Network and Security : Assignment (Doc)
VerifiedAdded on 2021/06/16
|17
|2434
|25
AI Summary
Contribute Materials
Your contribution can guide someone’s learning journey. Share your
documents today.

Network and security
Secure Best Marks with AI Grader
Need help grading? Try our AI Grader for instant feedback on your assignments.

Table of Contents
1. Summary.............................................................................................................................................2
2. Scope...................................................................................................................................................2
3. Testing methodologies........................................................................................................................3
3.1 Reconnaissance.....................................................................................................................................3
3.2 Scanning................................................................................................................................................4
3.3 Exploitation............................................................................................................................................6
3.4 post- Exploitation..................................................................................................................................6
3.5 clearing tracks/reporting.......................................................................................................................7
4. Findings summary................................................................................................................................7
5. Risk assessment criteria.......................................................................................................................7
6. Penetration test findings.....................................................................................................................8
6.1 High Risk findings.................................................................................................................................11
7. Task 2- Boot 2 Root challenge...........................................................................................................12
8. Exploit attack against target address.................................................................................................14
9. Conclusion.........................................................................................................................................15
References.................................................................................................................................................16
1
1. Summary.............................................................................................................................................2
2. Scope...................................................................................................................................................2
3. Testing methodologies........................................................................................................................3
3.1 Reconnaissance.....................................................................................................................................3
3.2 Scanning................................................................................................................................................4
3.3 Exploitation............................................................................................................................................6
3.4 post- Exploitation..................................................................................................................................6
3.5 clearing tracks/reporting.......................................................................................................................7
4. Findings summary................................................................................................................................7
5. Risk assessment criteria.......................................................................................................................7
6. Penetration test findings.....................................................................................................................8
6.1 High Risk findings.................................................................................................................................11
7. Task 2- Boot 2 Root challenge...........................................................................................................12
8. Exploit attack against target address.................................................................................................14
9. Conclusion.........................................................................................................................................15
References.................................................................................................................................................16
1

1. Summary
The kali Linux is used for perform the penetration testing. Before using the penetration
testing, the white box testing, black box testing, and gray testing are used. The kali Linux and
also the other tools are used for perform the penetration testing. The penetration testing is
done by the following steps.
The intelligence of the network is finding out by using target system. The identified
targets are used for gather the information. Before we start the survey part we must need to
identify the target, and also provide the details about the customer. In this data tells how you
can find the best way to get the effective solution. The kali Linux provide different types of tools
like network investigation, data centers, wireless network, and host system.
The major goal of reconnaissance is use applications and services, acknowledge the
types of system, social engineering information, and also document information. We know that,
in kali Linux we are using several tools and these types of tools are also known as vulnerability
analysis. The assessment objectives are done the below resources, such as asses the target
system vulnerability, priority of vulnerable system, mapping the vulnerable system, and
problem discovery.
2. Scope
The net server is analyzed by using kali Linux. Net server is known as the main server
and it contains the services and this is used to the products. And these kind of server is used as
the framework. And this server appear like generic server and also it includes the single
connection server. We need to study the important objectives for analyze the net server. So in
this situation we are using the penetration testing. The major for using this system is the weak
points of the system is easily recognized. After the penetration analysis is completed by using
the kali Linux, and then we need to perform the Boot to Root activity. The target range is
known as 10.222.0.251 and 10.222.0.252.
2
The kali Linux is used for perform the penetration testing. Before using the penetration
testing, the white box testing, black box testing, and gray testing are used. The kali Linux and
also the other tools are used for perform the penetration testing. The penetration testing is
done by the following steps.
The intelligence of the network is finding out by using target system. The identified
targets are used for gather the information. Before we start the survey part we must need to
identify the target, and also provide the details about the customer. In this data tells how you
can find the best way to get the effective solution. The kali Linux provide different types of tools
like network investigation, data centers, wireless network, and host system.
The major goal of reconnaissance is use applications and services, acknowledge the
types of system, social engineering information, and also document information. We know that,
in kali Linux we are using several tools and these types of tools are also known as vulnerability
analysis. The assessment objectives are done the below resources, such as asses the target
system vulnerability, priority of vulnerable system, mapping the vulnerable system, and
problem discovery.
2. Scope
The net server is analyzed by using kali Linux. Net server is known as the main server
and it contains the services and this is used to the products. And these kind of server is used as
the framework. And this server appear like generic server and also it includes the single
connection server. We need to study the important objectives for analyze the net server. So in
this situation we are using the penetration testing. The major for using this system is the weak
points of the system is easily recognized. After the penetration analysis is completed by using
the kali Linux, and then we need to perform the Boot to Root activity. The target range is
known as 10.222.0.251 and 10.222.0.252.
2
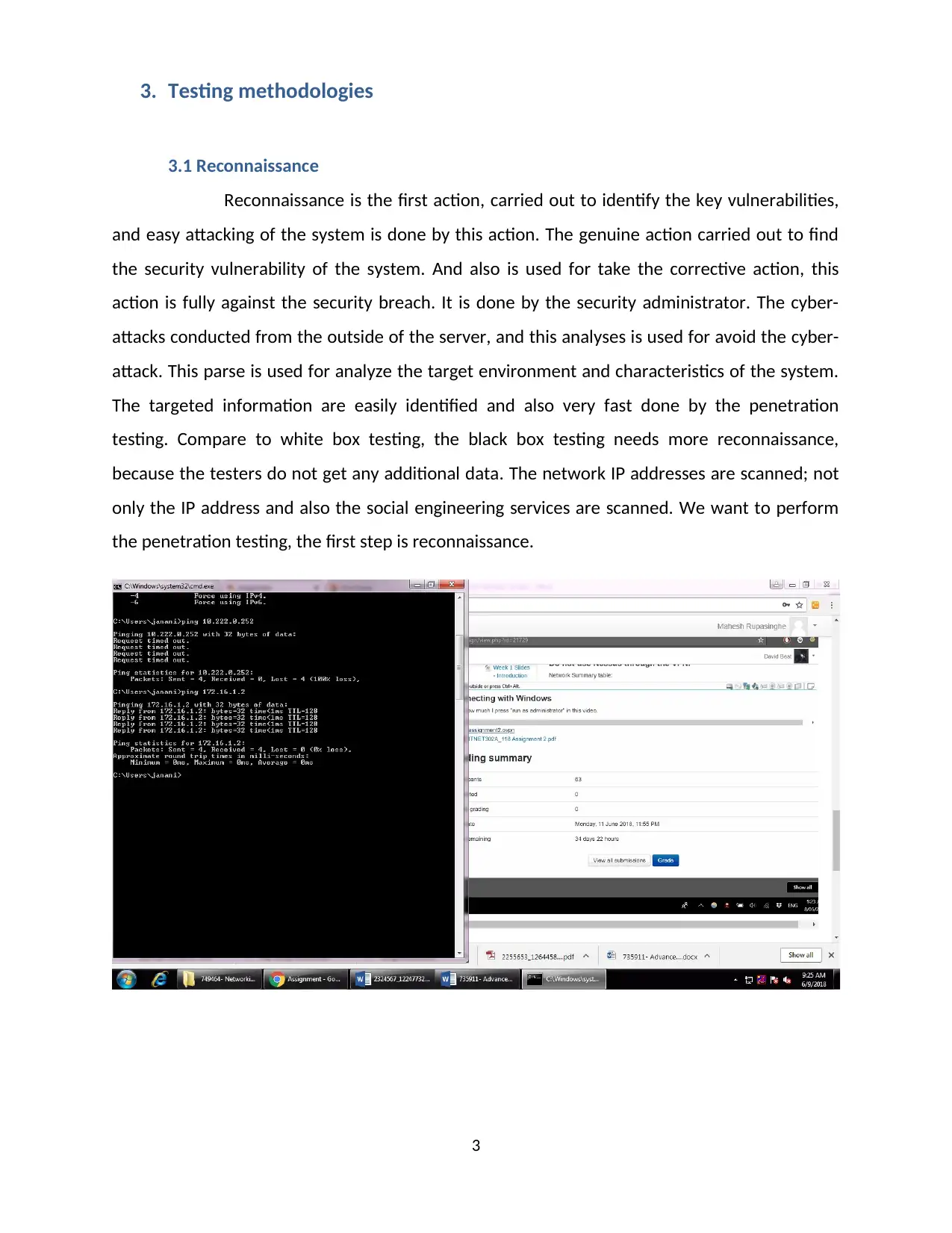
3. Testing methodologies
3.1 Reconnaissance
Reconnaissance is the first action, carried out to identify the key vulnerabilities,
and easy attacking of the system is done by this action. The genuine action carried out to find
the security vulnerability of the system. And also is used for take the corrective action, this
action is fully against the security breach. It is done by the security administrator. The cyber-
attacks conducted from the outside of the server, and this analyses is used for avoid the cyber-
attack. This parse is used for analyze the target environment and characteristics of the system.
The targeted information are easily identified and also very fast done by the penetration
testing. Compare to white box testing, the black box testing needs more reconnaissance,
because the testers do not get any additional data. The network IP addresses are scanned; not
only the IP address and also the social engineering services are scanned. We want to perform
the penetration testing, the first step is reconnaissance.
3
3.1 Reconnaissance
Reconnaissance is the first action, carried out to identify the key vulnerabilities,
and easy attacking of the system is done by this action. The genuine action carried out to find
the security vulnerability of the system. And also is used for take the corrective action, this
action is fully against the security breach. It is done by the security administrator. The cyber-
attacks conducted from the outside of the server, and this analyses is used for avoid the cyber-
attack. This parse is used for analyze the target environment and characteristics of the system.
The targeted information are easily identified and also very fast done by the penetration
testing. Compare to white box testing, the black box testing needs more reconnaissance,
because the testers do not get any additional data. The network IP addresses are scanned; not
only the IP address and also the social engineering services are scanned. We want to perform
the penetration testing, the first step is reconnaissance.
3
Secure Best Marks with AI Grader
Need help grading? Try our AI Grader for instant feedback on your assignments.
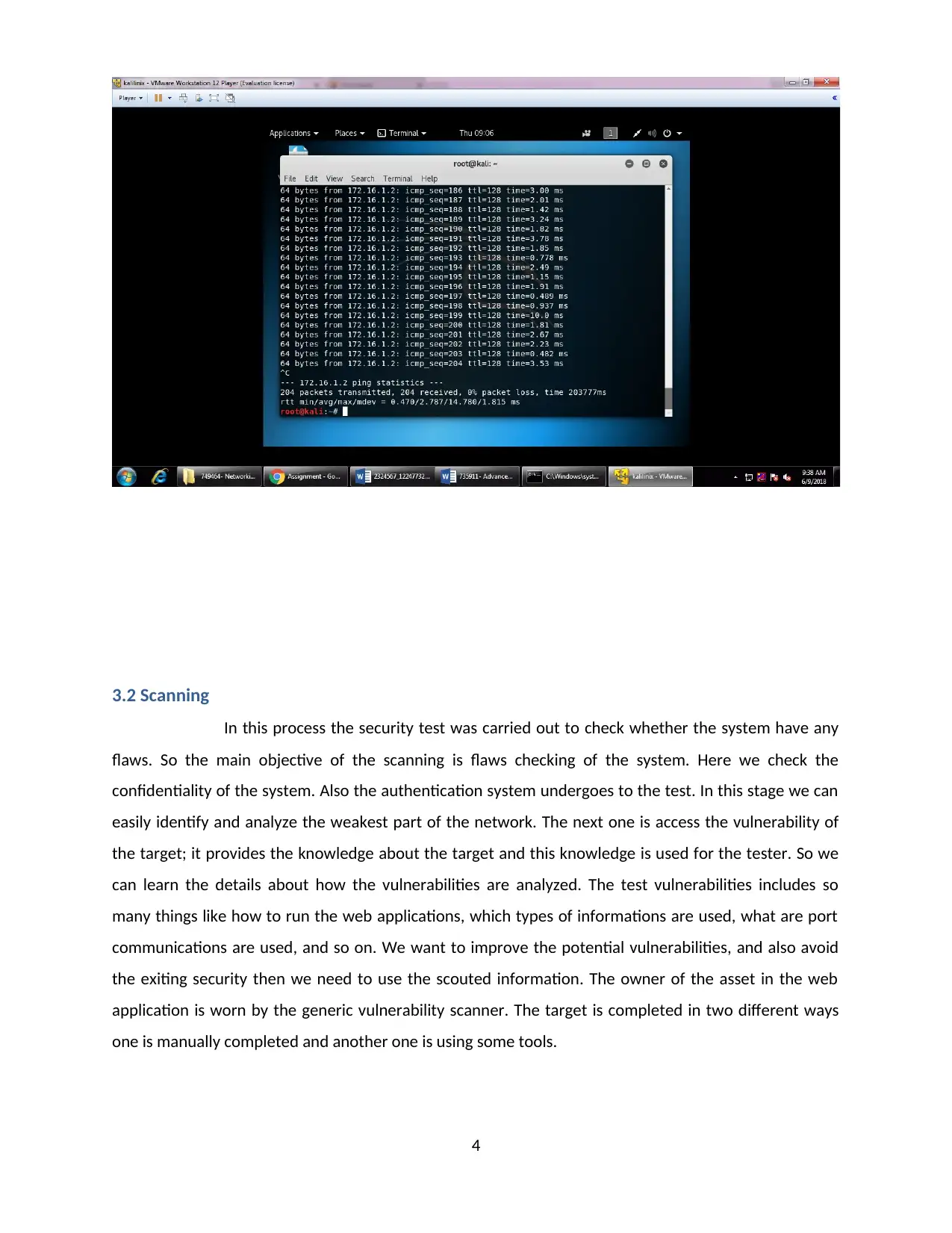
3.2 Scanning
In this process the security test was carried out to check whether the system have any
flaws. So the main objective of the scanning is flaws checking of the system. Here we check the
confidentiality of the system. Also the authentication system undergoes to the test. In this stage we can
easily identify and analyze the weakest part of the network. The next one is access the vulnerability of
the target; it provides the knowledge about the target and this knowledge is used for the tester. So we
can learn the details about how the vulnerabilities are analyzed. The test vulnerabilities includes so
many things like how to run the web applications, which types of informations are used, what are port
communications are used, and so on. We want to improve the potential vulnerabilities, and also avoid
the exiting security then we need to use the scouted information. The owner of the asset in the web
application is worn by the generic vulnerability scanner. The target is completed in two different ways
one is manually completed and another one is using some tools.
4
In this process the security test was carried out to check whether the system have any
flaws. So the main objective of the scanning is flaws checking of the system. Here we check the
confidentiality of the system. Also the authentication system undergoes to the test. In this stage we can
easily identify and analyze the weakest part of the network. The next one is access the vulnerability of
the target; it provides the knowledge about the target and this knowledge is used for the tester. So we
can learn the details about how the vulnerabilities are analyzed. The test vulnerabilities includes so
many things like how to run the web applications, which types of informations are used, what are port
communications are used, and so on. We want to improve the potential vulnerabilities, and also avoid
the exiting security then we need to use the scouted information. The owner of the asset in the web
application is worn by the generic vulnerability scanner. The target is completed in two different ways
one is manually completed and another one is using some tools.
4
5

3.3 Exploitation
This is the process of using the things for our own usage. In our case we need to find the
software or tool, which exploits the data for attackers. The weakness of the system software (OS) is easily
identified and solves it. Exploration is used for check the vulnerability is available or not. And also it is
used for check the current status of the vulnerability. There are two different types of passive services
are used one is assessment and another one is auditing. The vulnerability exploits and all the subsequent
steps are accessed without any proper authentication, so we need to get the permission from the owner
of the system. These kinds of situations are avoided by using exploitation.
It’s fully depending upon the above twp steps. Exploitation is the most famous technique
for identify the vulnerability and also incorrect performance. In the target system use two different ways
for exploits their vulnerable, one is manual and another one is automated. In SQL injunction we are
using different gain administrative access are used for the web application development.
3.4 post- Exploitation
In this test is used for find any traces of the exploiting software or bugs. For this test we
simply perform the IP configure command. That shows all the established connection of the system. So
we can able to find the details about the system attackers. Only the restriction data and resources are
allowed in vulnerable system. The evaluation of privilege includes password cracking, user account,
unlicensed IT space, and so on. If you want to gain the privilege evaluation, then we need to have some
vulnerable toolkits. This toolkit is provided by kali Linux. The post exploitation goals are obtain the
highest privilege, reveal the user account information, and other system access.
6
This is the process of using the things for our own usage. In our case we need to find the
software or tool, which exploits the data for attackers. The weakness of the system software (OS) is easily
identified and solves it. Exploration is used for check the vulnerability is available or not. And also it is
used for check the current status of the vulnerability. There are two different types of passive services
are used one is assessment and another one is auditing. The vulnerability exploits and all the subsequent
steps are accessed without any proper authentication, so we need to get the permission from the owner
of the system. These kinds of situations are avoided by using exploitation.
It’s fully depending upon the above twp steps. Exploitation is the most famous technique
for identify the vulnerability and also incorrect performance. In the target system use two different ways
for exploits their vulnerable, one is manual and another one is automated. In SQL injunction we are
using different gain administrative access are used for the web application development.
3.4 post- Exploitation
In this test is used for find any traces of the exploiting software or bugs. For this test we
simply perform the IP configure command. That shows all the established connection of the system. So
we can able to find the details about the system attackers. Only the restriction data and resources are
allowed in vulnerable system. The evaluation of privilege includes password cracking, user account,
unlicensed IT space, and so on. If you want to gain the privilege evaluation, then we need to have some
vulnerable toolkits. This toolkit is provided by kali Linux. The post exploitation goals are obtain the
highest privilege, reveal the user account information, and other system access.
6
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
3.5 clearing tracks/reporting
In this penetration testing method the last stage is reporting. The reporting phase is one of
the most important phases, it includes two parts one is management and another one is technical part.
It provides the effective information about the graphs, and figures. The vulnerable presentation is
providing by the penetration tester, and the technical description is providing by the document. The
client requirements of the document are meeting by the tester. And also provide the detailed
information about the document.
4. Findings summary
In the risks analysis the list of vulnerabilities are shown and the solution for the vulnerabilities
are found, explained about the vulnerability result. And the attacks are shown using the kali Linux
and also the risks are analyzed by the range. And in that each risk has own value and specified based
on each criteria. And the penetration has implemented using the kali Linux with VMware. And also
the attacks are analyzed through the implementation.
5. Risk assessment criteria
The risk is identified based on the impact and it can be medium, low, high and extreme. And in
that many risks are possible with low and medium. And in this analysis the medium and high risks
are identified and there is an option unlike and it is mentioned for low chance to get a risk. And by
the way the risks are analyzed and reported. And the risk described by moderate, low and critical
based on the risk it analyze the impact level.
Likelihood (Weight Factor) Definition
High (1.0)
The threat-source is highly motivated and sufficiently capable,
and controls to prevent the vulnerability from being exercised
are ineffective
Medium (0.5)
The threat-source is motivated and capable, but controls are in
place that may impede successful exercise of the vulnerability.
Low (0.1)
The threat-source lacks motivation or capability, or controls are
in place to prevent, or at least significantly impede, the
vulnerability from being exercised.
7
In this penetration testing method the last stage is reporting. The reporting phase is one of
the most important phases, it includes two parts one is management and another one is technical part.
It provides the effective information about the graphs, and figures. The vulnerable presentation is
providing by the penetration tester, and the technical description is providing by the document. The
client requirements of the document are meeting by the tester. And also provide the detailed
information about the document.
4. Findings summary
In the risks analysis the list of vulnerabilities are shown and the solution for the vulnerabilities
are found, explained about the vulnerability result. And the attacks are shown using the kali Linux
and also the risks are analyzed by the range. And in that each risk has own value and specified based
on each criteria. And the penetration has implemented using the kali Linux with VMware. And also
the attacks are analyzed through the implementation.
5. Risk assessment criteria
The risk is identified based on the impact and it can be medium, low, high and extreme. And in
that many risks are possible with low and medium. And in this analysis the medium and high risks
are identified and there is an option unlike and it is mentioned for low chance to get a risk. And by
the way the risks are analyzed and reported. And the risk described by moderate, low and critical
based on the risk it analyze the impact level.
Likelihood (Weight Factor) Definition
High (1.0)
The threat-source is highly motivated and sufficiently capable,
and controls to prevent the vulnerability from being exercised
are ineffective
Medium (0.5)
The threat-source is motivated and capable, but controls are in
place that may impede successful exercise of the vulnerability.
Low (0.1)
The threat-source lacks motivation or capability, or controls are
in place to prevent, or at least significantly impede, the
vulnerability from being exercised.
7
From the vulnerability analysis we have found the risks as high risk and also the medium risk. And the
risks are analyzed depending on the vulnerablity and attack. If it is high risk it used to control the
vulnerability and the medium has some range and in this threat source is capable.
In the high risk it analyzed through the conclusion as weak password for the system. So the risk is
considered as high risk . And in the medium risk is analyzed through the conclusion as affects in the
server.
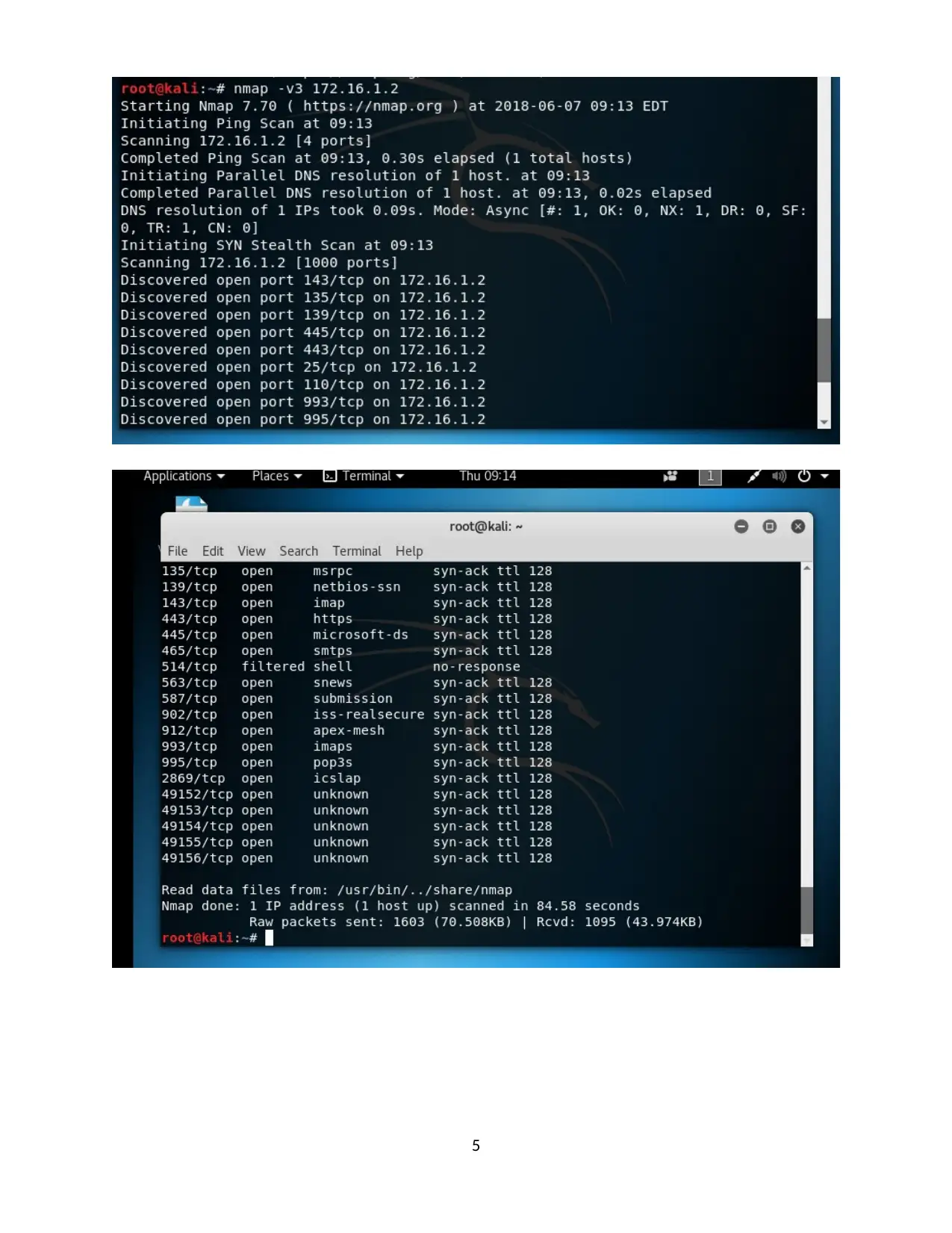
6. Penetration test findings
Penetration testing is used to finding the vulnerabilities in the website or the system by using
the tool such as nmap. In the nmap the testing has accomplished using the proper command. For
finding vulnerabilities the commands are described below.
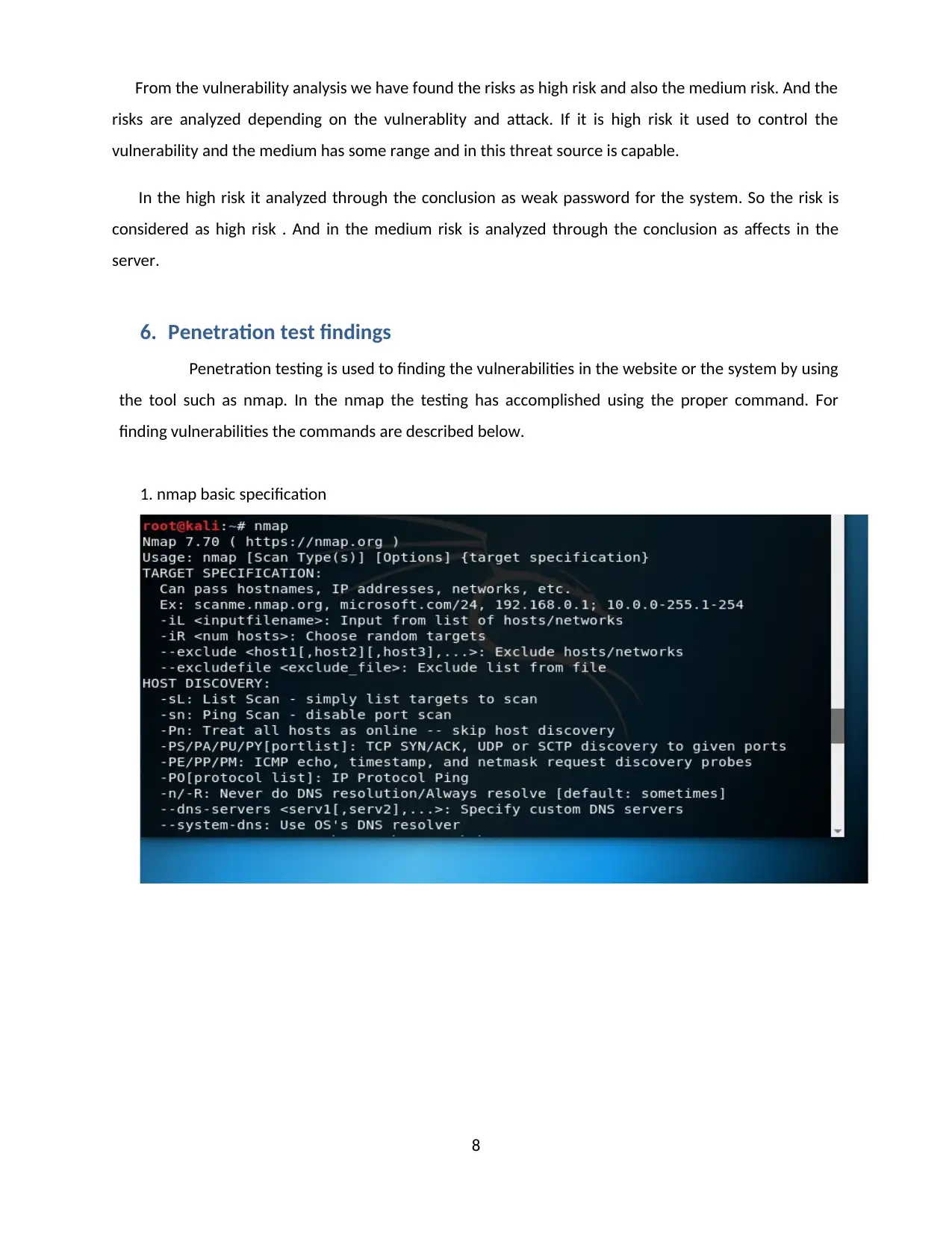
1. nmap basic specification
8
risks are analyzed depending on the vulnerablity and attack. If it is high risk it used to control the
vulnerability and the medium has some range and in this threat source is capable.
In the high risk it analyzed through the conclusion as weak password for the system. So the risk is
considered as high risk . And in the medium risk is analyzed through the conclusion as affects in the
server.
6. Penetration test findings
Penetration testing is used to finding the vulnerabilities in the website or the system by using
the tool such as nmap. In the nmap the testing has accomplished using the proper command. For
finding vulnerabilities the commands are described below.
1. nmap basic specification
8
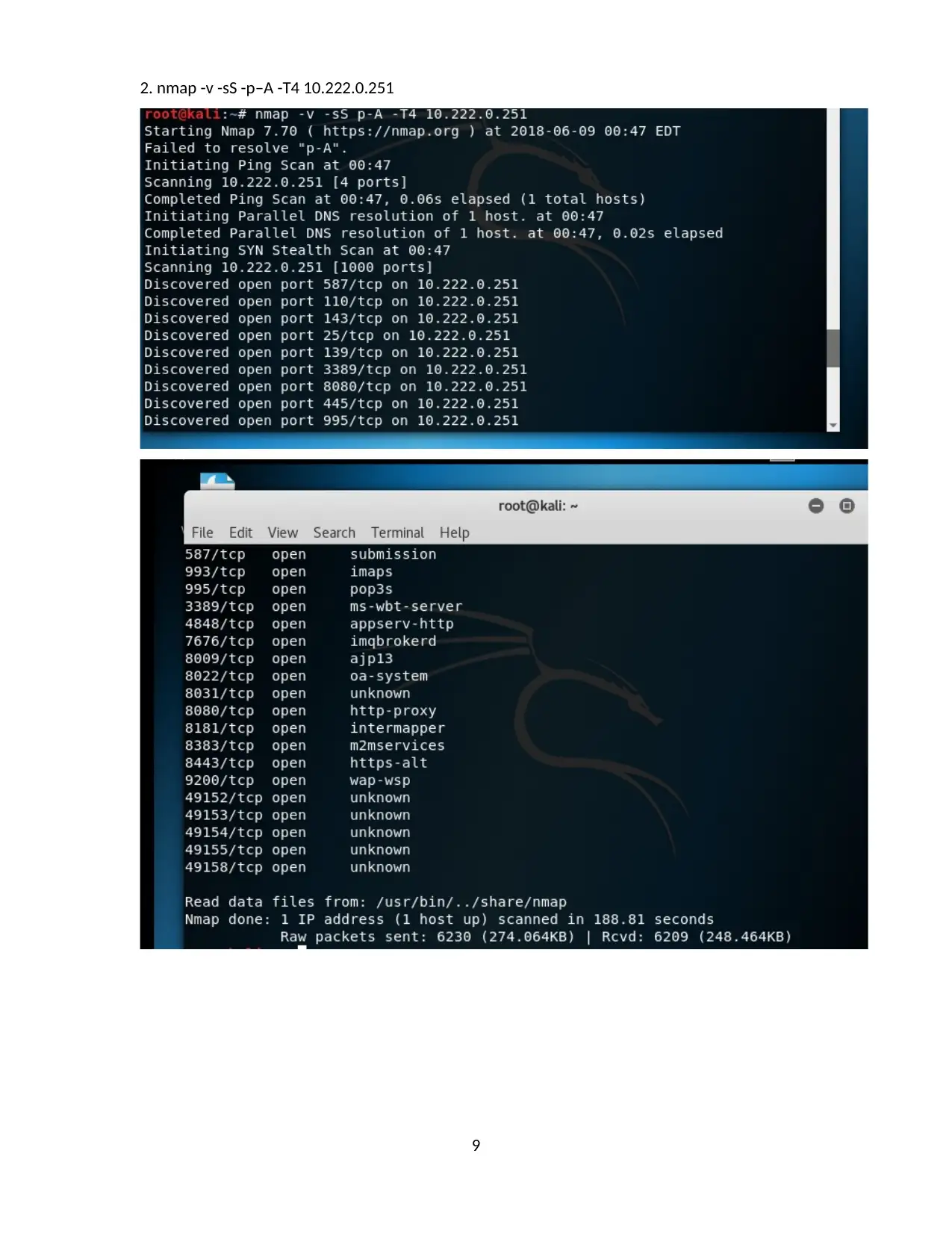
2. nmap -v -sS -p–A -T4 10.222.0.251
9
9
Secure Best Marks with AI Grader
Need help grading? Try our AI Grader for instant feedback on your assignments.
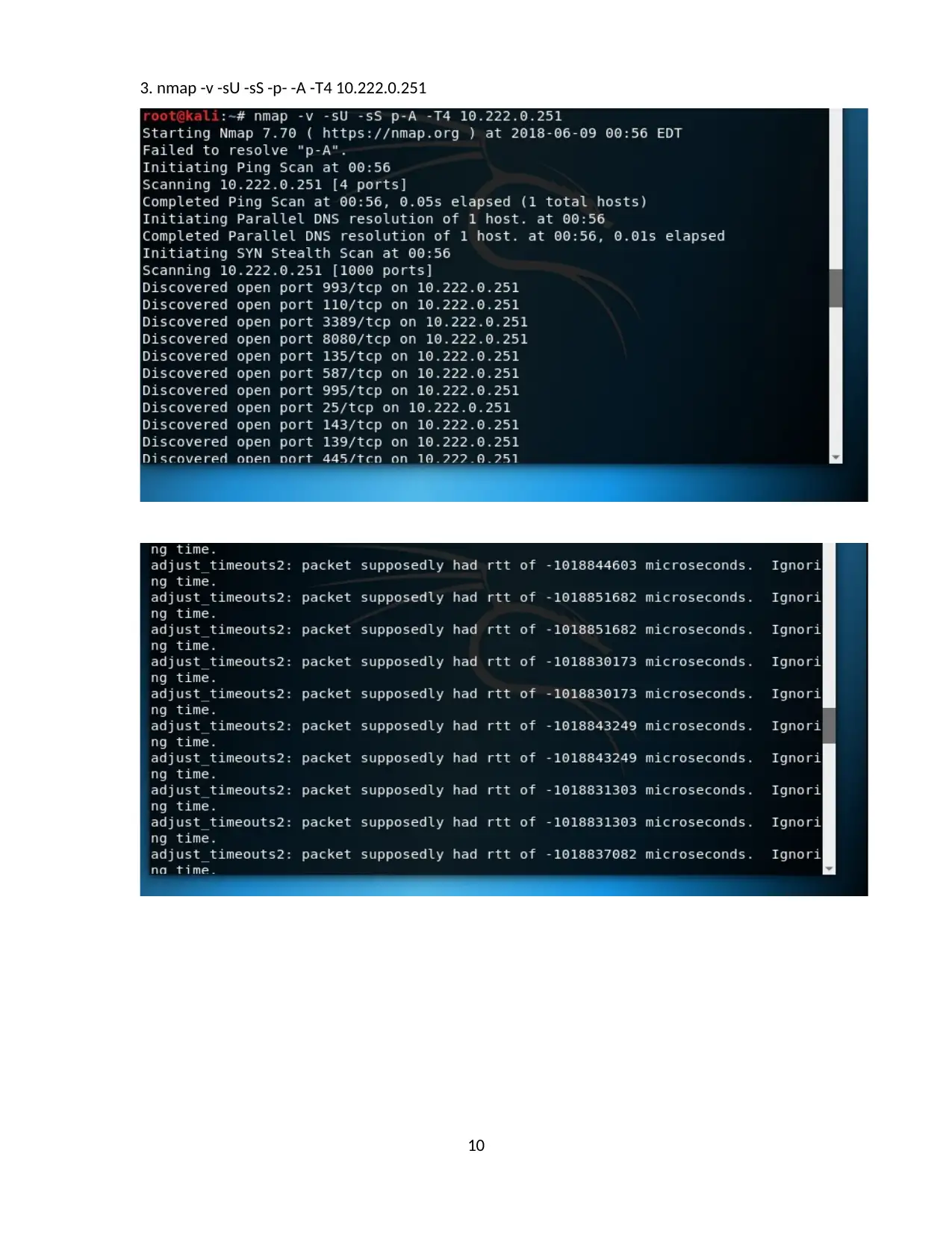
3. nmap -v -sU -sS -p- -A -T4 10.222.0.251
10
10
6.1 High Risk findings
1. From the vulnerability analysis it seems to be high risk in the form has weak passwords for the
authentication and the administration has the weak password. And here more techniques are
used to solve the weakness in the password so resolving this by the way of making strong
password.
Description
The head or administration seems to be weak password.
Impact
The impact of this has to lead the usage of techniques and solved by using the interface.
And the text of the password should be encrypted.
Resolving method
Make the interfaces with the complex passwords.
2. Another risk findings made on the port no 445 analyzed through the running server. And the
vulnerability known as ms17 and the attack such as wannacry in the exploit and create the
vulnerable attack in the network.
11
1. From the vulnerability analysis it seems to be high risk in the form has weak passwords for the
authentication and the administration has the weak password. And here more techniques are
used to solve the weakness in the password so resolving this by the way of making strong
password.
Description
The head or administration seems to be weak password.
Impact
The impact of this has to lead the usage of techniques and solved by using the interface.
And the text of the password should be encrypted.
Resolving method
Make the interfaces with the complex passwords.
2. Another risk findings made on the port no 445 analyzed through the running server. And the
vulnerability known as ms17 and the attack such as wannacry in the exploit and create the
vulnerable attack in the network.
11
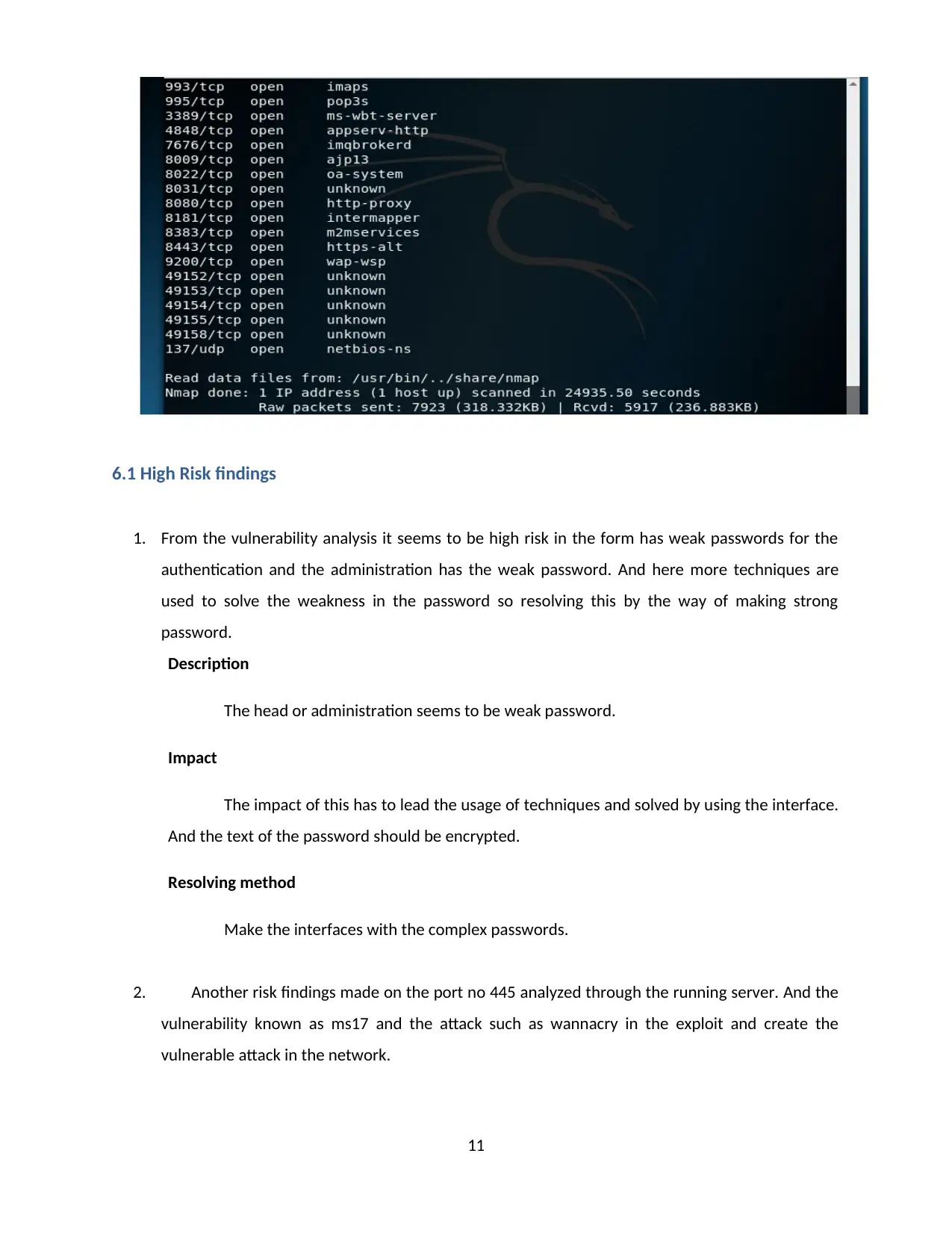
And from the nmap scanning the port is analyzed as 49152 and it is described as a secret
scanning reports. And this method is used as the web interface using the port no such as 49152 to
run in the server. This affect as vulnerable attack to get the details about the data and files about the
login details. And for the simple service 4915 ports are used.
7. Task 2- Boot 2 Root challenge
The boot to root challenge is used in security and also used in downloading as well as
used to make the vulnerable. And it has more exploitation to get the access of the root as
privileged.
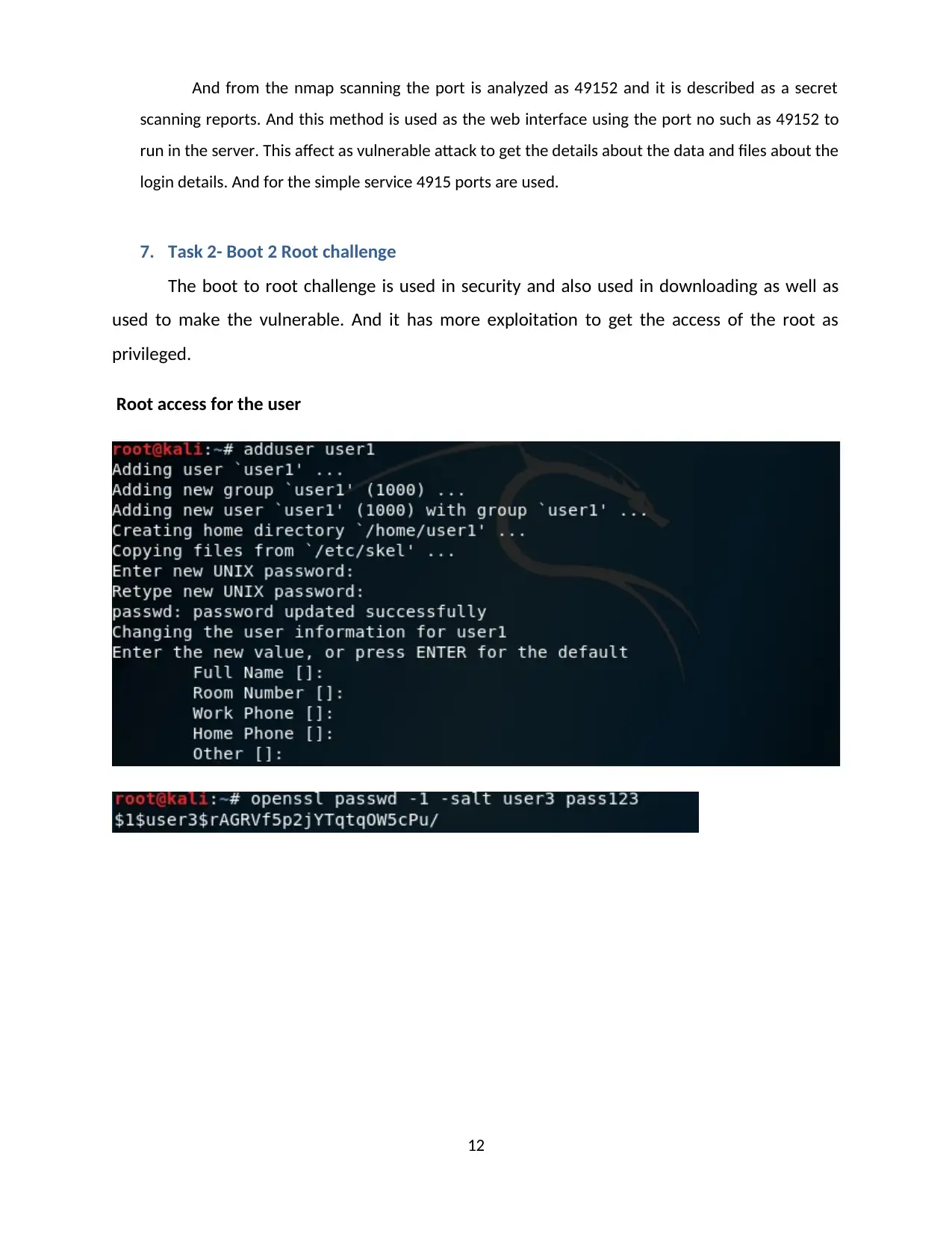
Root access for the user
12
scanning reports. And this method is used as the web interface using the port no such as 49152 to
run in the server. This affect as vulnerable attack to get the details about the data and files about the
login details. And for the simple service 4915 ports are used.
7. Task 2- Boot 2 Root challenge
The boot to root challenge is used in security and also used in downloading as well as
used to make the vulnerable. And it has more exploitation to get the access of the root as
privileged.
Root access for the user
12
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
13
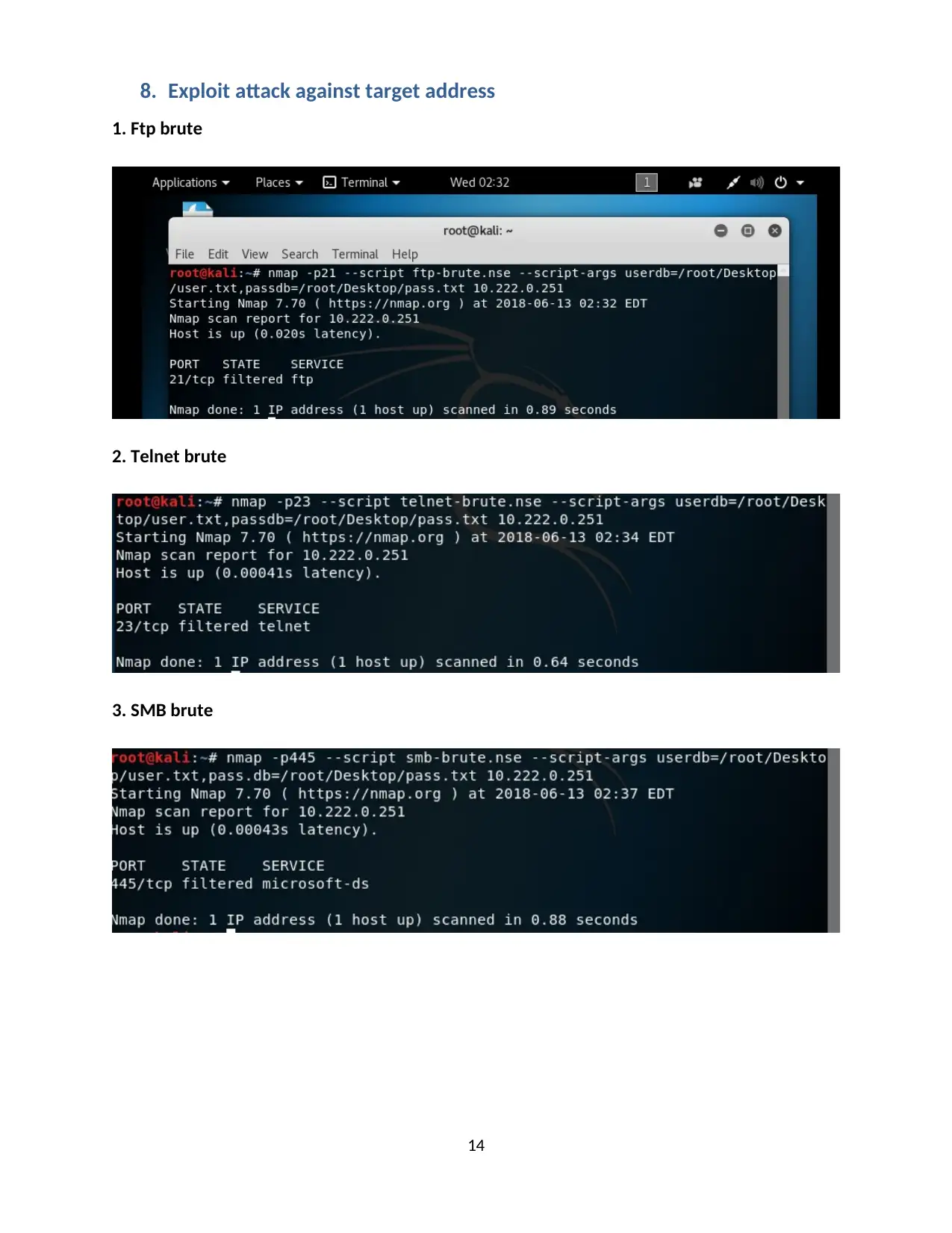
8. Exploit attack against target address
1. Ftp brute
2. Telnet brute
3. SMB brute
14
1. Ftp brute
2. Telnet brute
3. SMB brute
14

4. MYSQL brute
9. Conclusion
The kali Linux provide a set of exploit tools for avoid the vulnerabilities these tools are
known as exploitation tool. And also it includes some social engineering packages. Exploiting
vulnerabilities, gaining access, capturing access, unauthorized data, social engineering
implementation, and system applications are known as major exploit goals. The defection of attacks
is most difficult, and also reduces the security defense attack. It includes deletion of user log, exiting
channel access, and deletes the corrupted message.
Maintaining access means directory of kali Linux. It is used to create a foothold on the
target system. It allows multiple access point on the target network, evidence removing, and so many
things. The communication method is hiding by encryption, and repairs the affected system. And also
the boot to root challenge implemented through the kali Linux by the commands related to the
networks. And the exploit attacks against the target address is implemented through msf console in
Kali Linux.
15
9. Conclusion
The kali Linux provide a set of exploit tools for avoid the vulnerabilities these tools are
known as exploitation tool. And also it includes some social engineering packages. Exploiting
vulnerabilities, gaining access, capturing access, unauthorized data, social engineering
implementation, and system applications are known as major exploit goals. The defection of attacks
is most difficult, and also reduces the security defense attack. It includes deletion of user log, exiting
channel access, and deletes the corrupted message.
Maintaining access means directory of kali Linux. It is used to create a foothold on the
target system. It allows multiple access point on the target network, evidence removing, and so many
things. The communication method is hiding by encryption, and repairs the affected system. And also
the boot to root challenge implemented through the kali Linux by the commands related to the
networks. And the exploit attacks against the target address is implemented through msf console in
Kali Linux.
15
Secure Best Marks with AI Grader
Need help grading? Try our AI Grader for instant feedback on your assignments.

References
Babincev, I. and Vuletic, D. (2016). Web application security analysis using the Kali Linux
operating system. Vojnotehnicki glasnik, 64(2), pp.513-531.
Daly, P. (2000). Review: Linux (Installation, Configuration, Use). The Computer Bulletin, 42(1),
pp.31-31.
Gebser, M., Kaminski, R. and Schaub, T. (2011). aspcud: A Linux Package Configuration Tool
Based on Answer Set Programming. Electronic Proceedings in Theoretical Computer Science, 65,
pp.12-25.
Hunter, P. (2002). Network security architecture without perimeters. Network Security,
2002(12), pp.1-2.
Industrial Network Security. (2015). Network Security, 2015(3), p.4.
Kali Linux – Assuring Security by Penetration Testing. (2014). Network Security, 2014(8), p.4.
Kali.org. (2018). [online] Available at: https://www.kali.org/ [Accessed 11 Jun. 2018].
Kali.org. (2018). [online] Available at: https://www.kali.org/downloads/ [Accessed 11 Jun.
2018].
Network Security goes online. (2007). Network Security, 2007(12), p.20.
Network security needs numbers say CSOs. (2004). Network Security, 2004(3), p.1.
Patel, A. (2015). Network performance without compromising security. Network Security,
2015(1), pp.9-12.
The Practice of Network Security Monitoring. (2014). Network Security, 2014(10), p.4.
16
Babincev, I. and Vuletic, D. (2016). Web application security analysis using the Kali Linux
operating system. Vojnotehnicki glasnik, 64(2), pp.513-531.
Daly, P. (2000). Review: Linux (Installation, Configuration, Use). The Computer Bulletin, 42(1),
pp.31-31.
Gebser, M., Kaminski, R. and Schaub, T. (2011). aspcud: A Linux Package Configuration Tool
Based on Answer Set Programming. Electronic Proceedings in Theoretical Computer Science, 65,
pp.12-25.
Hunter, P. (2002). Network security architecture without perimeters. Network Security,
2002(12), pp.1-2.
Industrial Network Security. (2015). Network Security, 2015(3), p.4.
Kali Linux – Assuring Security by Penetration Testing. (2014). Network Security, 2014(8), p.4.
Kali.org. (2018). [online] Available at: https://www.kali.org/ [Accessed 11 Jun. 2018].
Kali.org. (2018). [online] Available at: https://www.kali.org/downloads/ [Accessed 11 Jun.
2018].
Network Security goes online. (2007). Network Security, 2007(12), p.20.
Network security needs numbers say CSOs. (2004). Network Security, 2004(3), p.1.
Patel, A. (2015). Network performance without compromising security. Network Security,
2015(1), pp.9-12.
The Practice of Network Security Monitoring. (2014). Network Security, 2014(10), p.4.
16
1 out of 17
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
© 2024 | Zucol Services PVT LTD | All rights reserved.





