IoT Network Security Analysis: Issues, Vulnerabilities & Solutions
VerifiedAdded on 2023/04/11
|14
|2059
|356
Report
AI Summary
This report presents a comprehensive analysis of a computer network, focusing on security issues and vulnerabilities within a medium-sized organization's IT infrastructure, particularly concerning Internet of Things (IoT) devices. The analysis identifies security flaws related to the Wireless Router (Linksys WRT1900AC) and the Switch (Netgear GS116PP-100AJS), highlighting weak authentication systems and remote password retrieval vulnerabilities. Further issues include improper network design, reliance on WEP shared key authentication, and vulnerabilities in the firewall due to a single firewall setup and lack of updates. The report references real-world attack scenarios and proposes countermeasures such as replacing the Linksys router with a more secure Netgear model, upgrading to managed Netgear switches, adopting Wi-Fi Protected Access (WPA) for wireless security, implementing a proxy server to shield devices, subnetting the network, and updating and adding more firewalls. The appendices provide diagrams illustrating correct network topology and firewall configurations.

NETWORK ANALYSIS REPORT
Cover Page
A REPORT ON THE ANALYSIS OF A COMPUTER NETWORK FOR SECURITY ISSUES,
VULNERABILITIES AND POSSIBLE SOLUTIONS
Cover Page
A REPORT ON THE ANALYSIS OF A COMPUTER NETWORK FOR SECURITY ISSUES,
VULNERABILITIES AND POSSIBLE SOLUTIONS
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

NETWORK ANALYSIS REPORT 2
Table of Contents
Cover Page…………………………………………………………………………………..1
Table of Contents……………………………………………………………………………2
Introduction………………………………………………………………………………….3
Security Issues……………………………………………………………………………….4
Attack Scenarios……………………………………………………………………………..6
Vulnerabilities………………………………………………………………………………..7
Proposed Countermeasure(s)/Solution(s)……………………………………………………8
References…………………………………………………………………………………..9
Appendices ………………………………………………………………………………...11
Table of Contents
Cover Page…………………………………………………………………………………..1
Table of Contents……………………………………………………………………………2
Introduction………………………………………………………………………………….3
Security Issues……………………………………………………………………………….4
Attack Scenarios……………………………………………………………………………..6
Vulnerabilities………………………………………………………………………………..7
Proposed Countermeasure(s)/Solution(s)……………………………………………………8
References…………………………………………………………………………………..9
Appendices ………………………………………………………………………………...11

NETWORK ANALYSIS REPORT 3
Introduction
The advent of the Internet of Things (IoT) has led to development of interconnected systems that
can share key information from their surroundings for decision making purposes (Habibi, Midi,
Mudgerikar & Bertino, 2017). Medium sized organizations have integrated IoT devices to help
automate functions that could have otherwise required human input. However there also comes
the aspect of security in how the devices interact and how the information is protected from
unauthorized access and compromise by cyber criminals. Besides these devices having security
mechanisms of their own and the existence of several security protocols and techniques to
protect the information exchanged between IoT devices, the system cannot be completely secure.
Cyber criminals are always on the look for these vulnerabilities and other overlooked security
issues so that they can use them to gain access to protected information. Even the seemingly least
security issues caused by device manufacturers can be best loopholes for hackers(Habibi, Midi,
Mudgerikar & Bertino, 2017).
This report seeks to analyse such a system in a medium sized organization network to identify
issues and vulnerabilities related to the IoT devices and the IT infrastructure. Finally solutions to
address the issues are addressed.
Introduction
The advent of the Internet of Things (IoT) has led to development of interconnected systems that
can share key information from their surroundings for decision making purposes (Habibi, Midi,
Mudgerikar & Bertino, 2017). Medium sized organizations have integrated IoT devices to help
automate functions that could have otherwise required human input. However there also comes
the aspect of security in how the devices interact and how the information is protected from
unauthorized access and compromise by cyber criminals. Besides these devices having security
mechanisms of their own and the existence of several security protocols and techniques to
protect the information exchanged between IoT devices, the system cannot be completely secure.
Cyber criminals are always on the look for these vulnerabilities and other overlooked security
issues so that they can use them to gain access to protected information. Even the seemingly least
security issues caused by device manufacturers can be best loopholes for hackers(Habibi, Midi,
Mudgerikar & Bertino, 2017).
This report seeks to analyse such a system in a medium sized organization network to identify
issues and vulnerabilities related to the IoT devices and the IT infrastructure. Finally solutions to
address the issues are addressed.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

NETWORK ANALYSIS REPORT 4
Security Issues
The security issues are divided into those that concern the IoT devices and those that concern the
IT infrastructure.
Security issues related to the IoT devices
After an analysis of the IoT devices in the network, two devices were identified to pose a
security threat to the network.
The Wireless Router (Linksys WRT1900AC)
The wireless router connects the computer in LAN 1 with the Wireless Temperature sensor. The
truth is, the router does indeed possess a security issue. This because the router has a weak
authentication system in place. The wireless router can be bypassed using multiple Common
Gateway Interface scripts that give one unrestricted access to the device’s administrative
functions without prompting a password (Habibi, Midi, Mudgerikar & Bertino, 2017). The
extensive vulnerability can be utilized by a cyber-criminal to give them unauthenticated access to
the router’s administrative logins thereby giving them full control of the router thereby
compromising the network.
The Switch (Netgear GS116PP-100AJS)
The Netgear switch has a security issue that can allow the attacker to remotely retrieve the login
passwords for users in the network (Szewczyk & Macdonald, 2017). All an attacker needs to do
is to access the web panel for authentication. Once the verification is canceled and recovery of
passwords disabled, the attacker will be redirected to a page where the reset password token is
exposed. If the attacker enters the correct token, they can access the administrator password for
the router, thereby compromising the whole network (Szewczyk & Macdonald, 2017).
IT Infrastructure
Improper network design and topology
A glance at the network and how the computers are connected gives a glimpse of a possible
security flaw in the network architecture. All computers and servers including the proxy server in
the network have a direct access to the Internet (Lapidous & Arsitov, 2018). The advantage of
this arrangement is that Internet access is fast. However, from a security perspective, this means
that when the computers access the Internet, each is identified with its own IP address which
makes it easy for hackers to identify the computers and initiate access to the network. Important
servers like the email servers, file servers and directory server are exposed to the different
security threats available on the Internet and with a weak firewall, accessing them becomes easy
(Habibi, Midi, Mudgerikar & Bertino, 2017).
Security Issues
The security issues are divided into those that concern the IoT devices and those that concern the
IT infrastructure.
Security issues related to the IoT devices
After an analysis of the IoT devices in the network, two devices were identified to pose a
security threat to the network.
The Wireless Router (Linksys WRT1900AC)
The wireless router connects the computer in LAN 1 with the Wireless Temperature sensor. The
truth is, the router does indeed possess a security issue. This because the router has a weak
authentication system in place. The wireless router can be bypassed using multiple Common
Gateway Interface scripts that give one unrestricted access to the device’s administrative
functions without prompting a password (Habibi, Midi, Mudgerikar & Bertino, 2017). The
extensive vulnerability can be utilized by a cyber-criminal to give them unauthenticated access to
the router’s administrative logins thereby giving them full control of the router thereby
compromising the network.
The Switch (Netgear GS116PP-100AJS)
The Netgear switch has a security issue that can allow the attacker to remotely retrieve the login
passwords for users in the network (Szewczyk & Macdonald, 2017). All an attacker needs to do
is to access the web panel for authentication. Once the verification is canceled and recovery of
passwords disabled, the attacker will be redirected to a page where the reset password token is
exposed. If the attacker enters the correct token, they can access the administrator password for
the router, thereby compromising the whole network (Szewczyk & Macdonald, 2017).
IT Infrastructure
Improper network design and topology
A glance at the network and how the computers are connected gives a glimpse of a possible
security flaw in the network architecture. All computers and servers including the proxy server in
the network have a direct access to the Internet (Lapidous & Arsitov, 2018). The advantage of
this arrangement is that Internet access is fast. However, from a security perspective, this means
that when the computers access the Internet, each is identified with its own IP address which
makes it easy for hackers to identify the computers and initiate access to the network. Important
servers like the email servers, file servers and directory server are exposed to the different
security threats available on the Internet and with a weak firewall, accessing them becomes easy
(Habibi, Midi, Mudgerikar & Bertino, 2017).
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

NETWORK ANALYSIS REPORT 5
Wireless Network with WEP shared key authentication
Wired Equivalent Privacy (WEP) is an older (compared to the latest) encryption procedure that
used to secure data transferred in wireless networks. Its authentication key is shared by all
devices across the network (Al-Janabi, Al-Shourbaji, Shojafar & Shamshirband, 2017). This
poses a security issue in that a cyber-criminal can use freely available programs to crack the key
easily. Even without cracking software, it is possible for the attackers to eavesdrop the
communication between devices in the wireless network and gather enough information to create
the key hence gaining unauthorised access to the router (Al-Janabi, Al-Shourbaji, Shojafar &
Shamshirband, 2017).
Wireless Network with WEP shared key authentication
Wired Equivalent Privacy (WEP) is an older (compared to the latest) encryption procedure that
used to secure data transferred in wireless networks. Its authentication key is shared by all
devices across the network (Al-Janabi, Al-Shourbaji, Shojafar & Shamshirband, 2017). This
poses a security issue in that a cyber-criminal can use freely available programs to crack the key
easily. Even without cracking software, it is possible for the attackers to eavesdrop the
communication between devices in the wireless network and gather enough information to create
the key hence gaining unauthorised access to the router (Al-Janabi, Al-Shourbaji, Shojafar &
Shamshirband, 2017).

NETWORK ANALYSIS REPORT 6
Attack Scenarios
According to Constantin (2016) on Network World, in 2016 December, 2016, researchers from
Kaspersky Lab discovered a malicious program that could hack into multiple models of Linksys
routers in local networks using the default credentials.
In 2016, Wired reported on its website that a security researcher named Andrew Rollins had
discovered a flaw in Netgear switches. When he reported to the company and got no response, he
went public, triggering Homeland Security to warn the public of possible attacks. Later on,
Netgear admitted that the problem was there, before releasing security patches to solve it
(Newman et al., 2016).
In March 2016, the New York Times reported a massive cyber-attack on a health insurer,
Primera Blue Cross that exposed the health records of up to 11 million customers. Sensitive
details like names, social security number and even bank account information were exposed
(Granville, 2016). The attack was rumoured to have been enabled by the network topology and
design which made it easier for hackers to track exactly where to find the information.
In June 2014, a hacking group named Rex Mundi went public, claiming it had hacked the
website of European Domino, a pizza chain company, and managed to retrieve customer records
for six hundred and fifty thousand customers (Chickowski, 2014). The hacker group threatened
to send the information to the public unless Domino pizza company paid a ransom. Even though
Domino downplayed the situation by assuring its user that the stolen information contained only
passwords, the hackers had made their mark. It was discovered that the hackers had used the
WEP security feature vulnerability for the WiFi setup up in Domino pizza shops to get access to
the information, claiming that a weak encryption mechanism enabled them to easily decrypt the
data.
Attack Scenarios
According to Constantin (2016) on Network World, in 2016 December, 2016, researchers from
Kaspersky Lab discovered a malicious program that could hack into multiple models of Linksys
routers in local networks using the default credentials.
In 2016, Wired reported on its website that a security researcher named Andrew Rollins had
discovered a flaw in Netgear switches. When he reported to the company and got no response, he
went public, triggering Homeland Security to warn the public of possible attacks. Later on,
Netgear admitted that the problem was there, before releasing security patches to solve it
(Newman et al., 2016).
In March 2016, the New York Times reported a massive cyber-attack on a health insurer,
Primera Blue Cross that exposed the health records of up to 11 million customers. Sensitive
details like names, social security number and even bank account information were exposed
(Granville, 2016). The attack was rumoured to have been enabled by the network topology and
design which made it easier for hackers to track exactly where to find the information.
In June 2014, a hacking group named Rex Mundi went public, claiming it had hacked the
website of European Domino, a pizza chain company, and managed to retrieve customer records
for six hundred and fifty thousand customers (Chickowski, 2014). The hacker group threatened
to send the information to the public unless Domino pizza company paid a ransom. Even though
Domino downplayed the situation by assuring its user that the stolen information contained only
passwords, the hackers had made their mark. It was discovered that the hackers had used the
WEP security feature vulnerability for the WiFi setup up in Domino pizza shops to get access to
the information, claiming that a weak encryption mechanism enabled them to easily decrypt the
data.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

NETWORK ANALYSIS REPORT 7
Vulnerabilities
Besides the above security issues, there exists several vulnerabilities in the network that make
the network weak and can be accessed and utilized by attackers to compromise the network. The
vulnerabilities are in the firewall which is the defence mechanism that monitors and filters
information transferred from the LAN to the Internet.
One set of firewall
The network consists of different devices; servers and client computers, all of which need to be
protected from outside attacks. The fact that only one set of firewall protects the network and all
its devices against attacks from the Internet leaves the whole network vulnerable (Jones et al.,
2018). Once attackers bypass that firewall, they have the whole network at their disposal.
Firewall not updated
The second vulnerability is that the firewall is not updated. Like every software, updates comes
with new fixes for security flaws identified by developers. By failing to update the firewall,
flaws in the older version make the network extremely vulnerable since they can be exploited by
attackers (Glazemakers et al., 2017).
Vulnerabilities
Besides the above security issues, there exists several vulnerabilities in the network that make
the network weak and can be accessed and utilized by attackers to compromise the network. The
vulnerabilities are in the firewall which is the defence mechanism that monitors and filters
information transferred from the LAN to the Internet.
One set of firewall
The network consists of different devices; servers and client computers, all of which need to be
protected from outside attacks. The fact that only one set of firewall protects the network and all
its devices against attacks from the Internet leaves the whole network vulnerable (Jones et al.,
2018). Once attackers bypass that firewall, they have the whole network at their disposal.
Firewall not updated
The second vulnerability is that the firewall is not updated. Like every software, updates comes
with new fixes for security flaws identified by developers. By failing to update the firewall,
flaws in the older version make the network extremely vulnerable since they can be exploited by
attackers (Glazemakers et al., 2017).
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

NETWORK ANALYSIS REPORT 8
Proposed Countermeasure(s)/Solution(s)
The following are the proposed countermeasures and solutions to the identified security issues
and vulnerabilities.
Linksys routers have been known to possess the identified security flaw. Therefore, the solution
is to replace the Linksys router with Netgear wireless router which is more secure. This owes to
the fact that Netgear constantly reviews and releases security patches every time they notice a
flaw in the network system of the routers or any device they manufacture for that matter
(Bednarczyk, 2017).
In order to fix the security flaw in the Netgear Switches, the best solution is upgrading to
managed Netgear switches. With managed switches protocols to protect the network and redirect
requests without exposing sensitive data can be set accordingly (Davie et al., 2017).
To handle the shortcomings of WEP, the solution is to use Wi-fi Protected Access (WPA) which
is more secure uses advanced security features like integrity checks to ensure attackers cannot
intercept messages send over the network. In fact WPA was created to replace WEP and deal
with the vulnerabilities WEP brought about (Sari & Karay, 2015). To enhance the security even
better, a WPA2 can be used as well. WPA2 is an improvement of WPA.
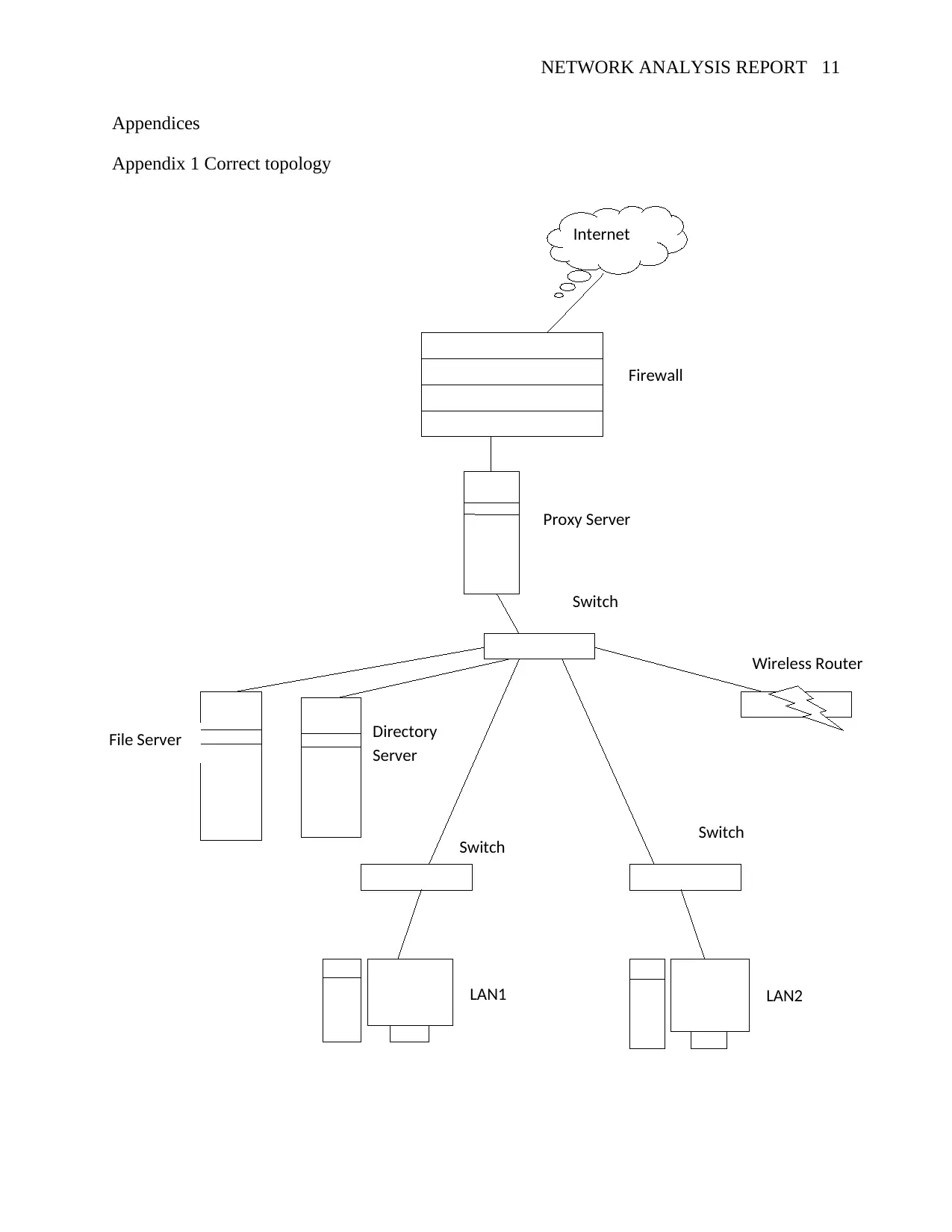
The best network topology that ensures all devices in the LAN are protected and there IP address
hidden is by ensuring that all other client computers and servers access the Internet through the
proxy server. With a proxy server, only one IP address is seen thereby shielding the other devices
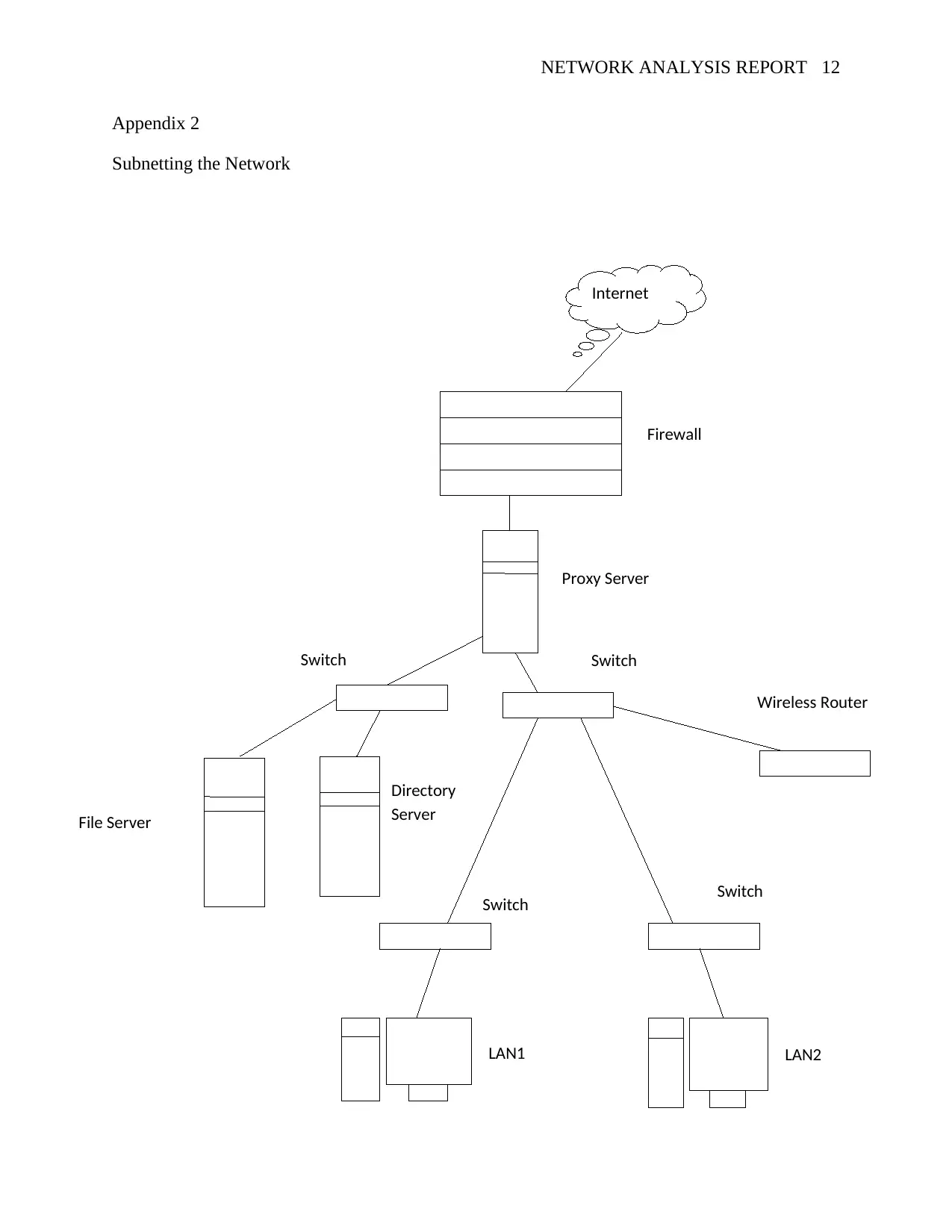
from attacks (See Appendix 1). The other solution would be subnetting the network; this not only
eases the traffic flow but also makes it harder for hackers to trace down to a particular device in
the network (Abdou, Van Oorschot & Wan, 2018) (See Appendix 2).
The vulnerabilities found in the firewall can be fixed by updating the edge firewall which
ensures it has the latest security patches hence more capable of preventing attacks. The second
vulnerability can fixed by setting up more firewalls, one for each LAN; LAN1 and LAN2, and a
different one for the servers, that is server firewall (Li et al.,2016). This will ensure every device
is more secure and hard for attackers attack them. (See Appendix 3)
Proposed Countermeasure(s)/Solution(s)
The following are the proposed countermeasures and solutions to the identified security issues
and vulnerabilities.
Linksys routers have been known to possess the identified security flaw. Therefore, the solution
is to replace the Linksys router with Netgear wireless router which is more secure. This owes to
the fact that Netgear constantly reviews and releases security patches every time they notice a
flaw in the network system of the routers or any device they manufacture for that matter
(Bednarczyk, 2017).
In order to fix the security flaw in the Netgear Switches, the best solution is upgrading to
managed Netgear switches. With managed switches protocols to protect the network and redirect
requests without exposing sensitive data can be set accordingly (Davie et al., 2017).
To handle the shortcomings of WEP, the solution is to use Wi-fi Protected Access (WPA) which
is more secure uses advanced security features like integrity checks to ensure attackers cannot
intercept messages send over the network. In fact WPA was created to replace WEP and deal
with the vulnerabilities WEP brought about (Sari & Karay, 2015). To enhance the security even
better, a WPA2 can be used as well. WPA2 is an improvement of WPA.
The best network topology that ensures all devices in the LAN are protected and there IP address
hidden is by ensuring that all other client computers and servers access the Internet through the
proxy server. With a proxy server, only one IP address is seen thereby shielding the other devices
from attacks (See Appendix 1). The other solution would be subnetting the network; this not only
eases the traffic flow but also makes it harder for hackers to trace down to a particular device in
the network (Abdou, Van Oorschot & Wan, 2018) (See Appendix 2).
The vulnerabilities found in the firewall can be fixed by updating the edge firewall which
ensures it has the latest security patches hence more capable of preventing attacks. The second
vulnerability can fixed by setting up more firewalls, one for each LAN; LAN1 and LAN2, and a
different one for the servers, that is server firewall (Li et al.,2016). This will ensure every device
is more secure and hard for attackers attack them. (See Appendix 3)

NETWORK ANALYSIS REPORT 9
References
Abdou, A., Van Oorschot, P.C. and Wan, T., 2018. Comparative Analysis of Control Plane
Security of SDN and Conventional Networks. IEEE Communications Surveys &
Tutorials, 20(4), pp.3542-3559.
Al-Janabi, S., Al-Shourbaji, I., Shojafar, M. and Shamshirband, S., 2017. Survey of main
challenges (security and privacy) in wireless body area networks for healthcare
applications. Egyptian Informatics Journal, 18(2), pp.113-122.
Bednarczyk, M., 2017, April. Competition in the domain of wireless networks security. In XI
Conference on Reconnaissance and Electronic Warfare Systems (Vol. 10418, p.
104180A). International Society for Optics and Photonics.
Chickowski, E. (2014). 6 Recent Real-Life Cyber Extortion Scams. [online] Dark Reading.
Available at: https://www.darkreading.com/attacks-breaches/6-recent-real-life-cyber-
extortion-scams/d/d-id/1278774 [Accessed 19 Apr. 2019].
Constantin, L. (2016). Flaws let attackers hijack multiple Linksys router models. [online]
Network World. Available at: https://www.networkworld.com/article/3191250/flaws-let-
attackers-hijack-multiple-linksys-router-models.html [Accessed 19 Apr. 2019].
Davie, B., Chanda, A., Pfaff, B.L., Pettit, J. and Padmanabhan, A., NICIRA Inc, 2017. Database
protocol for exchanging forwarding state with hardware switches. U.S. Patent 9,699,070.
Glazemakers, K., Allansson, P.J., Cellerier, T.B.E., Valianos, K. and Weber, T.V., Cryptzone
North America Inc, 2017. Protecting network devices by a firewall. U.S. Patent
Application 15/488,132.
Granville, K. (2016). 9 Recent Cyberattacks Against Big Businesses. [online] Nytimes.com.
Available at: https://www.nytimes.com/interactive/2015/02/05/technology/recent-
cyberattacks.html [Accessed 19 Apr. 2019].
Habibi, J., Midi, D., Mudgerikar, A. and Bertino, E., 2017. Heimdall: Mitigating the internet of
insecure things. IEEE Internet of Things Journal, 4(4), pp.968-978.
Jones, T., Dali, A., Rao, M.R., Biradar, N., Madassery, J. and Liu, K., 2018, July. Towards a
Layered and Secure Internet-of-Things Testbed via Hybrid Mesh. In 2018 IEEE
International Congress on Internet of Things (ICIOT) (pp. 17-24). IEEE.
Lapidous, E. and Arsitov, A., Anchorfree Inc, 2018. Secure communications with internet-
enabled devices. U.S. Patent Application 10/135,791.
References
Abdou, A., Van Oorschot, P.C. and Wan, T., 2018. Comparative Analysis of Control Plane
Security of SDN and Conventional Networks. IEEE Communications Surveys &
Tutorials, 20(4), pp.3542-3559.
Al-Janabi, S., Al-Shourbaji, I., Shojafar, M. and Shamshirband, S., 2017. Survey of main
challenges (security and privacy) in wireless body area networks for healthcare
applications. Egyptian Informatics Journal, 18(2), pp.113-122.
Bednarczyk, M., 2017, April. Competition in the domain of wireless networks security. In XI
Conference on Reconnaissance and Electronic Warfare Systems (Vol. 10418, p.
104180A). International Society for Optics and Photonics.
Chickowski, E. (2014). 6 Recent Real-Life Cyber Extortion Scams. [online] Dark Reading.
Available at: https://www.darkreading.com/attacks-breaches/6-recent-real-life-cyber-
extortion-scams/d/d-id/1278774 [Accessed 19 Apr. 2019].
Constantin, L. (2016). Flaws let attackers hijack multiple Linksys router models. [online]
Network World. Available at: https://www.networkworld.com/article/3191250/flaws-let-
attackers-hijack-multiple-linksys-router-models.html [Accessed 19 Apr. 2019].
Davie, B., Chanda, A., Pfaff, B.L., Pettit, J. and Padmanabhan, A., NICIRA Inc, 2017. Database
protocol for exchanging forwarding state with hardware switches. U.S. Patent 9,699,070.
Glazemakers, K., Allansson, P.J., Cellerier, T.B.E., Valianos, K. and Weber, T.V., Cryptzone
North America Inc, 2017. Protecting network devices by a firewall. U.S. Patent
Application 15/488,132.
Granville, K. (2016). 9 Recent Cyberattacks Against Big Businesses. [online] Nytimes.com.
Available at: https://www.nytimes.com/interactive/2015/02/05/technology/recent-
cyberattacks.html [Accessed 19 Apr. 2019].
Habibi, J., Midi, D., Mudgerikar, A. and Bertino, E., 2017. Heimdall: Mitigating the internet of
insecure things. IEEE Internet of Things Journal, 4(4), pp.968-978.
Jones, T., Dali, A., Rao, M.R., Biradar, N., Madassery, J. and Liu, K., 2018, July. Towards a
Layered and Secure Internet-of-Things Testbed via Hybrid Mesh. In 2018 IEEE
International Congress on Internet of Things (ICIOT) (pp. 17-24). IEEE.
Lapidous, E. and Arsitov, A., Anchorfree Inc, 2018. Secure communications with internet-
enabled devices. U.S. Patent Application 10/135,791.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

NETWORK ANALYSIS REPORT 10
Li, F., Durumeric, Z., Czyz, J., Karami, M., Bailey, M., McCoy, D., Savage, S. and Paxson, V.,
2016. You've got vulnerability: Exploring effective vulnerability notifications. In 25th
{USENIX} Security Symposium ({USENIX} Security 16) (pp. 1033-1050).
Newman, L., Graff, G., Baker-Whitcomb, A., Greenberg, A. and Barrett, B. (2016). A Ton of
Popular Netgear Routers Are Vulnerable to Hackers---And There's No Easy Fix. [online]
WIRED. Available at: https://www.wired.com/2016/12/ton-popular-netgear-routers-
exposed-no-easy-fix/ [Accessed 19 Apr. 2019].
Sari, A. and Karay, M., 2015. Comparative analysis of wireless security protocols: WEP vs
WPA. International Journal of Communications, Network and System Sciences, 8(12),
p.483.
Li, F., Durumeric, Z., Czyz, J., Karami, M., Bailey, M., McCoy, D., Savage, S. and Paxson, V.,
2016. You've got vulnerability: Exploring effective vulnerability notifications. In 25th
{USENIX} Security Symposium ({USENIX} Security 16) (pp. 1033-1050).
Newman, L., Graff, G., Baker-Whitcomb, A., Greenberg, A. and Barrett, B. (2016). A Ton of
Popular Netgear Routers Are Vulnerable to Hackers---And There's No Easy Fix. [online]
WIRED. Available at: https://www.wired.com/2016/12/ton-popular-netgear-routers-
exposed-no-easy-fix/ [Accessed 19 Apr. 2019].
Sari, A. and Karay, M., 2015. Comparative analysis of wireless security protocols: WEP vs
WPA. International Journal of Communications, Network and System Sciences, 8(12),
p.483.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
NETWORK ANALYSIS REPORT 11
Appendices
Appendix 1 Correct topology
Internet
Firewall
Proxy Server
Switch
Switch Switch
LAN1 LAN2
Directory
Server
File Server
Wireless Router
Appendices
Appendix 1 Correct topology
Internet
Firewall
Proxy Server
Switch
Switch Switch
LAN1 LAN2
Directory
Server
File Server
Wireless Router
NETWORK ANALYSIS REPORT 12
Appendix 2
Subnetting the Network
Internet
Firewall
Proxy Server
Switch
Switch Switch
LAN1 LAN2
Directory
ServerFile Server
Switch
Wireless Router
Appendix 2
Subnetting the Network
Internet
Firewall
Proxy Server
Switch
Switch Switch
LAN1 LAN2
Directory
ServerFile Server
Switch
Wireless Router
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
1 out of 14
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2025 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.





