University Network Design and Implementation Report: QAC020N253
VerifiedAdded on 2022/08/13
|17
|4223
|16
Report
AI Summary
This report focuses on the network design and implementation for Speedfix.co.uk, a small organization with four departments: HR/Finance, Administration, Engineering, and Sales. The report outlines the requirements for a new network architecture, including five servers (DNS, email, registration, file, and web). It explores network analysis, emphasizing the use of a star topology with a main router and departmental sub-routers. The analysis includes discussions of the OSI model, access control, DHCP, and VLAN technology. The report evaluates essential network components such as switches, routers, and connecting cables. It also covers the implementation of access control to restrict inter-departmental communication and the use of DHCP for IP address assignment. The report concludes with a discussion on testing and documentation, providing a comprehensive overview of the network design process.

Running head: - NETWORK DESIGN AND IMPLEMENTATION
NETWORK DESIGN AND IMPLEMENTATION
Name of the Student
Name of the University
Author Note
NETWORK DESIGN AND IMPLEMENTATION
Name of the Student
Name of the University
Author Note
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

1NETWORK DESIGN AND IMPLEMENTATION
Table of Contents
1. Introduction............................................................................................................................2
2. Understanding of the Network...............................................................................................2
3. Network Analysis...................................................................................................................4
3.1 OSI Model........................................................................................................................5
4. Component Evaluation of the Network Architecture.............................................................5
4.1 Switch...............................................................................................................................6
4.2 Router...............................................................................................................................7
4.3 Connecting Cables...........................................................................................................8
4.4 VLAN...............................................................................................................................9
4.5 Trunking.........................................................................................................................10
4.6 Access control................................................................................................................10
4.7 DHCP.............................................................................................................................11
5. Network Design...................................................................................................................11
6. Testing and Documentation.................................................................................................11
7. References............................................................................................................................13
Table of Contents
1. Introduction............................................................................................................................2
2. Understanding of the Network...............................................................................................2
3. Network Analysis...................................................................................................................4
3.1 OSI Model........................................................................................................................5
4. Component Evaluation of the Network Architecture.............................................................5
4.1 Switch...............................................................................................................................6
4.2 Router...............................................................................................................................7
4.3 Connecting Cables...........................................................................................................8
4.4 VLAN...............................................................................................................................9
4.5 Trunking.........................................................................................................................10
4.6 Access control................................................................................................................10
4.7 DHCP.............................................................................................................................11
5. Network Design...................................................................................................................11
6. Testing and Documentation.................................................................................................11
7. References............................................................................................................................13

2NETWORK DESIGN AND IMPLEMENTATION
1. Introduction
In the current aspect, Speedfix.co.uk is a small organization, which is aiming to
design and implement a new network so that the architecture of the whole network system of
the organization can be changed. The Speedfix.co.uk currently has four important sections
within their organization. These four sections are the HR or the Finance department,
Administration department, Engineering department and the sales department. As per the
requirement of the organization total, five types of servers need to be included in the new
network architecture of the organization. These five servers that are required for the
organization are the DNS server, email server, registration server, common file server and the
webserver (Kuleshov et al. 2016). With this, there are several other requirements for this
network, which needs to be fulfilled. All of the four departments of the organization should
have a specific number of workstations, and there is one printer for each of the department.
For wireless connectivity, all of the four departments will have a specific router. This router
will be acting as a sub-router for establishing a connection with the main router of the
organization (Kloth 2018). While the new network design will be developed for the
organization security, scalability and the availability of the whole network system will be also
considered. In an overall perspective, the current network architecture will be aiming to fulfil
the current objectives of the business.
2. Understanding of the Network
The network, which needs to be implemented for the organization is totally dependent
on the business requirement of the organization. It means the new network architecture needs
to fulfil all the requirement of all the four departments of the organization. In this case, an
effective network architecture needs to be implemented (Mihai et al. 2018), which will
effectively transfer the data from point a to point b. Proper analysis is required to develop this
1. Introduction
In the current aspect, Speedfix.co.uk is a small organization, which is aiming to
design and implement a new network so that the architecture of the whole network system of
the organization can be changed. The Speedfix.co.uk currently has four important sections
within their organization. These four sections are the HR or the Finance department,
Administration department, Engineering department and the sales department. As per the
requirement of the organization total, five types of servers need to be included in the new
network architecture of the organization. These five servers that are required for the
organization are the DNS server, email server, registration server, common file server and the
webserver (Kuleshov et al. 2016). With this, there are several other requirements for this
network, which needs to be fulfilled. All of the four departments of the organization should
have a specific number of workstations, and there is one printer for each of the department.
For wireless connectivity, all of the four departments will have a specific router. This router
will be acting as a sub-router for establishing a connection with the main router of the
organization (Kloth 2018). While the new network design will be developed for the
organization security, scalability and the availability of the whole network system will be also
considered. In an overall perspective, the current network architecture will be aiming to fulfil
the current objectives of the business.
2. Understanding of the Network
The network, which needs to be implemented for the organization is totally dependent
on the business requirement of the organization. It means the new network architecture needs
to fulfil all the requirement of all the four departments of the organization. In this case, an
effective network architecture needs to be implemented (Mihai et al. 2018), which will
effectively transfer the data from point a to point b. Proper analysis is required to develop this
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

3NETWORK DESIGN AND IMPLEMENTATION
network architecture as it will be helping to identify the necessary equipment that is
important for designing the network. The following stage is the implementation phase, where
the network architecture will be developed as per the identified criteria from the analysis
stage.
In this aspect, it has been identified that a total of five servers will be required to fulfil
the current requirement of the organization. The identified servers are the email server, DNS
server, web server, registration server and the file server. For creating a proper network
architecture, the server can be an important component (Corbellini and Parvis 2016). The
server is a specific type of device resides within a network and used for the network resource
management. As currently, the Speedfix.co.uk needs to provide four different types of
resources, implementing four different routers for each of the resource factors is important.
For this reason, individual servers will be established, and ultimately the entire network
architecture will develop a Wide Area Network connection or a Local Area Network
connection (López-Pérez et al. 2016). In this way, the implemented servers will be able to
fulfil the current business requirement of the Speedfix.co.uk where the servers of the
organization will be playing an important role. The servers will play an important role to
fulfil the main objective of the current organization.
In the current architecture, which will be developed, all the four departments have
their individual routers. All these four routers are connected to the main router. In this way,
the end-user devices in the network architecture, including the printers and the workstations
are provided with the internet connection. Due to the utilization of this kind of network
architecture, star topology will be used for designing of the network architecture (Gnad and
Hoffmann 2018). Here, the star topology will be appropriate for developing the network
architecture for Speedfix.co.uk. The star topology is considered as spoke-hub distribution
paradigm that is used among the computer networks. Within a star topology, all the hosts are
network architecture as it will be helping to identify the necessary equipment that is
important for designing the network. The following stage is the implementation phase, where
the network architecture will be developed as per the identified criteria from the analysis
stage.
In this aspect, it has been identified that a total of five servers will be required to fulfil
the current requirement of the organization. The identified servers are the email server, DNS
server, web server, registration server and the file server. For creating a proper network
architecture, the server can be an important component (Corbellini and Parvis 2016). The
server is a specific type of device resides within a network and used for the network resource
management. As currently, the Speedfix.co.uk needs to provide four different types of
resources, implementing four different routers for each of the resource factors is important.
For this reason, individual servers will be established, and ultimately the entire network
architecture will develop a Wide Area Network connection or a Local Area Network
connection (López-Pérez et al. 2016). In this way, the implemented servers will be able to
fulfil the current business requirement of the Speedfix.co.uk where the servers of the
organization will be playing an important role. The servers will play an important role to
fulfil the main objective of the current organization.
In the current architecture, which will be developed, all the four departments have
their individual routers. All these four routers are connected to the main router. In this way,
the end-user devices in the network architecture, including the printers and the workstations
are provided with the internet connection. Due to the utilization of this kind of network
architecture, star topology will be used for designing of the network architecture (Gnad and
Hoffmann 2018). Here, the star topology will be appropriate for developing the network
architecture for Speedfix.co.uk. The star topology is considered as spoke-hub distribution
paradigm that is used among the computer networks. Within a star topology, all the hosts are
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

4NETWORK DESIGN AND IMPLEMENTATION
connected to a central hub that has been followed in this network design (Moharana et al.
2020). In the star topology, the data is passed through the main hub before it can reach to the
actual destination.
3. Network Analysis
For the network, which will be implemented, Speedfix.co.uk needs to create a system
which will restrict the access of one department to another department through accessing the
workstations. In this way, any of the workstations will not be able to communicate with the
other workstations in some other department. In this case, the access control will be utilized
for preventing communication among the four departments of the organization (Lin et al.
2018). By using the access control, unnecessary access to the other departments can be
restricted, which is important to properly run the business. The access control can be also
configured so that one department can access the resources of the other department (Zhang,
Ma and Lu 2017), but in the ideal condition, the access control will be configured in such a
way that one department does not get the resource access of another department.
In this network architecture, all the workstations of each of the network will be
connected directly to the DHCP server so that they can function in a normal way. A DHCP is
a specific type of network server which is capable of automatic providing and assigning the
IP addresses (Younes 2016). The DHCP stands for Dynamic Host Configuration Protocol.
The DHCP server can also assign the default gateways and the network parameters for the
client devices. With the DHCP server, VLAN technology will be also used. The VLAN or the
virtual LAN can be any of the broadcast domain, which is isolated and partitioned within a
computer network at the data link layer (Seo, Kim and Min 2016). The main aim of using
VLAN technology is establishing a connection between the switch and the router.
connected to a central hub that has been followed in this network design (Moharana et al.
2020). In the star topology, the data is passed through the main hub before it can reach to the
actual destination.
3. Network Analysis
For the network, which will be implemented, Speedfix.co.uk needs to create a system
which will restrict the access of one department to another department through accessing the
workstations. In this way, any of the workstations will not be able to communicate with the
other workstations in some other department. In this case, the access control will be utilized
for preventing communication among the four departments of the organization (Lin et al.
2018). By using the access control, unnecessary access to the other departments can be
restricted, which is important to properly run the business. The access control can be also
configured so that one department can access the resources of the other department (Zhang,
Ma and Lu 2017), but in the ideal condition, the access control will be configured in such a
way that one department does not get the resource access of another department.
In this network architecture, all the workstations of each of the network will be
connected directly to the DHCP server so that they can function in a normal way. A DHCP is
a specific type of network server which is capable of automatic providing and assigning the
IP addresses (Younes 2016). The DHCP stands for Dynamic Host Configuration Protocol.
The DHCP server can also assign the default gateways and the network parameters for the
client devices. With the DHCP server, VLAN technology will be also used. The VLAN or the
virtual LAN can be any of the broadcast domain, which is isolated and partitioned within a
computer network at the data link layer (Seo, Kim and Min 2016). The main aim of using
VLAN technology is establishing a connection between the switch and the router.

5NETWORK DESIGN AND IMPLEMENTATION
Previously, it has been assessed that the inter-department communication has been
restricted in this network architecture by using the access control feature (Alansari, Paci and
Sassone 2017). Though there is a restriction to access the resources of another department, all
of the four departments can freely access the required four servers, which will provide the
important resources. For establishing this connection between the servers and the
departments, some specific switches will be utilized.
To create this network architecture, different types of network models can be utilized.
The important approach that can be utilized in this context is discussed in the following
section.
3.1 OSI Model
The OSI model or the Open System Interconnection model is a specific type of model
that standardises and characterise the communication protocols of a system (Zhao et al.
2018). The OSI model is one of the important aspects of networking. As it is mentioned that
the OSI model establishes the communication protocol, it can be used for setting the
connection among the workstations so that the whole network is able to function in a proper
way without any interruption in the communication process. Though the OSI model is one of
the best ways of establishing communication, it has certain limitations. In this aspect, the
system must be highly adaptable so that the OSI model can be used (Abdul and Umar 2017).
The OSI model can be very much useful to ensure that all the components of the system are
functioning properly, and they are communicating with each other in a proper function. The
OSI model consists of a total of seven layers. For this network architecture, all of these seven
layers will be utilized.
Previously, it has been assessed that the inter-department communication has been
restricted in this network architecture by using the access control feature (Alansari, Paci and
Sassone 2017). Though there is a restriction to access the resources of another department, all
of the four departments can freely access the required four servers, which will provide the
important resources. For establishing this connection between the servers and the
departments, some specific switches will be utilized.
To create this network architecture, different types of network models can be utilized.
The important approach that can be utilized in this context is discussed in the following
section.
3.1 OSI Model
The OSI model or the Open System Interconnection model is a specific type of model
that standardises and characterise the communication protocols of a system (Zhao et al.
2018). The OSI model is one of the important aspects of networking. As it is mentioned that
the OSI model establishes the communication protocol, it can be used for setting the
connection among the workstations so that the whole network is able to function in a proper
way without any interruption in the communication process. Though the OSI model is one of
the best ways of establishing communication, it has certain limitations. In this aspect, the
system must be highly adaptable so that the OSI model can be used (Abdul and Umar 2017).
The OSI model can be very much useful to ensure that all the components of the system are
functioning properly, and they are communicating with each other in a proper function. The
OSI model consists of a total of seven layers. For this network architecture, all of these seven
layers will be utilized.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

6NETWORK DESIGN AND IMPLEMENTATION
4. Component Evaluation of the Network Architecture
To implement the desired network architecture in the Speedfix.co.uk, several types of
components will be required for establishing a proper functional network. Thus, in this case,
in-depth knowledge is required for all the components, which will be required for this
network architecture. In the following section, a brief discussion is done regarding all the
network components which are mandatory in this case.
4.1 Switch
The switch is one of the important networking components that are mandatory for
creating the current desired network architecture for the Speedfix.co.uk. The network switch,
which is also known as the switching hub, is actually networking hardware that is used for
connecting devices on a specific computer network. Here, the switch uses packet switching
procedure for sending and receiving from the targeted device (Sood, Yu and Xiang 2016). In
the current network architecture, the switch plays an important role. In the current
architecture, there are several sub-routers, and all of them must be connected with their
respective department. This criterion can be fulfilled using the switches. Specifically for this
architecture, separate switches need to be used. Here all of the switches will have full control
over the switching of the network (Sule et al. 2018). It means that the whole connection can
be switched on or off, which will be coming directly from the main router, where the main
router will be connected to the servers of the organization. For this reason, implementing a
proper switch is important for this architecture.
4. Component Evaluation of the Network Architecture
To implement the desired network architecture in the Speedfix.co.uk, several types of
components will be required for establishing a proper functional network. Thus, in this case,
in-depth knowledge is required for all the components, which will be required for this
network architecture. In the following section, a brief discussion is done regarding all the
network components which are mandatory in this case.
4.1 Switch
The switch is one of the important networking components that are mandatory for
creating the current desired network architecture for the Speedfix.co.uk. The network switch,
which is also known as the switching hub, is actually networking hardware that is used for
connecting devices on a specific computer network. Here, the switch uses packet switching
procedure for sending and receiving from the targeted device (Sood, Yu and Xiang 2016). In
the current network architecture, the switch plays an important role. In the current
architecture, there are several sub-routers, and all of them must be connected with their
respective department. This criterion can be fulfilled using the switches. Specifically for this
architecture, separate switches need to be used. Here all of the switches will have full control
over the switching of the network (Sule et al. 2018). It means that the whole connection can
be switched on or off, which will be coming directly from the main router, where the main
router will be connected to the servers of the organization. For this reason, implementing a
proper switch is important for this architecture.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

7NETWORK DESIGN AND IMPLEMENTATION
(Figure 1: Network Switch)
(Source: Mirzaei et al. 2016)
4.2 Router
Same as the switch, the router is another important component used for the
networking purpose. A router is a specific type of networking component which is used for
forwarding the data packets between the computer networks. The routers can be also used for
executing the traffic directing functions for internet services. The router transmits important
assets which include emails and web pages as the data packets (Shen et al. 2017). In the
current network architecture, there is an important role of routers. There will be one router
which will be acting as the main router while the other routers will be the sub routers. There
will be only one main router, while the sub-routers will be department specific. It means there
will be separate sub-routers for all the departments. Here, all the sub-routers will be
connected to the main router so that wireless internet connection can be provided to each of
the department of the Speedfix.co.uk. In the current aspects, the data packets need to be
provided to each of the workstations and the printers (Liu et al. 2019), and for this reason,
both the main router and the sub-routers are important in this context.
(Figure 1: Network Switch)
(Source: Mirzaei et al. 2016)
4.2 Router
Same as the switch, the router is another important component used for the
networking purpose. A router is a specific type of networking component which is used for
forwarding the data packets between the computer networks. The routers can be also used for
executing the traffic directing functions for internet services. The router transmits important
assets which include emails and web pages as the data packets (Shen et al. 2017). In the
current network architecture, there is an important role of routers. There will be one router
which will be acting as the main router while the other routers will be the sub routers. There
will be only one main router, while the sub-routers will be department specific. It means there
will be separate sub-routers for all the departments. Here, all the sub-routers will be
connected to the main router so that wireless internet connection can be provided to each of
the department of the Speedfix.co.uk. In the current aspects, the data packets need to be
provided to each of the workstations and the printers (Liu et al. 2019), and for this reason,
both the main router and the sub-routers are important in this context.

8NETWORK DESIGN AND IMPLEMENTATION
(Figure 2: Network Router)
(Source: Mondal et al. 2016)
4.3 Connecting Cables
The connecting cables are one of the important components that are mandatory for the
current network architecture for the Speedfix.co.uk. These are actually the primary
component for designing a network architecture. The connecting cables help to establish the
connection among various networking component. These connecting cables will be
transferring the signals, including the data packets from one device to another device. In this
network infrastructure, the DTE connecting cables are one of the important cables. Here, the
DTE connecting cables will be used for establishing the connection between the main routers
and the sub-routers within the network architecture (Chaudhary, Kumar and Kaushik 2018).
By using the DTE cables, all the data packets can be sent from the main router to the sub-
router efficiently. In this way, an effective connection can be established among the routers.
A specific type of copper wires is another type of connecting cable that is required in
this aspect. In this network architecture, the copper connecting wires will be used for
establishing the connection between the switches and the workstation. By using the copper
wire connection, a secured and fast connection can be established among the switches and the
(Figure 2: Network Router)
(Source: Mondal et al. 2016)
4.3 Connecting Cables
The connecting cables are one of the important components that are mandatory for the
current network architecture for the Speedfix.co.uk. These are actually the primary
component for designing a network architecture. The connecting cables help to establish the
connection among various networking component. These connecting cables will be
transferring the signals, including the data packets from one device to another device. In this
network infrastructure, the DTE connecting cables are one of the important cables. Here, the
DTE connecting cables will be used for establishing the connection between the main routers
and the sub-routers within the network architecture (Chaudhary, Kumar and Kaushik 2018).
By using the DTE cables, all the data packets can be sent from the main router to the sub-
router efficiently. In this way, an effective connection can be established among the routers.
A specific type of copper wires is another type of connecting cable that is required in
this aspect. In this network architecture, the copper connecting wires will be used for
establishing the connection between the switches and the workstation. By using the copper
wire connection, a secured and fast connection can be established among the switches and the
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
9NETWORK DESIGN AND IMPLEMENTATION
workstations. This type of wire will also safeguard the information which will be transferred
through this wire (Lamberti et al. 2016). In this way, any type of data theft due to the data
transfer medium can be minimised. For this network architecture, all of the connecting cables
that will be utilized must be of high quality. By using the high-quality components efficient
and an effective connection can be established. This criterion is important for the
organization so that it can be ensured that the business of efficient enough so that it can
handle the high amount of pressure if this type of situation occurs. Also, several advanced
protocol systems can be used to make network architecture more responsive and advanced.
(Figure 3: Network Cables)
(Source: Mokhtar et al. 2019)
4.4 VLAN
VLAN refers to a Virtual Area Network that forms a primary component within the
field of networking having dealt with the domain related to broadcasting. This takes place in
reference to the partition belonging to the computer network that is isolated and consists of
workstations. This type of wire will also safeguard the information which will be transferred
through this wire (Lamberti et al. 2016). In this way, any type of data theft due to the data
transfer medium can be minimised. For this network architecture, all of the connecting cables
that will be utilized must be of high quality. By using the high-quality components efficient
and an effective connection can be established. This criterion is important for the
organization so that it can be ensured that the business of efficient enough so that it can
handle the high amount of pressure if this type of situation occurs. Also, several advanced
protocol systems can be used to make network architecture more responsive and advanced.
(Figure 3: Network Cables)
(Source: Mokhtar et al. 2019)
4.4 VLAN
VLAN refers to a Virtual Area Network that forms a primary component within the
field of networking having dealt with the domain related to broadcasting. This takes place in
reference to the partition belonging to the computer network that is isolated and consists of
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

10NETWORK DESIGN AND IMPLEMENTATION
the objective to connect the data-linking layer of the network. In regards to the network of the
speedfix.co.uk, the network has been designed in such a way that all the hosts or might as
well be termed as workstations have been placed under the same router (Cao et al. 2020).
This way the administrators have the provision to get access to all the hosts for monitoring
the connectivity that has been provided to the workstations from the common server present
in the common room.
4.5 Trunking
Within the field of telecommunications, trunking particularly refers to the primary
method of provisioning the access to the individual network to multiple clients by sharing a
collective set of lines or frequencies. This is done collectively instead of provisioning them
on an individual basis. This method also has the primary inclusion of port trunking where the
usage of multiple network connections that are concurrent to specifically aggregate the link
speed to each of the port or the cable that is a part of the network (Liu, He and Meng 2016).
In the network diagram that has been developed for the company named speedfix.co.uk, the
method of trunking has been done on the nodes, which do not have the access to the other
departments of the organization.
4.6 Access control
Access control refers to the particular method of enhancing or increasing the security
that lies within a respective business organization. This particular procedure is carried out by
restricting the availability of all the resources that is connected to a network through the
devices present at the endpoint of the major network. This is done to segregate the resources
that each individual department of a respective network deals with to mitigate the confusion
of the resources that communicate through the common communication channel belonging to
the same network (Bierman and Bjorklund 2018). In regards to this network of the
speedfix.co.uk organization, each of the departments have been provided with specific set of
the objective to connect the data-linking layer of the network. In regards to the network of the
speedfix.co.uk, the network has been designed in such a way that all the hosts or might as
well be termed as workstations have been placed under the same router (Cao et al. 2020).
This way the administrators have the provision to get access to all the hosts for monitoring
the connectivity that has been provided to the workstations from the common server present
in the common room.
4.5 Trunking
Within the field of telecommunications, trunking particularly refers to the primary
method of provisioning the access to the individual network to multiple clients by sharing a
collective set of lines or frequencies. This is done collectively instead of provisioning them
on an individual basis. This method also has the primary inclusion of port trunking where the
usage of multiple network connections that are concurrent to specifically aggregate the link
speed to each of the port or the cable that is a part of the network (Liu, He and Meng 2016).
In the network diagram that has been developed for the company named speedfix.co.uk, the
method of trunking has been done on the nodes, which do not have the access to the other
departments of the organization.
4.6 Access control
Access control refers to the particular method of enhancing or increasing the security
that lies within a respective business organization. This particular procedure is carried out by
restricting the availability of all the resources that is connected to a network through the
devices present at the endpoint of the major network. This is done to segregate the resources
that each individual department of a respective network deals with to mitigate the confusion
of the resources that communicate through the common communication channel belonging to
the same network (Bierman and Bjorklund 2018). In regards to this network of the
speedfix.co.uk organization, each of the departments have been provided with specific set of
11NETWORK DESIGN AND IMPLEMENTATION
resources to perform special activities, as a result each of the department have been
provisioned with access controls so that no other departments have the provision to access the
other departments and intervene within the normal procedures of the same.
4.7 DHCP
This term stands for the dynamic host configuration protocol and is a network
protocol that is specifically used upon an IP network wherein the DHCP server in an
automated manner assigns the IP address along with some other information to each
individual host. This provisions the host with the explicit provision to carry out an effective
communication with the other existing endpoints within the same network of the organization
(Rajput, Tewani and Dubey 2016). Along with this, the DHCP also carries out the activity of
assigning the subnet mask, the domain name server (DNS), the default gateway as well as the
other existing configurations of the devices within the network.
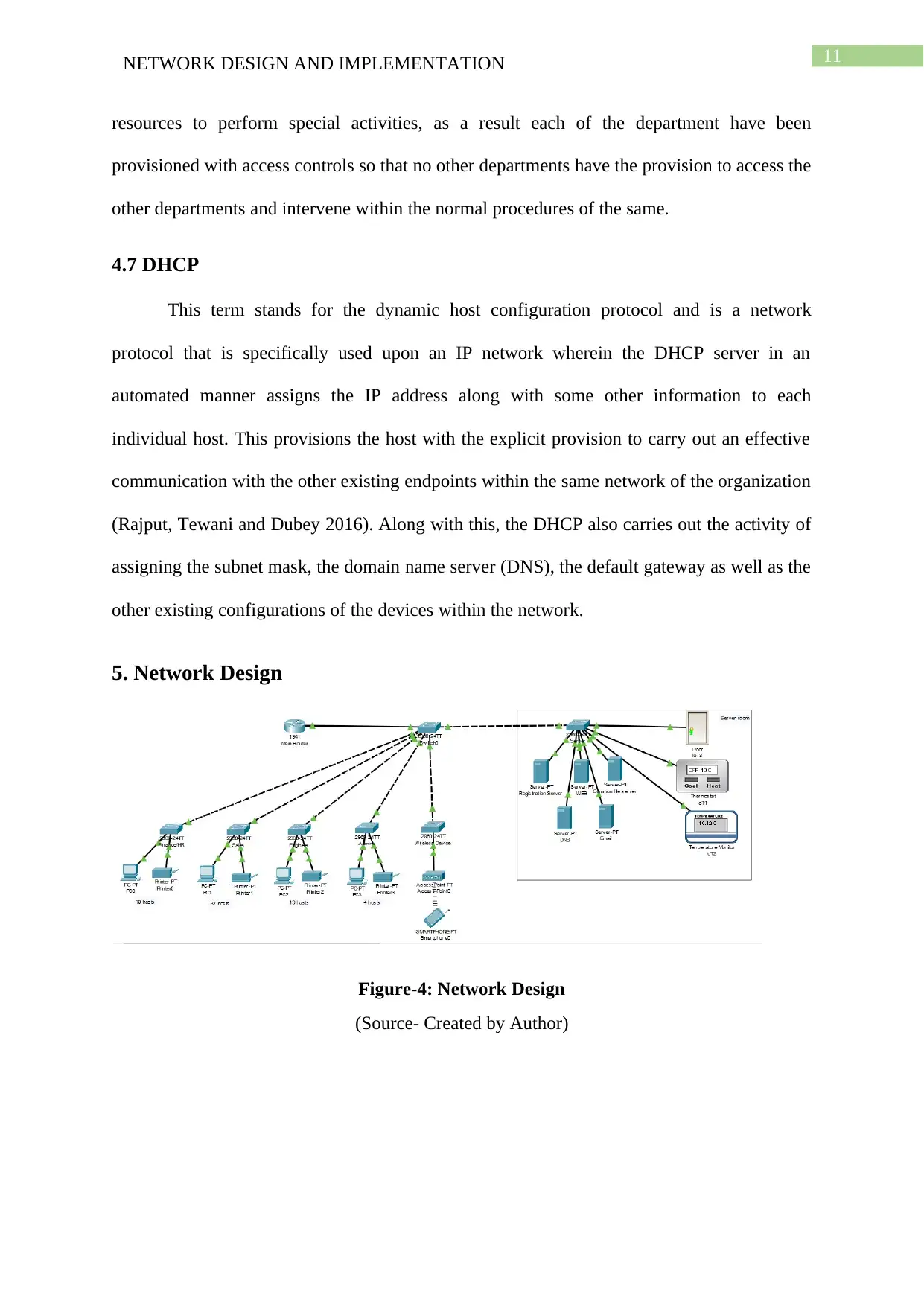
5. Network Design
Figure-4: Network Design
(Source- Created by Author)
resources to perform special activities, as a result each of the department have been
provisioned with access controls so that no other departments have the provision to access the
other departments and intervene within the normal procedures of the same.
4.7 DHCP
This term stands for the dynamic host configuration protocol and is a network
protocol that is specifically used upon an IP network wherein the DHCP server in an
automated manner assigns the IP address along with some other information to each
individual host. This provisions the host with the explicit provision to carry out an effective
communication with the other existing endpoints within the same network of the organization
(Rajput, Tewani and Dubey 2016). Along with this, the DHCP also carries out the activity of
assigning the subnet mask, the domain name server (DNS), the default gateway as well as the
other existing configurations of the devices within the network.
5. Network Design
Figure-4: Network Design
(Source- Created by Author)
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
1 out of 17
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2025 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.



