Detailed Report: Wireshark Analysis of Network Application
VerifiedAdded on 2023/06/11
|18
|2466
|388
Report
AI Summary
This report provides a detailed analysis of network application traffic using Wireshark, a network packet analyzer. The analysis involves capturing network packets on both Linux and Windows platforms, examining the captured data, and analyzing network protocols such as TCP and HTTP. The report includes an overview of Wireshark, the data capture process, and the identification of IP addresses and MAC addresses. It discusses the TCP three-way handshake, DNS queries, and round trip delay. The report also compares Wireshark with Microsoft Message Analyzer, highlighting their strengths and weaknesses in network analysis. The analysis aims to provide insights into network behavior, protocol usage, and potential network issues. The document also touches on network components such as PCs, interface cards, ethernet cables, modems, firewalls, routers, and switches.

NETWORK APPLICATION
Network Application
Student Name
Institution
Date
1
Network Application
Student Name
Institution
Date
1
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

NETWORK APPLICATION
OVERVIEW
It is a not built up source that checks network packets at stage that takes in and make analysis
of the traffics made on the net in two platforms, Linux plus Windows. Graphical User Interface
and Command Line in windows Operating System that possess version of the packet thus
giving an inclusive breakdown of the net code of behavior for every packet captured that adds
color to the specifics of packets based on net protocol adding to possessive functionality for
filtering and observing traffic flow filter that recognizes Transmission control Protocol (Mishra,
2006)
OVERALL DATA
The goal of the scheme is take in information from 2 webs using Wireshark. Data capturing is
carried out at home of the net where connections are via Interface of the Ethernet. In this
analysis carried out in the laboratory, Wireshark is used to mainly for capturing and examining
packets that would be produced amongst different webs that would have been given out
together with the Personal Computer browsers that uses HyperText Transfer Protocol and
Server of the website after analysis are made on the packets and error network. The
presentation made on the net is analyzed using info produced (Tarasov and Malakhov, 2015).
Introduction of Wireshark in the system regulates output, operational load, scalation of windows
and time sequence presentation by the use of produced packets.
2
OVERVIEW
It is a not built up source that checks network packets at stage that takes in and make analysis
of the traffics made on the net in two platforms, Linux plus Windows. Graphical User Interface
and Command Line in windows Operating System that possess version of the packet thus
giving an inclusive breakdown of the net code of behavior for every packet captured that adds
color to the specifics of packets based on net protocol adding to possessive functionality for
filtering and observing traffic flow filter that recognizes Transmission control Protocol (Mishra,
2006)
OVERALL DATA
The goal of the scheme is take in information from 2 webs using Wireshark. Data capturing is
carried out at home of the net where connections are via Interface of the Ethernet. In this
analysis carried out in the laboratory, Wireshark is used to mainly for capturing and examining
packets that would be produced amongst different webs that would have been given out
together with the Personal Computer browsers that uses HyperText Transfer Protocol and
Server of the website after analysis are made on the packets and error network. The
presentation made on the net is analyzed using info produced (Tarasov and Malakhov, 2015).
Introduction of Wireshark in the system regulates output, operational load, scalation of windows
and time sequence presentation by the use of produced packets.
2
NETWORK APPLICATION
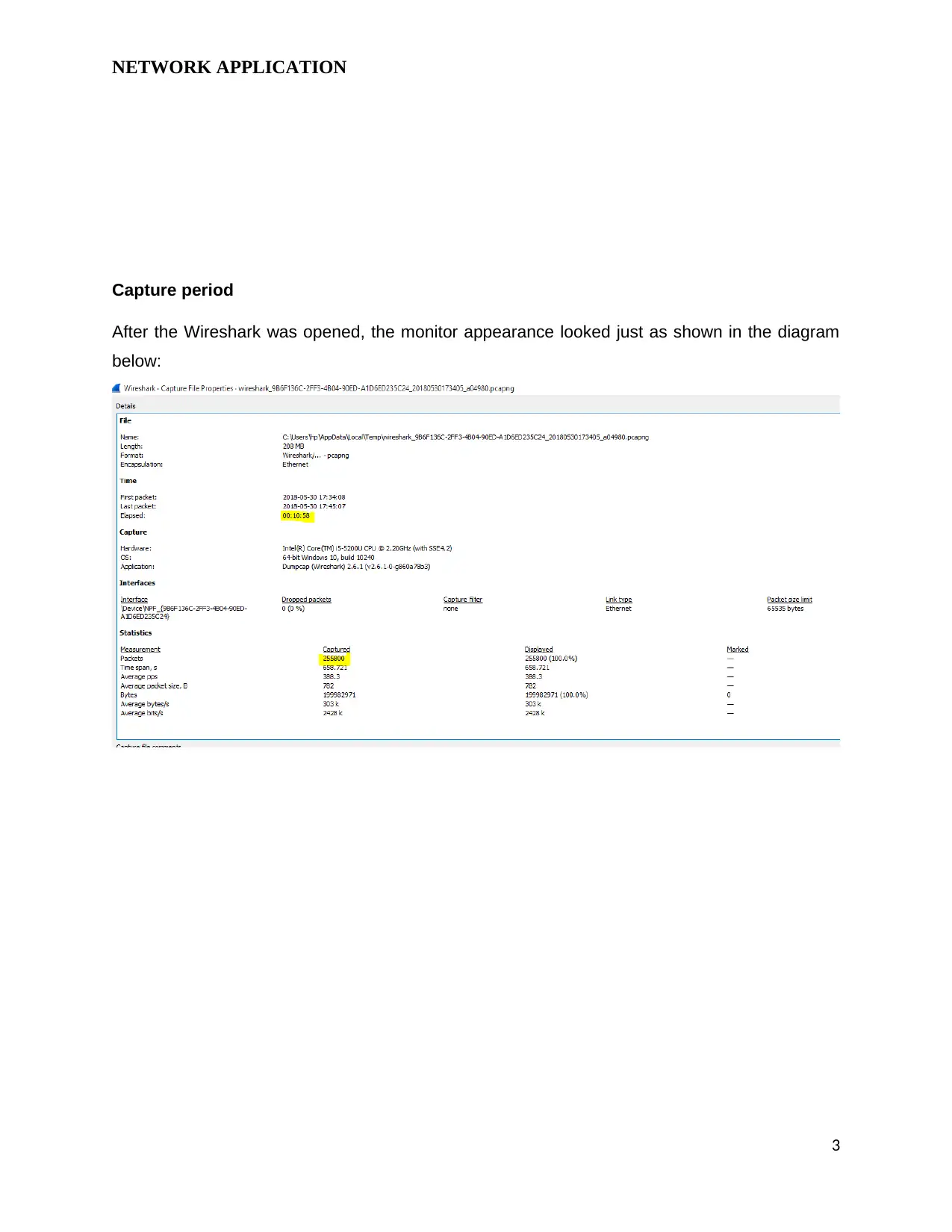
Capture period
After the Wireshark was opened, the monitor appearance looked just as shown in the diagram
below:
3
Capture period
After the Wireshark was opened, the monitor appearance looked just as shown in the diagram
below:
3
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
NETWORK APPLICATION
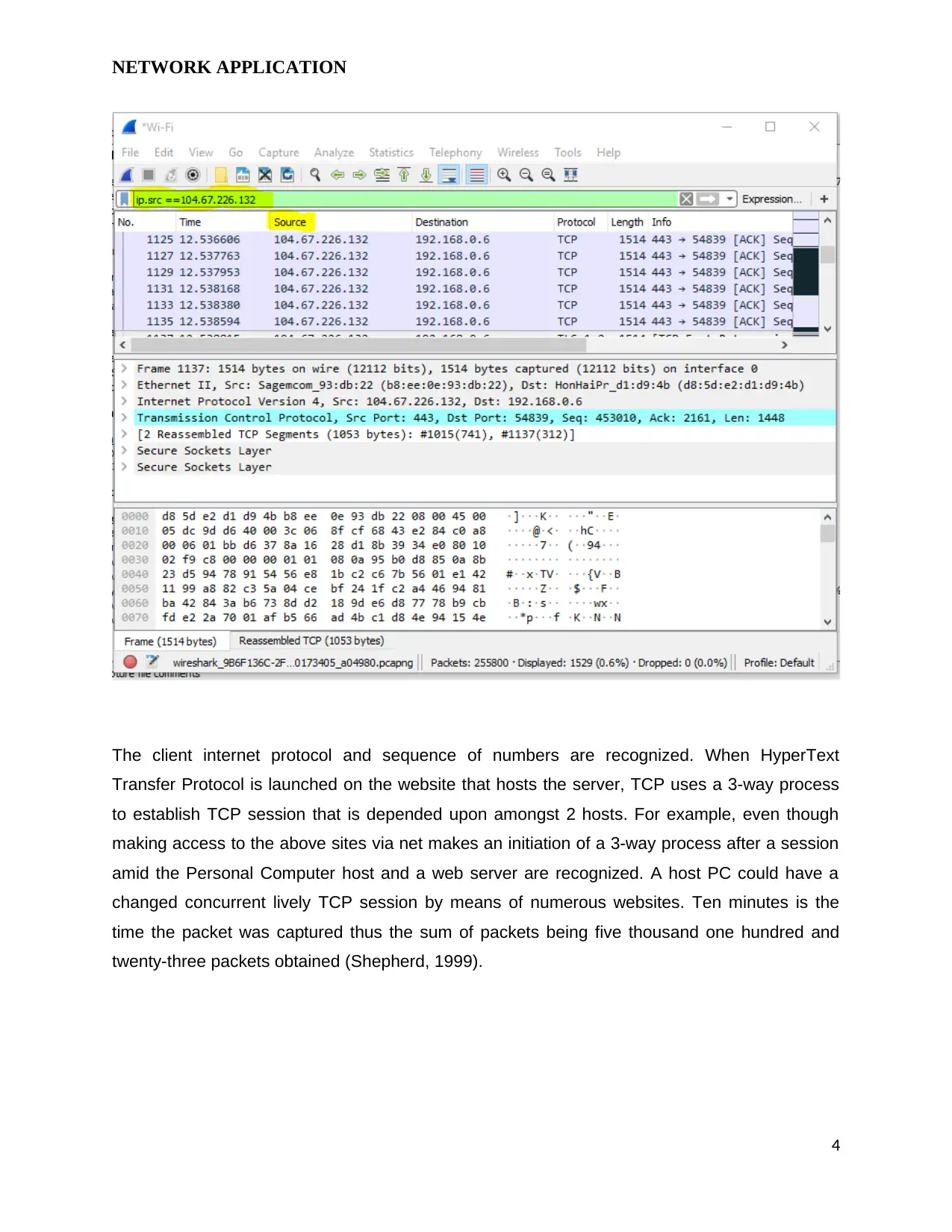
The client internet protocol and sequence of numbers are recognized. When HyperText
Transfer Protocol is launched on the website that hosts the server, TCP uses a 3-way process
to establish TCP session that is depended upon amongst 2 hosts. For example, even though
making access to the above sites via net makes an initiation of a 3-way process after a session
amid the Personal Computer host and a web server are recognized. A host PC could have a
changed concurrent lively TCP session by means of numerous websites. Ten minutes is the
time the packet was captured thus the sum of packets being five thousand one hundred and
twenty-three packets obtained (Shepherd, 1999).
4
The client internet protocol and sequence of numbers are recognized. When HyperText
Transfer Protocol is launched on the website that hosts the server, TCP uses a 3-way process
to establish TCP session that is depended upon amongst 2 hosts. For example, even though
making access to the above sites via net makes an initiation of a 3-way process after a session
amid the Personal Computer host and a web server are recognized. A host PC could have a
changed concurrent lively TCP session by means of numerous websites. Ten minutes is the
time the packet was captured thus the sum of packets being five thousand one hundred and
twenty-three packets obtained (Shepherd, 1999).
4
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
NETWORK APPLICATION
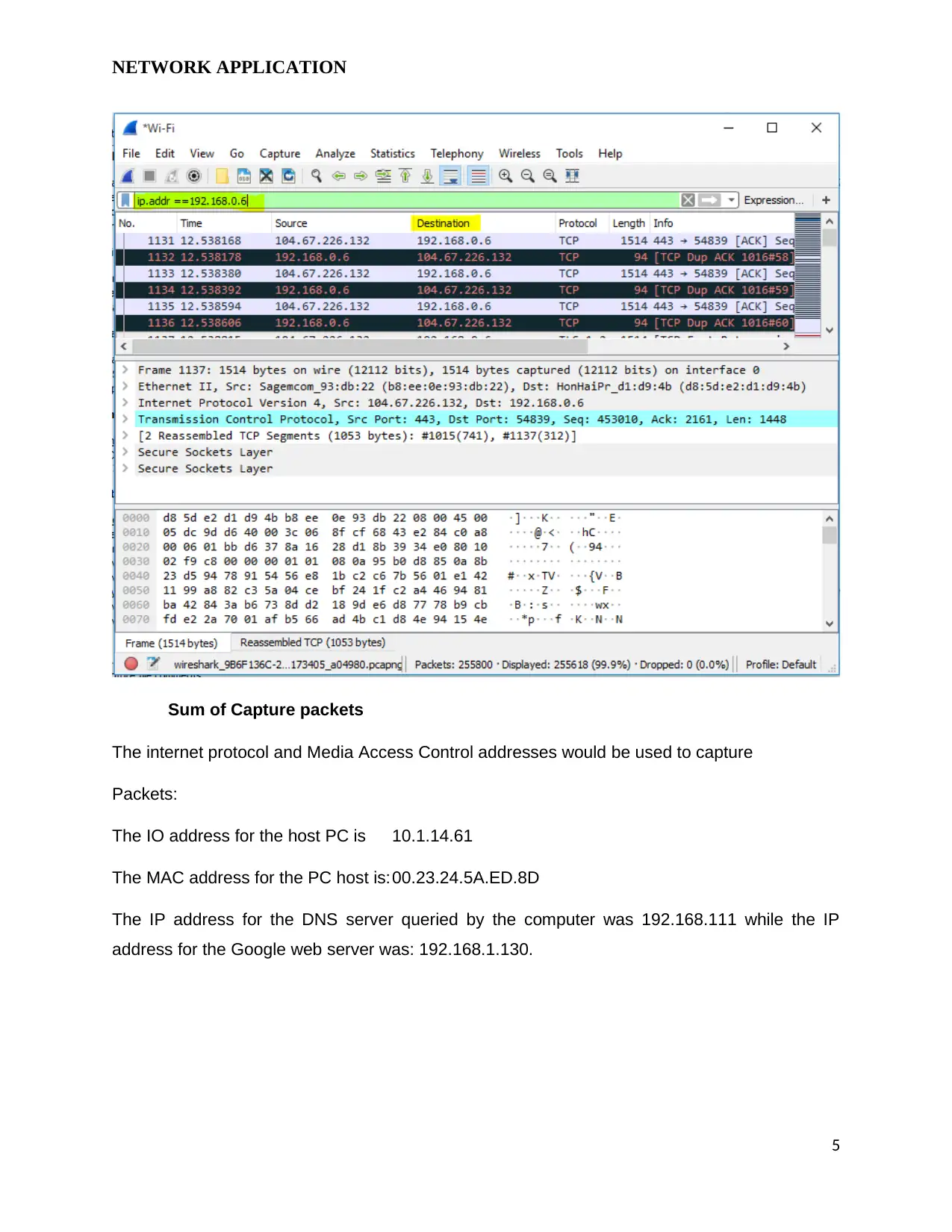
Sum of Capture packets
The internet protocol and Media Access Control addresses would be used to capture
Packets:
The IO address for the host PC is 10.1.14.61
The MAC address for the PC host is:00.23.24.5A.ED.8D
The IP address for the DNS server queried by the computer was 192.168.111 while the IP
address for the Google web server was: 192.168.1.130.
5
Sum of Capture packets
The internet protocol and Media Access Control addresses would be used to capture
Packets:
The IO address for the host PC is 10.1.14.61
The MAC address for the PC host is:00.23.24.5A.ED.8D
The IP address for the DNS server queried by the computer was 192.168.111 while the IP
address for the Google web server was: 192.168.1.130.
5
NETWORK APPLICATION
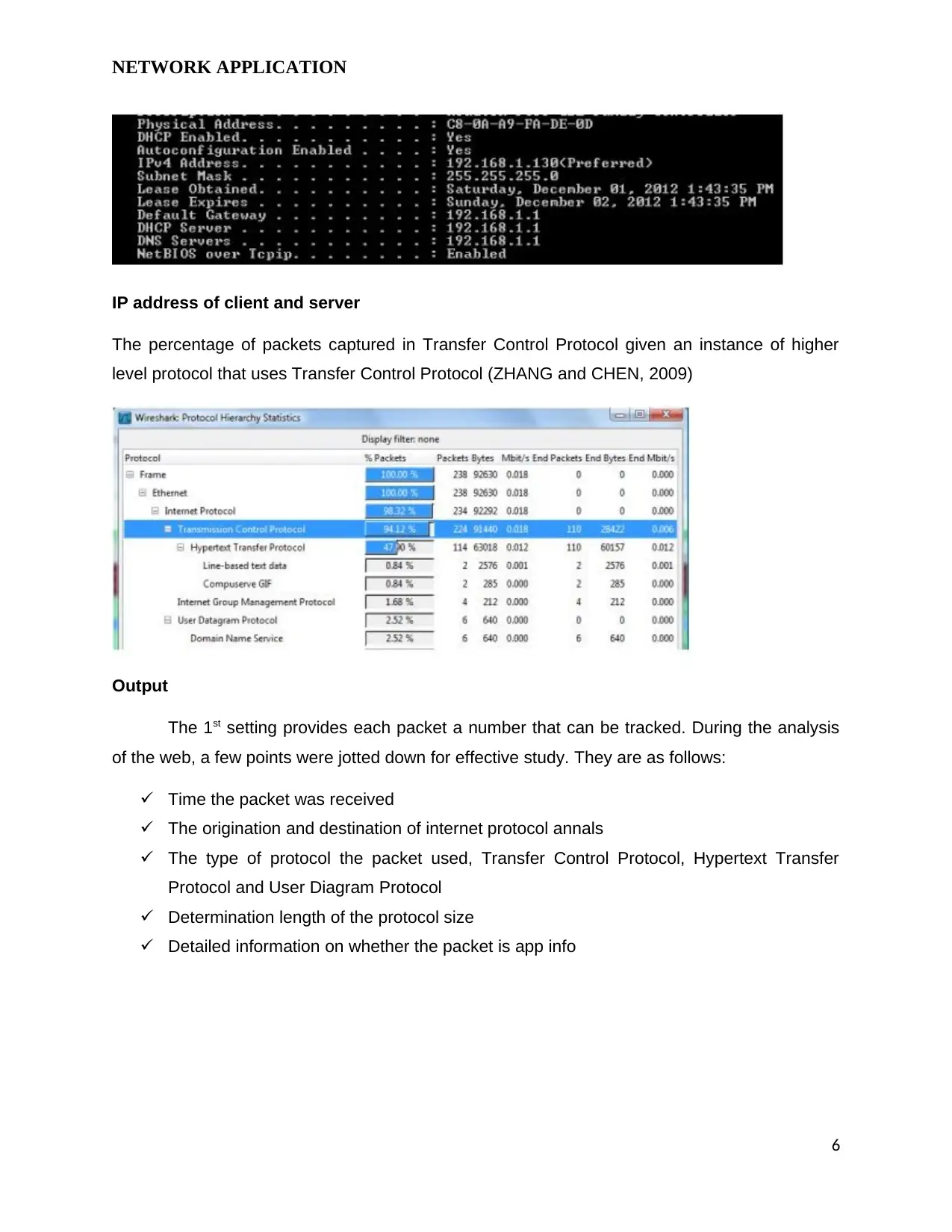
IP address of client and server
The percentage of packets captured in Transfer Control Protocol given an instance of higher
level protocol that uses Transfer Control Protocol (ZHANG and CHEN, 2009)
Output
The 1st setting provides each packet a number that can be tracked. During the analysis
of the web, a few points were jotted down for effective study. They are as follows:
Time the packet was received
The origination and destination of internet protocol annals
The type of protocol the packet used, Transfer Control Protocol, Hypertext Transfer
Protocol and User Diagram Protocol
Determination length of the protocol size
Detailed information on whether the packet is app info
6
IP address of client and server
The percentage of packets captured in Transfer Control Protocol given an instance of higher
level protocol that uses Transfer Control Protocol (ZHANG and CHEN, 2009)
Output
The 1st setting provides each packet a number that can be tracked. During the analysis
of the web, a few points were jotted down for effective study. They are as follows:
Time the packet was received
The origination and destination of internet protocol annals
The type of protocol the packet used, Transfer Control Protocol, Hypertext Transfer
Protocol and User Diagram Protocol
Determination length of the protocol size
Detailed information on whether the packet is app info
6
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
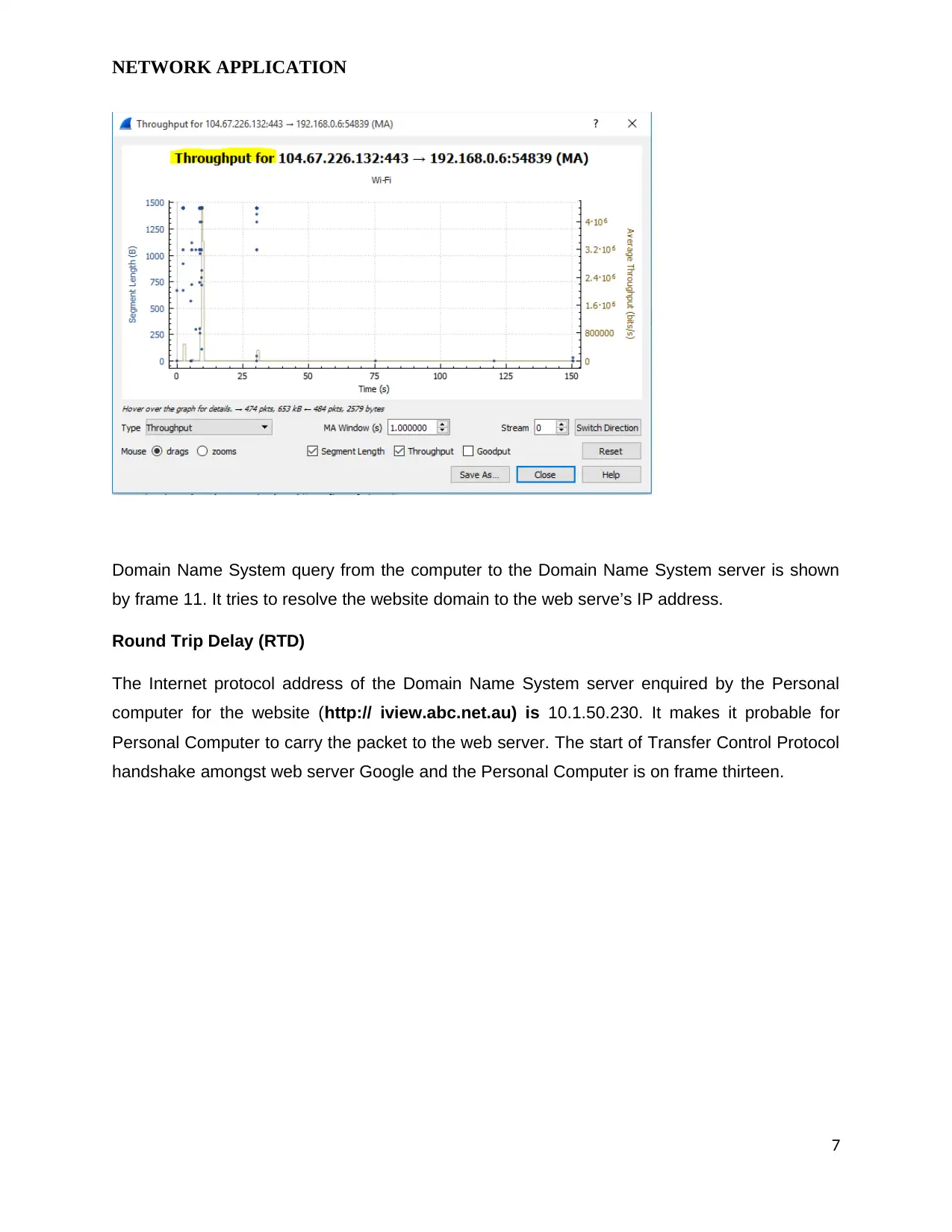
NETWORK APPLICATION
Domain Name System query from the computer to the Domain Name System server is shown
by frame 11. It tries to resolve the website domain to the web serve’s IP address.
Round Trip Delay (RTD)
The Internet protocol address of the Domain Name System server enquired by the Personal
computer for the website (http:// iview.abc.net.au) is 10.1.50.230. It makes it probable for
Personal Computer to carry the packet to the web server. The start of Transfer Control Protocol
handshake amongst web server Google and the Personal Computer is on frame thirteen.
7
Domain Name System query from the computer to the Domain Name System server is shown
by frame 11. It tries to resolve the website domain to the web serve’s IP address.
Round Trip Delay (RTD)
The Internet protocol address of the Domain Name System server enquired by the Personal
computer for the website (http:// iview.abc.net.au) is 10.1.50.230. It makes it probable for
Personal Computer to carry the packet to the web server. The start of Transfer Control Protocol
handshake amongst web server Google and the Personal Computer is on frame thirteen.
7
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
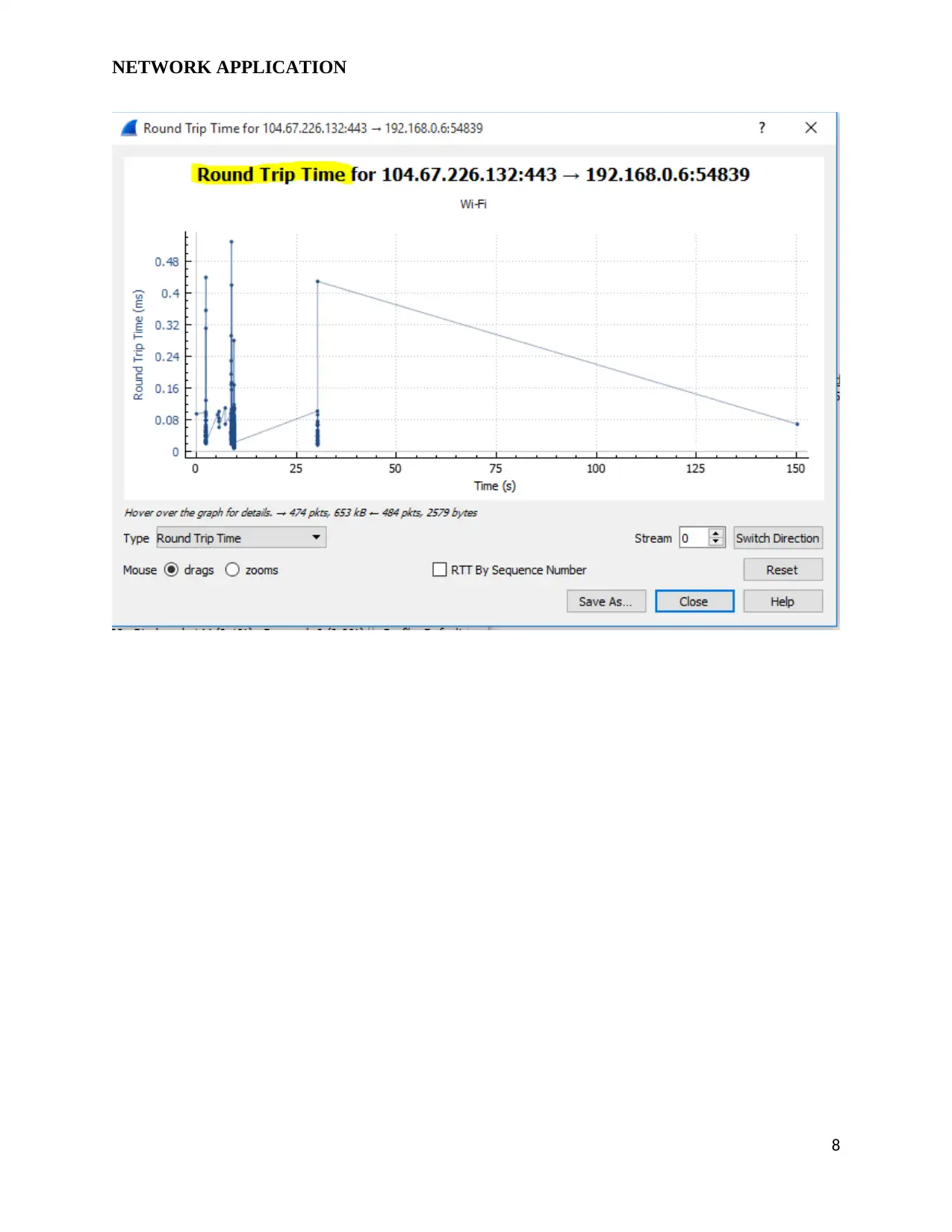
NETWORK APPLICATION
8
8
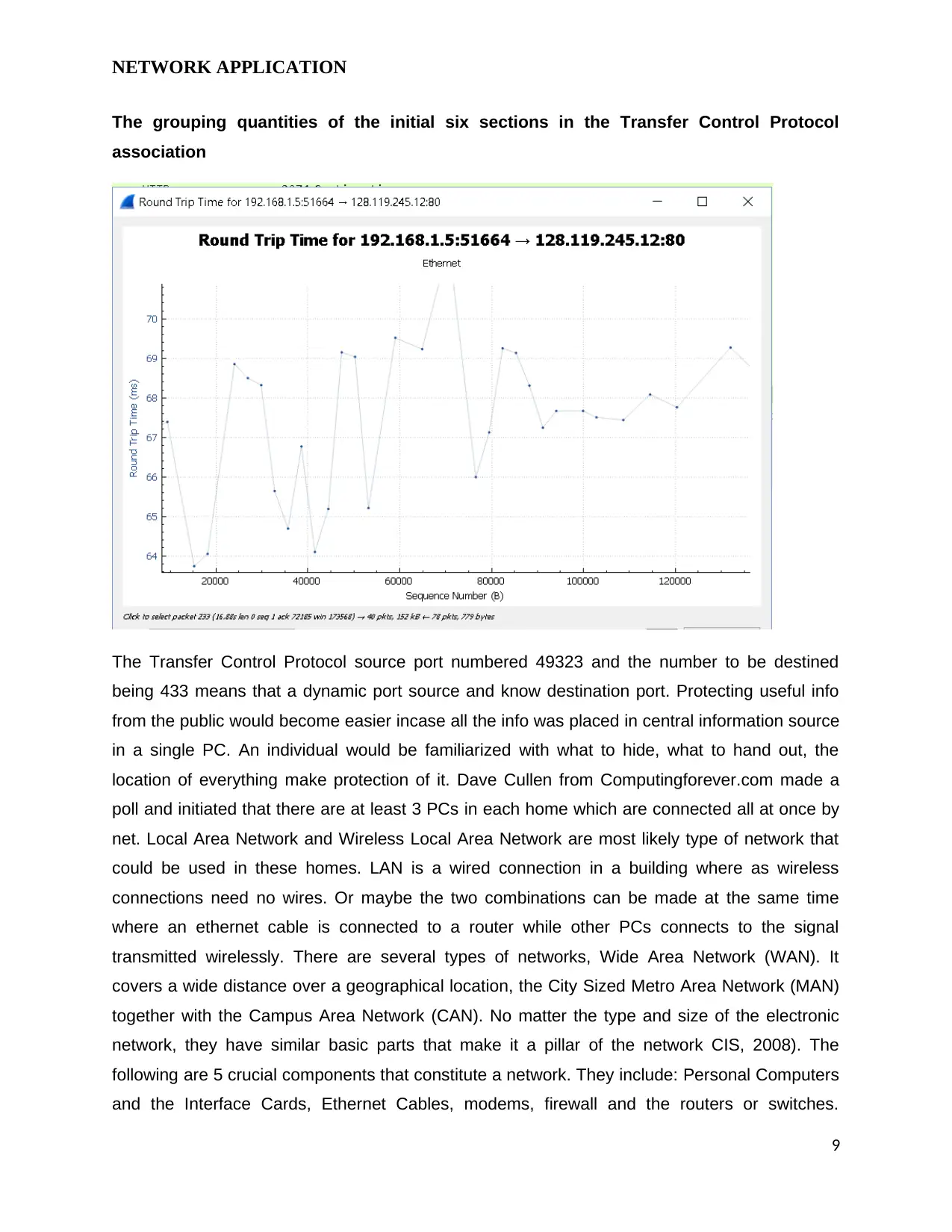
NETWORK APPLICATION
The grouping quantities of the initial six sections in the Transfer Control Protocol
association
The Transfer Control Protocol source port numbered 49323 and the number to be destined
being 433 means that a dynamic port source and know destination port. Protecting useful info
from the public would become easier incase all the info was placed in central information source
in a single PC. An individual would be familiarized with what to hide, what to hand out, the
location of everything make protection of it. Dave Cullen from Computingforever.com made a
poll and initiated that there are at least 3 PCs in each home which are connected all at once by
net. Local Area Network and Wireless Local Area Network are most likely type of network that
could be used in these homes. LAN is a wired connection in a building where as wireless
connections need no wires. Or maybe the two combinations can be made at the same time
where an ethernet cable is connected to a router while other PCs connects to the signal
transmitted wirelessly. There are several types of networks, Wide Area Network (WAN). It
covers a wide distance over a geographical location, the City Sized Metro Area Network (MAN)
together with the Campus Area Network (CAN). No matter the type and size of the electronic
network, they have similar basic parts that make it a pillar of the network CIS, 2008). The
following are 5 crucial components that constitute a network. They include: Personal Computers
and the Interface Cards, Ethernet Cables, modems, firewall and the routers or switches.
9
The grouping quantities of the initial six sections in the Transfer Control Protocol
association
The Transfer Control Protocol source port numbered 49323 and the number to be destined
being 433 means that a dynamic port source and know destination port. Protecting useful info
from the public would become easier incase all the info was placed in central information source
in a single PC. An individual would be familiarized with what to hide, what to hand out, the
location of everything make protection of it. Dave Cullen from Computingforever.com made a
poll and initiated that there are at least 3 PCs in each home which are connected all at once by
net. Local Area Network and Wireless Local Area Network are most likely type of network that
could be used in these homes. LAN is a wired connection in a building where as wireless
connections need no wires. Or maybe the two combinations can be made at the same time
where an ethernet cable is connected to a router while other PCs connects to the signal
transmitted wirelessly. There are several types of networks, Wide Area Network (WAN). It
covers a wide distance over a geographical location, the City Sized Metro Area Network (MAN)
together with the Campus Area Network (CAN). No matter the type and size of the electronic
network, they have similar basic parts that make it a pillar of the network CIS, 2008). The
following are 5 crucial components that constitute a network. They include: Personal Computers
and the Interface Cards, Ethernet Cables, modems, firewall and the routers or switches.
9
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

NETWORK APPLICATION
Personal Computers connect to the net via a wired or wired platform. Both procedures need to
go via the network Interface Card for data transmission from the Pc. There is a one place where
info is stored that is so private. Occasionally, PCs have programs that are always installed in
them to make sure that the data stored remains private. PCs that connected by use of cables
via a router have a standardized networking of cat5e cable. It is a twisted pair cable. Coaxial
cable is another type of the cable that used mainly for running larger areas together with the
fibred optic cable that is purposefully for a wide geographic location e.g. over seas. Digital
signal is converted into analog and analog signals are converted to digital signal by the modem
in to make data packets travel lengthwise from the phonelines plus out of the net. Separation of
the network from network components are done by the Firewall. Hub and switch are component
pieces that try to put almost everything connected via net. They control and allow data
transmission through the net. These two components operate differently but the hub is simplest
compared to other three.
http://www.news.com.au
Transfer Control Protocol Re-transmissions
The Internet Protocol address for the Host PC IS 192.168.1.130
MAC ADDRESS IS C8-Oa-a9-fa-de-od
10
Personal Computers connect to the net via a wired or wired platform. Both procedures need to
go via the network Interface Card for data transmission from the Pc. There is a one place where
info is stored that is so private. Occasionally, PCs have programs that are always installed in
them to make sure that the data stored remains private. PCs that connected by use of cables
via a router have a standardized networking of cat5e cable. It is a twisted pair cable. Coaxial
cable is another type of the cable that used mainly for running larger areas together with the
fibred optic cable that is purposefully for a wide geographic location e.g. over seas. Digital
signal is converted into analog and analog signals are converted to digital signal by the modem
in to make data packets travel lengthwise from the phonelines plus out of the net. Separation of
the network from network components are done by the Firewall. Hub and switch are component
pieces that try to put almost everything connected via net. They control and allow data
transmission through the net. These two components operate differently but the hub is simplest
compared to other three.
http://www.news.com.au
Transfer Control Protocol Re-transmissions
The Internet Protocol address for the Host PC IS 192.168.1.130
MAC ADDRESS IS C8-Oa-a9-fa-de-od
10
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
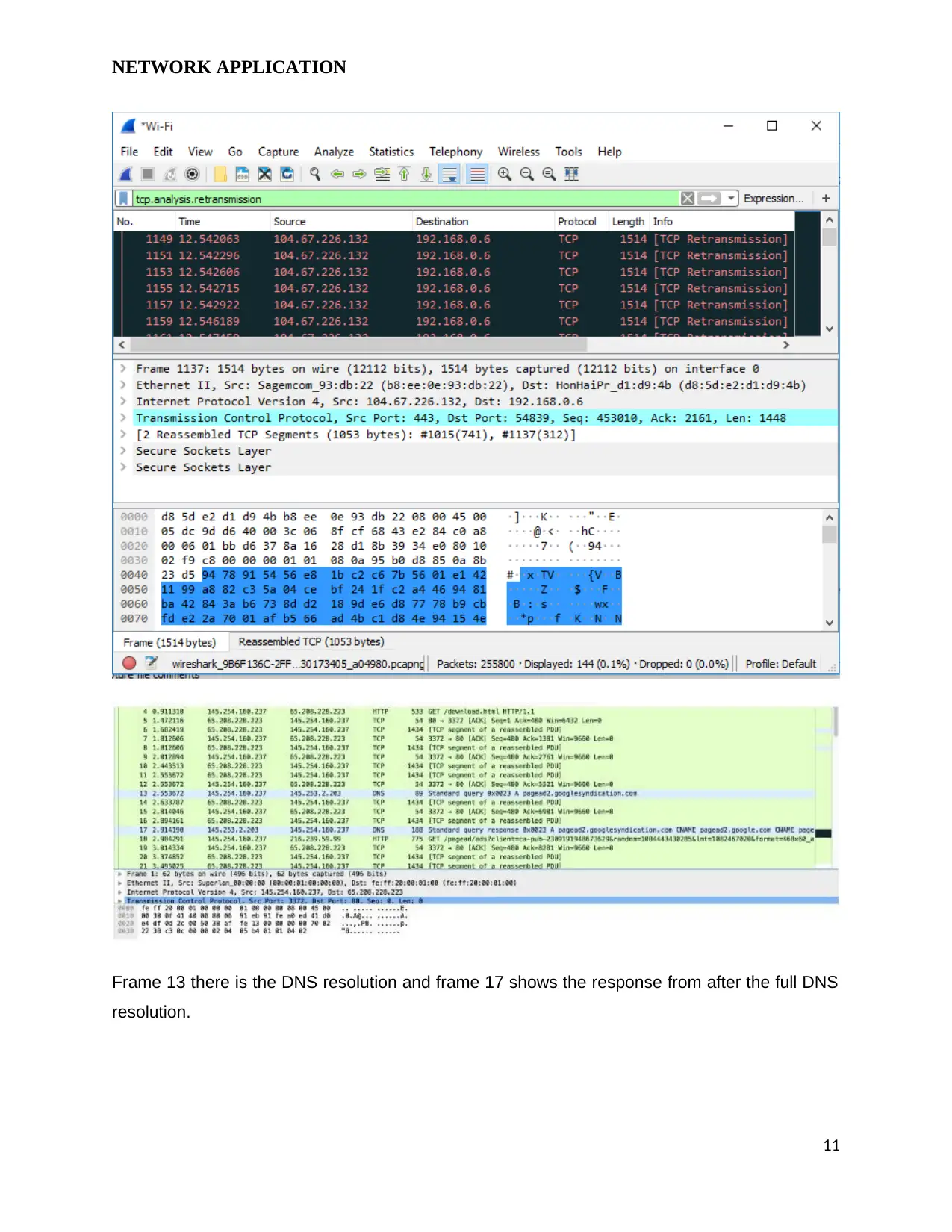
NETWORK APPLICATION
Frame 13 there is the DNS resolution and frame 17 shows the response from after the full DNS
resolution.
11
Frame 13 there is the DNS resolution and frame 17 shows the response from after the full DNS
resolution.
11

NETWORK APPLICATION
The start of three-way handshake among the Google web server and the PC is on frame 15
The IP address of the DNS server queried by the computer for the website (http://
iview.abc.net.au) is 10.1.50.230. This makes it possible for the PC to convey the packet to the
web server.
Re-transmitted segments in the document
12
The start of three-way handshake among the Google web server and the PC is on frame 15
The IP address of the DNS server queried by the computer for the website (http://
iview.abc.net.au) is 10.1.50.230. This makes it possible for the PC to convey the packet to the
web server.
Re-transmitted segments in the document
12
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
1 out of 18
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.



