
minimize the impact and frequency of the application security level issues. This particular
system is designed and modeled to ensure that the users can build the security app along with the
default system as well as the file permission. It helps to avoid different difficult decisions about
the operating system security. Besides
1.1 Aim
The aim of the research report is to identify different high level security and privacy
practices those are necessary for the OS developers to consider before its final application.
Different security tools and technologies are there that may help to avoid system threats, attack
trends and related statistics. Another aim of the research report is to identify the social, ethical
and legal issues associated to Mobile operating system.
1.2 Objectives
To identify all security level issues that may interrupt the running application of
mobile operating system
To investigate the security tools and policies those are helpful to mitigate the
operational issues of mobile OS
To examine and discuss all related standard industry level practices

2OPERATING SYSTEM SECURITY
2. Best security practices for securing mobile operating systems
2.1 Different Mobile Operating systems
Based on the model details and application level features of the mobile phones the best
suited Mobile Operating Systems (OS) is considered. Among the available mobile operating
systems some of the OS are elaborated below:
iOS: Only for the Apple devices such as iphone this iOS operating system is used. Over
last few years the market share of the iOS is growing rapidly and reached up to 16% (Mutchler et
al. 2015). The iOS operating system is consists of core OS, core services and media. The service
of iOS is comprises of high level framework that are used for the graphics, videotechnologies
etc.
Android: Google and Open Handset alliance has combiningly developed the Android
operating system. The market usability implies that android is the second widely used OS that is
comprises of Linux Kernel, using C and C++ coding open source Library, application framework
(Turland et al. 2015).
Apart from iOS and Android, windows blackberry OS are used for windows phone and
blackberry mobile phones respectively (Chen et al. 2016). Security is the most important aspect
that has to be considered for any mobile device to keep their data secured from the external
attackers.
2.2 Different security practices for securing mobile operating systems
In order to secure the mobile operating system, different security practices and policies
are available in the market those are strictly needed to be adopted and maintained by the system
developers. According to Abirami and Venkataraman (2016), it has already been established
2. Best security practices for securing mobile operating systems
2.1 Different Mobile Operating systems
Based on the model details and application level features of the mobile phones the best
suited Mobile Operating Systems (OS) is considered. Among the available mobile operating
systems some of the OS are elaborated below:
iOS: Only for the Apple devices such as iphone this iOS operating system is used. Over
last few years the market share of the iOS is growing rapidly and reached up to 16% (Mutchler et
al. 2015). The iOS operating system is consists of core OS, core services and media. The service
of iOS is comprises of high level framework that are used for the graphics, videotechnologies
etc.
Android: Google and Open Handset alliance has combiningly developed the Android
operating system. The market usability implies that android is the second widely used OS that is
comprises of Linux Kernel, using C and C++ coding open source Library, application framework
(Turland et al. 2015).
Apart from iOS and Android, windows blackberry OS are used for windows phone and
blackberry mobile phones respectively (Chen et al. 2016). Security is the most important aspect
that has to be considered for any mobile device to keep their data secured from the external
attackers.
2.2 Different security practices for securing mobile operating systems
In order to secure the mobile operating system, different security practices and policies
are available in the market those are strictly needed to be adopted and maintained by the system
developers. According to Abirami and Venkataraman (2016), it has already been established
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

3OPERATING SYSTEM SECURITY
that, Smartphone requires good security software to fight against the battle of array of hacks and
flaws. Due to cybercrime rather StageFright the reputation of mobile operating systems is
getting damaged each day (Xu et al. 2017). As android phone is open sourced and in this
operating system the developers can utilize different complex C ++ programming or JAVA also
as a result the cyber criminals can easily insert the malicious codes to the application. Mainly for
the malware this is referred to as one of the massive targets. Talha, Alper and Aydin (2015),
stated that, over 96% of malware targeted android are reported in the last 2 to 3 years over 24
million of apps attack.
The Android Operating System fails to develop automatic alert for any highlighted issue.
With the technical development in the business areas the Smartphones have become widely used
tools for successful web access. As a result the users are avoiding incorporating IT to their
source of technical leadership. This is all done because Mobile phones give cutting edge
technologies (Harris and Patten 2014). The user of the mobile phones look for consumer focused
vendors who are catering to their personal requirements.
2.3 Other standards to consider
Mostly for fraudulent and unethical hackers the Smartphones are becoming the most
attractive targets because of the combination of increasing ownership of the Smartphones and
usage of different valuable data services with the devices. Regardless of the type of the
Smartphones, proper even best of the security practices are required to be adopted by the
developers (Islam 2014). Security practices are intended to assist the business for taking the
necessary phases required to use the best security practice for the users of the mobile devices.
The best levels of security practices for mobile devices are as follows:
that, Smartphone requires good security software to fight against the battle of array of hacks and
flaws. Due to cybercrime rather StageFright the reputation of mobile operating systems is
getting damaged each day (Xu et al. 2017). As android phone is open sourced and in this
operating system the developers can utilize different complex C ++ programming or JAVA also
as a result the cyber criminals can easily insert the malicious codes to the application. Mainly for
the malware this is referred to as one of the massive targets. Talha, Alper and Aydin (2015),
stated that, over 96% of malware targeted android are reported in the last 2 to 3 years over 24
million of apps attack.
The Android Operating System fails to develop automatic alert for any highlighted issue.
With the technical development in the business areas the Smartphones have become widely used
tools for successful web access. As a result the users are avoiding incorporating IT to their
source of technical leadership. This is all done because Mobile phones give cutting edge
technologies (Harris and Patten 2014). The user of the mobile phones look for consumer focused
vendors who are catering to their personal requirements.
2.3 Other standards to consider
Mostly for fraudulent and unethical hackers the Smartphones are becoming the most
attractive targets because of the combination of increasing ownership of the Smartphones and
usage of different valuable data services with the devices. Regardless of the type of the
Smartphones, proper even best of the security practices are required to be adopted by the
developers (Islam 2014). Security practices are intended to assist the business for taking the
necessary phases required to use the best security practice for the users of the mobile devices.
The best levels of security practices for mobile devices are as follows:
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

4OPERATING SYSTEM SECURITY
Choosing Mobile devices: While question raise regarding security of Smartphones, it
can be said that, all the devices are not created considering similar types of security approaches.
Ipods are developed for the general consumers thus; it is less focused on security (Shahzad
2014). On the other hand, the blackberry operating system is much focused on its operational
security because it is mainly designed for the enterprises users like law enforcement, android and
apple Smartphones. Device access is the most important component that has to be considered.
Proper authentication should be implemented to make sure that only the authorized users are
capable to access the device and its operational applications (Roesner, Kohno and Molnar 2014).
Professional setup of the operating system is the most import thing that has to be considered to
protect the mobile device from unauthorized access.
Mobile app update: Whenever update is required the mobile devices gives notification
for the requirement (Shin et al. 2014). Whereas there are certain phones which enable the users
to set up phones in a way so that it can update the application automatically. It allows the users to
get a secured and updated mobile device.
Installation of antimalware and necessary application software: Each day new
malwares attacks are getting exploited in the android and iOS application. Like other software
the antivirus software are needed to be updated accordingly. For any employee or mobile phone
user the software update should be considered as a compulsory or mandatory one (Sajid, Abbas
and Saleem 2016). Sometimes the mobile devices are found to be connected with office data
server also. Thus, accurate software update is require keeping both the office server and mobile
data protected from the external attackers.
Communication should be encrypted: In the current technology era, wireless
communication has become the most widely used application for communication. It is found that
Choosing Mobile devices: While question raise regarding security of Smartphones, it
can be said that, all the devices are not created considering similar types of security approaches.
Ipods are developed for the general consumers thus; it is less focused on security (Shahzad
2014). On the other hand, the blackberry operating system is much focused on its operational
security because it is mainly designed for the enterprises users like law enforcement, android and
apple Smartphones. Device access is the most important component that has to be considered.
Proper authentication should be implemented to make sure that only the authorized users are
capable to access the device and its operational applications (Roesner, Kohno and Molnar 2014).
Professional setup of the operating system is the most import thing that has to be considered to
protect the mobile device from unauthorized access.
Mobile app update: Whenever update is required the mobile devices gives notification
for the requirement (Shin et al. 2014). Whereas there are certain phones which enable the users
to set up phones in a way so that it can update the application automatically. It allows the users to
get a secured and updated mobile device.
Installation of antimalware and necessary application software: Each day new
malwares attacks are getting exploited in the android and iOS application. Like other software
the antivirus software are needed to be updated accordingly. For any employee or mobile phone
user the software update should be considered as a compulsory or mandatory one (Sajid, Abbas
and Saleem 2016). Sometimes the mobile devices are found to be connected with office data
server also. Thus, accurate software update is require keeping both the office server and mobile
data protected from the external attackers.
Communication should be encrypted: In the current technology era, wireless
communication has become the most widely used application for communication. It is found that
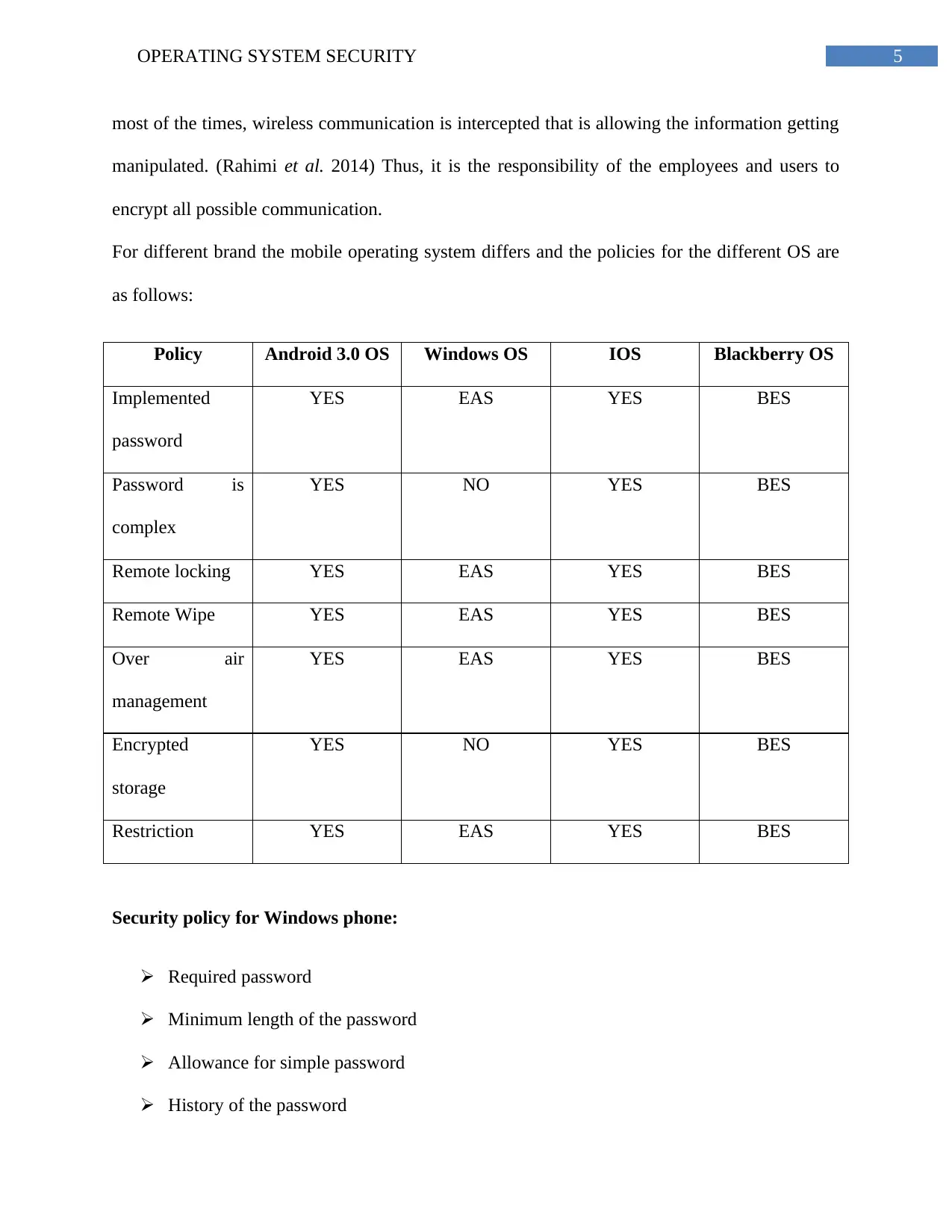
5OPERATING SYSTEM SECURITY
most of the times, wireless communication is intercepted that is allowing the information getting
manipulated. (Rahimi et al. 2014) Thus, it is the responsibility of the employees and users to
encrypt all possible communication.
For different brand the mobile operating system differs and the policies for the different OS are
as follows:
Policy Android 3.0 OS Windows OS IOS Blackberry OS
Implemented
password
YES EAS YES BES
Password is
complex
YES NO YES BES
Remote locking YES EAS YES BES
Remote Wipe YES EAS YES BES
Over air
management
YES EAS YES BES
Encrypted
storage
YES NO YES BES
Restriction YES EAS YES BES
Security policy for Windows phone:
Required password
Minimum length of the password
Allowance for simple password
History of the password
most of the times, wireless communication is intercepted that is allowing the information getting
manipulated. (Rahimi et al. 2014) Thus, it is the responsibility of the employees and users to
encrypt all possible communication.
For different brand the mobile operating system differs and the policies for the different OS are
as follows:
Policy Android 3.0 OS Windows OS IOS Blackberry OS
Implemented
password
YES EAS YES BES
Password is
complex
YES NO YES BES
Remote locking YES EAS YES BES
Remote Wipe YES EAS YES BES
Over air
management
YES EAS YES BES
Encrypted
storage
YES NO YES BES
Restriction YES EAS YES BES
Security policy for Windows phone:
Required password
Minimum length of the password
Allowance for simple password
History of the password
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

6OPERATING SYSTEM SECURITY
For the iOS operating system the policies are as follows:
Pass-code needed
Allowance for simple values
Length of the pass-code
Length of the pass-code
Maximum age for the pass-code
The policy for android (3.0) phone:
Complex password is needed
In password minimum number of letter are needed
Minimum letters and lowercase letters
Requirement for storage encryption
Conclusion
From the overall discussion it can be concluded that, in this current age of technology,
each of the mobile operating system supports different kinds of policies and practices
enforcement. Thus, this is the responsibility of the consumers to choose the most suitable OS that
has to be deployed. OS helps the users to run all necessary application in the mobile devices
with proper security and privacy. Any particular Mobile app can become a profitable business
only when it is an embedded operating system that is researching the EOS. Companies those are
dependent on rugged operating devices helps to run windows embedded operating system which
needs to consider their next step for supporting the business. Moreover it can be said that with
the help of mobile operating system the issues of traditional business can be eventually reduced
For the iOS operating system the policies are as follows:
Pass-code needed
Allowance for simple values
Length of the pass-code
Length of the pass-code
Maximum age for the pass-code
The policy for android (3.0) phone:
Complex password is needed
In password minimum number of letter are needed
Minimum letters and lowercase letters
Requirement for storage encryption
Conclusion
From the overall discussion it can be concluded that, in this current age of technology,
each of the mobile operating system supports different kinds of policies and practices
enforcement. Thus, this is the responsibility of the consumers to choose the most suitable OS that
has to be deployed. OS helps the users to run all necessary application in the mobile devices
with proper security and privacy. Any particular Mobile app can become a profitable business
only when it is an embedded operating system that is researching the EOS. Companies those are
dependent on rugged operating devices helps to run windows embedded operating system which
needs to consider their next step for supporting the business. Moreover it can be said that with
the help of mobile operating system the issues of traditional business can be eventually reduced
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

7OPERATING SYSTEM SECURITY
and minimized accordingly. In order to secure the mobile operating system certain mandatory
recommendations are needed to be followed by and the recommendations for the research are
elaborated below:
Recommendations
Credential password usage: In order to secure the mobile operating system from the
external assaults it is necessary for the users to develop credential password so that the no
unauthenticated users can access the information from the OS platform.
Cryptography support: It is necessary for the developers to incorporate proper
cryptographic support to encode confidential information. With accurate cryptography key
generation only the authenticated users will be able to decrypt the data whenever required.
However during the application of the cryptography algorithm potential function and condition
are also required to be considered.
Antivirus software: In order to avoid all unwanted file corruption and data hijack proper
antivirus is required to be applied to the mobile operating system.
and minimized accordingly. In order to secure the mobile operating system certain mandatory
recommendations are needed to be followed by and the recommendations for the research are
elaborated below:
Recommendations
Credential password usage: In order to secure the mobile operating system from the
external assaults it is necessary for the users to develop credential password so that the no
unauthenticated users can access the information from the OS platform.
Cryptography support: It is necessary for the developers to incorporate proper
cryptographic support to encode confidential information. With accurate cryptography key
generation only the authenticated users will be able to decrypt the data whenever required.
However during the application of the cryptography algorithm potential function and condition
are also required to be considered.
Antivirus software: In order to avoid all unwanted file corruption and data hijack proper
antivirus is required to be applied to the mobile operating system.

8OPERATING SYSTEM SECURITY
References
Abirami, G. and Venkataraman, R., 2016. Access control policy on mobile operating system
frameworks–a survey. Indian Journal of Science and Technology, 9(48).
Chen, M., Qian, Y., Mao, S., Tang, W. and Yang, X., 2016. Software-defined mobile networks
security. Mobile Networks and Applications, 21(5), pp.729-743.
Harris, M. and P. Patten, K., 2014. Mobile device security considerations for small-and medium-
sized enterprise business mobility. Information Management & Computer Security, 22(1), pp.97-
114.
Islam, S., 2014. Systematic literature review: Security challenges of mobile banking and
payments system. International Journal of u-and e-Service, Science and Technology, 7(6),
pp.107-116.
Mutchler, P., Doupé, A., Mitchell, J., Kruegel, C. and Vigna, G., 2015, May. A large-scale study
of mobile web app security. In Proceedings of the Mobile Security Technologies Workshop
(MoST).
Rahimi, M.R., Ren, J., Liu, C.H., Vasilakos, A.V. and Venkatasubramanian, N., 2014. Mobile
cloud computing: A survey, state of art and future directions. Mobile Networks and
Applications, 19(2), pp.133-143.
Roesner, F., Kohno, T. and Molnar, D., 2014. Security and privacy for augmented reality
systems. Communications of the ACM, 57(4), pp.88-96.
Sajid, A., Abbas, H. and Saleem, K., 2016. Cloud-assisted iot-based scada systems security: A
review of the state of the art and future challenges. IEEE Access, 4, pp.1375-1384.
References
Abirami, G. and Venkataraman, R., 2016. Access control policy on mobile operating system
frameworks–a survey. Indian Journal of Science and Technology, 9(48).
Chen, M., Qian, Y., Mao, S., Tang, W. and Yang, X., 2016. Software-defined mobile networks
security. Mobile Networks and Applications, 21(5), pp.729-743.
Harris, M. and P. Patten, K., 2014. Mobile device security considerations for small-and medium-
sized enterprise business mobility. Information Management & Computer Security, 22(1), pp.97-
114.
Islam, S., 2014. Systematic literature review: Security challenges of mobile banking and
payments system. International Journal of u-and e-Service, Science and Technology, 7(6),
pp.107-116.
Mutchler, P., Doupé, A., Mitchell, J., Kruegel, C. and Vigna, G., 2015, May. A large-scale study
of mobile web app security. In Proceedings of the Mobile Security Technologies Workshop
(MoST).
Rahimi, M.R., Ren, J., Liu, C.H., Vasilakos, A.V. and Venkatasubramanian, N., 2014. Mobile
cloud computing: A survey, state of art and future directions. Mobile Networks and
Applications, 19(2), pp.133-143.
Roesner, F., Kohno, T. and Molnar, D., 2014. Security and privacy for augmented reality
systems. Communications of the ACM, 57(4), pp.88-96.
Sajid, A., Abbas, H. and Saleem, K., 2016. Cloud-assisted iot-based scada systems security: A
review of the state of the art and future challenges. IEEE Access, 4, pp.1375-1384.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

9OPERATING SYSTEM SECURITY
Schulz, T., Gladhorn, F. and Sæther, J.A., 2015. Best Practices for Creating Accessible Mobile
Applications. Report Norsk Regnesentral-Norwegian Computing Center, (1031), p.19.
Scott-Hayward, S., 2015, April. Design and deployment of secure, robust, and resilient SDN
Controllers. In Network Softwarization (NetSoft), 2015 1st IEEE Conference on (pp. 1-5). IEEE.
Shahzad, F., 2014. State-of-the-art survey on cloud computing security Challenges, approaches
and solutions. Procedia Computer Science, 37, pp.357-362.
Shin, S., Song, Y., Lee, T., Lee, S., Chung, J., Porras, P., Yegneswaran, V., Noh, J. and Kang,
B.B., 2014, November. Rosemary: A robust, secure, and high-performance network operating
system. In Proceedings of the 2014 ACM SIGSAC conference on computer and communications
security (pp. 78-89). ACM.
Slavin, R., Wang, X., Hosseini, M.B., Hester, J., Krishnan, R., Bhatia, J., Breaux, T.D. and Niu,
J., 2016, May. Toward a framework for detecting privacy policy violations in android application
code. In Proceedings of the 38th International Conference on Software Engineering (pp. 25-36).
ACM.
Talha, K.A., Alper, D.I. and Aydin, C., 2015. APK Auditor: Permission-based Android malware
detection system. Digital Investigation, 13, pp.1-14.
Turland, J., Coventry, L., Jeske, D., Briggs, P. and van Moorsel, A., 2015, July. Nudging
towards security: Developing an application for wireless network selection for android phones.
In Proceedings of the 2015 British HCI conference(pp. 193-201). ACM.
Xu, Y., Hunt, T., Kwon, Y., Georgiev, M., Shmatikov, V. and Witchel, E., 2017. EARP:
Principled Storage, Sharing, and Protection for Mobile Apps. GetMobile: Mobile Computing and
Communications, 20(3), pp.29-33.
Schulz, T., Gladhorn, F. and Sæther, J.A., 2015. Best Practices for Creating Accessible Mobile
Applications. Report Norsk Regnesentral-Norwegian Computing Center, (1031), p.19.
Scott-Hayward, S., 2015, April. Design and deployment of secure, robust, and resilient SDN
Controllers. In Network Softwarization (NetSoft), 2015 1st IEEE Conference on (pp. 1-5). IEEE.
Shahzad, F., 2014. State-of-the-art survey on cloud computing security Challenges, approaches
and solutions. Procedia Computer Science, 37, pp.357-362.
Shin, S., Song, Y., Lee, T., Lee, S., Chung, J., Porras, P., Yegneswaran, V., Noh, J. and Kang,
B.B., 2014, November. Rosemary: A robust, secure, and high-performance network operating
system. In Proceedings of the 2014 ACM SIGSAC conference on computer and communications
security (pp. 78-89). ACM.
Slavin, R., Wang, X., Hosseini, M.B., Hester, J., Krishnan, R., Bhatia, J., Breaux, T.D. and Niu,
J., 2016, May. Toward a framework for detecting privacy policy violations in android application
code. In Proceedings of the 38th International Conference on Software Engineering (pp. 25-36).
ACM.
Talha, K.A., Alper, D.I. and Aydin, C., 2015. APK Auditor: Permission-based Android malware
detection system. Digital Investigation, 13, pp.1-14.
Turland, J., Coventry, L., Jeske, D., Briggs, P. and van Moorsel, A., 2015, July. Nudging
towards security: Developing an application for wireless network selection for android phones.
In Proceedings of the 2015 British HCI conference(pp. 193-201). ACM.
Xu, Y., Hunt, T., Kwon, Y., Georgiev, M., Shmatikov, V. and Witchel, E., 2017. EARP:
Principled Storage, Sharing, and Protection for Mobile Apps. GetMobile: Mobile Computing and
Communications, 20(3), pp.29-33.
1 out of 10
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.





