Analysis of Mobile Phone Security: User Behavior and Security Measures
VerifiedAdded on 2023/04/21
|17
|3756
|495
Report
AI Summary
This report investigates mobile phone usage and security practices among 502 participants. The study, employing a descriptive design, reveals that screen lock is the most popular security measure, while asset registers are the least. Data was collected through questionnaires assessing online time and security implementations. Results indicate a gap between internet usage and security consciousness, highlighting the need for enhanced measures like anti-malware software and strong passwords. The findings suggest that while users employ basic security features, more robust methods are underutilized, emphasizing the importance of educating users on comprehensive mobile security strategies to protect against theft, data loss, and hacking.

1/1/2019
Mobile phone security
Mobile phone security
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

Table of Contents
Abstract.......................................................................................................................................................1
Introduction.................................................................................................................................................1
Methods......................................................................................................................................................2
Sample.....................................................................................................................................................2
Procedure and materials.........................................................................................................................3
Study Design............................................................................................................................................3
Data analysis............................................................................................................................................4
Results.........................................................................................................................................................4
Descriptive statistics................................................................................................................................4
Hours spent online..............................................................................................................................4
Mobile security measures....................................................................................................................5
Discussion....................................................................................................................................................8
Conclusion.................................................................................................................................................10
References.................................................................................................................................................11
Abstract.......................................................................................................................................................1
Introduction.................................................................................................................................................1
Methods......................................................................................................................................................2
Sample.....................................................................................................................................................2
Procedure and materials.........................................................................................................................3
Study Design............................................................................................................................................3
Data analysis............................................................................................................................................4
Results.........................................................................................................................................................4
Descriptive statistics................................................................................................................................4
Hours spent online..............................................................................................................................4
Mobile security measures....................................................................................................................5
Discussion....................................................................................................................................................8
Conclusion.................................................................................................................................................10
References.................................................................................................................................................11

P a g e | 1
Abstract
Purpose: To investigate the frequency of mobile phone use and the extent to which individuals
have secured their mobile devices against such security threats.
Methods: 502 participants were admitted into the study. They were randomly assigned to one of
the three questionnaires; Questionnaire 1 involving the last week, Questionnaire 2 involving a
typical week and Questionnaire 3 involving a typical month.
Results: It was shown that screen lock is the most popular measure of enhancing mobile security
and asset registers are the least popular.
Conclusion: Several measures ought to be taken in order to enhance mobile phone device
security. Among the measures necessary for enhancing mobile phone security include
installation of anti-spam and anti-malware software and use of strong passwords and pins for
locking of phone screens and applications.
Introduction
There has been an observed increase in dependence on mobile phones by both individuals and
organizations. Securing of data contained in these mobile devices has turned out to be one of the
basic roles of the device users (Wang, 2015). However, the security for these gadgets has been in
the past not treated as of prime importance. On average, just about 10 per cent of the estimated
85 million mobile devices being used today are secured (de los Reyes, 2011). Cell phone devices
are viewed as being vulnerable to theft, loss and hacking due to several reasons such as the small
sizes and daily use and interaction of these devices (Hoffner, 2015).
The securing of these cell phones for both individual and business use has turned into a
continuous hot catch subject in the news, however very little research has been carried out on the
Abstract
Purpose: To investigate the frequency of mobile phone use and the extent to which individuals
have secured their mobile devices against such security threats.
Methods: 502 participants were admitted into the study. They were randomly assigned to one of
the three questionnaires; Questionnaire 1 involving the last week, Questionnaire 2 involving a
typical week and Questionnaire 3 involving a typical month.
Results: It was shown that screen lock is the most popular measure of enhancing mobile security
and asset registers are the least popular.
Conclusion: Several measures ought to be taken in order to enhance mobile phone device
security. Among the measures necessary for enhancing mobile phone security include
installation of anti-spam and anti-malware software and use of strong passwords and pins for
locking of phone screens and applications.
Introduction
There has been an observed increase in dependence on mobile phones by both individuals and
organizations. Securing of data contained in these mobile devices has turned out to be one of the
basic roles of the device users (Wang, 2015). However, the security for these gadgets has been in
the past not treated as of prime importance. On average, just about 10 per cent of the estimated
85 million mobile devices being used today are secured (de los Reyes, 2011). Cell phone devices
are viewed as being vulnerable to theft, loss and hacking due to several reasons such as the small
sizes and daily use and interaction of these devices (Hoffner, 2015).
The securing of these cell phones for both individual and business use has turned into a
continuous hot catch subject in the news, however very little research has been carried out on the
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

P a g e | 2
best way to take care of this issue (van Niekerk, 2010). Of more interest, Android security has
been a topic of discussion due to the rise in the number of these devices over the recent past
(Mutholib, 2013).The rise in the manufacture of these gadgets has come with threats such as
theft, data loss and hacking (Furnell, 2014).
Owing to the increased mobile insecurity (theft and hacking) the present study investigates the
frequency of mobile phone use and the extent to which individuals have secured their mobile
devices against such security threats. Potential threats to mobile phones include but are not
limited to;
i. Data leakage as a result of device loss or theft (Jeon, 2014).
ii. Surveillance attacks (Wu, 2014).
iii. Congestion on mobile networks (Nseir, 2013).
iv. Mobile malware and spyware attacks.
This study was motivated by the fact that many people use a lot of time on the internet or other
interfaces of their mobile phones but do not apply stringent measures towards securing their
devices, yet a lot of information exists in the internet on how to secure their gadgets (Wang,
2015).
Methods
Sample
Data was obtained from a sample of 502 individuals, of whom 269 were female representing
53.6 per cent and 231 were male representing 46.0 per cent. 2 participants representing 0.4 % did
best way to take care of this issue (van Niekerk, 2010). Of more interest, Android security has
been a topic of discussion due to the rise in the number of these devices over the recent past
(Mutholib, 2013).The rise in the manufacture of these gadgets has come with threats such as
theft, data loss and hacking (Furnell, 2014).
Owing to the increased mobile insecurity (theft and hacking) the present study investigates the
frequency of mobile phone use and the extent to which individuals have secured their mobile
devices against such security threats. Potential threats to mobile phones include but are not
limited to;
i. Data leakage as a result of device loss or theft (Jeon, 2014).
ii. Surveillance attacks (Wu, 2014).
iii. Congestion on mobile networks (Nseir, 2013).
iv. Mobile malware and spyware attacks.
This study was motivated by the fact that many people use a lot of time on the internet or other
interfaces of their mobile phones but do not apply stringent measures towards securing their
devices, yet a lot of information exists in the internet on how to secure their gadgets (Wang,
2015).
Methods
Sample
Data was obtained from a sample of 502 individuals, of whom 269 were female representing
53.6 per cent and 231 were male representing 46.0 per cent. 2 participants representing 0.4 % did
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

P a g e | 3
not respond on their gender. The participants’’ mean age was 25.45 years and the age standard
deviation was 8.615.
Of the 502 surveyed participants, 169 representing 33.7 per cent provided responses to
questionnaire a, 170 representing 33.9 per cent responded to questionnaire b and 163
representing 32.5 per cent responded to questionnaire c.
Procedure and materials
The study recruited respondents into the survey. Those who joined the survey were randomly
assigned to one of three questionnaires. They provided responses on their demographic
characteristics (age and gender). The respondents then provided responses to the written survey
questions. For purposes of this study, we investigate the level of mobile phone security among
mobile phone users and therefore we shall base emphasis only on question five which is
presented;
5. Which of the following security measures have you taken for your mobile phone? Please tick
all that apply.
The question consisted of the following six answers;
Recorded phone serial number Used screen lock code or pattern Used biometric lock (i.e. fingerprint or FaceID) Registered phone on an asset register Installed app to track or lock phone remotely (e.g. Find My iPhone, Android Device
Manager) Physically marked phone
not respond on their gender. The participants’’ mean age was 25.45 years and the age standard
deviation was 8.615.
Of the 502 surveyed participants, 169 representing 33.7 per cent provided responses to
questionnaire a, 170 representing 33.9 per cent responded to questionnaire b and 163
representing 32.5 per cent responded to questionnaire c.
Procedure and materials
The study recruited respondents into the survey. Those who joined the survey were randomly
assigned to one of three questionnaires. They provided responses on their demographic
characteristics (age and gender). The respondents then provided responses to the written survey
questions. For purposes of this study, we investigate the level of mobile phone security among
mobile phone users and therefore we shall base emphasis only on question five which is
presented;
5. Which of the following security measures have you taken for your mobile phone? Please tick
all that apply.
The question consisted of the following six answers;
Recorded phone serial number Used screen lock code or pattern Used biometric lock (i.e. fingerprint or FaceID) Registered phone on an asset register Installed app to track or lock phone remotely (e.g. Find My iPhone, Android Device
Manager) Physically marked phone
P a g e | 4
Study Design
The study employed a descriptive study design as we aim to describe the level of mobile security
among mobile phone users.
Data analysis
Data was analyzed for both descriptive and inferential statistics. Frequencies and bar graphs were
used for describing the variables of interest and regression analysis was used for analyzing the
effect of hours spent online on mobile security measures.
Data was exported from MS Excel into IBM SPSS for analysis.
Results
Descriptive statistics
Hours spent online
Generally, it was found that those who participated in questionnaires a spent about 25.272 hours
online on average and with a standard deviation of 17.2285 in the last week.
Those who took part in the survey involving questionnaire b spent about 24.145 hours online on
average and with a standard deviation of 15.1527 in a typical week.
Those who took part in questionnaire c responded to an average of 98.349 hours online in a
typical month and a standard deviation of 108.6248.
Descriptive Statistics
Questionnaire version N Minimum Maximum Mean Std. Deviation
a Q3 - Hours online
(questionnaires a & b
only)
167 1.0 90.0 25.272 17.2285
Q3 - Hours online
(questionnaire c only) 1 180.0 180.0 180.000 .
Valid N (listwise) 0
Study Design
The study employed a descriptive study design as we aim to describe the level of mobile security
among mobile phone users.
Data analysis
Data was analyzed for both descriptive and inferential statistics. Frequencies and bar graphs were
used for describing the variables of interest and regression analysis was used for analyzing the
effect of hours spent online on mobile security measures.
Data was exported from MS Excel into IBM SPSS for analysis.
Results
Descriptive statistics
Hours spent online
Generally, it was found that those who participated in questionnaires a spent about 25.272 hours
online on average and with a standard deviation of 17.2285 in the last week.
Those who took part in the survey involving questionnaire b spent about 24.145 hours online on
average and with a standard deviation of 15.1527 in a typical week.
Those who took part in questionnaire c responded to an average of 98.349 hours online in a
typical month and a standard deviation of 108.6248.
Descriptive Statistics
Questionnaire version N Minimum Maximum Mean Std. Deviation
a Q3 - Hours online
(questionnaires a & b
only)
167 1.0 90.0 25.272 17.2285
Q3 - Hours online
(questionnaire c only) 1 180.0 180.0 180.000 .
Valid N (listwise) 0
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
P a g e | 5
b Q3 - Hours online
(questionnaires a & b
only)
169 .0 100.0 24.145 15.1527
Q3 - Hours online
(questionnaire c only) 1 40.0 40.0 40.000 .
Valid N (listwise) 0
Descriptive Statistics
N Minimum Maximum Mean Std. Deviation
Q3 - Hours online
(questionnaire c only) 163 .0 1200.0 98.349 108.6248
Valid N (listwise) 163
Mobile security measures
The frequency of the mobile security measures as responded to by the survey participants are as
described below;
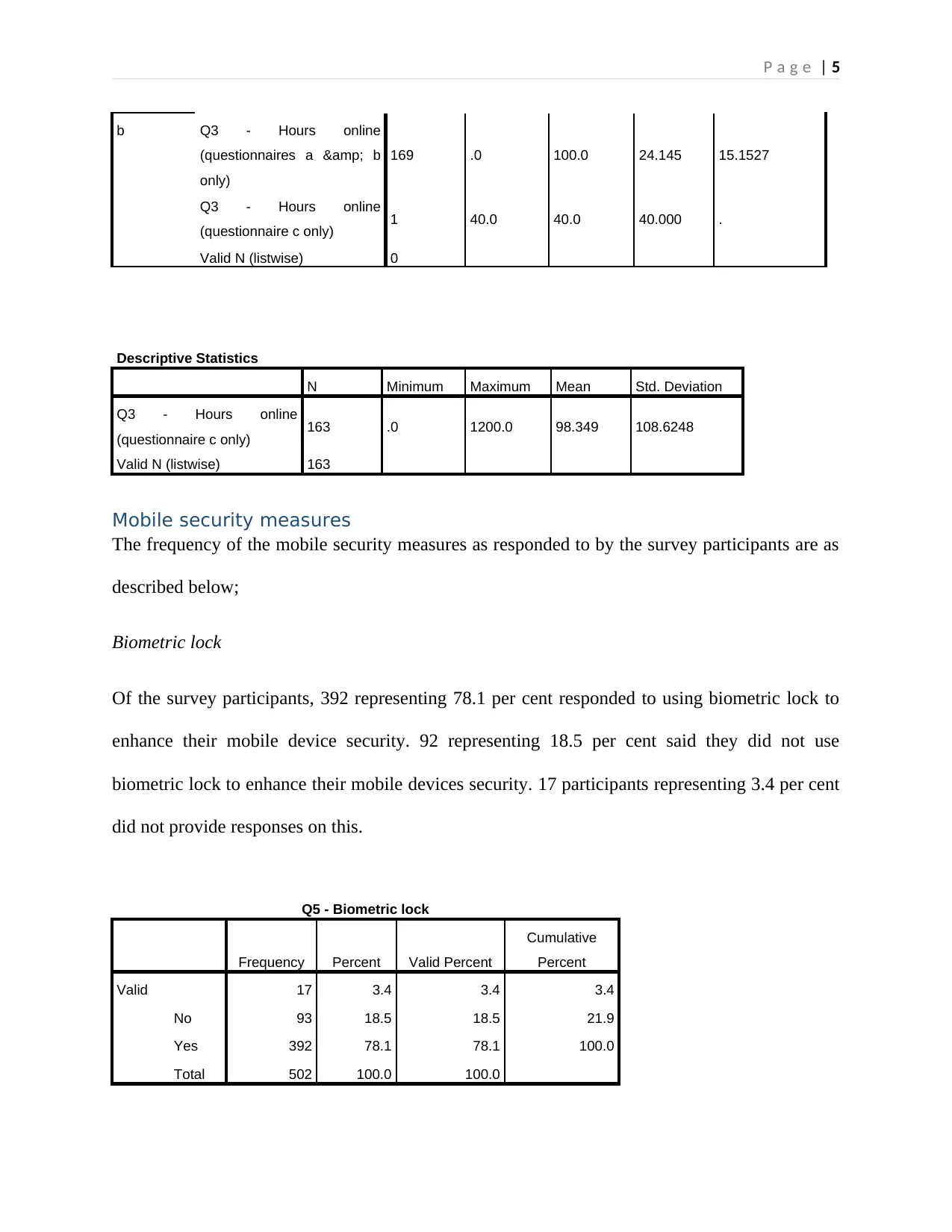
Biometric lock
Of the survey participants, 392 representing 78.1 per cent responded to using biometric lock to
enhance their mobile device security. 92 representing 18.5 per cent said they did not use
biometric lock to enhance their mobile devices security. 17 participants representing 3.4 per cent
did not provide responses on this.
Q5 - Biometric lock
Frequency Percent Valid Percent
Cumulative
Percent
Valid 17 3.4 3.4 3.4
No 93 18.5 18.5 21.9
Yes 392 78.1 78.1 100.0
Total 502 100.0 100.0
b Q3 - Hours online
(questionnaires a & b
only)
169 .0 100.0 24.145 15.1527
Q3 - Hours online
(questionnaire c only) 1 40.0 40.0 40.000 .
Valid N (listwise) 0
Descriptive Statistics
N Minimum Maximum Mean Std. Deviation
Q3 - Hours online
(questionnaire c only) 163 .0 1200.0 98.349 108.6248
Valid N (listwise) 163
Mobile security measures
The frequency of the mobile security measures as responded to by the survey participants are as
described below;
Biometric lock
Of the survey participants, 392 representing 78.1 per cent responded to using biometric lock to
enhance their mobile device security. 92 representing 18.5 per cent said they did not use
biometric lock to enhance their mobile devices security. 17 participants representing 3.4 per cent
did not provide responses on this.
Q5 - Biometric lock
Frequency Percent Valid Percent
Cumulative
Percent
Valid 17 3.4 3.4 3.4
No 93 18.5 18.5 21.9
Yes 392 78.1 78.1 100.0
Total 502 100.0 100.0
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
P a g e | 6
Asset register
11.6 per cent of the survey participants did not provide responses on this. However, 55
representing 11 per cent said that they used asset register to enhance their mobile phones’
security and 389 representing 77.5 per cent said that they did not use asset register to enhance
their devices security.
Q5 - Asset register
Frequency Percent Valid Percent
Cumulative
Percent
Valid 58 11.6 11.6 11.6
No 389 77.5 77.5 89.0
Yes 55 11.0 11.0 100.0
Total 502 100.0 100.0
Serial number
109 participants representing 21.7 per cent said that they used their device serial numbers to
enhance their mobile phone security. 341 participants representing 67.9 per cent did not use
serial number for enhancing the mobile phone security.
52 participants representing 10.4 per cent did not provide responses on this.
Asset register
11.6 per cent of the survey participants did not provide responses on this. However, 55
representing 11 per cent said that they used asset register to enhance their mobile phones’
security and 389 representing 77.5 per cent said that they did not use asset register to enhance
their devices security.
Q5 - Asset register
Frequency Percent Valid Percent
Cumulative
Percent
Valid 58 11.6 11.6 11.6
No 389 77.5 77.5 89.0
Yes 55 11.0 11.0 100.0
Total 502 100.0 100.0
Serial number
109 participants representing 21.7 per cent said that they used their device serial numbers to
enhance their mobile phone security. 341 participants representing 67.9 per cent did not use
serial number for enhancing the mobile phone security.
52 participants representing 10.4 per cent did not provide responses on this.
P a g e | 7
Q5 - Serial number
Frequency Percent Valid Percent
Cumulative
Percent
Valid 52 10.4 10.4 10.4
No 341 67.9 67.9 78.3
Yes 109 21.7 21.7 100.0
Total 502 100.0 100.0
Screen lock
464 participants representing 92.4% said that they used screen lock as a way of enhancing their
mobile phone security. 33 representing 6.6 per cent did not use screen lock as a way of ensuring
their mobile phone security. 5 participants representing 1% did not respond on this.
Q5 - Screen lock
Frequency Percent Valid Percent
Cumulative
Percent
Valid 5 1.0 1.0 1.0
No 33 6.6 6.6 7.6
Yes 464 92.4 92.4 100.0
Total 502 100.0 100.0
Tracking app
303 respondents representing 60.4 % said that they used tracking apps as a way of enhancing
their phone security while 166 representing 33.1 per cent did not use tracking apps as a way of
enhancing their mobile phone security. 33 participants representing 6.6 % did not respond on
this.
Q5 - Tracking app
Q5 - Serial number
Frequency Percent Valid Percent
Cumulative
Percent
Valid 52 10.4 10.4 10.4
No 341 67.9 67.9 78.3
Yes 109 21.7 21.7 100.0
Total 502 100.0 100.0
Screen lock
464 participants representing 92.4% said that they used screen lock as a way of enhancing their
mobile phone security. 33 representing 6.6 per cent did not use screen lock as a way of ensuring
their mobile phone security. 5 participants representing 1% did not respond on this.
Q5 - Screen lock
Frequency Percent Valid Percent
Cumulative
Percent
Valid 5 1.0 1.0 1.0
No 33 6.6 6.6 7.6
Yes 464 92.4 92.4 100.0
Total 502 100.0 100.0
Tracking app
303 respondents representing 60.4 % said that they used tracking apps as a way of enhancing
their phone security while 166 representing 33.1 per cent did not use tracking apps as a way of
enhancing their mobile phone security. 33 participants representing 6.6 % did not respond on
this.
Q5 - Tracking app
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
P a g e | 8
Frequency Percent Valid Percent
Cumulative
Percent
Valid 33 6.6 6.6 6.6
No 166 33.1 33.1 39.6
Yes 303 60.4 60.4 100.0
Total 502 100.0 100.0
Physical map
73 participants representing 14.5 per cent used physical map as a way of enhancing their mobile
phone security while 370 representing 73.7 % did not use physical map as a way of enhancing
the security of their mobile phone devices. 59 respondents representing 11.8 per cent did not
provide their responses on this.
Q5 - Physical mark
Frequency Percent Valid Percent
Cumulative
Percent
Valid 59 11.8 11.8 11.8
No 370 73.7 73.7 85.5
Yes 73 14.5 14.5 100.0
Total 502 100.0 100.0
From findings of the current study, of the methods used to enhance mobile phone security,
screen lock was the most popular with 92.4 per cent of the participants responding to using this
technique while asset register was the least popular with just 55 participants responding that they
used it as a way of enhancing their mobile phone device security. The findings agree with those
of (Zhang, 2013) who found out that the most common way through which people secure their
phone data against access from third party people was through locking their phone screens.
Frequency Percent Valid Percent
Cumulative
Percent
Valid 33 6.6 6.6 6.6
No 166 33.1 33.1 39.6
Yes 303 60.4 60.4 100.0
Total 502 100.0 100.0
Physical map
73 participants representing 14.5 per cent used physical map as a way of enhancing their mobile
phone security while 370 representing 73.7 % did not use physical map as a way of enhancing
the security of their mobile phone devices. 59 respondents representing 11.8 per cent did not
provide their responses on this.
Q5 - Physical mark
Frequency Percent Valid Percent
Cumulative
Percent
Valid 59 11.8 11.8 11.8
No 370 73.7 73.7 85.5
Yes 73 14.5 14.5 100.0
Total 502 100.0 100.0
From findings of the current study, of the methods used to enhance mobile phone security,
screen lock was the most popular with 92.4 per cent of the participants responding to using this
technique while asset register was the least popular with just 55 participants responding that they
used it as a way of enhancing their mobile phone device security. The findings agree with those
of (Zhang, 2013) who found out that the most common way through which people secure their
phone data against access from third party people was through locking their phone screens.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

P a g e | 9
Discussion
Results of the analysis have shown that different mobile security measures have different levels
of popularity. It has been shown that screen lock is the most favored mobile security measure,
followed by biometric lock, followed by tracking app, followed by serial number, followed by
physical map and the least popular security measure foe enhancing mobile phone device security
is asset register.
Screen lock is the most preferred method as it is easy to use and it is readily and easily accessible
from the settings menu. However, it is not a tight security measure as passwords, pin and
patterns could be easily mastered b third party persons (John Markoff, 2009).
Biometric lock is an advanced version of screen lock which involves use of body characteristics
such as fingerprint and eye visualization (Abhishek Nagar, 2010). For the phone to be unlocked,
the owner of the phone is the only authorized person to access unlock the phone. Third party
persons cannot be able to unlock the phone as each person’s bodily characteristics do differ
(Marc Ferrant, 2010).
A tracking app refers to a mobile application that can be used for locating lost or stolen devices
(Cleeff, 2009). The tracking app is a good security measure since when a change in mobile
phone sim cards is detected, the original owner is alerted on the current location and ownership
of the phone.
A mobile phone serial number refers to a unique number assigned to every device by the
manufacturer (Irmler, 2012). In case of phone loss or theft, the serial number can always be used
for determining the current ownership and location of the mobile phone.
Discussion
Results of the analysis have shown that different mobile security measures have different levels
of popularity. It has been shown that screen lock is the most favored mobile security measure,
followed by biometric lock, followed by tracking app, followed by serial number, followed by
physical map and the least popular security measure foe enhancing mobile phone device security
is asset register.
Screen lock is the most preferred method as it is easy to use and it is readily and easily accessible
from the settings menu. However, it is not a tight security measure as passwords, pin and
patterns could be easily mastered b third party persons (John Markoff, 2009).
Biometric lock is an advanced version of screen lock which involves use of body characteristics
such as fingerprint and eye visualization (Abhishek Nagar, 2010). For the phone to be unlocked,
the owner of the phone is the only authorized person to access unlock the phone. Third party
persons cannot be able to unlock the phone as each person’s bodily characteristics do differ
(Marc Ferrant, 2010).
A tracking app refers to a mobile application that can be used for locating lost or stolen devices
(Cleeff, 2009). The tracking app is a good security measure since when a change in mobile
phone sim cards is detected, the original owner is alerted on the current location and ownership
of the phone.
A mobile phone serial number refers to a unique number assigned to every device by the
manufacturer (Irmler, 2012). In case of phone loss or theft, the serial number can always be used
for determining the current ownership and location of the mobile phone.

P a g e | 10
Physical maps and asset register are not so much popular for enhancing mobile phone device
security as they are not easy to use as compared to the other methods of enhancing phone
security.
Conclusion
Owing to the fact that mobile security has become a pressing need for both organizations and
individuals, several measures ought to be put in place in order to enhance mobile phone security.
For organizations, they can expand versatile security by bringing together the engineering of the
system framework. They can bring together remote system, wired system and (VPNs) into one
concentrated system. Through this, organizations can easily and effectively screen their
communication and data systems. It will likewise enable them to identify danger to their system
quicker than if it was decentralized. They can perform execution test utilizing ethical hackers.
For individuals, they can enhance the security of their mobile phones by utilizing password
protection to unlock screens, changing of pins, passwords and patterns frequently, and avoiding
use of easily predicted passwords, pins and patterns. Further, users should make use of
antimalware, antispam and device personal firewall to minimize device vulnerability to theft,
hacking and attacks rom malware and spam. Installation of such software shall help fight against
mobile communication attacks. Phones should also be backed up to avoid loss of data and
regularly restored.
In today’s industries, mobile devices have helped provide a convenience in in maintaining and
securing their big data that need not exposed or lost. Threats are a potential hamper to big data
and can be avoided by implementing the above discussed measures.
Physical maps and asset register are not so much popular for enhancing mobile phone device
security as they are not easy to use as compared to the other methods of enhancing phone
security.
Conclusion
Owing to the fact that mobile security has become a pressing need for both organizations and
individuals, several measures ought to be put in place in order to enhance mobile phone security.
For organizations, they can expand versatile security by bringing together the engineering of the
system framework. They can bring together remote system, wired system and (VPNs) into one
concentrated system. Through this, organizations can easily and effectively screen their
communication and data systems. It will likewise enable them to identify danger to their system
quicker than if it was decentralized. They can perform execution test utilizing ethical hackers.
For individuals, they can enhance the security of their mobile phones by utilizing password
protection to unlock screens, changing of pins, passwords and patterns frequently, and avoiding
use of easily predicted passwords, pins and patterns. Further, users should make use of
antimalware, antispam and device personal firewall to minimize device vulnerability to theft,
hacking and attacks rom malware and spam. Installation of such software shall help fight against
mobile communication attacks. Phones should also be backed up to avoid loss of data and
regularly restored.
In today’s industries, mobile devices have helped provide a convenience in in maintaining and
securing their big data that need not exposed or lost. Threats are a potential hamper to big data
and can be avoided by implementing the above discussed measures.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
1 out of 17
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2025 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.





