Mobile Payment Techniques Analysis
VerifiedAdded on 2020/05/08
|6
|1097
|70
AI Summary
This assignment delves into the intricacies of mobile payment techniques, focusing on the inherent security and privacy issues associated with this burgeoning technology. It analyzes various risks stemming from both traditional and emerging threats, exploring their impact on different stakeholders within the mobile payment ecosystem. The document proposes practical recommendations for mitigating these risks, emphasizing the importance of stakeholder collaboration, robust security measures, and clear regulatory frameworks.
Contribute Materials
Your contribution can guide someone’s learning journey. Share your
documents today.

RUNNING HEAD: MOBILE PAYMENT TECHNIQUES 1
MOBILE PAYMENT TECHNIQUES
Student Name
Institute Name
MOBILE PAYMENT TECHNIQUES
Student Name
Institute Name
Secure Best Marks with AI Grader
Need help grading? Try our AI Grader for instant feedback on your assignments.

MOBILE PAYMENT TECHNIQUES 2
Contents
Introduction................................................................................................................................3
Analyses of the issues................................................................................................................3
Security and privacy issues for the mobile payment..................................................................3
Cause of issues...........................................................................................................................4
Recommendations......................................................................................................................4
Reference....................................................................................................................................6
Contents
Introduction................................................................................................................................3
Analyses of the issues................................................................................................................3
Security and privacy issues for the mobile payment..................................................................3
Cause of issues...........................................................................................................................4
Recommendations......................................................................................................................4
Reference....................................................................................................................................6
MOBILE PAYMENT TECHNIQUES 3
Introduction
In the current time, mobile devices have completely transformed the business and day to day
life in the field of interaction. In addition to it has also changed the way financial transaction
of all kind are made (Suo et al, 2013). The concept of mobile devices specifically mobile
phones is in usage widely and customers are becoming increasingly popular with maximum
usage of mobile phones for many motives like secure financial transactions of all kinds that
are made. Mobile devices specifically mobile phone is in huge usage as well and customers
are becoming more and more familiar with usage of mobile phones for many motives like
safe or secure financial transactions through web banking websites.
Analyses of the issues
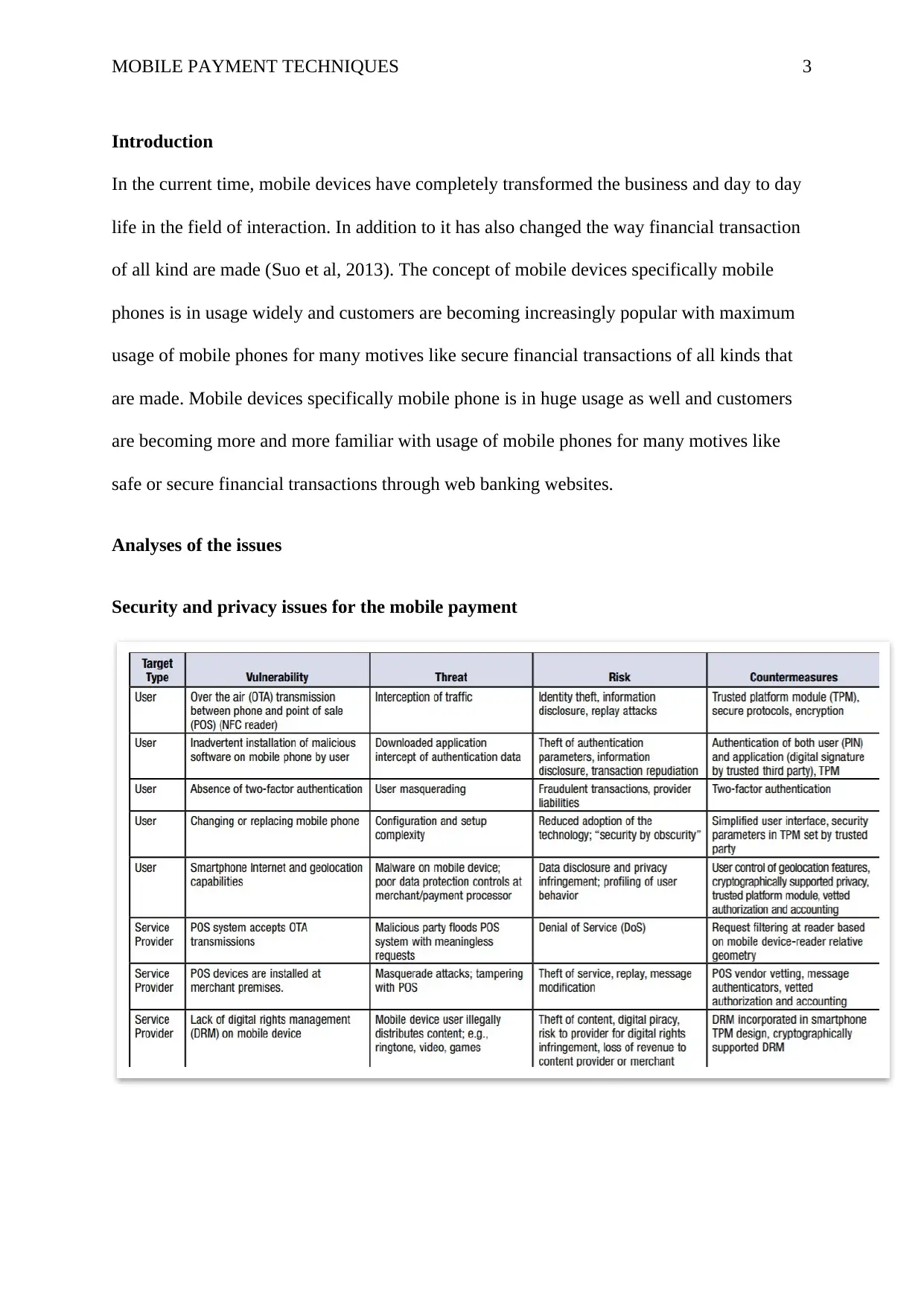
Security and privacy issues for the mobile payment
Introduction
In the current time, mobile devices have completely transformed the business and day to day
life in the field of interaction. In addition to it has also changed the way financial transaction
of all kind are made (Suo et al, 2013). The concept of mobile devices specifically mobile
phones is in usage widely and customers are becoming increasingly popular with maximum
usage of mobile phones for many motives like secure financial transactions of all kinds that
are made. Mobile devices specifically mobile phone is in huge usage as well and customers
are becoming more and more familiar with usage of mobile phones for many motives like
safe or secure financial transactions through web banking websites.
Analyses of the issues
Security and privacy issues for the mobile payment

MOBILE PAYMENT TECHNIQUES 4
Cause of issues
While looking at the history, there are many fraudsters that have targeting many kinds of
payment vehicles and this is likely to be the main case for mobile payments. Thus, the
concept which is upfront and based on counter measures are required to mitigate the overall
risk of the double-edged techniques. There are number of risks from mobile payment
approach that can be divided since it is emerging or traditional by approach (Thakur &
Srivastava, 2014). There is a lot of traditional risk based on denial as well as theft of loss
associated with revenue, reputation of brand and consumer base whereas there is emerging
risk also based on the usage of mobile payments like money laundering and terrorist
associated funding. Therefore, the most widely spread present execution is the bank based
NFC model and the emerging risk current is completely out of scope of the current paper.
The concept of money laundering as well as terrorist risks mitigating approaches with a
source of information from different studies (Slade et al, 2015). Risk associated with the
participants in the current mobile payment ecosystem completely depend on the current role
of the user based entity, network as well as communication provider or payment service
providers. There are some entities like MNOs that can play two of the discussed role side by
side (Yang et al, 2015).
Recommendations
1. It is very important to carefully play and include all the stakeholders along with
procedure and techniques consisting, the option that exists to make security as an
intrinsic component of all kind of mobile payment systems. The financial, payment as
well as network based service provider should execute the right kind of safeguards as
well as privacy and security governance programs. It also lacks clear set of
regulations that should not be utilised by the company as an excuse for not being
active (Arvidsson, 2014). There is risk from misusing or by authorizing the user like
Cause of issues
While looking at the history, there are many fraudsters that have targeting many kinds of
payment vehicles and this is likely to be the main case for mobile payments. Thus, the
concept which is upfront and based on counter measures are required to mitigate the overall
risk of the double-edged techniques. There are number of risks from mobile payment
approach that can be divided since it is emerging or traditional by approach (Thakur &
Srivastava, 2014). There is a lot of traditional risk based on denial as well as theft of loss
associated with revenue, reputation of brand and consumer base whereas there is emerging
risk also based on the usage of mobile payments like money laundering and terrorist
associated funding. Therefore, the most widely spread present execution is the bank based
NFC model and the emerging risk current is completely out of scope of the current paper.
The concept of money laundering as well as terrorist risks mitigating approaches with a
source of information from different studies (Slade et al, 2015). Risk associated with the
participants in the current mobile payment ecosystem completely depend on the current role
of the user based entity, network as well as communication provider or payment service
providers. There are some entities like MNOs that can play two of the discussed role side by
side (Yang et al, 2015).
Recommendations
1. It is very important to carefully play and include all the stakeholders along with
procedure and techniques consisting, the option that exists to make security as an
intrinsic component of all kind of mobile payment systems. The financial, payment as
well as network based service provider should execute the right kind of safeguards as
well as privacy and security governance programs. It also lacks clear set of
regulations that should not be utilised by the company as an excuse for not being
active (Arvidsson, 2014). There is risk from misusing or by authorizing the user like
Secure Best Marks with AI Grader
Need help grading? Try our AI Grader for instant feedback on your assignments.

MOBILE PAYMENT TECHNIQUES 5
money laundering and threat of illegal usage. The latter area can need support from
various new set of laws that will evolve to make sure right kind of protection. Every
organization consist of a chain of work based data that must be put in place for a
strong and positive control to save such while it is in the custody.
2. One main concern is making sure that the transaction must be undertaken is most
likely being carried by the person who is authorized to carry it out. Usage of the two-
factor authentication will further help in contributing to have a more effective kind of
identity to save for the consumers and high identity based assurance for the merchant
(Dinh et al, 2013). It is also a case of bank based NFC work and saving or protecting
from the transactions that originate from many unauthorised users can be achieved by
using dynamic card verification values and CVVs.
3. Another crucial factor that can be considered in the current data classification during
the transmission as well as storing of the data at many nodes. Companies must also
recognize the data which is also considered sensitive and should make sure that right
methods are in place. In addition, in case of financial data, it is valuable time to
consider the matter of data integrity also (Morosan & DeFranco, 2016).
money laundering and threat of illegal usage. The latter area can need support from
various new set of laws that will evolve to make sure right kind of protection. Every
organization consist of a chain of work based data that must be put in place for a
strong and positive control to save such while it is in the custody.
2. One main concern is making sure that the transaction must be undertaken is most
likely being carried by the person who is authorized to carry it out. Usage of the two-
factor authentication will further help in contributing to have a more effective kind of
identity to save for the consumers and high identity based assurance for the merchant
(Dinh et al, 2013). It is also a case of bank based NFC work and saving or protecting
from the transactions that originate from many unauthorised users can be achieved by
using dynamic card verification values and CVVs.
3. Another crucial factor that can be considered in the current data classification during
the transmission as well as storing of the data at many nodes. Companies must also
recognize the data which is also considered sensitive and should make sure that right
methods are in place. In addition, in case of financial data, it is valuable time to
consider the matter of data integrity also (Morosan & DeFranco, 2016).

MOBILE PAYMENT TECHNIQUES 6
Reference
Arvidsson, N. (2014). Consumer attitudes on mobile payment services–results from a proof
of concept test. International Journal of Bank Marketing, 32(2), 150-170.
Dinh, H. T., Lee, C., Niyato, D., & Wang, P. (2013). A survey of mobile cloud computing:
architecture, applications, and approaches. Wireless communications and mobile
computing, 13(18), 1587-1611.
Morosan, C., & DeFranco, A. (2016). It's about time: Revisiting UTAUT2 to examine
consumers’ intentions to use NFC mobile payments in hotels. International Journal
of Hospitality Management, 53, 17-29.
Slade, E. L., Dwivedi, Y. K., Piercy, N. C., & Williams, M. D. (2015). Modeling consumers’
adoption intentions of remote mobile payments in the United Kingdom: extending
UTAUT with innovativeness, risk, and trust. Psychology & Marketing, 32(8), 860-
873.
Suo, H., Liu, Z., Wan, J., & Zhou, K. (2013, July). Security and privacy in mobile cloud
computing. In Wireless Communications and Mobile Computing Conference
(IWCMC), 2013 9th International (pp. 655-659). IEEE.
Thakur, R., & Srivastava, M. (2014). Adoption readiness, personal innovativeness, perceived
risk and usage intention across customer groups for mobile payment services in
India. Internet Research, 24(3), 369-392.
Yang, Y., Liu, Y., Li, H., & Yu, B. (2015). Understanding perceived risks in mobile payment
acceptance. Industrial Management & Data Systems, 115(2), 253-269.
Reference
Arvidsson, N. (2014). Consumer attitudes on mobile payment services–results from a proof
of concept test. International Journal of Bank Marketing, 32(2), 150-170.
Dinh, H. T., Lee, C., Niyato, D., & Wang, P. (2013). A survey of mobile cloud computing:
architecture, applications, and approaches. Wireless communications and mobile
computing, 13(18), 1587-1611.
Morosan, C., & DeFranco, A. (2016). It's about time: Revisiting UTAUT2 to examine
consumers’ intentions to use NFC mobile payments in hotels. International Journal
of Hospitality Management, 53, 17-29.
Slade, E. L., Dwivedi, Y. K., Piercy, N. C., & Williams, M. D. (2015). Modeling consumers’
adoption intentions of remote mobile payments in the United Kingdom: extending
UTAUT with innovativeness, risk, and trust. Psychology & Marketing, 32(8), 860-
873.
Suo, H., Liu, Z., Wan, J., & Zhou, K. (2013, July). Security and privacy in mobile cloud
computing. In Wireless Communications and Mobile Computing Conference
(IWCMC), 2013 9th International (pp. 655-659). IEEE.
Thakur, R., & Srivastava, M. (2014). Adoption readiness, personal innovativeness, perceived
risk and usage intention across customer groups for mobile payment services in
India. Internet Research, 24(3), 369-392.
Yang, Y., Liu, Y., Li, H., & Yu, B. (2015). Understanding perceived risks in mobile payment
acceptance. Industrial Management & Data Systems, 115(2), 253-269.
1 out of 6
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
© 2024 | Zucol Services PVT LTD | All rights reserved.





