Network And security Assignment PDF
23 Pages1376 Words18 Views
Added on 2021-06-18
Network And security Assignment PDF
Added on 2021-06-18
ShareRelated Documents
Running head: NETWORK AND SECURITY
Network and Security
Name of the Student
Name of the University
Author Note
Network and Security
Name of the Student
Name of the University
Author Note

1
NETWORK AND SECURITY
Table of Contents
Answer 1..............................................................................................................................2
Answer 2..............................................................................................................................4
Answer 3..............................................................................................................................5
Answer 4..............................................................................................................................6
References..........................................................................................................................24
NETWORK AND SECURITY
Table of Contents
Answer 1..............................................................................................................................2
Answer 2..............................................................................................................................4
Answer 3..............................................................................................................................5
Answer 4..............................................................................................................................6
References..........................................................................................................................24

2
NETWORK AND SECURITY
Answer 1
WIMAX is one kind of wireless network. It dedicates to the advancement of IEEE 802.16
standards. WIMAX works on the basis of wide area network. The network offers relatively faster
comparison to Wi-Fi. WIMAX is commonly termed as 4G and the network is immensely
popular in the world. The WIMAX technology is known to offer long range wireless networking
for both fixed connection as well as the mobile. The technology has been taken up by several
people all over the world and for this reason, appropriate security measures must be taken for
ensuring security of WIMAX. The three most common encryption standards that are used in the
WIMAX technology is the RSA, 3DES or tripe data encryption standard and AES or Advanced
Encryption Method. There are dissimilarities among the three. The encryption keys used for all
the three encryption algorithms are all different from each other. RSA uses public keys as well as
private keys for both encryption and decryption. In case of AES, 256 bit, 128 bit and 192 bit
encryption keys are used. In case of 3DES, each three keys of 56 bits are used for the encryption
purpose. These are the encryption standards which come up with some contrasting features
which are elaborated below-
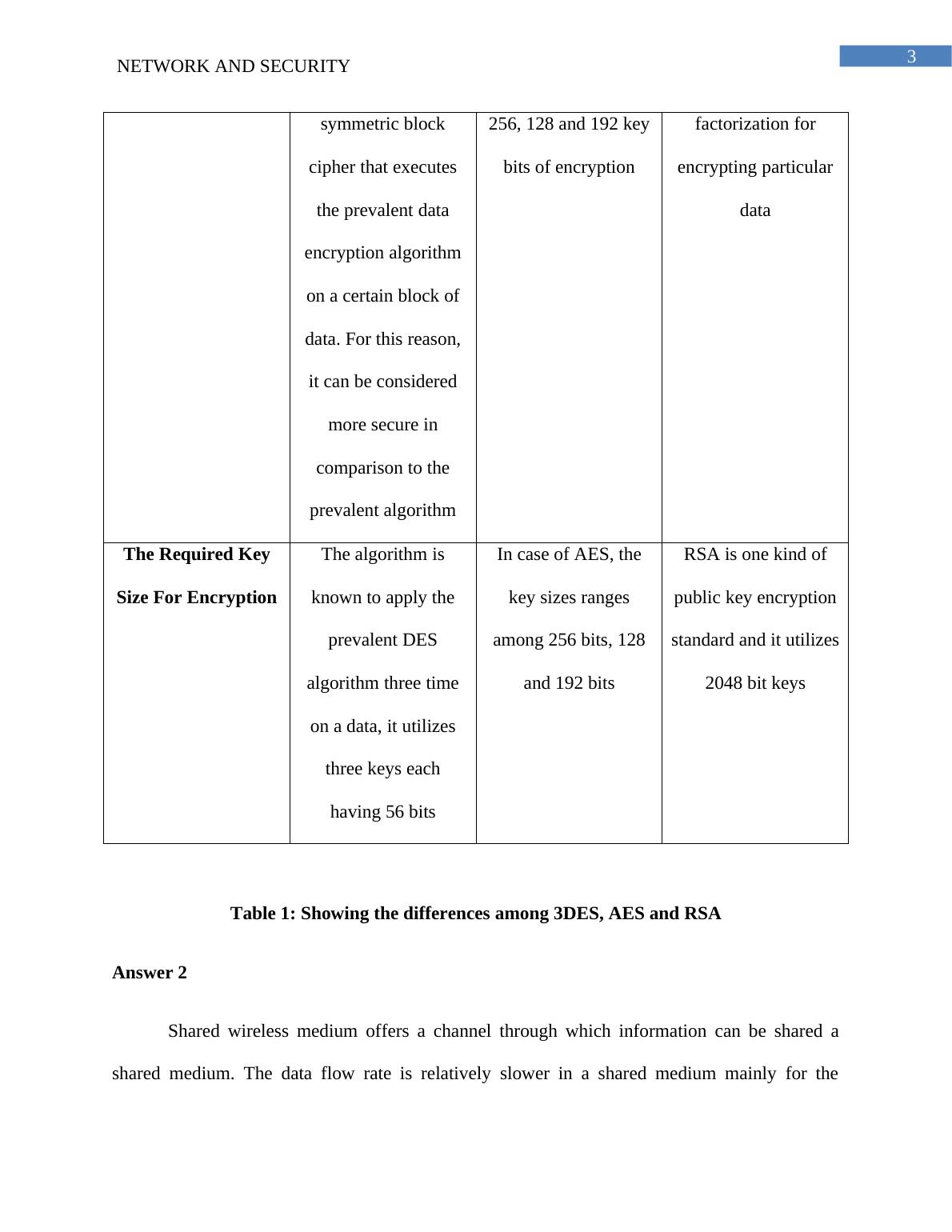
Characteristic
Features
Triple Data
Encryption standard
Advanced
Encryption
Standard
RSA
Definition of the
standard
3DES is the modified
version of the
prevalent data
encryption algorithm.
It is one sort of
AES is one sort of
symmetric block
cipher and it allows
block range of 18 bits.
It allows key bits of
RSA encryption
standard is one kind
of public key
encryption technology
that uses the prime
NETWORK AND SECURITY
Answer 1
WIMAX is one kind of wireless network. It dedicates to the advancement of IEEE 802.16
standards. WIMAX works on the basis of wide area network. The network offers relatively faster
comparison to Wi-Fi. WIMAX is commonly termed as 4G and the network is immensely
popular in the world. The WIMAX technology is known to offer long range wireless networking
for both fixed connection as well as the mobile. The technology has been taken up by several
people all over the world and for this reason, appropriate security measures must be taken for
ensuring security of WIMAX. The three most common encryption standards that are used in the
WIMAX technology is the RSA, 3DES or tripe data encryption standard and AES or Advanced
Encryption Method. There are dissimilarities among the three. The encryption keys used for all
the three encryption algorithms are all different from each other. RSA uses public keys as well as
private keys for both encryption and decryption. In case of AES, 256 bit, 128 bit and 192 bit
encryption keys are used. In case of 3DES, each three keys of 56 bits are used for the encryption
purpose. These are the encryption standards which come up with some contrasting features
which are elaborated below-
Characteristic
Features
Triple Data
Encryption standard
Advanced
Encryption
Standard
RSA
Definition of the
standard
3DES is the modified
version of the
prevalent data
encryption algorithm.
It is one sort of
AES is one sort of
symmetric block
cipher and it allows
block range of 18 bits.
It allows key bits of
RSA encryption
standard is one kind
of public key
encryption technology
that uses the prime

3
NETWORK AND SECURITY
symmetric block
cipher that executes
the prevalent data
encryption algorithm
on a certain block of
data. For this reason,
it can be considered
more secure in
comparison to the
prevalent algorithm
256, 128 and 192 key
bits of encryption
factorization for
encrypting particular
data
The Required Key
Size For Encryption
The algorithm is
known to apply the
prevalent DES
algorithm three time
on a data, it utilizes
three keys each
having 56 bits
In case of AES, the
key sizes ranges
among 256 bits, 128
and 192 bits
RSA is one kind of
public key encryption
standard and it utilizes
2048 bit keys
Table 1: Showing the differences among 3DES, AES and RSA
Answer 2
Shared wireless medium offers a channel through which information can be shared a
shared medium. The data flow rate is relatively slower in a shared medium mainly for the
NETWORK AND SECURITY
symmetric block
cipher that executes
the prevalent data
encryption algorithm
on a certain block of
data. For this reason,
it can be considered
more secure in
comparison to the
prevalent algorithm
256, 128 and 192 key
bits of encryption
factorization for
encrypting particular
data
The Required Key
Size For Encryption
The algorithm is
known to apply the
prevalent DES
algorithm three time
on a data, it utilizes
three keys each
having 56 bits
In case of AES, the
key sizes ranges
among 256 bits, 128
and 192 bits
RSA is one kind of
public key encryption
standard and it utilizes
2048 bit keys
Table 1: Showing the differences among 3DES, AES and RSA
Answer 2
Shared wireless medium offers a channel through which information can be shared a
shared medium. The data flow rate is relatively slower in a shared medium mainly for the
4
NETWORK AND SECURITY
possible collisions. For this reason, traffic coordination is utmost necessity as it is capable to
eliminate the possibility of collisions. All these collisions are responsible for delays that the
wireless network.
In case of shared wireless medium, the traffic gets coordinated with the Carrier Sensed
Multiple Access. The technology is basically utilized to the shared network topologies like the
Ethernet. The Ethernet aids in controlling the particular wireless network. The WIMAX
technology can only to detect any collision. The technology is used in controlling the traffic in
shared wireless media.
Answer 3
In recent times the field of wireless networking has shown significant growth. ZigBee is
has been the result of both low data and low power networking programs. The technology was
mainly developed keeping in mind the military purpose and the personal area network. The
devices having ZigBee Technology operates in the frequency bands of 2.4 GHz, 868 MHz and
915 Khz. One can gain the maximum data rate of 250K bits using ZigBee technology. The
technology can be specified for conducting high level communication by using low cost, small
and low power radios.
Answer 4
NETWORK AND SECURITY
possible collisions. For this reason, traffic coordination is utmost necessity as it is capable to
eliminate the possibility of collisions. All these collisions are responsible for delays that the
wireless network.
In case of shared wireless medium, the traffic gets coordinated with the Carrier Sensed
Multiple Access. The technology is basically utilized to the shared network topologies like the
Ethernet. The Ethernet aids in controlling the particular wireless network. The WIMAX
technology can only to detect any collision. The technology is used in controlling the traffic in
shared wireless media.
Answer 3
In recent times the field of wireless networking has shown significant growth. ZigBee is
has been the result of both low data and low power networking programs. The technology was
mainly developed keeping in mind the military purpose and the personal area network. The
devices having ZigBee Technology operates in the frequency bands of 2.4 GHz, 868 MHz and
915 Khz. One can gain the maximum data rate of 250K bits using ZigBee technology. The
technology can be specified for conducting high level communication by using low cost, small
and low power radios.
Answer 4

5
NETWORK AND SECURITY
NETWORK AND SECURITY

End of preview
Want to access all the pages? Upload your documents or become a member.
Related Documents
Signal Processing and Wireless Networks (pdf)lg...
|5
|1174
|22
Network and Security Assignment PDFlg...
|26
|2127
|51
Wireless Networking Concepts: Assignment (Doc)lg...
|7
|1115
|120
Assignment On Wireless Networking Concepts (Doc)lg...
|9
|1534
|47
Wireless Networking Conceptslg...
|5
|897
|471
Wireless Networking | Assignmentlg...
|9
|1836
|43
