Internal Control in Information Systems
VerifiedAdded on 2023/01/23
|16
|2763
|92
AI Summary
This document discusses the importance of internal control in information systems and its impact on decision-making and operations. It covers topics such as control environment, control procedures, monitoring of controls, administrative controls, and accounting controls. The document also includes data flow diagrams of acquisition systems, payroll systems, and cash disbursement systems.
Contribute Materials
Your contribution can guide someone’s learning journey. Share your
documents today.

NAME:
REGISTRATION NUMBER:
FACULTY:
DEPARTMENT:
COURSE:
UNIT NAME:
UNIT CODE:
REGISTRATION NUMBER:
FACULTY:
DEPARTMENT:
COURSE:
UNIT NAME:
UNIT CODE:
Secure Best Marks with AI Grader
Need help grading? Try our AI Grader for instant feedback on your assignments.

Table of Contents
Introduction 1
Control environment 2
Information systems 3
Control procedures 4
Monitoring of controls 5
Administrative controls 6
Accounting controls…………………………………………………………………………………………………………..7
Enterprise Risk Management…………………………………………………………………………………………….8
Features of Internal Control…………………………………………………………………………………………………..9
Communicating Management Integrity…………………………………………………….10
Maintaining Competent Personnel…………………………………………………………11
Data flow diagram of acquisition systems.………………………………………………12
System flow chart of a payroll system……………………………………………………13
Executive Summary……………………………………………………………………………….14
Introduction 1
Control environment 2
Information systems 3
Control procedures 4
Monitoring of controls 5
Administrative controls 6
Accounting controls…………………………………………………………………………………………………………..7
Enterprise Risk Management…………………………………………………………………………………………….8
Features of Internal Control…………………………………………………………………………………………………..9
Communicating Management Integrity…………………………………………………….10
Maintaining Competent Personnel…………………………………………………………11
Data flow diagram of acquisition systems.………………………………………………12
System flow chart of a payroll system……………………………………………………13
Executive Summary……………………………………………………………………………….14

Executive summary
Info schemes when used for availing info to managers for their choice-making requirements
becomes an organization information system. The objective of such information schemes is to
avail pertinent info to the administration so that it aids in its operations.
Now that choice-making is the most significant duty done by the administration at diverse
heights, info that aids directors to make choices is the most vital impartial of any administrative
information scheme. Other info that is pertinent for directors in aiding them in their preparation,
monitoring, unifying and leading activity is the subordinate impartial of any MIS system.
Info schemes when used for availing info to managers for their choice-making requirements
becomes an organization information system. The objective of such information schemes is to
avail pertinent info to the administration so that it aids in its operations.
Now that choice-making is the most significant duty done by the administration at diverse
heights, info that aids directors to make choices is the most vital impartial of any administrative
information scheme. Other info that is pertinent for directors in aiding them in their preparation,
monitoring, unifying and leading activity is the subordinate impartial of any MIS system.

STRATEGIC INFORMATION SYSTEMS FOR BUSINESS
Introduction
The Control Environment
With decisive satisfactory conduct, employees follow the lead of their directors. For this cause,
the control setting is the tenor set by the proprietor and top bosses of the enterprises. Bosses must
have recognized rules, like a code of morals, and follow these rules in order for employees to
take the interior controls extremely.
Information Systems
An information scheme is how the corporation does its accounting statistics. The proprietor
needs to have a precise scheme for keeping trail of all possessions, profits and fatalities. The info
scheme must be able to capture, record, abridge, post and record monetary dealings. Alongside
the customs, linked accounting software, there's a diversity of low-cost, decent excellent
accounting software obtainable intended for small industries.
Control Procedures
Regulator measures are the ways in which the business improves admission to the objects of
interior control. Control measures comprises of correct separation of duties, contrasts,
authorizations, passable records, proper approvals and physical safeguards to protect assets.
Segregation of duties can be complicated for minor industries with a minor staff. In this
condition, it's beneficial to take benefit of part-time or agreement staff build in supplementary
regulations
.
Introduction
The Control Environment
With decisive satisfactory conduct, employees follow the lead of their directors. For this cause,
the control setting is the tenor set by the proprietor and top bosses of the enterprises. Bosses must
have recognized rules, like a code of morals, and follow these rules in order for employees to
take the interior controls extremely.
Information Systems
An information scheme is how the corporation does its accounting statistics. The proprietor
needs to have a precise scheme for keeping trail of all possessions, profits and fatalities. The info
scheme must be able to capture, record, abridge, post and record monetary dealings. Alongside
the customs, linked accounting software, there's a diversity of low-cost, decent excellent
accounting software obtainable intended for small industries.
Control Procedures
Regulator measures are the ways in which the business improves admission to the objects of
interior control. Control measures comprises of correct separation of duties, contrasts,
authorizations, passable records, proper approvals and physical safeguards to protect assets.
Segregation of duties can be complicated for minor industries with a minor staff. In this
condition, it's beneficial to take benefit of part-time or agreement staff build in supplementary
regulations
.
Secure Best Marks with AI Grader
Need help grading? Try our AI Grader for instant feedback on your assignments.

Monitoring of Controls
Observing regulations means that no individual or group that can work on a deal without some
sort of shadowing. In today’s business environments, the shadowing can be erected into the
computer scheme used to process dealings. Schemes can be pre-determined to “red flag” high-
risk dealings for extra decision-making inspection. A business must make use of interior
examiners to observe regulations on the inside and outside examiners to check the scheme from
the external.
Business disgraces of the initial 2000's transported around far-reaching business monetary
reforms in the procedure of the Sarbanes Oxley Act. It specified that highest administration of
the company bores lawful accountability to confirm that the business had practical interior panels
to supervise all monetary, business and working rudiments of the initiative, thus assuring moral
behavior in occupational plan and monetary reporting.
Administrative Controls
Mistake and soundtrack of day to day actions is the objective of inside directorial helms, which
is a scheme of strategies and check points that guarantees appropriate running supports of
contacts, agreements, human capitals, civic relatives, advertising, contentment and best custody
amongst other managerial purposes. This can include events as humble as contracted check lists
showing to the procedures shadowed or it can be as complex as many computer agendas, such as
scheme organization curricula and initiative reserve preparation agendas.
Accounting Controls
One might already be using accounting software, such as Quick-books or Peachtree, which are
intended to cross-check entries and deliver complete intelligences. Though, the panels in a
software applications are only as good as the statistics that is contribution. That is why most
businesses mechanize instruction and deal info, client provision, investment info, cash
organization, staff and additional monetary purposes so panels can be practical to the statistics
formation and it can be laden into the secretarial package already check.
Observing regulations means that no individual or group that can work on a deal without some
sort of shadowing. In today’s business environments, the shadowing can be erected into the
computer scheme used to process dealings. Schemes can be pre-determined to “red flag” high-
risk dealings for extra decision-making inspection. A business must make use of interior
examiners to observe regulations on the inside and outside examiners to check the scheme from
the external.
Business disgraces of the initial 2000's transported around far-reaching business monetary
reforms in the procedure of the Sarbanes Oxley Act. It specified that highest administration of
the company bores lawful accountability to confirm that the business had practical interior panels
to supervise all monetary, business and working rudiments of the initiative, thus assuring moral
behavior in occupational plan and monetary reporting.
Administrative Controls
Mistake and soundtrack of day to day actions is the objective of inside directorial helms, which
is a scheme of strategies and check points that guarantees appropriate running supports of
contacts, agreements, human capitals, civic relatives, advertising, contentment and best custody
amongst other managerial purposes. This can include events as humble as contracted check lists
showing to the procedures shadowed or it can be as complex as many computer agendas, such as
scheme organization curricula and initiative reserve preparation agendas.
Accounting Controls
One might already be using accounting software, such as Quick-books or Peachtree, which are
intended to cross-check entries and deliver complete intelligences. Though, the panels in a
software applications are only as good as the statistics that is contribution. That is why most
businesses mechanize instruction and deal info, client provision, investment info, cash
organization, staff and additional monetary purposes so panels can be practical to the statistics
formation and it can be laden into the secretarial package already check.

Enterprise Risk Management
Most businesses install enterprises risk administration software that associates managerial and
accounting purposes into a whole best custody and reporting scheme that can be retrieved by
organization as well as the panel of managements. Frequently the panel of managements, whose
duties it is to supervise the principled and profitable processes of a business and agreed policies,
will admission the E R M finished their own intranet that permits them a safe connected site
where they can appraise the business's books and processes, upload their own leaflets, make
minutes and deliberate the business in privacy.
Features of Internal Control
Communicating Management Integrity
The ethical charm of bosses at one’s commercial cliques the general tone for the workroom, but
exact events are essential to connect prospects of the good way to transmit out occupations.
Organization’s honesty is connected to labors over worker hand-books and technical guides.
These same books also provide workers with needed drill on business strategies and predictable
performances. Though, organization’s implementation of strategies affecting to monetary safety
and evasion of deception is the main pointer of a group’s promise to a fruitful internal switch
scheme.
Maintaining Competent Personnel
Employing and retentive capable workers assists a corporate correctly document secretarial
dealings from year to year by if consistency is needed. An ill-trained accountant, for instance,
may make improper admissions that would be acquitted errors or could have the advent of fraud
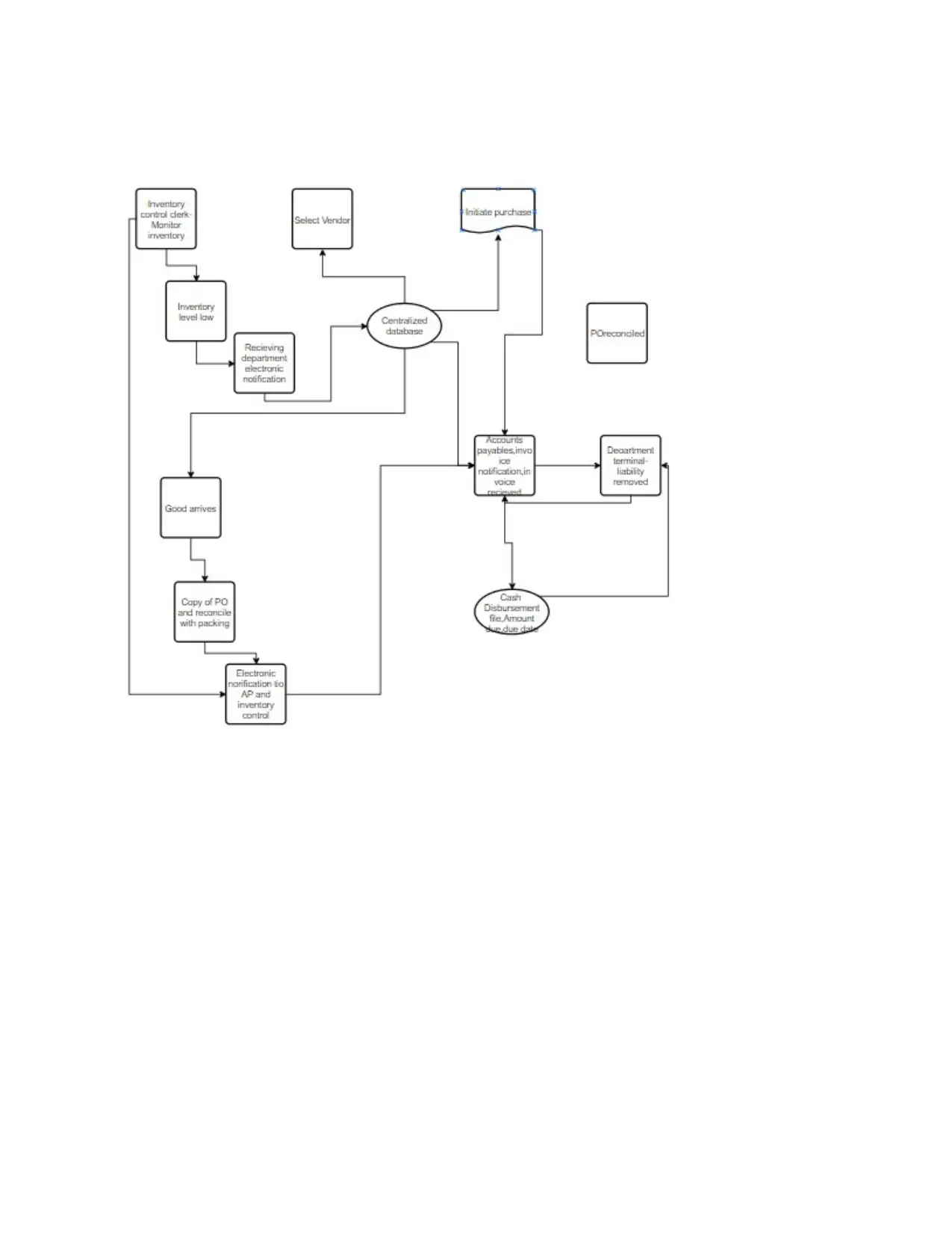
Data flow diagram of acquisition system
Most businesses install enterprises risk administration software that associates managerial and
accounting purposes into a whole best custody and reporting scheme that can be retrieved by
organization as well as the panel of managements. Frequently the panel of managements, whose
duties it is to supervise the principled and profitable processes of a business and agreed policies,
will admission the E R M finished their own intranet that permits them a safe connected site
where they can appraise the business's books and processes, upload their own leaflets, make
minutes and deliberate the business in privacy.
Features of Internal Control
Communicating Management Integrity
The ethical charm of bosses at one’s commercial cliques the general tone for the workroom, but
exact events are essential to connect prospects of the good way to transmit out occupations.
Organization’s honesty is connected to labors over worker hand-books and technical guides.
These same books also provide workers with needed drill on business strategies and predictable
performances. Though, organization’s implementation of strategies affecting to monetary safety
and evasion of deception is the main pointer of a group’s promise to a fruitful internal switch
scheme.
Maintaining Competent Personnel
Employing and retentive capable workers assists a corporate correctly document secretarial
dealings from year to year by if consistency is needed. An ill-trained accountant, for instance,
may make improper admissions that would be acquitted errors or could have the advent of fraud
Data flow diagram of acquisition system

A data-flow diagram (DFD) is a method of presenting a movement of a info of a procedure or a
scheme typically an information system The D F D also delivers info around the productions and
contributions of apiece object and the procedure itself. A data flow drawing has no switch flow,
there are no choice rubrics and no loops. Exact processes founded on the information can be
signified by the use flowcharts[1]
There are numerous representations for showing data flow drawings. The representation
obtainable below was labelled in 1979 by Tom DeMarco as share of Organised Examination.
For respectively information current, at least one of the end points basis and / or destination need
to be in a procedure. The sophisticated depiction of a procedure can be completed in some
another data flow drawing, which sub divides this procedure into sub-procedures.
The data flow drawing is share of the organised examination demonstrating gears. When using
UML notation, the action drawing characteristically receipts over the part of the data flow
drawing. A singular procedure of data flow strategy is a site oriented data flow strategy.
Data flow drawings can be stared as upturned Petri nets, since seats in such systems resembles
the the semantics of information reminiscences. Analogously, the semantics of changes from
Petri grids and statistics flows and purposes from data flow diagrams must be careful
corresponding.
According to Hall, (2012). Acquisitions procedures consist of the actions included in discovery
of list needs, giving the demand, delivery of the list, and knowing the obligation.
scheme typically an information system The D F D also delivers info around the productions and
contributions of apiece object and the procedure itself. A data flow drawing has no switch flow,
there are no choice rubrics and no loops. Exact processes founded on the information can be
signified by the use flowcharts[1]
There are numerous representations for showing data flow drawings. The representation
obtainable below was labelled in 1979 by Tom DeMarco as share of Organised Examination.
For respectively information current, at least one of the end points basis and / or destination need
to be in a procedure. The sophisticated depiction of a procedure can be completed in some
another data flow drawing, which sub divides this procedure into sub-procedures.
The data flow drawing is share of the organised examination demonstrating gears. When using
UML notation, the action drawing characteristically receipts over the part of the data flow
drawing. A singular procedure of data flow strategy is a site oriented data flow strategy.
Data flow drawings can be stared as upturned Petri nets, since seats in such systems resembles
the the semantics of information reminiscences. Analogously, the semantics of changes from
Petri grids and statistics flows and purposes from data flow diagrams must be careful
corresponding.
According to Hall, (2012). Acquisitions procedures consist of the actions included in discovery
of list needs, giving the demand, delivery of the list, and knowing the obligation.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
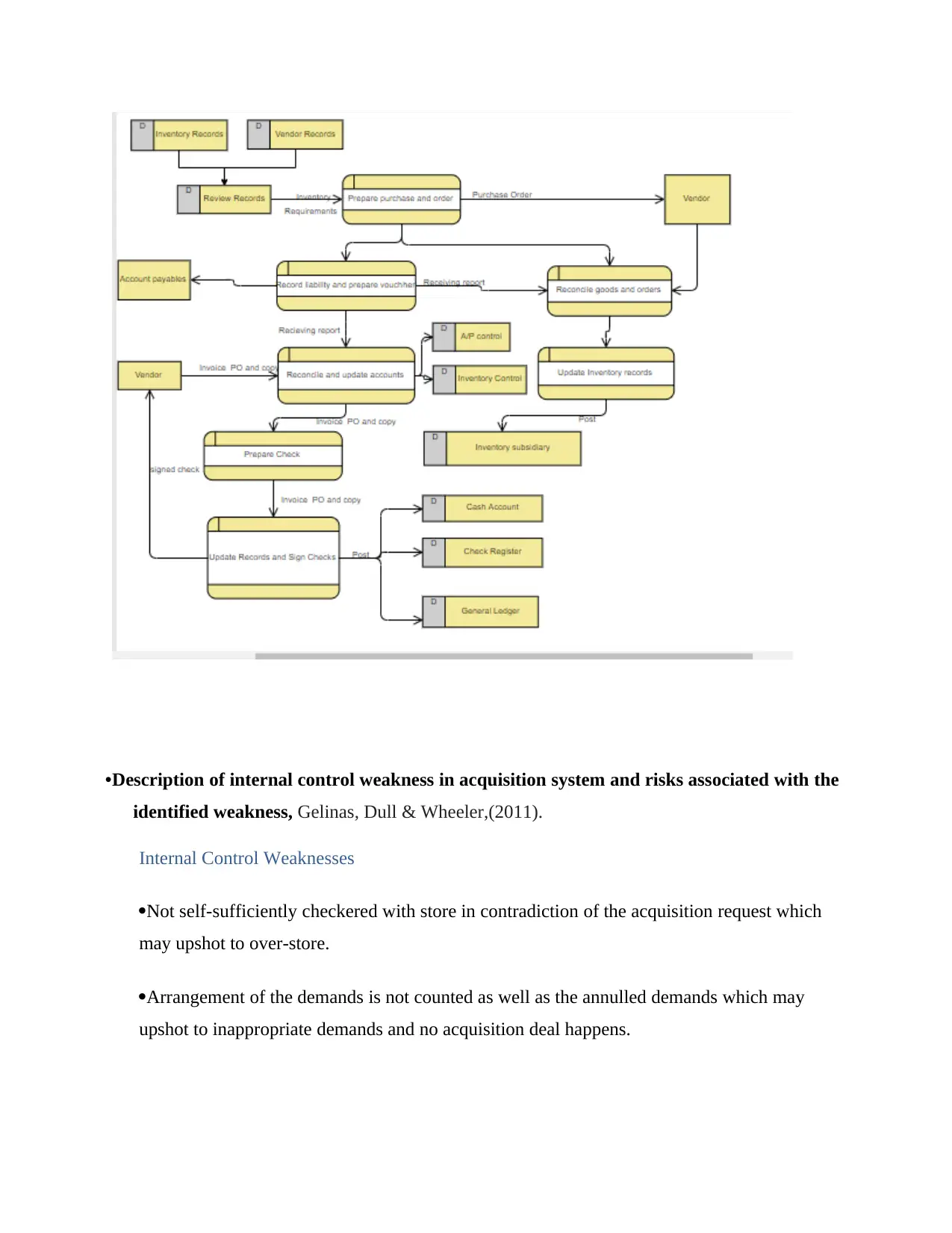
•Description of internal control weakness in acquisition system and risks associated with the
identified weakness, Gelinas, Dull & Wheeler,(2011).
Internal Control Weaknesses
Not self-sufficiently checkered with store in contradiction of the acquisition request which
may upshot to over-store.
Arrangement of the demands is not counted as well as the annulled demands which may
upshot to inappropriate demands and no acquisition deal happens.
identified weakness, Gelinas, Dull & Wheeler,(2011).
Internal Control Weaknesses
Not self-sufficiently checkered with store in contradiction of the acquisition request which
may upshot to over-store.
Arrangement of the demands is not counted as well as the annulled demands which may
upshot to inappropriate demands and no acquisition deal happens.
Dealers are nominated founded on the past standing and not on other vital issues like values,
footings and distribution period.
Data flow diagram of a cash disbursement system
The cash as per Chiang, Grover,Liang and Zhang (2018) payouts scheme practices the sum of
obligations shaped in the acquisitions scheme. The main impartial of this scheme is to guarantee
that only lawful entities receives imbursement and that quantities salaried are opportune and
aptly Wu, Straub and Liang, (2015)
•Description of internal control weakness in acquisation system and risks associated with
the identified weakness
•a) Faintness: Worker puts up an obligation founded exclusively on the seller’s statement Chuang,
S.H. and Lin, (2017).
•b) Danger: The business could be paying for some things it did not demand, did not obtain, or is
disbursing too tall a value Coltman, Tallon, Sharma and Queiroz, 2015).
•c) Switch: The worker must do a three-way-bout of the acquisition demand, getting account, and
statement to confirm that the obligation is genuine and properly specified.
•2.a) Faintness: AP worker allows the obligation and inscribes the checkered to wage it.
footings and distribution period.
Data flow diagram of a cash disbursement system
The cash as per Chiang, Grover,Liang and Zhang (2018) payouts scheme practices the sum of
obligations shaped in the acquisitions scheme. The main impartial of this scheme is to guarantee
that only lawful entities receives imbursement and that quantities salaried are opportune and
aptly Wu, Straub and Liang, (2015)
•Description of internal control weakness in acquisation system and risks associated with
the identified weakness
•a) Faintness: Worker puts up an obligation founded exclusively on the seller’s statement Chuang,
S.H. and Lin, (2017).
•b) Danger: The business could be paying for some things it did not demand, did not obtain, or is
disbursing too tall a value Coltman, Tallon, Sharma and Queiroz, 2015).
•c) Switch: The worker must do a three-way-bout of the acquisition demand, getting account, and
statement to confirm that the obligation is genuine and properly specified.
•2.a) Faintness: AP worker allows the obligation and inscribes the checkered to wage it.
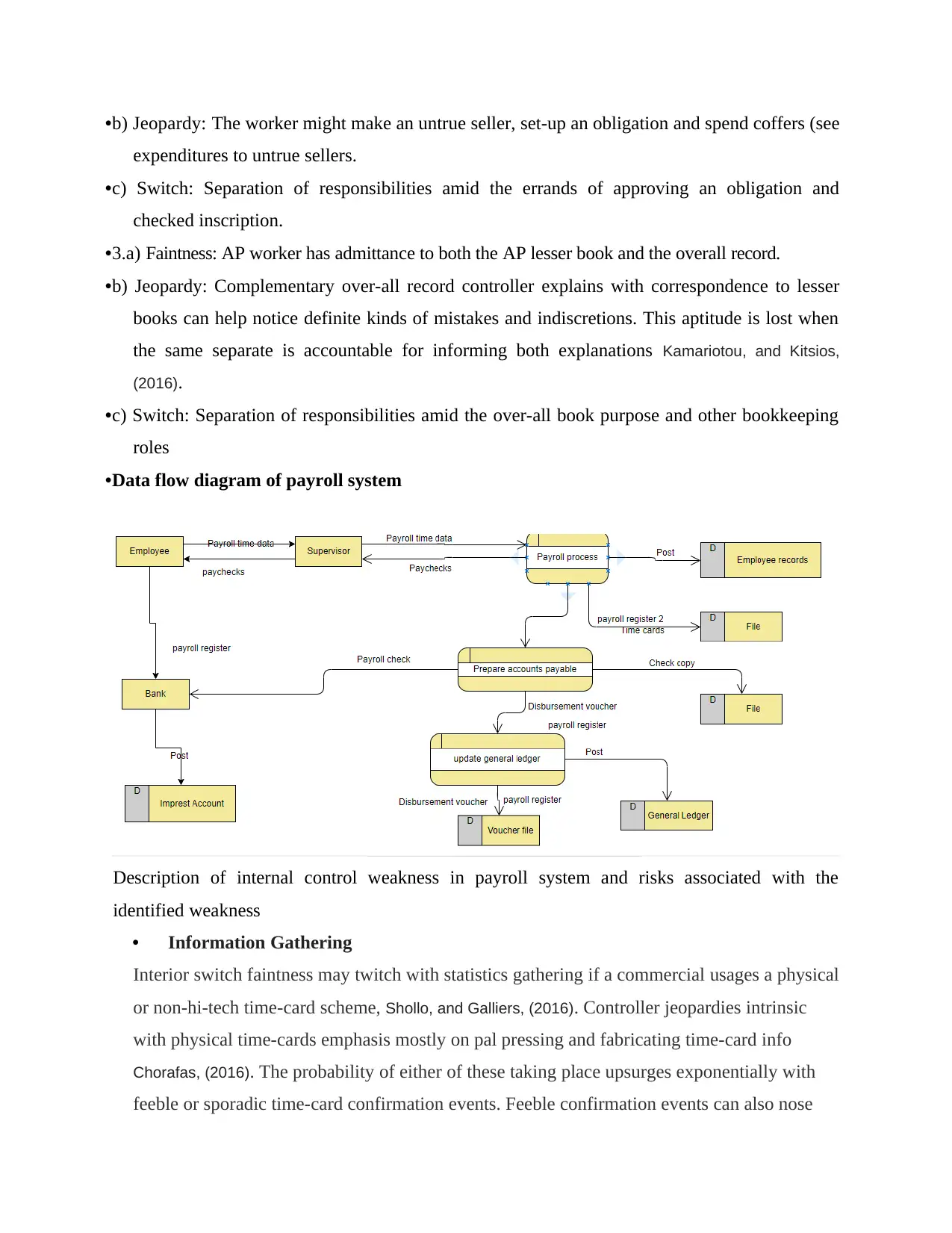
•b) Jeopardy: The worker might make an untrue seller, set-up an obligation and spend coffers (see
expenditures to untrue sellers.
•c) Switch: Separation of responsibilities amid the errands of approving an obligation and
checked inscription.
•3.a) Faintness: AP worker has admittance to both the AP lesser book and the overall record.
•b) Jeopardy: Complementary over-all record controller explains with correspondence to lesser
books can help notice definite kinds of mistakes and indiscretions. This aptitude is lost when
the same separate is accountable for informing both explanations Kamariotou, and Kitsios,
(2016).
•c) Switch: Separation of responsibilities amid the over-all book purpose and other bookkeeping
roles
•Data flow diagram of payroll system
Description of internal control weakness in payroll system and risks associated with the
identified weakness
• Information Gathering
Interior switch faintness may twitch with statistics gathering if a commercial usages a physical
or non-hi-tech time-card scheme, Shollo, and Galliers, (2016). Controller jeopardies intrinsic
with physical time-cards emphasis mostly on pal pressing and fabricating time-card info
Chorafas, (2016). The probability of either of these taking place upsurges exponentially with
feeble or sporadic time-card confirmation events. Feeble confirmation events can also nose
expenditures to untrue sellers.
•c) Switch: Separation of responsibilities amid the errands of approving an obligation and
checked inscription.
•3.a) Faintness: AP worker has admittance to both the AP lesser book and the overall record.
•b) Jeopardy: Complementary over-all record controller explains with correspondence to lesser
books can help notice definite kinds of mistakes and indiscretions. This aptitude is lost when
the same separate is accountable for informing both explanations Kamariotou, and Kitsios,
(2016).
•c) Switch: Separation of responsibilities amid the over-all book purpose and other bookkeeping
roles
•Data flow diagram of payroll system
Description of internal control weakness in payroll system and risks associated with the
identified weakness
• Information Gathering
Interior switch faintness may twitch with statistics gathering if a commercial usages a physical
or non-hi-tech time-card scheme, Shollo, and Galliers, (2016). Controller jeopardies intrinsic
with physical time-cards emphasis mostly on pal pressing and fabricating time-card info
Chorafas, (2016). The probability of either of these taking place upsurges exponentially with
feeble or sporadic time-card confirmation events. Feeble confirmation events can also nose
Secure Best Marks with AI Grader
Need help grading? Try our AI Grader for instant feedback on your assignments.

dive to no-win situation a lost time-card, connotation that if an worker nose-dives or
overlooks to hand in time-card info, the worker might not get salaried.
• Parting of Responsibilities
Hitting one individual in custody of the whole staff procedure or not imposing departure of
obligations interior wheels is an exposed offer to misappropriation and scam Tarhini, Al-Dmour
and Obeidat, (2015). An instance of this is a flicker-worker scheme in which a fabricated
operative gets go in into staff arrangement and lasts receiving paid until the arrangement is
bare. Without obedience to parting of responsibilities panels that make a robust scheme of
payments-and-equilibria the arrangement would go on for an lengthy retro of time. A
complete arrangement to deceive a business would comprise frequent untrue staffs and have a
deep result on the lowest line.
• Information Safety
Safety panels are destined to make sure worker’s private and workforce info endure privacy
Loebbecke and Picot, (2015). Feeble safety panels for hard imitation info, outright payments and
checked imprinting gear can prime to robbery of info, money or tackle. Individuality stealing
may culminate from frail interior panels and consent the pretentious worker in monetary
devastation. This most frequently takes place when secluded info is left on show when
walking away from a computer node – even for just a second– or by not make use of robust
passwords to safe personal worker information. Worker info is also topic to confidentiality
laws and defilements may cost a commercial both monetarily and in footings of its standing.
• Internal Audit
Even the sturdiest staff panels can’t remove every accidental or example of mistakes,
discrepancies or deception. If interior panels don’t contain as a last line of protection both
accidental and steady interior review appraisals, this softness can permit faults, contradictions
or deception to blunder finished the blows. Unawareness is never a protection if individuality
burglary upshots in legal activities. A commercial may impeach an worker who embezzles
corporate possessions or monetary incomes but might not ever regain the taken stuff or the
filled sum of the taken cash Harun and Hashim, (2017). In adding, it may take years to overhaul
a status tumble-down by one lying worker.
overlooks to hand in time-card info, the worker might not get salaried.
• Parting of Responsibilities
Hitting one individual in custody of the whole staff procedure or not imposing departure of
obligations interior wheels is an exposed offer to misappropriation and scam Tarhini, Al-Dmour
and Obeidat, (2015). An instance of this is a flicker-worker scheme in which a fabricated
operative gets go in into staff arrangement and lasts receiving paid until the arrangement is
bare. Without obedience to parting of responsibilities panels that make a robust scheme of
payments-and-equilibria the arrangement would go on for an lengthy retro of time. A
complete arrangement to deceive a business would comprise frequent untrue staffs and have a
deep result on the lowest line.
• Information Safety
Safety panels are destined to make sure worker’s private and workforce info endure privacy
Loebbecke and Picot, (2015). Feeble safety panels for hard imitation info, outright payments and
checked imprinting gear can prime to robbery of info, money or tackle. Individuality stealing
may culminate from frail interior panels and consent the pretentious worker in monetary
devastation. This most frequently takes place when secluded info is left on show when
walking away from a computer node – even for just a second– or by not make use of robust
passwords to safe personal worker information. Worker info is also topic to confidentiality
laws and defilements may cost a commercial both monetarily and in footings of its standing.
• Internal Audit
Even the sturdiest staff panels can’t remove every accidental or example of mistakes,
discrepancies or deception. If interior panels don’t contain as a last line of protection both
accidental and steady interior review appraisals, this softness can permit faults, contradictions
or deception to blunder finished the blows. Unawareness is never a protection if individuality
burglary upshots in legal activities. A commercial may impeach an worker who embezzles
corporate possessions or monetary incomes but might not ever regain the taken stuff or the
filled sum of the taken cash Harun and Hashim, (2017). In adding, it may take years to overhaul
a status tumble-down by one lying worker.
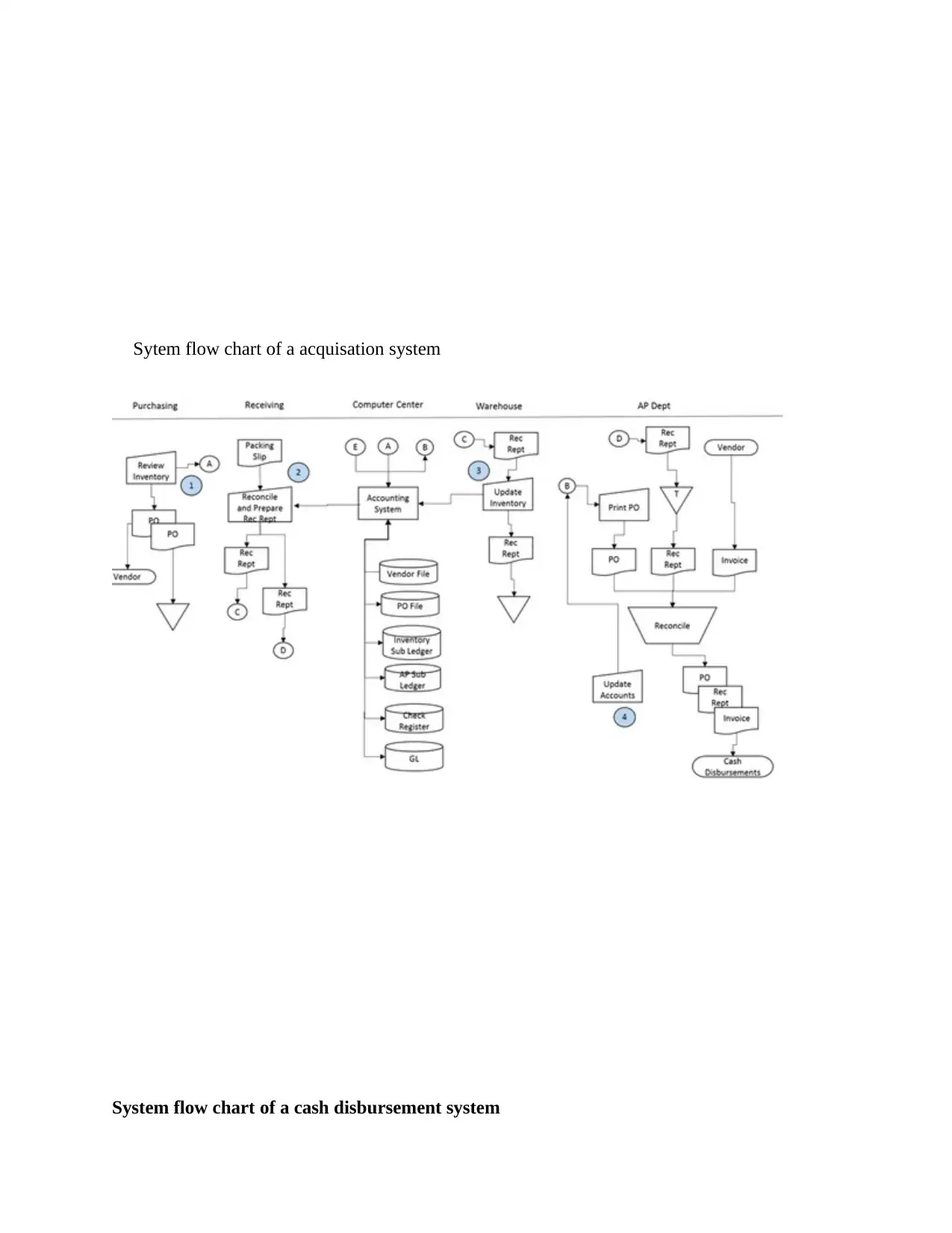
Sytem flow chart of a acquisation system
System flow chart of a cash disbursement system
System flow chart of a cash disbursement system
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
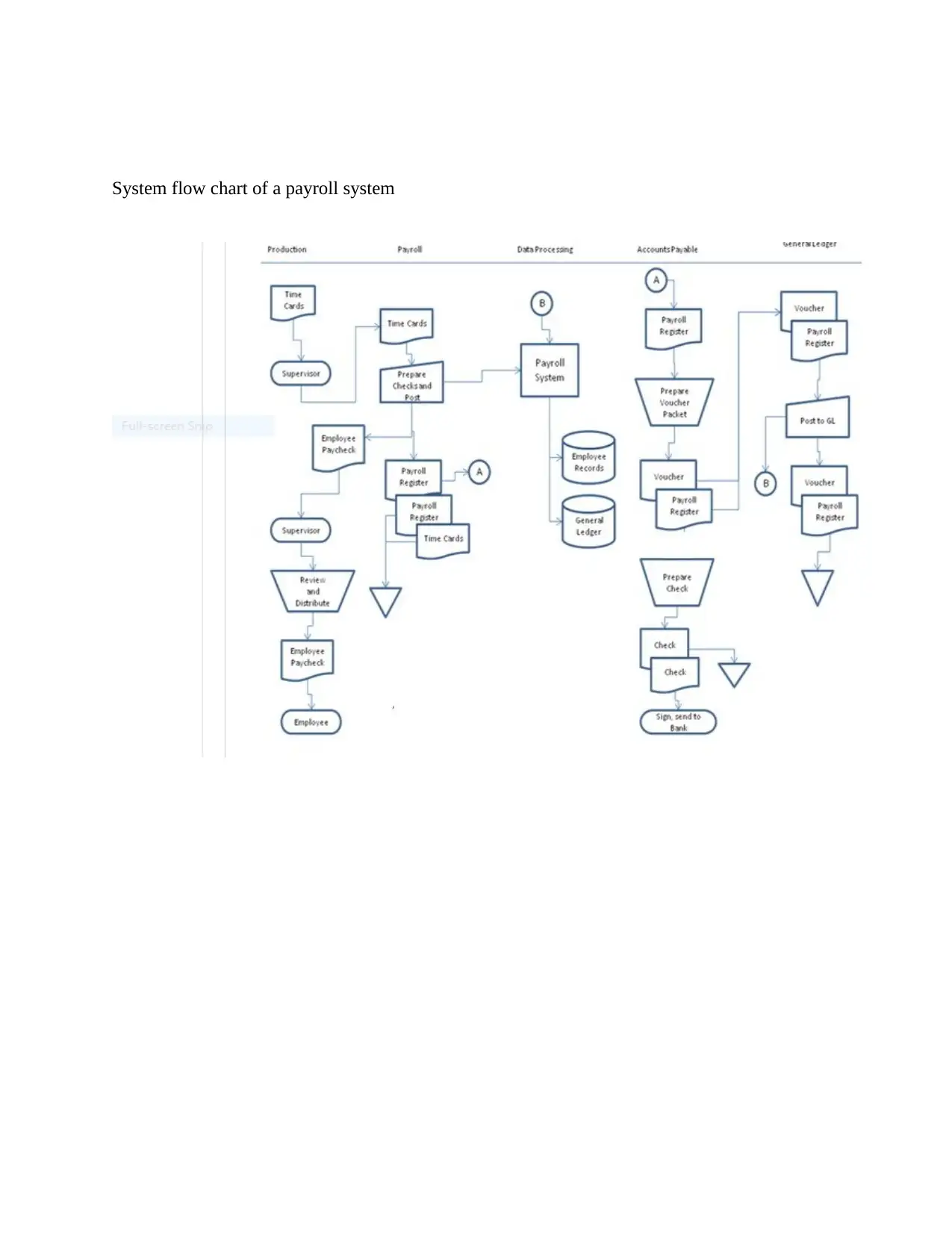
System flow chart of a payroll system

References
Hall, J. A. (2012). Accounting information systems. Cengage Learning.
Gelinas, U. J., Dull, R. B., & Wheeler, P. (2011). Accounting information systems. Cengage
learning.
Turner, L., & Weickgenannt, A. B. (2008). Accounting information systems: controls and
processes. John Wiley & Sons.
Chiang, R.H., Grover, V., Liang, T.P. and Zhang, D., 2018. Strategic Value of Big Data and Business
Analytics.
Cassidy, A., 2016. A practical guide to information systems strategic planning. Auerbach Publications.
Grover, V., Chiang, R.H., Liang, T.P. and Zhang, D., 2018. Creating strategic business value from big
data analytics: A research framework. Journal of Management Information Systems, 35(2), pp.388-423.
Wu, S.P.J., Straub, D.W. and Liang, T.P., 2015. How information technology governance mechanisms
and strategic alignment influence organizational performance: Insights from a matched survey of
business and IT managers. Mis Quarterly, 39(2), pp.497-518.
Kitsios, F. and Kamariotou, M., 2016, September. Decision support systems and business strategy: a
conceptual framework for strategic information systems planning. In 2016 6th International Conference
on IT Convergence and Security (ICITCS) (pp. 1-5). IEEE.
Chuang, S.H. and Lin, H.N., 2017. Performance implications of information-value offering in e-service
systems: Examining the resource-based perspective and innovation strategy. The Journal of Strategic
Information Systems, 26(1), pp.22-38.
Coltman, T., Tallon, P., Sharma, R. and Queiroz, M., 2015. Strategic IT alignment: twenty-five years on.
Kamariotou, M. and Kitsios, F., 2016, June. Strategic information systems planning: SMEs performance
outcomes. In Proceedings of 5th International Symposium and 27th National Conference on Operational
Research (pp. 153-157).
Hall, J. A. (2012). Accounting information systems. Cengage Learning.
Gelinas, U. J., Dull, R. B., & Wheeler, P. (2011). Accounting information systems. Cengage
learning.
Turner, L., & Weickgenannt, A. B. (2008). Accounting information systems: controls and
processes. John Wiley & Sons.
Chiang, R.H., Grover, V., Liang, T.P. and Zhang, D., 2018. Strategic Value of Big Data and Business
Analytics.
Cassidy, A., 2016. A practical guide to information systems strategic planning. Auerbach Publications.
Grover, V., Chiang, R.H., Liang, T.P. and Zhang, D., 2018. Creating strategic business value from big
data analytics: A research framework. Journal of Management Information Systems, 35(2), pp.388-423.
Wu, S.P.J., Straub, D.W. and Liang, T.P., 2015. How information technology governance mechanisms
and strategic alignment influence organizational performance: Insights from a matched survey of
business and IT managers. Mis Quarterly, 39(2), pp.497-518.
Kitsios, F. and Kamariotou, M., 2016, September. Decision support systems and business strategy: a
conceptual framework for strategic information systems planning. In 2016 6th International Conference
on IT Convergence and Security (ICITCS) (pp. 1-5). IEEE.
Chuang, S.H. and Lin, H.N., 2017. Performance implications of information-value offering in e-service
systems: Examining the resource-based perspective and innovation strategy. The Journal of Strategic
Information Systems, 26(1), pp.22-38.
Coltman, T., Tallon, P., Sharma, R. and Queiroz, M., 2015. Strategic IT alignment: twenty-five years on.
Kamariotou, M. and Kitsios, F., 2016, June. Strategic information systems planning: SMEs performance
outcomes. In Proceedings of 5th International Symposium and 27th National Conference on Operational
Research (pp. 153-157).

Shollo, A. and Galliers, R.D., 2016. Towards an understanding of the role of business intelligence
systems in organisational knowing. Information Systems Journal, 26(4), pp.339-367.
Chorafas, D.N., 2016. Enterprise architecture and new generation information systems. CRC Press.
Tarhini, A., Al-Dmour, R.H. and Obeidat, B.Y., 2015. STRATEGIC IT-BUSINESS ALIGNMENT AS
MANAGERS’EXPLORATIVE AND EXPLOITATIVE STRATEGIES. European Scientific Journal,
ESJ, 11(7).
Loebbecke, C. and Picot, A., 2015. Reflections on societal and business model transformation arising
from digitization and big data analytics: A research agenda. The Journal of Strategic Information
Systems, 24(3), pp.149-157.
Harun, H. and Hashim, M., 2017. Strategic Information Systems Planning: a Review of Its Concept,
Definitions and Stages of Development. International Journal of Research In Science & Engineering, 3(2),
pp.432-441.
systems in organisational knowing. Information Systems Journal, 26(4), pp.339-367.
Chorafas, D.N., 2016. Enterprise architecture and new generation information systems. CRC Press.
Tarhini, A., Al-Dmour, R.H. and Obeidat, B.Y., 2015. STRATEGIC IT-BUSINESS ALIGNMENT AS
MANAGERS’EXPLORATIVE AND EXPLOITATIVE STRATEGIES. European Scientific Journal,
ESJ, 11(7).
Loebbecke, C. and Picot, A., 2015. Reflections on societal and business model transformation arising
from digitization and big data analytics: A research agenda. The Journal of Strategic Information
Systems, 24(3), pp.149-157.
Harun, H. and Hashim, M., 2017. Strategic Information Systems Planning: a Review of Its Concept,
Definitions and Stages of Development. International Journal of Research In Science & Engineering, 3(2),
pp.432-441.
1 out of 16
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
© 2024 | Zucol Services PVT LTD | All rights reserved.





