Network Design and Analysis Report for Globex Corporation - ITC306
VerifiedAdded on 2022/11/14
|16
|3723
|77
Report
AI Summary
This report presents a comprehensive network design and analysis for Globex Corporation, encompassing both logical and physical network diagrams to illustrate network connectivity and security implementations across three office locations. It details the project goals, including ensuring connectivity for various devices and servers. The logical design outlines the network architecture, utilizing Amazon AWS cloud services for web hosting and VoIP, with VPNs securing site-to-site connections. It also describes the roles of servers in each site, including network administration, application server functions, and DMZ setup. The physical design section discusses network topology, LAN and WAN technologies. The report further explores addressing and naming structures, including subnetting plans, routing protocols, and security measures like DMZ and VPNs. It also covers VLANs and wireless network implementations. Finally, the report provides an analysis of network management practices, including monitoring tools and performance analysis.

Running head: NETWORK DESIGN AND ANALYSIS
1.
1.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
1
NETWORK DESIGN AND ANALYSIS
2. Change History
All changes to the Design Document must be recorded in the Change History.
Date Description of
Change
Reason for
Change
Author of
Change
Version No.
dd/mm/yyyy Initial draft N/A Version 1
3.
4.
NETWORK DESIGN AND ANALYSIS
2. Change History
All changes to the Design Document must be recorded in the Change History.
Date Description of
Change
Reason for
Change
Author of
Change
Version No.
dd/mm/yyyy Initial draft N/A Version 1
3.
4.

2
NETWORK DESIGN AND ANALYSIS
Table of Contents
1. Change History...................................................................................................................1
Executive Summary...................................................................................................................2
Project Goals..............................................................................................................................3
Logical Design...........................................................................................................................4
Logical Network Diagram......................................................................................................4
Addressing and Naming Structure.........................................................................................6
Routing and Switching Protocols...........................................................................................7
Security..................................................................................................................................8
Virtual LANs..........................................................................................................................8
Wireless Networks.................................................................................................................9
Network Management............................................................................................................9
Physical Design........................................................................................................................10
Network Topology...............................................................................................................10
LAN technologies................................................................................................................10
WAN technologies...............................................................................................................10
Physical Network Diagram..................................................................................................11
Minimal server and PC requirements...................................................................................12
Wireless technologies...........................................................................................................12
Conclusion................................................................................................................................13
References................................................................................................................................14
NETWORK DESIGN AND ANALYSIS
Table of Contents
1. Change History...................................................................................................................1
Executive Summary...................................................................................................................2
Project Goals..............................................................................................................................3
Logical Design...........................................................................................................................4
Logical Network Diagram......................................................................................................4
Addressing and Naming Structure.........................................................................................6
Routing and Switching Protocols...........................................................................................7
Security..................................................................................................................................8
Virtual LANs..........................................................................................................................8
Wireless Networks.................................................................................................................9
Network Management............................................................................................................9
Physical Design........................................................................................................................10
Network Topology...............................................................................................................10
LAN technologies................................................................................................................10
WAN technologies...............................................................................................................10
Physical Network Diagram..................................................................................................11
Minimal server and PC requirements...................................................................................12
Wireless technologies...........................................................................................................12
Conclusion................................................................................................................................13
References................................................................................................................................14
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

3
NETWORK DESIGN AND ANALYSIS
Executive Summary
The use of both logical and physical network diagrams helps immensely in understanding the
configuration and implementation of the network of an organization. The following report
therefore presents the logical design diagram and physical design diagram of Globex
Corporation in order to present the connectivity of the network and the implementation of
security measures. First the report presents a summary of the requirements for the network
being proposed where the report mentions the different locations of the three different offices
of Globex along with the kind of devices used by these offices, role of the devices, how the
networks are configured, how the VPN and security is set up and how the cloud services are
availed. Following this the report jumps into the network design section where it provides the
logical design diagram and the physical design diagram and describes the network according
to the diagrams explaining how the network meets the requirements. After this the report
talks about other candidate technologies that could have been applied on the network instead
of the present ones where the report specifically discusses three kinds of technologies,
namely – cloud solutions, VPN and virtual machines. For VPN, a unique alternative is
identified in Microsoft DirectAccess and for virtual machines two alternatives identified are
vmware and virtual box. Thereafter the report ends with observations in the concluding notes.
Project Goals
The goals of implementing and configuring the network at Wagga Wagga site by Globex is
as follows:
To ensure network connectivity to individual devices like workstations and IP phones
To ensure network connectivity for the physical servers responsible for networking and
administrative needs as also specific uses
To ensure network connectivity for the virtually set up servers
NETWORK DESIGN AND ANALYSIS
Executive Summary
The use of both logical and physical network diagrams helps immensely in understanding the
configuration and implementation of the network of an organization. The following report
therefore presents the logical design diagram and physical design diagram of Globex
Corporation in order to present the connectivity of the network and the implementation of
security measures. First the report presents a summary of the requirements for the network
being proposed where the report mentions the different locations of the three different offices
of Globex along with the kind of devices used by these offices, role of the devices, how the
networks are configured, how the VPN and security is set up and how the cloud services are
availed. Following this the report jumps into the network design section where it provides the
logical design diagram and the physical design diagram and describes the network according
to the diagrams explaining how the network meets the requirements. After this the report
talks about other candidate technologies that could have been applied on the network instead
of the present ones where the report specifically discusses three kinds of technologies,
namely – cloud solutions, VPN and virtual machines. For VPN, a unique alternative is
identified in Microsoft DirectAccess and for virtual machines two alternatives identified are
vmware and virtual box. Thereafter the report ends with observations in the concluding notes.
Project Goals
The goals of implementing and configuring the network at Wagga Wagga site by Globex is
as follows:
To ensure network connectivity to individual devices like workstations and IP phones
To ensure network connectivity for the physical servers responsible for networking and
administrative needs as also specific uses
To ensure network connectivity for the virtually set up servers
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

4
NETWORK DESIGN AND ANALYSIS
To ensure network connectivity for the devices that require wireless connectivity
Logical Design
Logical Network Diagram
Fi
gure 1: Logical Network Diagram
The above figure presents the logical network diagram to describe the proposed
network design (Park et al., 2017). Each of the three office sites placed at different locations
are connected to the amazon AWS cloud solution. Here the various hardware resources of
AWS are availed by the sites to perform activities like web hosting, and facilitate VoIP
connectivity (Amazon, 2015). These are made available through the IaaS or Infrastructure as
a Service type of services that are offered by Amazon AWS (Wittig & Wittig, 2015). The
connections that each site have with the AWS cloud solution pass through firewalls which
have VPN or Virtual Private Network tunnels set up (Yang et al., 2018). Thus, this results in
every connection between either two of the three company sites to be secured through Site to
Site VPNs. The web server is used to make web hosting of the common portal. This web
NETWORK DESIGN AND ANALYSIS
To ensure network connectivity for the devices that require wireless connectivity
Logical Design
Logical Network Diagram
Fi
gure 1: Logical Network Diagram
The above figure presents the logical network diagram to describe the proposed
network design (Park et al., 2017). Each of the three office sites placed at different locations
are connected to the amazon AWS cloud solution. Here the various hardware resources of
AWS are availed by the sites to perform activities like web hosting, and facilitate VoIP
connectivity (Amazon, 2015). These are made available through the IaaS or Infrastructure as
a Service type of services that are offered by Amazon AWS (Wittig & Wittig, 2015). The
connections that each site have with the AWS cloud solution pass through firewalls which
have VPN or Virtual Private Network tunnels set up (Yang et al., 2018). Thus, this results in
every connection between either two of the three company sites to be secured through Site to
Site VPNs. The web server is used to make web hosting of the common portal. This web

5
NETWORK DESIGN AND ANALYSIS
portal is also secured through VPNs from the browsers. These are SSL VPNs and does not
require additional equipment like firewalls, routers and extra software to set it up. The
windows servers of the different sites perform network administration tasks like regulating
user groups using active directory, configuring DNS changes, assigning auto configured IP
addresses to the different devices of the network through the DHCP protocol, set up firewall
rules and policies and maintain backups to say the least. The sites at Griffith also maintains
Hyper-V Failover measures through these servers (Darabont, Kiss & Domokos, 2015). Thus
the domain specific administrative tasks as well as remote access to other sites can be
conducted with the help of these servers. The roles of the application server vary for each
site. The site at Albury uses the application server for setting up the DMZ network after
another firewall. This helps the devices of the DMZ network partially accessible to the
network over the web portal while the firewall doubly screens the rest of the network and
thus intrusion from attackers are prevented. Only those devices that require access from the
outside the internal network of the company are kept in the DMZ network. The application
server of the site at Griffith is used for creating and maintaining two Hyper-V sessions where
the second session serves as the failover cluster lest the first session experiences downtime. A
separate server in the site is dedicated for maintaining the configurations and policies and
data about is Hyper-V Failover cluster so as to minimize data loss from the virtualization
activities of Globex Corporation. The application server of the site at Wagga Wagga is
responsible for setting up a network segment for enabling transfer of Syslog messages and
setting up of the SNMP trap. These Syslog messages are key monitoring mechanisms which
proactively collects information about the chronic issues that are affecting the network or not
(Villari et al., 2016). These logs are capable of identifying more degradation warnings of the
network and other exceptions than the monitoring metrics available through SNMP traps. The
NETWORK DESIGN AND ANALYSIS
portal is also secured through VPNs from the browsers. These are SSL VPNs and does not
require additional equipment like firewalls, routers and extra software to set it up. The
windows servers of the different sites perform network administration tasks like regulating
user groups using active directory, configuring DNS changes, assigning auto configured IP
addresses to the different devices of the network through the DHCP protocol, set up firewall
rules and policies and maintain backups to say the least. The sites at Griffith also maintains
Hyper-V Failover measures through these servers (Darabont, Kiss & Domokos, 2015). Thus
the domain specific administrative tasks as well as remote access to other sites can be
conducted with the help of these servers. The roles of the application server vary for each
site. The site at Albury uses the application server for setting up the DMZ network after
another firewall. This helps the devices of the DMZ network partially accessible to the
network over the web portal while the firewall doubly screens the rest of the network and
thus intrusion from attackers are prevented. Only those devices that require access from the
outside the internal network of the company are kept in the DMZ network. The application
server of the site at Griffith is used for creating and maintaining two Hyper-V sessions where
the second session serves as the failover cluster lest the first session experiences downtime. A
separate server in the site is dedicated for maintaining the configurations and policies and
data about is Hyper-V Failover cluster so as to minimize data loss from the virtualization
activities of Globex Corporation. The application server of the site at Wagga Wagga is
responsible for setting up a network segment for enabling transfer of Syslog messages and
setting up of the SNMP trap. These Syslog messages are key monitoring mechanisms which
proactively collects information about the chronic issues that are affecting the network or not
(Villari et al., 2016). These logs are capable of identifying more degradation warnings of the
network and other exceptions than the monitoring metrics available through SNMP traps. The
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
6
NETWORK DESIGN AND ANALYSIS
workstations of the offices at the site of Albury and Wagga Wagga are dedicated for
operating in virtualized environments with the help of Hyper-V.
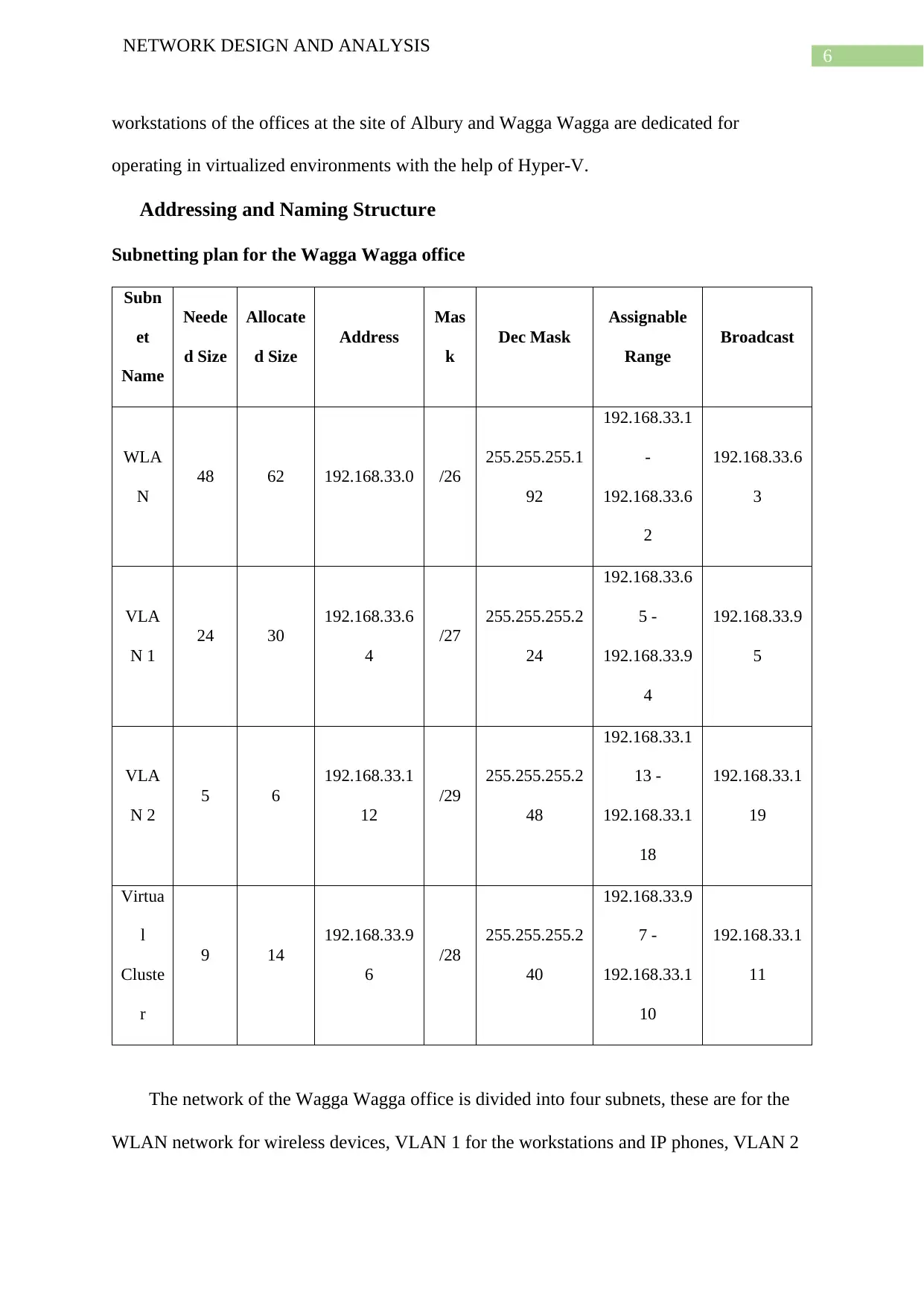
Addressing and Naming Structure
Subnetting plan for the Wagga Wagga office
Subn
et
Name
Neede
d Size
Allocate
d Size
Address
Mas
k
Dec Mask
Assignable
Range
Broadcast
WLA
N
48 62 192.168.33.0 /26
255.255.255.1
92
192.168.33.1
-
192.168.33.6
2
192.168.33.6
3
VLA
N 1
24 30
192.168.33.6
4
/27
255.255.255.2
24
192.168.33.6
5 -
192.168.33.9
4
192.168.33.9
5
VLA
N 2
5 6
192.168.33.1
12
/29
255.255.255.2
48
192.168.33.1
13 -
192.168.33.1
18
192.168.33.1
19
Virtua
l
Cluste
r
9 14
192.168.33.9
6
/28
255.255.255.2
40
192.168.33.9
7 -
192.168.33.1
10
192.168.33.1
11
The network of the Wagga Wagga office is divided into four subnets, these are for the
WLAN network for wireless devices, VLAN 1 for the workstations and IP phones, VLAN 2
NETWORK DESIGN AND ANALYSIS
workstations of the offices at the site of Albury and Wagga Wagga are dedicated for
operating in virtualized environments with the help of Hyper-V.
Addressing and Naming Structure
Subnetting plan for the Wagga Wagga office
Subn
et
Name
Neede
d Size
Allocate
d Size
Address
Mas
k
Dec Mask
Assignable
Range
Broadcast
WLA
N
48 62 192.168.33.0 /26
255.255.255.1
92
192.168.33.1
-
192.168.33.6
2
192.168.33.6
3
VLA
N 1
24 30
192.168.33.6
4
/27
255.255.255.2
24
192.168.33.6
5 -
192.168.33.9
4
192.168.33.9
5
VLA
N 2
5 6
192.168.33.1
12
/29
255.255.255.2
48
192.168.33.1
13 -
192.168.33.1
18
192.168.33.1
19
Virtua
l
Cluste
r
9 14
192.168.33.9
6
/28
255.255.255.2
40
192.168.33.9
7 -
192.168.33.1
10
192.168.33.1
11
The network of the Wagga Wagga office is divided into four subnets, these are for the
WLAN network for wireless devices, VLAN 1 for the workstations and IP phones, VLAN 2
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

7
NETWORK DESIGN AND ANALYSIS
for the physical servers, and the Virtual Cluster for the virtualized servers. VLAN 2 includes
the windows server, application server as also the syslog ng servers. The virtual cluster
includes virtualized servers running in virtual machines for various networking and
administrative needs like DHCP, DNS, Firewall, Active Directory, Backup, File server as
also the servers that act as SNMP agents.
Major networks and IP Addressing
The major networks used by the sites are 192.168.11.0 with the router IP address
192.168.11.1 for Albury, 192.168.22.0 with the router IP address 192.168.22.1 for Griffith
and 192.168.33.0 with the router IP address 192.168.33.1 for Wagga Wagga respectively.
The DMZ network devices are using a separate network 172.16.1.0. The IP addressing
scheme used here is classless Inter Domain Routing or CIDR as it has found to be more
efficient than the classful IP addressing scheme.
DHCP
The DHCP protocol is used for assigning IP addresses to all systems of the Wagga Wagga
office by mainly associating the IP address assigning ranges with the different VLANs
present in the network. However it should be noted that the most benefit obtained from this
auto allocation of IP addresses is the WLAN network that connects devices through Wi-Fi.
Naming Convention
The naming conventions used for the domains, severs, routers and hosts are according to the
networking model used and the kinds of activities performed on the network at the particular
site.
Routing and Switching Protocols
The routing protocol that have been used among the three routers of the three different sites is
static routing. In each of the three routers the static routes for the networks of another router
are configured through the appropriate interface. For example the DMZ network in Albury
NETWORK DESIGN AND ANALYSIS
for the physical servers, and the Virtual Cluster for the virtualized servers. VLAN 2 includes
the windows server, application server as also the syslog ng servers. The virtual cluster
includes virtualized servers running in virtual machines for various networking and
administrative needs like DHCP, DNS, Firewall, Active Directory, Backup, File server as
also the servers that act as SNMP agents.
Major networks and IP Addressing
The major networks used by the sites are 192.168.11.0 with the router IP address
192.168.11.1 for Albury, 192.168.22.0 with the router IP address 192.168.22.1 for Griffith
and 192.168.33.0 with the router IP address 192.168.33.1 for Wagga Wagga respectively.
The DMZ network devices are using a separate network 172.16.1.0. The IP addressing
scheme used here is classless Inter Domain Routing or CIDR as it has found to be more
efficient than the classful IP addressing scheme.
DHCP
The DHCP protocol is used for assigning IP addresses to all systems of the Wagga Wagga
office by mainly associating the IP address assigning ranges with the different VLANs
present in the network. However it should be noted that the most benefit obtained from this
auto allocation of IP addresses is the WLAN network that connects devices through Wi-Fi.
Naming Convention
The naming conventions used for the domains, severs, routers and hosts are according to the
networking model used and the kinds of activities performed on the network at the particular
site.
Routing and Switching Protocols
The routing protocol that have been used among the three routers of the three different sites is
static routing. In each of the three routers the static routes for the networks of another router
are configured through the appropriate interface. For example the DMZ network in Albury

8
NETWORK DESIGN AND ANALYSIS
can be accessed from Wagga Wagga by means of routing the network 172.16.1.0 through the
router IP 172.16.1.254 on the router of Wagga Wagga office. From the core router of Wagga
Wagga the rest of the network in the office is arranged through switches where VLANs are
configured for the respective network segments. Four different VLANs are created for the
four main sections of the Wagga Wagga network. Connectivity between the segments is
ensured through inter VLAN routing. The IP addresses the devices of the respective VLANs
are auto assigned using the DHCP protocol.
Security
First the network of Globex gets secured through the DMZ network hosted by the site at
Albury to prevent intrusions. The virtualized servers of Wagga Wagga is used to access this
DMZ network as well as configure all the firewalls present in the networks. In today’s world
of computing the leading types of VPN are SSL VPN and IPsec VPN (Diakakis, Almaliotis
& Mitakos, 2016). Almost every VPN solution available today is a derivative of either of the
two above mentioned VPN frameworks. The only distinctly different alternative to SSL and
IPsec VPNs is Microsoft DirectAccess (Diakakis, Almaliotis & Mitakos, 2016). Microsoft
DirectAccess is uniquely different in the sense that instead of offering a better VPN
framework the solution attempts to solve the issues that VPNs try to address in alternate ways
(Krause, 2015). However this solution is very new and exhibits bugs and glitches from time
to time. Therefore the combined use of IPsec and SSL VPNs are still seen as the most
comprehensive VPN solution an organization can establish in their network.
Virtual LANs
Virtual LANs or VLANs have been used in the network of Wagga Wagga. Since this office
provides connections in four different use cases that is in connecting the client devices,
physical servers, virtualized servers and the wireless devices, four different VLANs are
created.
NETWORK DESIGN AND ANALYSIS
can be accessed from Wagga Wagga by means of routing the network 172.16.1.0 through the
router IP 172.16.1.254 on the router of Wagga Wagga office. From the core router of Wagga
Wagga the rest of the network in the office is arranged through switches where VLANs are
configured for the respective network segments. Four different VLANs are created for the
four main sections of the Wagga Wagga network. Connectivity between the segments is
ensured through inter VLAN routing. The IP addresses the devices of the respective VLANs
are auto assigned using the DHCP protocol.
Security
First the network of Globex gets secured through the DMZ network hosted by the site at
Albury to prevent intrusions. The virtualized servers of Wagga Wagga is used to access this
DMZ network as well as configure all the firewalls present in the networks. In today’s world
of computing the leading types of VPN are SSL VPN and IPsec VPN (Diakakis, Almaliotis
& Mitakos, 2016). Almost every VPN solution available today is a derivative of either of the
two above mentioned VPN frameworks. The only distinctly different alternative to SSL and
IPsec VPNs is Microsoft DirectAccess (Diakakis, Almaliotis & Mitakos, 2016). Microsoft
DirectAccess is uniquely different in the sense that instead of offering a better VPN
framework the solution attempts to solve the issues that VPNs try to address in alternate ways
(Krause, 2015). However this solution is very new and exhibits bugs and glitches from time
to time. Therefore the combined use of IPsec and SSL VPNs are still seen as the most
comprehensive VPN solution an organization can establish in their network.
Virtual LANs
Virtual LANs or VLANs have been used in the network of Wagga Wagga. Since this office
provides connections in four different use cases that is in connecting the client devices,
physical servers, virtualized servers and the wireless devices, four different VLANs are
created.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

9
NETWORK DESIGN AND ANALYSIS
Wagga Wagga VLANs incclude
A number of four VLANs
Which user groups belong to which VLAN
Physical servers VLAN belong to VLAN 2 and virtually hosted servers belong to the
Virtual Cluster
Inter VLAN Routing is ensured by the distribution switch by connecting with router
and lower layer switches with interfaces in trunk mode
Configuration for Inter-VLAN routing is performed on the core router of the Wagga
Wagga office. All four VLANs are defined in the distribution layer switch so that
VLAN trunking can be done.
You should discuss the benefits of your chosen VLAN allocation, how the resources
(servers) are allocated and/or distributed between the VLANs and if communication between
the VLANs is necessary.
Wireless Networks
Wagga Wagga office network includes wireless network support for appropriate devices like
laptops and smartphones.
Wireless access points for the network are located across the outdoor premises by
utilizing the POE or Power over Ethernet functionality.
Only one large subnet is dedicated for the WLAN network
The WPA2 encryption techniques are used to secure the connectivity through pre
assigned WPSK keys.
NETWORK DESIGN AND ANALYSIS
Wagga Wagga VLANs incclude
A number of four VLANs
Which user groups belong to which VLAN
Physical servers VLAN belong to VLAN 2 and virtually hosted servers belong to the
Virtual Cluster
Inter VLAN Routing is ensured by the distribution switch by connecting with router
and lower layer switches with interfaces in trunk mode
Configuration for Inter-VLAN routing is performed on the core router of the Wagga
Wagga office. All four VLANs are defined in the distribution layer switch so that
VLAN trunking can be done.
You should discuss the benefits of your chosen VLAN allocation, how the resources
(servers) are allocated and/or distributed between the VLANs and if communication between
the VLANs is necessary.
Wireless Networks
Wagga Wagga office network includes wireless network support for appropriate devices like
laptops and smartphones.
Wireless access points for the network are located across the outdoor premises by
utilizing the POE or Power over Ethernet functionality.
Only one large subnet is dedicated for the WLAN network
The WPA2 encryption techniques are used to secure the connectivity through pre
assigned WPSK keys.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

10
NETWORK DESIGN AND ANALYSIS
Network Management
The network of Wagga Wagga office is continuously monitored and analysed by network
administrators.
Since the company deals with sensitive information, it needs to ensure that the
network is not compromised. Hence it aims to monitor the network from hacking
attempts
The monitoring applications used by Globex in monitoring their network at Wagga
Wagga are Wireshark and Microsoft Message Analyser (MMA). Wireshark is an
open source free to use software while MMA is a proprietory tool provided by
Microsoft
Network Performance is thoroughly analysed and the login session packets are
scrutinized to eliminate the threat of spoofing.
Physical Design
Network Topology
The physical networking topology used in the network of Wagga Wagga office for
connecting the various devices and switches is star topology. This minimizes risk of entire
network getting affected from failures.
LAN technologies
The LAN network connections are ensured Cat 6 Ethernet LAN cables through the RJ45
ports. These cables cover most of the network except WLAN section and the site to site links
through ISPs.
WAN technologies
The site to site VPN based connections take place through the ISPs. The tunnelling defined in
the IPsec VPN configuration ensures the networks can access select networks like that of
NETWORK DESIGN AND ANALYSIS
Network Management
The network of Wagga Wagga office is continuously monitored and analysed by network
administrators.
Since the company deals with sensitive information, it needs to ensure that the
network is not compromised. Hence it aims to monitor the network from hacking
attempts
The monitoring applications used by Globex in monitoring their network at Wagga
Wagga are Wireshark and Microsoft Message Analyser (MMA). Wireshark is an
open source free to use software while MMA is a proprietory tool provided by
Microsoft
Network Performance is thoroughly analysed and the login session packets are
scrutinized to eliminate the threat of spoofing.
Physical Design
Network Topology
The physical networking topology used in the network of Wagga Wagga office for
connecting the various devices and switches is star topology. This minimizes risk of entire
network getting affected from failures.
LAN technologies
The LAN network connections are ensured Cat 6 Ethernet LAN cables through the RJ45
ports. These cables cover most of the network except WLAN section and the site to site links
through ISPs.
WAN technologies
The site to site VPN based connections take place through the ISPs. The tunnelling defined in
the IPsec VPN configuration ensures the networks can access select networks like that of

11
NETWORK DESIGN AND ANALYSIS
other sites and the networks and resources of the AWS cloud solution where the web and
VOIP servers are hosted. This way the Globex intranet among the three main sites is formed
in a WAN configuration.
Physical Network Diagram
Figure 2: Physical Network Diagram
The above figure is the physical network diagram that explains in detail, which segment
of the network is located at what site (Hehenberger et al., 2016). It also provides the major IP
network used by each of the three as well as mentions the VLANs that are used by the
different types of devices (Nguyen & Kim, 2016). Though the VLANs are different, the
required access to the devices of other VLANs from a device of another VLAN is ensured by
means of inter VLAN routing (Ashraf & Yousaf, 2016). Additional security measures and
access restrictions within the network segments are configured with the help of ACL or
access control list commands.
The type of cloud service being availed from Amazon AWS is IaaS which lets the
organization share hardware resources of the datacentres and servers of AWS (García, del
NETWORK DESIGN AND ANALYSIS
other sites and the networks and resources of the AWS cloud solution where the web and
VOIP servers are hosted. This way the Globex intranet among the three main sites is formed
in a WAN configuration.
Physical Network Diagram
Figure 2: Physical Network Diagram
The above figure is the physical network diagram that explains in detail, which segment
of the network is located at what site (Hehenberger et al., 2016). It also provides the major IP
network used by each of the three as well as mentions the VLANs that are used by the
different types of devices (Nguyen & Kim, 2016). Though the VLANs are different, the
required access to the devices of other VLANs from a device of another VLAN is ensured by
means of inter VLAN routing (Ashraf & Yousaf, 2016). Additional security measures and
access restrictions within the network segments are configured with the help of ACL or
access control list commands.
The type of cloud service being availed from Amazon AWS is IaaS which lets the
organization share hardware resources of the datacentres and servers of AWS (García, del
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
1 out of 16
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.




