MN504 Networked Application Management T3: Wireshark Network Analysis
VerifiedAdded on 2023/04/23
|21
|2659
|55
Report
AI Summary
This report presents a network analysis conducted using Wireshark, comparing the performance of two websites across three different networks. The analysis identifies network issues, suitable networked applications for performance analysis, and ways to improve service quality. The report details the use of Wireshark for identifying networking protocols and analyzing data traffic flow, including packet loss and IP addresses. It examines name resolution, retransmission, and packet loss to assess quality of service. The study compares statistics collected from Wireshark across the networks and contrasts Wireshark with Microsoft Message Analyzer in terms of ease of use, GUI, traffic visualization, and statistics generation. The findings indicate varying network stability and vulnerabilities, with recommendations for network configuration and management to mitigate identified risks.

Running head: NETWORKED APPLICATION MANAGEMENT
Network Analysis using Wireshark
Name of the Student
Name of the University
Author’s Note
Network Analysis using Wireshark
Name of the Student
Name of the University
Author’s Note
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

1
NETWORKED APPLICATION MANAGEMENT
Table of Contents
Introduction...........................................................................................................................................2
Part 1:....................................................................................................................................................2
Part 2:....................................................................................................................................................7
Part 3...................................................................................................................................................12
Part 4...................................................................................................................................................15
Conclusion...........................................................................................................................................18
NETWORKED APPLICATION MANAGEMENT
Table of Contents
Introduction...........................................................................................................................................2
Part 1:....................................................................................................................................................2
Part 2:....................................................................................................................................................7
Part 3...................................................................................................................................................12
Part 4...................................................................................................................................................15
Conclusion...........................................................................................................................................18
2
NETWORKED APPLICATION MANAGEMENT
Introduction
The report is prepared for the analysing and comparing the performance of two websites
https://www.abc.net.au/news/, https://iview.abc.net.au/ using wireshark. The different network
issues and the networked application that can be used for analysing the system performance are
identified and improving the quality of service. A research is made on the usability of wireshark for
identification of the networking protocol and analysing the flow of data traffic in the network.
Different network is used for analysing the performance of the website and identification of the
vulnerability acting on the system using wireshark. It helps in identification of the packet loss and the
IP address of the client and server. The quality of service that can be achieved using the wireshark
application is analysed by analysing the name resolution-network address, retransmission and the
packet loss during surfing the website. The packet loss is identified from the generation of the
throughput graph and application of tcp.analysis.lost_segment filter in wireshark. The statistics
collected from wireshark is collected and compared with each other for the identification of the
network performance. Along with wireshark Microsoft Message Analyzer is used and its usability is
compared by analysing its ease of access, GUI, visualization of traffic and statistics generation.
Part 1:
Network 1:
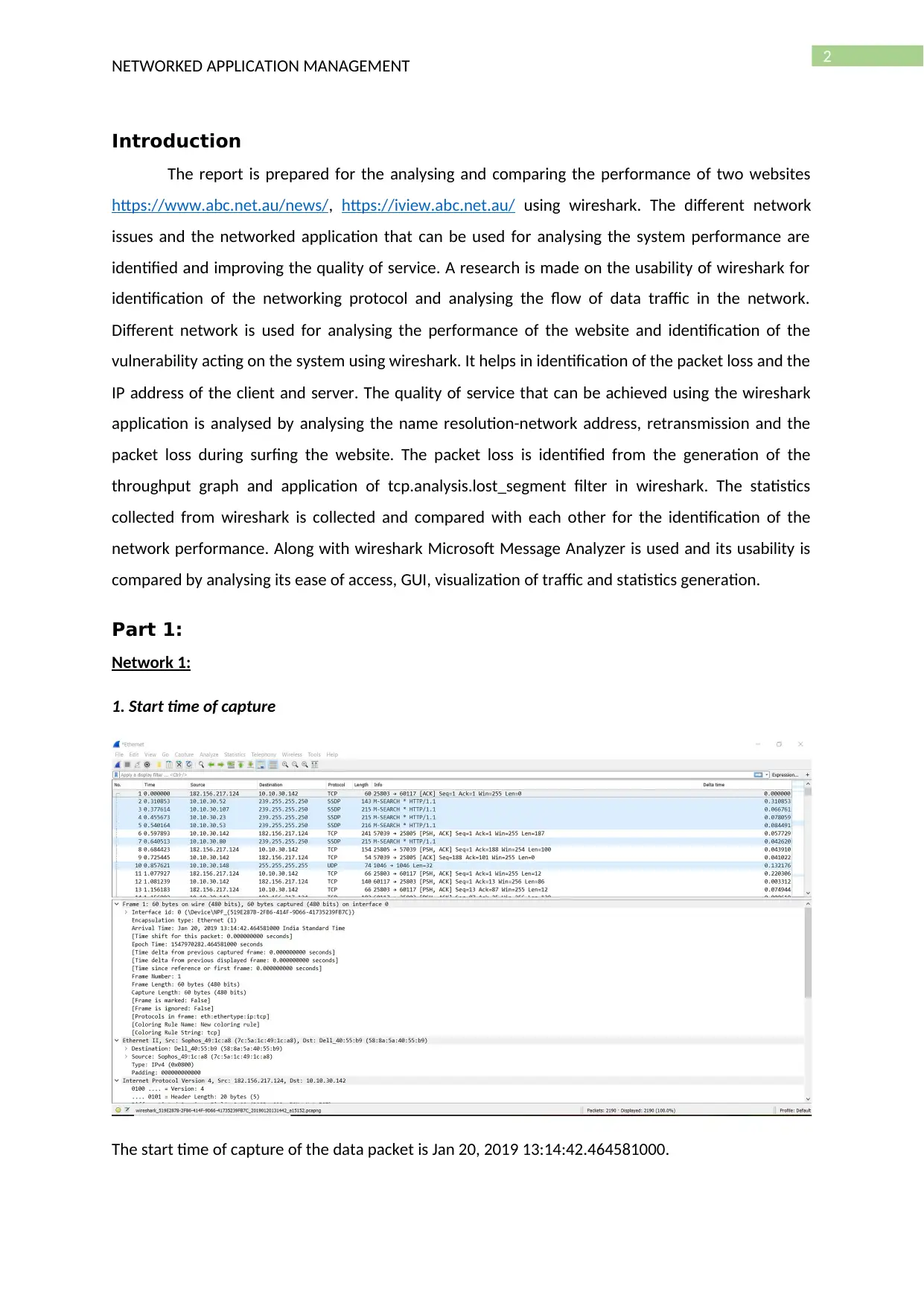
1. Start time of capture
The start time of capture of the data packet is Jan 20, 2019 13:14:42.464581000.
NETWORKED APPLICATION MANAGEMENT
Introduction
The report is prepared for the analysing and comparing the performance of two websites
https://www.abc.net.au/news/, https://iview.abc.net.au/ using wireshark. The different network
issues and the networked application that can be used for analysing the system performance are
identified and improving the quality of service. A research is made on the usability of wireshark for
identification of the networking protocol and analysing the flow of data traffic in the network.
Different network is used for analysing the performance of the website and identification of the
vulnerability acting on the system using wireshark. It helps in identification of the packet loss and the
IP address of the client and server. The quality of service that can be achieved using the wireshark
application is analysed by analysing the name resolution-network address, retransmission and the
packet loss during surfing the website. The packet loss is identified from the generation of the
throughput graph and application of tcp.analysis.lost_segment filter in wireshark. The statistics
collected from wireshark is collected and compared with each other for the identification of the
network performance. Along with wireshark Microsoft Message Analyzer is used and its usability is
compared by analysing its ease of access, GUI, visualization of traffic and statistics generation.
Part 1:
Network 1:
1. Start time of capture
The start time of capture of the data packet is Jan 20, 2019 13:14:42.464581000.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
3
NETWORKED APPLICATION MANAGEMENT
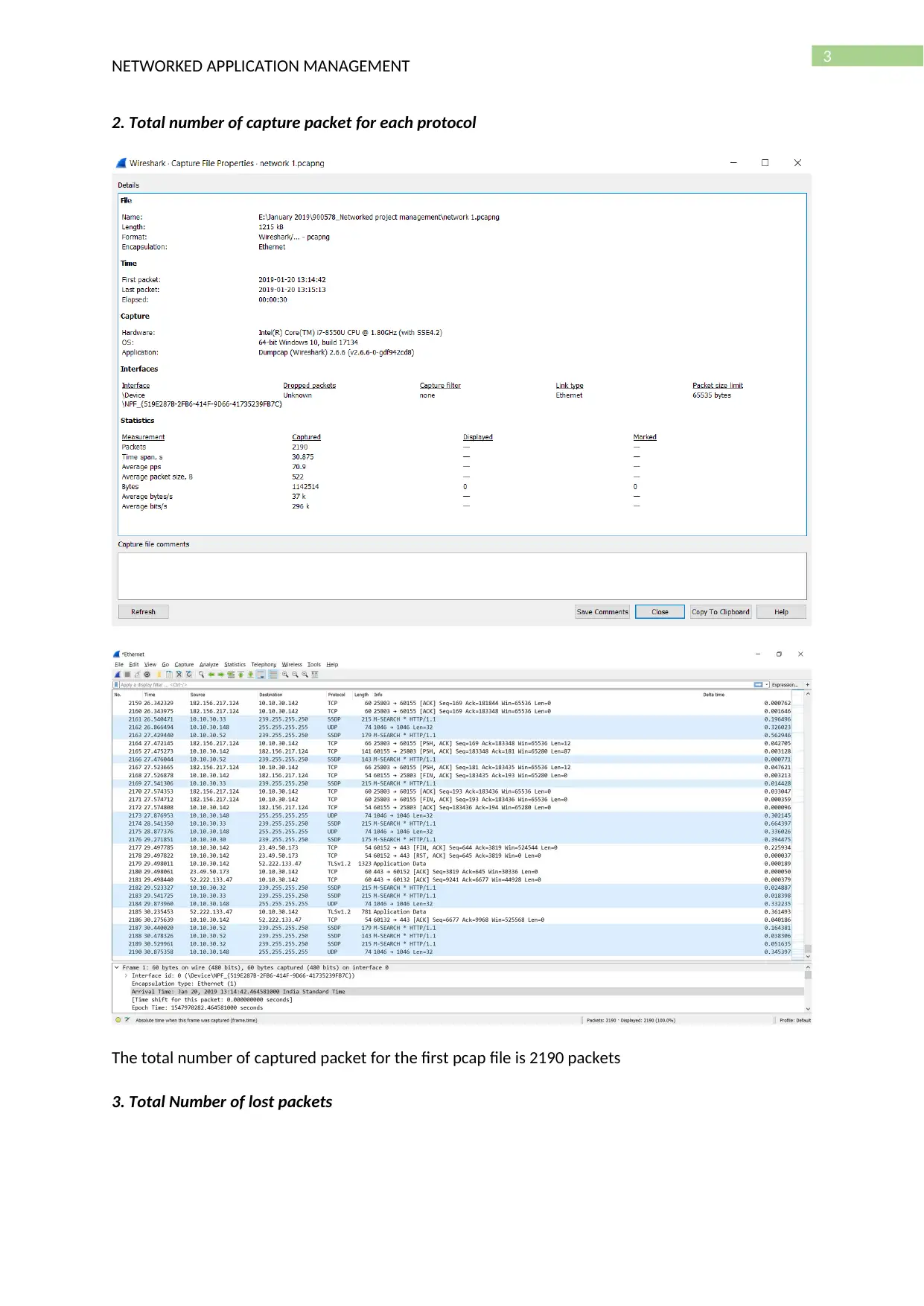
2. Total number of capture packet for each protocol
The total number of captured packet for the first pcap file is 2190 packets
3. Total Number of lost packets
NETWORKED APPLICATION MANAGEMENT
2. Total number of capture packet for each protocol
The total number of captured packet for the first pcap file is 2190 packets
3. Total Number of lost packets
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
4
NETWORKED APPLICATION MANAGEMENT
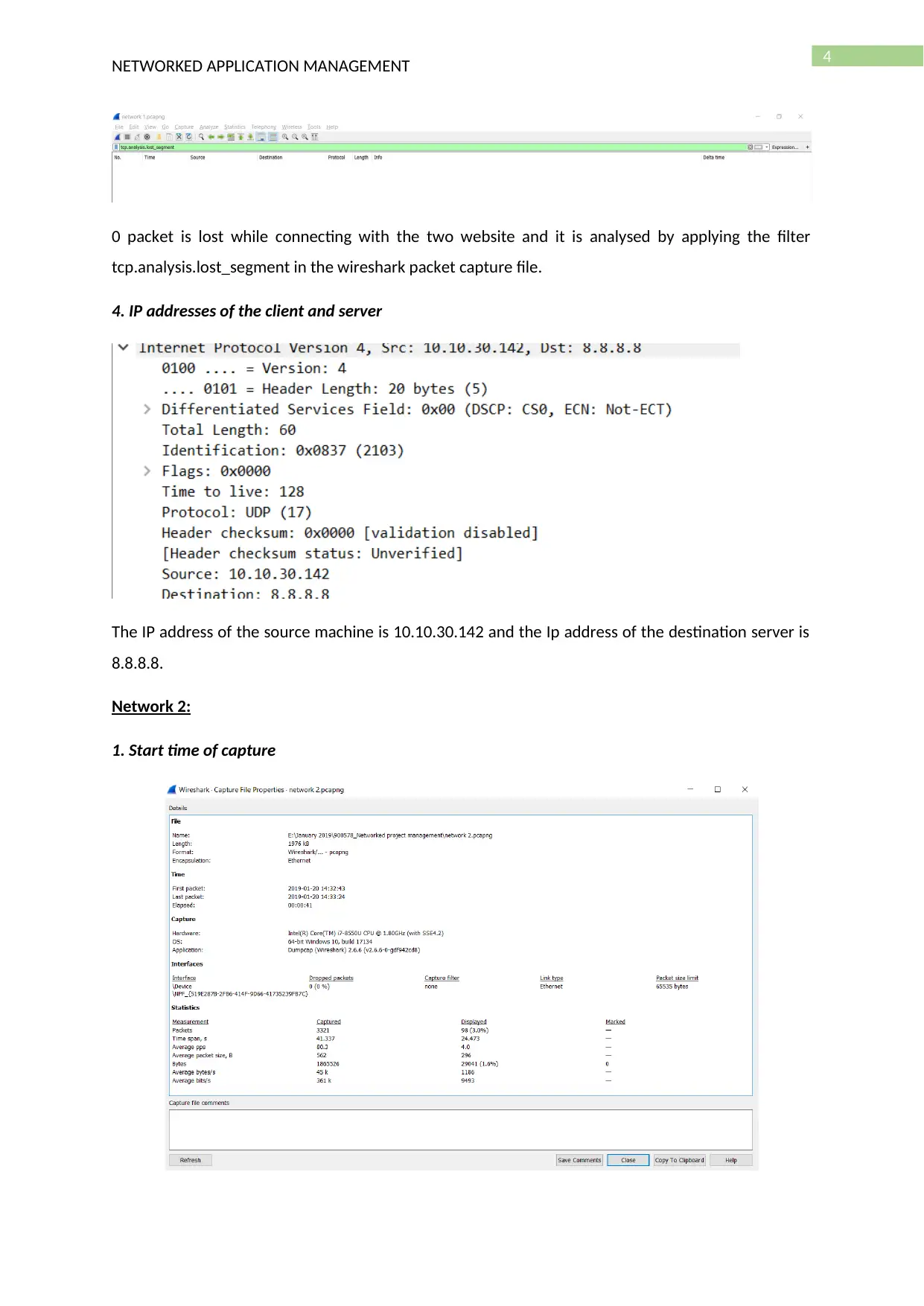
0 packet is lost while connecting with the two website and it is analysed by applying the filter
tcp.analysis.lost_segment in the wireshark packet capture file.
4. IP addresses of the client and server
The IP address of the source machine is 10.10.30.142 and the Ip address of the destination server is
8.8.8.8.
Network 2:
1. Start time of capture
NETWORKED APPLICATION MANAGEMENT
0 packet is lost while connecting with the two website and it is analysed by applying the filter
tcp.analysis.lost_segment in the wireshark packet capture file.
4. IP addresses of the client and server
The IP address of the source machine is 10.10.30.142 and the Ip address of the destination server is
8.8.8.8.
Network 2:
1. Start time of capture
5
NETWORKED APPLICATION MANAGEMENT
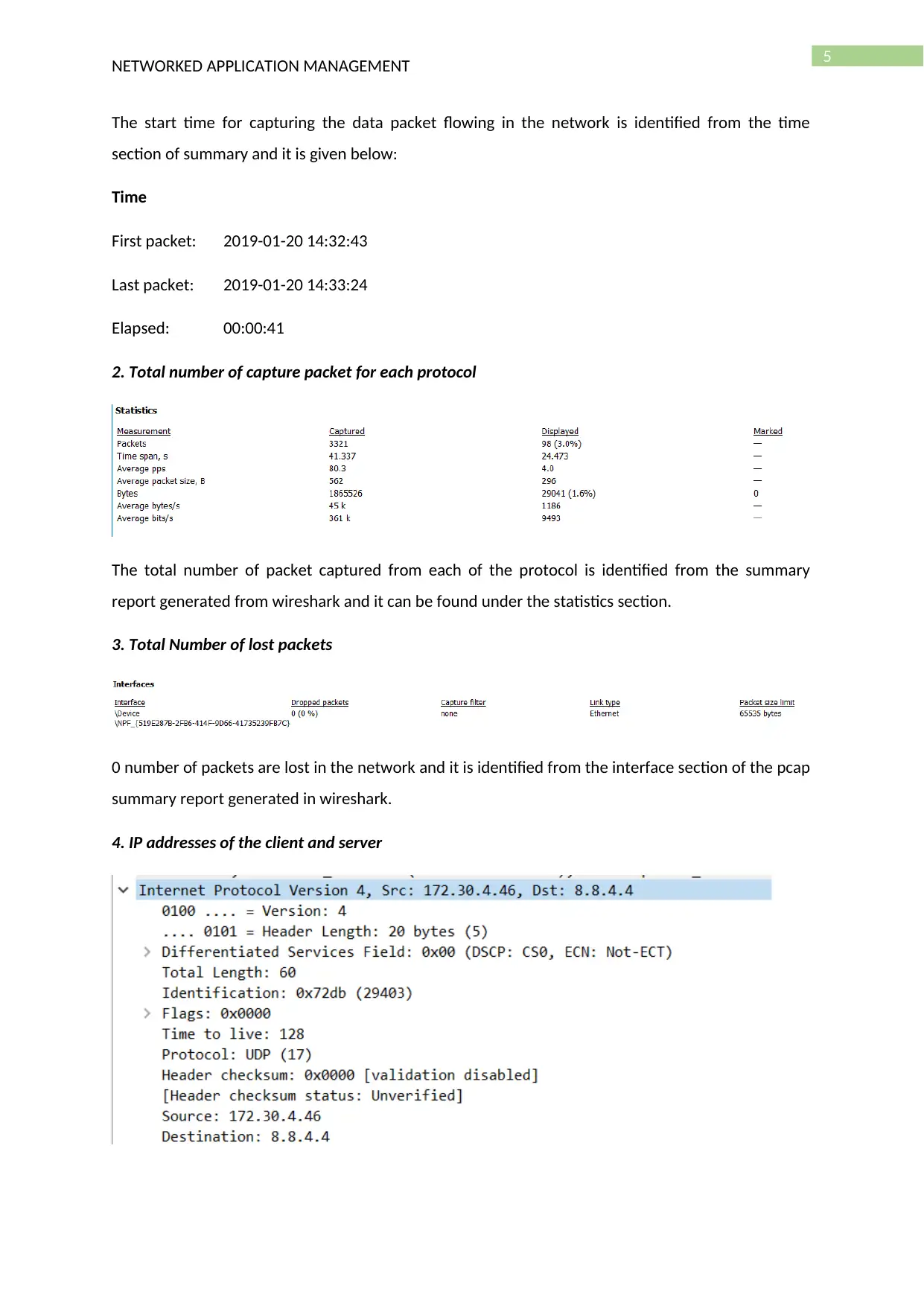
The start time for capturing the data packet flowing in the network is identified from the time
section of summary and it is given below:
Time
First packet: 2019-01-20 14:32:43
Last packet: 2019-01-20 14:33:24
Elapsed: 00:00:41
2. Total number of capture packet for each protocol
The total number of packet captured from each of the protocol is identified from the summary
report generated from wireshark and it can be found under the statistics section.
3. Total Number of lost packets
0 number of packets are lost in the network and it is identified from the interface section of the pcap
summary report generated in wireshark.
4. IP addresses of the client and server
NETWORKED APPLICATION MANAGEMENT
The start time for capturing the data packet flowing in the network is identified from the time
section of summary and it is given below:
Time
First packet: 2019-01-20 14:32:43
Last packet: 2019-01-20 14:33:24
Elapsed: 00:00:41
2. Total number of capture packet for each protocol
The total number of packet captured from each of the protocol is identified from the summary
report generated from wireshark and it can be found under the statistics section.
3. Total Number of lost packets
0 number of packets are lost in the network and it is identified from the interface section of the pcap
summary report generated in wireshark.
4. IP addresses of the client and server
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
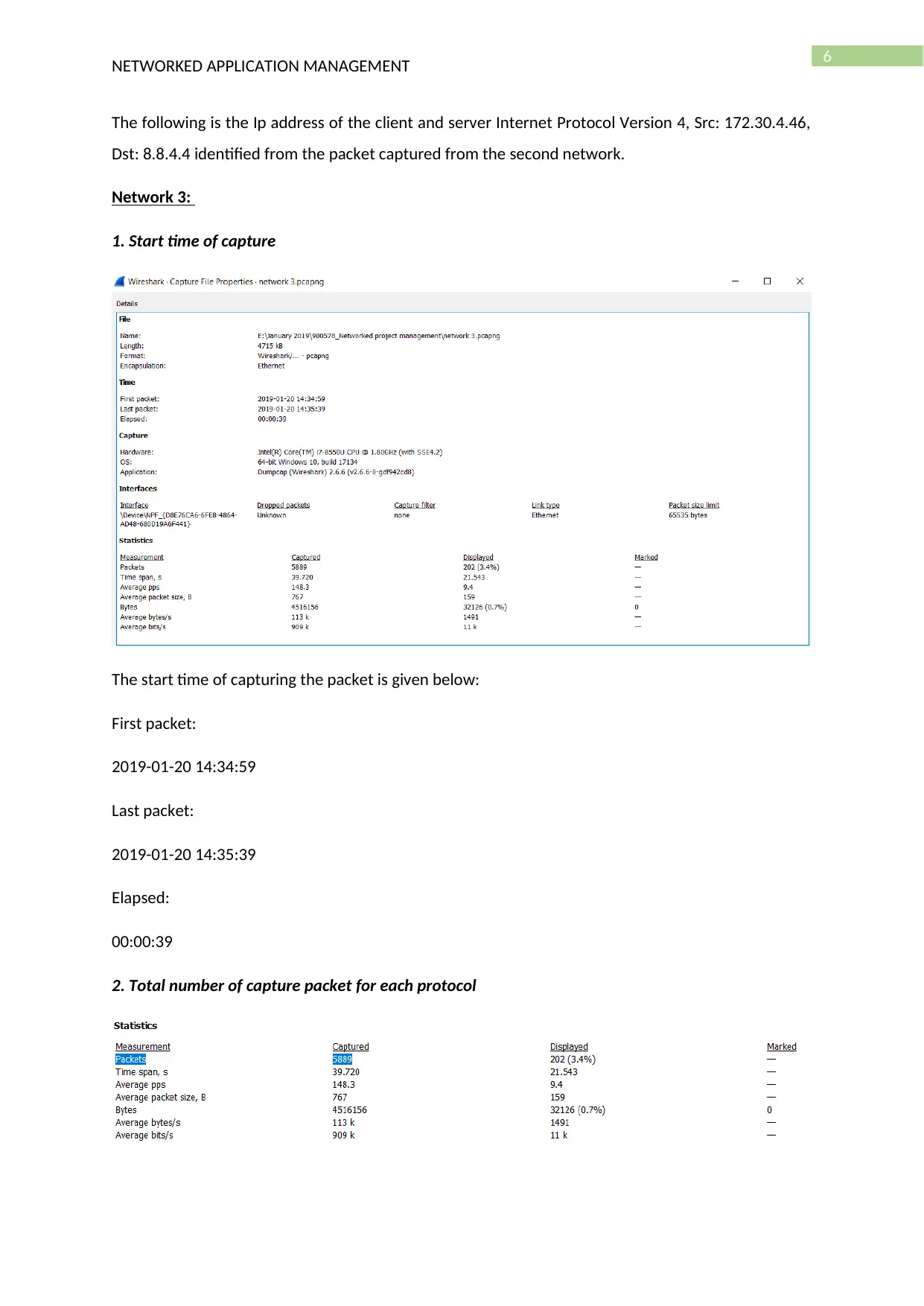
6
NETWORKED APPLICATION MANAGEMENT
The following is the Ip address of the client and server Internet Protocol Version 4, Src: 172.30.4.46,
Dst: 8.8.4.4 identified from the packet captured from the second network.
Network 3:
1. Start time of capture
The start time of capturing the packet is given below:
First packet:
2019-01-20 14:34:59
Last packet:
2019-01-20 14:35:39
Elapsed:
00:00:39
2. Total number of capture packet for each protocol
NETWORKED APPLICATION MANAGEMENT
The following is the Ip address of the client and server Internet Protocol Version 4, Src: 172.30.4.46,
Dst: 8.8.4.4 identified from the packet captured from the second network.
Network 3:
1. Start time of capture
The start time of capturing the packet is given below:
First packet:
2019-01-20 14:34:59
Last packet:
2019-01-20 14:35:39
Elapsed:
00:00:39
2. Total number of capture packet for each protocol
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
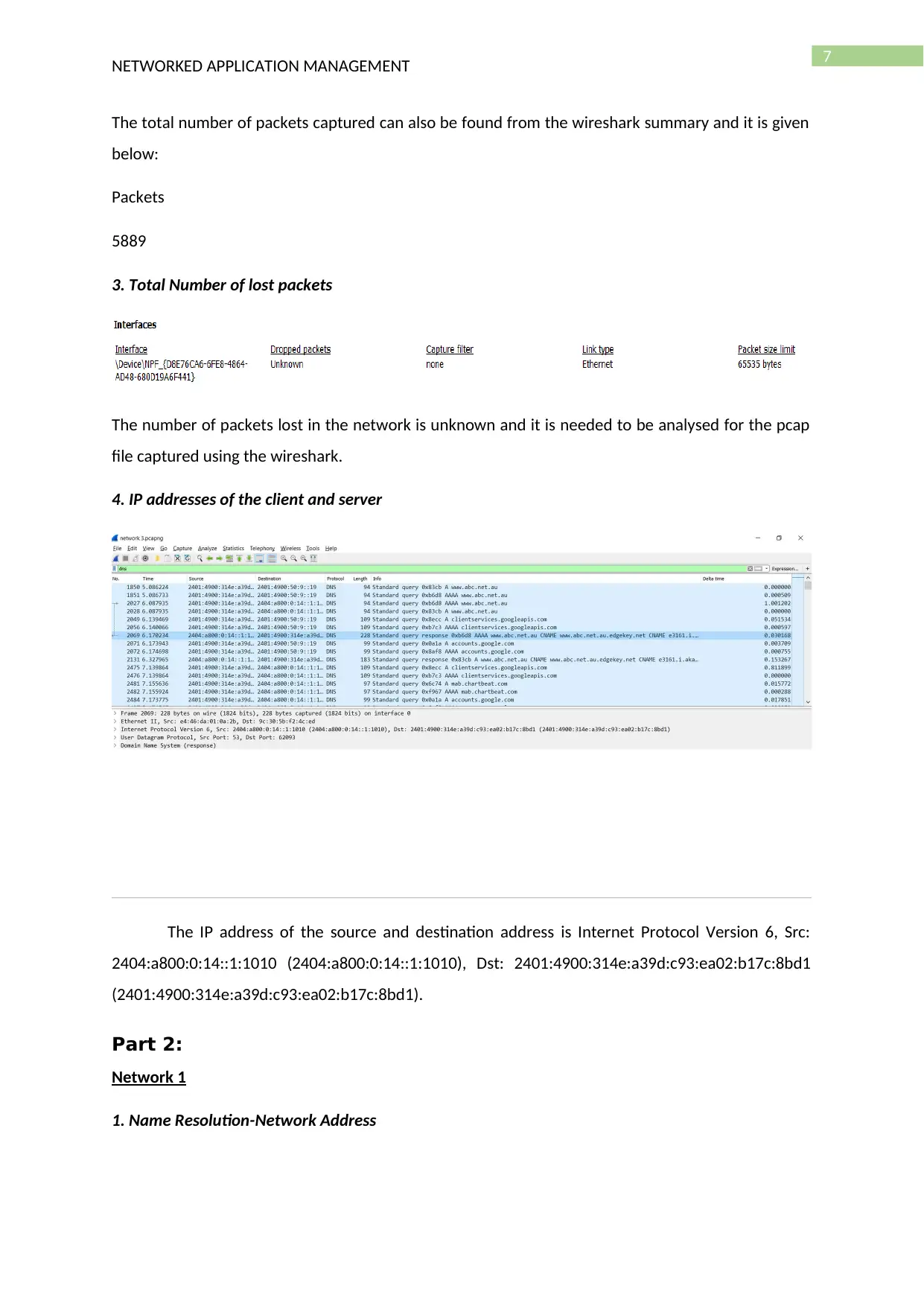
7
NETWORKED APPLICATION MANAGEMENT
The total number of packets captured can also be found from the wireshark summary and it is given
below:
Packets
5889
3. Total Number of lost packets
The number of packets lost in the network is unknown and it is needed to be analysed for the pcap
file captured using the wireshark.
4. IP addresses of the client and server
The IP address of the source and destination address is Internet Protocol Version 6, Src:
2404:a800:0:14::1:1010 (2404:a800:0:14::1:1010), Dst: 2401:4900:314e:a39d:c93:ea02:b17c:8bd1
(2401:4900:314e:a39d:c93:ea02:b17c:8bd1).
Part 2:
Network 1
1. Name Resolution-Network Address
NETWORKED APPLICATION MANAGEMENT
The total number of packets captured can also be found from the wireshark summary and it is given
below:
Packets
5889
3. Total Number of lost packets
The number of packets lost in the network is unknown and it is needed to be analysed for the pcap
file captured using the wireshark.
4. IP addresses of the client and server
The IP address of the source and destination address is Internet Protocol Version 6, Src:
2404:a800:0:14::1:1010 (2404:a800:0:14::1:1010), Dst: 2401:4900:314e:a39d:c93:ea02:b17c:8bd1
(2401:4900:314e:a39d:c93:ea02:b17c:8bd1).
Part 2:
Network 1
1. Name Resolution-Network Address
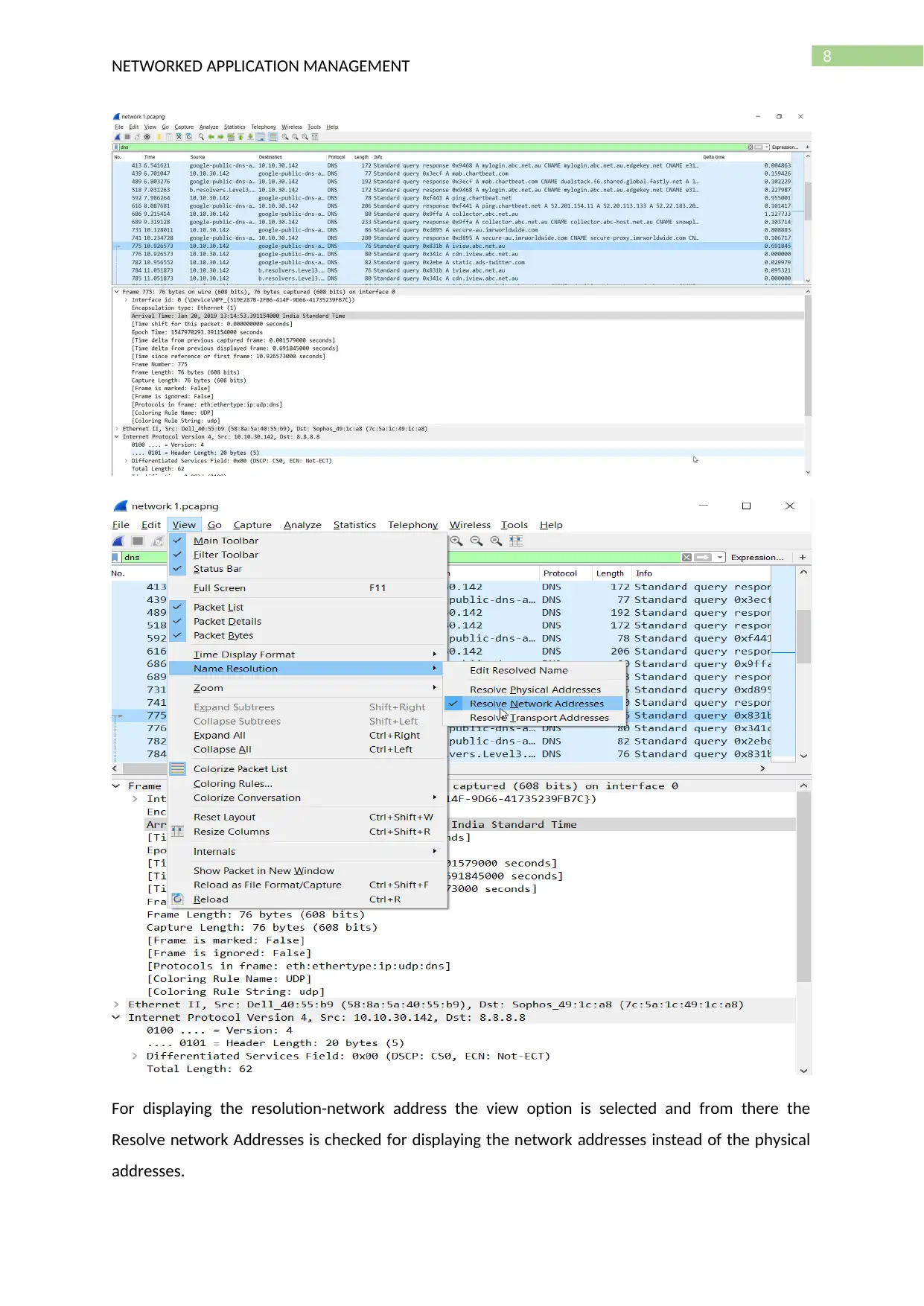
8
NETWORKED APPLICATION MANAGEMENT
For displaying the resolution-network address the view option is selected and from there the
Resolve network Addresses is checked for displaying the network addresses instead of the physical
addresses.
NETWORKED APPLICATION MANAGEMENT
For displaying the resolution-network address the view option is selected and from there the
Resolve network Addresses is checked for displaying the network addresses instead of the physical
addresses.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
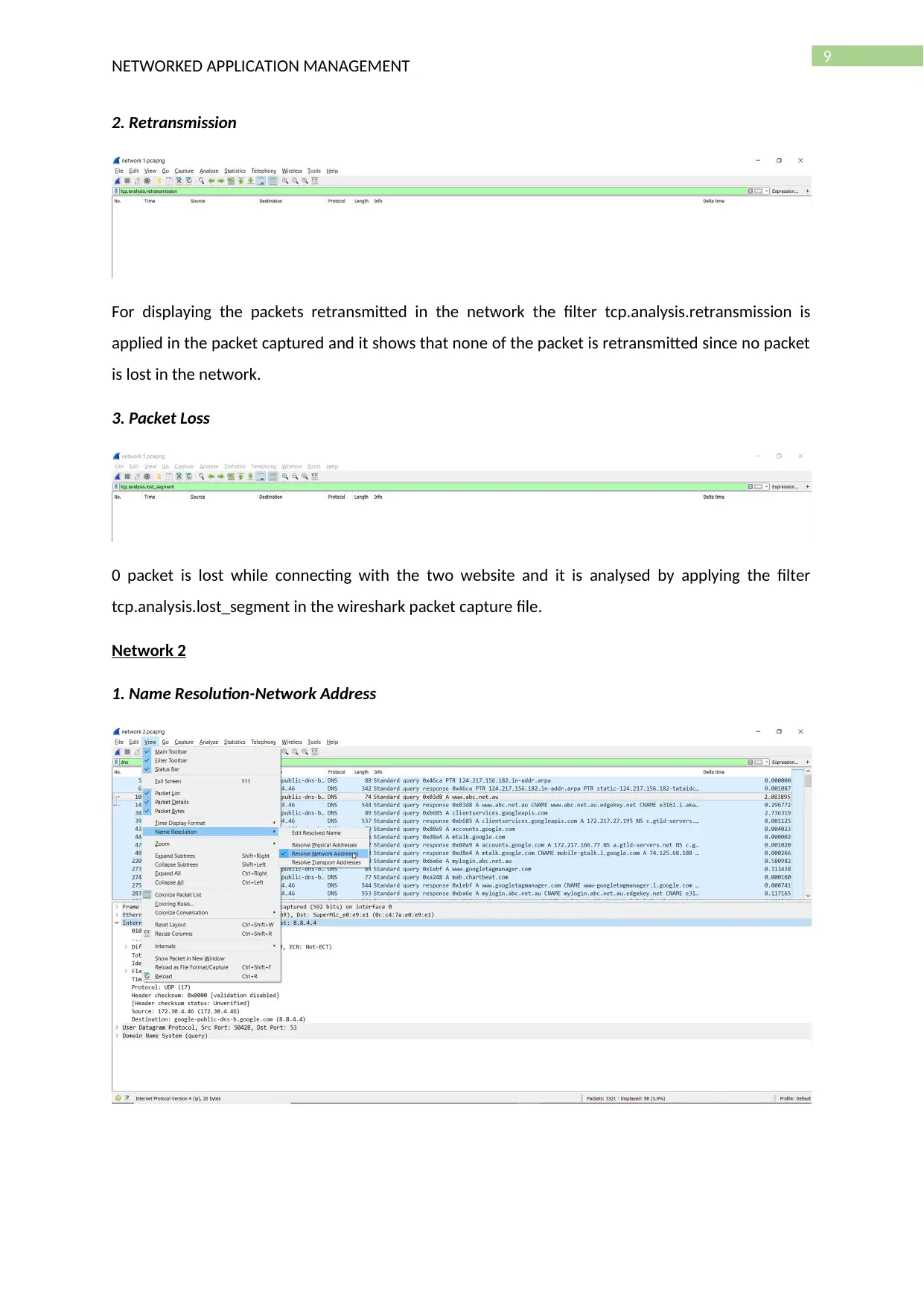
9
NETWORKED APPLICATION MANAGEMENT
2. Retransmission
For displaying the packets retransmitted in the network the filter tcp.analysis.retransmission is
applied in the packet captured and it shows that none of the packet is retransmitted since no packet
is lost in the network.
3. Packet Loss
0 packet is lost while connecting with the two website and it is analysed by applying the filter
tcp.analysis.lost_segment in the wireshark packet capture file.
Network 2
1. Name Resolution-Network Address
NETWORKED APPLICATION MANAGEMENT
2. Retransmission
For displaying the packets retransmitted in the network the filter tcp.analysis.retransmission is
applied in the packet captured and it shows that none of the packet is retransmitted since no packet
is lost in the network.
3. Packet Loss
0 packet is lost while connecting with the two website and it is analysed by applying the filter
tcp.analysis.lost_segment in the wireshark packet capture file.
Network 2
1. Name Resolution-Network Address
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
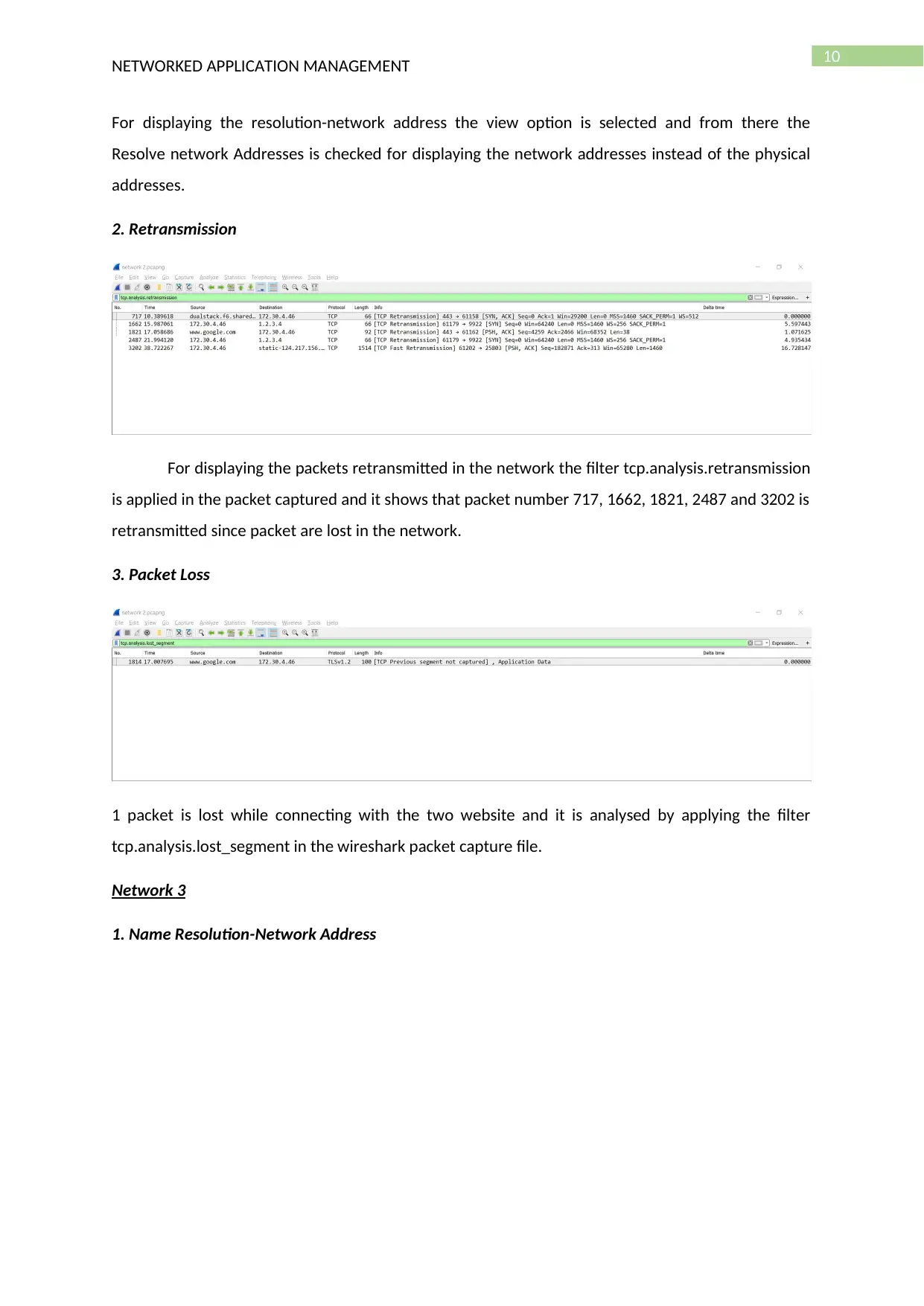
10
NETWORKED APPLICATION MANAGEMENT
For displaying the resolution-network address the view option is selected and from there the
Resolve network Addresses is checked for displaying the network addresses instead of the physical
addresses.
2. Retransmission
For displaying the packets retransmitted in the network the filter tcp.analysis.retransmission
is applied in the packet captured and it shows that packet number 717, 1662, 1821, 2487 and 3202 is
retransmitted since packet are lost in the network.
3. Packet Loss
1 packet is lost while connecting with the two website and it is analysed by applying the filter
tcp.analysis.lost_segment in the wireshark packet capture file.
Network 3
1. Name Resolution-Network Address
NETWORKED APPLICATION MANAGEMENT
For displaying the resolution-network address the view option is selected and from there the
Resolve network Addresses is checked for displaying the network addresses instead of the physical
addresses.
2. Retransmission
For displaying the packets retransmitted in the network the filter tcp.analysis.retransmission
is applied in the packet captured and it shows that packet number 717, 1662, 1821, 2487 and 3202 is
retransmitted since packet are lost in the network.
3. Packet Loss
1 packet is lost while connecting with the two website and it is analysed by applying the filter
tcp.analysis.lost_segment in the wireshark packet capture file.
Network 3
1. Name Resolution-Network Address
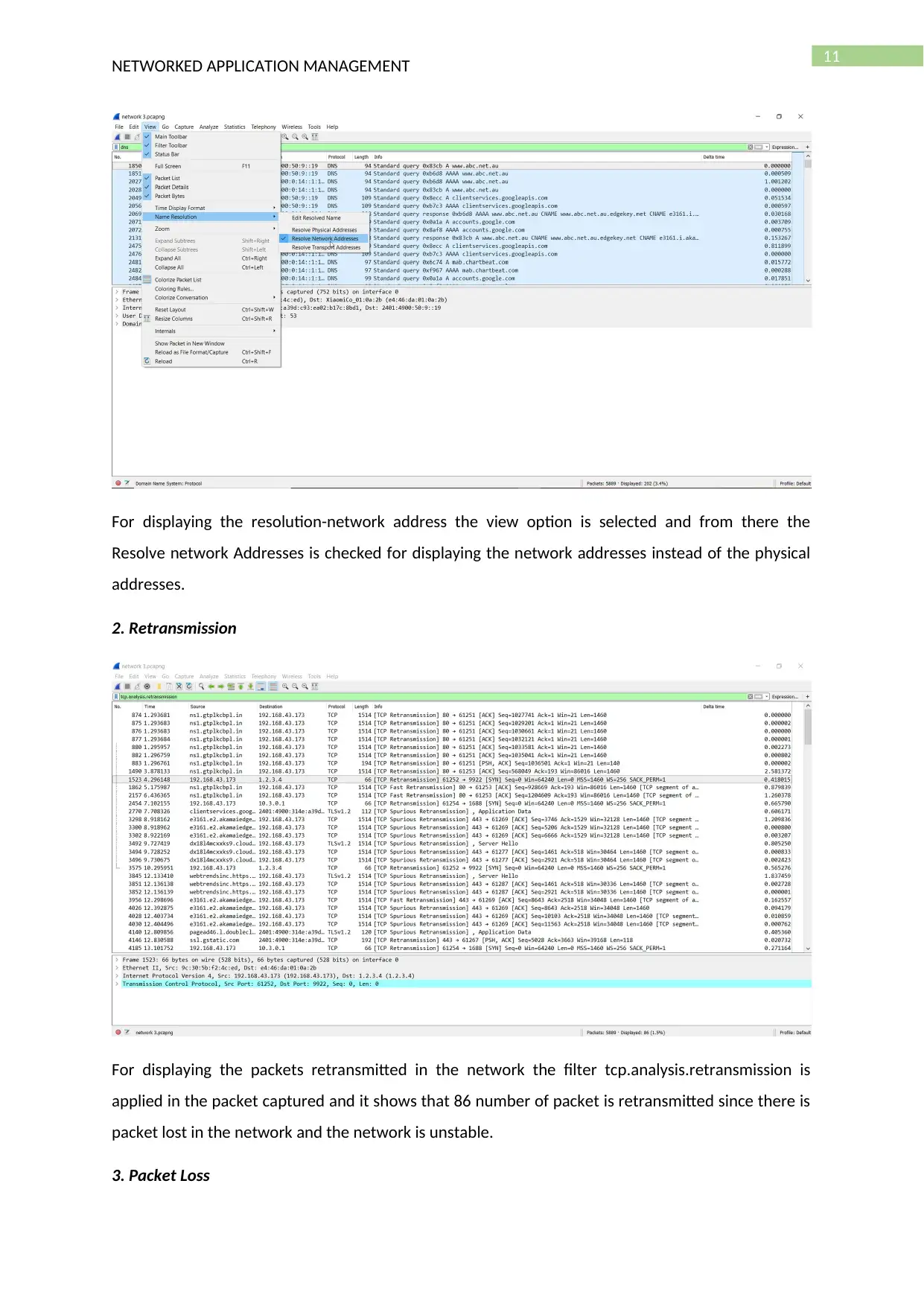
11
NETWORKED APPLICATION MANAGEMENT
For displaying the resolution-network address the view option is selected and from there the
Resolve network Addresses is checked for displaying the network addresses instead of the physical
addresses.
2. Retransmission
For displaying the packets retransmitted in the network the filter tcp.analysis.retransmission is
applied in the packet captured and it shows that 86 number of packet is retransmitted since there is
packet lost in the network and the network is unstable.
3. Packet Loss
NETWORKED APPLICATION MANAGEMENT
For displaying the resolution-network address the view option is selected and from there the
Resolve network Addresses is checked for displaying the network addresses instead of the physical
addresses.
2. Retransmission
For displaying the packets retransmitted in the network the filter tcp.analysis.retransmission is
applied in the packet captured and it shows that 86 number of packet is retransmitted since there is
packet lost in the network and the network is unstable.
3. Packet Loss
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
1 out of 21
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.



