Comprehensive Network Addressing and Security Design for UMUC
VerifiedAdded on 2023/06/14
|8
|2018
|225
Report
AI Summary
This report provides a comprehensive network design proposal for a school (UMUC) building, focusing on network addressing and security. It includes a subnet chart detailing IP address ranges for various areas like classrooms, labs, and offices. The report discusses subnetting, firewall selection (packet filtering, stateful inspection, circuit level gateway), Intrusion Detection and Prevention Systems (IDS/IPS), and DMZ implementation for enhanced security. Physical security measures like mantraps, door access controls, and video surveillance are also outlined. Additionally, the report addresses social engineering attacks and recommends user education and administrator accounts for network devices to prevent malware introduction. The document emphasizes the importance of securing the network from both internal and external threats and implementing policies for personal device usage within the school.

Running head: NETWORK ADDRESSING 1
Network Addressing
Prince peprah
Umuc
Network Addressing
Prince peprah
Umuc
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
NETWORK ADDRESSING
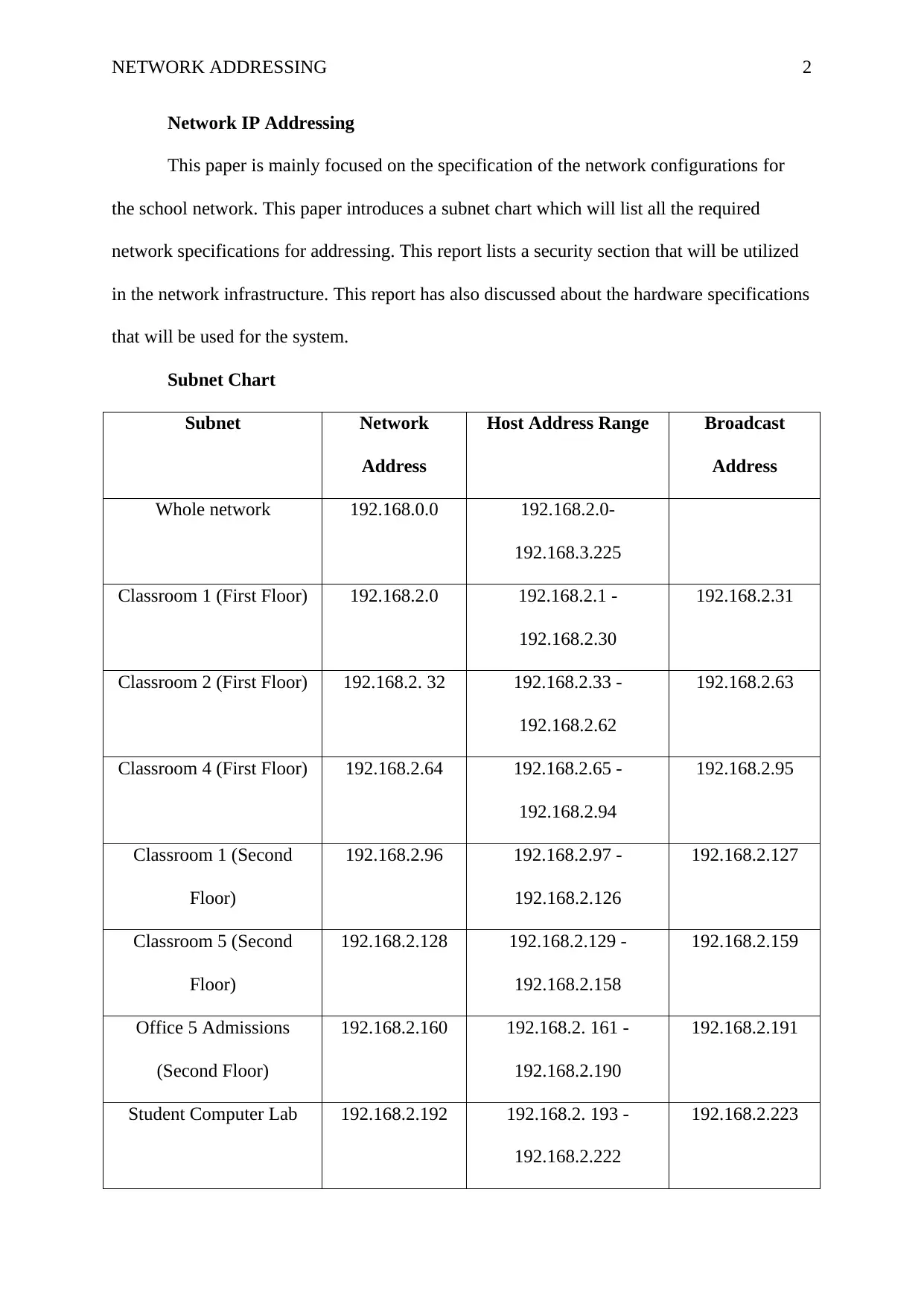
Network IP Addressing
This paper is mainly focused on the specification of the network configurations for
the school network. This paper introduces a subnet chart which will list all the required
network specifications for addressing. This report lists a security section that will be utilized
in the network infrastructure. This report has also discussed about the hardware specifications
that will be used for the system.
Subnet Chart
Subnet Network
Address
Host Address Range Broadcast
Address
Whole network 192.168.0.0 192.168.2.0-
192.168.3.225
Classroom 1 (First Floor) 192.168.2.0 192.168.2.1 -
192.168.2.30
192.168.2.31
Classroom 2 (First Floor) 192.168.2. 32 192.168.2.33 -
192.168.2.62
192.168.2.63
Classroom 4 (First Floor) 192.168.2.64 192.168.2.65 -
192.168.2.94
192.168.2.95
Classroom 1 (Second
Floor)
192.168.2.96 192.168.2.97 -
192.168.2.126
192.168.2.127
Classroom 5 (Second
Floor)
192.168.2.128 192.168.2.129 -
192.168.2.158
192.168.2.159
Office 5 Admissions
(Second Floor)
192.168.2.160 192.168.2. 161 -
192.168.2.190
192.168.2.191
Student Computer Lab 192.168.2.192 192.168.2. 193 -
192.168.2.222
192.168.2.223
2
Network IP Addressing
This paper is mainly focused on the specification of the network configurations for
the school network. This paper introduces a subnet chart which will list all the required
network specifications for addressing. This report lists a security section that will be utilized
in the network infrastructure. This report has also discussed about the hardware specifications
that will be used for the system.
Subnet Chart
Subnet Network
Address
Host Address Range Broadcast
Address
Whole network 192.168.0.0 192.168.2.0-
192.168.3.225
Classroom 1 (First Floor) 192.168.2.0 192.168.2.1 -
192.168.2.30
192.168.2.31
Classroom 2 (First Floor) 192.168.2. 32 192.168.2.33 -
192.168.2.62
192.168.2.63
Classroom 4 (First Floor) 192.168.2.64 192.168.2.65 -
192.168.2.94
192.168.2.95
Classroom 1 (Second
Floor)
192.168.2.96 192.168.2.97 -
192.168.2.126
192.168.2.127
Classroom 5 (Second
Floor)
192.168.2.128 192.168.2.129 -
192.168.2.158
192.168.2.159
Office 5 Admissions
(Second Floor)
192.168.2.160 192.168.2. 161 -
192.168.2.190
192.168.2.191
Student Computer Lab 192.168.2.192 192.168.2. 193 -
192.168.2.222
192.168.2.223
2

NETWORK ADDRESSING
Library 192.168.2. 224 192.168.2.225 -
192.168.2.254
192.168.2.255
Wi-Fi Network 192.168.3.0 192.168.3.1 -
192.168.3.224
192.168.3.225
The process of subdividing a network to smaller subnetworks (subnets) is referred to
as subnetting. It is basically used for dividing the whole IP address range into similar ports
which can be used for going into each device in the network. It is also used for addressing the
computers belonging to a particular subnet with an identical and similar IP address. This
process is carried out when there is an extension of subnet mast default boundary. The mask
that subdivides IP address to create a network and host addresses is called subnet mask. A
subnet mask is used to mask the IP address and divide it into two various types of addresses,
the host address and the network address.
SECTION 2: Network Security
Firewall Selection
A firewall protects local networks from the outside global networks. That is, all data
packets entering or leaving the network have to pass through the firewall and it screens them
to pass through, modify or block them. A properly implemented firewall can be extremely
effective in reducing or eliminating many network threats [1].
The segmented network architecture proposed for the building is very efficient in
controlling threats to the network. This is due to the subdividing the network into sub-
networks which allows prevention of hosts belonging to a subnetwork invisible from outside
world. The most efficient types of firewalls to implement in this network are packet filtering
3
Library 192.168.2. 224 192.168.2.225 -
192.168.2.254
192.168.2.255
Wi-Fi Network 192.168.3.0 192.168.3.1 -
192.168.3.224
192.168.3.225
The process of subdividing a network to smaller subnetworks (subnets) is referred to
as subnetting. It is basically used for dividing the whole IP address range into similar ports
which can be used for going into each device in the network. It is also used for addressing the
computers belonging to a particular subnet with an identical and similar IP address. This
process is carried out when there is an extension of subnet mast default boundary. The mask
that subdivides IP address to create a network and host addresses is called subnet mask. A
subnet mask is used to mask the IP address and divide it into two various types of addresses,
the host address and the network address.
SECTION 2: Network Security
Firewall Selection
A firewall protects local networks from the outside global networks. That is, all data
packets entering or leaving the network have to pass through the firewall and it screens them
to pass through, modify or block them. A properly implemented firewall can be extremely
effective in reducing or eliminating many network threats [1].
The segmented network architecture proposed for the building is very efficient in
controlling threats to the network. This is due to the subdividing the network into sub-
networks which allows prevention of hosts belonging to a subnetwork invisible from outside
world. The most efficient types of firewalls to implement in this network are packet filtering
3
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

NETWORK ADDRESSING
firewall, stateful inspection firewall, and circuit level gateway firewall. The packet filtering
firewall is used to work at routers and switching junctions and compares received packets to a
set of established criteria. The stateful inspection firewall will help in examining the packets
and tracking whether they are being generated in established TCP sessions. Lastly, the circuit
level gateway firewall is used to determine malicious contents in the internet.
The packet filtering gateway type of firewall will help in regulating sub-network
boundaries access through examining the IP addresses of data packets. Data packets are
termed as small units of data which are used in IP address transmission. This is done from
any of the source subnets or its destination or by carrying out port filtering (filtering of the
ports) for each data packet from any of the subnets to another. Packets that are deemed to be
unacceptable in light of this firewall security policy will be filtered out. The choice of this
type of firewall is based on its simplicity in implementing and its common effectiveness.
In order to have a consideration on the context of the data packets sending and
received by various hosts within the sub-networks, a stateful inspection type of firewall can
be implemented [4]. This is because this type of firewall keeps track of host’s activities
within the network. This is very important as it will be able to identify any host within the
sub-networks that may represent a threat to the entire network and if the threat exceeds the
firewall security policy, then the traffic directed to or from the host is blocked. This type of
firewall application is very effective and its implementation in the proposed network will
ensure total security from port scanner attacks. A port scanner attack is used by an attacker to
send packets with varying destinations which helps in determining the resources used for the
connection like the OS.
Another choice of a firewall to implement in this network setting is the circuit-level
gateway. This works in the session layer of the OSI model or the application and transport
layer of TCP/IP model. This type of firewall examines incoming or outgoing data packets IP
4
firewall, stateful inspection firewall, and circuit level gateway firewall. The packet filtering
firewall is used to work at routers and switching junctions and compares received packets to a
set of established criteria. The stateful inspection firewall will help in examining the packets
and tracking whether they are being generated in established TCP sessions. Lastly, the circuit
level gateway firewall is used to determine malicious contents in the internet.
The packet filtering gateway type of firewall will help in regulating sub-network
boundaries access through examining the IP addresses of data packets. Data packets are
termed as small units of data which are used in IP address transmission. This is done from
any of the source subnets or its destination or by carrying out port filtering (filtering of the
ports) for each data packet from any of the subnets to another. Packets that are deemed to be
unacceptable in light of this firewall security policy will be filtered out. The choice of this
type of firewall is based on its simplicity in implementing and its common effectiveness.
In order to have a consideration on the context of the data packets sending and
received by various hosts within the sub-networks, a stateful inspection type of firewall can
be implemented [4]. This is because this type of firewall keeps track of host’s activities
within the network. This is very important as it will be able to identify any host within the
sub-networks that may represent a threat to the entire network and if the threat exceeds the
firewall security policy, then the traffic directed to or from the host is blocked. This type of
firewall application is very effective and its implementation in the proposed network will
ensure total security from port scanner attacks. A port scanner attack is used by an attacker to
send packets with varying destinations which helps in determining the resources used for the
connection like the OS.
Another choice of a firewall to implement in this network setting is the circuit-level
gateway. This works in the session layer of the OSI model or the application and transport
layer of TCP/IP model. This type of firewall examines incoming or outgoing data packets IP
4
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

NETWORK ADDRESSING
addresses from sub-networks and determines whether they are being sent or received from
the target network. However, the main disadvantages of this are that it can only handle the
TCP connections. In addition, active contents are not scanned by this type of firewall.
IDS and IPS selection
In order to maintain the network security, ways of detecting and preventing attacks
from happening on the network are required. This is done by introducing Intrusion Detection
and Prevention Systems (IDS/IPS) into to the network for monitoring traffic and identifying
whether something malicious is happening. In order to respond to any suspicious event
happening on the network, it needs to be detected [2]. The most appropriate IDS are the
Network-based IDS as it monitors network traffic and then produces an alert when an
abnormal activity is detected. This alert is made by the system on getting intrusions which are
then sent to the administrators who can then undertake several mechanisms for mitigations.
Also, Host-based IDS can be selected as it monitors activities like logs and files in
specific host machines on the network and also produces alerts. The use of the host based
IDS can be used in the internal monitoring of the systems and monitoring of the network
packets. However, IDS just monitors traffic on a network but cannot take action against
malicious activities. That is where IPS comes in to proactively react to the identified
activities and prevent attacks. It may carry out a firewall reconfiguration or reset a transport
connection protocol when it looks like an attack is going on. Selection of IDS and IPS is very
important in securing the network from both internal and external intrusions.
DMZ Implementation
A demilitarized zone (DMZ) is a local subnet within a network where administrator places
their internet services like email and web servers intended for public access [3]. It is placed
between the public (mainly internet) and a protected network. Setting up a public FTP server
on DMZ ensures users are served with files on the network. A FTP server is used to setup the
5
addresses from sub-networks and determines whether they are being sent or received from
the target network. However, the main disadvantages of this are that it can only handle the
TCP connections. In addition, active contents are not scanned by this type of firewall.
IDS and IPS selection
In order to maintain the network security, ways of detecting and preventing attacks
from happening on the network are required. This is done by introducing Intrusion Detection
and Prevention Systems (IDS/IPS) into to the network for monitoring traffic and identifying
whether something malicious is happening. In order to respond to any suspicious event
happening on the network, it needs to be detected [2]. The most appropriate IDS are the
Network-based IDS as it monitors network traffic and then produces an alert when an
abnormal activity is detected. This alert is made by the system on getting intrusions which are
then sent to the administrators who can then undertake several mechanisms for mitigations.
Also, Host-based IDS can be selected as it monitors activities like logs and files in
specific host machines on the network and also produces alerts. The use of the host based
IDS can be used in the internal monitoring of the systems and monitoring of the network
packets. However, IDS just monitors traffic on a network but cannot take action against
malicious activities. That is where IPS comes in to proactively react to the identified
activities and prevent attacks. It may carry out a firewall reconfiguration or reset a transport
connection protocol when it looks like an attack is going on. Selection of IDS and IPS is very
important in securing the network from both internal and external intrusions.
DMZ Implementation
A demilitarized zone (DMZ) is a local subnet within a network where administrator places
their internet services like email and web servers intended for public access [3]. It is placed
between the public (mainly internet) and a protected network. Setting up a public FTP server
on DMZ ensures users are served with files on the network. A FTP server is used to setup the
5

NETWORK ADDRESSING
transfer of files among clients. While a mail server enables users to access services remotely,
implementation of a DMZ on the network provides extra security layer on the local network
from an external attack which helps in preventing direct access to the network resources.
Physical Security Measures
In a network, the reliance should not only be on technology to control access but also
on information about physical measures for security as well. Some of the security control
measures that ought to be put in place are mantraps [5]. These are designed as breezeways
where the entering of one user causes the door for exit to get closed. All doors are normally
unlocked and opening one of the doors causes all others to close. It can be used to control
people walking within an area.
Also, the use of door access controls is a super way to regulate access to network
resources like the server room. A door access control is comprised of a network specification
which helps in providing authentication controls to the users. The use of authentication
measures helps in securing the access to the network such that all the associated
administrators can be able to access them. Another security control is by installing video
surveillance like CCTV camera (surveillance camera) in critical locations and monitor
activities all the time [6]. Posting security guards in the building also offer security as they
provide physical protection and also use of access cards to validate the identification of
existing users.
Additional Network Security
There are also other malicious schemes by users or a network or external intruders
which can cause harm to the entire network if allowed to be performed. These may include
social engineering attacks where characters use trickery to gain access to a network [7].
Mostly they are carried out online through sending or receiving malicious emails,
downloading suspicious software, sharing of personal details like passwords. The basic
6
transfer of files among clients. While a mail server enables users to access services remotely,
implementation of a DMZ on the network provides extra security layer on the local network
from an external attack which helps in preventing direct access to the network resources.
Physical Security Measures
In a network, the reliance should not only be on technology to control access but also
on information about physical measures for security as well. Some of the security control
measures that ought to be put in place are mantraps [5]. These are designed as breezeways
where the entering of one user causes the door for exit to get closed. All doors are normally
unlocked and opening one of the doors causes all others to close. It can be used to control
people walking within an area.
Also, the use of door access controls is a super way to regulate access to network
resources like the server room. A door access control is comprised of a network specification
which helps in providing authentication controls to the users. The use of authentication
measures helps in securing the access to the network such that all the associated
administrators can be able to access them. Another security control is by installing video
surveillance like CCTV camera (surveillance camera) in critical locations and monitor
activities all the time [6]. Posting security guards in the building also offer security as they
provide physical protection and also use of access cards to validate the identification of
existing users.
Additional Network Security
There are also other malicious schemes by users or a network or external intruders
which can cause harm to the entire network if allowed to be performed. These may include
social engineering attacks where characters use trickery to gain access to a network [7].
Mostly they are carried out online through sending or receiving malicious emails,
downloading suspicious software, sharing of personal details like passwords. The basic
6
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

NETWORK ADDRESSING
approach to prevent this is to educate the network users and support staff on how to identify
these occurrences and how to avoid them. In order to prevent the introduction of malware
onto the network by either students or faculty, it is advisable to create administrator accounts
on network devices like routers and servers to authenticate any introduction of unwanted or
unknown software into the network. The administrator accounts will have access to the
network resources and will be able to monitor the traffic on the system. Creating user
accounts for students and faculty is also good to ensure only authenticated users can access
internal or external network resources.
According to the policies used to control the usage of devices like smartphones and
laptops in the school building, any personal device that gets damaged will be at the user’s
own risk. For this reason, UMUC will not be responsible for any such problems
7
approach to prevent this is to educate the network users and support staff on how to identify
these occurrences and how to avoid them. In order to prevent the introduction of malware
onto the network by either students or faculty, it is advisable to create administrator accounts
on network devices like routers and servers to authenticate any introduction of unwanted or
unknown software into the network. The administrator accounts will have access to the
network resources and will be able to monitor the traffic on the system. Creating user
accounts for students and faculty is also good to ensure only authenticated users can access
internal or external network resources.
According to the policies used to control the usage of devices like smartphones and
laptops in the school building, any personal device that gets damaged will be at the user’s
own risk. For this reason, UMUC will not be responsible for any such problems
7
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

NETWORK ADDRESSING
References
[1] Zuk, Nir, and Kowsik Guruswamy. "Multi-method gateway-based network security
systems and methods." U.S. Patent 8,370,936, issued February 5, 2013.
[2] Modi, Chirag, Dhiren Patel, Bhavesh Borisaniya, Hiren Patel, Avi Patel, and
Muttukrishnan Rajarajan. "A survey of intrusion detection techniques in
cloud." Journal of Network and Computer Applications 36, no. 1 (2013): 42-57.
[3] Rojas, Carlos, and Peter Morell. "Guidelines for Industrial Ethernet infrastructure
implementation: A control engineer's guide." In Cement Industry Technical
Conference, 2010 IEEE-IAS/PCA 52nd, pp. 1-18. IEEE, 2010.
[4] Stouffer, Keith, Joe Falco, and Karen Scarfone. "Guide to industrial control systems
(ICS) security." NIST special publication 800, no. 82 (2011): 16-16.
[5] Allsopp, Wil. Unauthorised access: physical penetration testing for IT security teams.
John Wiley & Sons, 2010.
[6] Welsh, Brandon C., and David P. Farrington. "Public area CCTV and crime
prevention: an updated systematic review and meta‐analysis." Justice Quarterly 26,
no. 4 (2009): 716-745.
[7] Workman, Michael. "Wisecrackers: A theory‐grounded investigation of phishing and
pretext social engineering threats to information security." Journal of the Association
for Information Science and Technology 59, no. 4 (2008): 662-674.
8
References
[1] Zuk, Nir, and Kowsik Guruswamy. "Multi-method gateway-based network security
systems and methods." U.S. Patent 8,370,936, issued February 5, 2013.
[2] Modi, Chirag, Dhiren Patel, Bhavesh Borisaniya, Hiren Patel, Avi Patel, and
Muttukrishnan Rajarajan. "A survey of intrusion detection techniques in
cloud." Journal of Network and Computer Applications 36, no. 1 (2013): 42-57.
[3] Rojas, Carlos, and Peter Morell. "Guidelines for Industrial Ethernet infrastructure
implementation: A control engineer's guide." In Cement Industry Technical
Conference, 2010 IEEE-IAS/PCA 52nd, pp. 1-18. IEEE, 2010.
[4] Stouffer, Keith, Joe Falco, and Karen Scarfone. "Guide to industrial control systems
(ICS) security." NIST special publication 800, no. 82 (2011): 16-16.
[5] Allsopp, Wil. Unauthorised access: physical penetration testing for IT security teams.
John Wiley & Sons, 2010.
[6] Welsh, Brandon C., and David P. Farrington. "Public area CCTV and crime
prevention: an updated systematic review and meta‐analysis." Justice Quarterly 26,
no. 4 (2009): 716-745.
[7] Workman, Michael. "Wisecrackers: A theory‐grounded investigation of phishing and
pretext social engineering threats to information security." Journal of the Association
for Information Science and Technology 59, no. 4 (2008): 662-674.
8
1 out of 8
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.





