Mobile Spoofing Enterprise Apps and Ethical Considerations Report
VerifiedAdded on 2023/01/19
|10
|2042
|97
Report
AI Summary
This report delves into the ethical issues arising from mobile spoofing in enterprise applications. It begins by defining ethics and the concept of spoofing, identifying different types like IP, DNS, and ARP spoofing. The report then highlights how mobile spoofing poses threats to enterprise employees through apps like Shaunet, which can lead to data leakage and phishing attacks. It analyzes these issues through classical ethical theories such as utilitarianism, deontology, rights, and virtue ethics. Furthermore, the report offers practical recommendations for protecting against mobile spoofing, including advanced security settings, antivirus protection, and encryption policies. The conclusion summarizes the key findings and emphasizes the importance of mitigating these risks to safeguard enterprise data and employee performance.

Running head: MOBILE SPOOFING ENTERPRISE APPS
Mobile Spoofing Enterprise Apps
Name of the Student
Name of the University
Authors note
Mobile Spoofing Enterprise Apps
Name of the Student
Name of the University
Authors note
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

1MOBILE SPOOFING ENTERPRISE APPS
Table of Contents
Introduction................................................................................................................................2
Discussion..................................................................................................................................2
Identification of the Ethical Issue..........................................................................................3
Threats and Issues associated with mobile Enterprise App...................................................3
Analysis based on the Ethical Theories.................................................................................4
Protection against spoofing enterprise apps...............................................................................5
Conclusion..................................................................................................................................6
References..................................................................................................................................7
Table of Contents
Introduction................................................................................................................................2
Discussion..................................................................................................................................2
Identification of the Ethical Issue..........................................................................................3
Threats and Issues associated with mobile Enterprise App...................................................3
Analysis based on the Ethical Theories.................................................................................4
Protection against spoofing enterprise apps...............................................................................5
Conclusion..................................................................................................................................6
References..................................................................................................................................7
Running head: MOBILE SPOOFING ENTERPRISE APPS
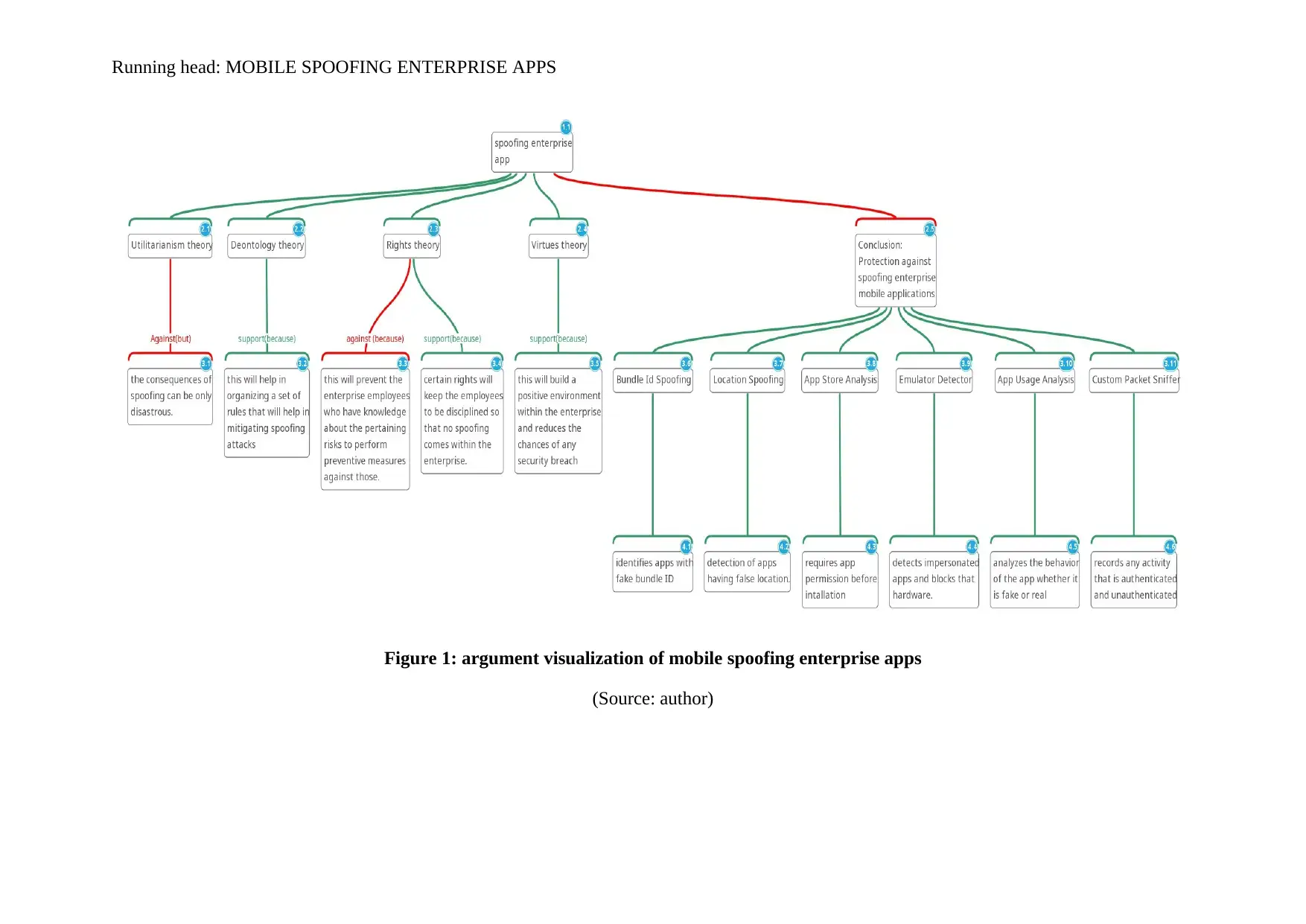
Figure 1: argument visualization of mobile spoofing enterprise apps
(Source: author)
Figure 1: argument visualization of mobile spoofing enterprise apps
(Source: author)
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

Running head: MOBILE SPOOFING ENTERPRISE APPS
Introduction
Ethics is related to the behavior and principle that a person acquires in his professional and
personal life. The strong belief that defines one’s personality can be termed as ethics (Lucas,
Van Wee & Maat, 2016). The paper provides the brief description of ethical issues related to
ICT. The paper aims to identify and discuss the spoofing activities that exits in an enterprise.
The mobile spoofing of employees has made them vulnerable and gives the attacks more
power to perform again and again. The implementation of ICT and its rapid growth has raised
several issues related to the ethics (Alavesa et al., 2016). The violation of intellectual
property rights and increased cyber-attacks includes the ethical issues. The paper also
provides recommendations that will help in eliminating ethical issues. According to
researches, the evolving ethical issues has raised a major issue in privacy and security
concern. These ethical issues are generally raises the personal privacy concern, and results in
dangerous impacts.
Discussion
Spoofing is said to be a malicious practice which is performed by the cyber attackers
which involves masquerading as an authenticated source in order to gain sensitive
information. The main objective of spoofing is to hamper the network security by disguising
as a known source. There are three types of spoofing attacks IP spoofing, DNS spoofing and
ARP spoofing. The IP spoofing generates fake IP packets that behaves as real IP source and
enters into the system. The attackers changes the source of IP address and makes it look like
authenticated source (Ali et al., 2017). DNS spoofing is done by the attackers to steal
important credentials of user by enforcing them to access a false website which looks exactly
real. The ARP spoofing attacks the network where the cyber scammers sends false Address
Introduction
Ethics is related to the behavior and principle that a person acquires in his professional and
personal life. The strong belief that defines one’s personality can be termed as ethics (Lucas,
Van Wee & Maat, 2016). The paper provides the brief description of ethical issues related to
ICT. The paper aims to identify and discuss the spoofing activities that exits in an enterprise.
The mobile spoofing of employees has made them vulnerable and gives the attacks more
power to perform again and again. The implementation of ICT and its rapid growth has raised
several issues related to the ethics (Alavesa et al., 2016). The violation of intellectual
property rights and increased cyber-attacks includes the ethical issues. The paper also
provides recommendations that will help in eliminating ethical issues. According to
researches, the evolving ethical issues has raised a major issue in privacy and security
concern. These ethical issues are generally raises the personal privacy concern, and results in
dangerous impacts.
Discussion
Spoofing is said to be a malicious practice which is performed by the cyber attackers
which involves masquerading as an authenticated source in order to gain sensitive
information. The main objective of spoofing is to hamper the network security by disguising
as a known source. There are three types of spoofing attacks IP spoofing, DNS spoofing and
ARP spoofing. The IP spoofing generates fake IP packets that behaves as real IP source and
enters into the system. The attackers changes the source of IP address and makes it look like
authenticated source (Ali et al., 2017). DNS spoofing is done by the attackers to steal
important credentials of user by enforcing them to access a false website which looks exactly
real. The ARP spoofing attacks the network where the cyber scammers sends false Address
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

1MOBILE SPOOFING ENTERPRISE APPS
Resolution Protocol messages to LAN to block or modify the traffics. All these spoofing
attack aims to impersonate any devices to steal confidential files and data.
Identification of the Ethical Issue
Every employees in the enterprise uses mobile applications to perform their common
task. In order to share data, send messages using email and sending packets mobile apps are
required. It has been an important part of job in an employee’s life (Yeboah-Boateng &
Amanor, 2014). Hence any malicious activity will trouble the performance of the employee.
The several spoofed apps such as Blackboard’s Mobile Learn app Zendesk and VMware’s
Horizon Client uses the brand name that is trusted by people and acts as malware
applications. These apps spoofs the real brand name and tricks the employees of the
enterprise to use them (Malisa, Kostiainen & Capkun, 2015). The valuable enterprise data are
on risk as mobile attacks are rapidly taking place in the organization. According to surveys, it
has been founded that 67% of organization has already been attacked through mobile
spoofing and the rest are suspected to fall under this pit. From the above report it has been
clear that attackers are proactively using mobile phones to spread their threats (Alotaibi,
AlBar & Hoque, 2016).
The Shaunet app is an example of spoofing application. This apps automatically
attaches itself to a device and installs itself on the system. Once it installs itself it is difficult
to remove. It is a kind of malware application which keeps o installing more application in
the same system it has been installed. It does not require the user’s permission and proceeds
quickly by more malware application (Malisa, Kostiainen & Capkun, 2017).
Resolution Protocol messages to LAN to block or modify the traffics. All these spoofing
attack aims to impersonate any devices to steal confidential files and data.
Identification of the Ethical Issue
Every employees in the enterprise uses mobile applications to perform their common
task. In order to share data, send messages using email and sending packets mobile apps are
required. It has been an important part of job in an employee’s life (Yeboah-Boateng &
Amanor, 2014). Hence any malicious activity will trouble the performance of the employee.
The several spoofed apps such as Blackboard’s Mobile Learn app Zendesk and VMware’s
Horizon Client uses the brand name that is trusted by people and acts as malware
applications. These apps spoofs the real brand name and tricks the employees of the
enterprise to use them (Malisa, Kostiainen & Capkun, 2015). The valuable enterprise data are
on risk as mobile attacks are rapidly taking place in the organization. According to surveys, it
has been founded that 67% of organization has already been attacked through mobile
spoofing and the rest are suspected to fall under this pit. From the above report it has been
clear that attackers are proactively using mobile phones to spread their threats (Alotaibi,
AlBar & Hoque, 2016).
The Shaunet app is an example of spoofing application. This apps automatically
attaches itself to a device and installs itself on the system. Once it installs itself it is difficult
to remove. It is a kind of malware application which keeps o installing more application in
the same system it has been installed. It does not require the user’s permission and proceeds
quickly by more malware application (Malisa, Kostiainen & Capkun, 2017).

2MOBILE SPOOFING ENTERPRISE APPS
Threats and Issues associated with mobile Enterprise App
The major threat that is caused due to Shaunet app is that it roots the device. It is also
very hard to remove from the system once it has been attached. It easily gains the employees
personal information such as name, phone number and login credentials (Neal & Woodard,
2017). Shaunet can modify and alter the data and files of the employee and gains full
customization. It can install many malicious software and puts the data and device at risk.
Issues due to spoofing of mobile apps are:
Data leakage: The data leakage of nay enterprise can affect the production of
the enterprise. The loss of important data can make the company lose useful
their reputation and competitive advantage.
Phishing: the increase in spoofing gives rise to phishing attacks obtains the
user’s username name and password and manipulate the users to click on the
infected URL’s.
Analysis based on the Ethical Theories
The classical ethical theories have been broadly classified into four categories:
Utilitarianism,
Utilitarianism: The utilitarianism ethical theory involves focusing on the
consequences of any activity. According to this theory, the happiness of an individual is the
primary concern. An action is said to be ethically fair and justified if the outcome gives
happiness to the person. If the consequences are sad and heartbreaking then those actions are
said to moral less actions (Fok, Payne & Corey, 2016). The Act utilitarianism is the act of
providing help and advantages for the people who are in need irrespective of the personal
Threats and Issues associated with mobile Enterprise App
The major threat that is caused due to Shaunet app is that it roots the device. It is also
very hard to remove from the system once it has been attached. It easily gains the employees
personal information such as name, phone number and login credentials (Neal & Woodard,
2017). Shaunet can modify and alter the data and files of the employee and gains full
customization. It can install many malicious software and puts the data and device at risk.
Issues due to spoofing of mobile apps are:
Data leakage: The data leakage of nay enterprise can affect the production of
the enterprise. The loss of important data can make the company lose useful
their reputation and competitive advantage.
Phishing: the increase in spoofing gives rise to phishing attacks obtains the
user’s username name and password and manipulate the users to click on the
infected URL’s.
Analysis based on the Ethical Theories
The classical ethical theories have been broadly classified into four categories:
Utilitarianism,
Utilitarianism: The utilitarianism ethical theory involves focusing on the
consequences of any activity. According to this theory, the happiness of an individual is the
primary concern. An action is said to be ethically fair and justified if the outcome gives
happiness to the person. If the consequences are sad and heartbreaking then those actions are
said to moral less actions (Fok, Payne & Corey, 2016). The Act utilitarianism is the act of
providing help and advantages for the people who are in need irrespective of the personal
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

3MOBILE SPOOFING ENTERPRISE APPS
relationships. The Rule utilitarianism also aims to provide benefit to the people but only with
the help of legal laws and rules.
Deontology: The deontology theory depicts the ethical relationship between the moral
values and the duty of a person. It is important for every individual to obey their duty before
making any decisions. This act is opposite to the utilitarianism because it does not require
thinking of the outcomes. It involves following the set of duties which is always associated
with an individual.
Rights: The classical ethical theories which have been given the most preference and
importance is Rights. Any person can claim their right on anybody if he or she has the
sufficient resources available.
Virtue: The main motive of this ethical theory is to focus on the moral values of a person
rather than to the actions. It determines the character of a person whether he or she is virtuous
or not. Virtue describes the actual character of the person. To lead a moral life, this ethics is
required in order to gain good habits and kind spirit. According to (Evans& Smith, 2018),
virtue ethics emphasizes in building a strong moral character. Therefore, it guides a person to
live life with a good character without following any specific rules.
Protection against spoofing enterprise apps
Use advance security setting: The enhancement of securiry settings will protect
against unknown attachments from unauthorized senders.
Use antivirus protection: the antivirus software will keep the mobile updated and
prone to any risk.
App store Analysis: identifies any data that is not present in the play store and sends
a permission request to the user (Xia, Xiaofeng & Fang, 2018).
relationships. The Rule utilitarianism also aims to provide benefit to the people but only with
the help of legal laws and rules.
Deontology: The deontology theory depicts the ethical relationship between the moral
values and the duty of a person. It is important for every individual to obey their duty before
making any decisions. This act is opposite to the utilitarianism because it does not require
thinking of the outcomes. It involves following the set of duties which is always associated
with an individual.
Rights: The classical ethical theories which have been given the most preference and
importance is Rights. Any person can claim their right on anybody if he or she has the
sufficient resources available.
Virtue: The main motive of this ethical theory is to focus on the moral values of a person
rather than to the actions. It determines the character of a person whether he or she is virtuous
or not. Virtue describes the actual character of the person. To lead a moral life, this ethics is
required in order to gain good habits and kind spirit. According to (Evans& Smith, 2018),
virtue ethics emphasizes in building a strong moral character. Therefore, it guides a person to
live life with a good character without following any specific rules.
Protection against spoofing enterprise apps
Use advance security setting: The enhancement of securiry settings will protect
against unknown attachments from unauthorized senders.
Use antivirus protection: the antivirus software will keep the mobile updated and
prone to any risk.
App store Analysis: identifies any data that is not present in the play store and sends
a permission request to the user (Xia, Xiaofeng & Fang, 2018).
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

4MOBILE SPOOFING ENTERPRISE APPS
Advanced emulator detection: it identifies any applications that are false and
impersonated and blocks the usage of such apps.
Put on location spoofing: this will help in detecting any source that reports fake
location ID.
Mobile encryption policy: proper encryption policy will protect the data from
untrusted users. Encryption of important and databases will help secure the apps.
Conclusion
Finally, to conclude with the paper successfully provides various methods will
eliminate the risks of mobile spoofing in the organization. The paper has critically analyzed
the effect of spoofing in the enterprise and how it can affect the employee’s performance. The
spoofing apps such as Shaunet, androrat, PJapps, ooqqzz aims to interrupt the employee’s job
by manipulating them to navigate fake websites to spoof their phones.
Advanced emulator detection: it identifies any applications that are false and
impersonated and blocks the usage of such apps.
Put on location spoofing: this will help in detecting any source that reports fake
location ID.
Mobile encryption policy: proper encryption policy will protect the data from
untrusted users. Encryption of important and databases will help secure the apps.
Conclusion
Finally, to conclude with the paper successfully provides various methods will
eliminate the risks of mobile spoofing in the organization. The paper has critically analyzed
the effect of spoofing in the enterprise and how it can affect the employee’s performance. The
spoofing apps such as Shaunet, androrat, PJapps, ooqqzz aims to interrupt the employee’s job
by manipulating them to navigate fake websites to spoof their phones.

5MOBILE SPOOFING ENTERPRISE APPS
References
Alavesa, P., Lehto, M., Ojala, K., & Asare, K. O. (2016, December). Here n'there: location
based mobile game exploring the possibilities of location spoofing in game
mechanics. In Proceedings of the 15th International Conference on Mobile and
Ubiquitous Multimedia (pp. 331-333). ACM.
Ali, A., Alsufyani, N., Hoque, S., & Deravi, F. (2017, December). Biometric Counter-
Spoofing for Mobile Devices Using Gaze Information. In International Conference
on Pattern Recognition and Machine Intelligence (pp. 11-18). Springer, Cham.
Alotaibi, E. F., AlBar, A. M., & Hoque, M. R. (2016). Mobile computing security: Issues and
requirements. Journal of Advances in Information Technology Vol, 7(1).
Evans, J., & Smith, M. (2018). Toward a Role Ethical Theory of Right Action. Ethical
Theory and Moral Practice, 21(3), 599-614.
Fok, L. Y., Payne, D. M., & Corey, C. M. (2016). Cultural values, utilitarian orientation, and
ethical decision making: A comparison of US and Puerto Rican
professionals. Journal of Business Ethics, 134(2), 263-279.
Lucas, K., Van Wee, B., & Maat, K. (2016). A method to evaluate equitable accessibility:
combining ethical theories and accessibility-based approaches. Transportation, 43(3),
473-490.
Malisa, L., Kostiainen, K., & Capkun, S. (2015). Technical Report: Detecting Mobile
Application Spoofing Attacks by Leveraging User Visual Similarity Perception.
Malisa, L., Kostiainen, K., & Capkun, S. (2017, March). Detecting mobile application
spoofing attacks by leveraging user visual similarity perception. In Proceedings of the
References
Alavesa, P., Lehto, M., Ojala, K., & Asare, K. O. (2016, December). Here n'there: location
based mobile game exploring the possibilities of location spoofing in game
mechanics. In Proceedings of the 15th International Conference on Mobile and
Ubiquitous Multimedia (pp. 331-333). ACM.
Ali, A., Alsufyani, N., Hoque, S., & Deravi, F. (2017, December). Biometric Counter-
Spoofing for Mobile Devices Using Gaze Information. In International Conference
on Pattern Recognition and Machine Intelligence (pp. 11-18). Springer, Cham.
Alotaibi, E. F., AlBar, A. M., & Hoque, M. R. (2016). Mobile computing security: Issues and
requirements. Journal of Advances in Information Technology Vol, 7(1).
Evans, J., & Smith, M. (2018). Toward a Role Ethical Theory of Right Action. Ethical
Theory and Moral Practice, 21(3), 599-614.
Fok, L. Y., Payne, D. M., & Corey, C. M. (2016). Cultural values, utilitarian orientation, and
ethical decision making: A comparison of US and Puerto Rican
professionals. Journal of Business Ethics, 134(2), 263-279.
Lucas, K., Van Wee, B., & Maat, K. (2016). A method to evaluate equitable accessibility:
combining ethical theories and accessibility-based approaches. Transportation, 43(3),
473-490.
Malisa, L., Kostiainen, K., & Capkun, S. (2015). Technical Report: Detecting Mobile
Application Spoofing Attacks by Leveraging User Visual Similarity Perception.
Malisa, L., Kostiainen, K., & Capkun, S. (2017, March). Detecting mobile application
spoofing attacks by leveraging user visual similarity perception. In Proceedings of the
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

6MOBILE SPOOFING ENTERPRISE APPS
Seventh ACM on Conference on Data and Application Security and Privacy (pp. 289-
300). ACM.
Neal, T. J., & Woodard, D. L. (2017, October). Spoofing analysis of mobile device data as
behavioral biometric modalities. In 2017 IEEE International Joint Conference on
Biometrics (IJCB) (pp. 62-70). IEEE.
Xia, S., Li, N., Xiaofeng, T., & Fang, C. (2018, August). Multiple Attributes Based Spoofing
Detection Using an Improved Clustering Algorithm in Mobile Edge Network. In 2018
1st IEEE International Conference on Hot Information-Centric Networking
(HotICN) (pp. 242-243). IEEE.
Yeboah-Boateng, E. O., & Amanor, P. M. (2014). Phishing, SMiShing & Vishing: an
assessment of threats against mobile devices. Journal of Emerging Trends in
Computing and Information Sciences, 5(4), 297-307.
Seventh ACM on Conference on Data and Application Security and Privacy (pp. 289-
300). ACM.
Neal, T. J., & Woodard, D. L. (2017, October). Spoofing analysis of mobile device data as
behavioral biometric modalities. In 2017 IEEE International Joint Conference on
Biometrics (IJCB) (pp. 62-70). IEEE.
Xia, S., Li, N., Xiaofeng, T., & Fang, C. (2018, August). Multiple Attributes Based Spoofing
Detection Using an Improved Clustering Algorithm in Mobile Edge Network. In 2018
1st IEEE International Conference on Hot Information-Centric Networking
(HotICN) (pp. 242-243). IEEE.
Yeboah-Boateng, E. O., & Amanor, P. M. (2014). Phishing, SMiShing & Vishing: an
assessment of threats against mobile devices. Journal of Emerging Trends in
Computing and Information Sciences, 5(4), 297-307.
1 out of 10
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.

