MN504 Wireshark Analysis: Networked Application Management Report
VerifiedAdded on 2023/03/31
|25
|2343
|65
Report
AI Summary
This report details a network analysis conducted using Wireshark, focusing on capturing and analyzing network traffic from two websites, www.lightfm.com.au and iview.abc.net.au, across both home and university networks. The analysis includes trace routes and packet captures, utilizing protocol analyzers like Wireshark and Microsoft Message Analyzer (MMA). The report presents throughput, round trip time, and packet loss graphs for each website under different network conditions. It further discusses the functional differences between Microsoft Message Analyzer and Wireshark, providing a comparative analysis of their features and usability. The study compares network performance metrics such as throughput, segment length, and packet loss between home and university networks when accessing the specified websites, highlighting variations in network behavior and efficiency. The report concludes by summarizing the findings and emphasizing the effectiveness of network analysis tools in understanding network dynamics.

Running head: NETWORK CAPTURE AND ANALYSIS
Network Capture and Analysis
Name of the Student
Name of the University
Author Note
Network Capture and Analysis
Name of the Student
Name of the University
Author Note
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

1NETWORK CAPTURE AND ANALYSIS
Summary
The purpose of this report is all about conducting trace routes of two different websites
www.lightfm.com.au and iview.abc.net.au, once from the home network and then from the
university network by the group of students. From one website, multiple images need to be
captured, while from the other various content needs to be streamed followed by a comparison of
the graphs between both the networks are discussed. The report begins by showing the trace routes
and packet capture of the two websites. In this process the websites are traced and the packages
recorded with the help of protocol analysers like Wireshark and MMA or Microsoft Message
Analyser. After conducting the trace routes, the throughput, round trip time and packet loss based
graphs and charts are presented twice with for each website. Once from the university network and
then from the home or workgroup network. After discussing about the differences, difference of
functioning between Microsoft Message Analyser and Wireshark gets explained in detail. Then
conducted the comparison of the two applications the report ends with concluding notes.
Summary
The purpose of this report is all about conducting trace routes of two different websites
www.lightfm.com.au and iview.abc.net.au, once from the home network and then from the
university network by the group of students. From one website, multiple images need to be
captured, while from the other various content needs to be streamed followed by a comparison of
the graphs between both the networks are discussed. The report begins by showing the trace routes
and packet capture of the two websites. In this process the websites are traced and the packages
recorded with the help of protocol analysers like Wireshark and MMA or Microsoft Message
Analyser. After conducting the trace routes, the throughput, round trip time and packet loss based
graphs and charts are presented twice with for each website. Once from the university network and
then from the home or workgroup network. After discussing about the differences, difference of
functioning between Microsoft Message Analyser and Wireshark gets explained in detail. Then
conducted the comparison of the two applications the report ends with concluding notes.

2NETWORK CAPTURE AND ANALYSIS
Table of Contents
Introduction...............................................................................................................................3
Part 1..........................................................................................................................................4
Home network...................................................................................................................4
Trace route.........................................................................................................................4
Trace route.........................................................................................................................4
University network.............................................................................................................5
Trace route.........................................................................................................................5
Trace route.........................................................................................................................5
Part 2......................................................................................................................................6
Home network...................................................................................................................6
Trace route.........................................................................................................................6
University Network..........................................................................................................11
Part3.................................................................................................................................17
Microsoft Message Analyser (MMA)...............................................................................21
Conclusion................................................................................................................................22
Bibliography.............................................................................................................................23
Table of Contents
Introduction...............................................................................................................................3
Part 1..........................................................................................................................................4
Home network...................................................................................................................4
Trace route.........................................................................................................................4
Trace route.........................................................................................................................4
University network.............................................................................................................5
Trace route.........................................................................................................................5
Trace route.........................................................................................................................5
Part 2......................................................................................................................................6
Home network...................................................................................................................6
Trace route.........................................................................................................................6
University Network..........................................................................................................11
Part3.................................................................................................................................17
Microsoft Message Analyser (MMA)...............................................................................21
Conclusion................................................................................................................................22
Bibliography.............................................................................................................................23
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

3NETWORK CAPTURE AND ANALYSIS
Introduction
This report concerns conducting trace routes of two websites www.lightfm.com.au and
iview.abc.net.au, once from the home network and then from the university network by the group
of students and then a comparison of the graphs between both the networks are discussed. The
report begins by showing the trace routes and packet capture of the two websites. In this process
the websites are traced and the packages recorded with the help of protocol analysers like
Wireshark and MMA or Microsoft Message Analyser [1]. After conducting the trace routes, the
throughput, round trip time and packet loss based graphs and charts are presented twice with for
each website. Once from the university network and then from the home or workgroup network.
After discussing about the differences, difference of functioning between Microsoft Message
Analyser and Wireshark gets explained in detail. Then conducted the comparison of the two
applications the report ends with concluding notes.
Introduction
This report concerns conducting trace routes of two websites www.lightfm.com.au and
iview.abc.net.au, once from the home network and then from the university network by the group
of students and then a comparison of the graphs between both the networks are discussed. The
report begins by showing the trace routes and packet capture of the two websites. In this process
the websites are traced and the packages recorded with the help of protocol analysers like
Wireshark and MMA or Microsoft Message Analyser [1]. After conducting the trace routes, the
throughput, round trip time and packet loss based graphs and charts are presented twice with for
each website. Once from the university network and then from the home or workgroup network.
After discussing about the differences, difference of functioning between Microsoft Message
Analyser and Wireshark gets explained in detail. Then conducted the comparison of the two
applications the report ends with concluding notes.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

4NETWORK CAPTURE AND ANALYSIS
General Statistics
Part 1: Time of Capture number of packets and client server IP
Home network
In this section the group of users are tasked with tracing websites and capturing packets for
loading multiple images as well as streaming content for long durations from the home network. The
websites from which packets have been captured are www.lightfm.com.au and iview.abc.net.au.
The following data have been gathered from the packet capture of the network activity on
the two websites. These are 9 different criteria namely the time of day of commencing packet
capture, number of DNS packets obtained, number of ICMP packets obtained, number of SSL
packets obtained, number of SSDP packets obtained, number of TCP packets obtained, number of
packets that were lost, the IP address of client computer and the IP address of the network server.
Trace route
www.lightfm.com.au
1. Time of capture: 10:36 AM
2. DNS packets: 74
3. ICMP packets: 165
4. SSL packets: 413
5. SSDP packets: 497
6. TCP packets: 3020
7. Lost packets: 0
8. IP address of client: 10.10.30.107
9. IP address of server: 182.156.217.124
Trace route
iview.abc.net.au
1. Time 10:49AM
2. DNS packets: 74
3. ICMP packets: 133
4. SSL packets: 303
5. SSDP packets: 421
6. TCP packets: 2944
General Statistics
Part 1: Time of Capture number of packets and client server IP
Home network
In this section the group of users are tasked with tracing websites and capturing packets for
loading multiple images as well as streaming content for long durations from the home network. The
websites from which packets have been captured are www.lightfm.com.au and iview.abc.net.au.
The following data have been gathered from the packet capture of the network activity on
the two websites. These are 9 different criteria namely the time of day of commencing packet
capture, number of DNS packets obtained, number of ICMP packets obtained, number of SSL
packets obtained, number of SSDP packets obtained, number of TCP packets obtained, number of
packets that were lost, the IP address of client computer and the IP address of the network server.
Trace route
www.lightfm.com.au
1. Time of capture: 10:36 AM
2. DNS packets: 74
3. ICMP packets: 165
4. SSL packets: 413
5. SSDP packets: 497
6. TCP packets: 3020
7. Lost packets: 0
8. IP address of client: 10.10.30.107
9. IP address of server: 182.156.217.124
Trace route
iview.abc.net.au
1. Time 10:49AM
2. DNS packets: 74
3. ICMP packets: 133
4. SSL packets: 303
5. SSDP packets: 421
6. TCP packets: 2944

5NETWORK CAPTURE AND ANALYSIS
7. Lost packets: 0
8. IP address of client: 10.10.30.107
9. IP address of server: 54.66.253.179
University network
In this section the group of users are tasked with tracing websites and capturing
packets for loading multiple images as well as streaming content for long durations from the
university network. The websites from which packets have been captured are
www.lightfm.com.au and iview.abc.net.au.
The following data have been gathered from the packet capture of the network
activity on the two websites. These are 9 different criteria namely the time of day of
commencing packet capture, number of DNS packets obtained, number of ICMP packets
obtained, number of SSL packets obtained, number of SSDP packets obtained, number of
TCP packets obtained, number of packets that were lost, the IP address of client computer
and the IP address of server computer.
Trace route
www.lightfm.com.au
1. Time 13:00AM
2. DNS packets: 56
3. ICMP packets: 107
4. SSL packets: 132
5. SSDP packets: 214
6. TCP packets: 1128
7. Lost packets: 0
8. IP address of client: 10.10.30.107
9. IP address of server: 182.156.217.124
With the trace route and packet capture of www.lightfm.com.au conducted, the group of students
perform the same for iview.abc.net.au. Here also the analysis has been conducted in the same
process and the criteria of information for analysis of the network activity remains the same [16].
Trace route
iview.abc.net.au
7. Lost packets: 0
8. IP address of client: 10.10.30.107
9. IP address of server: 54.66.253.179
University network
In this section the group of users are tasked with tracing websites and capturing
packets for loading multiple images as well as streaming content for long durations from the
university network. The websites from which packets have been captured are
www.lightfm.com.au and iview.abc.net.au.
The following data have been gathered from the packet capture of the network
activity on the two websites. These are 9 different criteria namely the time of day of
commencing packet capture, number of DNS packets obtained, number of ICMP packets
obtained, number of SSL packets obtained, number of SSDP packets obtained, number of
TCP packets obtained, number of packets that were lost, the IP address of client computer
and the IP address of server computer.
Trace route
www.lightfm.com.au
1. Time 13:00AM
2. DNS packets: 56
3. ICMP packets: 107
4. SSL packets: 132
5. SSDP packets: 214
6. TCP packets: 1128
7. Lost packets: 0
8. IP address of client: 10.10.30.107
9. IP address of server: 182.156.217.124
With the trace route and packet capture of www.lightfm.com.au conducted, the group of students
perform the same for iview.abc.net.au. Here also the analysis has been conducted in the same
process and the criteria of information for analysis of the network activity remains the same [16].
Trace route
iview.abc.net.au
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
6NETWORK CAPTURE AND ANALYSIS
1. Time 13:24AM
2. DNS packets: 73
3. ICMP packets: 133
4. SSL packets: 303
5. SSDP packets: 421
6. TCP packets: 2944
7. Lost packets: 0
8. IP address of client: 10.10.30.107
9. IP address of server: 54.66.253.179
Network Analysis
Part 2: Screenshots and analysis
Home network
Here the trace routes of the two websites are again performed by the group of
students followed by the subsequent packet capture of the process in wireshark. This
process is conducted on the home or workgroup network of the students.
Trace route
www.lightfm.com.au
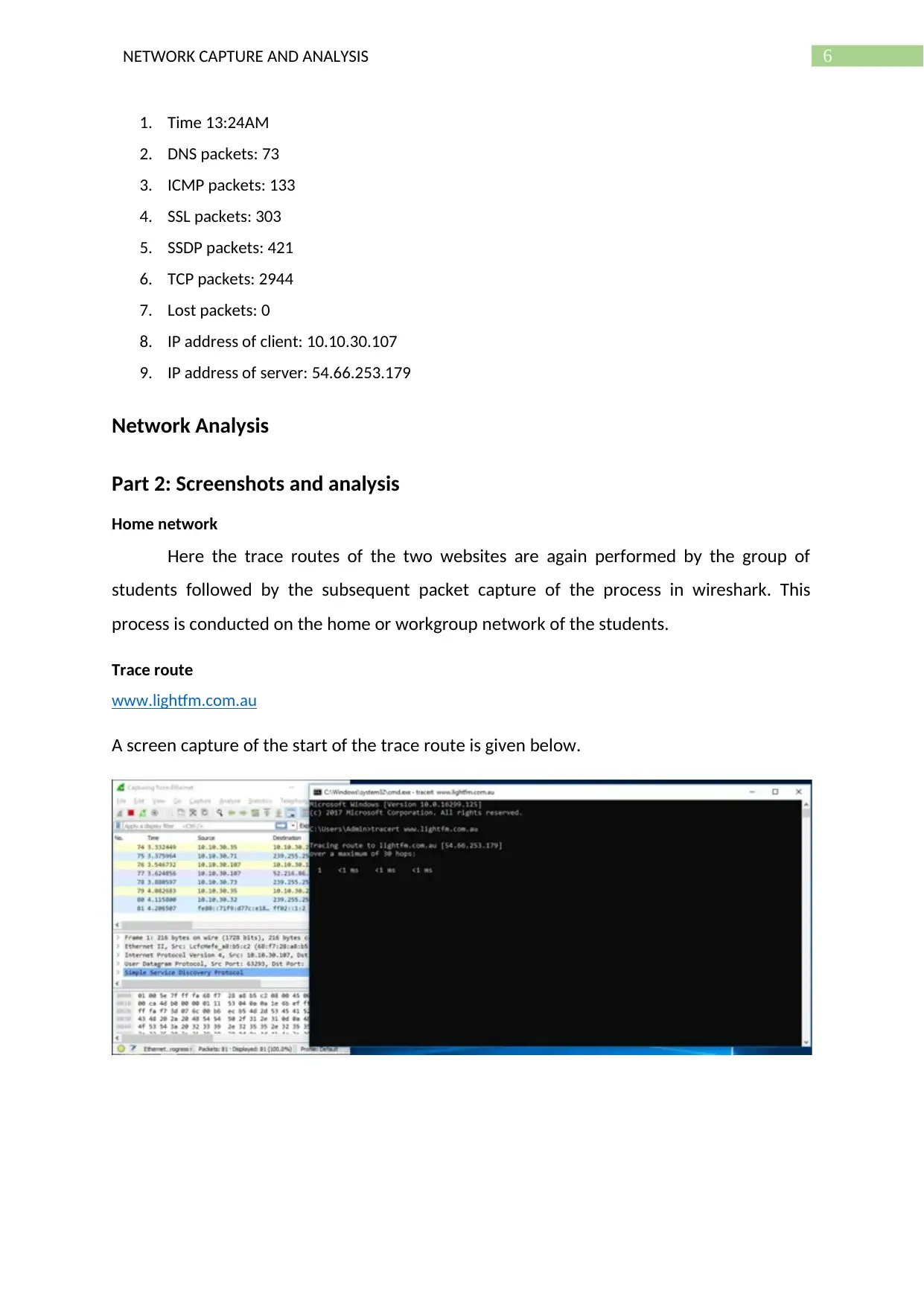
A screen capture of the start of the trace route is given below.
1. Time 13:24AM
2. DNS packets: 73
3. ICMP packets: 133
4. SSL packets: 303
5. SSDP packets: 421
6. TCP packets: 2944
7. Lost packets: 0
8. IP address of client: 10.10.30.107
9. IP address of server: 54.66.253.179
Network Analysis
Part 2: Screenshots and analysis
Home network
Here the trace routes of the two websites are again performed by the group of
students followed by the subsequent packet capture of the process in wireshark. This
process is conducted on the home or workgroup network of the students.
Trace route
www.lightfm.com.au
A screen capture of the start of the trace route is given below.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
7NETWORK CAPTURE AND ANALYSIS
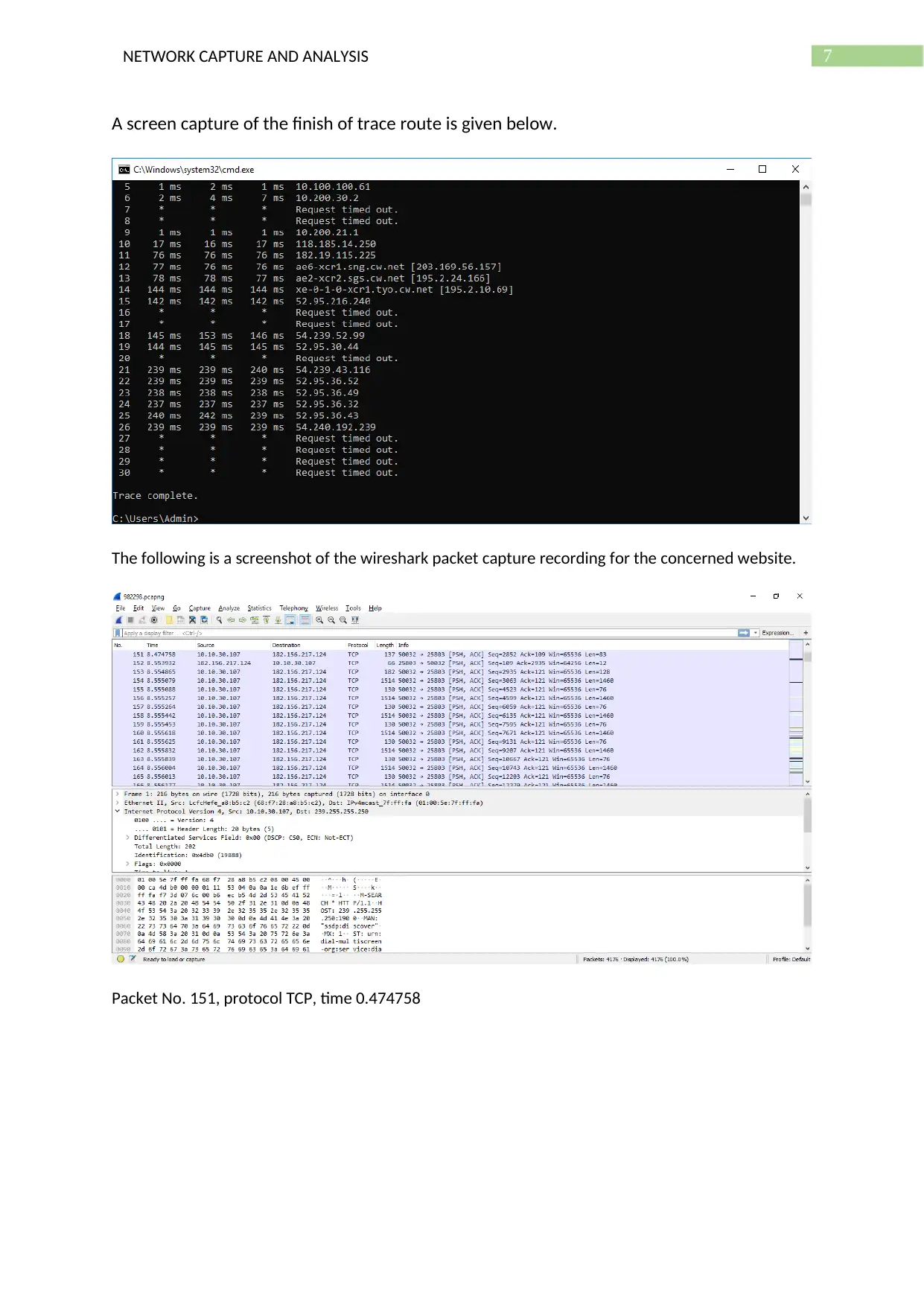
A screen capture of the finish of trace route is given below.
The following is a screenshot of the wireshark packet capture recording for the concerned website.
Packet No. 151, protocol TCP, time 0.474758
A screen capture of the finish of trace route is given below.
The following is a screenshot of the wireshark packet capture recording for the concerned website.
Packet No. 151, protocol TCP, time 0.474758
8NETWORK CAPTURE AND ANALYSIS
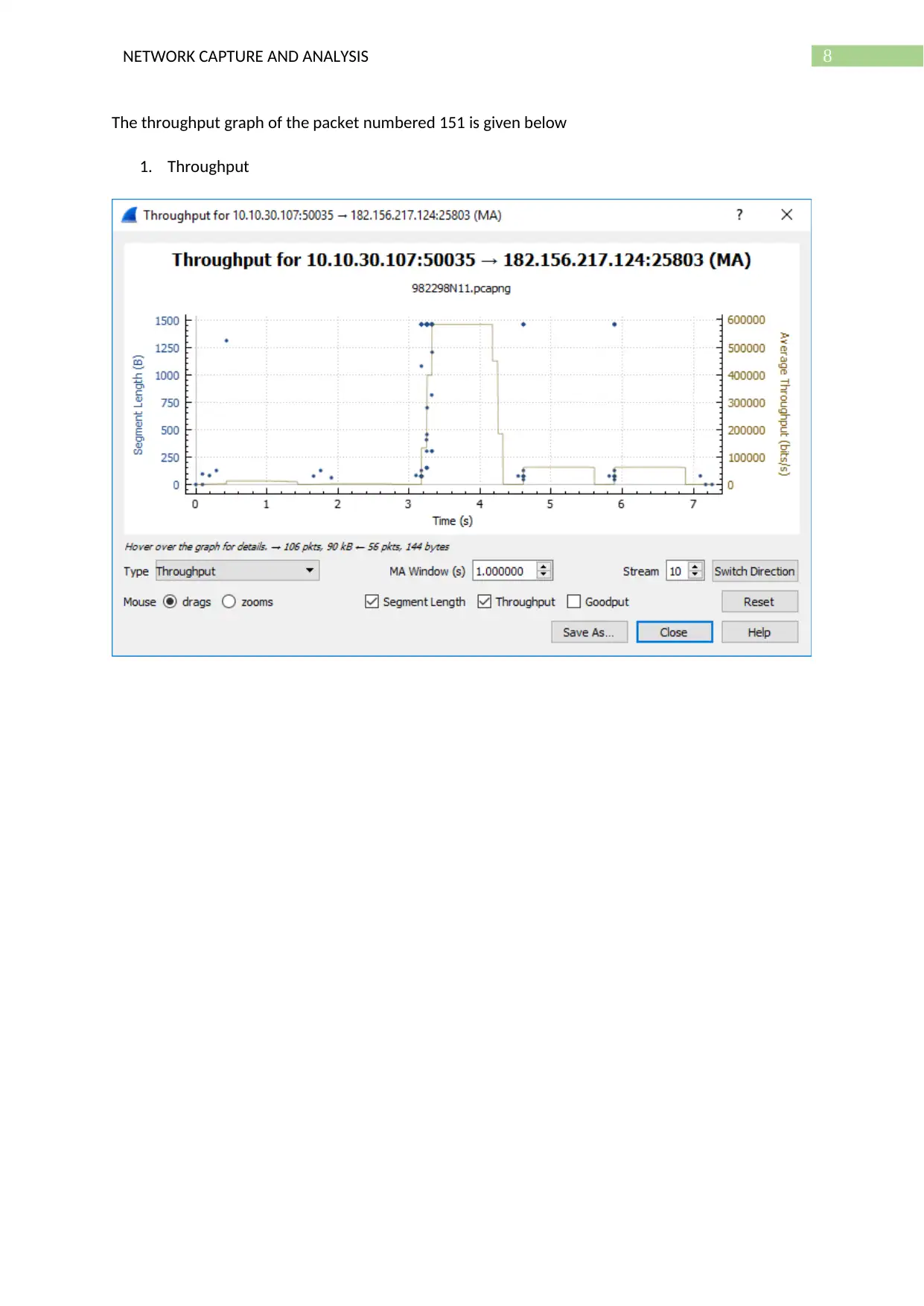
The throughput graph of the packet numbered 151 is given below
1. Throughput
The throughput graph of the packet numbered 151 is given below
1. Throughput
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
9NETWORK CAPTURE AND ANALYSIS
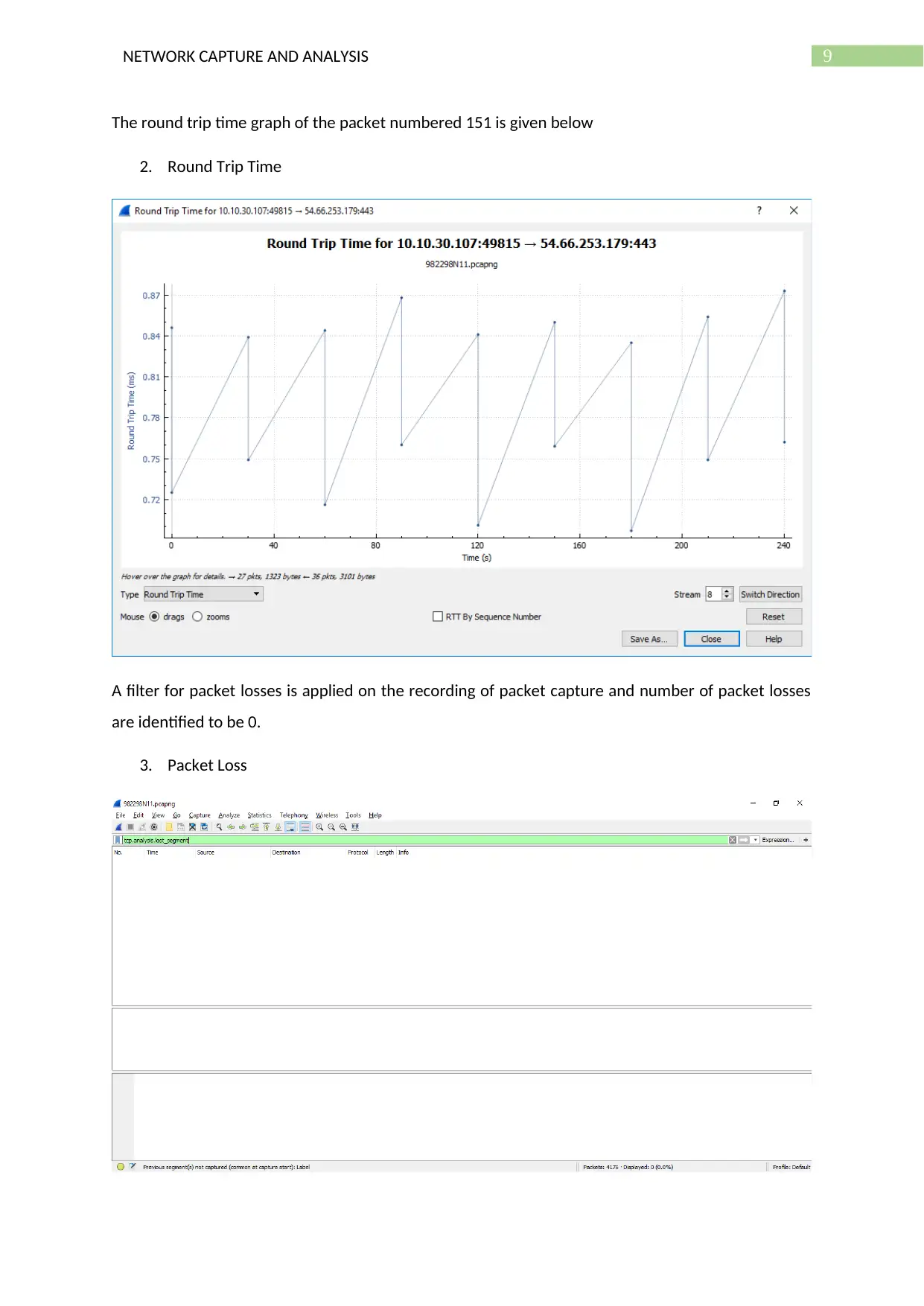
The round trip time graph of the packet numbered 151 is given below
2. Round Trip Time
A filter for packet losses is applied on the recording of packet capture and number of packet losses
are identified to be 0.
3. Packet Loss
The round trip time graph of the packet numbered 151 is given below
2. Round Trip Time
A filter for packet losses is applied on the recording of packet capture and number of packet losses
are identified to be 0.
3. Packet Loss
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
10NETWORK CAPTURE AND ANALYSIS
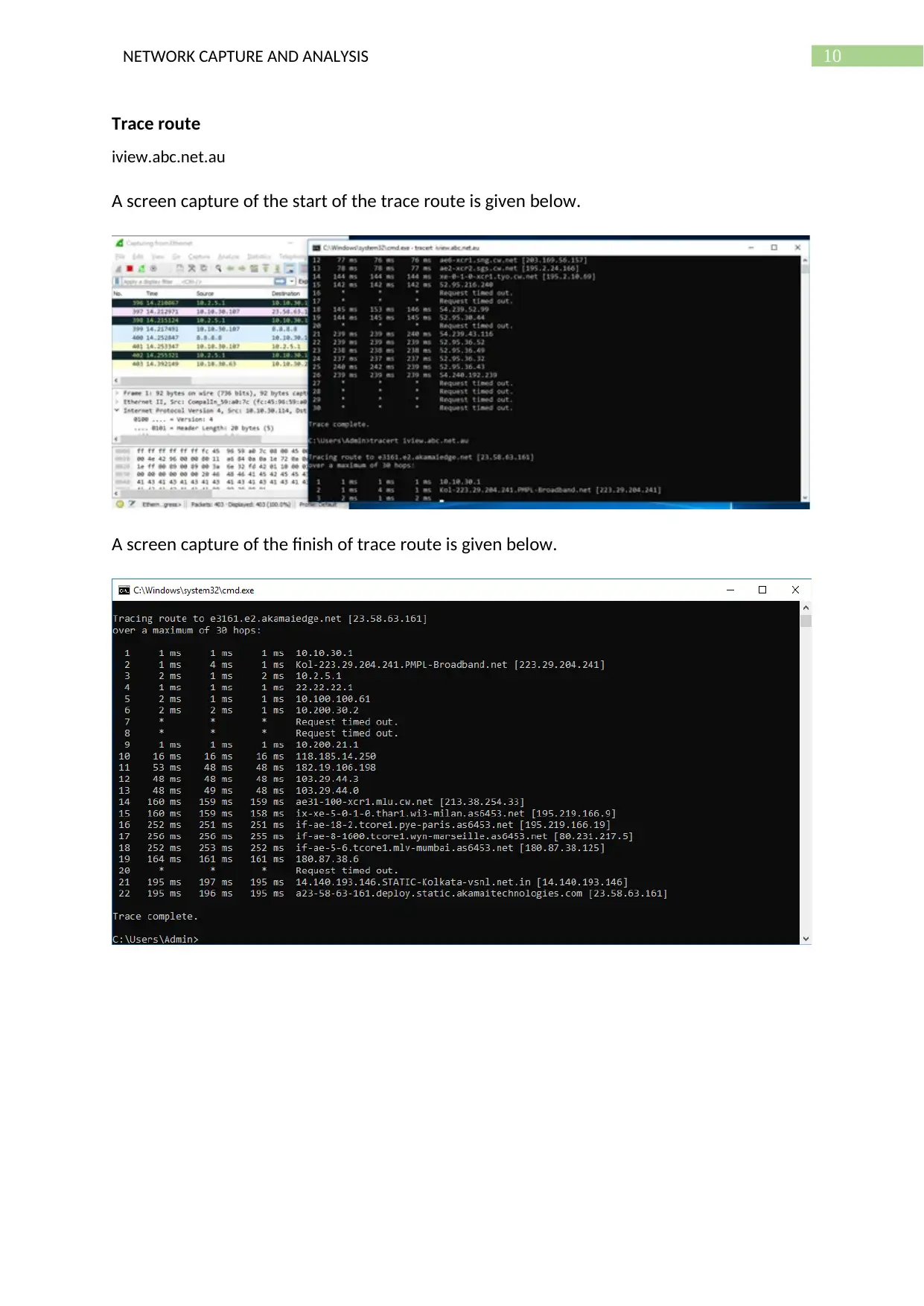
Trace route
iview.abc.net.au
A screen capture of the start of the trace route is given below.
A screen capture of the finish of trace route is given below.
Trace route
iview.abc.net.au
A screen capture of the start of the trace route is given below.
A screen capture of the finish of trace route is given below.
11NETWORK CAPTURE AND ANALYSIS
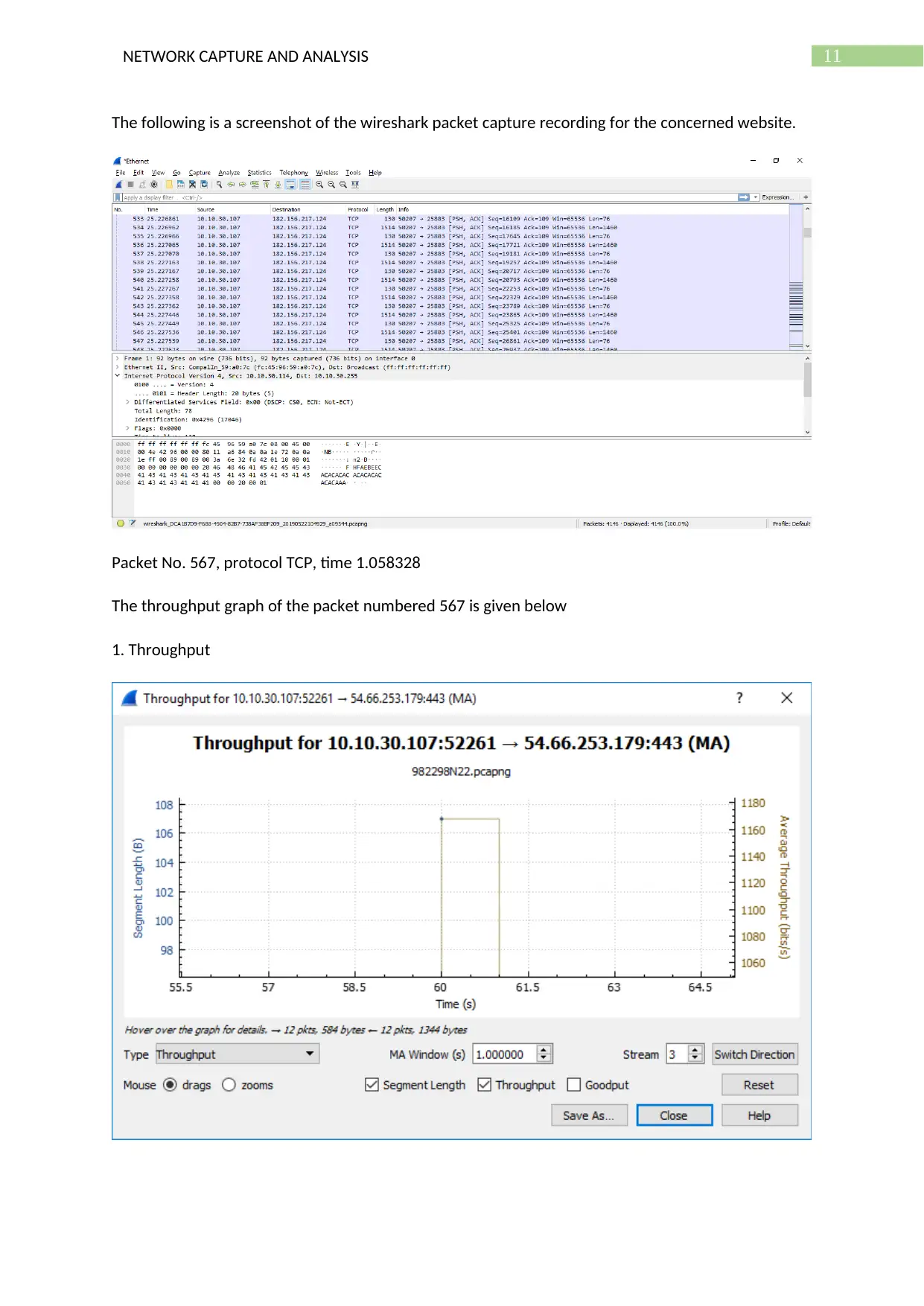
The following is a screenshot of the wireshark packet capture recording for the concerned website.
Packet No. 567, protocol TCP, time 1.058328
The throughput graph of the packet numbered 567 is given below
1. Throughput
The following is a screenshot of the wireshark packet capture recording for the concerned website.
Packet No. 567, protocol TCP, time 1.058328
The throughput graph of the packet numbered 567 is given below
1. Throughput
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
1 out of 25
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2025 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.





