Network and Communications: Packet Transmission and Routing
VerifiedAdded on 2021/04/24
|15
|3633
|111
Homework Assignment
AI Summary
This assignment solution analyzes network and communication concepts, focusing on packet transmission, routing, and protocols. It examines how NAT devices handle packet transmission, including the conversion of IP addresses and port assignments. The solution explains the role of ICMP in error reporting and discusses IP routing and frame forwarding, including the use of ARP. It also details the processes of encapsulation and decapsulation in data transmission. Furthermore, the assignment explores dynamic routing protocols, specifically OSPF and EIGRP, and explains why BGP is not suitable for the given network. The solution uses examples and calculations to illustrate these concepts, providing a comprehensive understanding of network communication principles.

NETWORK AND COMMUNICATIONS 1
Network and Communications
Name
Course
Institution
Date of Submission
Network and Communications
Name
Course
Institution
Date of Submission
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

NETWORK AND COMMUNICATIONS 2
When communication and computing technologies are employed in the process of
transferring data from one place to another in a faster and secure way, it can be termed to be data
communication. For a stable network to exist, there are technologies and techniques that have to
be put in place for success to be realized. For instance, technologies like computer networking,
telecommunications, radio among others have to be there. The communication or transportation
medium has to be existing between the nodes that are in need of communication. Therefore, data
terminal equipment (DTE) and data communication equipment (DCE) is vital in a stable and
running network.
Question 1
Packet Transmission for PC-1 and Subsequent NAT Router Activities
Packets from the Source IP
The IP address for PC-1 (192.168.10.7) which is internal in this case is converted by the
NAT device when a packet is transmitted from PC-1 to the external network. This being the
address of the sender (packet header), it is therefore replaced with an IP address
(209.165.200.226) which in this case is an external IP address belonging to NAT device meaning
that a port number that is available from its own pool is assigned to the connection.
From the Router to the Destination Server
This port number is inserted in the packet header also known as the source port field for
the packet to be forwarded to the external network. What follows is an entry being made by the
NAT devise in a translation table (Park, Chung and Ahn, 2012). This entry is composed of the
source port that was original, the current source port that is translated, and the internal IP address
of the send packet. This means that all the succeeding packets that are originating from the same
connection are therefore translated to the matching port number. Basing on the fact that the
When communication and computing technologies are employed in the process of
transferring data from one place to another in a faster and secure way, it can be termed to be data
communication. For a stable network to exist, there are technologies and techniques that have to
be put in place for success to be realized. For instance, technologies like computer networking,
telecommunications, radio among others have to be there. The communication or transportation
medium has to be existing between the nodes that are in need of communication. Therefore, data
terminal equipment (DTE) and data communication equipment (DCE) is vital in a stable and
running network.
Question 1
Packet Transmission for PC-1 and Subsequent NAT Router Activities
Packets from the Source IP
The IP address for PC-1 (192.168.10.7) which is internal in this case is converted by the
NAT device when a packet is transmitted from PC-1 to the external network. This being the
address of the sender (packet header), it is therefore replaced with an IP address
(209.165.200.226) which in this case is an external IP address belonging to NAT device meaning
that a port number that is available from its own pool is assigned to the connection.
From the Router to the Destination Server
This port number is inserted in the packet header also known as the source port field for
the packet to be forwarded to the external network. What follows is an entry being made by the
NAT devise in a translation table (Park, Chung and Ahn, 2012). This entry is composed of the
source port that was original, the current source port that is translated, and the internal IP address
of the send packet. This means that all the succeeding packets that are originating from the same
connection are therefore translated to the matching port number. Basing on the fact that the

NETWORK AND COMMUNICATIONS 3
address that is being transmitted to the remote server is being translated by the NAT device, a
connection to the IP 209.165.200.226 and the port as definite in the transformed packet is
established.
The packet from the Destination Server Back to the Source Through a Router
When it is time for a packet to be transmitted from the external network back to PC-1,
there is what is termed as mapping of that packet to the matching IP 192.168.10.7 which in this
case is the internal source IP address of the packet and the port number that was assigned by the
NAT device in the translation table. This is usually the first step in determining the correct
source of the packet in the transmission mode.
At the Router
There is the replacement of an external IP of the NAT device (209.165.200.226) together
with the port number contained in the arriving packet header’s port and IP address. There is a
total transformation of this packet form the IP address that it had while in the external network
back to its original internal one. At this point, the packet can be forwarded internally over the
internal network to the specific device.
The Way in which a Router Keeps Track the Incoming Packet
An IP address and the port of the internal hosts or the source PC-1 are translated by the
NAT devices for security purposes. This is to mean that, the valid endpoints of an internal host
that expects the incoming packet are concealed on a private network (KumarGarg and
P.C.Gupta, 2012, p.14). The data that is transmitted back from the destination server back to the
source PC-1 in the internal network is secure and directly delivered to the rightful owner of that
data.
Question 2
address that is being transmitted to the remote server is being translated by the NAT device, a
connection to the IP 209.165.200.226 and the port as definite in the transformed packet is
established.
The packet from the Destination Server Back to the Source Through a Router
When it is time for a packet to be transmitted from the external network back to PC-1,
there is what is termed as mapping of that packet to the matching IP 192.168.10.7 which in this
case is the internal source IP address of the packet and the port number that was assigned by the
NAT device in the translation table. This is usually the first step in determining the correct
source of the packet in the transmission mode.
At the Router
There is the replacement of an external IP of the NAT device (209.165.200.226) together
with the port number contained in the arriving packet header’s port and IP address. There is a
total transformation of this packet form the IP address that it had while in the external network
back to its original internal one. At this point, the packet can be forwarded internally over the
internal network to the specific device.
The Way in which a Router Keeps Track the Incoming Packet
An IP address and the port of the internal hosts or the source PC-1 are translated by the
NAT devices for security purposes. This is to mean that, the valid endpoints of an internal host
that expects the incoming packet are concealed on a private network (KumarGarg and
P.C.Gupta, 2012, p.14). The data that is transmitted back from the destination server back to the
source PC-1 in the internal network is secure and directly delivered to the rightful owner of that
data.
Question 2
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

NETWORK AND COMMUNICATIONS 4
ICMP
Due to problems that may arise in an event like a network blocking the transfer of an IP
packet, a router may adopt an error reporting protocol so that error messages are generated to the
IP address that is the source of the packet. The message basically indicates that there is a
gateway obstruction to the internet. Despite the fact that ICMP does not do the same work like a
transport protocol for sending packets amid systems, all devices connected to an IP network can
process, receive or even send messages related to ICMP. The data in ICMP is encapsulated in an
IP header allowing the message to be transmitted in a datagram format (Mariyammal, 2016). For
the system to be able to determine the failed packet, the ICMP message is composed with the
complete IP header of the message that is original.
IP Routing and Frame Forwarding
The internet protocol is known to be a Network Layer Protocol whereby it borders the
Transport Layer and the Network Layer. The ARP, on the other hand, is known to translate amid
a Network Layer and a Data Link Layer address. When PC-A pings PC-B (200.10.4.59), there is
a need for first determining the destined network. This is made possible with the help of the
address resolution protocol which checks the subnet mask and the IP address of PC-A. For the
pinged packet to be routed to the desired remote destination PC-B.
Determining Whether PC-B is on a Local or Remote Destination
IP AI PC-A can easily determine come up with a conclusion whether PC-B is a
destination that is local or remote through a mathematical calculation termed as an AND
operation. This process is done internally by the sending host so that it can choose which mode
to send the packets (direct to the host or through the router). ANDing can be done whereby all
ICMP
Due to problems that may arise in an event like a network blocking the transfer of an IP
packet, a router may adopt an error reporting protocol so that error messages are generated to the
IP address that is the source of the packet. The message basically indicates that there is a
gateway obstruction to the internet. Despite the fact that ICMP does not do the same work like a
transport protocol for sending packets amid systems, all devices connected to an IP network can
process, receive or even send messages related to ICMP. The data in ICMP is encapsulated in an
IP header allowing the message to be transmitted in a datagram format (Mariyammal, 2016). For
the system to be able to determine the failed packet, the ICMP message is composed with the
complete IP header of the message that is original.
IP Routing and Frame Forwarding
The internet protocol is known to be a Network Layer Protocol whereby it borders the
Transport Layer and the Network Layer. The ARP, on the other hand, is known to translate amid
a Network Layer and a Data Link Layer address. When PC-A pings PC-B (200.10.4.59), there is
a need for first determining the destined network. This is made possible with the help of the
address resolution protocol which checks the subnet mask and the IP address of PC-A. For the
pinged packet to be routed to the desired remote destination PC-B.
Determining Whether PC-B is on a Local or Remote Destination
IP AI PC-A can easily determine come up with a conclusion whether PC-B is a
destination that is local or remote through a mathematical calculation termed as an AND
operation. This process is done internally by the sending host so that it can choose which mode
to send the packets (direct to the host or through the router). ANDing can be done whereby all
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

NETWORK AND COMMUNICATIONS 5
values are converted to binary and source subnet mask is applied to source address then source
subnet mask is then applied to the destination address (Huang and Wang, 2013, p.2915).
Calculations
0 AND 1 will be 0
0 AND 0 will be 0
1 AND 1 will be 1
PC-A IP address: 200.10.5.68/28
Subnet mask: 255.255.255.240
PC-B (destination) IP address: 200.10.4.59/27
When all the Values are Converted into Binary
PC-A IP: 11001000.00001010.00000101.01000100
Source Subnet: 11111111.11111111.11111111.11110000
PC-B IP: 11001000.00001010.00000100.00111011
When Source Subnet Mask is Applied or ANDed to Source Address
PC-A: 11001000.00001010.00000101.01000100
Subnet: 11111111.11111111.11111111.11110000
Result: 11001000.00001010.00000101.01000000
When Source Subnet Mask is Applied to Destination Address
PC-B IP: 11001000.00001010.00000100.00111011
Source subnet: 11111111.11111111.11111111.11110000
Results: 11001000.00001010.00000100.00110000
values are converted to binary and source subnet mask is applied to source address then source
subnet mask is then applied to the destination address (Huang and Wang, 2013, p.2915).
Calculations
0 AND 1 will be 0
0 AND 0 will be 0
1 AND 1 will be 1
PC-A IP address: 200.10.5.68/28
Subnet mask: 255.255.255.240
PC-B (destination) IP address: 200.10.4.59/27
When all the Values are Converted into Binary
PC-A IP: 11001000.00001010.00000101.01000100
Source Subnet: 11111111.11111111.11111111.11110000
PC-B IP: 11001000.00001010.00000100.00111011
When Source Subnet Mask is Applied or ANDed to Source Address
PC-A: 11001000.00001010.00000101.01000100
Subnet: 11111111.11111111.11111111.11110000
Result: 11001000.00001010.00000101.01000000
When Source Subnet Mask is Applied to Destination Address
PC-B IP: 11001000.00001010.00000100.00111011
Source subnet: 11111111.11111111.11111111.11110000
Results: 11001000.00001010.00000100.00110000

NETWORK AND COMMUNICATIONS 6
When Both results are Compared for Equality
Result 1: 11001000.00001010.00000101.01000000
Results 2: 11001000.00001010.00000100.00110000
If the ANDing results turn out to be identical, to be the same, this would automatically
mean that the both PC-A and PC-B reside on a similar subnet. However, when the results turn
out different like in the calculations above, it means that PC-B which is the destination host is
remote hence the packet ah to go through the router.
Device Used for Encapsulation of an IP
At this point, a packet originating from PC-A goes straight to the router. The MAC
address of the router is first determined (the hardware address that identifies the router on that
network). The router acts as the intermediate host for the purpose of packet-passing which
identifies the IP address and replies to host 1(PC-A). There is time variation for the ARP to act in
terms of response from the machine. However, in an incidence where ping packet expires, it is
termed as TTL meaning (time to live) has elapsed. Encapsulation will, therefore, happen using
the routers’ MAC address since the network of the hosts differs (remote).
Encapsulation
Due to the movement of data from the upper to the lower layer of the TCP/IP (PC-A to
PC-B for our case), there is information in the header of each layer together with the actual data.
This can be termed as the supplementary data that is located at the beginning of each frame of
data during transmission. On arrival at PC-B, the data in the headers is used in the process of
extracting the entire data that is encapsulated in the data packet.
Decapsulation
When Both results are Compared for Equality
Result 1: 11001000.00001010.00000101.01000000
Results 2: 11001000.00001010.00000100.00110000
If the ANDing results turn out to be identical, to be the same, this would automatically
mean that the both PC-A and PC-B reside on a similar subnet. However, when the results turn
out different like in the calculations above, it means that PC-B which is the destination host is
remote hence the packet ah to go through the router.
Device Used for Encapsulation of an IP
At this point, a packet originating from PC-A goes straight to the router. The MAC
address of the router is first determined (the hardware address that identifies the router on that
network). The router acts as the intermediate host for the purpose of packet-passing which
identifies the IP address and replies to host 1(PC-A). There is time variation for the ARP to act in
terms of response from the machine. However, in an incidence where ping packet expires, it is
termed as TTL meaning (time to live) has elapsed. Encapsulation will, therefore, happen using
the routers’ MAC address since the network of the hosts differs (remote).
Encapsulation
Due to the movement of data from the upper to the lower layer of the TCP/IP (PC-A to
PC-B for our case), there is information in the header of each layer together with the actual data.
This can be termed as the supplementary data that is located at the beginning of each frame of
data during transmission. On arrival at PC-B, the data in the headers is used in the process of
extracting the entire data that is encapsulated in the data packet.
Decapsulation
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
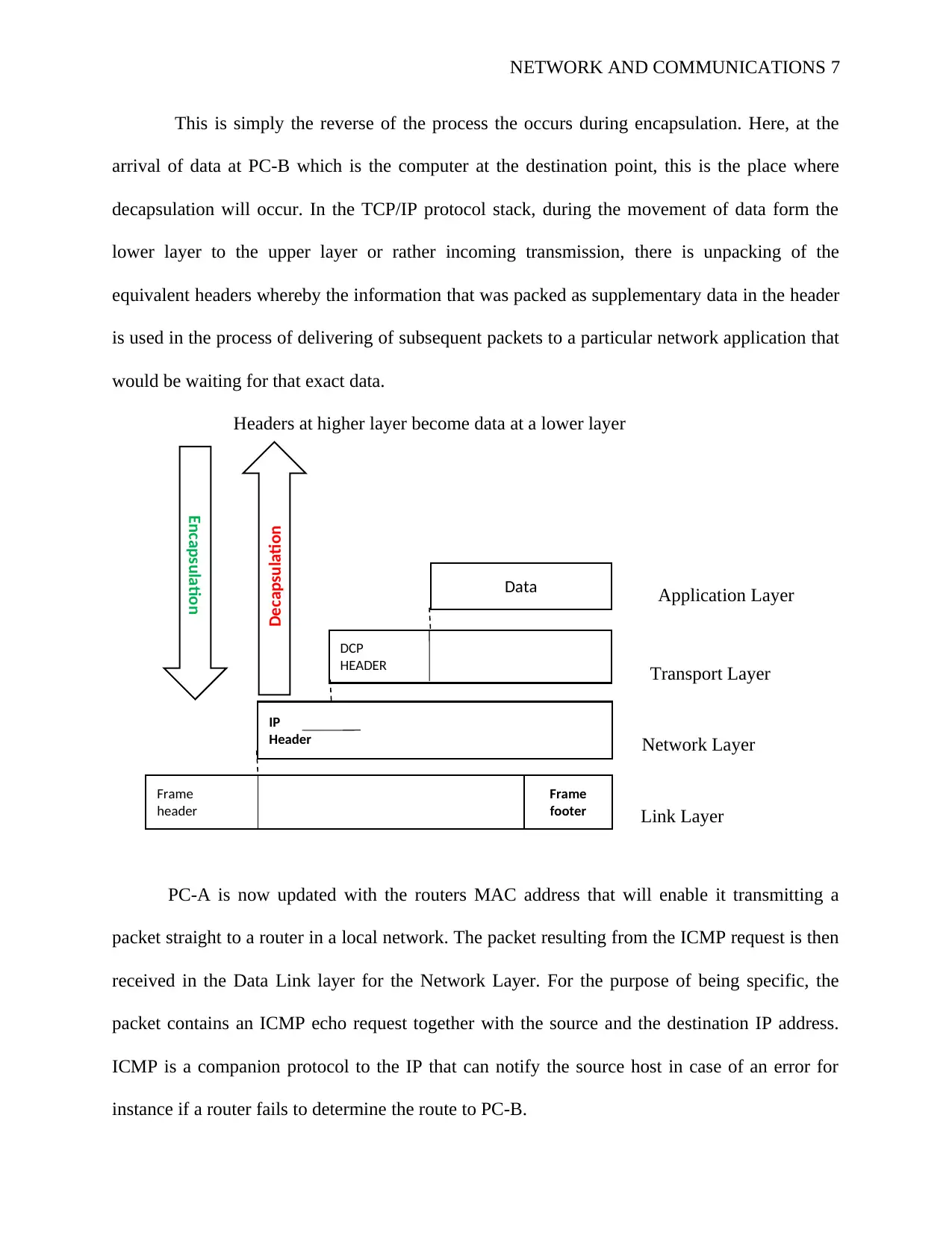
NETWORK AND COMMUNICATIONS 7
This is simply the reverse of the process the occurs during encapsulation. Here, at the
arrival of data at PC-B which is the computer at the destination point, this is the place where
decapsulation will occur. In the TCP/IP protocol stack, during the movement of data form the
lower layer to the upper layer or rather incoming transmission, there is unpacking of the
equivalent headers whereby the information that was packed as supplementary data in the header
is used in the process of delivering of subsequent packets to a particular network application that
would be waiting for that exact data.
Headers at higher layer become data at a lower layer
Application Layer
Transport Layer
Network Layer
Link Layer
PC-A is now updated with the routers MAC address that will enable it transmitting a
packet straight to a router in a local network. The packet resulting from the ICMP request is then
received in the Data Link layer for the Network Layer. For the purpose of being specific, the
packet contains an ICMP echo request together with the source and the destination IP address.
ICMP is a companion protocol to the IP that can notify the source host in case of an error for
instance if a router fails to determine the route to PC-B.
Encapsulation
Decapsulation
Data
DCP
HEADER
IP
Header
Frame
header
Frame
footer
This is simply the reverse of the process the occurs during encapsulation. Here, at the
arrival of data at PC-B which is the computer at the destination point, this is the place where
decapsulation will occur. In the TCP/IP protocol stack, during the movement of data form the
lower layer to the upper layer or rather incoming transmission, there is unpacking of the
equivalent headers whereby the information that was packed as supplementary data in the header
is used in the process of delivering of subsequent packets to a particular network application that
would be waiting for that exact data.
Headers at higher layer become data at a lower layer
Application Layer
Transport Layer
Network Layer
Link Layer
PC-A is now updated with the routers MAC address that will enable it transmitting a
packet straight to a router in a local network. The packet resulting from the ICMP request is then
received in the Data Link layer for the Network Layer. For the purpose of being specific, the
packet contains an ICMP echo request together with the source and the destination IP address.
ICMP is a companion protocol to the IP that can notify the source host in case of an error for
instance if a router fails to determine the route to PC-B.
Encapsulation
Decapsulation
Data
DCP
HEADER
IP
Header
Frame
header
Frame
footer
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

NETWORK AND COMMUNICATIONS 8
The frame at the Physical Layer
A frame is then created in the Data Link Layer of PC-A that is composed of the MAC
address of the source and destination PCs. The frame is handed to the Physical Layer to be
encoded into a digital signal then transmitted. The frame is handed to PC-A in the router's buffer
where a frame is created and transmitted to the destination host (PC-B). ARP helps in
determining the MAC of PC-B and the IP defines the destination of the packets IP address
whereby if it matches with host PC-B, there is the generation of another ICMP echo containing
source and destination IP of both hosts (Saring and Singh, 2018, p.1). This leads to the protocol
repeating itself again but changes direction.
Question 3
Dynamic Routing Protocols
This technology is well known for its character of providing data routing that is optimal
compared to the rest of the protocols. Depending on the real-time logical changes in the network,
routers are able to select their paths. The maintenance, creation, and updating of the what is
called a routing dynamic table is the work of a routing protocol that will be operating in a
particular router unlike in a static routing environment where the system administrator is tasked
with doing all the tasks manually.
Two Dynamic Protocols That Would Work with the Routers
Open Shortest Path First(OSPF) will be a first choice dynamic routing protocol for this
network. Being a link state protocol, its link status has to be tasted to all the neighbors before any
information is sent to them. It has high stabilization probabilities and does not rely on UDP or
TCP meaning that it makes use of IP directly (Hamamreh, 2012, p.14). OSPF has the advantage
of being an open protocol meaning it can be run by any server or router. Despite being able to
The frame at the Physical Layer
A frame is then created in the Data Link Layer of PC-A that is composed of the MAC
address of the source and destination PCs. The frame is handed to the Physical Layer to be
encoded into a digital signal then transmitted. The frame is handed to PC-A in the router's buffer
where a frame is created and transmitted to the destination host (PC-B). ARP helps in
determining the MAC of PC-B and the IP defines the destination of the packets IP address
whereby if it matches with host PC-B, there is the generation of another ICMP echo containing
source and destination IP of both hosts (Saring and Singh, 2018, p.1). This leads to the protocol
repeating itself again but changes direction.
Question 3
Dynamic Routing Protocols
This technology is well known for its character of providing data routing that is optimal
compared to the rest of the protocols. Depending on the real-time logical changes in the network,
routers are able to select their paths. The maintenance, creation, and updating of the what is
called a routing dynamic table is the work of a routing protocol that will be operating in a
particular router unlike in a static routing environment where the system administrator is tasked
with doing all the tasks manually.
Two Dynamic Protocols That Would Work with the Routers
Open Shortest Path First(OSPF) will be a first choice dynamic routing protocol for this
network. Being a link state protocol, its link status has to be tasted to all the neighbors before any
information is sent to them. It has high stabilization probabilities and does not rely on UDP or
TCP meaning that it makes use of IP directly (Hamamreh, 2012, p.14). OSPF has the advantage
of being an open protocol meaning it can be run by any server or router. Despite being able to

NETWORK AND COMMUNICATIONS 9
assign cost basing on round trip time and reliability, administrators have the privilege to
determine the cost for particular hops.
Enhanced Interior Gateway Routing Protocol (EIGRP) will also work well for the routers
since it is also full-featured just like OSPF. With this protocol, the best route is determined in
consideration of reliability, bandwidth, how the link delays and load. Basing on administrative
distance, EIGRP is the best for instance when you compare with a protocol like RIP (Routing
Information Protocol). Therefore, both OSPF and EIGRP have lesser administrative distances
which prioritize them as far as determining the best route is concerned.
A protocol that Cannot Work
BGP (Border Gateway Protocol) is a good example that cannot be used in the provided
network. This is because BGP is known to function well in networks that are autonomous and
here the routers are seen to exist in the same network. This will be impossible based on the fact
that BGP works well on networks that are not the same. Looking at the routers provided, they
share an AS number that is the same. This is to mean, there has to be an ISP in between the
routers for the purpose of being tagged to the other AS. However, after the ISP has passed the
data to the other router, to avoid dropping the routes, a command known as neighbor allowas-in
will have to be issued so that updates can be injected by BGP on the other.
Network Addresses after Dynamic Routing Configuration
The network classes available are two. This is to mean there will be also two network
addresses after the configuration. The first one will be class A 10.10.10.0/24 and the other one
will be class B 172.16.10.0/24.
Comparison of the Routing Protocols Based on Convergence
assign cost basing on round trip time and reliability, administrators have the privilege to
determine the cost for particular hops.
Enhanced Interior Gateway Routing Protocol (EIGRP) will also work well for the routers
since it is also full-featured just like OSPF. With this protocol, the best route is determined in
consideration of reliability, bandwidth, how the link delays and load. Basing on administrative
distance, EIGRP is the best for instance when you compare with a protocol like RIP (Routing
Information Protocol). Therefore, both OSPF and EIGRP have lesser administrative distances
which prioritize them as far as determining the best route is concerned.
A protocol that Cannot Work
BGP (Border Gateway Protocol) is a good example that cannot be used in the provided
network. This is because BGP is known to function well in networks that are autonomous and
here the routers are seen to exist in the same network. This will be impossible based on the fact
that BGP works well on networks that are not the same. Looking at the routers provided, they
share an AS number that is the same. This is to mean, there has to be an ISP in between the
routers for the purpose of being tagged to the other AS. However, after the ISP has passed the
data to the other router, to avoid dropping the routes, a command known as neighbor allowas-in
will have to be issued so that updates can be injected by BGP on the other.
Network Addresses after Dynamic Routing Configuration
The network classes available are two. This is to mean there will be also two network
addresses after the configuration. The first one will be class A 10.10.10.0/24 and the other one
will be class B 172.16.10.0/24.
Comparison of the Routing Protocols Based on Convergence
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

NETWORK AND COMMUNICATIONS 10
For OSPF to determine the cost of the link and be able to understand the link states, it
first has to send a hallo packet to the neighboring router. Thereafter, it can distinguish which path
is the shortest to the destination or hop so that the packet can be forwarded to the short path.
However, LSA (Link-State Advertisements) in this protocol are seen to be flooded almost
covering the entire area which results in heavy traffic in case of large areas. Due to the flooding
of the LSA, each and every router now has to create a shortest-path tree of its own making the
whole process to be fairly faster.
EIGRP has an advantage over OSPF in that it has five different types of packets which
are an update packet, a hallo packet, a reply packet, and an acknowledgement packet. OSPF only
has a hallo packet. All the packets are well explanatory since their names identify the work of
each packet. EIGRP, therefore, is faster compared to OSPF since there are no loops like the ones
witnessed in OSPF.
BGP, on the other hand, is scalable in that it can solve the problems relating to
convergence in a better way than the other protocols due to its capability to transmit data
between different networks. There is a minimal rate of failure when transmitting data between
autonomous devises when BGP is employed making it the best choice in a Wide Area Network
(Jangra, 2016, p.15).
Question 4
Stop-and-Wait Protocol Diagram
This is an ARQ (Automatic Repeat Request) whose main purpose is to packets are
delivered sequentially and orderly while eliminating errors even if they are witnessed. In this
protocol, an information frame is sent to the receiver by the sender, the sender has to stop and
wait for an acknowledgement (ACK) from the receiver (Qin and Yang, 2012, p.1402). When an
For OSPF to determine the cost of the link and be able to understand the link states, it
first has to send a hallo packet to the neighboring router. Thereafter, it can distinguish which path
is the shortest to the destination or hop so that the packet can be forwarded to the short path.
However, LSA (Link-State Advertisements) in this protocol are seen to be flooded almost
covering the entire area which results in heavy traffic in case of large areas. Due to the flooding
of the LSA, each and every router now has to create a shortest-path tree of its own making the
whole process to be fairly faster.
EIGRP has an advantage over OSPF in that it has five different types of packets which
are an update packet, a hallo packet, a reply packet, and an acknowledgement packet. OSPF only
has a hallo packet. All the packets are well explanatory since their names identify the work of
each packet. EIGRP, therefore, is faster compared to OSPF since there are no loops like the ones
witnessed in OSPF.
BGP, on the other hand, is scalable in that it can solve the problems relating to
convergence in a better way than the other protocols due to its capability to transmit data
between different networks. There is a minimal rate of failure when transmitting data between
autonomous devises when BGP is employed making it the best choice in a Wide Area Network
(Jangra, 2016, p.15).
Question 4
Stop-and-Wait Protocol Diagram
This is an ARQ (Automatic Repeat Request) whose main purpose is to packets are
delivered sequentially and orderly while eliminating errors even if they are witnessed. In this
protocol, an information frame is sent to the receiver by the sender, the sender has to stop and
wait for an acknowledgement (ACK) from the receiver (Qin and Yang, 2012, p.1402). When an
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

NETWORK AND COMMUNICATIONS 11
ACK fails to arrive within time, it is termed as time-out and the sender has to resend the frame
again and then stop and wait for an ACK.
In the diagram, there are three packets being transmitted but it is well understood that no
matter the number of packets being transmitted, the only permitted sequence in stop and wait is
of the numbers which are 0 and 1.
ACK fails to arrive within time, it is termed as time-out and the sender has to resend the frame
again and then stop and wait for an ACK.
In the diagram, there are three packets being transmitted but it is well understood that no
matter the number of packets being transmitted, the only permitted sequence in stop and wait is
of the numbers which are 0 and 1.
NETWORK AND COMMUNICATIONS 12
Duplicate Packet and Acknowledgement
The delay of an ACK can basically occur due to the congestion in a particular network or
in an event when there are issues in the link. The third packed was delayed due to the delay of
ACK of the original packet. After the end of the time-out period due to delayed ACK, the sender
had to resend the packet again. The time-out which is at the sender is used to avoid deadlock
meaning that the receiver has to keep track of packets previously conveyed. The packets are
numbered in a way that the receiver is able to recognize the original packet and discard those
packets that are duplicates. There are sequence numbers which are included in every packet
header for easy identification of original packets by the sender.
Data Acknowledgements and Sender and Receiver Sliding Windows
The receiving window always moves forward compared to the sender’s window for a
packet that is successfully received (correct checksum). The successfully received in-order
packet is the one that determines the sequence number on the ACK that is sent by the receiver.
On the side of the sender’s window, it moves forward past the previously sent packet having a
sequence number of the ACK in the ACK packet received (De et al., 2012, p.2128). Therefore,
the packets that have sequence numbers corresponding with the number on the received ACK are
the only successfully received packets.
Packet Sender Sequence
Number
Receiver Sequence
Number
ACK sequence
Number
1 0 1 1
2 1 0 0
3 0 1 1
Duplicate Third Packet and ACK
Duplicate Packet and Acknowledgement
The delay of an ACK can basically occur due to the congestion in a particular network or
in an event when there are issues in the link. The third packed was delayed due to the delay of
ACK of the original packet. After the end of the time-out period due to delayed ACK, the sender
had to resend the packet again. The time-out which is at the sender is used to avoid deadlock
meaning that the receiver has to keep track of packets previously conveyed. The packets are
numbered in a way that the receiver is able to recognize the original packet and discard those
packets that are duplicates. There are sequence numbers which are included in every packet
header for easy identification of original packets by the sender.
Data Acknowledgements and Sender and Receiver Sliding Windows
The receiving window always moves forward compared to the sender’s window for a
packet that is successfully received (correct checksum). The successfully received in-order
packet is the one that determines the sequence number on the ACK that is sent by the receiver.
On the side of the sender’s window, it moves forward past the previously sent packet having a
sequence number of the ACK in the ACK packet received (De et al., 2012, p.2128). Therefore,
the packets that have sequence numbers corresponding with the number on the received ACK are
the only successfully received packets.
Packet Sender Sequence
Number
Receiver Sequence
Number
ACK sequence
Number
1 0 1 1
2 1 0 0
3 0 1 1
Duplicate Third Packet and ACK
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
1 out of 15
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.




